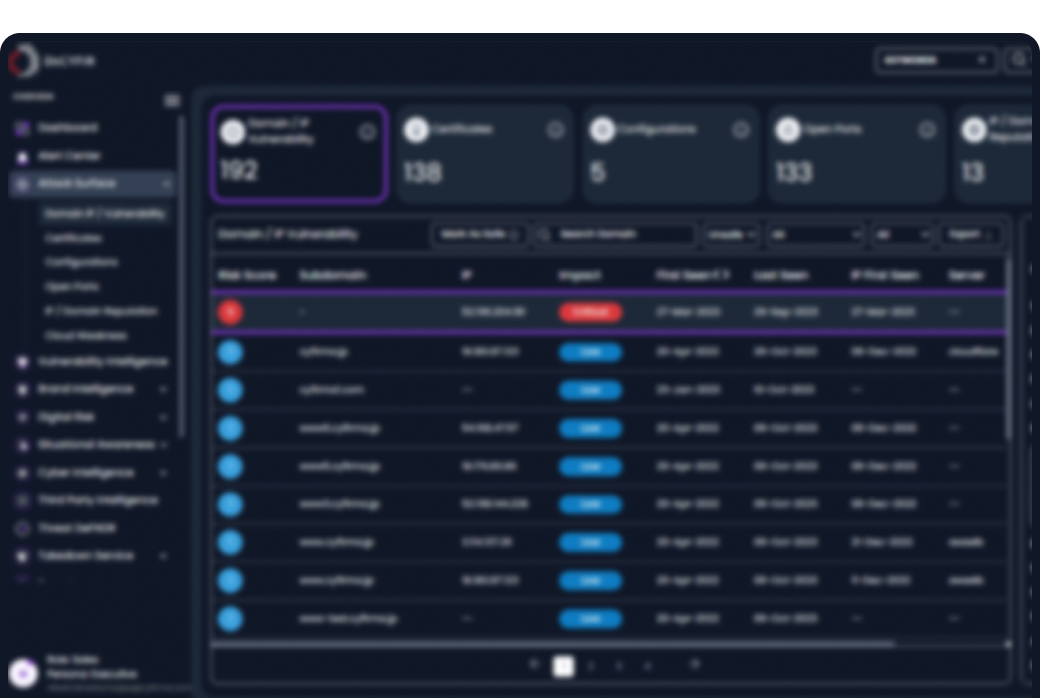
The Common Vulnerability Scoring System (CVSS) is a useful measure of severity but a poor measure of risk. A “Critical” 9.8 vulnerability in a publicly exposed, non-essential system may be less dangerous than a “Medium” 6.5 vulnerability in an internet-facing system that is actively being exploited in the wild and is relevant to your industry. SOC and vulnerability management teams are paralyzed by thousands of vulnerabilities and lack the context to know which ones to patch immediately.
We weaponize intelligence. Our platform correlates the vulnerabilities found on your assets (from Pillar 1) with a real-time stream of threat intelligence. We analyze:
The output is a dynamic, risk-based priority list. You are not told to “patch all Criticals”; you are told to “patch this specific vulnerability on this specific server within 48 hours because a known APT group is using it against companies like yours.”
Dramatic reduction in mean time to patch (MTTP) for high-risk vulnerabilities. Security teams can focus their limited resources on the 2% of vulnerabilities that represent 98% of the actual risk, drastically improving efficiency and reducing the window of exposure.
By combining cyber-intelligence with attack surface discovery and digital risk protection, CYFIRMA delivers predictive, personalized, contextual, outside-in and multi-layered insights to help clients prepare against upcoming attacks.

DeCYFIR’s 9-Pillar Intelligence Preemptive ETLM Framework delivers comprehensive, proactive cyber defense through continuous, adversary-focused discovery and response.
You cannot defend what you cannot see. We are illuminating every shadow domain, forgotten asset, and silent exposure before the adversary ever see it.
Learn MoreContinuously maps IT and OT assets to identify vulnerabilities like misconfigurations, cloud gaps, open ports, weak certificates, and exposed logins or APIs. Combines threat intelligence, brand and third-party risks to deliver prioritized, actionable insights into critical attack paths based on adversary intent.
Learn More »Proactive monitoring for impersonation, fraud, and brand abuse across digital channels
Learn More »Detection and mitigation of data leaks, cloud exposures, and executive threats
Learn More »Assessment of supply chain vulnerabilities commonly exploited by attackers.
Learn More »Industry-specific, geo-targeted analysis of emerging threat trends.
Learn More »Provides actionable insights into attackers’ motives, tactics, and timelines, delivering early, environment-specific threat warnings tailored to the customer’s industry and location.
Learn More »Contextual, real-world threat education tailored for teams.
Learn More »Customized deception playbooks and intelligence from sector-focused sources, such as simulating supply-chain attacks in manufacturing to trap reconnaissance efforts or leveraging industry insider leaks for hyper-precise misdirection.
Learn More »CYFIRMA is proud to be recognized by some of the most important and influential publications and organizations around the world.
Join hundreds of organizations already using DeCYFIR to continuously monitor their threat landscape to preempt cyberattacks.
Get started