


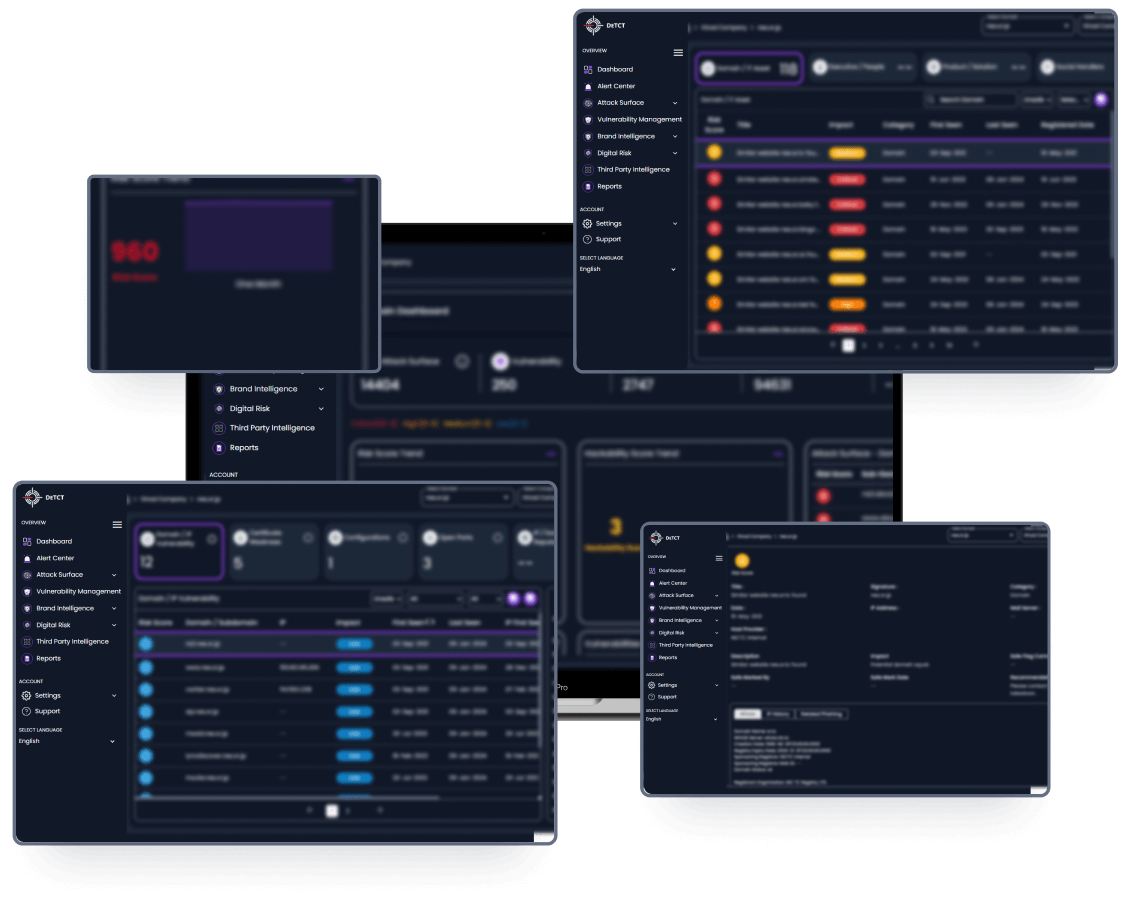




DeTCT is designed to help leaders mitigate the rising digital risk so they can focus on building a thriving business



DeTCT is the only fully automated, proactive monitoring service what works 24x7 to help you stay on top of rising cyber threats.

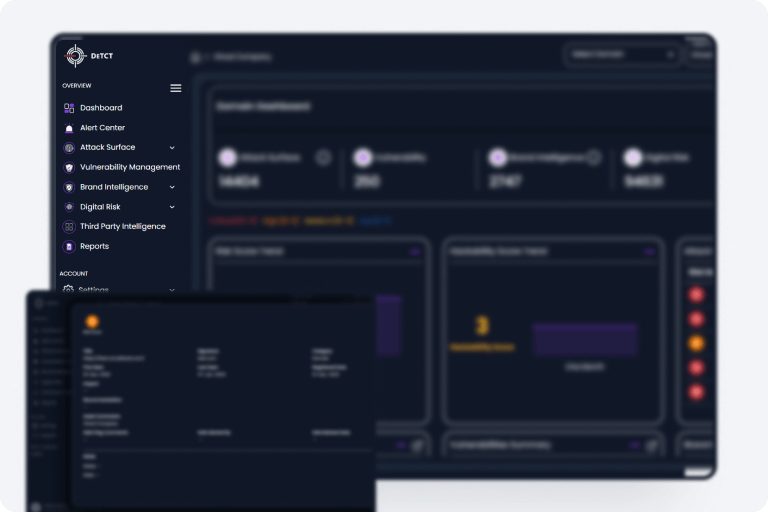

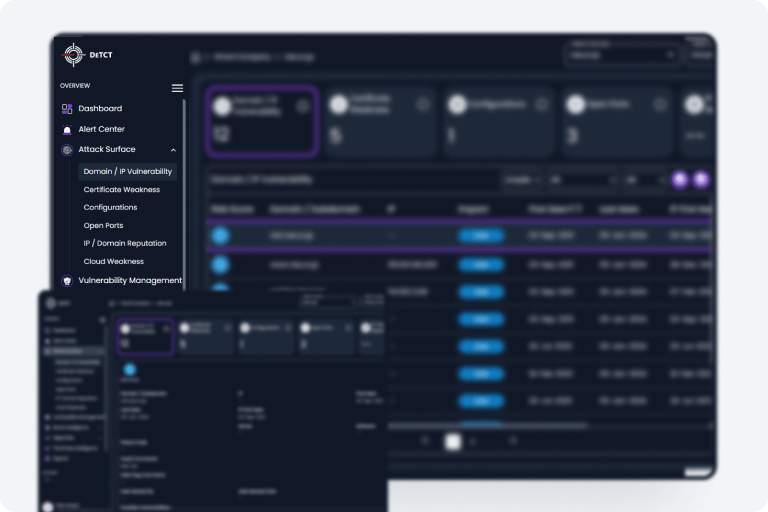
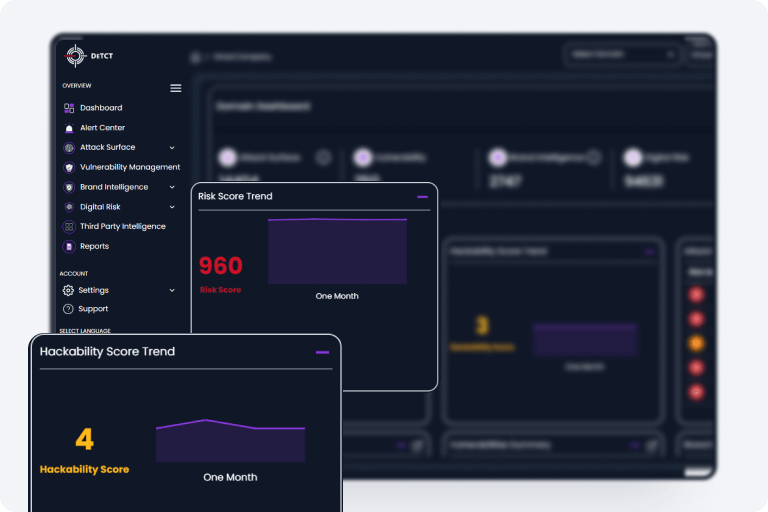
DeTCT monitors your attack surface so you would never be blindsided.

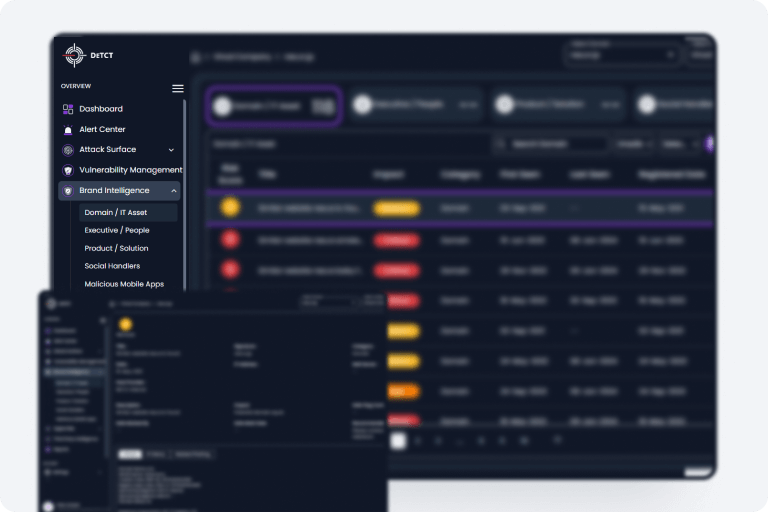

DeTCT scans deep/dark/surface web and social media to look to signs of impersonation and infringement
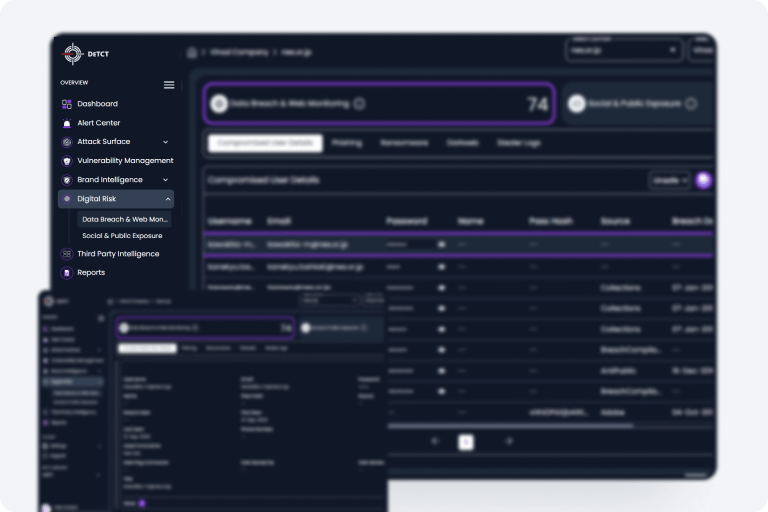
DeTCT brings to your attention data which has been stolen and available for sale in underground marketplaces. This includes data which has been exfiltrated by ransomware groups.

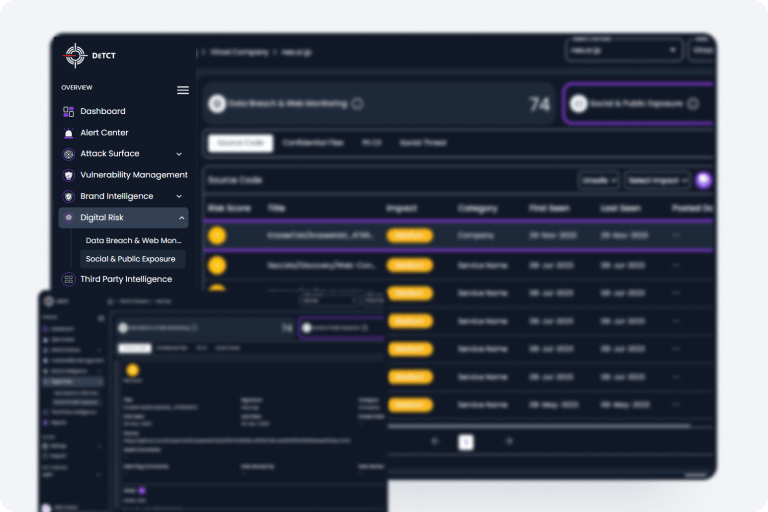

With DeTCT, you would always know if your IP and confidential data has been exposed, including lookalike or malicious apps. You will also receive alerts on social sentiments that could present a threat to you or your business

"DeTCT saves us from becoming a victim of malicious cyberattacks and risk eroding the trust our customers have placed on us by keeping a constant watch on our digital footprint and alerting us to any exposures the moment these occur.
This has given us precious lead time to quickly kick in remedial actions before a full-blown attack is upon us. DeTCT has unlocked visibility which we never thought possible."
Managing Director
CEO, Raptech






Simple, transparent pricing that grows with you. Try free for 14 days.
Trial Plan
Everything you need to know about the product and billing. Can’t find the answer
you’re looking for? Please chat with our friendly team.
Join the many businesses who are already using DeTCT to secure their digital assets
Get Started