Most threat intelligence is historical; it tells you about attacks that have already happened. By the time an Indicator of Compromise (IOC) is published, the sophisticated adversaries have already moved on.
We move beyond IOCs to focus on Indicators of Attack (IOAs) and, most importantly, Indicators of Intent (IOIs). By analyzing adversary communication on underground forums, tracking the development of new malware tools, and modeling campaign patterns, we can forecast attacks before they are launched. This is the difference between being told, “You were attacked with this malware yesterday,” and being warned, “A threat group is preparing to use a new phishing kit against the financial sector next week.”
This is the cornerstone of preemption. It allows organizations to shift resources before an attack wave hits, to pre-configure defenses against specific anticipated TTPs, and to warn the “human firewall” (Pillar 8) about the specific social engineering lures they are about to encounter.
By combining cyber-intelligence with attack surface discovery and digital risk protection, CYFIRMA delivers predictive, personalized, contextual, outside-in and multi-layered insights to help clients prepare against upcoming attacks.

DeCYFIR’s 9-Pillar Intelligence Preemptive ETLM Framework delivers comprehensive, proactive cyber defense through continuous, adversary-focused discovery and response.
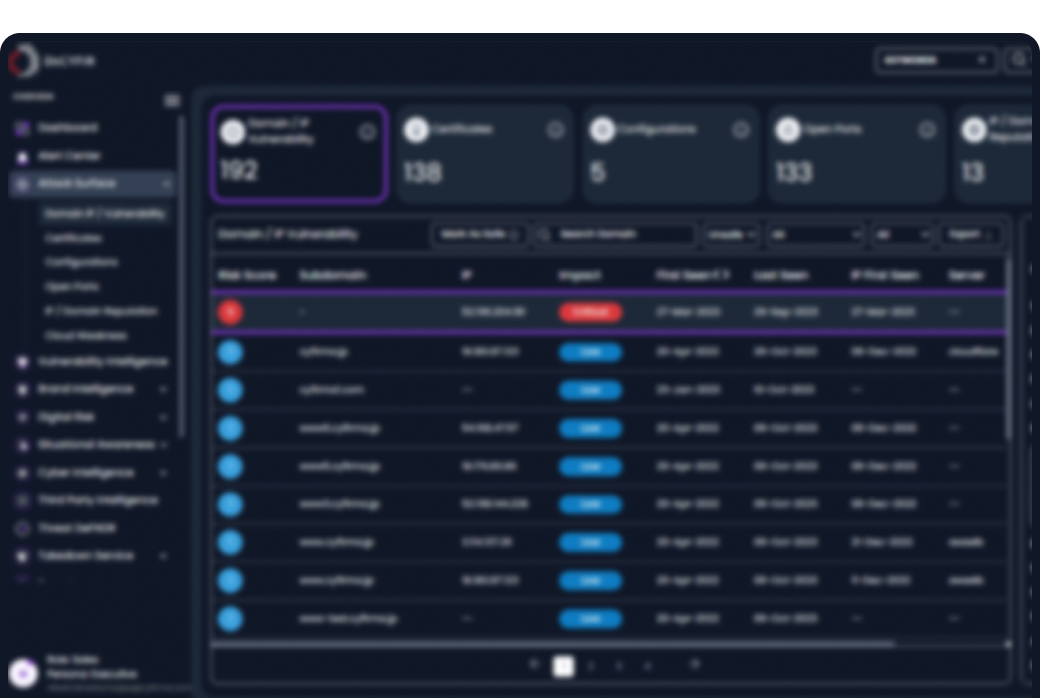
You cannot defend what you cannot see. We are illuminating every shadow domain, forgotten asset, and silent exposure before the adversary ever see it.
Learn MoreContinuously maps IT and OT assets to identify vulnerabilities like misconfigurations, cloud gaps, open ports, weak certificates, and exposed logins or APIs. Combines threat intelligence, brand and third-party risks to deliver prioritized, actionable insights into critical attack paths based on adversary intent.
Learn More »Real-time detection of weaknesses in applications, operating systems, APIs, and misconfigurations. Integrates threat intelligence to deliver prioritized and actionable insights into vulnerabilities based on adversary intent.
Learn More »Proactive monitoring for impersonation, fraud, and brand abuse across digital channels
Learn More »Detection and mitigation of data leaks, cloud exposures, and executive threats
Learn More »Assessment of supply chain vulnerabilities commonly exploited by attackers.
Learn More »Industry-specific, geo-targeted analysis of emerging threat trends.
Learn More »Contextual, real-world threat education tailored for teams.
Learn More »Customized deception playbooks and intelligence from sector-focused sources, such as simulating supply-chain attacks in manufacturing to trap reconnaissance efforts or leveraging industry insider leaks for hyper-precise misdirection.
Learn More »CYFIRMA is proud to be recognized by some of the most important and influential publications and organizations around the world.
Join hundreds of organizations already using DeCYFIR to continuously monitor their threat landscape to preempt cyberattacks.
Get started