Seven pillars of threat views include attack surface discovery, vulnerability intelligence, brand intelligence, digital risk discovery and protection, situational awareness, third party risk and cyber-intelligence

Predict cyber-attacks targeting your organization and subsidiaries before cybercriminals can cause harm to your business. Early warnings and alerts help you prioritize risk and be well prepared to fend off attacks

Data points and insights are tailored to match the technology you are using, the industry you are operating in, and your geolocation. Remove noise and reduce false positives to ensure the high-impact alerts are actioned upon

Complete contextual details of the external threat including adversary details, TTPs, the path of attack, malicious hosting site, affiliated cybercrime campaign, and much more

Strategic, management and tactical intelligence are provided on the platform allowing both business and technology leaders to gain insights into their external threat landscape and risk posture

Detailed insights into your external threat landscape including intel on the cybercriminals interested in you, their motive and intent, when can they attack and how are they going to attack
Businesses can turn the tide against cybercriminals with quality cyber-intelligence to give them the view through the adversary’s lens and take remedial actions to stop an attacker in his/her track.
Navigating the fog of cyberwar and delivering intelligence around emerging threats should not only be restricted to government organizations. Enterprises should also have access to military-grade intelligence, tuned to meet their commercial needs. Meet DeCYFIR – predictive and actionable intelligence for companies to stay ahead of adversarial forces.
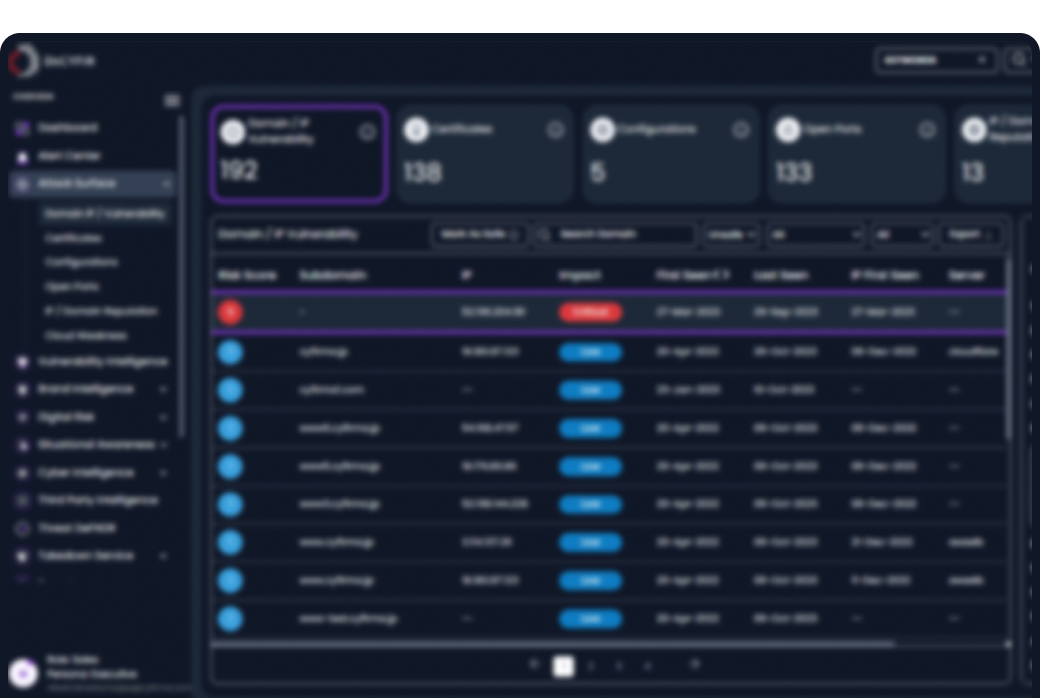
Real-time continuous monitoring to identify shadow IT or porous systems which can be accessed by cybercriminals.
Learn MorePersonalized to your needs
Developed for both business and technology leaders to support risk strategies
Case studies from some of our customers who have chosen DeCYFIR's intelligence-led approach to build a more secure enterprise
Predictive And Non-intrusive Solution Rather Than Expensive & Reactive Silo Offerings

DeCYFIR is the industry’ first External Threat landscape management platform that delivers predictive, personalized and contextualized cyber intelligence enriched with attack surface and digital risk insights

The DeCYFIR platform informs defenders of impending cyberattacks at the stage of reconnaissance and weaponization before the adversary has started exploitation
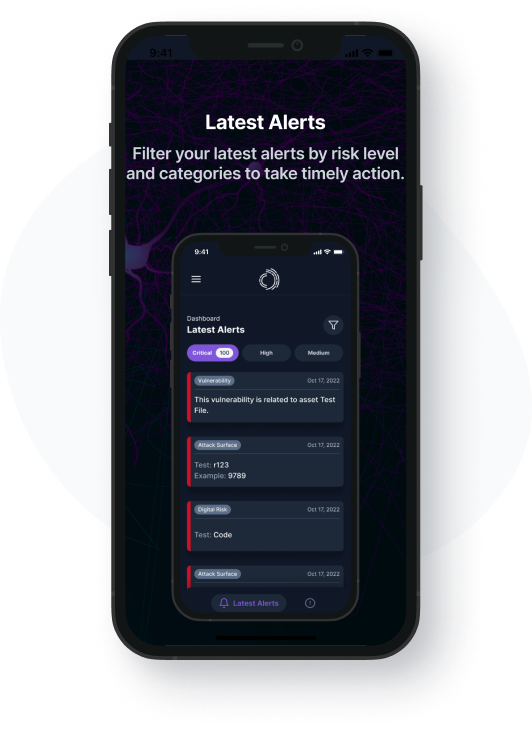
With the Alert App, clients gain the time advantage to take swift actions to close security gaps before cyber adversaries can cause damage
Clients can customize the notifications of the Alert App to support their risk posture management objectives