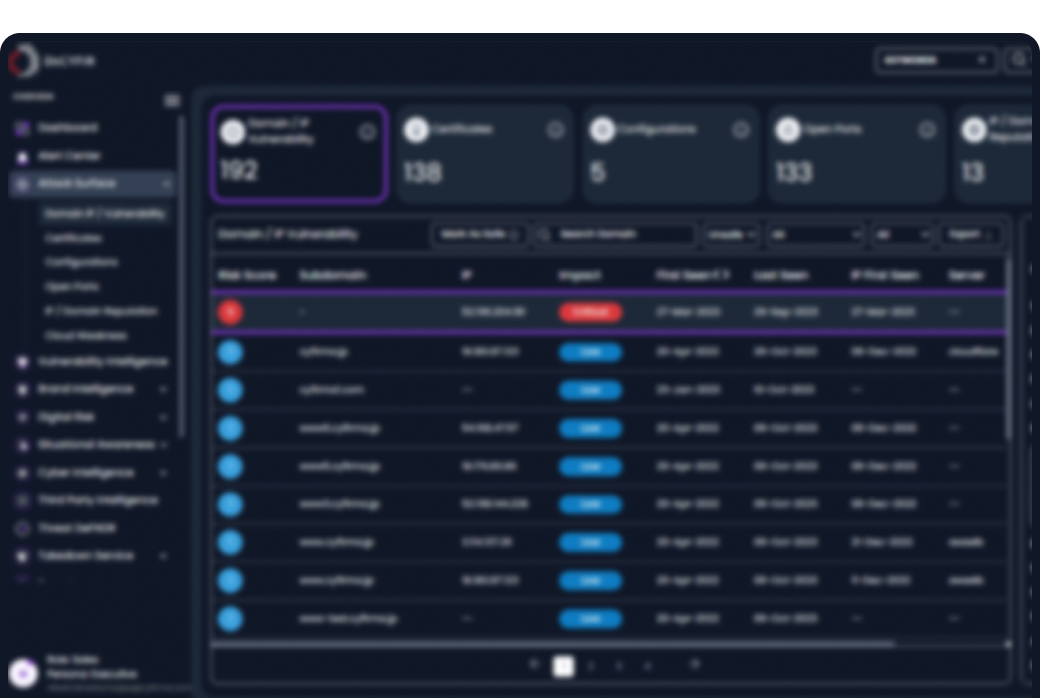
The modern digital estate is a constantly evolving entity. Beyond the known corporate network and cloud instances, organizations contend with shadow IT, forgotten domains, misconfigured APIs, acquired company assets, and employee-created cloud storage. This “unknown” attack surface is where adversaries spend their first and most productive weeks of reconnaissance. Traditional asset discovery tools are often internal-focused and lack the adversary’s perspective.
We provide a continuous, automated discovery process that scans the entire internet from an attacker’s viewpoint. Using a combination of advanced reconnaissance techniques, passive DNS analysis, SSL certificate parsing, and dark web monitoring, we identify every asset that can be associated with your organization. This isn’t a periodic scan; it’s a persistent surveillance system that alerts you to new exposures—a new S3 bucket, a forgotten subdomain, a rogue IoT device—as they appear, often before your own IT team is aware.
Organizations achieve complete visibility of their external attack surface. This allows for effective security governance, reduces the “low-hanging fruit” that attackers rely on, and provides the foundational inventory for all other security controls. It transforms security from a guessing game into a science of managed risk.

By combining cyber-intelligence with attack surface discovery and digital risk protection, CYFIRMA delivers predictive, personalized, contextual, outside-in and multi-layered insights to help clients prepare against upcoming attacks.

DeCYFIR’s 9-Pillar Intelligence Preemptive ETLM Framework delivers comprehensive, proactive cyber defense through continuous, adversary-focused discovery and response.
You cannot defend what you cannot see. We are illuminating every shadow domain, forgotten asset, and silent exposure before the adversary ever see it.
Learn MoreReal-time detection of weaknesses in applications, operating systems, APIs, and misconfigurations. Integrates threat intelligence to deliver prioritized and actionable insights into vulnerabilities based on adversary intent.
Learn More »Proactive monitoring for impersonation, fraud, and brand abuse across digital channels
Learn More »Detection and mitigation of data leaks, cloud exposures, and executive threats
Learn More »Assessment of supply chain vulnerabilities commonly exploited by attackers.
Learn More »Industry-specific, geo-targeted analysis of emerging threat trends.
Learn More »Provides actionable insights into attackers’ motives, tactics, and timelines, delivering early, environment-specific threat warnings tailored to the customer’s industry and location.
Learn More »Contextual, real-world threat education tailored for teams.
Learn More »Customized deception playbooks and intelligence from sector-focused sources, such as simulating supply-chain attacks in manufacturing to trap reconnaissance efforts or leveraging industry insider leaks for hyper-precise misdirection.
Learn More »CYFIRMA is proud to be recognized by some of the most important and influential publications and organizations around the world.
Join hundreds of organizations already using DeCYFIR to continuously monitor their threat landscape to preempt cyberattacks.
Get started