



A virtual private server (VPS) hosting offers a similar experience to dedicated hosting without the high expenses and maintenance burden of a dedicated server, especially for businesses or individuals whose websites or apps have outgrown shared hosting.
In an unintended manner, VPS can be used to host criminal infrastructure components, such as phishing pages or control panels for botnets, and leveraged as “jump servers” that help attackers break into organizational infrastructures more securely. VPS also helps attackers ‘mask’ their true source IP address and, therefore, their physical location. As VPS can be conveniently purchased from commercial providers, the pain of resource acquisition is limited, and considering the nifty features that help in defense evasion, the ROI makes VPS an attractive option for threat actors.
What VPS services are used by Threat Actor groups
Most common pattern of VPS use by Threat Actor groups
Elaborated further as follows:
According to Law Enforcement Agencies, Chinese state-sponsored actors utilized command line utility programs like PuTTY Link (Plink) to establish SSH tunnels [T1572] between internal hosts and leased virtual private server (VPS) infrastructure.
| Tactics | Techniques |
| TA0011: Command and Control | T1572: Protocol Tunneling |
These actors often conducted system network configuration discovery [T1016.001] on these host networks by sending hypertext transfer protocol (HTTP) requests to C2 infrastructure in order to illuminate the external public IP address.
| Tactics | Techniques |
| TA0007: Discovery | T1016.001: System Network Configuration Discovery |
Following are the Commands:
The use of overseas VPS servers is an ongoing trend for some time and is unlikely to change anytime soon. For example, for a Chinese Threat Actors, it is a lot easier to evade detection by using a US-based AWS server as a proxy, then their own server in the basement of a military building. VPS hosting services provide an elegant and easy way to get IP from a “clean” and trustworthy IP range from anywhere in the world.
VPS are most commonly used by nation-state Threat Actors as a proxy or “in the middle” bridges between actual servers and targeted victims. Since VPS are internet-facing and exposed to anyone, including other TAs, counterintelligence and law enforcement are likely to probe. Therefore, hosting any kind of sensitive data or critical infrastructure is considered a bad practice.
Typically, TAs do host everything themselves locally, where they have absolute control and the option to physically destroy all evidence if needed. VPS do host only the necessary minimum to be able to reach the victim from locally hosted systems and mask their real locations.
One of the most common uses of VPS by TAs is landing phishing sites. Legitimate services and their free trials or promotions are frequently abused to host such sites.

FIG: XSS.IS forums advice on where to ideally host a phishing site.
Another common use case is hosting simple proxies / RDP / VPN gateways to mask the real location of Command & Control (C2) servers. Often TAs also seek specific IP ranges of these servers to look more legitimate and to avoid raising red flags by being in their actual and known bad IP ranges.
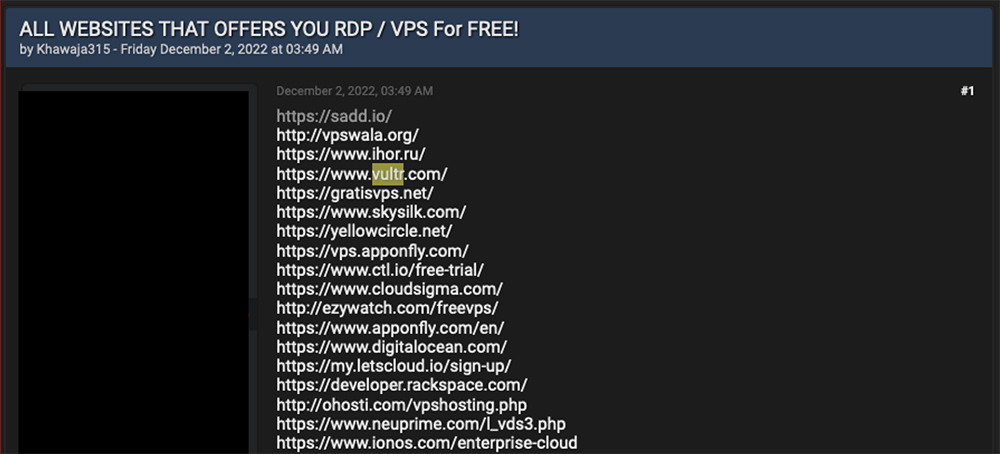
FIG: Breached forums post on FREE VPS with RDP.
Furthermore, both cybercriminals and nation-state THREAT ACTORs favor the use of compromised accounts and VPS. This offers great deniability and obfuscation of real location.

FIG: Breached forums hosting services marketplace offering AWS and Azure accounts
Another popular solution is the so-called “bulletproof hosting” (BPH) service. Using techniques like DNS Fast Flux, these services provide hosting distributed on botnet networks, privately hosted VPS, or compromised cloud accounts. While the malicious content is hosted on one server, their domain’s IP keeps rotating from a pool of thousands of different IPs and is essentially untraceable.

FIG: Google dork “inurl:bulletproof ”VPS”” shown nearly 2000 results for BPH service.
Lastly, there are what seems like legitimate businesses providing anonymous hosting, catering to the legitimate demand from privacy-conscious users and businesses that are looking to avoid corporations or their own or foreign governments from spying. One of the most prominent options in recent months and a good example is CrazyRDP[.]com.
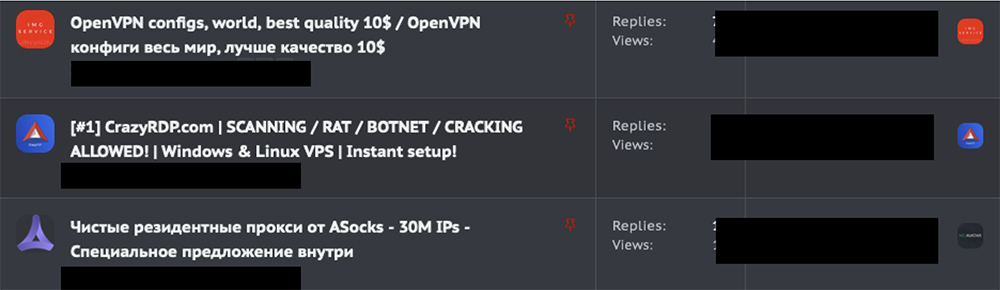
FIG: CrazyRDP advertised on XSS.IS forum.

FIG: CrazyRDP advertised on cracked.io forum.

FIG: CrazyRDP website
The infrastructure component of cybercrime is undoubtedly critical to the success of almost every form of cybercrime we see today. VPS is an important component of cybercriminals’ infrastructure. Threat actors prefer to host everything locally, where they have complete control and the option to physically destroy all evidence, if necessary, but in order to maintain anonymity and avoid being tracked by law enforcement, they use VPS to reach the victim from locally hosted systems and mask their true locations. Pricing, features, and benefits of using VPS in cybercriminal infrastructure enable increased buying and selling of such services, and we see no reason for this trend to change.