



Recently, CYFIRMA Research published a report on a new threat actor group known as FusionCore. In a follow-up, we were able to get in touch with “NecroSys”, who is the developer of SarinLocker ransomware. Recently, it was announced that the main developer of Typhon Reborn stealer is no longer part of the group. We asked some questions to learn more about their recent activities, including their alleged links with APT groups and what is on the horizon since a founding member and main developer has left the group.
ShapeCYFIRMA: Just to confirm, what should we call you and your group?
NecroSys: FusionCore is my group, and my alias is NecroSyS.
CYFIRMA: Before we go ahead, why are you talking to us?
NecroSys: We don’t mind answering questions. A lot of information we have seen in articles about us has been inaccurate. All people need to do if they want information is to simply ask. We don’t hate researchers.
CYFIRMA: To properly introduce you, how would you describe yourself in terms of business? (Access Broker, Trafficker, etc.)
NecroSys: I am a Malware developer and also handle most of the marketing and negotiations with other groups, etc. If that also counts. In general, I would consider myself a regular software developer. It’s not different from any other kinds of software development, other than its intended use.
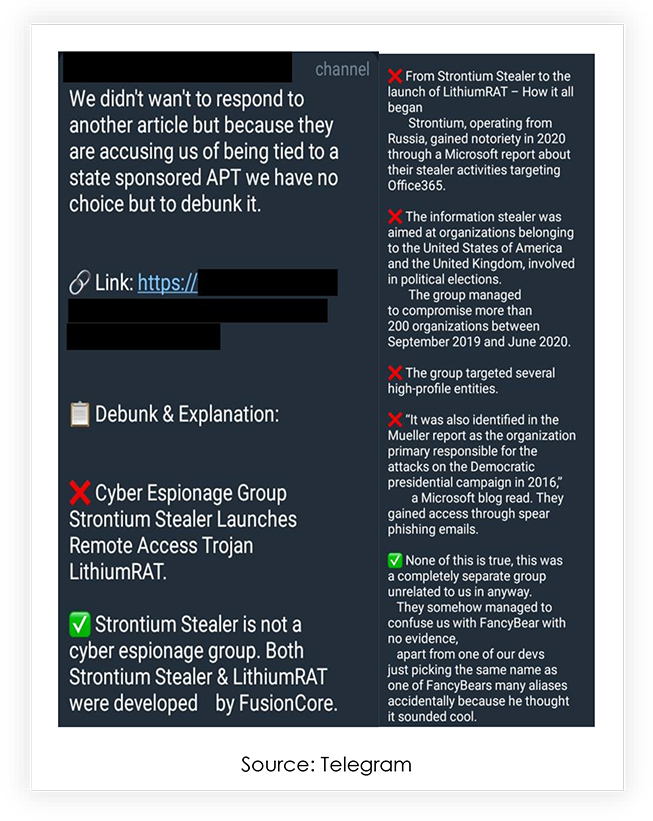
CYFIRMA: There was a recent article about you published; can you explain how that article made you feel or affected your operations?
NecroSys: It didn’t necessarily affect our operations; we were just more worried about it drawing the attention of authorities like the FBI. If they read the article and thought we were connected to more serious groups they were already looking into, it could have been problematic. It was just a lot of misinformation, and we didn’t want to take any potential risks, so we had to debunk it.
The lack of any evidence at all also felt kind of weird to us. When writing an article, you would think there would be some kind of quality control to prevent anything like this. Many researchers saw our response and assumed we hate researchers. We don’t have a problem with researchers; we just don’t like being lied about. I do understand why people haven’t just asked us, though. You would assume most “cybercriminals” wouldn’t want to talk to anyone conducting any kind of investigation on them.
CYFIRMA: What is your specialty or true passion in technical terms?
NecroSys: My passion is programming. I do malware development rather than any other cybercrime, such as traditional hacking, because I’m not really that interested in breaking into stuff. I like being able to write code to make any computer do whatever I want; it’s one of the few things I have control over.
CYFIRMA: Tell us about your origins. How did you become involved in malware development, specifically ransomware?
NecroSys: One day, I was stuck on a computer trying to do homework, but I couldn’t focus on it and procrastinated instead. I thought it would be cool to google “how to make a computer virus,” and it came up with stuff like batch scripts and app bombers. At the time, I thought it was the coolest thing ever. Then, I started changing things and adding new features to see what else I could do. I just started getting more creative with it. When that wasn’t enough, I moved on to more serious stuff. I got into ransomware mainly because it’s my favourite malware to write. It allows the most creativity and is the best way to practice general-purpose programming, as it involves everything you will ever need in programming. Before, I would just do art, but after improving a bit, I kinda got addicted and wanted to keep learning more.
CYFIRMA: Have you ever collaborated with other groups? We’re curious if you have formed any affiliations or alliances. If you can’t tell specific names, a generic answer is good too.
NecroSys: Yes, especially recently. I have connections to some very big, well-known groups, but they are too serious for me to be able to name. I am working on various secret projects with them too.
CYFIRMA: Could you provide insights into the development process of FusionCore’s malware? How do you determine the features and functionalities to include?
NecroSys: Usually, the development process is very long, and a lot of planning is needed. If we want to sell something, we look at what’s popular currently and what people have requested from us. Based on that, we decide on the product. Then, we decide on the language to use. We use C# for most of what we sell due to the flexibility needed when selling builders. For our personal projects, we usually use C/C++, but also C#; it all depends on what we’re doing. The features are determined based on existing features in other malware, but we also get creative and add anything we think would be good. We also ensure its well-written and good-quality code. Development is a lengthy process because we care about our work. We could just sell skidded variants of other malware, but then it would just feel empty. There’s no achievement, and we don’t learn anything or increase our reputation from that. The development process, in general, though, is extremely time-consuming and stressful.
CYFIRMA: Can you provide any insights into FusionCore’s future plans for expanding its malware arsenal?
NecroSys: We don’t really plan that much ahead, to be honest. We are hoping to write Typhon++ soon (TyphonStealer written in C++). It’s going to be closer to a botnet with a web panel and more features such as a loader and all the other features you would expect a botnet to have. Possibly some banking features too using overlays.
CYFIRMA: Are there any specific types of malware or attack techniques that you are actively researching or developing?
NecroSys: I have to research a lot of active directory.
CYFIRMA: What are the favourite type vulnerabilities or weaknesses in systems that FusionCore frequently exploits?
NecroSys: We mainly use post-exploitation techniques. We often use UAC bypass and LOLBIN techniques like explorer.exe for code execution if those count.
CYFIRMA: We have seen your malware use Obfuscar, NETShield, ConfuserEX. Are there any other specific open-source tools or frameworks that FusionCore relies on for increasing evasiveness in its malware toolkit?
NecroSys: We no longer use any open-source tools since they all get detected. We have since developed our own custom tools and have become better at evading AV in general, with or without obfuscation, by using techniques that aren’t as commonly used by others.
CYFIRMA: We have noticed that FusionCore has been using compromised bots. Is it a known or a private botnet?
NecroSys: Private botnet as in custom botnet or our own bots? We do have multiple; I think the one you’re referencing may have been LithiumRAT. I can’t remember, but we do have several private botnets made only for our personal use.
CYFIRMA: Now for a more touchy topic, the money. How do you monetize your operations, what is the biggest money maker for you? Do you study and employ any business practices to maximize effectiveness and profits?
NecroSys: We have many sources of income. Since FusionCore is public, I will address that. To maximize profits, we put a lot of time and effort into customer support, are active in many malware communities, and basically just socialize as normal. People check out our products and purchase because we provide very good customer support, which is why they come back to us. A lot of other groups don’t care about the customers at all. Our community is very loyal; even after being quiet for quite a while, the members still stuck around and are waiting for us to release our next products. I think some of it may be due to how we handle customers. If they have any problems at all, we will fix it. If the product is faulty, they get a new one for no extra cost because these people are paying for everything we have, and we show that appreciation by providing the best products and support we can.
Another reason why so many products have yet to be released is that we won’t sell anything we aren’t proud to have written. If it’s not something we would use, then it’s not sellable. It gets loyal customers and increases our reputation as a seller. If they are giving you money, they deserve what they paid for and help using it if they don’t know how to. There’s no reason not to provide good support. It’s just being nice, as everyone should be to their customers.
They provide food, clothing, RDPS, and whatever other necessities we need, so it’s the least we can do.
CYFIRMA: Are there any challenges you face, operational stuff like keeping infrastructure up, managing people in the group, getting things done on time, etc.?
NecroSys: Getting things done is definitely a challenge. The workload is seemingly infinite. For one project for a separate, more serious group, I often stay awake up to 4-5 days in a row just writing code, and it’s still not being done. When you want to make real money, mental health is just something you need to sacrifice to get there. No normal person gets to the top; you need to give everything you have to earn your place. And it will destroy you. But the money is worth it. That’s why most malware devs use stimulants to stay awake. We’ve got to keep working; 8 hours a day isn’t even close to enough time. But it will get easier once things are operational. This is the reality of life as a malware developer. It’s just how it is. It’s definitely not for everyone. You need passion and the motivation to make money by any means necessary, no matter what it costs you.
CYFIRMA: What’s on the horizon for you, any near-term and long-term ambitions?
NecroSys: Maybe a job in cybersec, but there aren’t many suited to me. I wouldn’t want to be a pentester because I’m not interested in finding and exploiting bugs. Malware research would be okay, but then there are the long reports, and I physically cannot do massive write-ups. There’s also no programming involved. What I want to do is red team tactics development, which is legal malware development for companies such as CobaltStrike since it’s my passion and what I do best. But there aren’t many jobs like that around.
CYFIRMA: As thanks for your time, this is space for you. Anything you want to say to the world?
NecroSys: Not really, but thank you for the opportunity to have my say, and have a great day!