


Research team at CYFIRMA has recently identified and published a report on a new European threat actor group called FusionCore. The group operates Malware-as-a-service and hacker- for-hire operations. They offer a variety of tools and services on their website to purchase cost- effective yet customizable malware.
In continuation of our investigation on FusionCore and its associated tools and malware, the CYFIRMA research team presents a detailed analysis report on “SarinLocker,” a new ransomware that we were able to access. It is worth noting that while investigating FusionCore, we discovered that the group has started a ransomware affiliate program that provides attackers with ransomware and affiliate software to manage victims.
We believe that the ransomware is still under development, and that there will be additional versions with more features. The SarinLocker ransomware encrypts files having particular extensions, searches drives and exfiltrates victim’s information to Telegram. It drops ransom note with additional instructions and demands ransom in crypto-currency.
KEY POINTS
SarinLocker Association:
SarinLocker is written by NecroSys, who is associated with FusionCore group. The threat actor group known as FusionCore is a relatively new and determined group, originating from Europe. The group is running Malware-as-a-service, along with hacker-for-hire services. They have a wide range of skills and rely on open-source tools to increase evasiveness in their malware toolkit. The current version of SarinLocker v1.0 may not be highly sophisticated, we anticipate that it is still undergoing development and expect that future versions will include enhanced capabilities.
Victimology:
They have recently started an affiliate program named AnthraXXXLocker and are likely to add more affiliates in the future. Their targets mainly depend on their buyers and affiliates. However, so far, their known targets include Lindesberg Municipality in Sweden and an infosec company in the Asia Pacific, where the Typhon Stealer was used in a phishing attempt. With new developers on board, FusionCore is set to enhance its malware arsenal, adding to the booming infostealer business and also dipping their toes into the extortion business.
Underground Chatter:
According to the information provided on their Telegram channel, NecroSys recently announced the release of SarinLocker v2.0 on December 22, 2022. One notable change in the updated version is a longer decryption key, which addresses a vulnerability in the previous version that allowed for brute-force attacks. Our team is actively seeking access to this new version and will release a report accordingly with updated findings.
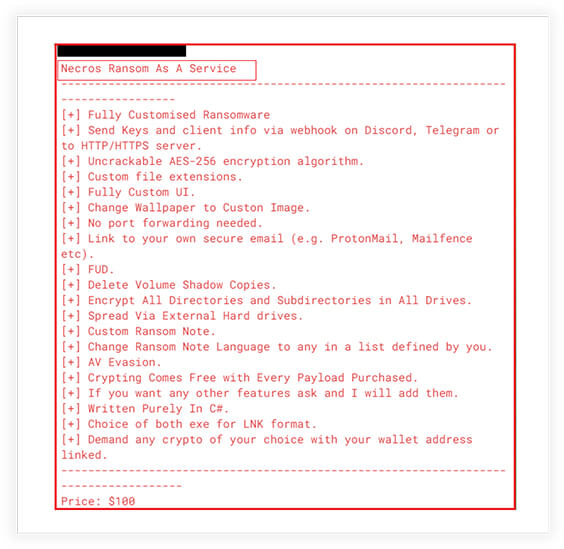
The author of SarinLocker, NecroSys, is actively promoting their ransomware-as-a-service on both Telegram and underground forums. To entice potential customers, they are making claims about the advanced functionality and customizable features of their service. Although we have analyzed SarinLocker v1.0, we have found that some of the functionalities advertised by the author are not present in this version. However, we suspect that these features may be available in newer versions of the ransomware. This ransomware-as-a-service stands out from its competitors with its affordable price point of only $100, which is significantly lower than other similar services available in the market.
Future Scope:
It is clear that ransomware-as-a-service (RaaS) is becoming more common among threat actor groups. FusionCore is a relatively new group in current threat landscape, offering a wide range of services, including malware-as-a-service. They have created a ransomware affiliate program, offering attackers ransomware and affiliate software to manage victims.
One of their key offerings is the SarinLocker ransomware, which we have analyzed in detail. Although the current version may not be advanced, it is expected that upcoming versions will possess more sophisticated features. The members of the FusionCore group are coming up with their own set of malware, with the help of more seasoned malware developers present in the group, and are creating a one-stop shop for threat actors.
Basic Details:
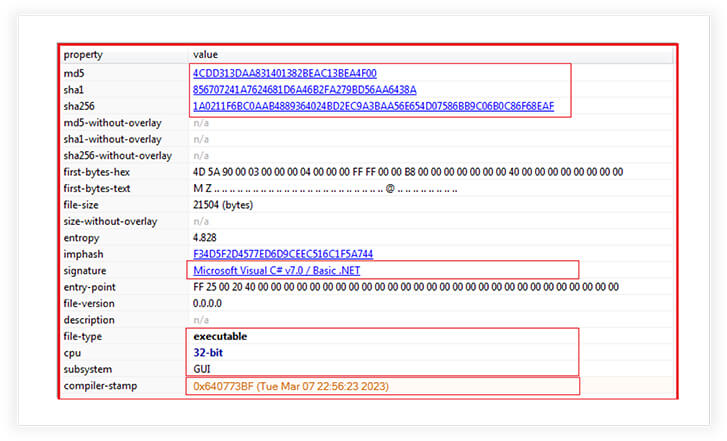
MD5: 4cdd313daa831401382beac13bea4f00
SHA256: 1a0211f6bc0aab4889364024bd2ec9a3baa56e654d07586bb9c06b0c86f68eaf
The binary we are able to access of SarinLocker is 32 bit PE file having a GUI subsystem. The binary is written in .NET and the compilation time is as recent as 7th March 2023.
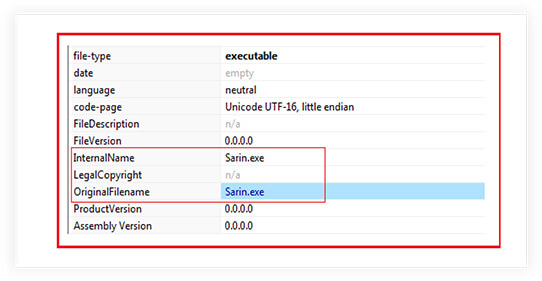
The internal and original file name mentioned in metadata is “Sarin.exe”.
The sample is not packed.
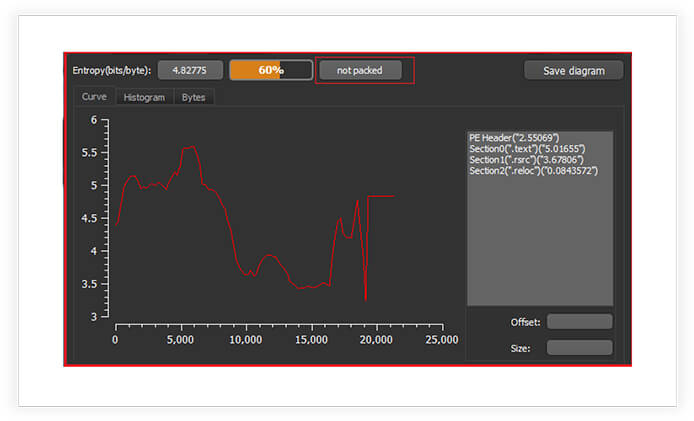
Code Analysis:
We had reverse engineered the sample to analyze the code. As shown below, the main function of the binary calling other functions like “SatrtEncryption”, “Telegram” etc. is for executing specific tasks. Initially the ransomware retrieves the startup path from where it is executing and sets its attributes to hidden, to effectively hide it from view in the file explorer.
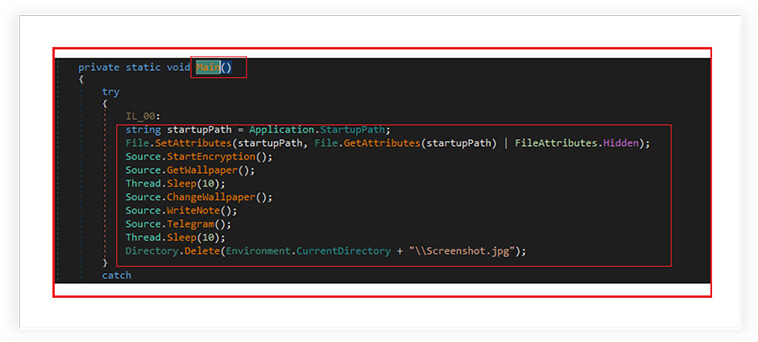
Encryption:
Later its calls the “StartEncryption” module to start the encryption, where the ransomware encrypts files in a victim’s user directory and potentially all the drives on the system. The ransomware first collects the information of user like username, constructs a path to the user’s directory, and subsequently calls the “EncryptDirectory” method to encrypt the files in the user’s directory, using the encryption password calculated at runtime. It also checks and iterates through all the drives on the system to encrypts the files.
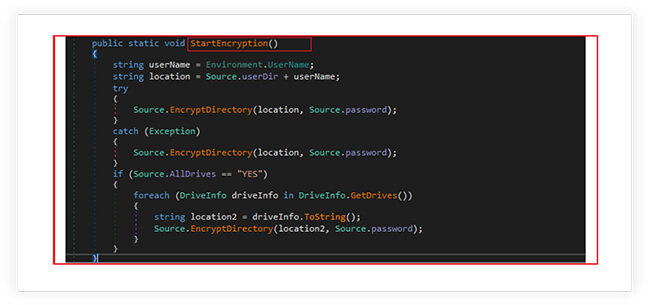
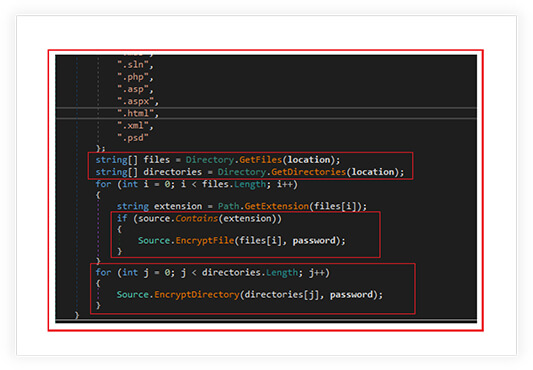
The function “EncryptDirectory” is designed to encrypt files in a given directory and its subdirectories. The function also checks the types of files to be encrypted, it gets all files and sub-directories in the directory, then the function iterates over each file and checks its extension. If the file extension matches, the function encrypts the file.
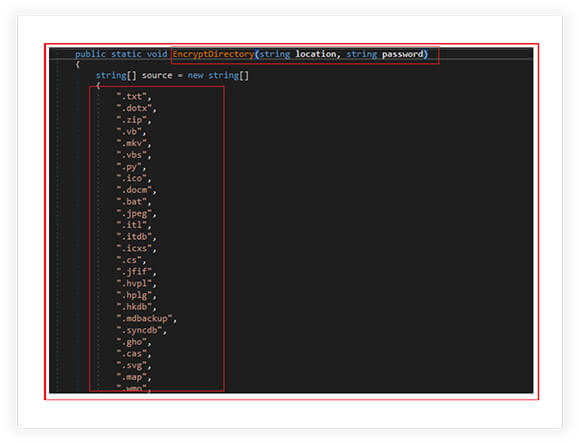
File Extensions Check:
Following file extensions checked by the ransomware for encryption:
“.txt”, “.dotx”, “.zip”, “.vb”, “.mkv”, “.vbs”, “.py”, “.ico”, “.docm”, “.bat”, “.jpeg”, “.itl”, “.itdb”, “.icxs”, “.cs”, “.jfif”, “.hvpl”, “.hplg”, “.hkdb”, ” .mdbackup”, “.syncdb”, “.gho”, “.cas”, “.svg”, “.map”, “.wmo”, “.itl”, “.itdb”, “.icxs”, “.hvpl”, “.hplg”, “.hkdb”, “.mdbackup”, “.sync db”, “.gho”, “.cas”, “.svg”, “.map”, “.wmo”, “.t13”, “.t12”, “.qdf”, “.gdb”, “.tax”, “.pkpass”, “.bc6”, “.bc7”, “.bkp”, “.qic”, “.bkf”, “.sidn”, “. sidd”, “.mddata”, “.png”, “.gif”, “.sql”, “.mp4”, “.7z”, “.rar”, “.m4a”, “.wma”, “.avi”, “.wmv”, “.itm”, “.sb”, “.fos”, “.mov”, “.vdf”, “.ztmp”, “.s is”, “.sid”, “.ncf”, “.menu”, “.layout”, “.dmp”, “.blob”, “.esm”, “.vcf”, “.vtf”, “.dazip”, “.fpk”, “.mlx”, “.kf”, “.iwd”, “.vpk”, “.tor”, “.psk”, “.rim”, “.w3x”, “.fsh”, “.ntl”, “.dba”, “.rofl”, “.hkx”, “.bar”, “.upk”, “.das”, “.iwi”, “.litemod”, “.asset”, “.forge”, “.ltx”, “.bsa”, “.apk”, “.re4”, “.ai”, “.eps”, “.pdf”, “.pdd”, “.psd”, “.dbf”, “.mdf”, “.wb2”, “.rtf”, “.wpd”, “.dxg”, “.xf”, “.dwg”, “.pst”, “.accdb”, “.odc”, “.odm”, “.odp”, “.ods”, “.odt”, “.csv”, “.d3dbsp”, “.zip”, “.sie”, “.sum”, “.ibank”, “.wav”, “.mov”, “.MOV”, “.html”, “.htm”, “.log”, “.js”, “.doc”, “.docx”, “.xls”, “.xlsx”, “.ppt”, “.pptx”, “.odt”, “.mp4”, “.mp3”, “.JPG”, “.PNG”, “.jpg”, “.ps1”, “.dng”, “.pptx”, “.pst”, “.csv”, “.sql”, “.mdb”, “.sln”, “.php”, “.asp”, “.as px”, “.html”, “.xml”, “.psd”
Finally, the function iterates over each subdirectory and calls itself recursively with the subdirectory as the new location parameter. This ensures that all files in the subdirectories are also encrypted.
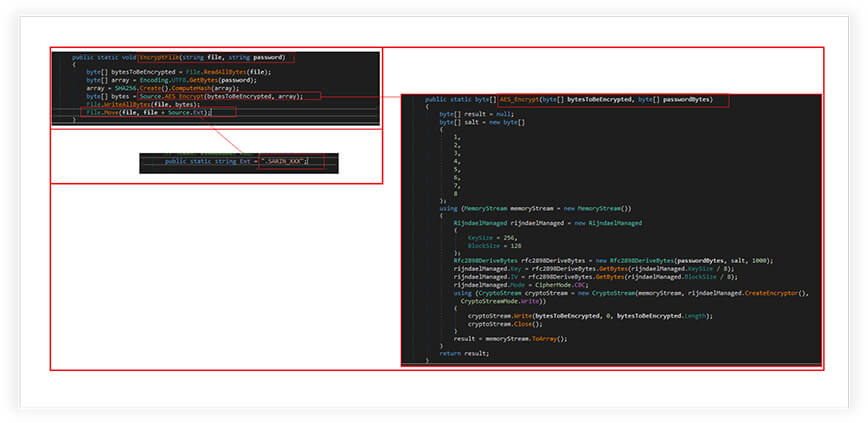
Encryption Algorithm:
Ransomware reads all the bytes from the file, It also converts the password string to a byte array and creates a SHA256 hash of it. This hash is then used as the encryption key. The ransomware used the Advanced Encryption Standard (AES) Encryption to encrypt the files. The encrypted data is then written back to the same file, overwriting the original file with the encrypted data.
The encryption algorithm sets the key size to 256 bits and the block size to 128 bits. The CipherMode is set to CBC (Cipher Block Chaining), which is a block cipher mode of operation that provides confidentiality by XORing each plaintext block with the previous ciphertext block before encryption.
Finally, the ransomware renames the encrypted file with an additional extension “SARIN.XXX”. This extension is stored in a static string variable called Ext.
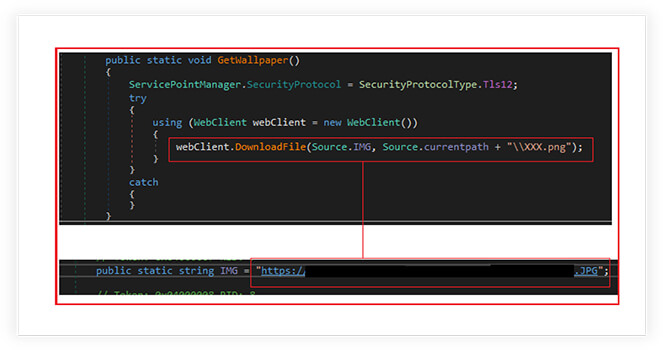
Desktop Wallpaper:
The ransomware downloads an image file from a specified hardcoded URL and saves it as XXX.png in the current working directory. This functionality is used to update or change the desktop wallpaper.
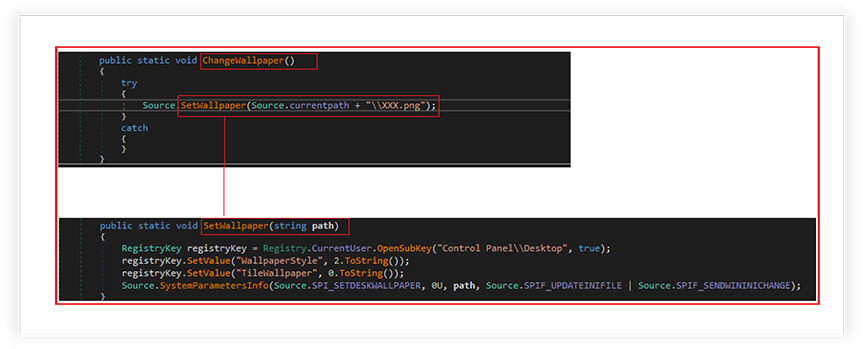
The SetWallpaper function is responsible for setting the wallpaper on a Windows desktop. The function opens the registry key, “HKEY_CURRENT_USER\Control Panel\Desktop” in write mode. It sets the values of two registry entries: WallpaperStyle and TileWallpaper. WallpaperStyle determines how the wallpaper is displayed (stretched, tiled, centered, etc.) and TileWallpaper determines whether the wallpaper is tiled or not. In this case, WallpaperStyle is set to “2”, which means the wallpaper will be stretched to fill the screen, and TileWallpaper is set to “0”, which means the wallpaper will not be tiled.
Following screenshot shows the wallpaper, which is downloaded by the ransomware (from hardcoded URL) as explained above and applied on victim’s desktop. The wallpaper mentions the message that “Your files have been encrypted” and follow the instructions in dropped file “_README_.html”.
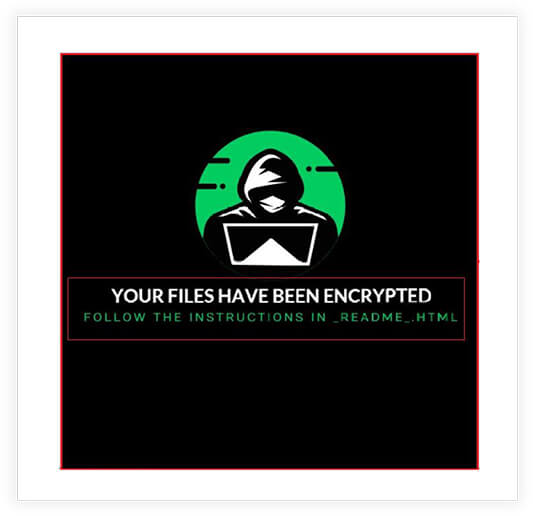
Ransom Note:
The following function “WriteNote” is creating a ransom note file that is dropped on the victim’s desktop. The note contains information about how to pay the ransom and recover the encrypted files. The ransomware creates two files on the desktop, a text file called “HOW_TO_GET_YOUR_FILES_BACK.txt” and an HTML file called “README.html”.
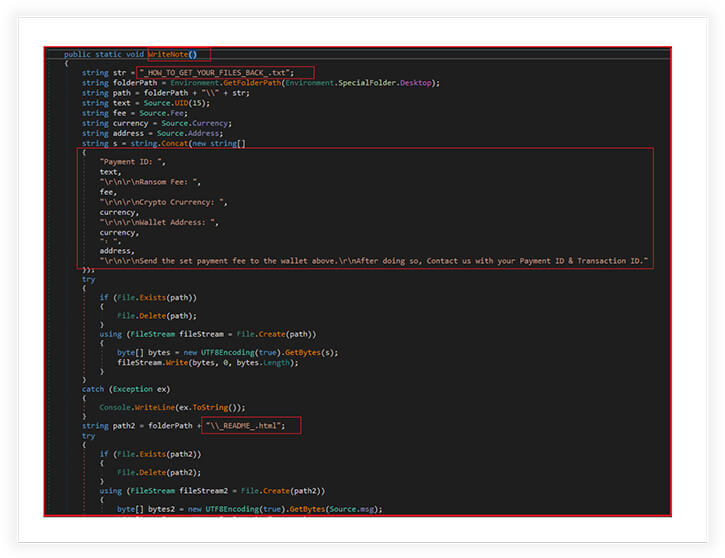
The text file contains the payment ID, a ransom fee, crypto currency, and wallet address. The victim is instructed to send the ransom fee to the wallet address and then contact the attackers with their payment ID and transaction ID. The HTML file contains a message from the attackers, explaining what has happened and what the victim needs to do to recover their files. If the files already exist on the desktop, the function deletes them and creates new ones with the updated information. Finally, the function opens the note file so that the victim sees it immediately.
There is a difference in the contents of both the above mentioned ransom notes files. The file “HOW_TO_GET_YOUR_FILES_BACK.txt” mentioned the following details:
payment ID (generate a random/unique payment ID), a ransom fee ($50), crypto currency (Ethereum (ETH), and wallet address (“0x4509C125Ed6753177579bd6cE9463907B662dDd7”) and instruction “Send the set payment fee to the wallet above, After doing so, Contact us with your Payment ID & Transaction ID.
While the file “README.html” mentioned following text:
You Have Been Infected With SarinLocker Ransomware:
All of your data has been encrypted using a military grade encryption algorithm.
How do I get my files back?:
You must pay a fee of $200 equivalent in the form of Monero cryptocurrency (XMR). After this payment has been received you will be sent the decryption software needed to unlock your files along with a decryption key. Once you have entered that decryption key into the software your files will be unlocked and the ransomware files will be deleted from your device. All your files are encrypted with RSA-2048 and AES-128 ciphers. More information about RSA and AES can be found here:
http[:]//en[.]wikipedia[.]org/wiki/RSA_(cryptosystem)
http[:]//en[.]Wikipedia[.]org/wiki/Advanced_Encryption_Standard
Decryption of your files is only possible with the private key and our decrypt software, which is stored in our secret server. To receive your private key please contact us at:
Email: [email protected]
Follow these instructions to get your files back:
So there is a difference in the content. The ransom demanded and the currency is also different in both files. The .txt file mentioned the ransom value of $50 in Etherium, whereas, the .html file mentioned the value of $200 in Monero.
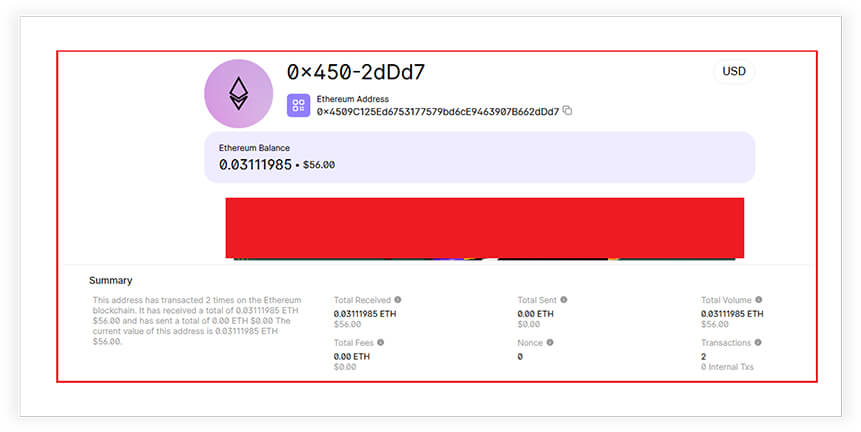
Crypto Wallet Address:
We further investigated the authenticity of cryptowallet address (“0x4509C125Ed6753177579bd6cE9463907B662dDd7”) and it is valid as shown below. It’s an Etherium wallet address having current value; $56 (0.0311985 ETH) and a total of two times of transactions.
Communication and Notification Mechanisms:
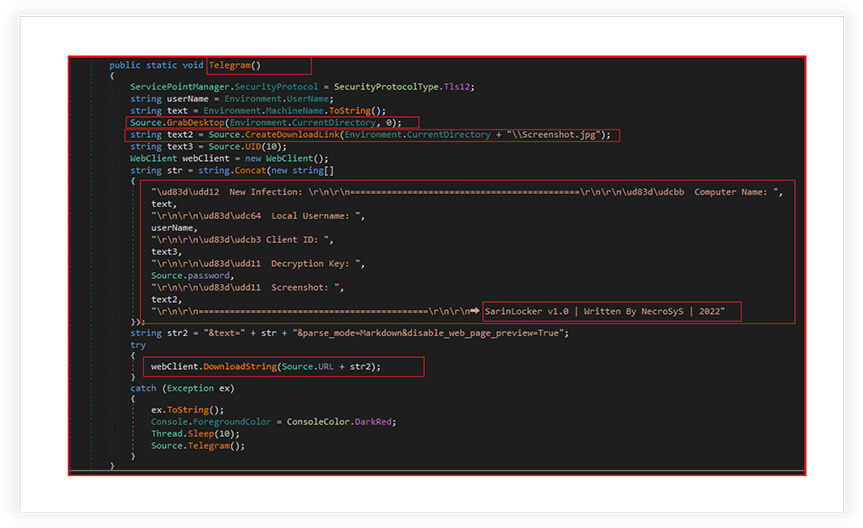
Function “Telegram” as shown below is responsible for sending a message to a Telegram chat. It is used to notify the attacker through a Telegram chat about a successful infection and provide some information about the victim’s computer.
It first sets the security protocol to Tls12, which is a secure communication protocol. It then retrieves the current username and machine name, takes a screenshot of the desktop and saves it to a specified location on the local machine, and subsequently creates a download link for the screenshot. For creating the download link, it uploads a file to the anonfiles server and If the upload is successful, the function returns the download link for the file, which is extracted from the response string, received from the server.
It further generates a random client ID/UID for victim and creates a message string, containing the computer name, username, client ID, decryption key, screenshot download link, and some additional text. The ransomware then sends a request to the specified URL (“https[:]//api[.]telegram[.]org/bot5589520987[:]AAEf0S128_2nbg3Rp6- EjdpqFmJfTkHjjHs/sendMessage?chat_id=1924412993”) with the message string as a parameter. If the request fails, it catches the exception and recursively calls itself with a 10 millisecond delay to retry sending the message. The message also includes Unicode emojis to indicate various aspects of the infection. Later, the ransomware also deletes the screenshot of the desktop from victim’s machine.
As shown in below screenshot, the ransomware author is NecroSys and the version number for SarinLocker is mentioned as V1.0. NecroSys is one of the primary associates of FusionCore group. NecroSys also advertised the SarinLocker ransomware as soon to be released ransomware.
Anonfiles is a file-hosting service that allows users to upload and share files anonymously. The server returns a download link for the uploaded file, which can be used to access the file from anywhere on the internet. In this case, the malware is using the anonfiles server to host the desktop’s screenshot image file and generate a download link that will be included in the Telegram message sent by the Telegram function.
CYFIRMA Research team believes that the emergence of the FusionCore group, their Malware-as-a-Service and hacker-for-hire operations, and the development of their own suite of tools and malware, including the newly analyzed SarinLocker ransomware, highlights the evolving sophistication of the threat group. The group’s ambition to create a suite of malware tools, covering most of the kill-chain highlights the potential for a one-stop-shop for threat actors. As the cybersecurity landscape evolves, it is imperative for security teams to have complete visibility of their attack surface to prevent attacks like SarinLocker. As SarinLocker continues to develop, it remains a potent threat, with future versions expected to have even more advanced capabilities. With the increasing threat posed by MaaS and the potential damage of a single breach, it is crucial for organizations to have complete visibility and a proactive approach to cyber threat landscape.
LIST OF IOCS
| Sr no. | Indicator | Type | Remarks |
| 1 | 4cdd313daa831401382beac13bea4f00 | MD5 File Hash | SarinLocker Ransomware |
| 2 | 856707241a7624681d6a46b2fa279bd56aa6438a | SHA1 File Hash | SarinLocker Ransomware |
| 3 | 1a0211f6bc0aab4889364024bd2ec9a3baa56e654d07586bb9c06b0c86f68eaf | SHA256 Hash | SarinLocker Ransomware |
| 4 | 65595f4249baa1f453934096551a1146 | MD5 File Hash | SarinDesktop.JPG (Downloaded Desktop Wallpaper) |
| 5 | 5542bcffd50834389eda22700693c2cf909028dc | SHA1 File Hash | SarinDesktop.JPG (Downloaded Desktop Wallpaper) |
| 6 | 2f27d0a79065bd5a60ace7eccaba4e67fbb60578f77288e8adb6a464e1490739 | SHA256 Hash | SarinDesktop.JPG (Downloaded Desktop Wallpaper) |
| 7 | https[:]//api.telegram[.]org/bot5589520987[:]AAEf0S128_2nbg3Rp6-EjdpqFmJfTkHjjHs/sendMessage?chat_id=1924412993 | URL | Telegram |
| 8 | crypsis@mailfence[.]com | Email-id | Contact for Ransom Payment |
| 9 | 0x4509C125Ed6753177579bd6cE9463907B662dDd7 | Address | Crypto Wallet Address |
MITRE ATT&CK TACTICS AND TECHNIQUES
| No. | Tactic | Technique |
| 1 | Execution (TA0002) | T1204.002: Malicious File |
| 2 | Defense Evasion (TA0005) | T1112: Modify Registry |
| 3 | Discovery (TA0007) | T1012: Query Registry T1082: System Information Discovery |
| 4 | Collection (TA0009) | T1113: Screen Capture |
| 5 | Command & Control (TA0011) | T1071: Application Layer Protocol |
| 6 | Exfiltration (TA0010) | T1048: Exfiltration over alternative protocol |
| 7 | Impact (TA0040) | T1486: Data Encrypted for Impact |