



Conti gang is one of the largest cybercrime syndicates in the world. Third-party blockchain analysis of their bitcoin wallets estimates up to USD 200 million of annual revenue. Recently leaked chat logs of the group provide unprecedented insight into the life and operations of the gang. From asking leave approval to internal cybersecurity or TTPs used in attacks, these leaks are sure to be studied by analysts for weeks and months to come. Our research team at CYFIRMA has focused mainly on extracting IOCs and TTPs but has also observed interesting insights about the gang’s inner workings.
After the arrest of REvil members, the Conti gang is now dominating the scene of so-called “big game hunting” groups (focused only on large companies with above USD 100m in annual revenue). Insights into their leaked conversations confirm what threat researchers, including at CYFIRMA – as part of our 2022 Predictions [https://www.cyfirma.com/cyfirma-cybersecurity-predictions-2022/] – have suspected and speculated. Top cybercriminal gangs are organized and operate as a business within their little industry of cybercrime. This includes outsourcing, for example, initial access brokers, typical HR problems, physical offices, and of course, performance reviews.
With the RaaS business booming, the need for reliable talent from low-level programmers to highly skilled pentesters has grown as well. In leaked chat logs, there are conversations of dedicated HR personnel and promotions of referral programs with bonuses. Particularly fascinating and shady is the practice of abusing legitimate headhunting services to hire employees who have no idea who they really are working for. The pressing matter appears to be talent retention as the pay is not too great, working hours are grueling and work is a repetitive cycle of monotonous tasks at Conti “company”.
Also discussed are operational issues of inconsistency and struggle to maintain its infrastructure. Domains, VPNs, and other services are not being properly tracked and renewed on time, causing issues for networks of compromised hosts calling said domains and so on. High turnover of employees also seems to cause human errors in the malware itself, where simple misconfigurations result in unsuccessful breaches and loss of profit.
Before we jump into hacking and tools used, it is noteworthy to mention the use of business intelligence by Conti to learn about their victims. They are particularly interested in reported revenue and information about available cash or if an organization has ransomware/cybersecurity insurance. They also look for contacts of executives or board members in order to harass them and force out the ransom. Two paid tools that were specifically mentioned were ZoomInfo and Crunchbase.
Another interesting observation is shopping for all sorts of cybersecurity products. Naturally, they want to protect themselves against being hacked by the competition or law enforcement, so they buy Antivirus products and EDR solutions for their defense. At the same time, they are buying licenses of all major cybersecurity products to test their own malware and TTPs to keep it functional and stay at least one step ahead in this never-ending cat and mouse race.
The final point is their suspected collaboration with Russian government agencies. While there is still no concrete evidence even with these leaks, there are mentions of the FSB agency and Conti allegedly attacking an organization to gather information for FSB.
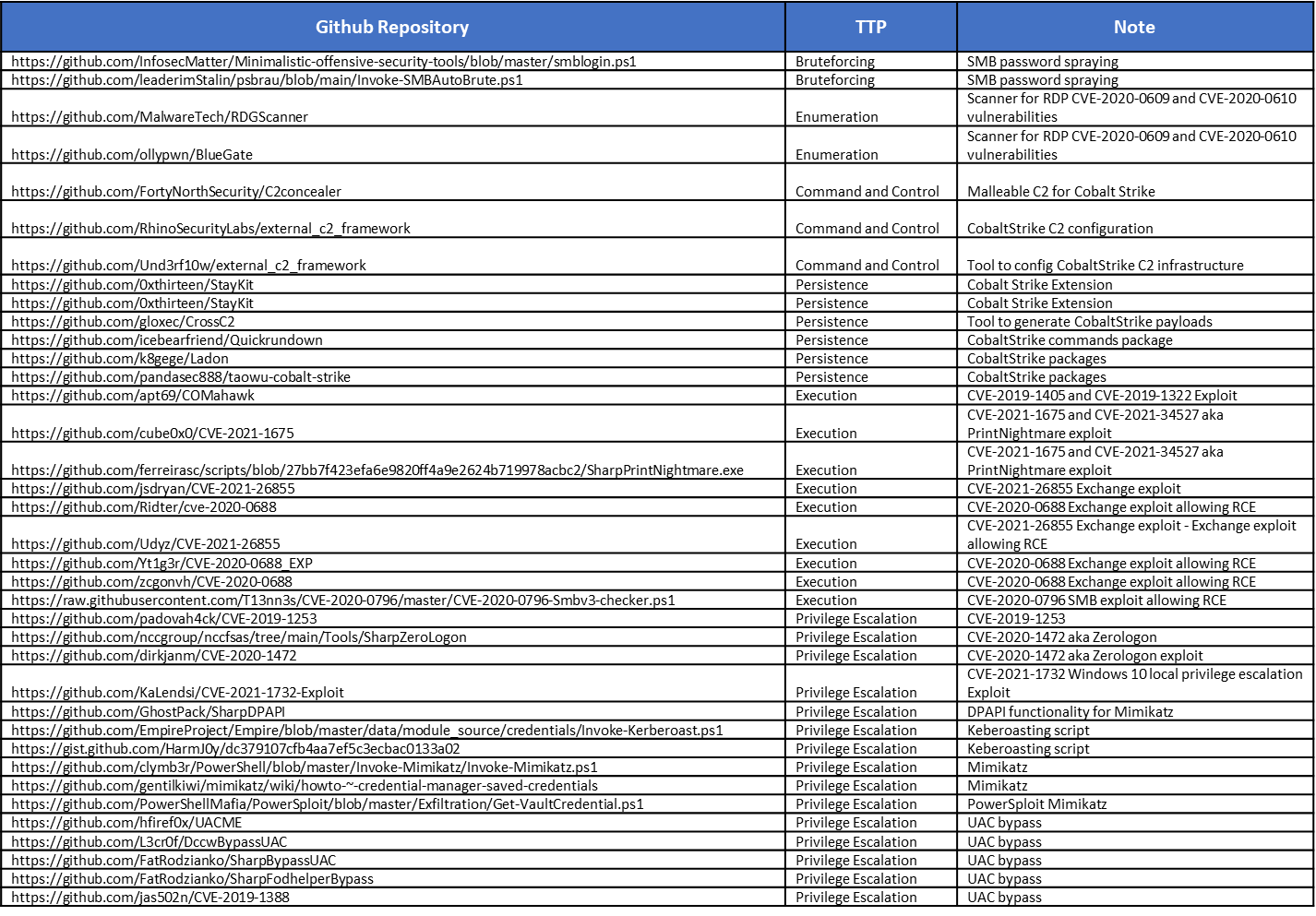
From extracted IOC and TTPs by CYFIRMA, there is a clear absence of any initial access materials implying heavy reliance on initial access brokers and affiliates to take care of this side of the business. From the snippet below it appears that Conti’s focus is on the speed of lateral movement and access to emails.
![]()
The snippet of GitHub repositories mentioned in leaked Conti chat logs
Download the links Conti Ransomware_Mar 2022_GitHub.
While there are a lot more TTPs and CVEs that the CYFIRMA research team extracted from the leaks on GitHub and beyond, this snippet illustrates some of Conti’s favorites. It is clear that they are not trying to re-invent the wheel, rather relying heavily on existing and readily available tools. Their coders focus on locker code and botnet networks.
Combining the previously leaked playbook of Conti, with these recent chat leaks, we can quite clearly see preferred protocols and systems to exploit and tools used for it. Once initial access is obtained, usually, from 3rd party brokers, Conti is well equipped to establish persistence and move laterally for maximum damage in the shortest amount of time possible.
Here are observations of the CYFIRMA research team.
It has been very insightful to see the Conti gang’s preferred methods and tools and how they operate. Like anyone else, they like to stick to what works and incrementally make changes to ensure it keeps working without drastically changing any part of their playbook. From a threat research and defense perspective, this provides valuable information on what to focus on. Notable is the universal adoption of OS native tools and PowerShell, which is very likely going to evolve further into living off the land.
From the organizational perspective, their somewhat impressive and unexpected “ordinary business” structure still has major problems and clearly struggles with issues of efficiency and consistency. However, we can expect that these will get ironed out and consequently, the gang will continue to get better and more dangerous to organizations around the world.
Finally, many are speculating if this is the end of Conti. And it likely is not. They have had leaks before and from the size of their operation, it seems they are almost too big to fail. There is also a suspected connection to the Russian government which makes the discontinuation of Conti even less likely. If it comes to the worst, they are most likely to go with the time-proven strategy of taking a break and coming back stronger than ever with a re-brand.