


This research report examines a security vulnerability discovered in the Blubrry Powerpress plugin, specifically affecting versions 10.2.3 and earlier. The vulnerability identified is a zero-day authenticated stored cross-site scripting (XSS) exploit, found within the “Show Title” field, which allows an attacker with authenticated access to inject malicious code into the podcast’s title, potentially compromising the security and integrity of the affected website. Note: CYFIRMA researchers have identified this vulnerability as a zero-day exploit, and it was reported as such to the vendor.
Blubrry Powerpress, a popular plugin used by podcasters to enhance their websites, has recently come under scrutiny due to a security vulnerability. This research report focuses on a zero-day exploit found in versions 10.2.3 and earlier Powerpress plugins, specifically within the “Show Title” field. The vulnerability in question involves an authenticated stored cross-site scripting (XSS) attack, posing a significant threat to websites utilizing this plugin. XSS attacks are particularly concerning, as they allow attackers to inject and execute malicious code within web pages, potentially compromising user data and the overall security of the affected website. This report aims to provide a comprehensive analysis of the vulnerability, its implications, and recommendations for mitigating the risk posed by this zero-day XSS exploit. By understanding the nature of this security flaw and implementing the suggested measures, website administrators and developers can take proactive steps to protect their systems and maintain a secure podcasting platform.
Key Takeaways:
Acknowledgements:
Vulnerability type: Stored Cross-Site Scripting
CVE ID: Not Assigned
CVSS Severity Score: 2.4 [Temporal]
CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:U/C:L/I:N/A:N/E:P/RL:U Application: PowerPress
Impact: Potentially compromise user data or the security of the application Severity: LOW [Temporal]
Affected Versions: <= 10.2.3
Patched Available: NO
Latest Version: 10.2.3
The vulnerability in PowerPress plugin version <= 10.2.3 for WordPress allows authenticated attackers via a “Show Title” field in “powerpressadmin_basic” page, leading to stored cross-site scripting (XSS) attacks. The issue arises due to improper validation of user-supplied data. A successful exploit could enable attackers to execute arbitrary code, steal sensitive information or perform unauthorized actions. Currently, there is no patch available.
The impact of the Stored Cross-Site Scripting (XSS) vulnerability in WordPress PowerPress 10.2.3 and earlier plugins, can be severe as it can allow attackers to inject malicious code into a website and potentially compromise user data or the security of the application. This can lead to data theft, unauthorized access, and other malicious activities.
The vulnerability affects version 10.2.3 and earlier versions of the PowerPress WordPress plugin.
The CYFIRMA research team analysed a method to exploit the zero day in Power press 10.2.3. We have setup our own lab for analysing the vulnerability.
Installation
We have installed Blubrry PowerPress latest version 10.2.3, which was our scope for this research.
The Vulnerability
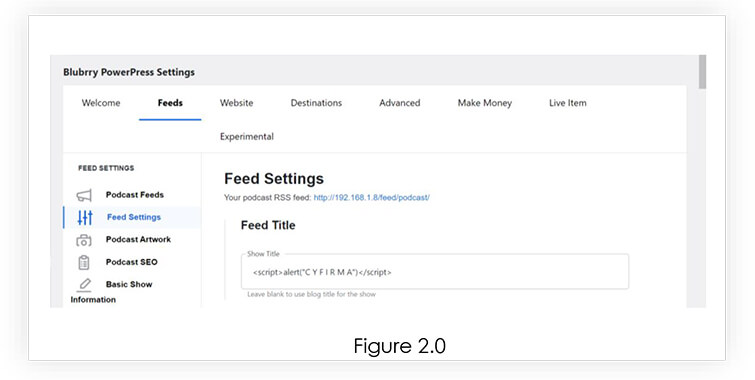
To exploit the identified vulnerability, our research involved accessing the “powerpressadmin_basic” page within the Powerpress plugin. Specifically, we focused on the Feed Settings section, which provided us with the opportunity to inject the Stored XSS payload. By leveraging this access point, we were able to demonstrate the extent of the vulnerability and highlight the potential risks associated with unauthorized code injection. Refer Figure 2.0
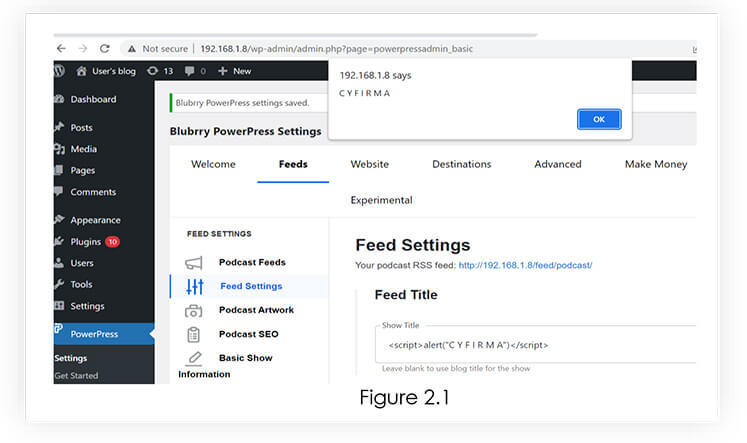
Next, upon injecting an XSS payload into the “Show Title” field within the Feed Settings section of the “powerpressadmin_basic” page, we observed a noteworthy outcome. The payload successfully triggered a pop-up message, indicating that the injected code had been executed. Refer 2.1
CYFIRMA researchers have identified this vulnerability as a zero-day exploit, and it was reported as such to the product vendor. It is crucial to take immediate mitigation steps to protect the affected websites. Below are some recommended actions:
It is crucial to emphasize the importance of reaching out to the Blubrry team again, persistently requesting their attention to this critical security vulnerability. Engaging with them directly can facilitate a timelier resolution and provide an opportunity for collaboration to protect users and websites, relying on the Powerpress plugin.
Target Geography:
Based on the information available, the PowerPress 10.2.3 Stored Cross-Site Scripting (XSS) vulnerability in WordPress can potentially impact websites worldwide that use the PowerPress plugin.
However, it is more likely to be exploited by attackers targeting websites hosted in regions with a higher concentration of WordPress users, such as North America, Europe, and Asia-Pacific. Websites in these regions may be at a higher risk of exploitation, due to the larger pool of potential victims and a higher likelihood of finding vulnerable websites. Additionally, the severity of the vulnerability and the popularity of the PowerPress plugin may increase the likelihood of exploitation.
Target Industry:
The PowerPress 10.2.3 Stored Cross-Site Scripting (XSS) vulnerability in WordPress can potentially impact websites across various industries, using the PowerPress plugin. However, the vulnerability may be more attractive to attackers targeting specific industries that regularly publish multimedia content, such as podcasters, bloggers, news media outlets, and other content creators.
These industries often use the PowerPress plugin to enhance the user experience of their multimedia content, by embedding audio and video players into their websites. As a result, a successful exploitation of the PowerPress vulnerability can allow authenticated attackers to inject malicious code and potentially compromise the security of the website and its visitors.
Target Technology:
The PowerPress 10.2.3 Cross-Site Scripting (XSS) vulnerability in WordPress is related to a specific plugin, the PowerPress plugin. However, the vulnerability may not be limited to just this plugin, as WordPress itself is a popular and widely used content management system (CMS) that can be vulnerable to various types of attacks.
Due to its popularity and the large number of plugins available, WordPress websites can be targeted by attackers looking to exploit vulnerabilities in the platform or its plugins.
From underground forums, CYFIRMA Research team has observed that unknown hackers are selling WordPress accounts with wp-admin and wp-login access, which could help the malicious actors to gain the access and install vulnerable version of PowerPress.
Organizations and individuals using WordPress are advised to remain vigilant and take proactive measures to protect their websites from potential attacks. This includes regularly updating WordPress and all associated plugins, using strong and unique passwords, and implementing additional security measures, such as two-factor authentication and web application firewalls. It is also recommended to monitor underground forums and security news outlets to stay informed about emerging threats and vulnerabilities.
At CYFIRMA, we are dedicated to responsible disclosure and advocating for a safety-focused outcome in all our cybersecurity endeavours. Despite our repeated attempts, we have received no response from vendors, when reaching out to address vulnerabilities, we have identified. Prompt and transparent communication is crucial in mitigating risks and ensuring the safety and security of customers and end-users.
| Date | Action | Response |
| 5th May 2023 | First Contact with Blubrry Team | No Response |
| 8th May 2023 | Follow-up mail to Blubrry Team | Response Received |
| 9th May 2023 | POC shared with Blubrry Team | – |
| 10th May 2023 | Follow-up mail to Blubrry Team | No Response |
| 16th May 2023 | Follow-up mail to Blubrry Team | No Response |
| 24th May 2023 | CYFIRMA discovers vulnerability in latest version 10.2.3, POC shared | No Response |
| 5th June 2023 | Follow-up mail to Blubrry Team | No Response |
| 6th June 2023 | Follow-up mail to Blubrry Team | Response Recieved |
| 6th June 2023 | Latest POC for version 10.2.3 sent | No Response |
The discovery of a zero-day authenticated stored XSS vulnerability in Blubrry Powerpress versions 10.2.3 and earlier versions, specifically in the “Show Title” field, poses a significant security risk to affected websites. Despite reporting the issue to the Blubrry team, the urgency and lack of a response necessitates immediate mitigation measures. Temporary workarounds, such as restricting access to the vulnerable field, reduce the attack surface, monitoring incoming requests through security plugins or web application firewalls aids in detecting and blocking suspicious activities. Staying informed and engaging with the community allows for collaborative solutions. Preparing for prompt patch implementation upon the developer’s response is essential. Administrators should consider alternative plugins with stronger security records if responsiveness remains inadequate. This incident underscores the importance of robust security measures and proactive developer engagement to ensure the protection of website assets and user data.