



The team at CYFIRMA analyzed a malicious Android sample designed to target high-value assets in Southern Asia. This sample, attributed to an unknown threat actor, was generated using the Spynote Remote Administration Tool. While the specifics of the targeted asset remain confidential, it is likely that such a target would attract the interest of APT groups. However, we are restricted from disclosing further details about the actual target and its specific region. For a comprehensive analysis, please refer to the detailed report.
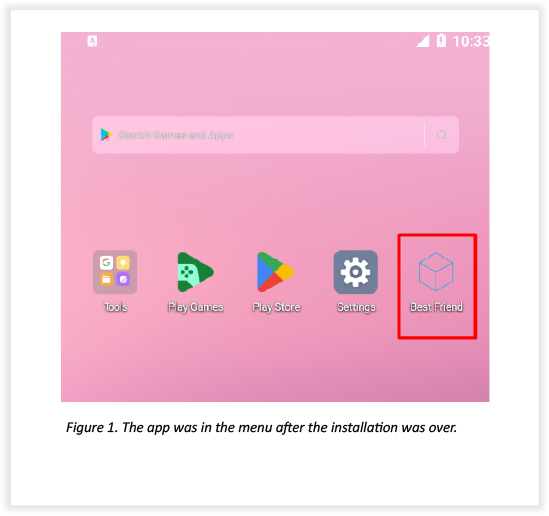
The team received a malicious Android sample for investigation. The sample was part of a targeted attack on highly valued individuals in southern Asia. The team observed that the unknown actor tried to deliver the Android payload via WhatsApp which seems like a terrible move from the threat actor’s viewpoint. The victim received a total of four payloads with different names, three of which were the same size, hinting at an effort by the threat actor to compromise the victim. The apps were named “Best Friend, Best-Friend 1, Friend, best”. All four apps had the same command and control server. During analysis, it was found that the code for the Android payloads was obfuscated. The app was installed and was concealed within seconds while operating in the background.
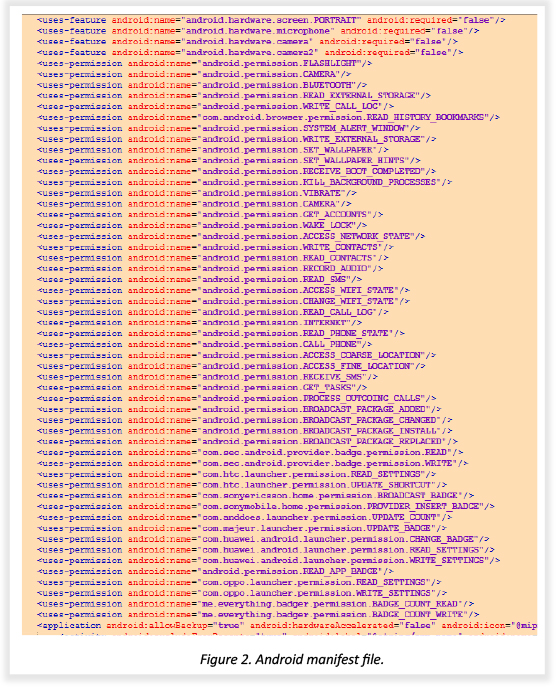
The snippet shows the Android Manifest file of one of the payloads we decompiled.
The table below covers important permissions with descriptions that apps take use for malicious activity.
| Sr.no | Permissions | Descriptions |
| 1. | ACESS_FINE_LOCATION | Allows the threat actor to fetch precise locations and track the live movement of mobile phones. |
| 2. | READ_CONTACTS | This permission allows the threat actor to read and fetch contacts. |
| 3. | CAMERA | This permission helps the app to interact with the Camera |
| 4. | READ_SMS | This permission helps the App to read and access the SMS. |
| 5. | WRITE_EXTERNAL_STORAGE | This permission allows the app to interact with device storage |
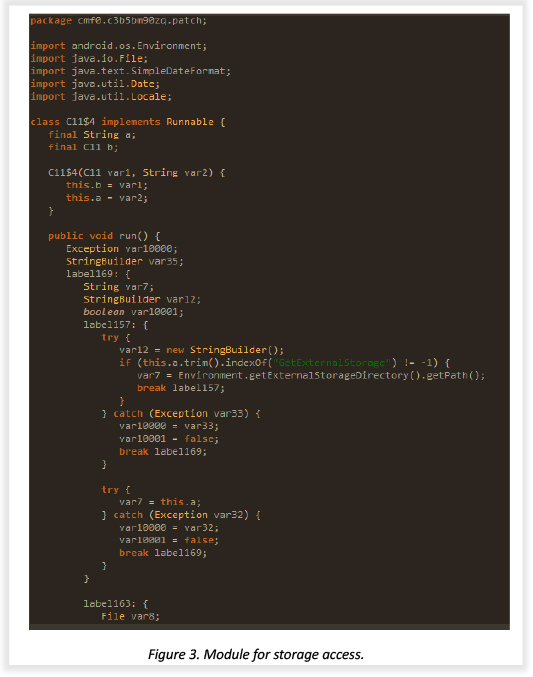
The snippet below shows the code that interacts with Android’s file system and helps the attacker explore the file storage and initiate data extraction.
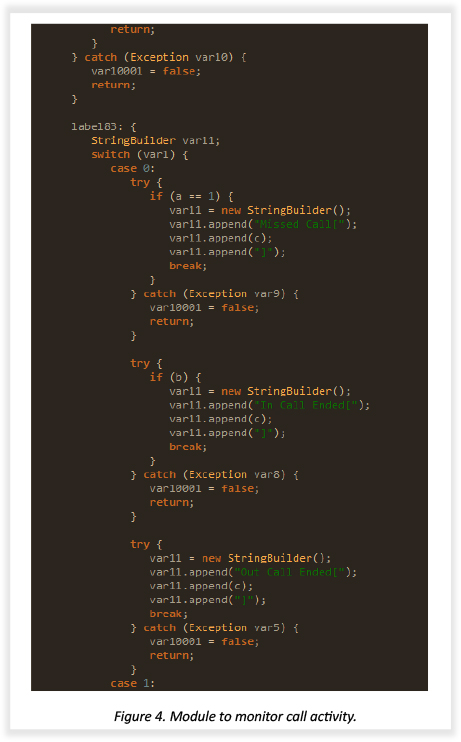
This snippet from the module allows an attacker to monitor the incoming and outgoing calls.
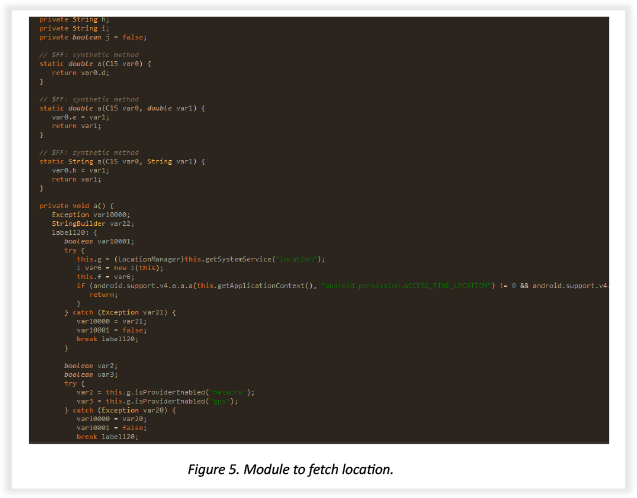
The snippet below shows code from a module tasked to fetch the victim’s precise location.
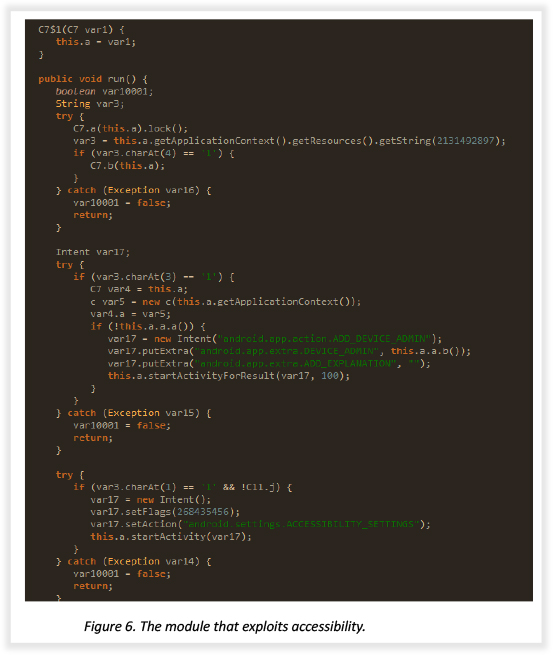
The code below shows that the app tries to open the Accessibility Settings page. Once enabled, the threat actor will be able to monitor user activity on the mobile screen, potentially leading to more disastrous outcomes for the victim. Enabling accessibility for the maliciously installed app allows the attacker to perform dangerous maneuvers, such as screen capture and keystroke capturing, restricting the victim from uninstalling the app.
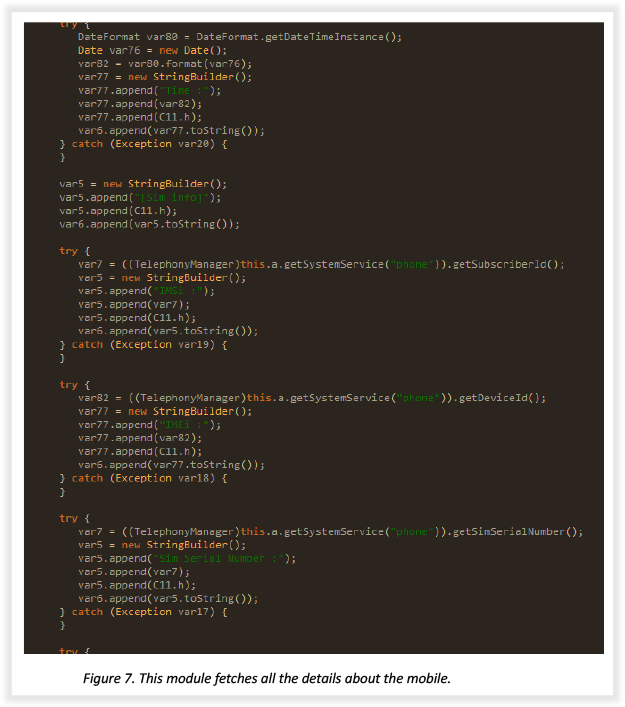
The snippet below shows the code part of a module that fetches detailed information about the compromised device, such as the IMEI number, SIM, Android version, Network type, IMSI, etc.
The SpyNote Remote Administration Tool (RAT) has evolved over time, with various updated versions designed to compromise Android devices. Threat actors ranging from individual hackers to organized APT (Advanced Persistent Threat) groups have leveraged various versions of SpyNote for espionage, financial fraud, and even personal vendettas. Over the years, SpyNote has emerged with modified versions, such as SpyMax, Crax RAT, and Eagle Spy, each equipped with enhanced and increasingly dangerous capabilities.
APT groups, including OilRig (APT34), APT-C-37 (also known as Pat-Bear), and OilAlpha, have utilized SpyNote in their malicious campaigns. These operations have often targeted critical sectors, such as government agencies, NGOs, media organizations, financial institutions, and even individual activists. These tools enable attackers to compromise Android devices to spy on communications, steal sensitive data, and maintain persistence in their victims’ systems. The tool has the potential to be exploited by other APT groups, as evidenced in this incident, where we suspect the attack may have been orchestrated by an unidentified APT group or an unknown threat actor.
Indicators of Compromise
| Indicator | Type | Remarks |
| 182.191.122.219 | IP Address | Command and Control |
| 8AA1A66E03596C0EBA6F91FB081DDB4081F43B02D421E069C6BE8BBF5D399B89 | SHA256 | Android package |
| 0552137AAA2C9419C8843D50BCB15A4C80913ED47EB71C5E5AB9B5AC257944ED | SHA256 | Android package |
| 6127DAF756865EE089BA83EFDADEBDA2C047026A698759DE09127D0DFE630E8D | SHA256 | Android package |
| A70089301FF628F09B90B269F6E8F5C6B5AE0B3073028ABCC62FEC9D2F1C954C | SHA256 | Android package |
MITRE ATT&CK Technique
MITRE ATT&CK framework for Android malware payload in a table format
| Tactics | Technique ID | Description |
| Persistence | T1541 – Foreground Persistence | The app utilizes the startForeground() API method to continue running in the foreground. |
| Defense Evasion | T1406 – Obfuscated Files or Information | Uses obfuscation techniques to hide malicious code within the APK. |
| Credential Access | T1417 – Input Capture | Captures keystrokes to steal sensitive credentials like usernames and passwords. |
| Discovery | T1420 – File and Directory Discovery | Enumerate files and directories on the device to locate valuable information. |
| Discovery | T1426 – System Information Discovery | Collects device information, such as device model, and user details. |
| Collection | T1533 – Data from Local System | Extracts data such as contacts, messages, photos, and videos from the infected device. |
| Collection | T1513 – Screen Capture | Takes screenshots of the infected device to capture sensitive information. |
| Exfiltration | T1646 – Exfiltration Over C2 Channel | Sends stolen data (e.g., contacts, messages, credentials) to the C2 server. |
The attack was aimed at high-value targets in the Southern Asian region. Based on the knowledge we gained about the victim; we believe it was carried out by an APT group that remains unidentified or if not then an unknown threat actor. The continued use of SpyNote is notable, as it highlights the threat actors’ preference for leveraging this tool to target high-profile individuals despite being publicly available on various underground forums and telegram channels.