


In September 2025, ransomware activity remained elevated, with 504 global victims, heavily impacting consumer services, professional services, and manufacturing sectors. Qilin maintained the highest attack volume, while Incransom and Safepay experienced significant growth. Emerging actors such as Interlock leveraged stealthy FileFix delivery methods, Gunra expanded operations to Linux environments, and GLOBAL GROUP introduced an AI-powered Ransomware-as-a-Service (RaaS) model. The U.S. continued to be the primary target, followed by Canada and the U.K. High-profile campaigns, including Scattered Spider’s VMware ESXi intrusions and Warlock’s exploitation of zero-day vulnerabilities, highlighted the convergence of cybercrime and nation-state techniques. Meanwhile, nascent groups like Dire Wolf and D4RK4RMY shifted their focus toward data leaks and politically motivated campaigns, moving beyond traditional encryption-based ransomware operations.
Welcome to the September 2025 Ransomware Threat Report. This report delivers a detailed analysis of the ransomware landscape, highlighting the emergence of new ransomware groups, evolving attack techniques, and notable shifts in targeted industries. By examining key trends, tactics, and significant incidents, this report aims to support organizations and security teams in understanding the current threat environment. As ransomware campaigns continue to grow in complexity, this report serves as a vital resource for anticipating future threats and strengthening proactive cybersecurity strategies.
Akira evolved its tradecraft by breaching MFA-protected SonicWall VPNs through OTP seed theft, signaling a shift from patchable exploits (CVE-2024-40766) to persistent bypasses of multi-factor authentication.
MalTerminal introduced AI-powered ransomware, embedding GPT-4 to dynamically generate malicious payloads and reverse shells at runtime, blurring the line between static malware and adaptive attack frameworks.
Scattered Spider reemerged with targeted intrusions into financial services, combining AI-assisted vishing, Azure AD self-service password reset abuse, and VMware ESXi exploitation to maximize extortion impact.
CountLoader marked the rise of modular delivery platforms in the Russian ecosystem, leveraging multi-language variants (.NET, PowerShell, JavaScript) to distribute Cobalt Strike, AdaptixC2, and PureHVNC RAT.
HybridPetya weaponized UEFI bootkits (via CVE-2024-7344 Secure Boot bypass), encrypting the MFT at the firmware level and establishing pre-boot persistence, elevating ransomware to a near-irrecoverable extortion model.
Throughout Sept 2025, there was notable activity from several ransomware groups. Here are the trends regarding the top 5:
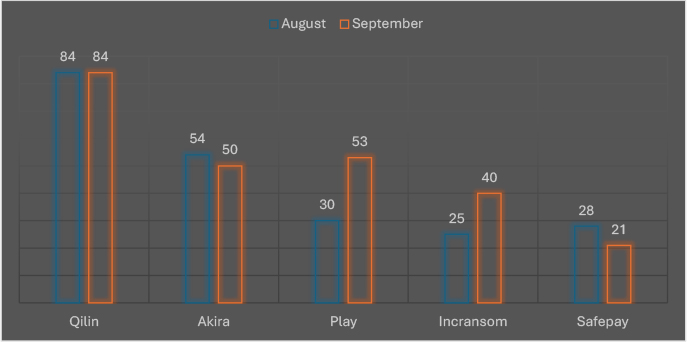
The September 2025 comparison highlights notable shifts among the top five ransomware groups. Play recorded the sharpest surge, with activity rising 77% from 30 to 53 victims, signaling increased operational momentum. Incransom also grew significantly, climbing 60% from 25 to 40 incidents, while Qilin maintained steady dominance with 84 victims in both months, underscoring its consistency. By contrast, Akira declined slightly by 7.4% (54 to 50), and Safepay saw the steepest drop, falling 25% (28 to 21). These patterns reflect the fluid nature of the ransomware ecosystem, where emerging groups are expanding aggressively while established players show both resilience and volatility.
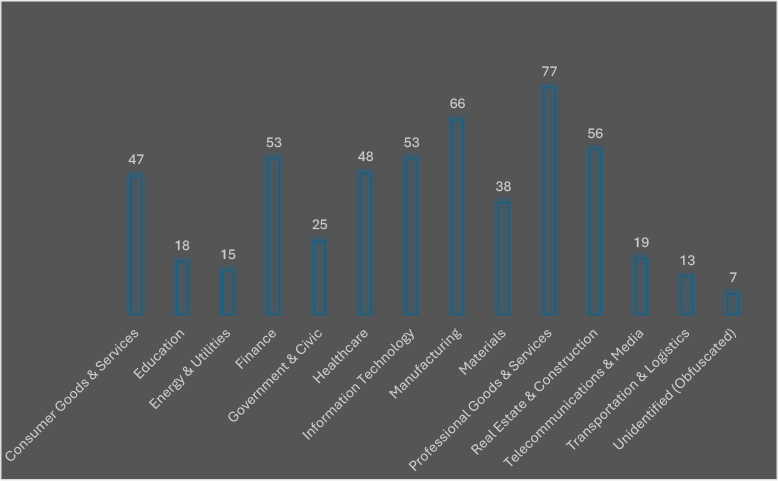
In September 2025, ransomware actors most heavily targeted the Professional Goods & Services sector, which recorded 77 victims, followed by Manufacturing (66), Real Estate & Construction (56), Information Technology (53), and Finance (53). Healthcare (48) and Consumer Goods & Services (47) also ranked among the most affected, highlighting attackers’ focus on industries with sensitive data, operational urgency, and strong ransom-paying potential. Materials (38) and Government & Civic (25) sectors continued to draw steady interest, while Education (18), Telecommunications & Media (19), Energy & Utilities (15), and Transportation & Logistics (13) saw moderate exposure. The Automotive sector (10 victims) also emerged as a notable target, reflecting adversaries’ expanding focus on supply chain–linked industries. A smaller set of 7 unidentified/obfuscated cases underscores persistent attribution challenges. Overall, September’s targeting patterns confirm ransomware groups’ dual strategy of exploiting both high-value service industries and critical infrastructure sectors to maximize impact and leverage.
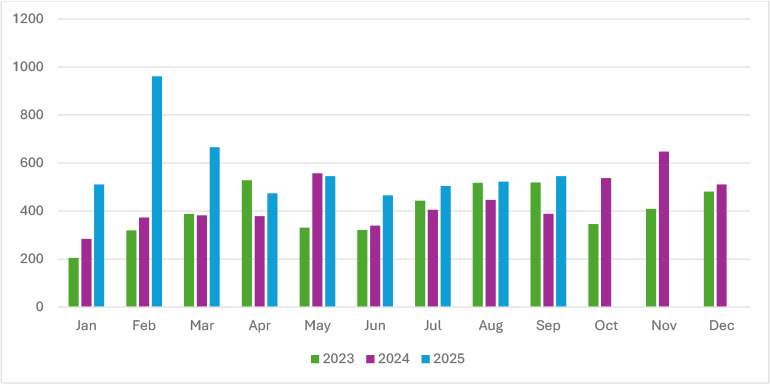
Ransomware victim volumes in 2025 reflect sharp volatility compared to prior years. After peaking at 961 cases in February, activity declined through the spring, bottoming out at 465 in June. The summer months showed relative stability, with July (504), August (522), and September (545), maintaining a steady pace. While this mid-year cooling contrasts with the explosive early-year surge, the overall scale remains significantly higher than in 2023–2024. The downturn likely reflects affiliate reshuffling, reduced output from high-volume operators, such as Incransom and Qilin, and possible tactical pivots toward quieter, more targeted intrusions. At the same time, actors like Devman and Safepay may be regrouping after early spikes or experimenting with campaigns that emphasize persistence over volume. Despite these fluctuations, ransomware remains deeply entrenched, with 2025 figures already outpacing previous years by a wide margin.
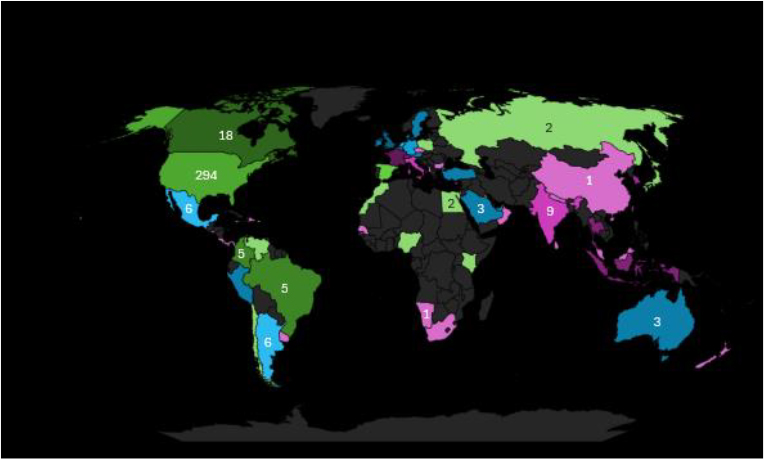
As of September 2025, the United States remained by far the most heavily targeted country by ransomware actors, with 294 victims, an order of magnitude higher than any other nation. South Korea (33), Germany (19), Canada (18), and France (13) followed distantly, while the United Kingdom (12), Spain (11), India (9), and Italy (9) also recorded notable activity. Mid-range targeting in countries such as Mexico, the Netherlands, and Argentina (6 each), alongside Colombia and Brazil (5 each), underscores ransomware’s spread across both advanced and emerging economies. Smaller but geographically diverse clusters in Asia, the Middle East, Africa, and Latin America, including Thailand, Taiwan, Indonesia, Switzerland (4 each), and numerous single-victim cases, demonstrate ransomware’s persistent global reach. The continued concentration in North America and Western Europe highlights adversaries’ preference for digitally mature and ransom-paying economies, even as campaigns extend strategically into new regions.
Adaptive Threats: AI-Powered Malware at the Forefront of Cyber Extortion
MalTerminal exemplifies a new phase in ransomware evolution by embedding GPT-4 to dynamically generate malicious payloads at runtime, blurring the line between static malware and on-demand ransomware creation. Unlike traditional ransomware, which relies on precompiled encryption logic, MalTerminal demonstrates adaptive, AI-assisted code generation, allowing operators to instantly produce ransomware or reverse shells, making detection and mitigation significantly more challenging.
ETLM Assessment:
Future LLM-enabled malware could leverage AI to automate attack chain generation, dynamically craft obfuscated ransomware, and adapt payloads per target environment, effectively producing personalized attacks at scale. Threat actors may combine this capability with automated phishing, runtime exploit selection, or multi-platform targeting, transforming ransomware from a static threat into a highly flexible, AI-driven attack-as-a-service model.
Reemergence & Recalibration: Targeted Intrusions into Financial Workflows
Scattered Spider’s resurfacing reflects an evolution from opportunistic credential theft to targeted, high-impact intrusions against financial services: operators combined sophisticated social engineering (vishing and lookalike domains) with Azure AD self‑service password reset abuse to gain executive access, then moved laterally through VPN/Citrix and VMware ESXi to harvest sensitive IT and cloud assets for extortion.
ETLM Assessment:
The group may double down on the financial sector by pairing AI assisted vishing and automated voice-synthesis tools with supply chain and cloud-targeted extortion playbooks. They are likely to monetize stolen data through direct extortion, resale to ransomware affiliates, or coordinated multi-stage campaigns that combine data theft, credential misuse, and selective destructive actions effectively, fusing leak and sell operations with opportunistic ransomware partnerships.
Dynamic Deployment Platforms: Advancing Malware Delivery in the Russian Ransomware Ecosystem
CountLoader represents an evolution in ransomware delivery by functioning as a tool, including Cobalt Strike, AdaptixC2, and PureHVNC RAT. Unlike traditional single-purpose loaders, CountLoader exists in .NET, PowerShell, and JavaScript variants, supporting multiple download and execution methods, leveraging LOLBins, and using on-the-fly PowerShell command encryption. This versatility demonstrates a shift toward modular, multi-platform loader architectures that enable ransomware affiliates to dynamically deploy payloads while evading defenses.
ETLM Assesment:
Looking ahead, CountLoader-like frameworks may expand to integrate adaptive payload generation, AI-assisted targeting, and autonomous lateral movement. Operators could combine multiple loaders, RATs, and ransomware modules into a single orchestration platform, allowing affiliates to select and deploy the optimal malware mix per target, automate post-exploitation tasks, and integrate ransomware-as-a-service campaigns with minimal technical friction.
Pre Boot Persistence: Firmware Level Extortion Rising
HybridPetya represents the maturation of ransomware into firmware level threat actors: by installing a UEFI bootkit on the EFI System Partition and exploiting CVE 2024 7344 to bypass Secure Boot, it moves encryption from userland to the pre boot environment, encrypting the MFT and weaponizing bootloader persistence. This shift elevates ransomware from recoverable disk level extortion to highly persistent, hard to remediate firmware sabotage that can survive OS reinstall and evade endpoint controls.
ETLM Assessment:
Adversaries will likely weaponize UEFI bootkits more broadly, combining Secure Boot bypasses, signed component abuse, and supply chain tricks to mass deploy firmware implants. Expect hybrid campaigns that pair destructive MFT/bootloader encryption with data exfiltration or ransom for decryption services, tighter targeting of enterprise imaging/backup systems, and automated tooling to reconstruct or brute force recovery keys, turning firmware exploits into turnkey, high impact ransomware offerings.
Black Shrantac
An emerging ransomware group that has recently surfaced in 2025, gaining traction in multiple sectors. As of September 2025, the group has claimed a total of 8 victims, targeting online services and platforms. Black Shrantac primarily engages in data exfiltration and extortion, publicly leaking stolen information on its dedicated leak sites. The concentrated activity in September highlights the group’s growing operational capacity and its focus on reputational and financial pressure rather than purely technical disruption. Its targeted approach and small but notable victim count suggest an early-stage threat with potential for rapid escalation.
Coinbase Cartel is an emerging ransomware/data extortion group that has gained attention in 2025. As of September 2025, it has claimed a total of 14 victims, primarily targeting online platforms and web services. The group is known for leaking stolen data on its dedicated leak sites, emphasizing financial and reputational pressure rather than widespread encryption attacks. The activity observed in September highlights its growing operational footprint, with consistent updates and a structured approach to victim engagement, marking it as a developing threat actor with potential for escalation.
Lunalock is a newly observed ransomware group that emerged in 2025, primarily focusing on targeted data theft and extortion. As of September 2025, the group has claimed a total of 2 victims. Lunalock appears to operate with a highly selective targeting approach, emphasizing reputational and financial leverage over widespread encryption campaigns. Its limited but confirmed activity in September suggests an early-stage group that could expand its operations if successful in its initial campaigns.
Radar is an emerging ransomware group that surfaced in 2025, conducting targeted extortion campaigns against select organizations. As of September 2025, it has claimed a total of 7 victims. The group primarily engages in data theft and public leaks rather than broad encryption attacks, using these tactics to exert financial and reputational pressure. Radar’s activity in September highlights its growing presence and structured approach, positioning it as a developing threat actor with potential for further expansion.
Shifting Frontlines: Akira’s Tactics Against SonicWall VPNs
The Akira ransomware campaign demonstrates a significant evolution by breaching even MFA-protected SonicWall VPN accounts, highlighting a shift from exploiting known vulnerabilities (CVE-2024-40766) to leveraging stolen OTP seeds and sidestepping multi-factor authentication itself. This progression underscores how ransomware operators are moving beyond simple credential theft and patchable flaws, advancing toward more persistent and stealthy methods that erode traditional security safeguards.
ETLM Assessment:
Looking forward, Akira and similar ransomware groups could expand into systematic MFA seed theft, real-time OTP interception, and broader abuse of BYOVD attacks to neutralize endpoint defenses at scale. They may also refine automated credential harvesting and target backup infrastructure more aggressively to maximize extortion leverage, positioning themselves not just as data-encryptors but as long-term infiltrators capable of repeated intrusions even after remediation.
Based on available public reports, approximately 31% of enterprises are compelled to halt their operations, either temporarily or permanently, in the aftermath of a ransomware onslaught. The ripple effects extend beyond operational disruptions, as detailed by additional metrics:
Ransomware remains a major threat to both organizations and individuals, locking critical data and demanding payment for its release. The consequences extend well beyond the ransom, often leading to costly recovery efforts, extended downtime, reputational harm, and potential regulatory fines. Such disruptions can destabilize operations and erode stakeholder trust. Addressing this growing risk demands a proactive cybersecurity posture and stronger collaboration between public and private sectors to build resilience against future attacks.
Cybercriminals are increasingly targeting industries that manage vast amounts of sensitive data, ranging from personal and financial information to proprietary assets. Sectors such as manufacturing, real estate, healthcare, FMCG, e-commerce, finance, and technology remain high on the threat radar due to their complex and extensive digital infrastructures. Adversaries strategically exploit vulnerabilities in economically advanced regions, launching well-planned attacks designed to encrypt critical systems and extract significant ransom payments. These operations are calculated to yield maximum financial returns.
The ransomware threat landscape in September 2025 revealed a shift toward modular, evasive, and high-impact operations. While overall victim numbers declined slightly, key groups like Qilin demonstrated technical maturity by exploiting zero-day vulnerabilities and introducing legal pressure tactics. Emerging groups such as Fog and Anubis showcased complex tool chains, indicating a strategic pivot to stealth and long-term compromise. Established actors also began leveraging legitimate tools and cloud platforms for persistence and data exfiltration. Organizations must enhance resilience, as ransomware now operates as a service ecosystem, rapidly adapting to security countermeasures.