



TRACKING RANSOMWARE : NOVEMBER 2024
November 2024 saw a 15.65% increase in ransomware incidents compared to October, with 606 reported victims globally. Emerging groups like Interlock and Ymir demonstrated advanced capabilities, targeting critical vulnerabilities, such as Veeam Backup systems. The Manufacturing, Healthcare, and Finance sectors experienced heightened attacks, while geographical focus remained on developed nations, led by the USA. This report also explores major ransomware events, highlighting the evolving tactics and impact of prominent and newly emerging ransomware groups.
The November 2024 ransomware landscape showcased escalating threats, with significant developments in tactics and targeted vulnerabilities. This report provides an in-depth analysis of ransomware trends, with a comparison to the previous month. It highlights the most affected industries, geographies, and the rise of sophisticated groups like Interlock and Ymir. Additionally, the report examines major events, such as sector-specific attacks and the exploitation of high-value vulnerabilities, offering insights into the current and emerging threat landscape.
Throughout November 2024, there was notable activity from several ransomware groups. Here are the trends regarding the top 5:
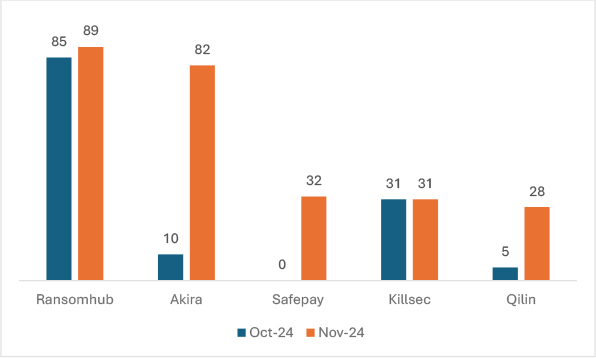
In November 2024, ransomware victim numbers showed significant fluctuations compared to October, with Akira experiencing a dramatic increase of 720%, indicating intensified activity. Safepay, a new entrant, surged to 32 victims, while RansomHub saw a modest increase of 4.7%. Killsec maintained its victim count at 31, showing no change, and Qilin had a notable rise of 460%, suggesting growing activity.
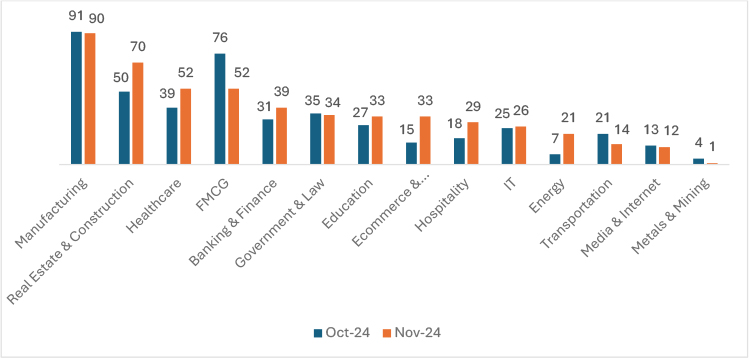
In November 2024, ransomware victim counts showed varied percentage changes across industries. The Manufacturing sector saw a slight decrease of 1.1%, while Real Estate & Construction rose by 40%. Healthcare increased by 33.3%, and FMCG experienced a 31.6% decline. Banking & Finance saw a 25.8% rise, while Government & Law had a minor decrease of 2.9%. Education increased by 22.2%, and Ecommerce & Telecommunication surged by 120%. Hospitality rose by 61.1%, IT had a small increase of 4%, and Energy saw a 200% jump. Transportation decreased by 33.3%, Media & Internet declined by 7.7%, and Metals & Mining dropped by 75%.
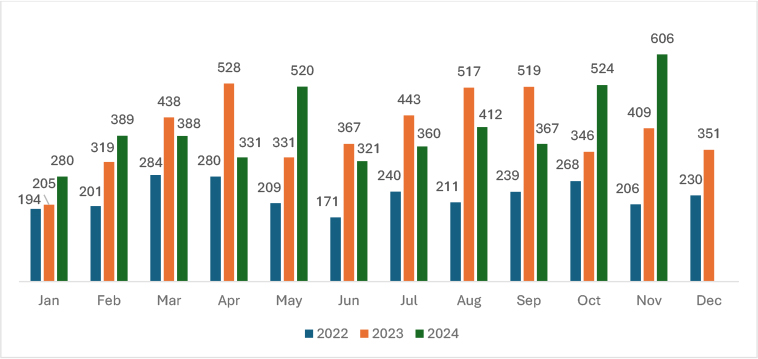
The increase from 524 victims in October 2024 to 606 victims in November 2024 represents a 15.65% rise in ransomware incidents, highlighting intensified attacks. This sharp uptick underscores ransomware operators’ escalating activities, likely exploiting critical sectors during high-demand periods, emphasizing the urgency of robust cybersecurity measures.
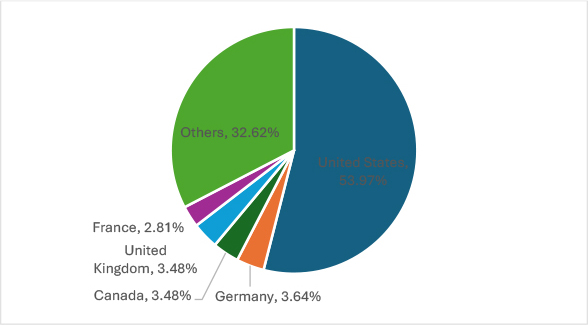
The chart illustrates the geographical distribution of ransomware targets in November 2024. The United States led with 326 victims, followed by Germany (22), Canada (21), United Kingdom (21), and France (17). Other regions reported 197 incidents, highlighting a concentrated focus on developed nations with critical industries and high-value data.
Frag seen exploiting vulnerability
A critical Veeam Backup and Replication (VBR) vulnerability (CVE-2024-40711) involving untrusted data deserialization is being actively exploited, notably by the recently identified “Frag” ransomware. Threat actors leverage this flaw, combined with stolen VPN credentials, to execute remote code on unpatched VBR servers, enabling them to add rogue accounts and deploy ransomware. The Frag ransomware group, similar to Akira and Fog, employs “Living Off the Land” (LOLBins) binaries, using pre-existing, legitimate software on systems to evade detection and complicate defenses. These attacks highlight VBR servers as high-value targets for ransomware groups seeking access to critical backup infrastructure.
ETLM Assessment: Threat actors are expected to continue exploiting VBR vulnerabilities, targeting backup systems for ransomware deployment. Vigilant patching and secure configurations are critical to mitigate further ransomware incidents.
Interlock is locking aggressively
Since stepping into the ransomware landscape in late September 2024, Interlock ransomware has launched targeted attacks against FreeBSD and Windows systems globally, claiming victims in various sectors, including Wayne County, Michigan. Uniquely, Interlock’s FreeBSD encryptor, compiled for FreeBSD 10.4, reflects a rare tactic previously seen only in the now-disbanded Hive operation. While the FreeBSD version experienced execution issues during testing, the Windows encryptor proved operational, wiping event logs and appending a “.interlock” extension to encrypted files. Interlock deploys a double-extortion method, breaching networks to exfiltrate data, and then encrypting files across devices. Victims are provided with a Company ID for communication on a dark web negotiation site, where ransom demands range from hundreds of thousands to millions.
ETLM Assessment: Interlock ransomware will likely continue exploiting FreeBSD and Windows systems, especially within critical infrastructure, given FreeBSD’s widespread use. Continued vigilance is essential as these ransomware operators may refine their tools for broader attack capabilities.
North Korean group seen collaborating with Play ransomware actors
The evolving cyber threat landscape reveals a significant collaboration between the North Korean state-sponsored group Jumpy Pisces and Play ransomware actors. In May 2024, Jumpy Pisces exploited a compromised user account to gain initial access, deploying tools like Sliver, an open-source red-teaming framework, for command-and-control (C2) operations, and DTrack, an infostealer disguised as a GIF file, for data theft. The attackers also utilized credential harvesting tools, such as Mimikatz and a trojanized binary targeting browser-stored data.
By early September, the same compromised account was used for pre-ransomware activities, including privilege escalation, lateral movement via PsExec, and the removal of security tools, culminating in the deployment of Play ransomware. Overlapping infrastructure, such as shared C2 servers and malware storage locations, strongly indicates collaboration or a sale of network access by Jumpy Pisces. This incident highlights the group’s shift toward broader ransomware campaigns, signaling an elevated global threat to organizations.
ETLM Assessment:
The collaboration between state-sponsored actors like Jumpy Pisces and ransomware groups signals a troubling evolution in ransomware tactics. Future campaigns may see increased use of advanced nation-state tools, expanded targeting across industries, and heightened global impact, emphasizing the urgent need for proactive defenses against these sophisticated ransomware threats.
BianLian Ransomware Evolution
BianLian ransomware has shifted exclusively to data theft extortion since January 2024, abandoning file encryption. It exploits vulnerabilities like ProxyShell (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207) for initial access and CVE-2022-37969 for privilege escalation on Windows systems.
Key tactics include using Ngrok and modified Rsocks for traffic masking, UPX-packed binaries for detection evasion, and renaming malicious tasks to mimic legitimate services. The group compresses exfiltrated data with PowerShell scripts and leverages webshells for persistence. Ransom notes include updated Tox IDs and pressure tactics involve printing ransom demands and directly contacting victim employees.
BianLian’s focus on data exfiltration, advanced evasion techniques, and infrastructure targeting reflects a sophisticated evolution in ransomware operations.
ETLM Assessment: BianLian’s exclusive focus on data theft extortion and advanced evasion tactics suggests continued evolution. With sophisticated targeting and exploitation of vulnerabilities, the group is likely to intensify attacks, increasing risks for organizations lacking robust cybersecurity defenses.
CyberVolk
A pro-Russian hacktivist group, CyberVolk, has launched its own ransomware-as-a-service (RaaS) operation. In June 2024, the group began using ransomware derived from AzzaSec’s leaked code. AzzaSec, a pro-Russia group, originally used AES and SHA512 encryption, but CyberVolk updated it to use ChaCha20-Poly1305, AES, RSA, and quantum-resistant algorithms. The ransomware terminates key processes like Task Manager and drops .bmp files before encryption starts. Victims are presented with a ransom note and a five-hour timer, with payment in cryptocurrencies.
CyberVolk has targeted government agencies in Japan and promoted other ransomware families, such as Doubleface, HexaLocker, and Parano, all based on AzzaSec’s code. The group’s operations show a blend of cybercrime and hacktivism, with shifting alliances and the growing threat posed by easy access to ransomware tools. The group’s communication was recently disrupted by mass bans on Telegram.
ETLM Assessment
Future ransomware developments may see further adoption of leaked codebases like AzzaSec, with increased sophistication in encryption and payload delivery. Ransomware-as-a-service models will likely evolve, exploiting geopolitical tensions and alliances for targeted, financially motivated attacks.
Helldown
A new ransomware group, Helldown, has emerged, exploiting vulnerabilities in certain firewalls to breach corporate networks. The group is believed to target CVE-2024-42057, a critical command injection flaw in the IPSec VPN feature. This vulnerability allows unauthenticated attackers to execute OS commands on vulnerable devices by sending crafted long usernames, but only if the device is configured with User-Based-PSK authentication.
Helldown, active since August 2024, has rapidly grown in prominence, with its extortion portal listing victims primarily from small to medium-sized businesses in the U.S. and Europe.
The group uses SSL VPN to gain access to networks, move laterally, and disable defenses. A malicious account (‘OKSDW82A’) and configuration file (‘zzz1.conf’) were identified as part of their tactics.
ETLM Assessment
Helldown is likely to intensify attacks, targeting more vulnerable systems worldwide, exploiting new vulnerabilities, and expanding operations. Expect increased use of sophisticated lateral movement and evasion tactics, impacting small-to-medium businesses.
Ymir ransomware
The Ymir ransomware, a newly identified Windows strain, follows RustyStealer infections, capitalizing on compromised high-privilege accounts to enable network lateral movement. RustyStealer initially infiltrates systems and uses tools like WinRM and PowerShell for remote control, along with utilities, such as Process Hacker and Advanced IP Scanner. SystemBC malware is deployed to create covert channels, potentially for data exfiltration or command execution. After establishing a foothold, Ymir is deployed as the final payload, running entirely in memory to avoid detection.
Upon execution, Ymir performs system reconnaissance, verifying the environment’s sandbox status. It uses the ChaCha20 encryption algorithm and appends a random extension to encrypted files, generating ransom notes in PDF format within affected directories. A pre-login message demanding ransom is displayed via Windows Registry modifications. Although Ymir currently lacks a dedicated data leak site, its operators appear to be accumulating victim data, with further leak threats anticipated.
Chort
Chort is the newest ransomware group to emerge, launching its leak site in mid-November 2024.
The site already lists 7 victims: five based in the USA and one high-profile target—the Ministry of Finance in Kuwait.
KAIROS
By mid-November 2024, another new ransomware emerged named KAIROS. The group has listed 8 victims to date.
Argonauts
Researchers have recently uncovered a ransomware group known as “Argonauts,” which has claimed responsibility for attacks on at least 10 organizations. The targets include six entities in Italy, three in Taiwan, and one in Japan, with the attacks possibly commencing as early as September 15.
Safepay
A newly observed ransomware operation, SafePay, emerged in November, targeting 22 victims across various industries and geographies. Using a LockBit-based binary, SafePay employs techniques borrowed from other ransomware groups, including ALPHV/BlackCat. The group gains access via Remote Desktop Protocol (RDP) and encrypts files while exfiltrating data.
The ransomware’s binary, obfuscated through a three-step XOR loop, is relatively simple to reverse engineer. SafePay leverages PowerShell scripts like ShareFinder.ps1 for network reconnaissance, with activity sequences including archiving stolen data using WinRAR, transferring files via FileZilla, and encrypting systems while disabling recovery features. It utilizes User Account Control (UAC) bypasses and privilege escalation tactics, such as token impersonation and enabling SeDebugPrivilege.
The group directs victims to ransom payment sites on Tor and “The Open Network” (TON). Notably, researchers exploited vulnerabilities in SafePay’s infrastructure, gaining insight into the backend server and operational methods.
Safepay, a new player claiming the attack on Microlise
The newly emerged SafePay ransomware gang has claimed responsibility for a cyberattack on UK-based telematics provider Microlise, alleging theft of 1.2 TB of data. The attack disrupted tracking services for major clients like DHL and Serco, causing delivery delays and temporarily affecting prisoner transport tracking systems. Microlise disclosed substantial progress in containing the threat, with the majority of customer systems restored, though some remain offline for security verification. While ransomware involvement is suspected due to the nature of disruptions, Microlise has not explicitly confirmed this. The company stated no customer systems data was compromised, and services are gradually resuming normal operations.
Ransomware is active more on weekends
Ransomware groups increasingly target weekends and holidays, exploiting reduced cybersecurity staffing during these periods. A recent study revealed that 86% of ransomware incidents occurred during off-hours, despite most organizations maintaining 24/7 security operations centers. Reduced staffing, budget constraints, and a false sense of security contribute to weaker defenses. Attackers leverage these vulnerabilities to infiltrate networks, steal data, and encrypt systems undetected. The researchers also found that 63% of attacks followed corporate events like mergers or workforce changes. Furthermore, while many organizations feel confident in their identity defenses, 83% experienced ransomware attacks in the past year, with insufficient budget allocation for securing critical systems like Active Directory cited as a key weakness.
Russia arrests cybercriminal Wazawaka
Mikhail Pavlovich Matveev, a notorious ransomware affiliate known as Wazawaka and Boriselcin, has been arrested by Russian authorities for developing malicious software used in ransomware operations targeting commercial organizations. He is linked to major ransomware groups like LockBit, Babuk, and Hive, responsible for significant attacks, including a 2020 breach of a New Jersey law enforcement agency, a 2021 attack on Washington D.C.’s Metropolitan Police Department, and a 2022 attack on a healthcare organization. Matveev is also accused of creating a hacking forum and has been sanctioned for targeting critical U.S. infrastructure. A $10 million reward was offered for his capture.
Bologna FC discloses data breach following RansomHub ransomware attack
Bologna Football Club 1909 confirmed a ransomware attack by the RansomHub group, resulting in the theft and publication of sensitive data. The stolen dataset includes sponsorship contracts, financial records, player medical and personal details, transfer strategies, fan and employee information, and confidential business plans. The attackers initially demanded a ransom, leveraging GDPR violations as pressure, but later released the data when demands were unmet. Ransomware targeting sports organizations is rare but impactful, with high-profile teams managing vast financial resources. This incident highlights the growing risks of ransomware in sports, highlighting the severe consequences of leaked sensitive data on operations and reputation.
Based on available public reports approximately 31% of enterprises are compelled to halt their operations, either temporarily or permanently, in the aftermath of a ransomware onslaught. The ripple effects extend beyond operational disruptions, as detailed by additional metrics:
Ransomware remains a serious threat to organizations and individuals, with its ability to encrypt critical data and demand payment for decryption. These attacks extend beyond ransom demands, inflicting financial burdens through recovery efforts and cybersecurity measures while disrupting operations and eroding customer trust. Victims often face reputational damage, regulatory penalties, and market instability, further undermining consumer confidence. To protect financial stability and public trust, it is imperative for businesses and governments to prioritize proactive measures against ransomware threats.
Cybercriminals are intensifying their focus on businesses that manage large volumes of sensitive data, such as personal information, financial records, and intellectual property. Sectors like manufacturing, real estate, healthcare, FMCG, e-commerce, finance, and technology face heightened risks due to their extensive data repositories. Targeting nations with robust economies and advanced digital infrastructures, attackers exploit vulnerabilities to encrypt vital data and issue substantial ransom demands, aiming to maximize their financial gains through sophisticated and calculated strategies.
The November 2024 ransomware surge highlights the persistent evolution of cyber threats, with increased sophistication in attack methods and growing exploitation of critical vulnerabilities. Key industries, including manufacturing, healthcare, and finance, remain at heightened risk. Organizations must prioritize robust cybersecurity measures, including regular patching, employee training, and incident response planning, to mitigate risks. Strengthening defenses against ransomware is essential to safeguard operations, protect sensitive data, and ensure resilience against this escalating global cyber threat.
STRATEGIC RECOMMENDATIONS:
MANAGEMENT RECOMMENDATIONS:
TACTICAL RECOMMENDATIONS: