


In May 2025, ransomware attacks targeted critical industries such as Professional Goods & Services, Consumer Goods, and Manufacturing, with a total of 545 incidents reported globally marking a 15.95% increase from April. Emerging groups such as SafePay and SilentRansomGroup led with 72 and 67 attacks respectively, while established actors like Qilin, Akira, and Play experienced a decline in activity. The United States remained the top geographical target, followed by Germany and Canada. Notably, threat actors intensified the abuse of legitimate tools, adopted advanced loaders, and explored new delivery methods such as JPEG-embedded ransomware. Additionally, newly identified groups like J Group and IMN Crew added further complexity to the landscape.
Welcome to the May 2025 ransomware report. This report provides an in-depth analysis of the evolving ransomware threat landscape observed during the month. It highlights the emergence of new ransomware groups, changing attack patterns, and shifting industry targeting. By examining trends, tactics, and key events, the report aims to help organizations and security teams better understand the current threat environment and prepare for potential future attacks. As ransomware campaigns become increasingly stealthy, modular, and diverse in delivery methods, this report serves as a critical resource for tracking these developments and shaping proactive cybersecurity strategies.
KEY POINTS
Throughout May, several notable ransomware groups were active. Here are the trends regarding the top 5:
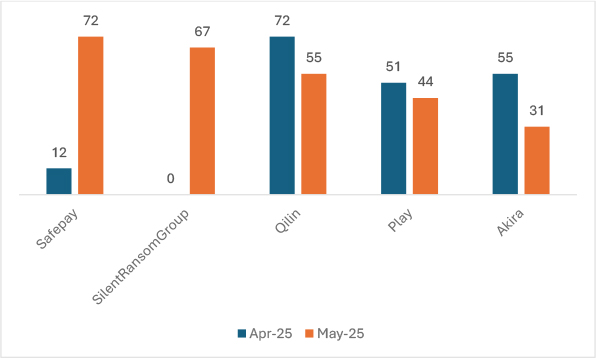
In May, ransomware activity saw a dynamic shift with the emergence of new groups and fluctuating trends among established actors. SafePay and SilentRansomGroup appeared as significant threats, recording 72 and 67 incidents respectively, with no recorded activity in April, indicating their recent emergence. Qilin, previously dominant with 72 attacks in April, experienced a decline to 55 incidents. Similarly, Play dropped from 51 to 44, and Akira saw a notable reduction from 55 to 31. This transition highlights the volatile ransomware landscape, where new actors quickly gain traction while some established groups reduce operations or shift focus.
It’s also possible that SilentRansomGroup was active previously and only launched its leak site recently.
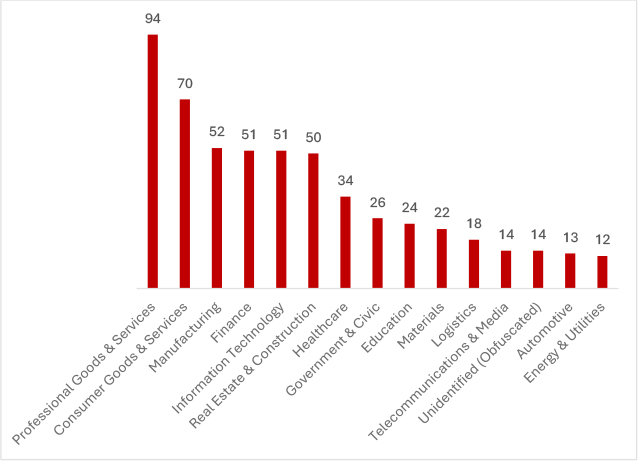
In May 2025, ransomware groups primarily targeted the Professional Goods & Services sector with 94 incidents, followed by Consumer Goods & Services (70) and Manufacturing (52). Critical industries like Finance, IT, and Real Estate also faced significant threats, each recording over 50 attacks. Healthcare and Government sectors continued to be vulnerable, while Education, Logistics, and Telecommunications saw moderate activity. Even less commonly targeted sectors like Automotive and Energy faced attacks, highlighting the broad and indiscriminate nature of ransomware campaigns across industries.
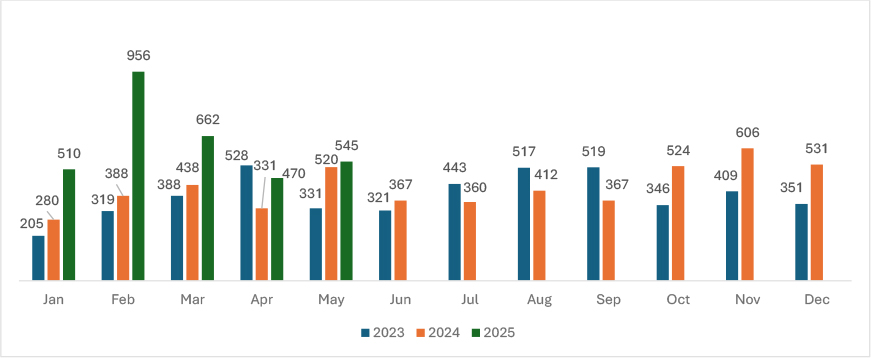
In May, ransomware attacks recorded 331 incidents in 2023, 520 in 2024, and 545 in 2025, reflecting a consistent upward trend year-over-year. Compared to April 2025, May 2025 registered a 15.95% increase in ransomware activity. This surge indicates heightened threat actor operations, with May 2025 marking one of the highest activity months of the year so far. The year-over-year growth and month-over-month escalation highlight the increasing scale and aggressiveness of ransomware campaigns in 2025.
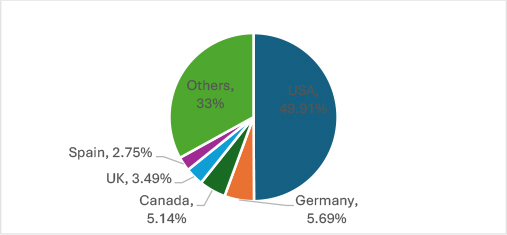
In May 2025, the United States remained the top target of ransomware attacks, with 272 victims, significantly outpacing other regions. Germany followed with 31 attacks, while Canada (28) the United Kingdom (19), and Spain (15) saw lower but notable ransomware activity. These regions are prime targets due to their robust economies, data-rich enterprises, critical infrastructure, and high potential for ransom payments, making them highly lucrative for cybercriminals.
Qilin Adds SmokeLoader and NETXLOADER to Their Arsenal
The Agenda ransomware group, also known as Qilin, has significantly advanced its attack methodology by integrating two sophisticated loaders: NETXLOADER and SmokeLoader. NETXLOADER, a .NET-based loader protected with .NET Reactor 6, employs advanced obfuscation techniques such as control flow obfuscation, anti-tamper mechanisms, and JIT hooking to evade detection and complicate analysis. It dynamically loads encrypted assemblies and uses reflection to invoke obfuscated methods at runtime, facilitating the in-memory execution of subsequent payloads. Following this, SmokeLoader acts as an intermediary, performing sandbox and virtualization checks, injecting into legitimate processes like explorer.exe, and terminating analysis tools to ensure stealth. The final payload, the Agenda ransomware, is deployed using reflective DLL injection, allowing it to execute directly in memory without touching the disk. The group’s shift from Go to Rust for their ransomware development further enhances their capabilities, introducing features like remote execution and improved propagation within virtual environments.
ETLM Assessment:
Looking ahead, the Agenda ransomware group is likely to continue refining its tactics, techniques, and procedures (TTPs), potentially incorporating more advanced evasion strategies and expanding its target base. Their adoption of Rust and sophisticated loaders indicates a trend towards more resilient and stealthier malware, posing increased challenges for detection and mitigation efforts.
Kickidler abused in ransomware attacks
Ransomware affiliates of Qilin and Hunters International are leveraging legitimate employee monitoring software, Kickidler, for post-compromise reconnaissance. The infection chain begins with a malvertising campaign using fake Google Ads for RVTools, which redirects users to a trojanized installer hosted on a counterfeit domain. This installer acts as a loader for the SMOKEDHAM PowerShell-based .NET backdoor. Once executed, SMOKEDHAM downloads and installs Kickidler to record keystrokes, capture screenshots, and log user activity. This method allows attackers to stealthily harvest privileged credentials – especially for off-site cloud backups – without using high-risk memory dumping techniques. The collected credentials enable lateral movement and access to critical infrastructure, including VMware ESXi environments. In the final stage, ransomware payloads are deployed, with Hunters International utilizing VMware PowerCLI and WinSCP Automation to enable SSH and execute encryption scripts targeting VMDK files on ESXi servers, leading to widespread disruption.
ETLM Assessment
Qilin and Hunters International are expected to intensify their abuse of legitimate tools like Kickidler and SMOKEDHAM to evade detection and harvest credentials over extended dwell times. Their focus on backup infrastructure and ESXi environments suggests a shift toward high-impact enterprise disruptions, likely leading to broader targeting of IT administrators and more refined, stealthy initial access techniques in future campaigns.
Cybercriminals Hide Undetectable Ransomware Inside JPG Images
A novel ransomware delivery method has emerged, leveraging seemingly benign JPEG images to bypass detection and execute fully undetectable (FUD) ransomware attacks. The attack unfolds in multiple stages. First, a JPEG image embeds a concealed payload that activates a stager script upon viewing. This stager then connects to a remote server to retrieve the ransomware executable. To enhance evasion, the payload is split between the image and a secondary decoy file, such as a PDF or Word document, minimizing detection by traditional antivirus tools. The ransomware leverages advanced obfuscation and encryption techniques, resulting in near-zero detection rates across most engines. Social engineering plays a key role, in exploiting user trust in common file formats. The method requires minimal effort – just two files per attack – making it scalable for mass campaigns. The approach demonstrates a shift toward stealth, sophistication, and psychological manipulation in ransomware deployment.
ETLM Assessment:
This image-based ransomware method is expected to evolve into more refined and harder-to-detect variants. Future campaigns will likely pair visual file types with decoy documents in more convincing social engineering lures. As detection evasion improves, attackers may automate and scale this delivery model, leading to widespread enterprise targeting, especially in sectors with weak behavioral monitoring and poor attachment vetting protocols.
Threat Actor Leverages SAP NetWeaver Vulnerability to Deploy PipeMagic Trojan
Multiple threat actors, including BianLian, RansomExx, and Qilin, have exploited CVE-2025-31324 – a critical vulnerability in SAP NetWeaver – allowing for full system access. In some cases, attackers also chained this with CVE-2025-42999, a related deserialization flaw. Following exploitation, web shells were deployed to gain persistent access and deliver payloads such as the plugin-based PipeMagic trojan. PipeMagic was previously linked to zero-day privilege escalation in Windows CLFS (CVE-2025-29824). Post-exploitation activities included the use of Brute Ratel C2 and SOCKS5 tunneling via tools like rs64c.exe, with communication observed between infected hosts and known command-and-control infrastructure. Despite some failed attempts, these campaigns highlight the convergence of high-profile vulnerability exploitation and sophisticated post-exploitation tooling. Infrastructure overlaps across incidents link back to known BianLian and Qilin operations, suggesting broader threat actor interest in SAP ecosystem compromise for data extortion or ransomware deployment.
ETLM Assessment
With CVE-2025-31324 gaining traction among ransomware groups, exploitation is likely to increase, especially targeting unpatched SAP environments. As threat actors refine access methods and combine them with tools like PipeMagic and Brute Ratel, more successful breaches and ransomware deployments are expected. Organizations relying on SAP NetWeaver face elevated risks of lateral movement, data theft, and encryption-based extortion.
Ransomware Gangs Use Skitnet Malware for Stealthy Data Theft and Remote Access
Skitnet malware, also known as Bossnet, is increasingly being adopted by ransomware groups, including Black Basta, for post-exploitation activities such as data exfiltration and remote access. First advertised in April 2024, Skitnet is a multi-stage tool using Rust and Nim to establish a DNS-based reverse shell, allowing stealthy communication with command-and-control (C2) servers. It features persistence mechanisms, PowerShell execution, screenshot capture, AV enumeration, and deployment of remote access software like AnyDesk or Rutserv. The initial Rust binary decrypts and launches a Nim-based payload that communicates via DNS every 10 seconds to receive and execute commands. To evade detection, it dynamically resolves API calls using GetProcAddress. In parallel, a malware loader named TransferLoader has been used to deliver the Morpheus ransomware. TransferLoader comprises a downloader, backdoor, and loader, using IPFS as a fallback C2 channel and employing obfuscation for anti-analysis. These developments highlight evolving trends in stealthy ransomware delivery and execution methods.
ETLM Assessment
Skitnet’s modular design, DNS tunneling, and language diversity make it highly adaptable for stealthy operations. Its growing popularity among ransomware operators like Black Basta suggests increased adoption across the ecosystem. Future variants will likely integrate enhanced obfuscation, broader remote access capabilities, and tighter C2 evasion, making detection and remediation even more challenging for enterprise defenders.
Overall Trends:
Advanced Loader Chains Enhance Stealth and Evasion – Groups like Qilin now integrate custom loaders such as NETXLOADER and SmokeLoader to enable reflective DLL injection, in-memory execution, and sandbox evasion. These toolchains complicate detection, analysis, and mitigation, signaling a trend toward stealthy delivery architectures.
Abuse of Legitimate Software for Reconnaissance and Credential Theft – Ransomware affiliates increasingly deploy tools like Kickidler and SMOKEDHAM for post-compromise surveillance. These methods avoid traditional credential dumping by capturing keystrokes and screen activity, emphasizing a shift toward long-dwell reconnaissance without raising alerts.
Ransomware Delivery via Non-Traditional Vectors – Attackers are embedding ransomware in JPEG images and pairing them with decoy documents to bypass detection. This demonstrates a growing reliance on social engineering and FUD (fully undetectable) techniques, targeting human vulnerabilities rather than system flaws.
Exploitation of Enterprise Software Vulnerabilities – Threat actors including Qilin, BianLian, and RansomExx are exploiting SAP NetWeaver vulnerabilities (CVE-2025-31324) for initial access. The use of tools like PipeMagic and Brute Ratel post-exploitation reflects a trend toward coordinated exploitation and advanced lateral movement within enterprise environments.
J Group
A newly emerged ransomware group launched its leak site at the beginning of May 2025 and has already listed over 15 victims. While detailed information about the group remains limited, our team is actively monitoring the situation. Stay tuned to our reports for timely updates and in-depth analysis as more intelligence becomes available.
IMN Crew
IMN Crew is a new financially motivated ransomware and data-extortion group active since March 2025. They exploit vulnerable external services to access networks, exfiltrate data using open-source tools, and recently began encrypting Windows systems with a leaked ransomware builder (.imn extension). Targeting mainly small to medium businesses across various sectors and countries, they demand Bitcoin ransoms but use polite communication without aggressive pressure tactics. At the time of writing the group claimed 8 victims.
Germany doxes Conti ransomware and TrickBot ringleader
A recently identified key figure behind the TrickBot and Conti cybercrime operations, Vitaly Nikolaevich Kovalev, also known as “Stern,” has been named as the ringleader of these groups by German authorities. Previously sanctioned by the U.S., Kovalev was tied to aliases such as “Bentley” and “Bergen” and was linked to ransomware strains including Ryuk, Conti, and Diavol, as well as malware variants BazarLoader, SystemBC, IcedID, and TrickBot itself. Internal leaks – TrickLeaks and ContiLeaks – revealed his control over the gangs and highlighted his role in approving attacks and legal defense strategies. The groups were responsible for infecting hundreds of thousands of systems globally, particularly in Germany, targeting hospitals, public institutions, companies, and private individuals. Operating in a structured, hierarchical manner, the group’s illicit profits reached hundreds of millions. Despite recent takedown efforts under Operation Endgame, Kovalev remains at large, reportedly residing in Russia, as authorities continue to pursue intelligence on his current digital footprint.
An Iranian pleads guilty to RobbinHood ransomware attacks
An Iranian national, Sina Gholinejad (aka “Sina Ghaaf”), has pleaded guilty for his role in the RobbinHood ransomware operation that targeted U.S. cities and organizations from January 2019 to March 2024. The group attacked networks belonging to Baltimore, Greenville, Gresham, Yonkers, Meridian Medical Group, and Berkshire Farm Center. RobbinHood was deployed manually using administrator credentials or exploited vulnerabilities, encrypting systems and demanding Bitcoin ransoms via Tor-based portals. The ransomware campaign gained prominence after crippling Baltimore’s IT infrastructure in May 2019. Later campaigns incorporated data exfiltration, using leak threats to increase extortion pressure. Technically notable, RobbinHood leveraged Bring Your Own Vulnerable Driver (BYOVD) techniques, exploiting a signed but flawed Gigabyte driver (gdrv.sys) to disable antivirus protections and execute payloads undetected. The attackers used VPS infrastructure in Europe, VPNs and crypto mixers to evade tracking. Gholinejad now faces up to 30 years in prison for his involvement in fraud, extortion, and laundering proceeds from these ransomware operations.
MATLAB dev confirms ransomware attack
MathWorks, a developer of mathematical computing tools, confirmed a ransomware attack on May 18 that disrupted several internal systems and customer-facing services, including cloud center, file exchange, and license management. Multi-factor authentication and Single Sign-On were restored by May 21, but issues persist, especially for users inactive since October 11, 2024. The identity of the ransomware group remains unknown, as no public claims have been made, raising the possibility of ransom payment or ongoing negotiations. The extent of data compromise has not been disclosed. Law enforcement has been notified, and service recovery is ongoing amid limited communication from the organization.
Interlock seen locking aggressively
Kettering Health, a major healthcare provider in Ohio, suffered a cyberattack on May 20, leading to widespread technology outages. Elective inpatient and outpatient procedures were canceled, and the call center was rendered inaccessible. The attack is linked to the Interlock ransomware group, associated with the threat actor Nefarious Mantis, known for targeting healthcare networks using the Interlock RAT for internal reconnaissance. A ransom note confirmed system compromise and threatened data leaks. While emergency services remain operational, scam calls impersonating staff have also been reported. No official claim has been posted on leak sites, but the incident aligns with Interlock’s known tactics and past campaigns.
VanHelsing ransomware builder leaked
The VanHelsing ransomware-as-a-service operation, active since March 2025 with eight known victims, has published its own source code after a former developer, “th30c0der,” attempted to sell it on a cybercrime forum. The leaked materials include the Windows encryptor builder, affiliate panel, and partial data leak infrastructure but exclude the Linux builder and database. The builder links to an API endpoint and requires modification to function independently. The source also reveals attempts to develop an MBR locker to overwrite boot records with a ransom message. This mirrors past leaks from Babuk, Conti, and LockBit, which enabled new threat actors to replicate attacks.
Based on available public reports approximately 31% of enterprises are compelled to halt their operations, either temporarily or permanently, in the aftermath of a ransomware onslaught. The ripple effects extend beyond operational disruptions, as detailed by additional metrics:
Impact Assessment
Ransomware continues to pose a significant threat to both organizations and individuals, restricting access to vital data and demanding payment for its release. The impact goes far beyond the ransom itself, often resulting in expensive recovery efforts, prolonged operational disruptions, and lasting reputational damage. Affected entities may also incur regulatory penalties and market instability, undermining stakeholder confidence and financial health. Mitigating these risks requires the public and private sectors to implement proactive cybersecurity measures and enhance their overall resilience against such threats.
Victimology
Cybercriminals are intensifying their focus on industries that handle large volumes of sensitive data, including personal information, financial records, and intellectual property. High-risk sectors such as manufacturing, real estate, healthcare, FMCG, e-commerce, finance, and technology are prime targets due to their expansive digital infrastructure. Threat actors strategically exploit vulnerabilities in economically advanced nations, aiming to encrypt critical data and demand substantial ransoms. These attacks are carefully orchestrated to maximize financial gain.
In May 2025, the ransomware threat landscape showcased intensified efforts by financially motivated threat actors. These groups have demonstrated enhanced operational sophistication, leveraging vulnerabilities, obfuscated payloads, and social engineering for high-impact enterprise disruption. The evolution of ransomware delivery including stealth loaders, image-based payloads, and abuse of legitimate tools – highlights the growing complexity of attacks. With emerging groups rapidly gaining ground and established actors shifting tactics, organizations must adopt layered defense strategies. Investment in proactive threat intelligence, security governance, employee training, and infrastructure hardening is essential to mitigate the risks of ransomware and ensure long-term cyber resilience.