



This CYFIRMA Monthly Ransomware report thoroughly analyses ransomware activity in January 2024, covering significant attacks, the top five ransomware families, geographical distribution, targeted industries, evolution of attacks, and trends. Organizations can leverage these insights to enhance their cybersecurity strategies and mitigate ransomware risks.
Welcome to the January 2024 Ransomware Report. This report offers a detailed analysis of ransomware events during this period. We explore the top 5 most active ransomware groups and the industries they targeted, as well as the locations that experienced the most attacks. We also discuss the evolution of ransomware groups and vulnerabilities exploited, intending to equip organizations with crucial insights to bolster their cybersecurity measures and combat the evolving threat landscape effectively.
In January 2024, multiple ransomware groups were active. Below, we outline trends concerning the top five groups.
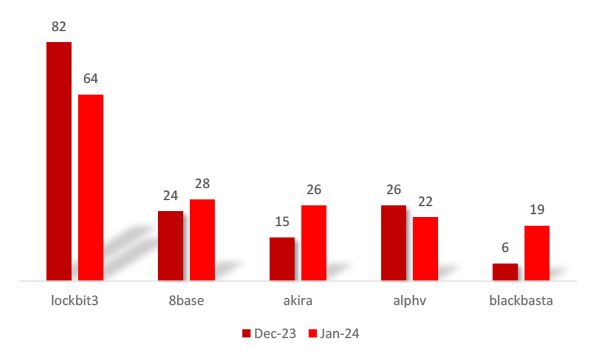
The decline in the number of victims for LockBit and Alphv indicates either potential success in ransom negotiations, or fewer targets. The increased number of victims of 8Base, Akira and Blackbasta showcase the increased activity of these groups and the possible failure in ransom negotiations.
The growing Akira victim list can also be attributed to the exploitation of vulnerabilities in Cisco products.
LOCKBIT
Manufacturing stands out as the primary industry targeted, with the United States being the most focused nation for LockBit.
As per the information available, LockBit disclosed the victim organizations reporting revenue up to $19.3 billion, suggesting that the attackers targeted organizations across a broad range of revenue scales.
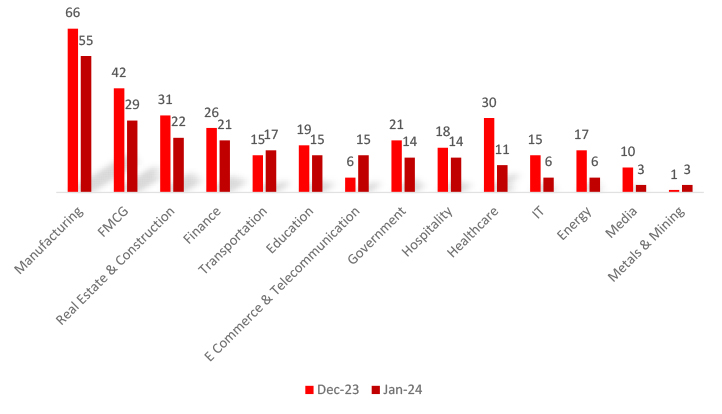
The trend comparison of ransomware incidents from December 2023 to January 2024 indicates fluctuations across various sectors. Manufacturing witnessed a 16.67% decrease, while FMCG experienced a 30.95% decline. Real Estate & Construction fell by 29.03%, Finance decreased by 19.23%, and Transportation increased by 13.33%. E Commerce & Telecommunication surged by 150%, while Healthcare and IT both suffered notable declines. The reasons for targeting these sectors include financial gains, sensitive data availability, and critical infrastructure reliance. Ransomware attackers exploit vulnerabilities in these sectors for monetary extortion or disrupting essential services, amplifying their impact.
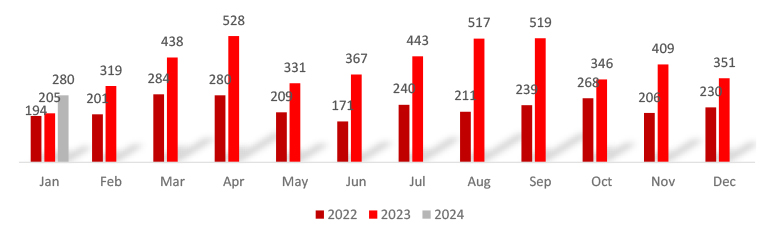
Over the years, ransomware attacks have shown a concerning upward trend, steadily increasing by 39.02% between 2022 to 2023, rising by a further 36.59% into 2024, underscoring the growing threat.
Despite a 20.51% decrease in the number of victims between December 2023 to January 2024, the continued need for robust cybersecurity measures remains, as the overall trend longer-term is the reverse, and this is likely to represent a minor fluctuation.
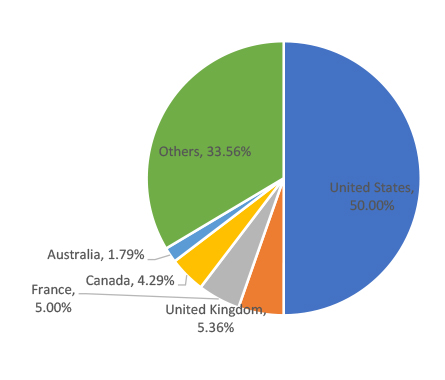
In January 2024, the top five countries targeted by ransomware attacks were the United States with 140 incidents, followed by the United Kingdom with 15, France with 14, Canada with 12, and Australia with 5. These countries are targeted due to their strong economies, and high levels of internet connectivity, making them lucrative targets for cybercriminals seeking financial gains.
CVE ID: CVE-2020-3259
CVSS Score: 7.5
Associated Ransomware: Possibly Akira Ransomware
NAME: Cisco ASA (Adaptive Security Appliance) and FTD (Firepower Threat Defence) vulnerability
Vulnerability Affected version details.
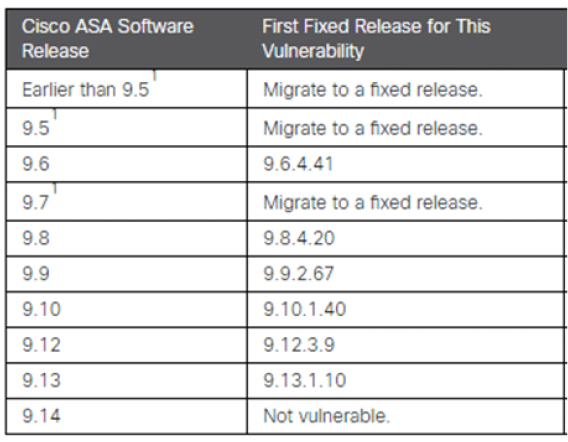
Table of software versions vulnerable to CVE-2020-3259 and fixed releases for Cisco ASA devices (Source: Surface web)
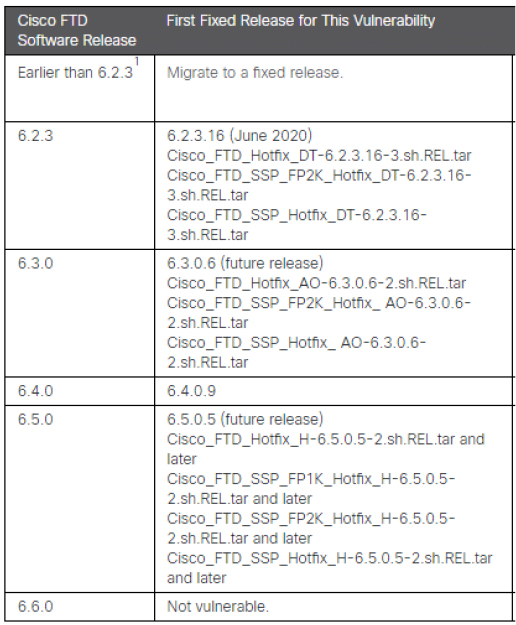
Table of software versions vulnerable to CVE-2020-3259 and fixed releases for Cisco FTD devices (Source: Surface web)
3AM ransomware tied to Conti and Royal cybercrime syndicates.
Researchers examined the recently emerged 3AM ransomware and found strong connections between this new threat – also called ThreeAM – and well-known groups like Conti syndicate and the Royal ransomware gang. 3AM uses a unique method of publicizing data breaches on victims’ social media, announcing the breach to affected parties’ followers, deploying bots to interact with key accounts on X (formerly Twitter) and leading them to the leaked information.
Slug
Slug is a new Ransomware group that launched its leak site in mid-January. However, as of now, no additional information about the group is available. Their logo showcases a Glaucus Atlanticus, also known as a blue sea dragon. The group claimed 1 victim during the writing of this report.
Going Insane
Another new ransomware group that launched a leak site in January is Going Insane. The group actively promotes its program, highlighting the following features:
The group accepts payments in Bitcoin, Ethereum, and Monero (Cryptocurrency payments assuring anonymity).
During the drafting of this report, the group had already claimed one victim.
Kasseika Ransomware
Kasseika is a newly emerged ransomware and exhibits similarities with BlackMatter, adopting the “bring-your-own-vulnerable-driver” trend. Utilizing targeted phishing, it infiltrates networks, exploits the Martini driver to disable antivirus processes, and employs PsExec for malicious file execution. The ransomware, packed with Themida, encrypts files using ChaCha20 and RSA algorithms, changing extensions and appending ransom notes. It further conceals its activities by clearing event logs.
Akira Hits IT Gaint
Finnish IT services provider; Tietoevry, experienced an Akira ransomware attack on one of its data centers in Sweden, impacting cloud hosting services. The attack affected various businesses, including Sweden’s largest cinema chain; Filmstaden, which led to outages for multiple customers. The Akira ransomware gang, known for double-extortion attacks, have previously targeted weakly secured Cisco VPN implementations. The Finnish National Cyber Security Center had even issued a warning about Akira targeting organizations in the country prior to the event.
Medusa targeted Water for People
Water for People, a nonprofit dedicated to enhancing access to clean water, is the most recent organization to be targeted by ransomware criminals. The ransomware group demanded for $300K but the organization denied it, and as a result, some data was leaked (but the total leak size is unknown).
Blackhunt targeting Paraguay
Paraguay’s largest mobile carrier; Tigo, faced a cyberattack impacting its business division’s cloud and hosting services. While the company officially confirmed the security incident, details were not disclosed. Reports on social media suggested the involvement of the Black Hunt ransomware, who claimed over 330 servers were encrypted, with compromised backups. The Paraguay military’s General Directorate issued a warning about Black Hunt ransomware attacks following the incident.
Blackcat made a dark impact on FNF
Fidelity National Financial (FNF), a major U.S. title insurance and transaction services provider, confirmed a cyberattack by the BlackCat ransomware gang, exposing the data of 1.3 million customers. The attack used non-propagating malware, leading to successful containment within seven days. FNF notified affected customers, providing credit monitoring and other services. The company believes the incident won’t materially impact its finances.
Source code of Zeppelin for sale
A cybercriminal posted on a forum, offering the Zeppelin ransomware-builder’s source code and a cracked version for $500. Though the offer’s legitimacy is unverified, screenshots given by the threat actor suggest authenticity. The buyer could employ the malware to establish a new ransomware-as-a-service (RaaS) operation or create a new locker within the Zeppelin family.
Based on available public reports approximately 31% of enterprises are compelled to halt their operations, either temporarily or permanently, in the aftermath of a ransomware onslaught. The ripple effects extend beyond operational disruptions, as detailed by additional metrics:
A case in point involves Johnson Controls, which became a target of the Dark Angels Ransomware faction. The attackers demanded a hefty sum of $51 million for the deletion of the exfiltrated 27TB of data and the provision of decryption keys. Despite Johnson Controls’ decision against paying the ransom, the incident led to the company incurring around $27 million in response and remediation costs, demonstrating the extensive financial implications of ransomware attacks, irrespective of the ransom payment decision.
Furthermore, organizations embroiled in such cybersecurity incidents often find themselves grappling with legal repercussions, including civil penalties and are subjected to intensified regulatory scrutiny. This not only compounds the financial burden but also poses significant reputational risks, affecting stakeholder trust and market positioning.
Impact Assessment
Ransomware poses a significant threat, causing challenges for both companies and individuals, through the theft of crucial data, followed by a demand for payment in exchange for its return. These attacks can result in substantial financial losses, incurred either by paying the ransom or investing in cybersecurity solutions for restoration. Additionally, there are financial setbacks from disrupted services, diminished customer trust, and emotional distress. Beyond immediate financial concerns, such attacks can violate data regulation laws, impacting reputation, consumer trust, and market confidence. Hence, addressing ransomware stands out as a paramount priority for businesses and government organizations.
Victimology
Presently, threat actors concentrate on businesses holding valuable data, encompassing personal details, financial information, and intellectual property. Industries like Manufacturing, Real Estate, Healthcare, FMCG, E-commerce, Finance, and Technology face heightened vulnerability due to their data abundance. Cybercriminals strategically select countries with strong economies and advanced digital infrastructures to optimize ransom returns. Their goal is clear: pinpoint vulnerabilities, encrypt data, and demand substantial ransoms for release, all with the objective of securing significant profits.
In January 2024, the ransomware landscape witnessed notable shifts, with LockBit focusing on manufacturing, and the US being the most affected region. The rise of new and evolving players such as Slug, Going Insane and Kasseika is giving a new dimension to the ransomware landscape. Notable events include Akira targeting a major IT firm, and Medusa impacting the non-profit organization; Water for People. Blackhunt attacked Paraguay’s Tigo, and Blackcat hit Fidelity National Financial, exposing the data of 1.3 million customers. Additionally, the source code of Zeppelin ransomware was offered for sale. While there was a decrease in ransomware victims from December 2023 to January 2024, the overall trend reveals a consistent rise in incidents from January 2022 to January 2024.