



August 2024 witnessed a noticeable increase in ransomware activity, with emerging groups like Lynx and RansomHub showing dramatic surges in victim numbers. The report highlights a 14.4% overall increase in ransomware incidents compared to July 2024. Sectors such as Finance, FMCG, and Manufacturing saw significant increases in targeting, while Healthcare and Government sectors saw a decline. New tactics employed by groups like Qilin and Mad Liberator, along with the dismantling of Radar/Dispossessor’s infrastructure by the FBI, underline the dynamic nature of the threat landscape. This report concludes with an analysis of the key ransomware events of the month, including major ransom payments and law enforcement actions.
The August 2024 ransomware landscape has been marked by significant developments and shifts, with emerging groups like RansomHub and Lynx gaining traction. This report provides a comprehensive analysis of the top ransomware trends, comparing the activity levels from July 2024 to August 2024, and highlighting the evolving strategies of key ransomware groups. Additionally, the report examines the sectors most targeted by ransomware attacks and the geographical locations that were most affected. Key ransomware events, including significant attacks and law enforcement actions, are also detailed, offering insights into the current threat landscape.
Throughout August 2024, there was notable activity from several ransomware groups. Here are the trends regarding the top 5:
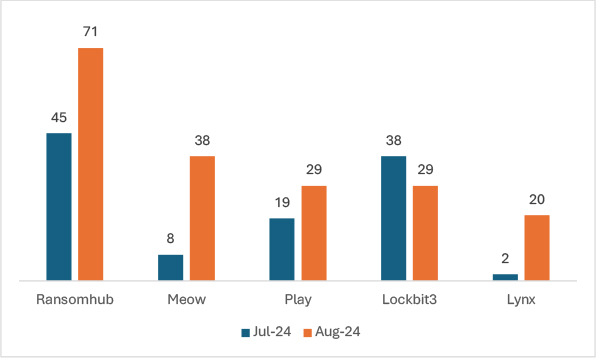
In August 2024, ransomware trends exhibited significant shifts, with emerging groups gaining momentum. RansomHub saw a 57.78% increase in victims compared to July, while Meow surged by 375%, growing from 8 to 38 victims. Play ransomware also experienced a 52.63% rise. In contrast, LockBit3 faced a 23.68% decline, dropping from 38 to 29 victims. Lynx had the most dramatic surge, with a 900% increase, rising from 2 to 20 victims.
This data highlights the rise of new ransomware groups, which are increasingly dominating the landscape, while more established groups are losing ground.
RansomHub
RansomHub, a newly emerged ransomware group, debuted its leak site in February 2024. It is likely an updated iteration of the older Knight ransomware, rebranded by new actors, who possibly acquired Knight’s source code earlier in 2024. Their sophisticated ransomware targets multiple platforms and leverages vulnerabilities for initial access. Employing advanced obfuscation and attack techniques, RansomHub has swiftly become a significant player in the ransomware threat landscape in a very short period.
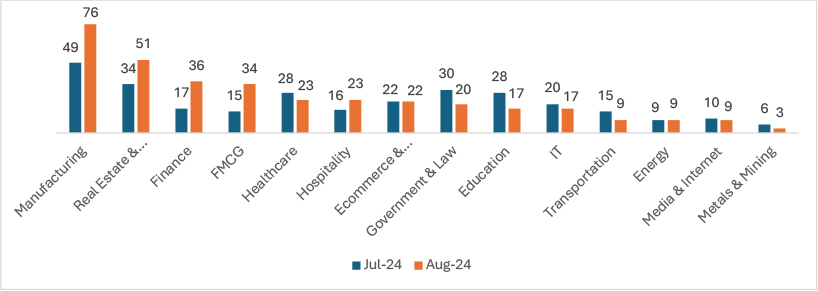
In August 2024, ransomware attacks demonstrated varying trends across industries. The Manufacturing sector experienced a 55.10% increase, while Real Estate and Construction saw a 50% rise. The Finance and FMCG sectors witnessed substantial growths of 111.76% and 126.67%, respectively, highlighting their attractiveness due to high financial stakes and critical supply chains. The Hospitality industry saw a 43.75% increase, likely due to its vulnerability and reliance on customer data. Conversely, Healthcare faced a 17.86% decrease, and Government and Law experienced a 33.33% decline. Both the Education and IT sectors saw a 39.29% reduction in attacks, potentially due to improved awareness and defenses. Transportation attacks dropped by 40%, while the Energy, and Media and Internet sectors remained stable. However, Metals and Mining saw a 50% decline.
These shifts suggest ransomware groups are increasingly targeting sectors with high financial returns.
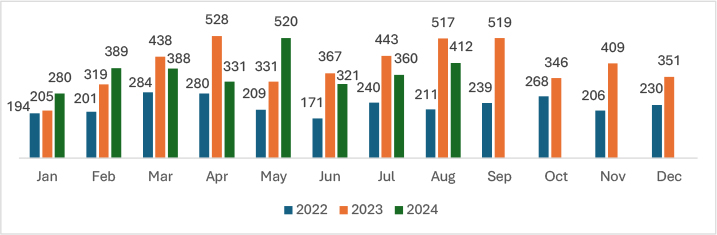
August 2024 shows an increase in ransomware incidents, experiencing a 14.4% rise as compared to July 2024.
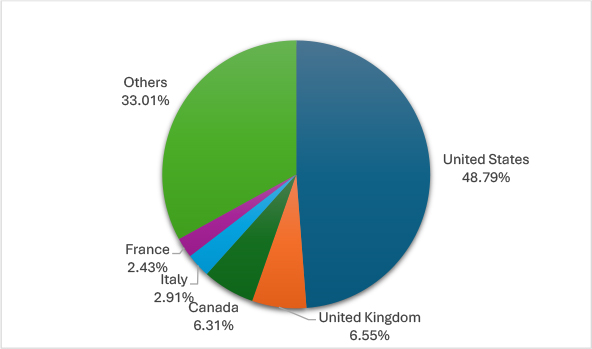
This chart illustrates the geographical distribution of ransomware targets, with the United States being the most impacted at 48.79%, followed by the United Kingdom at 6.55%, Canada at 6.31%, and other countries collectively accounting for 33.01%. France and Italy are also notable targets, with 2.43% and 2.91% respectively. This distribution highlights the concentration of ransomware attacks in certain key regions, developed economies being the key attraction for cybercriminals.
The evolution of Qilin
The Qilin ransomware group has adopted a new tactic, deploying a custom stealer to harvest credentials stored in Google Chrome. Researchers observed this method, starting with Qilin gaining network access via compromised VPN credentials without multi-factor authentication (MFA). After an 18-day dormancy, they used Group Policy Objects (GPOs) to execute a PowerShell script across the domain, stealing Chrome credentials from all machines. The stolen data was sent to Qilin’s command and control (C2) server before being wiped locally.
New Mad Liberator showcasing drastic adaptions
A new ransomware group, The Mad Liberator, targets AnyDesk users by initiating unsolicited connections. Once a connection is approved, the attackers drop a binary that displays a fake Microsoft Windows update screen, distracting the victim while stealing data from OneDrive, network shares, and local storage, using AnyDesk’s File Transfer tool. During this process, the victim’s keyboard is disabled to prevent interference. Despite not encrypting data, the group leaves ransom notes in shared directories and threatens to publish stolen data on their website if their demands are not met.
RansomHub seen employing new malware
RansomHub ransomware operators have been observed using a new malware, EDRKillShifter, to disable Endpoint Detection and Response (EDR) security software in Bring Your Own Vulnerable Driver (BYOVD) attacks. The malware deploys a legitimate but vulnerable driver on targeted devices to escalate privileges and disable security solutions. During a May 2024 attack, the tool attempted to disable protection but failed due to endpoint safeguards. EDRKillShifter can deliver various driver payloads based on an attackers’ needs, and its code suggests it was compiled on a Russian-localized computer.
Hunters hunting with new malware
SharpRhino, a new Remote Access Trojan (RAT) from the ThunderShell malware family, was identified during a recent ransomware incident. It was attributed to the group Hunters International, marking their first reported use of this RAT. SharpRhino, delivered via a typosquatting domain impersonating Angry IP Scanner, establishes persistence and remote access through sophisticated techniques. It uses a C#-based malware that creates directories in `C:\ProgramData\Microsoft` for Command and Control (C2) and maintains persistence. The malware utilizes a PowerShell script to compile and execute obfuscated C# code. Communication with the attacker’s infrastructure involves encrypted data, which was partially decrypted to reveal commands like “register” and “delay.” The analysis confirms SharpRhino’s capability for sophisticated attacks, including the use of fileless malware techniques.
| Sr.No | CVE | CVSS | Vulnerability Name | Associated Threat Actor | Patch |
| 1 | CVE-2024-23897 | 9.8 | Jenkins Command Line Interface (CLI) Path Traversal Vulnerability | RansomExx | YES |
| 2 | CVE-2024-37085 | 7.2 | VMware ESXi Authentication Bypass Vulnerability | BlackByte | YES |
Lynx
Lynx, a double-extortion ransomware actor, has been notably active in recent weeks, claiming multiple companies as victims on their website, However, the group asserts a strict policy against targeting governmental organizations, hospitals, non-profits, and other sectors crucial to society.
Upon compromising an environment, Lynx proceeds to encrypt machines and exfiltrate data. Encrypted files are appended with a .LYNX extension, and a ransom note (README.txt) is placed in various directories.
During the drafting of this report, the group claimed more than 20 victims.
Leaksite of ransomware (Source: Underground form)
Helldown
Helldown, a new but aggressive ransomware group, has quickly gained notoriety in the cybersecurity world. Using sophisticated encryption methods like AES, Salsa20, and RSA, the group maintains high anonymity through the dark web and cryptocurrencies. Helldown is feared for exploiting vulnerabilities to infiltrate networks and disable security measures, targeting IT services, telecommunications, and manufacturing sectors. Their tactic of exfiltrating sensitive data and threatening public release unless a ransom is paid has proven to be highly effective and destructive.

Leaksite of ransomware (Source: Underground form)
$1 million ransom paid
The American Radio Relay League (ARRL) paid a $1 million ransom to obtain a decryptor, following a May ransomware attack. The incident, attributed to the Embargo ransomware gang, resulted in the encryption of ARRL’s systems. The attack, which affected 150 employees, led to the organization taking systems offline to contain the breach. The ransom payment was largely covered by insurance, and ARRL is in the process of restoring affected systems under new infrastructure guidelines and standards.
Radar/Dispossessor dismantled
The FBI recently dismantled the infrastructure of the Radar/Dispossessor ransomware group, which emerged in August 2023. The takedown involved 24 servers and nine criminal domains across the US, UK, and Germany. Dispossessor, which shares tools and methods with the Radar group, has targeted 43 companies worldwide, primarily small-to-mid-sized businesses across various sectors. The group uses a dual-extortion model, encrypting data and threatening exposure if ransoms are not paid. Dispossessor members are believed to be former LockBit affiliates. The FBI’s actions highlight increased global efforts to combat ransomware, as threat actors continue to exploit vulnerabilities, particularly in smaller organizations, and professionalize their operations.
FBI issued warning against BlackSuit ransomware
The FBI and CISA have issued a warning about BlackSuit ransomware, which has demanded up to $500 million in ransoms, with one demand reaching $60 million. BlackSuit, an evolution of Royal ransomware, targets critical infrastructure sectors, including healthcare, and government facilities. It gains access through phishing, RDP, and vulnerable applications, then disables the antivirus software and exfiltrates data before encrypting systems. The group uses various tools for persistence and has escalated pressure tactics, including direct communications with victims. This development occurs alongside the emergence of new ransomware families and the evolution of existing groups using advanced techniques.
Magniber ransomware seen in the wild
A significant surge in Magniber ransomware attacks is currently impacting home users globally, demanding ransoms of up to $5,000 for decryption keys. Magniber, which emerged in 2017 as a successor to Cerber ransomware, has been linked to a variety of distribution methods, including exploiting Windows zero-days, fake updates, and trojanized software cracks. Since July 20, 2024, there has been a notable increase in victims reporting ransomware on forums and identification sites, with nearly 720 submissions recorded. The ransomware encrypts files on affected devices, appending random extensions and leaving a ransom note directing victims to a Tor site for payment. Initial ransom demands are set at $1,000 and escalate if payment is not made within three days.
Based on available public reports, approximately 31% of enterprises are compelled to halt their operations, either temporarily or permanently, in the aftermath of a ransomware onslaught. The ripple effects extend beyond operational disruptions, as detailed by additional metrics:
Impact Assessment
Ransomware poses a significant threat to both organizations and individuals by encrypting vital data and demanding ransom for its release. Beyond ransom payments, these attacks result in financial losses from cybersecurity efforts and recovery, while also causing operational disruptions, loss of customer trust, and emotional stress on victims. Moreover, ransomware incidents can lead to regulatory violations, damaging reputations, undermining consumer confidence, and destabilizing markets. Therefore, addressing ransomware is critical for businesses and governments to safeguard financial stability and preserve public trust.
Victimology
Cybercriminals are increasingly targeting businesses that store valuable data, including personal details, financial information, and intellectual property. Industries such as manufacturing, real estate, healthcare, FMCG, e-commerce, finance, and technology are particularly at risk due to their vast data resources. These criminals focus on countries with strong economies and advanced digital infrastructures to maximize ransom demands. Their strategy is clear: identify vulnerabilities, encrypt critical data, and demand large ransoms, aiming to generate significant profits.
The ransomware landscape in August 2024 reflects a dynamic shift, with emerging groups like Lynx and RansomHub rapidly ascending in prominence, employing sophisticated and aggressive tactics. While some established groups like LockBit3 have seen a decline, the rise of new actors highlights the evolving and increasingly complex nature of ransomware threats. The significant uptick in incidents, particularly in financially critical sectors, highlights the necessity for organizations to enhance their cybersecurity measures and remain vigilant against these adaptive and persistent threats. The ongoing evolution of ransomware tactics demands a proactive approach to defense and a deep understanding of emerging threats to effectively protect against potential breaches.