



A critical vulnerability, identified as CVE-2024-24919, has been discovered in certain End-of-life (EOL) devices that no longer receive updates or patches from Check Point. With a CVSS base score of 8.6, this vulnerability poses a severe threat due to the devices’ increased susceptibility to attacks without ongoing support. The hacktivist group “Ghost Clan Malaysia” has shared the vulnerable IP addresses of Check Point Security Gateways exposed worldwide. Organizations need to promptly mitigate the vulnerability by retiring or replacing compromised devices and applying necessary hotfixes to safeguard data and infrastructure from potential exploitation.
The CVE-2024-24919 vulnerability, with a CVSS score of 8.6, poses significant risks, including critical information disclosure, data theft, system modifications, and service attacks. This vulnerability affects Check Point Security Gateways, allowing remote attackers to read arbitrary files on affected devices. Exploitation can potentially expose sensitive information such as passwords and configuration files. Its inclusion in the Known Exploited Vulnerabilities catalog emphasizes the urgent need to address this issue promptly.
Key Takeaways:
Acknowledgements:
The CYFIRMA Research team acknowledges security researchers who responsibly disclosed this vulnerability.
Vulnerability Type: Information Disclosure
CVE ID: CVE-2024-24919
CVSS Severity Score: 8.6 (High)
Application: Check Point
Impact: Exposure of sensitive information
Severity: High
Affected Versions: Check Point products that have the Remote Access VPN and Mobile Access Software Blades
Patch Available: Yes
CVE-2024-24919 is an information disclosure vulnerability affecting internet-connected Gateways configured with IPSec VPN, remote access VPN, or mobile access software blades. Check Point has confirmed in-the-wild exploitation, particularly targeting devices using local accounts with password-only authentication. This vulnerability allows attackers to access sensitive information such as password hashes without requiring authentication or user interaction. Check Point advises against using local accounts with password-only authentication and recommends applying the available hotfix promptly to mitigate the risk. Impacted products include CloudGuard Network, Quantum Maestro, Quantum Scalable Chassis, Quantum Security Gateways, and Quantum Spark Appliances.
The impact of CVE-2024-24919 is significant due to its potential to expose sensitive information on affected Check Point Security Gateways. This vulnerability allows unauthenticated remote attackers to read arbitrary files, including passwords, SSH keys, and configuration files. Reports indicate active exploitation in the wild, posing a global threat with thousands of vulnerable devices. With a CVSS score of 8.6, the vulnerability is deemed highly severe, capable of granting unauthorized access and compromising network security. Prompt application of recommended mitigations is essential to safeguard systems against potential exploitation and data breaches.
The CVE-2024-24919 vulnerability impacts several versions of Check Point products, including Quantum Security Gateway firmware version R80.20.x, R81, R81.10, R81.2012, CloudGuard Network Security versions R80.40, R81.0/R81.101, and older versions like R77.20, R77.30, R80.10, R80.20, R80.20SP, R80.30, R80.30SP, R80.40, all of which are End-of-Life (EOL). Additionally, Quantum Maestro, Quantum Scalable Chassis, and Quantum Spark Appliances are affected. These versions are vulnerable when configured with IPSec VPN, remote access VPN, or mobile access software blades.
Is there already an exploit tool to attack this vulnerability?
Yes, exploit tools for CVE-2024-24919 are already circulating. These tools underscore the seriousness of the vulnerability and emphasize the critical need for users to promptly address it to prevent potential exploitation and compromise of their systems.
Has this vulnerability already been used in an attack?
Yes, CVE-2024-24919 has already been exploited in the wild. Since April 2024, there have been multiple reports of attackers targeting Check Point Security Gateways, using this vulnerability. Threat actors are exploiting it to gain unauthorized access to sensitive information. There are indications that exploit tools and related services may also be exchanged or sold, heightening the risk of widespread attacks on vulnerable systems.
Are hackers discussing this vulnerability in the Deep/Dark Web?
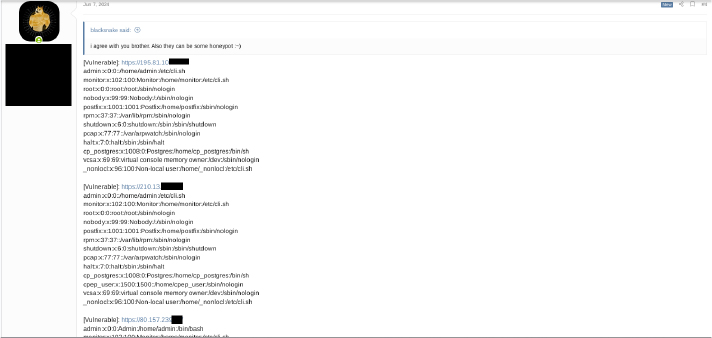
Hackers are actively discussing the CVE-2024-24919 vulnerability on the Deep/Dark Web, with reports of affected device IP addresses being shared in underground forums.
What is the attack complexity level?
The attack complexity level for CVE-2024-24919 in Check Point Security Gateways is assessed as High.
Our analysis identified that more than 16,035 Check Point SVN Foundation instances are publicly accessible and potentially vulnerable to CVE-2024-24919. This critical vulnerability in Check Point Security Gateways is classified as an arbitrary file read vulnerability, meaning that an attacker can read any file on the affected system by exploiting this flaw.
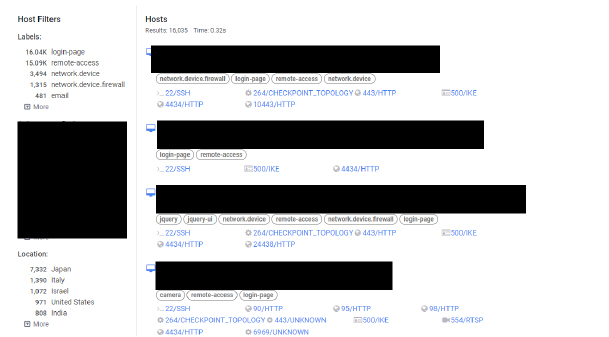
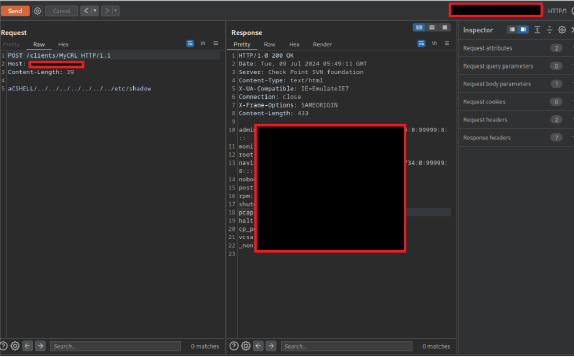
By setting up an in-house lab to simulate the environment, we tested the addresses to assess their vulnerability. Utilizing a public Proof-of-Concept (POC) exploit. The POC involved sending the following HTTP request to exploit the vulnerability:
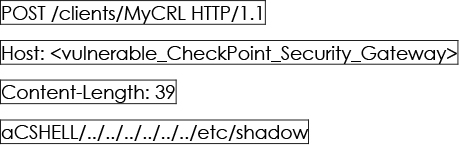
This HTTP POST request exploits a path traversal vulnerability in the Check Point SVN Foundation instance. By sending a request to the /clients/MyCRL endpoint with the payload aCSHELL/../../../../../../etc/shadow, the attacker attempts to access the /etc/passwd file, which typically contains user account information on Unix-based systems. Unauthorized access to this file can lead to critical information disclosure.
The vulnerability arises from improper sanitization and validation of user input, allowing attackers to include path traversal sequences in their requests. This request demonstrates how an attacker can potentially access sensitive files by exploiting the path traversal vulnerability present in the affected Check Point SVN Foundation instances.
To mitigate the CVE-2024-24919 vulnerability, organizations should apply the Check Point hotfix, update and use strong passwords, implement multi-factor authentication (MFA), disable local accounts for VPN access, and use centralized authentication like LDAP. Continuously monitor logs for suspicious activity, ensure all rules have logging enabled, and segment networks to limit attack spread. Restrict administrative access, enforce MFA for VPN, and conduct active security monitoring of endpoints, especially servers. By following these steps, organizations can enhance their security posture and protect against potential exploitation.
Target Geography:
The CVE-2024-24919 vulnerability poses a global threat, impacting a significant number of Check Point Security Gateways across regions, such as the United States, Europe (including Italy and Sweden), Asia (including Japan and India), and the Middle East (including Israel). With the widespread deployment of these gateways, organizations face substantial exploitation risks if vulnerable servers are not promptly addressed. It is crucial for organizations to prioritize proactive measures, such as conducting thorough vulnerability assessments, applying security patches, and enhancing monitoring capabilities to mitigate the risk and protect their data and infrastructure from potential cyber threats.
Target Industry:
The CVE-2024-24919 vulnerability primarily targets industries heavily reliant on Check Point Security Gateways for network security, including financial services, healthcare, government, telecommunications, energy, utilities, and retail. Financial institutions use these gateways to safeguard sensitive data and transactions, while healthcare providers secure patient information to comply with regulations like HIPAA. Government agencies protect classified data, telecom companies secure networks and customer data, and energy firms safeguard critical infrastructure. Retailers use these solutions for customer data protection and secure transactions. Given their widespread adoption, the impact of CVE-2024-24919 can be severe, necessitating prompt mitigation efforts across these sectors.
Target Technology:
The CVE-2024-24919 vulnerability targets Check Point Security Gateways configured with IPSec VPN, Mobile Access Blade, and remote access VPN technologies, impacting various Check Point products like CloudGuard Network, Quantum Maestro, Quantum Scalable Chassis, Quantum Security Gateways, and Quantum Spark appliances. Widely deployed across industries, these technologies are crucial for secure remote access and network connectivity. It is imperative for organizations to promptly address this vulnerability to protect sensitive information and maintain network security. Enhancing external threat landscape management (ETLM) strategies through robust security measures, regular vulnerability assessments, and timely updates are essential to mitigate exploitation risks and safeguard critical data and infrastructure from potential cyber threats.
In an underground forum, there is ongoing discussion surrounding the exploitation of a vulnerability discovered recently. The hacktivist group ”Ghost Clan Malaysia” associated with the threat actor Malaysia, has shared the vulnerable IP addresses of Check Point Security Gateways exposed worldwide. Forum members are considering the sale of exploits related to this vulnerability and analyzing technical details and potential consequences of associated proof-of-concepts (PoCs). This indicates significant attention and concern among malicious actors in the cybercriminal community regarding the seriousness and potential impact of this vulnerability.
In conclusion, CVE-2024-24919 poses a critical information disclosure vulnerability for Check Point Security Gateways, allowing remote attackers to access arbitrary files and potentially expose sensitive information. The active exploitation observed in the wild underscores the urgency of applying the provided hotfix and implementing additional security measures promptly. Discussions within underground forums further emphasize the severity of the threat, with forum members discussing the potential sale of exploits and detailed proof-of-concepts. This highlights the widespread risk of exploitation and reinforces the imperative for users and organizations to prioritize patching and securing their devices to safeguard against malicious attacks and protect critical data and infrastructure.