


In the ever-evolving landscape of cybersecurity threats, a recent storm has been brewing around ConnectWise’s remote support software, ScreenConnect. The vulnerabilities discovered have left more than 96,427 instances of ScreenConnect exposed and potentially vulnerable to malicious attacks. The severity of the situation is underscored by the active exploitation of these vulnerabilities by threat actors, leading to a widespread campaign that threatens organizations across the globe.
ConnectWise’s ScreenConnect has been hit by a duo of critical vulnerabilities, CVE-2024-1709 and CVE-2024-1708, both of which have been exploited in the wild. These vulnerabilities pave the way for threat actors to execute remote code on the affected systems, opening the floodgates for various malicious activities, including the deployment of ransomware. The severity of the vulnerabilities is emphasized by their ease of exploitation, making them an attractive target for cybercriminals.
ScreenConnect vulnerabilities have been identified, resulting in the delivery of various malware types. These include LockBit ransomware (constructed with a leaked builder tool), AsyncRAT payloads, password stealers like Vidar/Redline, deployment of the SimpleHelp remote access client followed by ransomware, Rust infostealer attacks, Cobalt Strike payloads, attempts to deliver the Xworm payload, and a Safe Mode RAT utilizing ScreenConnect for persistence.
As vulnerabilities in ScreenConnect are actively exploited, the threat landscape takes a menacing turn with the emergence of the LockBit ransomware. Exploiting these vulnerabilities provides threat actors with a direct pathway to propagate LockBit ransomware, renowned for its sophisticated tactics and destructive capabilities. Leveraging compromised ScreenConnect instances, malicious actors may efficiently deploy LockBit across networks, potentially causing widespread devastation to businesses and organizations.
A global law enforcement initiative has successfully confiscated numerous darknet domains managed by LockBit, a highly active ransomware group. This operation, named Operation Cronos, represents the latest in a series of impactful digital interventions. Although the complete scope of the effort remains undisclosed at this time, accessing the group’s ‘onion’ website reveals a seizure notice proclaiming, “Law enforcement has taken control of this site.”
The leak of the LockBit builder in September 2022 has further exacerbated the situation, making LockBit Black readily accessible to a broader range of threat actors. This revelation underscores the ongoing challenges in cybersecurity and emphasizes the critical need for proactive measures to address vulnerabilities and counter the relentless evolution of tactics employed by malicious actors.
The scope of this cybersecurity crisis extends globally, with more than 96,427 ScreenConnect instances potentially at risk.
Here are the top 5 affected countries/regions:
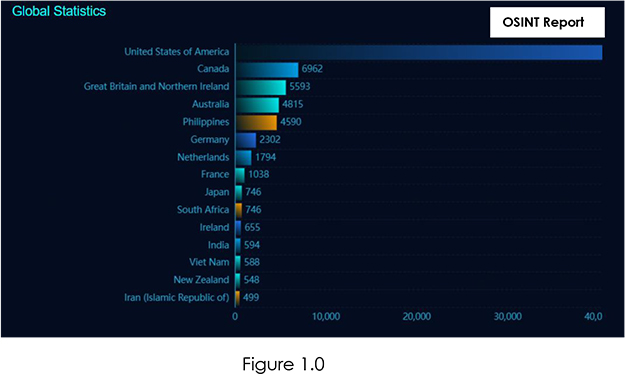
Organizations in these regions are urged to take immediate action to secure their ScreenConnect installations and mitigate the risk of falling victim to the active exploitation of these vulnerabilities.
ConnectWise has officially acknowledged the vulnerabilities and the active exploitation of ScreenConnect instances. Urgent remediation measures have been recommended, including the installation of patches and updates to address the identified vulnerabilities. Additionally, organizations are advised to conduct thorough security assessments and implement necessary hardening measures to further fortify their systems.
Government agencies, including the Cybersecurity and Infrastructure Security Agency (CISA), have issued warnings and directives, urging organizations to update their ScreenConnect servers promptly or take them offline to prevent further exploitation.
1. Assess Version Security:
2. Third-Party Vetting:
3. Post-Patch Surveillance:
4. Presume Client Vulnerability:
5. Client Safeguarding Strategy:
6. Validate On-Premises Deployment:
In conclusion, the ScreenConnect vulnerabilities and their exploitation by threat actors underscore the ever-present need for robust cybersecurity practices. The connection to the LockBit ransomware adds an additional layer of urgency, emphasizing the potential for devastating consequences if swift and decisive action is not taken. Organizations must prioritize security measures, apply patches promptly, and remain vigilant in the face of evolving cyber threats to ensure a resilient and secure digital environment.