

Ransomware activity accelerated sharply from late 2025 into early 2026, with a growing number of campaigns relying on credentials harvested by infostealers as the primary initial access vector. In January 2026 alone, approximately 149 million stolen credentials, largely harvested through infostealer infections, were exposed, significantly increasing the risk of rapid, credential-driven extortion chains. Threat intelligence indicates a clear convergence pattern in which infostealers feed credential data into underground markets and Initial Access Brokers (IABs), enabling ransomware groups to obtain validated enterprise access and deploy ransomware, often within 48 hours of initial compromise.
This trend is reinforced by broader telemetry showing that infostealers harvested an estimated 1.8 billion credentials in the first half of 2025, while a significant portion of ransomware victims were found to have domain credentials present in stealer logs prior to attack. The resulting compression of attack timelines reduces defender response windows and complicates detection efforts, highlighting the need for strong credential hygiene, enhanced endpoint monitoring, and zero-trust security architectures. For organizations operating in remote and hybrid work environments, this convergence represents an elevated risk, as increased reliance on personal and unmanaged devices expands the attack surface for credential theft and downstream ransomware compromise.
Over the past several years, the cybercrime ecosystem has shifted from isolated malware campaigns toward highly interconnected attack chains. Rather than relying on a single malware family to achieve objectives, threat actors increasingly combine multiple tools, services, and actors to maximize speed, scale, and profit. One of the most critical developments in this evolution is the convergence of information-stealing malware (infostealers) and ransomware operations.
Infostealers now play a foundational role in enabling ransomware attacks by harvesting credentials, session tokens, and sensitive system information that can be rapidly monetized or weaponized for follow-on intrusions. This report examines how infostealers act as the initial access enabler within modern ransomware campaigns, creating rapid extortion chains that significantly reduce attacker dwell time while increasing organizational impact.
Information stealers are a class of malware designed to extract sensitive data from infected systems. Common targets include browser-stored credentials, authentication cookies, cryptocurrency wallets, VPN configurations, email clients, and system metadata.
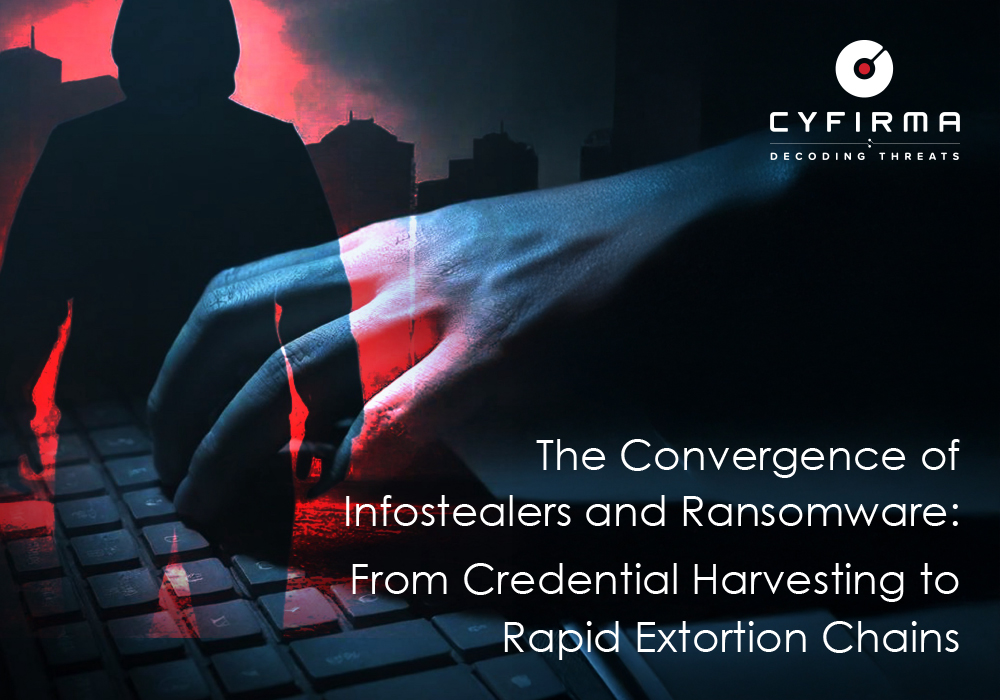
Popular infostealer families observed in recent threat intelligence reporting include RedLine, Raccoon, Vidar, Lumma, and MetaStealer. These tools are commonly distributed through malware-as-a-service (MaaS) models, enabling low-skill actors to conduct large-scale credential harvesting campaigns.
Infostealers are typically delivered via:
These vectors prioritize high infection volume over persistence, reflecting the stealer’s role as a rapid data-exfiltration tool rather than a long-term foothold.
| Family | Key Features | Prevalence | Common Delivery | Ransomware Link Example |
| Lumma | Crypto/2FA focus, C-based MaaS | High | Phishing, fake updates | Sold creds to RaaS groups |
| RedLine | Browser regex, long-standing | High | Malvertising | Fuels IAB-to-ransomware |
| Vidar | Potent harvesting, MFA seed theft | Rising | Supply-chain | Paired with encryption |
| StealC | Weekly updates, aggressive | High | ClickFix lures | Rapid credential resale |
Once executed, infostealers quickly enumerate the host system to collect credentials and other valuable artifacts. Of particular importance to ransomware operations are:
The use of stolen session cookies allows attackers to bypass multi-factor authentication (MFA), significantly increasing the value of infostealer logs in underground markets.
Stolen data harvested by infostealers is rarely used directly by the original operator. Instead, it is sold through underground forums, Telegram channels, and dedicated log marketplaces. This ecosystem has given rise to Initial Access Brokers (IABs), specialized actors who focus exclusively on selling access to compromised environments.
IABs categorize access based on factors such as:
This commoditization of access allows ransomware groups to rapidly acquire entry points without conducting their own initial compromise activities.
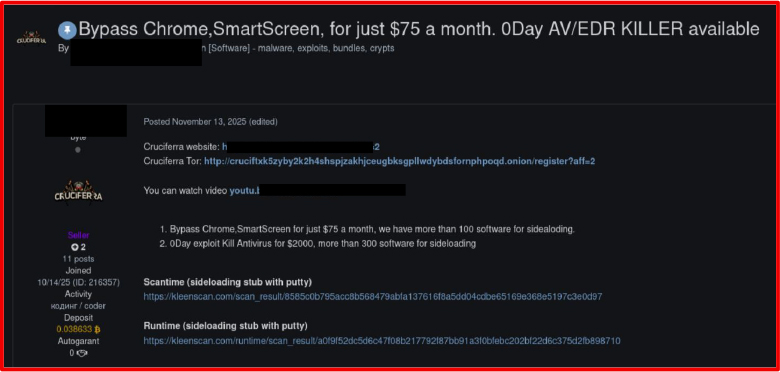
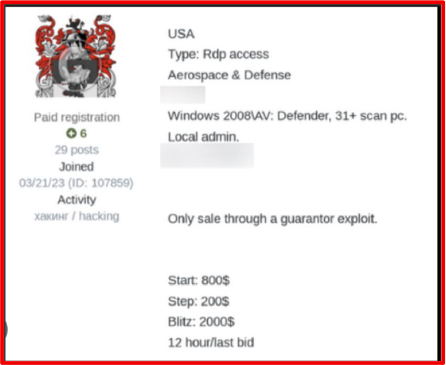
Example of underground forum advertisement for AV/EDR bypass and sideloading tools
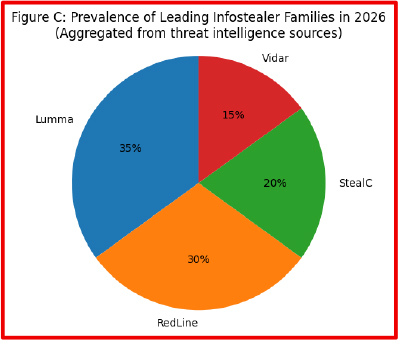
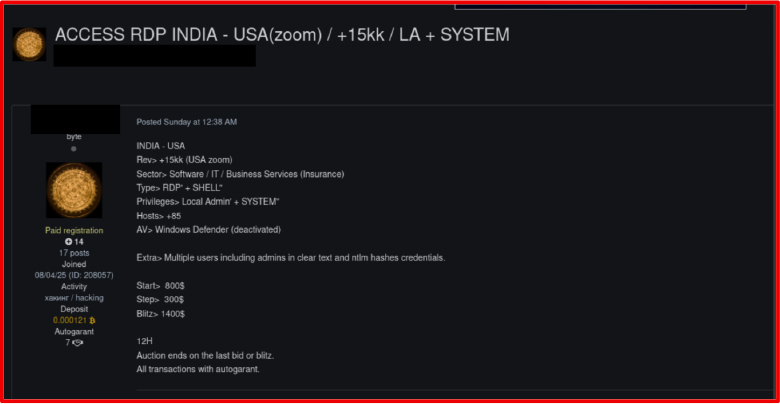
Threat intelligence monitoring of underground forums and Telegram-based Initial Access Broker (IAB) channels during late 2025 revealed a sustained increase in listings derived directly from infostealer logs. Advertisements frequently referenced access to corporate VPNs, Microsoft 365 tenants, and domain-level credentials, often categorized by organization size, geographic region, and security posture.
Pricing analysis across multiple marketplaces indicated that stealer-derived access typically ranged between USD 500 and USD 5,000, depending on privilege level, credential freshness, and industry sector. Access associated with healthcare, manufacturing, and financial services environments consistently commanded premium pricing. Many listings explicitly referenced “infostealer logs,” “browser sessions,” or “cookie-based access,” confirming the direct operational pipeline between credential harvesting operations, access brokers, and ransomware affiliates.
Modern ransomware operations increasingly rely on stolen credentials rather than exploit-driven intrusions, using data harvested by infostealers to bypass perimeter defenses and enable rapid lateral movement and privilege escalation through legitimate authentication.
A common attack chain now links infostealer infections to credential exfiltration, sale through Initial Access Brokers (IABs), and subsequent ransomware deployment by affiliates operating within a fragmented ransomware-as-a-service ecosystem.
In many cases, ransomware execution occurs in less than 48 hours after credentials appear in underground markets, significantly reducing detection and response windows. Ransomware activity rose by approximately 60 percent year over year by late 2025, with valid account abuse consistently identified as a leading initial access vector. Looking ahead to 2026, continued RaaS fragmentation, AI-assisted targeting, and widespread double and triple extortion models highlight a strategic shift toward identity abuse as the primary driver of ransomware risk, resulting in increasingly rapid extortion chains.
While individual campaigns vary, recurring patterns have been observed across multiple ransomware incidents:
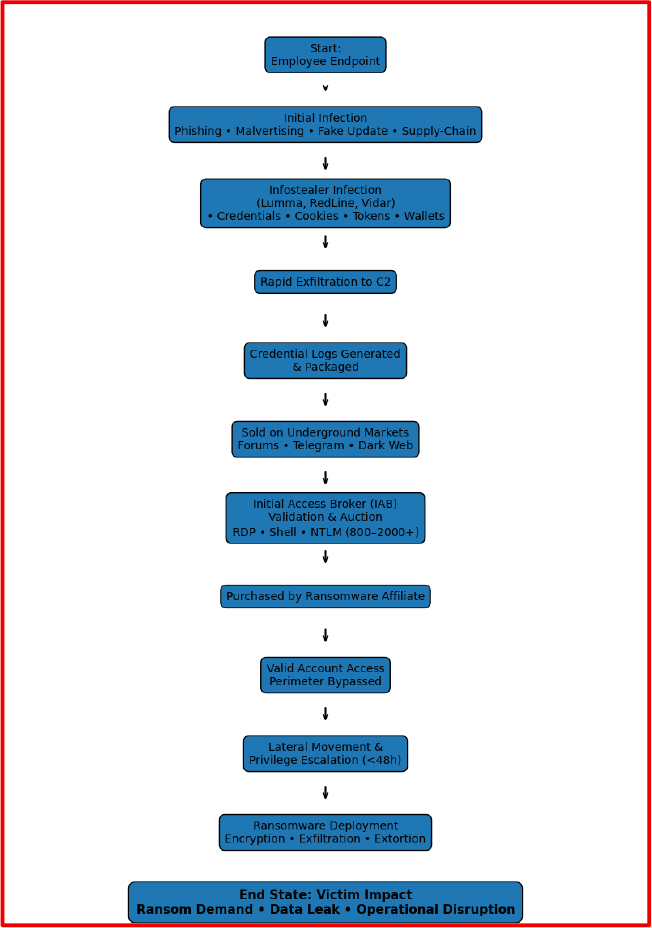
These patterns highlight the operational efficiency gained through stealer–ransomware convergence.
| ATT&CK Tactic | Technique ID | Technique Name |
| Initial Access | T1566 | Phishing |
| T1189 | Drive-by Compromise | |
| Execution | T1059 | Command and Scripting Interpreter |
| Credential Access | T1555 | Credentials from Password Stores |
| T1539 | Steal Web Session Cookie | |
| T1003 | OS Credential Dumping | |
| Discovery | T1082 | System Information Discovery |
| T1016 | Network Service Discovery | |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| T1562 | Impair Defenses | |
| Lateral Movement | T1021 | Remote Services |
| Persistence | T1078 | Valid Accounts |
| Privilege Escalation | T1078 | Valid Accounts |
| Command and Control | T1071 | Application Layer Protocol |
| T1102 | Web Service | |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| T1567 | Exfiltration Over Web Service | |
| Impact | T1486 | Data Encrypted for Impact |
| T1657 | Data Manipulation | |
| T1499 | Endpoint Denial of Service |
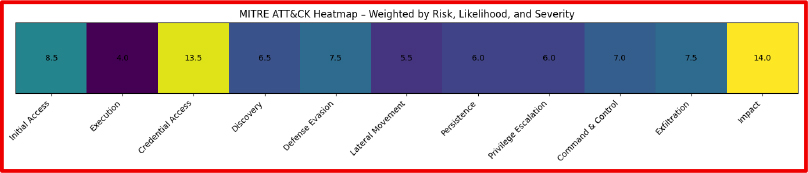
The resulting heatmap highlights tactical risk concentration, not merely technique volume.
Tactics such as Credential Access and Impact exhibit the highest weighted scores, indicating that while they may not contain the largest number of techniques, they represent the greatest overall risk exposure within the attack lifecycle.
This concentration reflects the central role of credential theft in enabling access brokerage and the strategic importance of impact-oriented techniques such as encryption, manipulation, and denial of service in ransomware monetization and extortion operations.
In contrast, tactics like Execution and Lateral Movement, while operationally necessary, demonstrate lower cumulative risk weighting, suggesting they function primarily as enabling stages rather than primary drivers of attacker value.
From a cyber threat intelligence perspective, early detection of infostealer activity provides a critical opportunity to disrupt ransomware attacks before they materialize. Key CTI indicators include:
Integrating stealer intelligence into defensive workflows can significantly reduce ransomware risk.
The convergence of infostealers and ransomware is expected to intensify as attackers continue to optimize for speed and profit. Increased automation, improved credential validation techniques, and deeper collaboration between cybercriminal groups are likely to further compress attack timelines.
Organizations that fail to monitor early-stage threats such as infostealers will remain vulnerable to downstream ransomware impacts.
Infostealers have evolved from low-level credential theft tools into critical enablers of modern ransomware operations. Their integration into rapid extortion chains represents a fundamental shift in the cybercrime ecosystem. Understanding and monitoring this convergence is essential for effective cyber threat intelligence and proactive defense strategies.
Prioritize Early Detection of Infostealer Activity
Organizations should treat infostealer infections as high-severity precursor events to ransomware. Monitoring for known infostealer command-and-control infrastructure, suspicious browser data access, and abnormal credential harvesting behaviour can enable early intervention before access is sold or reused by ransomware affiliates.
Monitor Underground Markets for Credential Exposure
Cyber threat intelligence programs should actively monitor stealer log marketplaces and Initial Access Broker channels for references to corporate domains, email addresses, VPN access, or cloud environments. Early identification of exposed credentials allows organizations to invalidate access before ransomware deployment occurs.
Strengthen Credential Hygiene and Identity Controls
Given the shift toward credential-driven intrusions, organizations should enforce strong password hygiene, frequent credential rotation, and phishing-resistant multi-factor authentication. Session management controls and conditional access policies should be used to limit the abuse of stolen cookies and tokens.
Enhance Endpoint Visibility on User Workstations
Infostealers primarily target end-user systems rather than servers. Improving visibility into endpoint behaviours particularly on remote and hybrid user devices can help detect malicious installers, unauthorized browser modifications, and abnormal process execution associated with stealer activity.
Treat Valid Account Abuse as a Primary Ransomware Indicator
Security operations teams should elevate the detection of anomalous authentication events, such as unusual login locations, a typical access times, or sudden privilege escalation using valid credentials. These signals often precede ransomware deployment in credential-based attacks.
Integrate CTI with Incident Response and SOC Workflows
Threat intelligence related to infostealers, IAB activity, and credential exposure should be directly integrated into SOC and incident response processes. Automated enrichment, alerting, and playbooks can reduce response time during the narrow window between initial access and ransomware execution.
Prepare for Multi-Stage and Multi-Extortion Scenarios
Organizations should assume that ransomware incidents will involve encryption, data exfiltration, and potential denial-of-service activity. Incident response plans should be updated to address multi-stage extortion scenarios and coordinated attacker actions.
Shift Defensive Focus from Malware to Identity Abuse
As attackers increasingly prioritize credential theft over exploitation, defensive strategies must evolve accordingly. Identity protection, access monitoring, and credential exposure intelligence should be treated as core ransomware defense measures rather than secondary controls.