Published On : 2024-03-22
EXECUTIVE SUMMARY
The Europe Threat Landscape Report provides a comprehensive overview of the evolving cybersecurity landscape in the region. In recent years, Europe has witnessed a significant increase in cyber threats, driven by factors such as rapid digitalization, increased internet penetration, and geopolitical tensions. This report aims to provide key insights into the current state of cyber threats, and emerging trends.
THE GEOGRAPHICAL SCOPE OF THIS REPORT
United Kingdom, Germany
YET TO BE UPDATED
Belgium, Czech Republic, Finland, France, Germany, Hungary, Ireland, Luxembourg, Spain.
UPDATED METHODOLOGY
This is a running report. Our research team will update this report on an ongoing basis to keep the reader updated on the evolving cyber threat landscape of the region.
THREAT LANDSCAPE TODAY
01 MOVEMENT FROM DIGITAL TO KINETIC TARGETS
Trend: Ransomware attacks on critical infrastructure
Motives: Disruption/Geopolitical/Extortion
02 DATA EXFILTRATION FROM IOT DEVICES
Trend: Spyware, malware and plug-ins to collect data.
Motive: Reputation impact, disruption, extortion
03 EXPLOITATION OF LEGACY SYSTEM
Trend: Brute force attacks, credential reuse and data exfiltration via malware
Motive: Operational disruption, espionage, IP exfiltration
04 CROSS-ENVIRONMENT ATTACK
Trend: social engineering/phishing. jump server Exploits, remote access tool compromise
Motive: Operational disruption, espionage, IP exfiltration
05 USE OF BOTNETS, AI, DEEPFAKE
Trend: Device scanning, firmware, phishing/malware download
Motives: Disruption, data harvesting, remote attacks (DDOS)
06 SUPPLY CHAIN OF INFRASTRUCTURE, UTILITY COMPANIES REMAIN AT RISK
Trend: Multi-behavioral malware (IT/OT, different operating system)
Target: CII trade secrets documents containing proprietary processes
EUROPE KEY FINDINGS
INCREASED SOPHISTICATION OF CYBER ATTACKS
The region has witnessed a rise in the sophistication of cyber attacks, with threat actors employing advanced techniques to compromise systems and networks.
TARGETED THREATS AGAINST CRITICAL INFRASTRUCTURE
The region has witnessed a rise in the sophistication of cyber attacks, with threat actors employing advanced techniques to compromise systems and networks.
RISE IN RANSOMWARE INCIDENTS
Ransomware attacks have surged in frequency and severity, posing significant challenges to businesses and government entities. The attackers often demand cryptocurrency payments for the release of compromised data.
NATION-STATE THREATS AND CYBER ESPIONAGE
Evidence suggests an increase in nation-state-sponsored cyber activities, including cyber espionage and information warfare. This poses significant geopolitical and security concerns for the region.
SUPPLY CHAIN VULNERABILITIES
The report identifies vulnerabilities in the regional supply chain, with cybercriminals exploiting weaknesses in third-party relationships to gain unauthorized access to targeted organizations.

UNITED KINGDOM
TRENDS IN THE UNITED KINGDOM THREAT LANDSCAPE
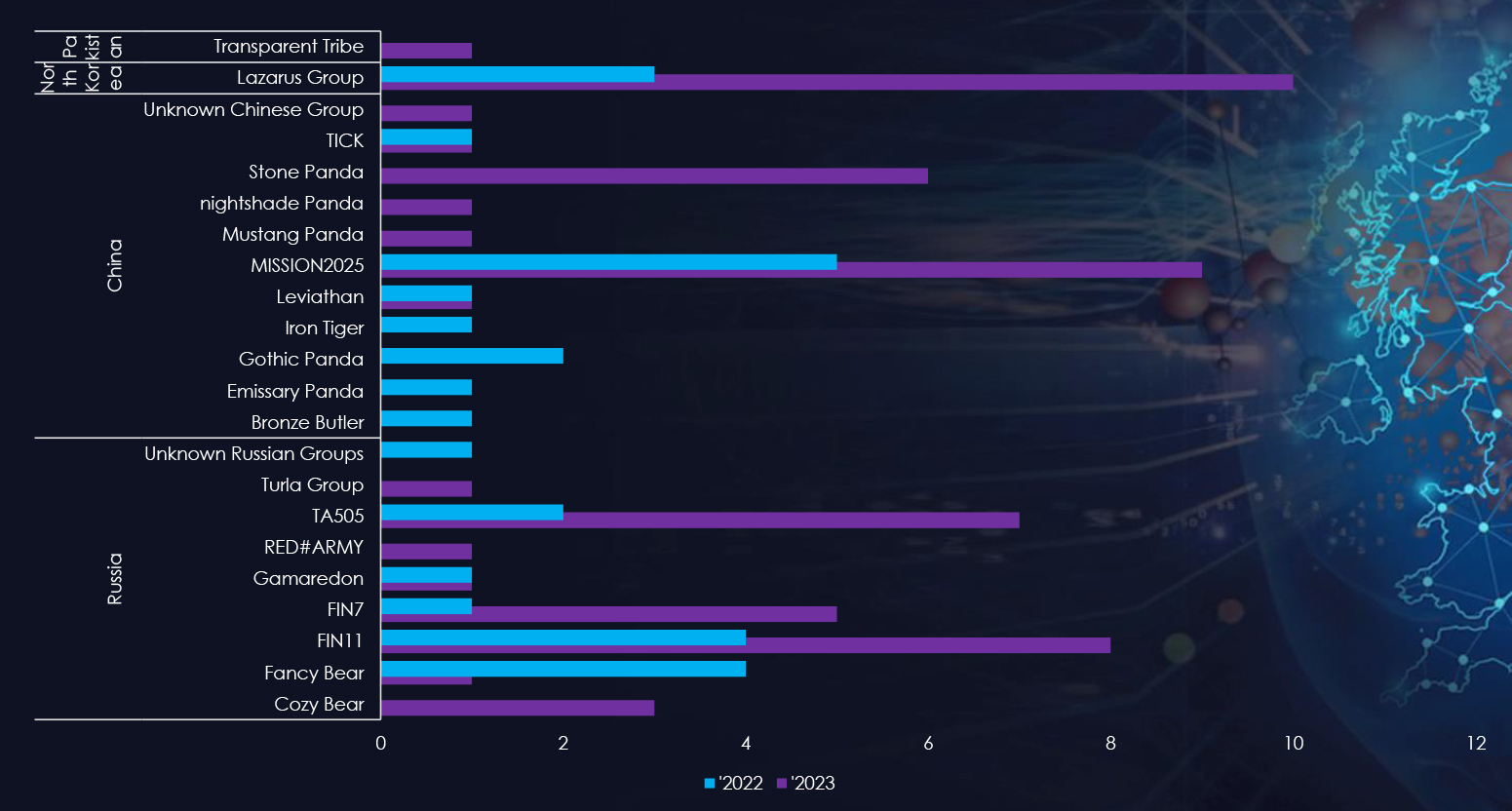
- Nation-State Threats: The UK remains a prime target for state-sponsored cyber espionage and sabotage activities. Nation-state actors, particularly from Russia, China, Iran, and North Korea, continue to conduct sophisticated cyber operations targeting government institutions, defense contractors, and critical infrastructure sectors such as energy, finance, and telecommunications.
- Ransomware Attacks: Ransomware attacks against UK organizations have surged in frequency and sophistication. Cybercriminal groups deploy ransomware to encrypt critical data and demand extortionate payments for decryption keys. These attacks cripple operations, disrupt services, and cause significant financial losses to businesses across various sectors, including healthcare, education, and finance.
- Supply Chain Vulnerabilities: Supply chain attacks pose a significant threat to the UK’s cybersecurity posture. Adversaries exploit weaknesses in the supply chain to infiltrate trusted vendors and compromise their products or services. This tactic allows threat actors to gain unauthorized access to target organizations, exfiltrate sensitive data, or deploy malicious payloads for espionage or sabotage.
- Phishing and Social Engineering: Phishing attacks remain a prevalent method for compromising UK organizations and individuals. Threat actors employ sophisticated social engineering tactics to deceive users into divulging sensitive information, clicking on malicious links, or downloading malware-infected attachments. With the proliferation of remote work and reliance on digital communication channels, the risk of falling victim to phishing scams has increased significantly.
- Emerging Technologies: Adopting emerging technologies such as the Internet of Things (IoT), artificial intelligence (AI), and cloud computing introduces new cybersecurity challenges. Inadequate security measures and vulnerabilities inherent in these technologies expose UK organizations to potential exploitation by malicious actors. Securing these evolving technological landscapes requires proactive risk management and robust cybersecurity controls.
WHAT ATTRACTS THREAT ACTORS TO THE UNITED KINGDOM?
- Economic Importance: The UK is one of the world’s largest economies, with a significant presence in finance, technology, and other industries. This economic importance makes it an attractive target for cybercriminals seeking financial gains through activities such as data theft, fraud, or ransomware attacks targeting businesses.
- Advanced Technological Infrastructure: The UK boasts advanced technological infrastructure, including widespread internet connectivity, digital services, and critical infrastructure systems. This presents numerous opportunities for cyber-attacks aimed at disrupting services, stealing valuable data, or compromising infrastructure for political or financial motives.
- Political Influence: As a major player on the global stage, the UK’s political influence and involvement in international affairs can make it a target for state-sponsored cyber espionage or cyber warfare activities. Threat actors may seek to gain access to sensitive government information, disrupt diplomatic relations, or influence political events.
- Regulatory Environment: The UK has implemented various cybersecurity regulations and standards to protect its critical infrastructure, sensitive data, and digital assets. However, compliance with these regulations can be challenging for organizations, leaving them vulnerable to cyber-attacks. Threat actors may exploit weaknesses in regulatory compliance to launch targeted attacks.
- Global Connectivity: The UK’s interconnectedness with the rest of the world through trade, travel, and digital communications means that cyber threats originating from other regions can easily impact the country. Threat actors operating from abroad may target UK-based entities as part of larger cybercrime or cyber warfare campaigns.
- Data-Rich Environment: The UK is home to a vast amount of valuable data, including personal, financial, and corporate information. Cybercriminals may target organizations or individuals in the UK to steal this data for various purposes, such as identity theft, financial fraud, or corporate espionage.
- Geopolitical Tensions: Geopolitical tensions and conflicts can spill over into cyberspace, leading to cyber-attacks aimed at disrupting or destabilizing adversaries. The UK’s involvement in international conflicts or disputes may increase its susceptibility to cyber threats from state-sponsored actors or hacktivist groups seeking to retaliate or exert influence.
HIGH-PROFILE CYBER-ATTACKS AND BREACHES
- The cyber landscape in the United Kingdom has witnessed a series of prominent incidents, each leaving significant impacts on various sectors. One notable case involved a ransomware attack on Yum! brands in January 2023, compelling the closure of 300 KFC, Pizza Hut, Taco Bell, and The Habit Burger Grill restaurants across the UK. This event triggered class action lawsuits in the United States, with allegations of privacy violations raised by current and former employees affected by the breach.
- In another instance, the LockBit ransomware group targeted ION Group, a UK-based software company specializing in financial services, leading to disruptions in trading, investment management, and market analytics. Similarly, JD Sports fell victim to a data breach in the same month, compromising the personal information of ten million customers.
- Royal Mail, the primary mail delivery service in the UK, faced operational disruptions in February 2023 due to a ransomware attack. The incident not only impacted the company but also caused inconvenience to its customers.
- The UK Electoral Commission disclosed a significant data breach in August 2023, affecting individuals who registered to vote between 2014 and 2022. This breach, detected ten months earlier, raised concerns about delayed public notification and involved unauthorized access to government servers containing sensitive electoral information.
- Subsequently, the British Library encountered a technology outage in October 2023, affecting online systems, website access, and onsite services. In November 2023, a cyberattack on CTS, a prominent managed service provider for legal firms, led to widespread outages affecting law firms and home buyers across the country.
- The University of Manchester faced a ransomware attack, prompting a threat to leak student data following non-payment of extortion demands. This incident utilized a ‘triple extortion’ tactic, highlighting the evolving strategies of cybercriminals.
- Samsung Electronics notified customers of a data breach affecting those who made purchases from its UK online store between July 2019 and June 2020. The breach, discovered in November 2023, exploited vulnerabilities in a third-party application.
- Lastly, WH Smith, a major UK retailer, experienced a data breach compromising information belonging to current and former employees. With a significant presence across the UK, this breach underscored the vulnerability of large organizations to cyber threats, emphasizing the need for robust cybersecurity measures.
GEO-POLITICAL RISK FACTORS
- Historical Significance: The UK’s historical role in global affairs and its status as a major European power make it a target for cyber threats seeking to exploit its political influence and economic significance.
- Special Relationship with the US: The UK’s close alliance with the United States exposes it to cyber threats targeting shared interests and joint initiatives, potentially leading to coordinated attacks or espionage activities.
- Geopolitical Tensions: Tensions with Russia, China, and Iran contribute to cyber threats, as these nations may conduct cyber operations against the UK to exert influence, gather intelligence, or disrupt critical infrastructure.
- NATO Membership and Defense Commitments: As a core member of NATO, the UK’s cybersecurity posture is intertwined with collective defense efforts, requiring robust cyber defenses to deter and mitigate potential attacks from adversaries.
- Technological Advancements and Vulnerabilities: The UK’s advanced technological infrastructure presents opportunities for innovation but also vulnerabilities to cyber threats, including sophisticated cyberattacks targeting critical systems and sensitive data.
- Global Connectivity and Economic Impact: The UK’s global connectivity and role as a financial hub increase its exposure to cyber threats, with attacks aiming to disrupt economic activities, steal financial data, or undermine public confidence in financial institutions.
- Critical Infrastructure Protection: Safeguarding critical infrastructure, such as energy, transportation, and healthcare systems, is paramount to national security, as cyber threats targeting these sectors can have far-reaching consequences on public safety and essential services.
- International Collaboration and Intelligence Sharing: Participation in intelligence alliances like The Five Eyes enables the UK to enhance its cybersecurity capabilities through collaboration, information sharing, and joint efforts to combat cyber threats on a global scale.
- Cyber Resilience and Preparedness: Building cyber resilience and preparedness is essential for mitigating cyber threats and minimizing the impact of potential cyberattacks, requiring investment in cybersecurity measures, training, and incident response capabilities.
TRENDS FROM THE DARK WEB
We observed 38 campaigns targeting various industries in the United Kingdom during 2023. Chinese, Russian, and North Korean state-sponsored threat actors are behind most of these campaigns.
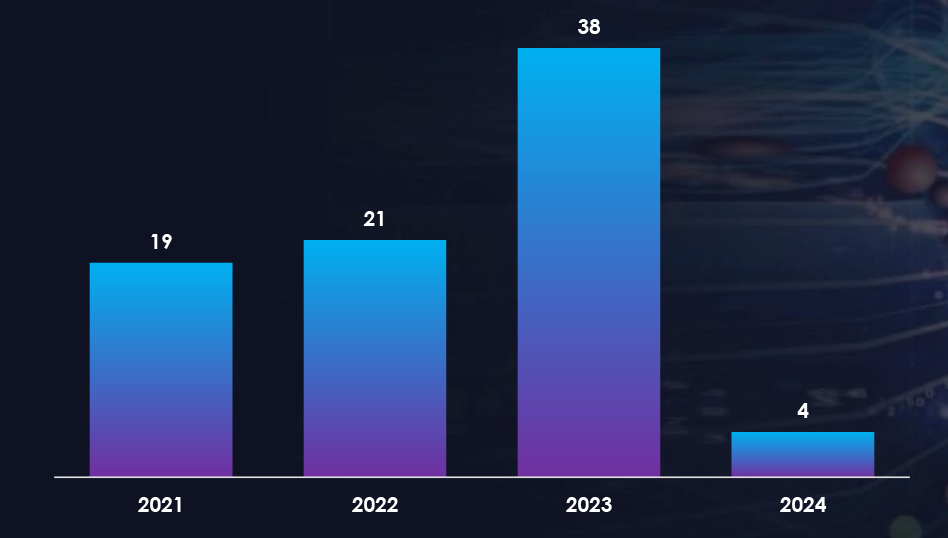
The number of observed campaigns significantly increased in 2023 as compared to the last two years, indicating threat actors’ interest in economic and geopolitical factors, especially due to the United Kingdom’s stand on the Russia-Ukraine war and China-Taiwan conflict.
THREAT ACTOR CAMPAIGNS, YEAR-ON-YEAR COMPARISON
TARGETED INDUSTRIES AND TECHNOLOGY
In the observed campaigns, threat actors have targeted diverse industries within the critical infrastructure, which is having a significant economic and social impact on the threat landscape.
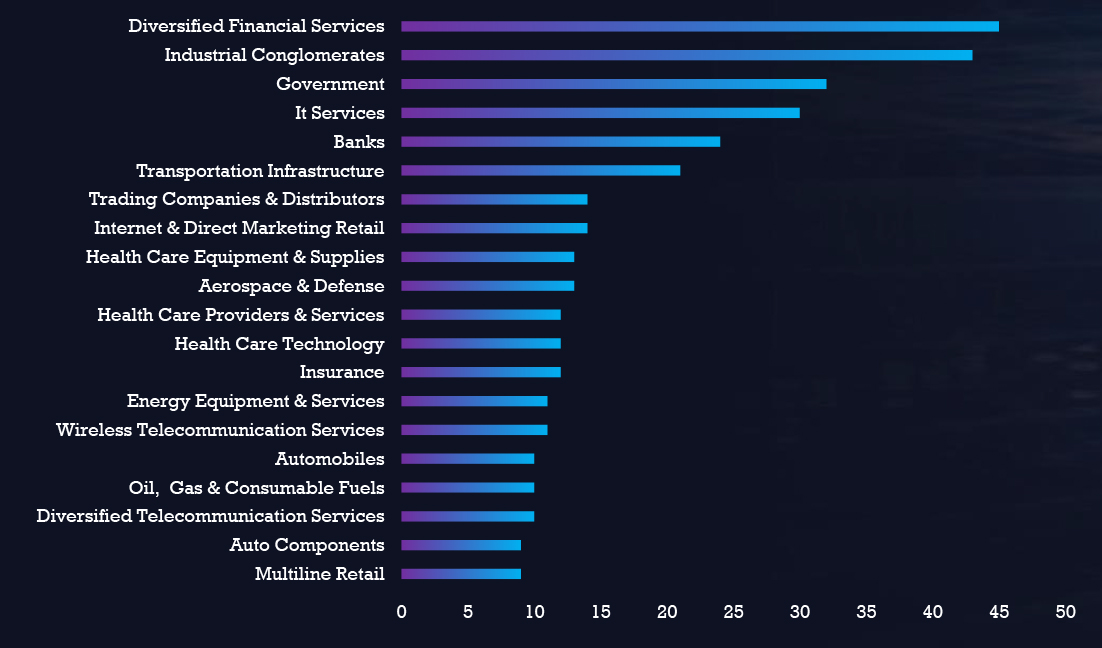
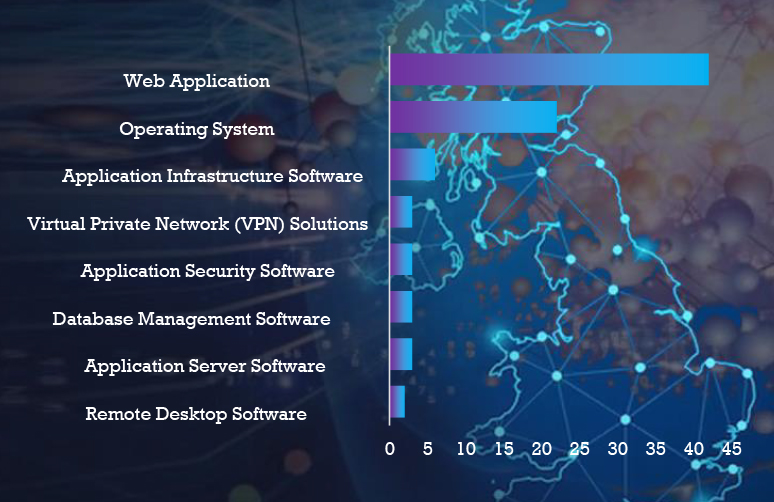
In the observed campaigns, threat actors focused on attacking web applications, operating systems, and various other applications.
THREAT ACTORS TO WATCH

DATA LEAKS
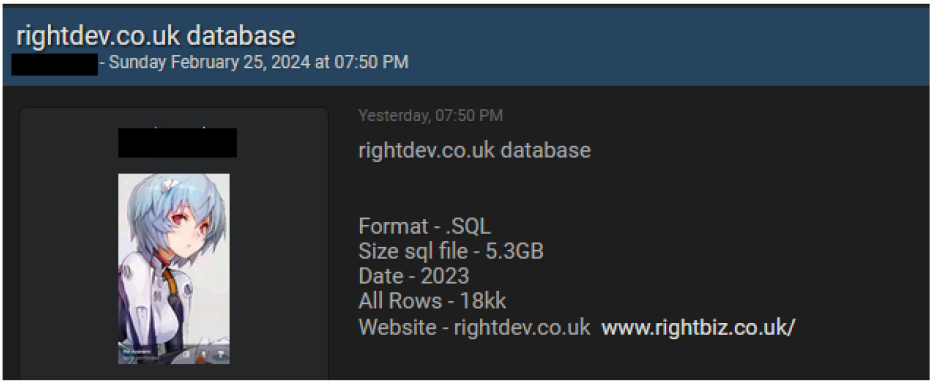
CYFIRMA Research team observed a data leak related to Rightbiz (rightdev[.]co[.]uk); a marketplace spanning over 50+ sectors, boasting over £10 billion worth of businesses for sale, trusted by thousands of people for searching, understanding, and investing in the businesses nationwide. Threat actor leaked the SQL database (5.3 GB) of Rightbiz in the leak forum.
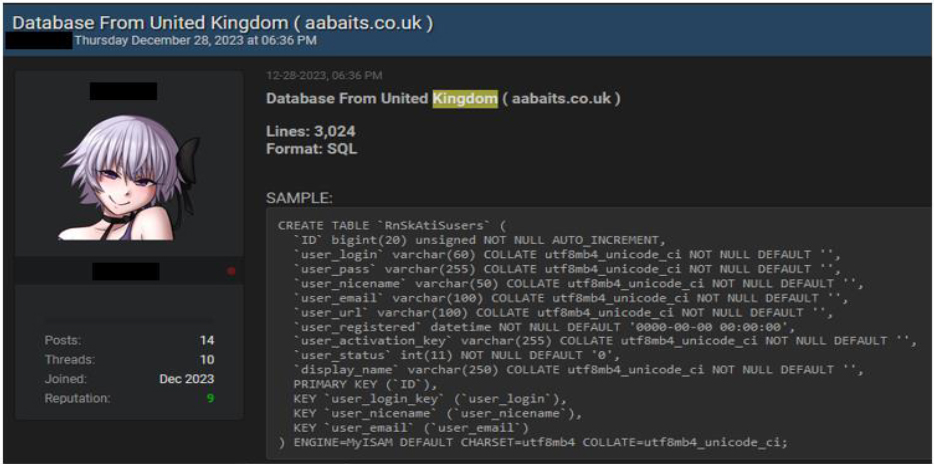
CYFIRMA Research team observed a data leak related to AA Baits (aabaits[.]co[.]uk, involved in retail business. Threat actor leaked the SQL database (3,024 lines) of AA Baits in the leak forum which contains confidential details of users.
CYFIRMA Research team observed a data leak related to SoftwareBase (softwarebase[.]uk). SoftwareBase is a global software technology company based in London and serving buyers across the United Kingdom, Europe, and worldwide. The threat actor leaked the SQL database (303 MB) and source code of the full site (7 GB) in the leak forum.
PHISHING
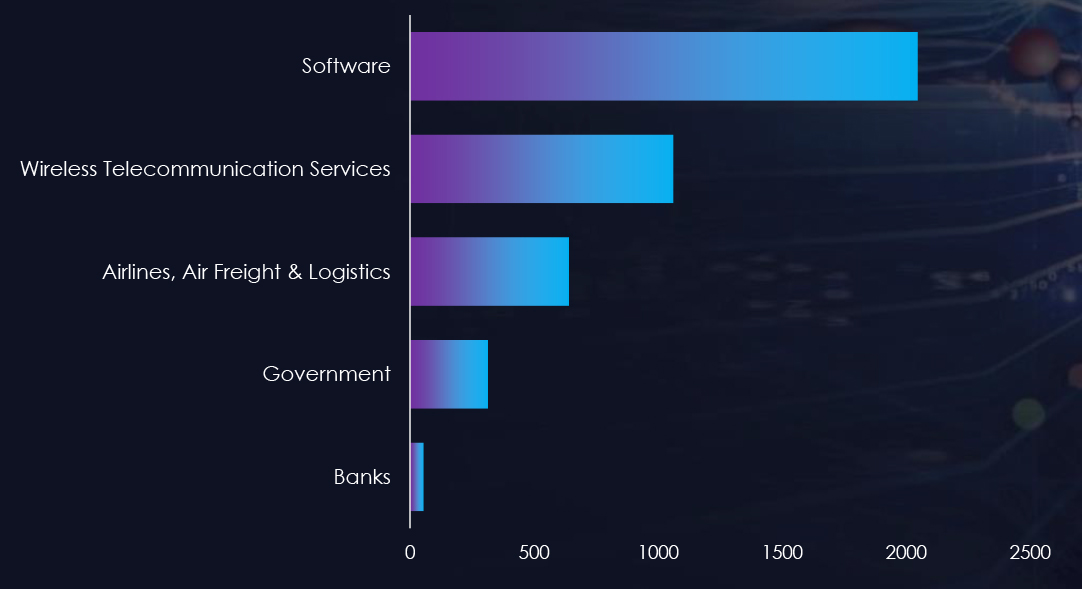
From 14th February 2023 to 14th February 2024, CYFIRMA’s telemetry recorded 8,959 phishing campaigns targeting the United Kingdom out of a total of 887,968 campaigns. Most impersonated themes are associated with Software, Wireless Telecommunication Services, Airlines, Air freight, Logistics, Government, and Banking sectors.
Most Targeted Industries in Phishing Attacks
RANSOMWARE
The United Kingdom, like many developed nations, is susceptible to ransomware attacks due to its strong economy, advanced digital infrastructure, and global connectivity. The attractiveness of potentially high ransom payments, coupled with the interconnectivity of critical systems, makes it a target for cybercriminals. Additionally, if cybersecurity measures are not consistently robust, vulnerabilities may be exploited, leading to an increased risk of successful attacks on both the public and private sectors. While specific motives can vary, the combination of economic factors and digital prominence contributes to the likelihood of the United Kingdom being targeted by ransomware attacks.
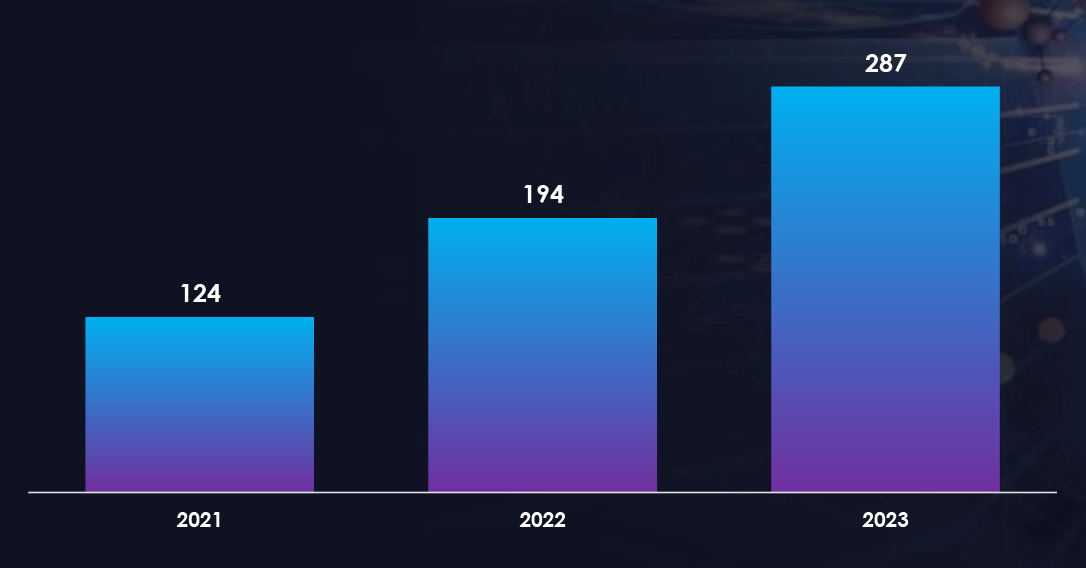
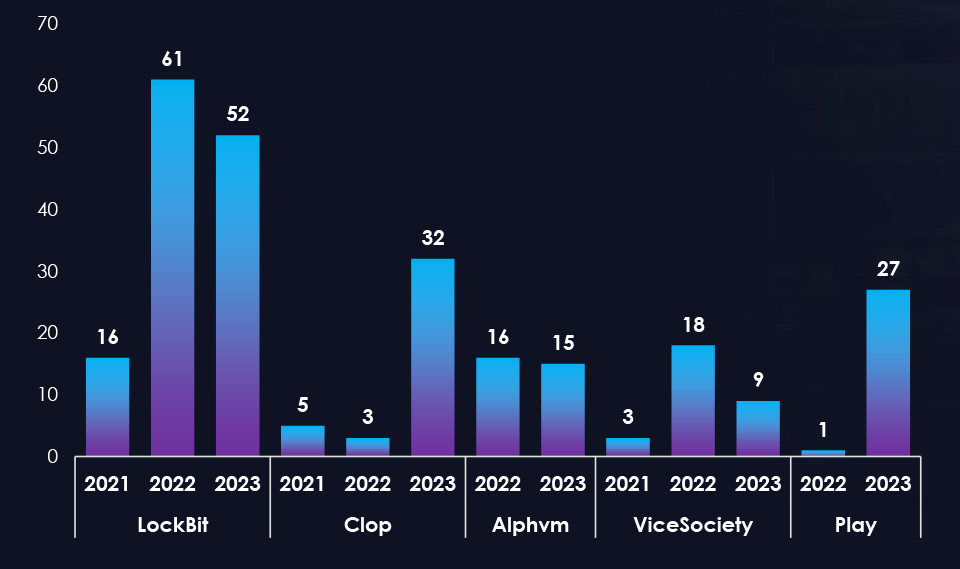
We observed a significant increase in Ransomware victims from the United Kingdom, compared to earlier years. Notably, this threat landscape is influenced by formidable ransomware groups, including LockBit, BlackCat (Alphvm), Cl0p, ViceSociety, and Play, who feature prominently on the list of perpetrators targeting the United Kingdom companies.
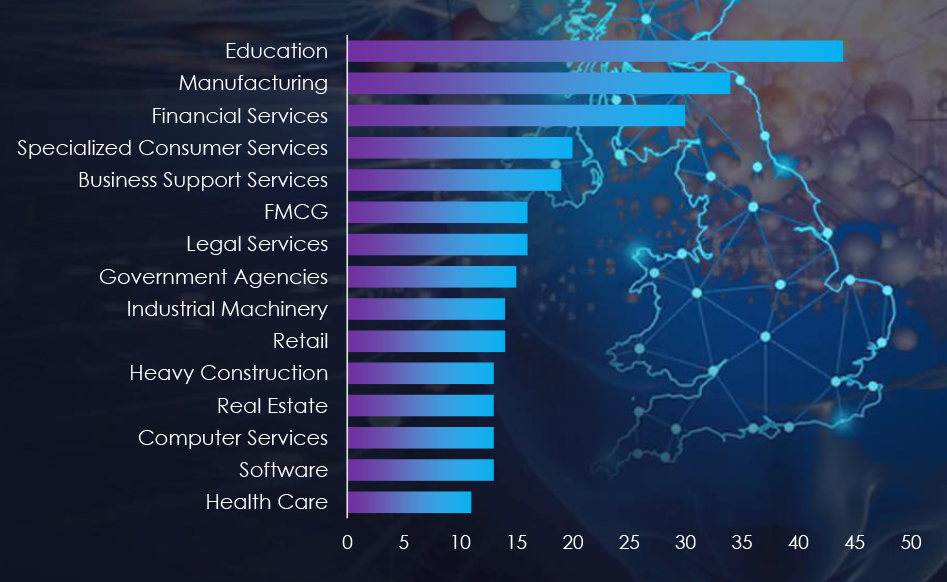
Education, manufacturing, financial services, FMCG, and Government agencies are the top targets of ransomware actors in the United Kingdom.
ASSET EXPOSURES & VULNERABILITIES
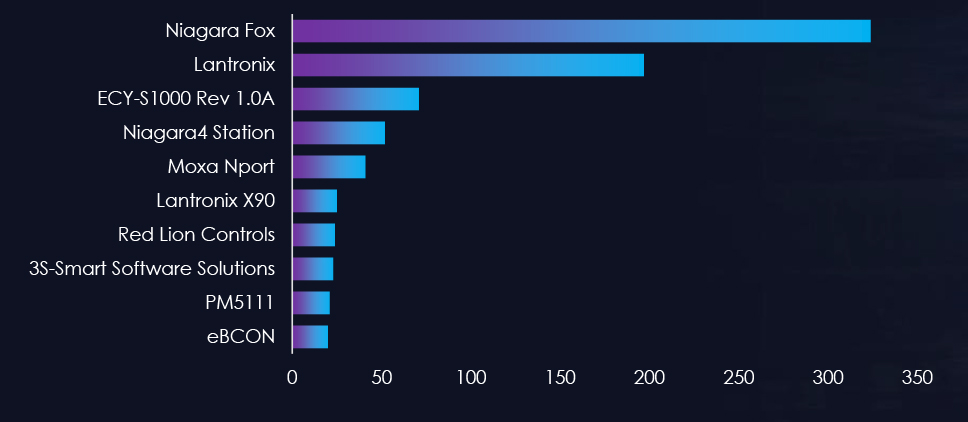
In our OSINT research, we found around 1485 Industrial Control Systems exposed to the Internet, owned by organizations in the United Kingdom, potentially allowing an attacker to access them.
Exposed Industrial Control Systems: Top 10 Products
Most Exploited Vulnerabilities in the United Kingdom – Last 3 months
HACKTIVIST
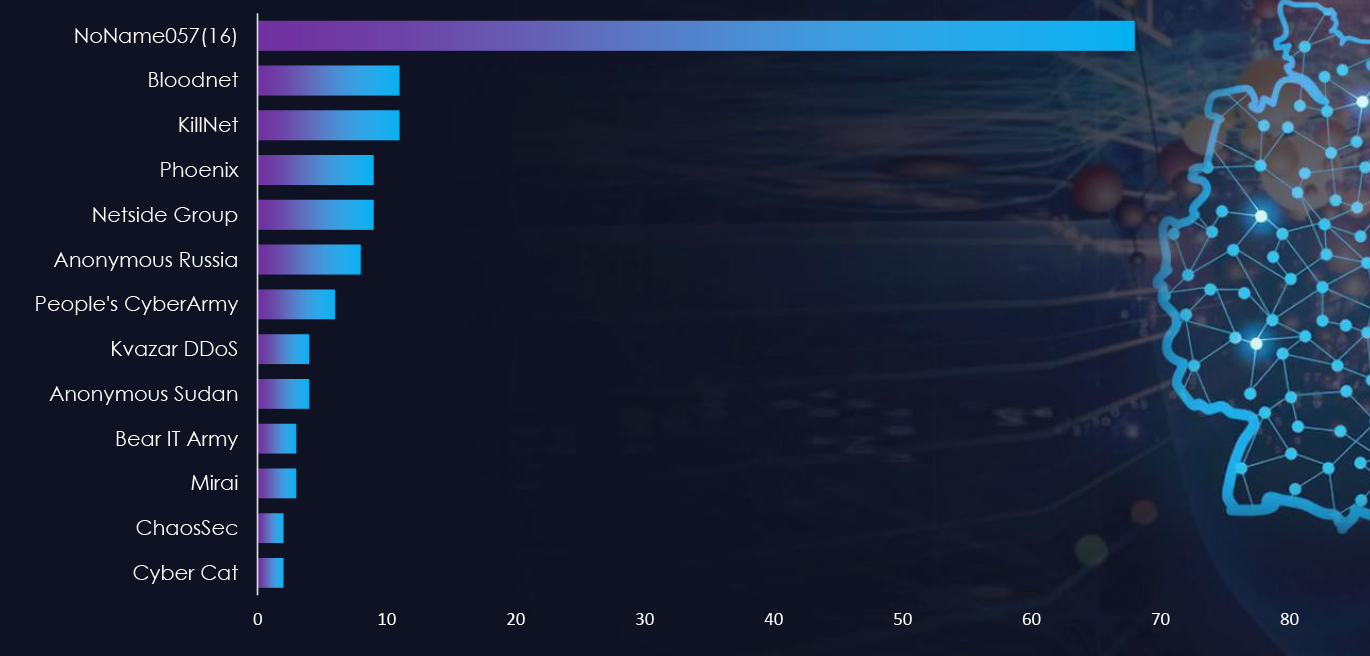
The Quantum of DDoS attacks increased globally after the start of the Russia-Ukraine war, when pro-Russian and pro-Ukraine hacktivists started targeting each other with DDoS campaigns and also started targeting alliance nations to show support to their respective country. The United Kingdom is the most targeted country in Europe by pro-Russian hacktivists.
Hacktivist Campaigns – United Kingdom
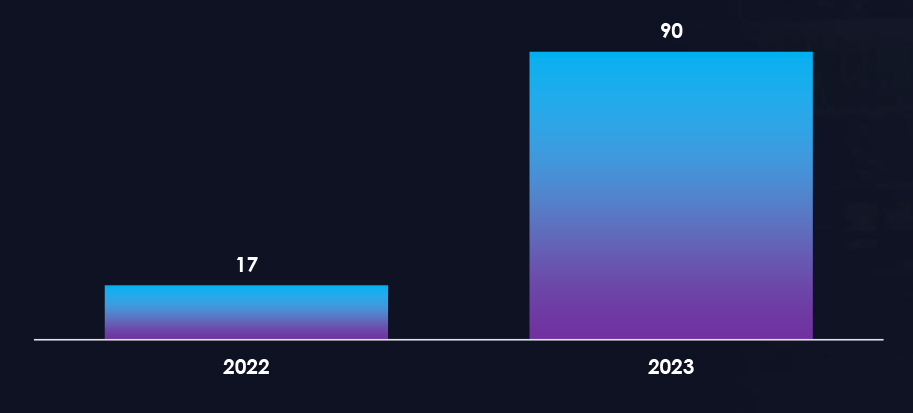
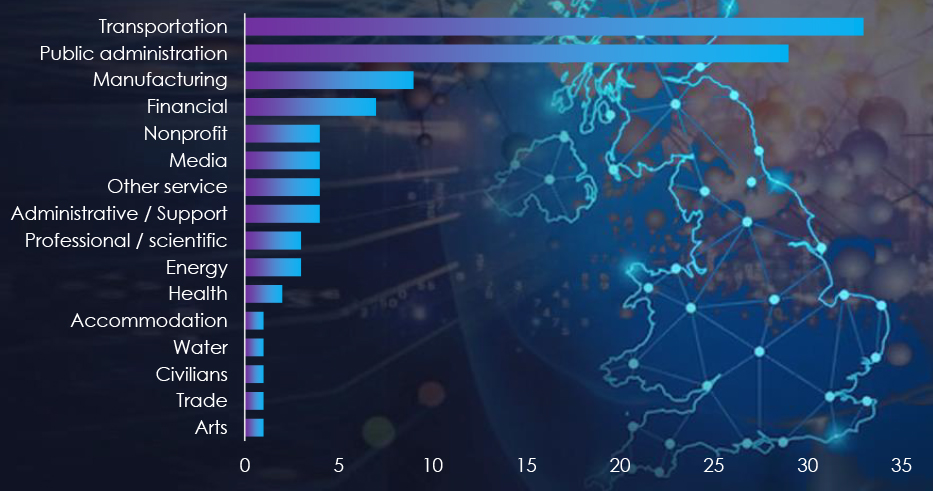
Overall, we observed 90 campaigns targeted the United Kingdom in 2023. Government Institutions, Transportation, and Manufacturing are the most targeted industries by pro-Russian hacktivists.
Hacktivist Campaigns – Targeted Industries
Hacktivist Campaigns – Threat Actors
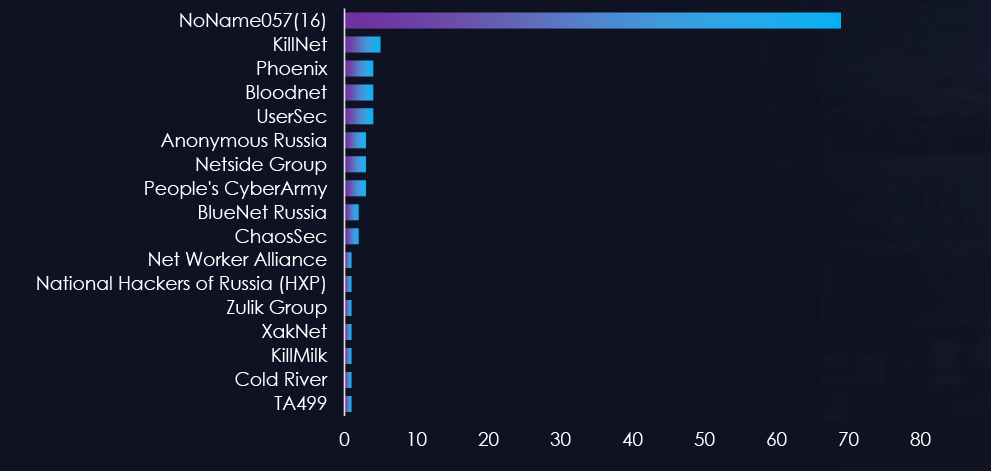
Recently we observed Anonymous Sudan claiming an attack on educational institutes in the United States.

DDoS
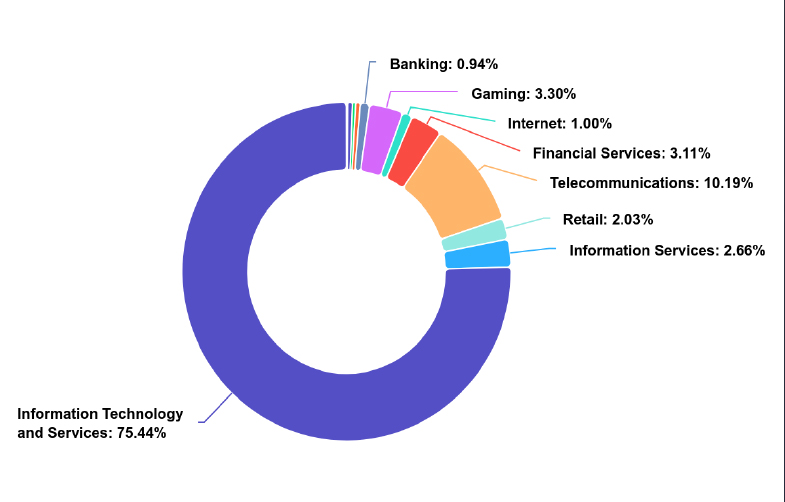
In the United Kingdom, Distributed Denial of Service (DDoS) attacks show a pronounced preference for targeting Information Technology and Services, Telecommunications, Financial Services, Gaming, and Retail sectors, with Information Technology and Services being the primary victim at a staggering 75.44%. Telecommunications, due to its pivotal role in providing essential communication services, faces substantial risks from such attacks, while financial institutions and gaming platforms are targeted for their high-value assets and lucrative nature. Retailers, reliant on digital platforms for sales and customer engagement, also experience significant disruption from DDoS assaults. These attacks, disrupting online services and causing financial losses, underscore the imperative for all industries to fortify their defenses against DDoS threats and ensure the continuity of operations.
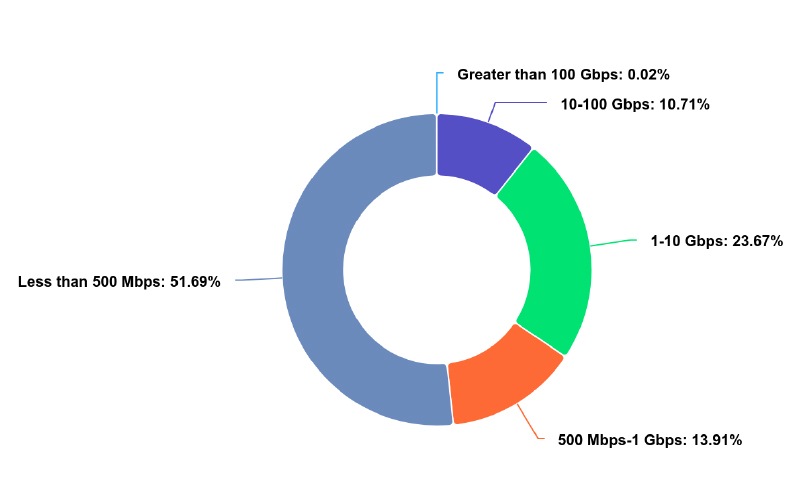
In the UK Threat Landscape, analysis of Distributed Denial of Service (DDoS) attack bitrates reveals that the majority, accounting for 51.69%, falls below 500 Mbps, indicating a prevalence of relatively lower-intensity attacks. However, a significant portion, 23.67%, ranges between 1 to 10 Gbps, posing a substantial threat to targeted organizations. Additionally, 10.71% of attacks register between 10 to 100 Gbps, showcasing a notable level of sophistication and potential for severe disruption. Attacks surpassing 100 Gbps are relatively rare, constituting only 0.02% of incidents. This breakdown underscores the diverse scale of DDoS threats faced by UK entities.

GERMANY
TRENDS IN GERMANY THREAT LANDSCAPE
- State-Sponsored Cyber Operations: Germany is frequently targeted by state-sponsored cyber operations, particularly from nation-states seeking to gather intelligence, disrupt critical infrastructure, or advance geopolitical agendas. Russia, China, and North Korea are among the primary actors engaging in such activities.
- Ransomware Attacks: Ransomware attacks continue to pose a significant threat to German organizations, including government agencies, healthcare providers, and small to medium-sized enterprises (SMEs). These attacks often result in data encryption, financial losses, and operational disruptions.
- Supply Chain Vulnerabilities: The interconnected nature of global supply chains exposes German businesses to supply chain attacks, where adversaries target third-party vendors to infiltrate larger organizations. Supply chain attacks can lead to data breaches, unauthorized access to systems, and compromise of intellectual property.
- Critical Infrastructure Risks: Germany’s critical infrastructure, including energy, transportation, and telecommunications networks, remains vulnerable to cyber threats. A successful cyber attack on these systems could have far-reaching consequences, disrupting essential services and undermining national security.
- Phishing and Social Engineering: Phishing attacks remain a prevalent tactic cybercriminals use to compromise sensitive information and gain unauthorized access to systems. Social engineering techniques, such as pretexting and spear-phishing, are increasingly sophisticated, making them difficult to detect and mitigate.
- Emerging Technologies: The adoption of emerging technologies, such as Internet of Things (IoT) devices, cloud computing, and artificial intelligence (AI), introduces new cybersecurity challenges. Vulnerabilities in IoT devices, for example, can be exploited to launch large-scale botnet attacks or infiltrate corporate networks.
WHAT ATTRACTS THREAT ACTORS TO GERMANY?
- Economic Strength: Germany is one of the world’s leading economies, with a strong industrial base and significant global trade connections. This economic strength provides ample opportunities for threat actors to target businesses, critical infrastructure, and financial institutions for financial gains through cybercrime, such as ransomware attacks, theft of sensitive data, or financial fraud.
- Advanced Technological Infrastructure: Germany boasts advanced technological infrastructure and widespread internet connectivity, making it an attractive target for cyber-attacks. Threat actors exploit vulnerabilities in networks, systems, and software to infiltrate organizations and carry out various malicious activities, including espionage, data theft, and disruption of services.
- Critical Infrastructure: Germany’s critical infrastructure sectors, including energy, transportation, healthcare, and telecommunications, are essential for the country’s functioning. Threat actors may target these sectors to disrupt services, cause economic damage, or undermine national security, posing significant risks to the country’s stability and resilience.
- Political Influence and Geopolitical Dynamics: Germany’s geopolitical position within Europe and its involvement in international affairs make it a target for state-sponsored cyber espionage and influence operations. Threat actors, including nation-state and state-affiliated groups, may target German government agencies, political organizations, and diplomatic institutions to gather intelligence, manipulate public opinion, or advance geopolitical agendas.
- Technological Innovation and Intellectual Property: Germany is known for its innovation-driven economy, particularly in sectors such as automotive, engineering, pharmaceuticals, and manufacturing. Threat actors may target German companies to steal intellectual property, trade secrets, or proprietary information, seeking to gain a competitive advantage or replicate advanced technologies for economic or strategic purposes.
- Cybersecurity Maturity and Response Capabilities: Despite Germany’s advanced cybersecurity measures and response capabilities, threat actors continually evolve their tactics, techniques, and procedures to exploit weaknesses and evade detection. This cat-and-mouse dynamic motivates threat actors to target Germany, challenging its cybersecurity resilience and readiness to combat emerging cyber threats effectively.
HIGH-PROFILE CYBER-ATTACKS AND BREACHES
- BaFin Under Cyber Siege: In September 2023, the German Federal Financial Supervisory Authority (BaFin), a cornerstone of the Federal Ministry of Finance overseeing 2,700 banks, 800 financial services, and 700 insurance providers, suffered a Distributed Denial of Service (DDoS) attack. BaFin’s critical role in law enforcement within Germany and on an international scale has made it a repeated target for pro-Russian hacktivists, including a notable DDoS onslaught in January 2024, largely attributed to the NoName057(16) group.
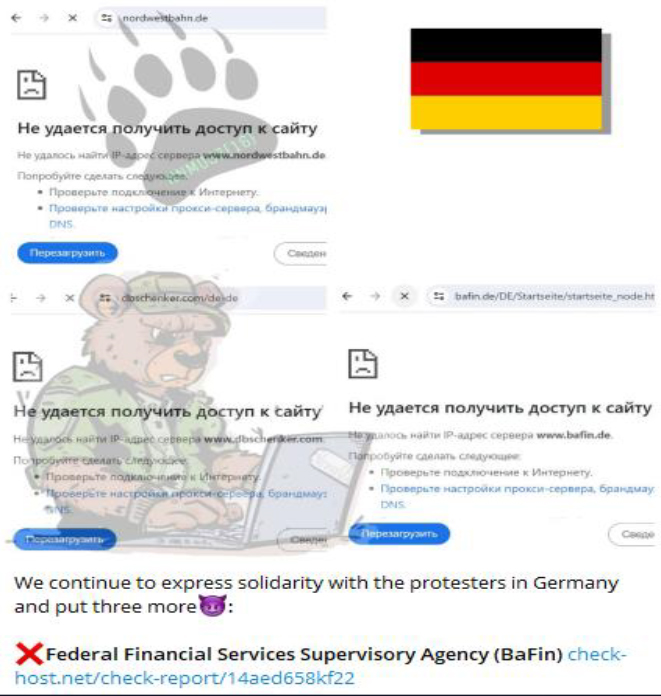
- Healthcare Disruption at KHO: The Katholische Hospitalvereinigung Ostwestfalen (KHO) network encountered a debilitating LockBit ransomware attack in December 2023. This cyber assault disrupted services across three hospitals in Bielefeld, Rheda-Wiedenbrück, and Herford, significantly threatening the provision of essential healthcare services and putting lives at risk due to the potential delay in medical emergencies.
- VARTA AG’s Production Paralysis: A cyberattack in February 2024 led VARTA AG, a prominent battery manufacturer with a history of innovation spanning 136 years, to halt its production activities. The attack, which necessitated the shutdown of IT systems across five plants, not only disrupted operations but also led to a 4.75% drop in VARTA’s share price, showcasing the financial impact of cyber threats on global manufacturing giants.
- Ransomware Hits PSI Software SE: PSI Software SE, a global provider of software solutions for energy suppliers, logistics, and production processes, was compromised by a ransomware attack. This incident, impacting the company’s internal infrastructure, highlights the vulnerability of critical software developers to cyber exploitation.
- ThyssenKrupp AG Automotive Division Breach: The automotive division of steel behemoth ThyssenKrupp AG faced a cybersecurity breach, prompting an immediate shutdown of IT systems to mitigate further damage. As a key player in the global supply chain with a workforce exceeding 100,000 and annual revenues topping $44.4 billion, this breach underscores the extensive ripple effects of cyberattacks on the manufacturing and industrial sectors.
- Consumer Protection Halted in Hessen: The Hessen Consumer Center experienced a ransomware attack that temporarily crippled its IT infrastructure, impacting the organization’s ability to serve over six million residents of central Germany, including Frankfurt. Claimed by the Blackcat/ALPHV ransomware gang, which also released data samples online, this attack on a non-profit dedicated to consumer protection and advice highlights the broad and indiscriminate nature of cyber threats.
GEO-POLITICAL RISK FACTORS
- Historical Ties and Current Geopolitical Shifts: Germany’s historical entanglements, including its past with Nazism and its division during the Cold War, have influenced its current geopolitical stance. Post-Cold War, Germany’s business entanglement with Russia and China has been significant, particularly in the energy and trade sectors. However, recent events such as Russia’s invasion of Ukraine and Iran’s disruptive actions in the Red Sea region have prompted a shift in Germany’s defense policy, aligning it more closely with Western institutions like NATO and the EU. This shift has strained relations with Russia, China, and Iran, potentially exposing Germany to retaliatory cyber threats.
- Dependency on Russian Energy: Germany’s reliance on Russian energy commodities, particularly natural gas, creates a vulnerability in its energy infrastructure. Disputes or tensions with Russia could lead to cyber threats aimed at disrupting energy supplies or infrastructure, impacting both the economy and national security.
- Political Alignment and Sanctions: Germany’s participation in Western sanctions against Russia and its recognition of China as a strategic competitor has strained diplomatic relations. As a result, Germany may face cyber threats from state-sponsored actors associated with Russia, China, and Iran. These threats could target government agencies, and financial sectors, or aim to steal intellectual property to retaliate against German policies.
- Cyber Espionage and Political Leniency: Germany’s previous political leniency towards Russia and China facilitated cyber espionage activities by these countries against the German government and business entities. With changing geopolitical dynamics, these cyber threats may escalate, targeting critical infrastructure, and sensitive information, or attempting to influence domestic politics.
- Rising Tensions in the Middle East: Germany’s support for Israel and opposition to Iran’s policies in the Middle East align it with Western interests but also make it a potential target for cyber threats from Iran or its allies. These threats could aim to disrupt trade, influence public opinion, or retaliate against Germany’s stance on Middle Eastern conflicts.
- Hacktivist and Opportunistic Threats: Germany faces cyber threats from hacktivist groups affiliated with Russia, China, and Muslim countries. These groups may target government agencies, and financial sectors, or engage in disruptive activities to express political grievances or support broader geopolitical objectives. Additionally, opportunistic threats from countries like North Korea, seeking financial gains or technological advancements, pose a risk to German businesses and critical infrastructure.
- Supply Chain Risks and Dual-Use Technologies: Germany’s advanced industrial base and technological expertise make it a target for cyber espionage aimed at stealing dual-use or military technologies. Threat actors may exploit supply chain vulnerabilities or engage in intellectual property theft to gain a competitive advantage or support military programs in adversarial countries.
TRENDS FROM THE DARK WEBS
We observed 30 campaigns targeting various industries in Germany during 2023. Chinese, Russian, and North Korean state-sponsored threat actors are behind most of these campaigns.
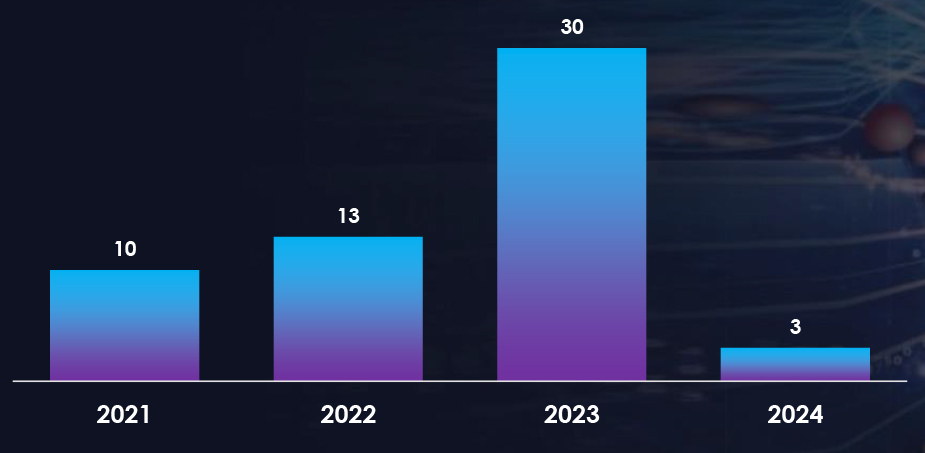
In 2023, there was a substantial rise in the number of observed campaigns, a marked increase when compared to the preceding two years. This uptick highlights the heightened interest of threat actors in economic and geopolitical dynamics, particularly in response to Germany’s position on the Russia-Ukraine conflict.
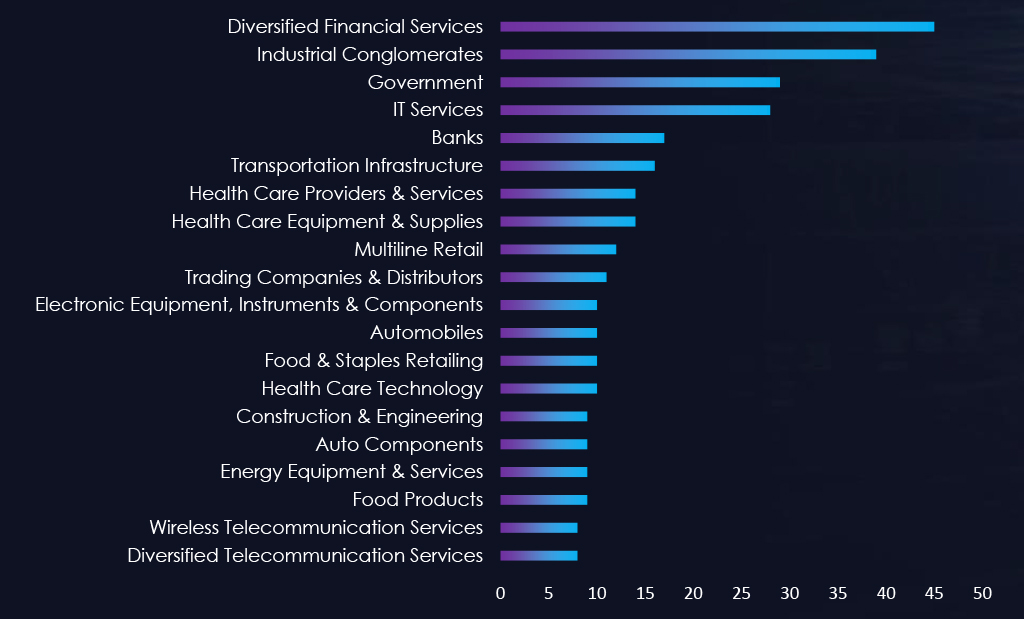
TARGETED INDUSTRIES AND TECHNOLOGY
In the observed cyber campaigns, threat actors have methodically targeted a multitude of industries within the critical infrastructure. This deliberate focus is generating substantial economic and social repercussions within the threat landscape, amplifying its overall impact.
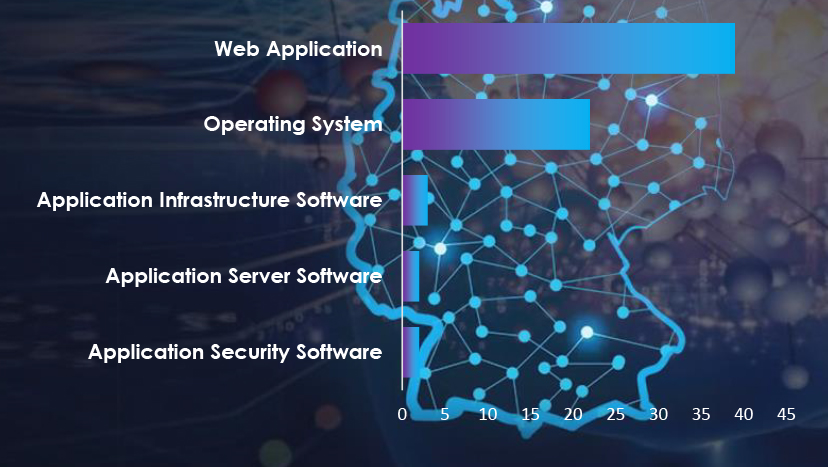
In the observed campaigns threat actors focused on attacking web applications, operating systems, and various other applications.
THREAT ACTORS TO WATCH

DATA LEAKS
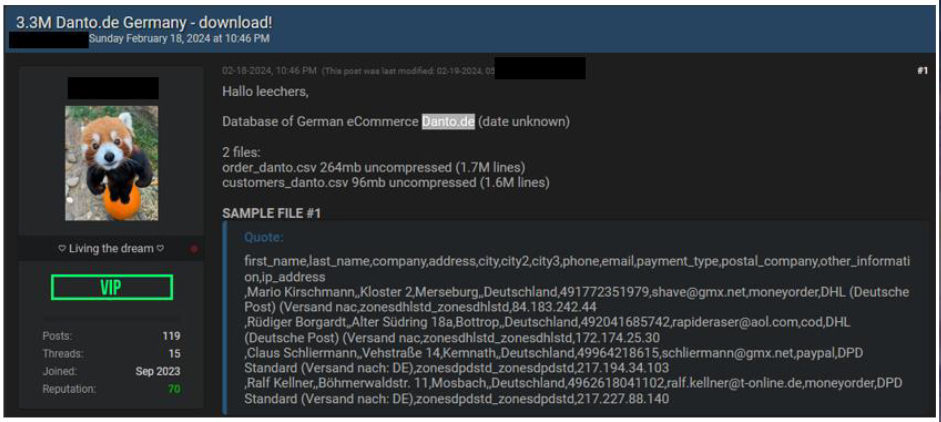
CYFIRMA Research team observed a data leak related to Danto (www[.]danto[.]de). Danto is a German company specializing in eCommerce. The Threat actor leaked customer and order data of Danto in the leak forum.
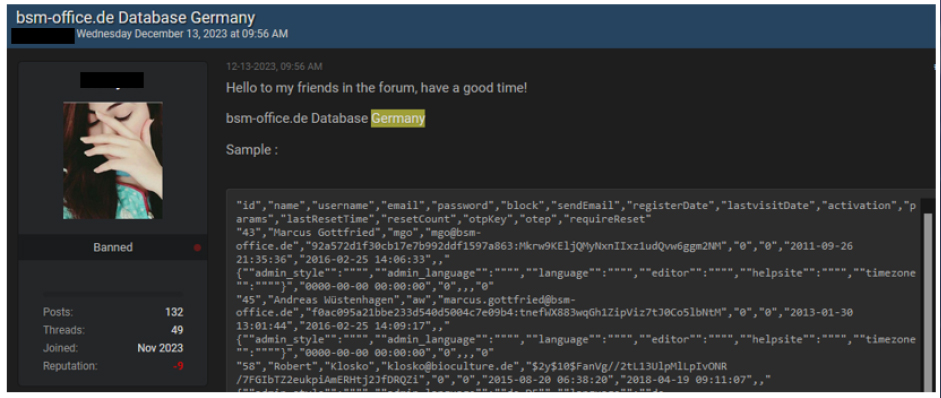
BSM Bürosysteme Vertriebs (www[.]bsm-office[.]de) is a company that operates in the Business Supplies and Equipment industry. BSM Bürosysteme Vertriebs database was advertised in the leak forum for sale.
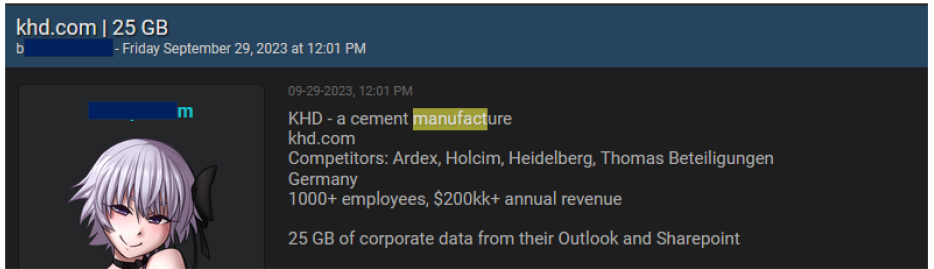
Through CYFIRMA Research, data breaches have been detected in connection with KHD Humboldt Wedag (www[.]khd[.]com, which provides various engineering products and services for the cement industry worldwide. The company offers clean technology solutions, and pyro processing equipment, including preheaters, calciner, and bypass. The compromised data encompasses 25 GB of corporate data from Outlook and Sharepoint.
PHISHING
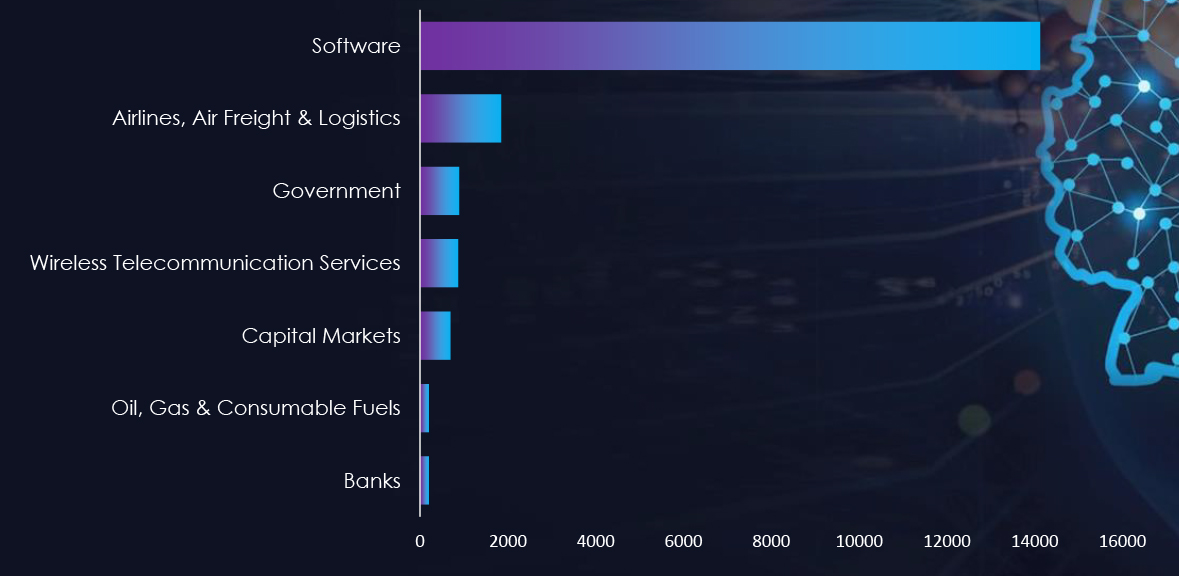
From 14th February 2023 to 14th February 2024 CYFIRMA’s telemetry recorded 33,894 phishing campaigns targeting Germany out of a total of 887,968 campaigns. Most impersonated themes are associated with Software, Wireless Telecommunication Services, Airlines, Air freight, Logistics, Government, and Banking sectors.
RANSOMWARE
Germany is one of the top targeted country in Europe by ransomware groups. Ransomware groups target Germany for several reasons. Germany boasts a robust economy, ranking as the world’s third-largest exporter with a significant portion of its GDP derived from the industry. This economic strength makes German businesses lucrative targets for ransomware attacks, as cybercriminals seek to exploit vulnerabilities in critical infrastructure and supply chains. Additionally, Germany’s advanced technological infrastructure and high internet connectivity provide ample opportunities for ransomware groups to infiltrate systems and execute attacks. Moreover, the widespread adoption of digital technologies in various sectors makes German organizations more susceptible to ransomware threats.
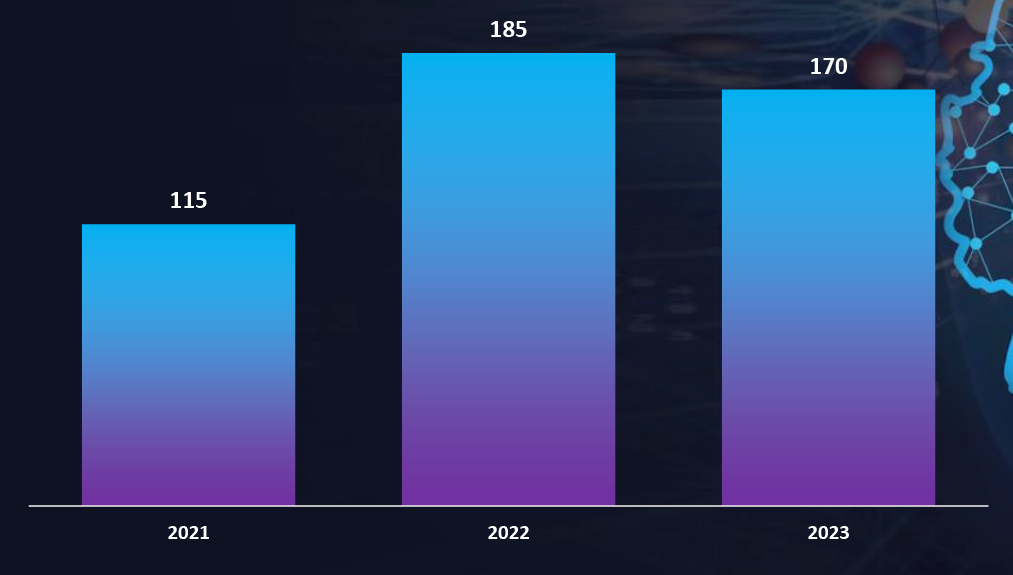
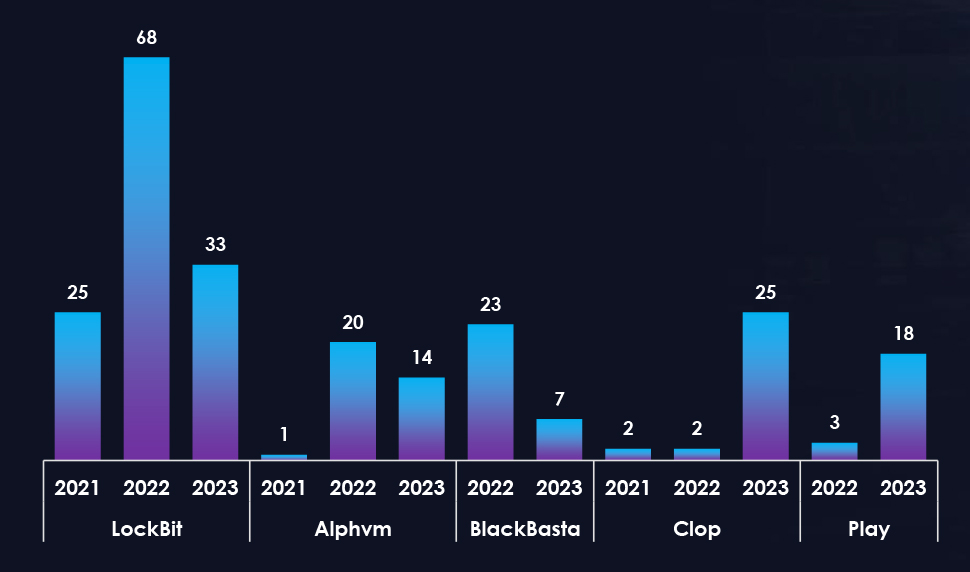
We observed a significant increase in Ransomware victims from Germany, compared to earlier years. Notably, this threat landscape is influenced by formidable ransomware groups, including LockBit, BlackCat (Alphvm), BlackBasta, Cl0p, and Play, which feature prominently on the list of perpetrators targeting German companies.
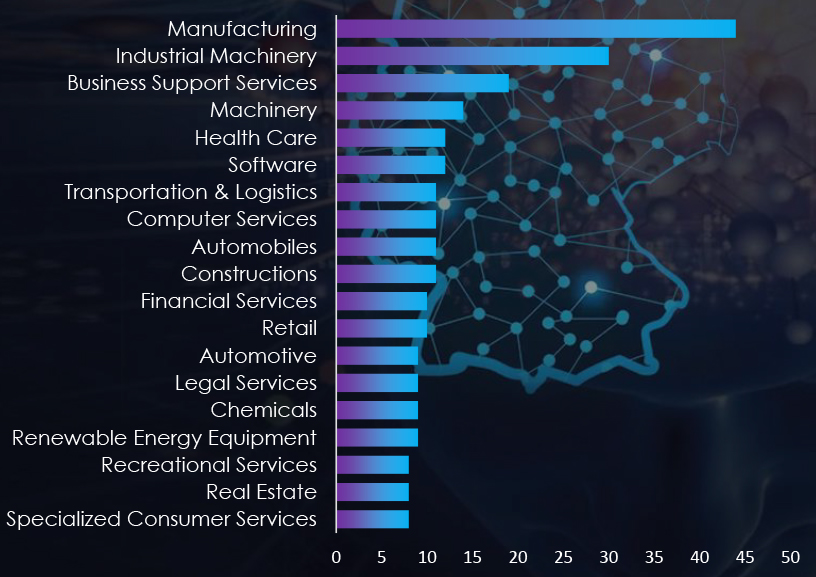
Manufacturing, Industrial Machinery, Business Support Services, Machinery, and Health Care are the top targets of ransomware actors in Germany.
ASSET EXPOSURES & VULNERABILITIES
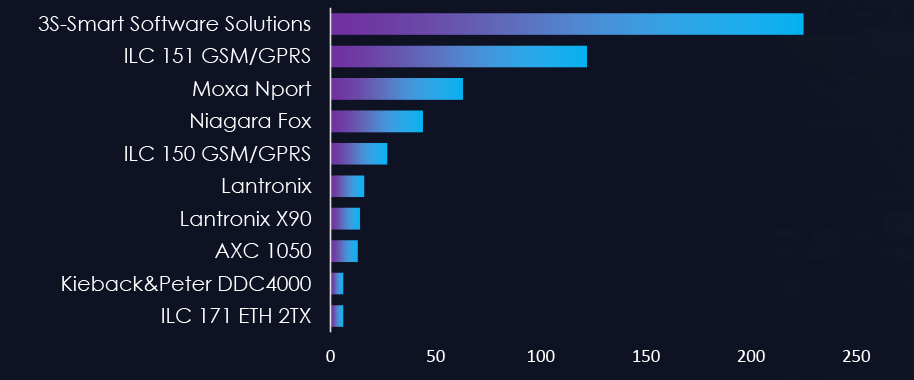
In our OSINT research, we found around 4,329 Industrial Control Systems exposed to the Internet, owned by organizations in Germany, potentially allowing an attacker to access them.
Exposed Industrial Control Systems: Top 10 Products
Most Exploited Vulnerabilities in Last 3 months
| Vulnerability |
Vendor |
Product |
CVSS |
| CVE-2023-20198 |
Cisco |
Cisco IOS XE |
10 |
| CVE-2024-1709 |
ConnectWise |
ScreenConnect |
10 |
| CVE-2023-0669 |
Fortra |
GoAnywhere MFT |
7.2 |
| CVE-2022-26134 |
Atlassian |
Confluence |
9.8 |
| CVE-2017-9841 |
PHPUnit – Sebastian Bergmann |
PHPUnit |
9.8 |
| CVE-2023-23752 |
Open Source Matters, Inc/Joomla community |
Joomla |
5.3 |
| CVE-2023-49103 |
ownCloud |
ownCloud |
7.5 |
| CVE-2023-4966 |
Citrix |
Citrix ADC and Citrix Gateway |
7.5 |
| CVE-2021-26084 |
Atlassian |
Confluence |
9.8 |
| CVE-2017-10271 |
Oracle |
Oracle Weblogic Server |
7.5 |
HACKTIVIST
The Quantum of DDoS attacks increased globally after the start of the Russia-Ukraine war when pro-Russian and pro-Ukraine hacktivists started targeting each other with DDoS campaigns and also started targeting alliance nations to show support to their respective country. Germany is one of the most targeted country in Europe by pro-Russian hacktivists.
Hacktivist Campaigns – Germany
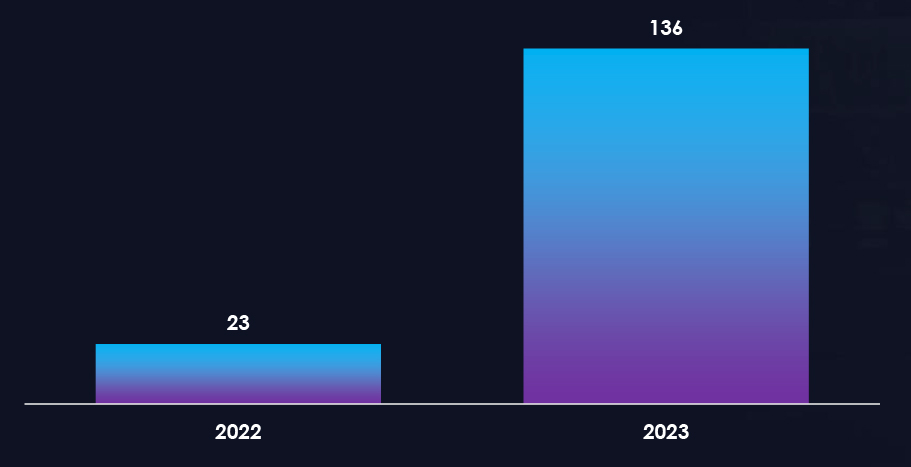
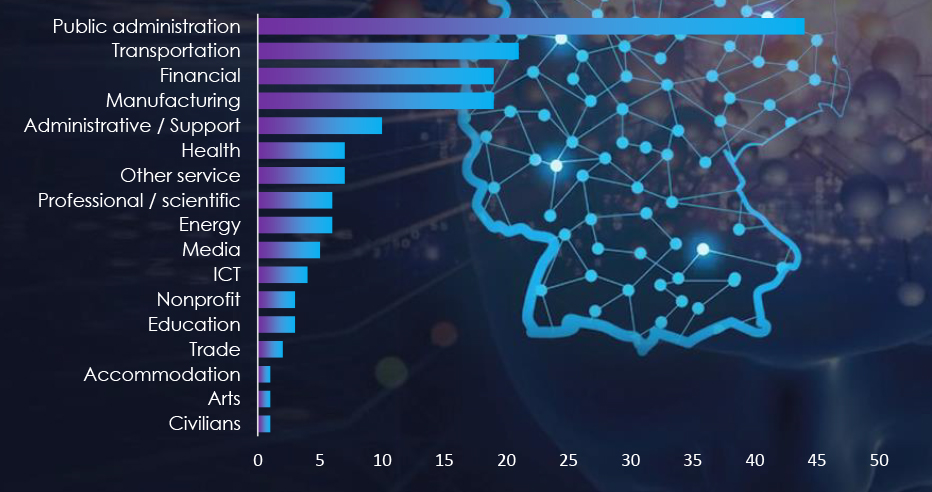
Overall, we observed 136 campaigns targeting Germany in 2023. Government Institutions, Transportation, Financial, and Manufacturing are the most targeted industries by pro-Russian hacktivists.
Hacktivist Campaigns – Targeted Industries
Hacktivist Campaigns – Threat Actors