



Australia and New Zealand’s cyber threat landscape has become increasingly complex, with challenges affecting critical infrastructure, healthcare, finance, manufacturing, mining, and more. This Report stresses the growing dangers posed by cybercriminals and state-sponsored threat actors alike while highlighting the proactive measures that businesses can take to strengthen their defenses.
Organizations are increasingly recognizing that cybersecurity is no longer a peripheral concern but a central element of operational resilience and national security.
The rapid evolution of cybercrime in the region is driven by an expanding ecosystem of access brokers, extortionists, and sophisticated adversaries. Common attack vectors such as business email compromise remain a persistent challenge, while ransomware, data exfiltration, and hacktivist denial-of-service attacks disrupt business continuity and inflict substantial financial and reputational harm. Additionally, supply chain vulnerabilities are being exploited at an unprecedented scale, heightening risks across interconnected systems.
Geopolitical factors have amplified these threats, with ideologically driven groups like the People’s Cyber Army and Mysterious Team Bangladesh targeting government websites, financial institutions, and critical infrastructure in response to Australia’s geopolitical alignments. These attacks are designed to disrupt essential services, influence public perception, and create pressure on national resources, signaling a shift towards politically motivated cyber aggression in the region.
In response to this escalating threat landscape, both Australia and New Zealand have adopted transformative measures to strengthen their cybersecurity postures. Strategic initiatives, such as national cybersecurity strategies, enhanced budgetary commitments, and robust legislation, are driving a coordinated approach to combatting cyber risks. This report offers a detailed analysis of the current threat environment and provides actionable insights for mitigating risks in high-priority sectors, including finance, healthcare, government, and infrastructure. Key focus areas include leveraging governmental directives, capitalizing on increased regional cybersecurity investments, adhering to evolving regulatory requirements, and fostering international collaboration to counteract the growing sophistication of cybercriminals and politically motivated threat actors.
The findings of this report stress the urgency of adopting a comprehensive cybersecurity framework, integrating advanced technologies, and fostering a culture of security awareness to stay ahead of evolving threats and ensure long-term resilience.
01 MOVEMENT FROM DIGITAL TO KINETIC TARGETS
Trend: Ransomware attacks on critical infrastructure
Motives: Disruption/Geopolitical/Extortion
02 DATA EXFILTRATION FROM IOT DEVICES
Trends: Spyware, Malware and Plug-ins to collect data
Motives: Reputation impact, disruption, extortion
03 EXPLOITATION OF LEGACY SYSTEM
Trends: Brute Force Attacks, Credential Reuse and Data Exfiltration via Malware
Motive: Operational Disruption, Espionage, IP Exfiltration
04 CROSS-ENVIRONMENT ATTACK
Trend: Social engineering/phishing. Jump server
Exploits, Remote access tool compromise
Motives: Operational Disruption, Espionage, IP Exfiltration
05 USE OF BOTNETS, AI, DEEPFAKE
Trends: Device Scanning, Firmware, Phishing/malware Download
Motives: Disruption, Data Harvesting, Remote Attacks (DDOS)
06 SUPPLY CHAIN OF INFRASTRUCTURE, UTILITY COMPANIES REMAIN AT RISK
Trends: Multi-behavioral malware (IT/OT), Different operating system
Target: CII trade secrets documents containing proprietary processes
INFORMATION TECHNOLOGY
With a strategic emphasis on the Information and Communication Technology (ICT) sector, both the Australian and New Zealand governments have launched various initiatives to drive its development, recognizing it as a critical industry. The goal is to significantly boost their digital economies, offering substantial growth prospects for the ICT market. In Australia, the digital economy is projected to contribute AUD 250 billion to GDP by 2030, while New Zealand aims to strengthen its position as a leading digital nation. This ambitious trajectory is highlighted by robust annual growth rates and substantial investments in technology and innovation.
Within this dynamic and expanding digital landscape, the IT industry in Australia and New Zealand attracts significant attention from cyber threat actors. The convergence of economic ambitions and rapid technological advancements renders the IT sector particularly vulnerable to cyber threats. Threat actors target this sector to exploit vulnerabilities for financial gains, intellectual property theft, or competitive advantage. As such, addressing cybersecurity challenges and implementing robust protective measures is crucial to safeguarding the IT infrastructure and ensuring the resilience of the digital economies in both countries.
AGRICULTURE INDUSTRY
Australia’s agriculture sector is a vital component of the national economy, significantly contributing to both domestic production and international exports. The sector’s diverse range of primary products, including wheat, milk, fruits, nuts, vegetables, and meat, play a crucial role in the country’s GDP. Key export commodities such as beef, wheat, wine, wool, and lamb highlight Australia’s prominence in global agricultural trade. Notably, the beef industry stands out as Australia’s largest agricultural enterprise, making the nation the world’s second-largest beef exporter, following Brazil. Approximately 72% of Australia’s agricultural production is exported internationally.
However, the agricultural sector faces increasing cyber threats, ranking as the sixth most susceptible to data breaches. These threats include data breaches, ransomware, phishing campaigns, scam emails, and malware. The sector’s complexity, spanning small-scale enterprises to large global operations, results in varied levels of IT proficiency and cybersecurity awareness. Despite growing technological investments, there remains a significant gap in prioritizing cybersecurity.
The adoption of digital platforms, payment gateways, and advanced agricultural machinery, such as precision agriculture technologies, creates vulnerabilities. These range from unauthorized access to personal and business data to the compromise of production systems and theft of intellectual property. Addressing these challenges is crucial to ensure the resilience and security of Australia’s agricultural industry against evolving cyber threats.
TOURISM
Beyond its economic contributions, Australia and NZ’s allure as a tourism hotspot is undeniable. Their diverse offerings cater to a broad spectrum of travellers, making the tourism industry a lucrative target, with its wealth of sensitive data, including traveller information, financial transactions, and reservation details. Additionally, the sector’s interconnected ecosystem, encompassing travel agencies, hospitality services, and online platforms, presents numerous avenues for cybercriminals to exploit vulnerabilities, ranging from data breaches and financial fraud to ransomware attacks.
LOGISTICS
The logistics industry plays an indispensable role in bolstering Australia and NZ’s economies, overseeing the intricate processes of production, storage, inventory management, and the efficient delivery and distribution of goods and services. As of 2023, the Australia Freight and Logistics Market commands a significant valuation of approximately 89.86 billion USD, with projections indicating a growth trajectory to reach 113.94 billion USD by 2029. This growth underscores the sector’s vitality, driven by the nation’s robust import and export dynamics. However, as the logistics industry evolves and expands, it concurrently becomes a focal point for cyber threats within the Australian threat landscape. Threat actors are increasingly targeting the logistics sector, drawn by its pivotal role in the supply chain ecosystem, an extensive network of stakeholders, and vast volumes of valuable data and goods in transit.
MINING
Australia’s mining sector continued to be a cornerstone of its economy in 2024, despite facing ongoing challenges. The sector remained a major contributor to the nation’s GDP and a significant source of export revenue, driven by strong demand for key commodities like iron ore, coal, and gold. However, the industry navigated a complex landscape marked by global economic uncertainties, geopolitical tensions, and the ever-present threat of climate change. The global economic slowdown, coupled with rising interest rates and inflationary pressures, posed challenges to the mining sector. Commodity prices experienced some volatility, impacting profitability and investment decisions. The growing emphasis on environmental, social, and governance (ESG) factors continued to shape the industry. Mining companies faced increasing pressure to reduce their environmental footprint, improve social and community engagement, and enhance governance practices. This led to a renewed focus on sustainable mining practices, including energy efficiency, water management, and responsible sourcing.
MANUFACTURING
Australia’s manufacturing sector in 2024 reflects a dynamic and diversified landscape, with core industries including food and beverages, machinery and equipment, chemicals, and metal products. Over the next two decades, the industry is poised to embrace a transformation characterized by increased integration, collaboration, and an export-oriented approach. Central to this evolution is the adoption of high-value, customized solutions within global value chains, emphasizing advanced design, R&D, and comprehensive after-sales services. The sector is also shifting toward sustainable practices and favoring low-volume, high-margin production models to meet changing market demands.
The 2024 CommBank Manufacturing Insights Report highlights that 72% of Australian manufacturers project robust production growth and are prioritizing capital expenditure in advanced technologies to enhance productivity, quality, and operational capacity. However, alongside these technological advancements comes an expanding cyber-attack surface. The sector’s dependence on interconnected systems and data-driven processes has heightened its vulnerability, with cyber threats ranging from intellectual property theft and espionage to operational disruptions and financial extortion. This makes cybersecurity a critical priority as the industry advances into a more technology-reliant future.
HEALTH
The governments of Australia and New Zealand have developed many programs for the progress of the health industry, with a strategic focus on the development of healthcare systems, since it holds huge significance. This helps in building better health conditions and easy accessibility, thus benefiting the nations as a whole by enabling overall development and economic stability. The health sector in Australia is supposed to contribute AUD 200 billion towards the GDP by 2025, and New Zealand is also making enough investments in enhancing health outcomes and infrastructure.
In this fast-changing landscape, the health industry in Australia and New Zealand stands vulnerable to serious cyber threats. The integration of digital health records, telemedicine, and advanced medical technologies exposes it to vulnerabilities. The cyber adversaries target this sector to exploit the weaknesses for financial gains, data theft, or disrupting the health care services. These threats, therefore, underscore the importance of effective cybersecurity measures that ensure sensitive health information is well-protected and the resiliency of healthcare systems is duly guarded. Overcoming these challenges will ensure patient data protection, retained trust, and continued high-quality delivery of healthcare services in both nations.
Australia’s geopolitical stance and its relationships with global powers profoundly influence its cybersecurity strategies.
Following a period of geopolitical normalcy, characterized by the resumption of trade relations with China and the enduring US alliance, Australia once again faced global disruptions in 2024. Moreover, Trump’s upcoming return to the White House brings a mix of opportunities and challenges for Southeast Asia. The new administration seems set to revitalize the Indo-Pacific strategy crafted during Trump’s first term, emphasizing countering China and bolstering alliances and partnerships across the region. But the new approach will bear more continuity with the previous administration than first meets the eye. This also relates to New Zealand.
On the same day U.S. President Joe Biden hosted the inaugural United States-Japan-Philippines summit at the White House, a quieter yet strategically significant meeting unfolded just a few blocks away. On April 11, New Zealand Foreign Minister Winston Peters met with U.S. Secretary of State Antony Blinken at the State Department, where the two officials issued a joint statement emphasizing that their nations are “working more closely than ever.”
This meeting marked a notable development in U.S.-New Zealand relations, which have historically been strained, partly due to Wellington’s earlier engagement with China. It highlighted how Beijing’s assertive behavior is increasingly driving regional actors toward Washington’s strategic embrace. While U.S.-New Zealand ties had cooled in the 1980s, relations began to improve in the 2010s, a shift catalyzed by Beijing’s actions. For New Zealand, revelations of widespread Chinese political interference in the country’s 2017 national elections were a turning point, transforming its perception of China from a partner to a concern.
Foreign Minister Peters has since called for New Zealand to deepen its engagement with security alliances like the Five Eyes intelligence network and NATO. Moreover, New Zealand may soon collaborate with AUKUS (Australia-United Kingdom-United States) on non-nuclear security initiatives, including cyber defense, hypersonic weapons, artificial intelligence, quantum technology, and undersea capabilities. Unsurprisingly, these developments have not been well-received in Beijing.
After weathering the COVID-19 storm and mending fences with China, Australia seemed poised to reclaim its traditional geopolitical role in 2024. The AUKUS partnership, a trilateral security pact with the US and UK, solidified its strategic alignment with the West, while trade ties with China gradually normalized.
However, this apparent stability masks an inherent contradiction. AUKUS and the nuclear submarine deal signed with the US, is widely viewed as a counterbalance to China’s growing assertiveness in the South China Sea, a vital trade route for Australia. Yet, China remains Australia’s largest trading partner, highlighting the delicate balancing act Australia must perform between its security and economic interests.
Despite this tension, Australia has managed to maintain good relations with its neighbors, including Indonesia, once perceived as a potential security threat. This diplomatic dexterity underscores Australia’s ability to navigate the complex geopolitical landscape of the Indo-Pacific.
The problem for both Australia and New Zealand is that China views alliances including AUKUS and the so-called “Quad” (Australia, Japan, the Philippines, and the United States) as part of a broader U.S.-led effort to contain its influence. While these partnerships are not the primary focus of Trump-era foreign policy, which prioritized Iran and China, their growing importance could make them key players in Southeast Asia’s geopolitics. Any progress by Washington in strengthening these relationships is likely to provoke subtle responses from Beijing, including the use of cyber tactics. Meanwhile, on the economic front, a downturn in the Chinese economy has reduced demand for iron ore and heightened the need for Australia to expand its trading networks.
Any movement closer to the US, something the upcoming American administration might demand for lending further support (in terms of forcing Australia and New Zealand to “choose” between the US and China, inherently carries risks of overt and covert retaliation from Beijing, particularly through economic warfare and cyberattacks. As U.S. military engagements in the region increase, including more frequent port visits to Australia and New Zealand, the geopolitical stakes will continue to rise, testing the resilience and unity of these emerging alliances.
China is a global champion in using cyber attacks as a tool of statecraft and has a bigger hacking program than that of every other major nation combined. Should Australia and New Zealand get their balancing act wrong, they would face consequences in the fifth domain swiftly.
In 2024, there is a rise in the number of observed campaigns, a slight increase compared to the preceding year. This uptick highlights the heightened interest of threat actors in the economic and geopolitical dynamics of Australia.
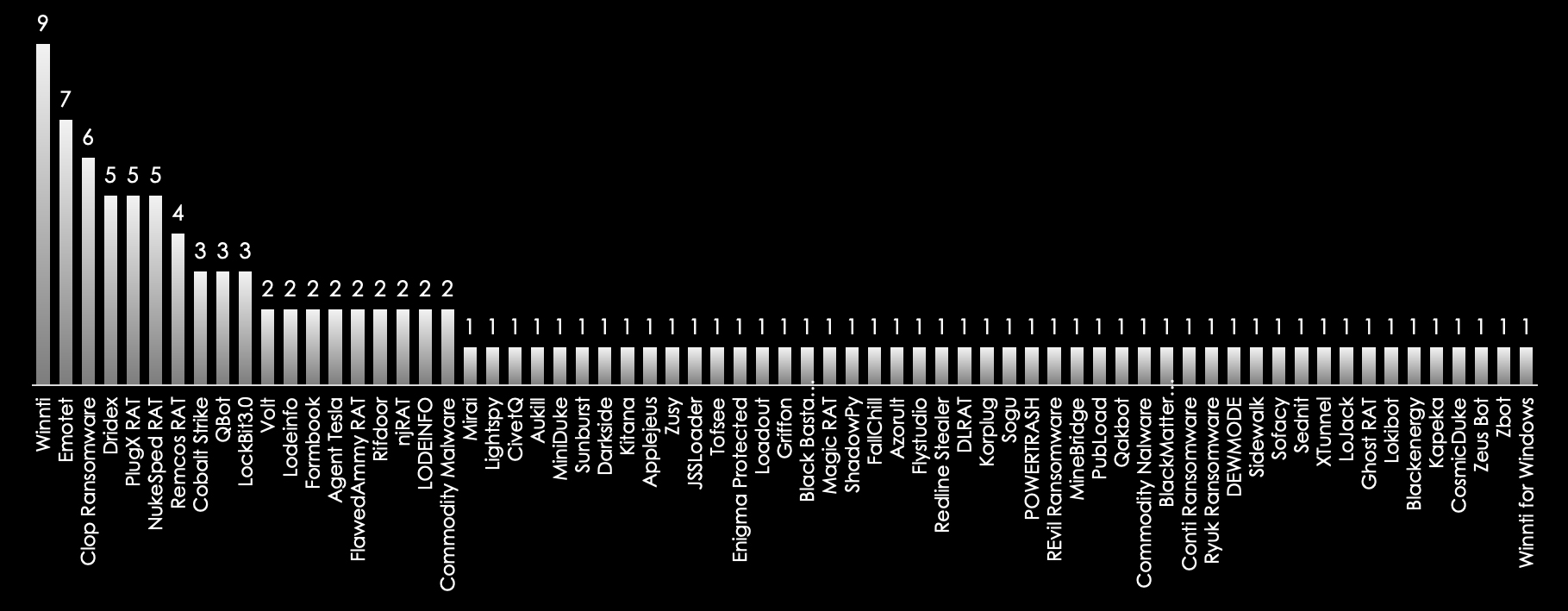
The malware landscape remains dominated by familiar threats, Winnti, Emotet, and various ransomware strains, including LockBit3.0, are responsible for a significant portion of cyberattacks. Remote Access Trojans (RATs) like PlugX, NukeSped RAT, Remcos RAT, and Cobalt Strike are also prevalent, enabling attackers to maintain persistent access to compromised systems and facilitate further attacks. These tools are often used by both state-sponsored and financially motivated actors.
The most active suspected threat actors in campaigns with recorded victims in Australia are MISSION2025, Lazarus group (DPKR), FIN7, TA505, combined Chinese Threat actors (Pandas) as well as combined Russian cybercriminal syndicates. MISSION2025 reigned supreme, their relentless campaigns yielding the highest observed count. Close behind were the notorious Lazarus Group and FIN7, notorious for their sophisticated techniques and lucrative exploits.
State-sponsored actors like TA505 and Stone Panda continued to pose significant threats, their operations often intertwined with geopolitical agendas. Groups like Fancy Bear and Cozy Bear, known for their involvement in high-profile intrusions, maintained a persistent presence.
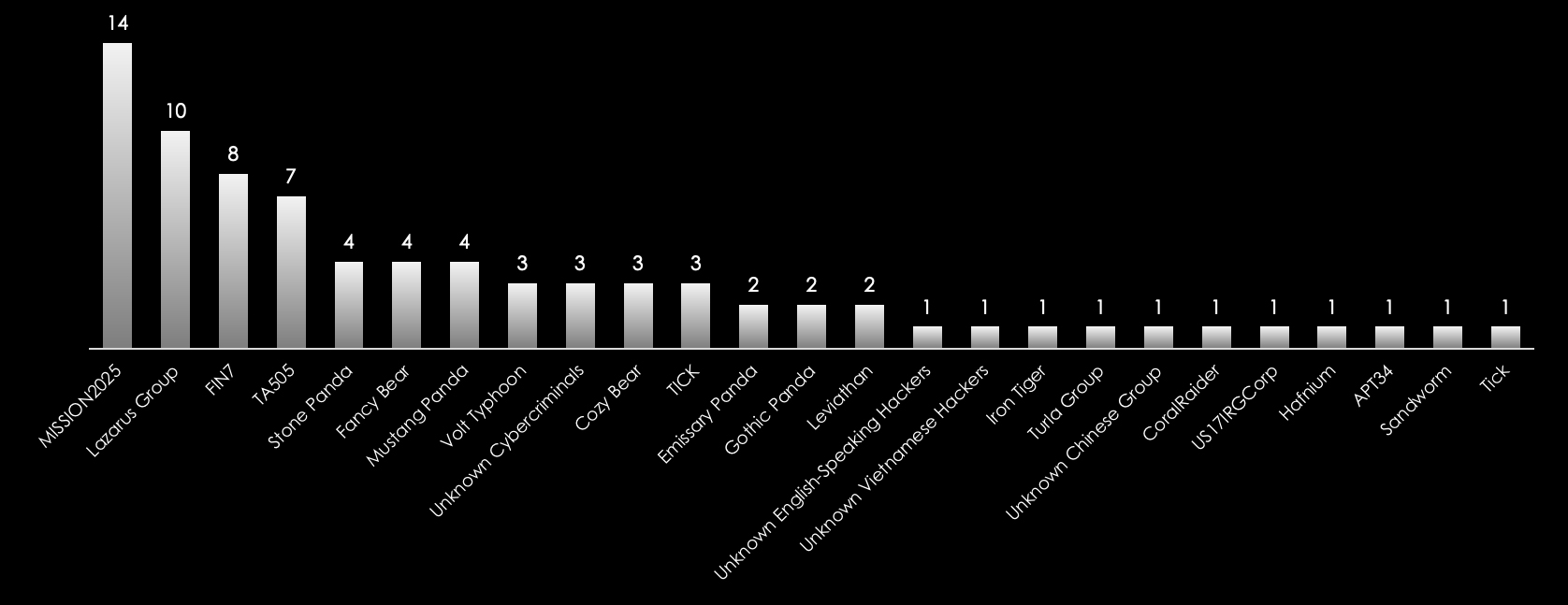
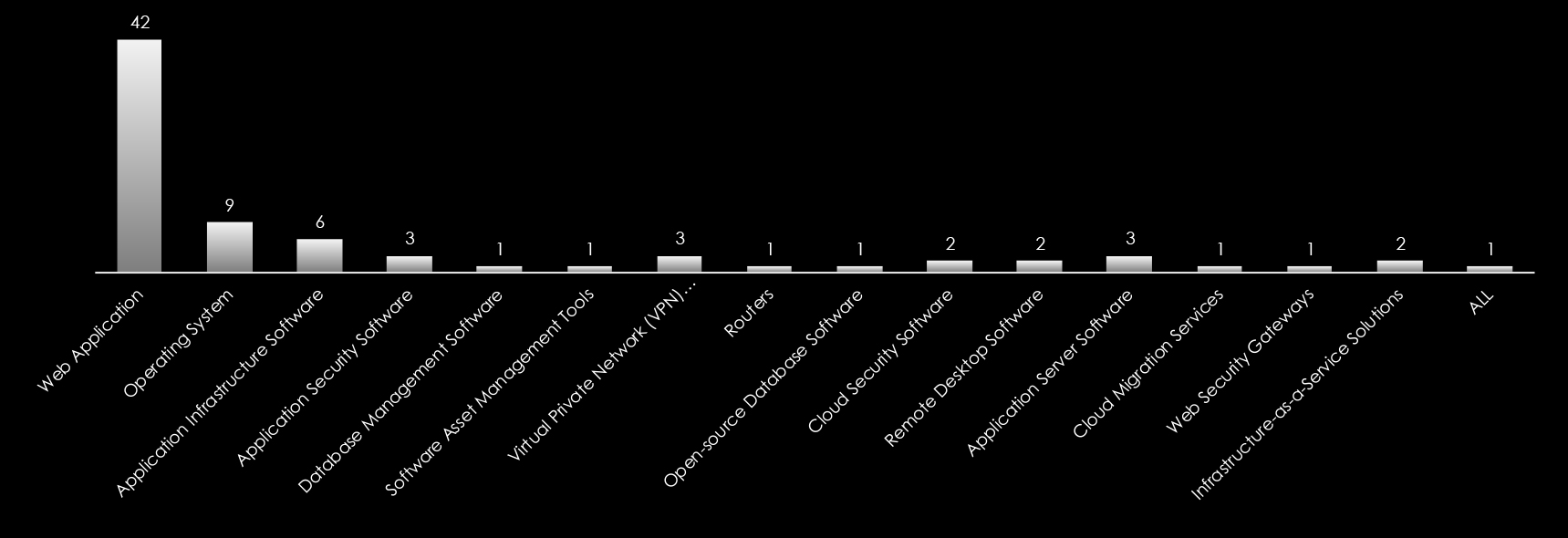
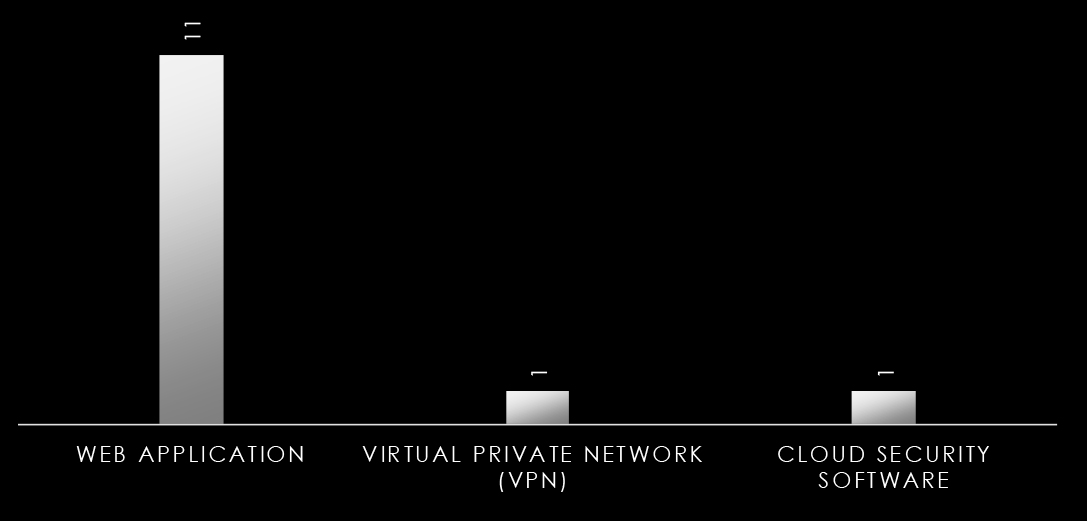
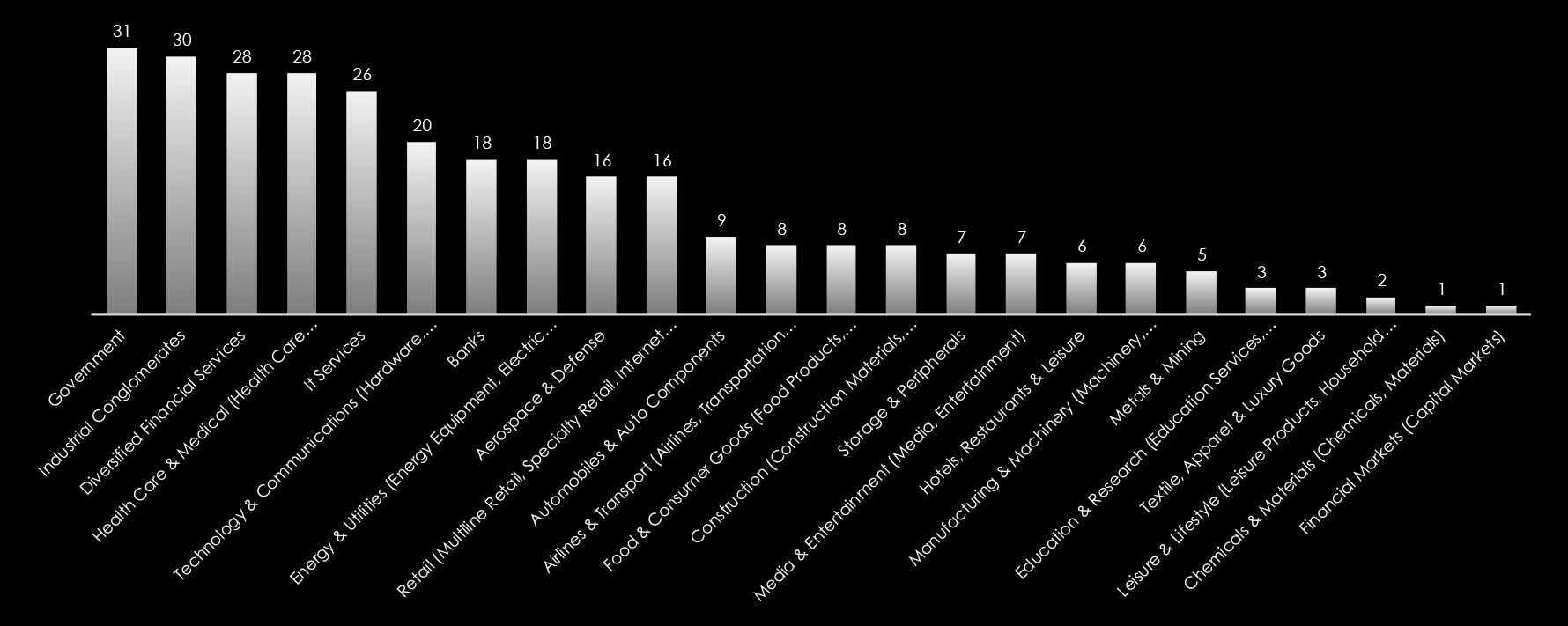
We observed 17 campaigns targeting various industries in Australia during 2024. Russian, Chinese, and North Korean state-sponsored threat actors are behind most of these campaigns. Here are some details about observed sample campaigns.
| Campaign Name | Suspected Threat Actor | Geography | Target Industries | Targeted Services/ vulnerabilities | Malware Name |
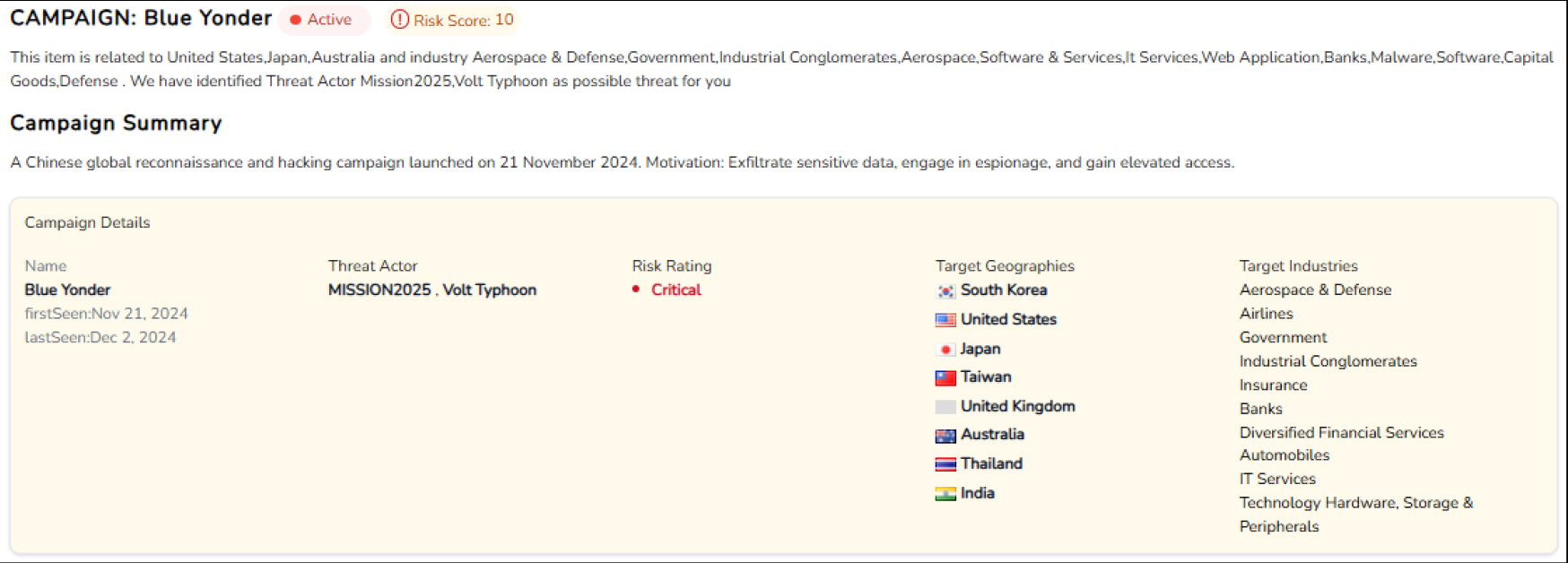
| Blue Yonder | MISSION2025, Volt Typhoon | South Korea, United States, Japan, Taiwan, United Kingdom, Australia, Thailand, India | Aerospace & Defense, Airlines, Government, Industrial Conglomerates, Insurance, Banks, IT Services, Diversified Financial Services, Automobiles, Technology Hardware, Storage & Peripherals | Web Application | Mirai, Volt, Lightspy |
| Thunderstorm | Volt Typhoon, Emissary Panda | United States, Japan, Taiwan, United Kingdom, Australia, Thailand, India | Government, Industrial Conglomerates, Insurance, Banks, It Services, Diversified Financial Services, Technology Hardware, Storage & Peripherals | Virtual Private Network (VPN) Solutions, Routers, Web Application | Volt |
| Red River | Unknown English-Speaking Hackers, Unknown Vietnamese Hackers | South Korea, Vietnam, United States, Japan, Taiwan, United Kingdom, Australia, Thailand, India | Aerospace & Defense, Diversified Telecommunication Services, Government, Industrial Conglomerates, Wireless Telecommunication Services, IT Services, Diversified Financial Services, Machinery, Technology Hardware, Storage & Peripherals | Web Application | Cobalt Strike |
Campaign details tracked by DeCYFIR where threat actors are targeting Australia/New Zealand organizations.

MISSION2025, APT41, Stone Panda

TA505, Cozy Bear, Fancy Bear, FIN7

LAZARUS GROUP
Data leaks play a crucial role in the landscape of cyber threats, acting as a significant vulnerability that can lead to a wide range of security issues and potential damages. When sensitive or confidential information is accidentally exposed or intentionally stolen and released, it can lead to identity theft, financial fraud, and a severe loss of trust and reputation for the affected organization. Such leaks often provide cybercriminals with the necessary data to conduct more targeted and effective attacks, such as phishing schemes, ransomware attacks, or further unauthorized access into secure systems. Additionally, data leaks can result in hefty regulatory fines and legal challenges, especially if the leaked information includes personally identifiable information (PII) protected under data privacy laws.
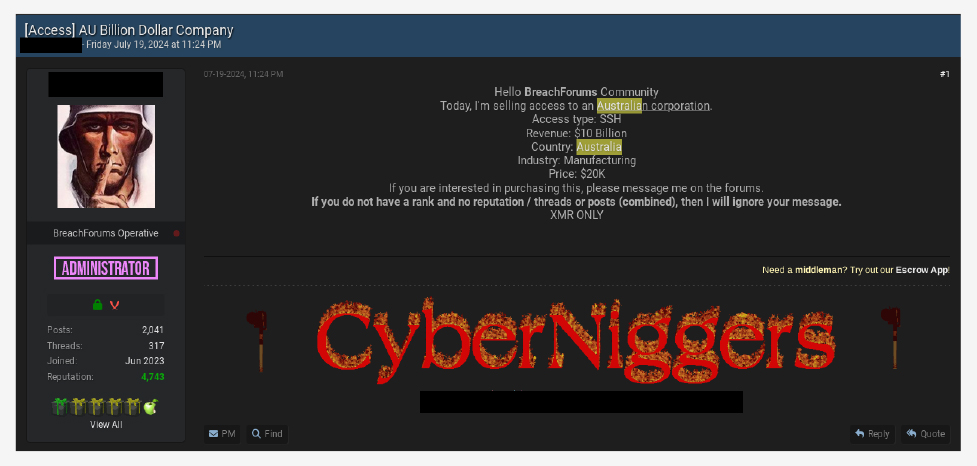
A well-known user on an Underground Forum is selling SSH access to an Australia-based manufacturing company.
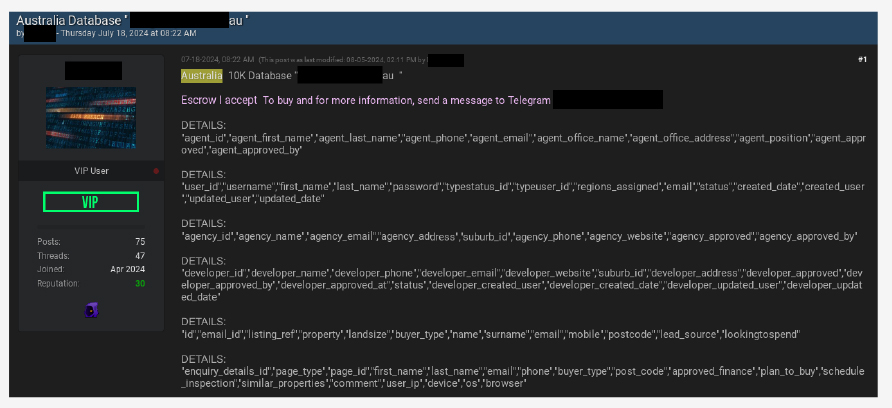
CYFIRMA observed a data leak related to an Australia-based organization. The leaked database contains 10,000 rows including first name, last name phone number, and more.
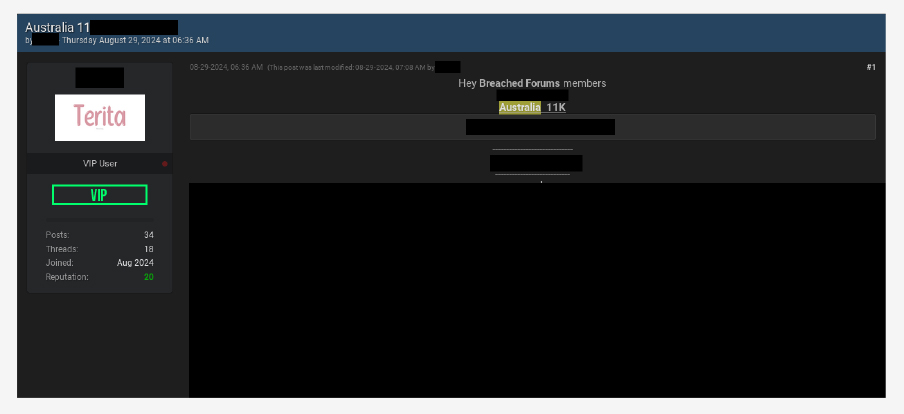
CYFIRMA observed a data leak related to an Australia-based marketing company. The leaked database contains 11,000 rows.
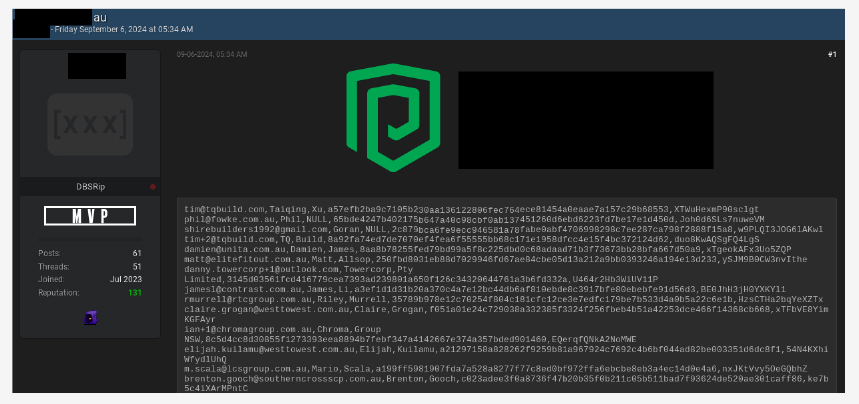
CYFIRMA observed a data leak related to an Australia-based construction service provider. The database contains 59,000 rows including email and hashed passwords.
CYFIRMA observed a data leak related to an Australia-based online platform for learning trading. The database contains 59,700 rows including first name, last name, email, passwords, and more.
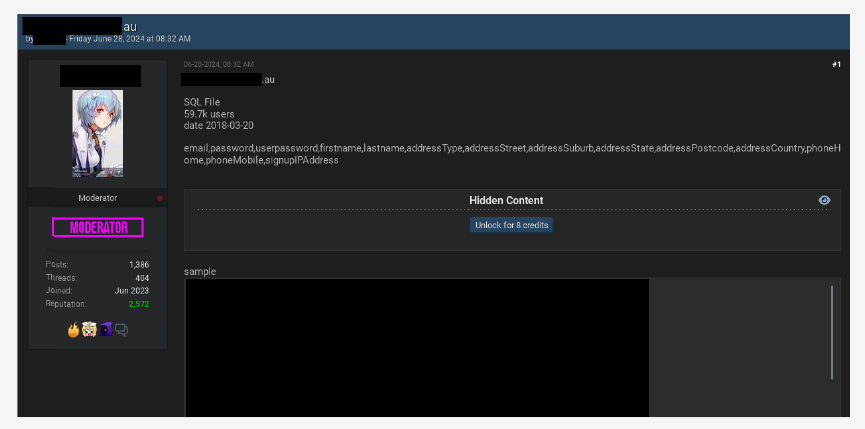
CYFIRMA observed a data leak related to a New Zealand-based beverage manufacturer. The database contains 6,969 rows of user data including first name, last name, email, password and more.
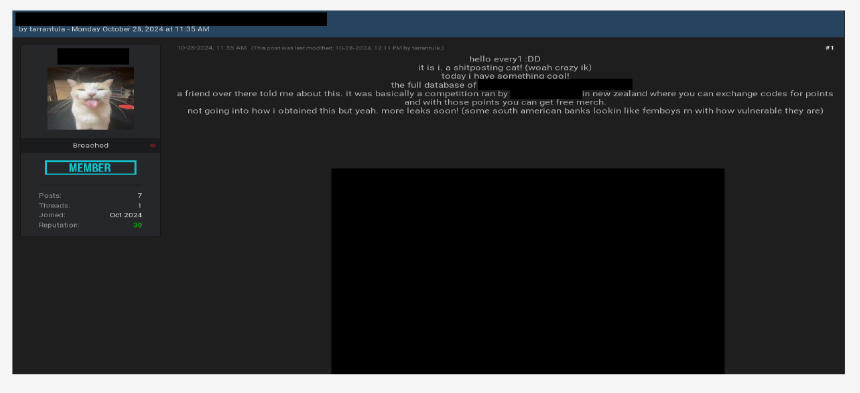
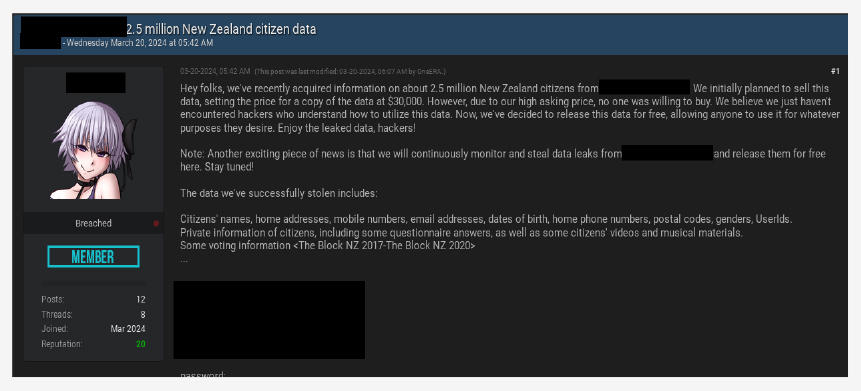
CYFIRMA observed a data leak related to a New Zealand-based radio network provider. The database contains 2.5 million rows of user data including names, phone numbers and more.
The Quantum of DDoS attacks increased globally after the start of the Russia-Ukraine war and Israel-Gaza conflict when pro-Russian, pro-Ukraine, and pro-Palestine hacktivists started targeting each other with DDoS campaigns and also started targeting alliance nations to show support to their respective country.
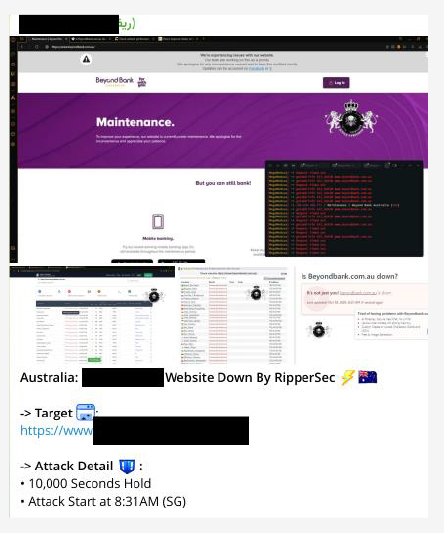
RipperSec is a Pro-Palestine hacktivist group that has conducted multiple DDoS attacks on an Australia-based organization.
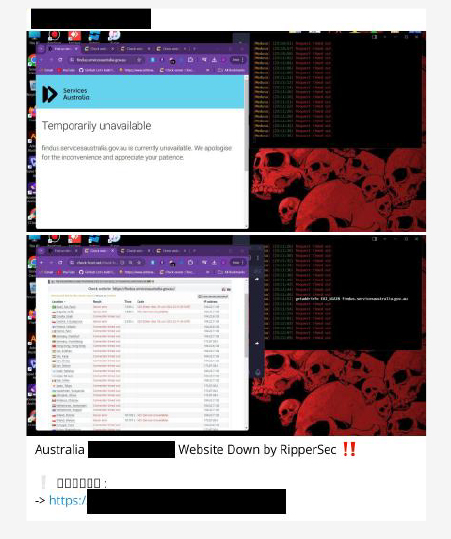
The same group targeted a Financial services provider based in Australia.
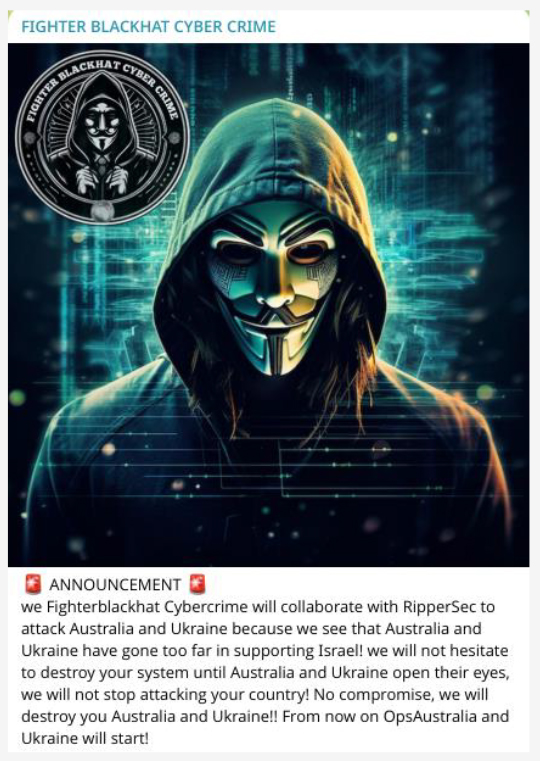
Fighter Blackhat Cyber Crime, an Indonesia-based hacktivist group, has announced a cyberattack against Australia and Ukraine. They have declared OpsAustralia and OpsUkraine to show their support for Palestine.
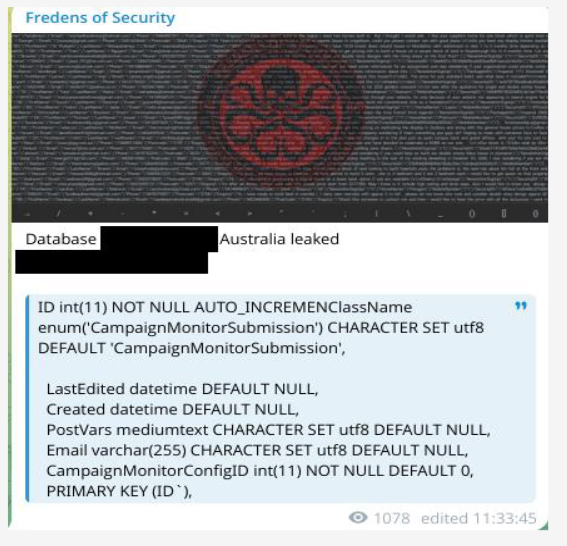
A threat actor named “Fredens of Security” has claimed to have leaked a database associated with the Australian region
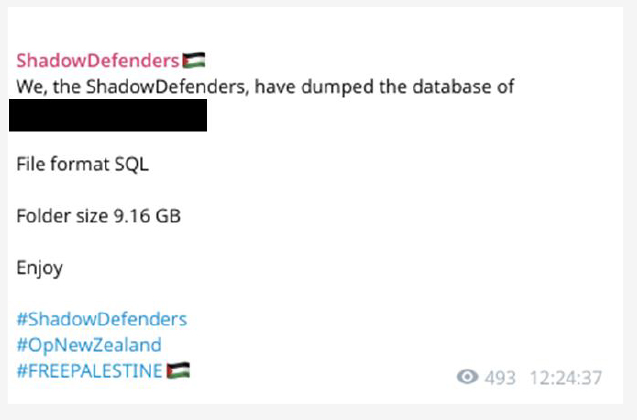
Another pro-Palestine hacktivist group “ShadowDefenders” has claimed to have leaked a database associated with the New Zealand region.
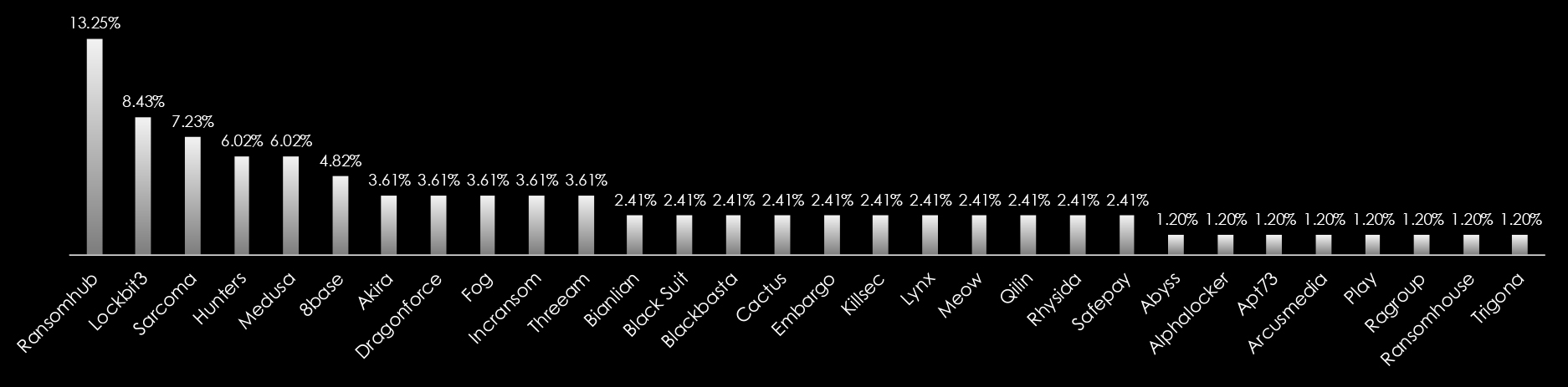
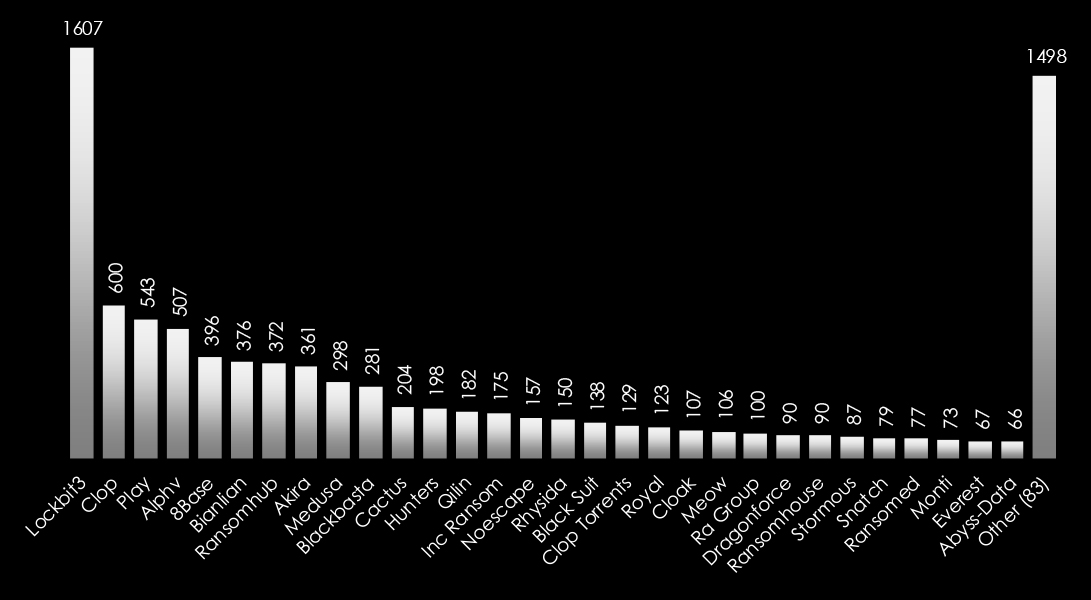
RansomHub ransomware is the most active group in Australia and has primarily targeted the Construction, Manufacturing, Hospitality, and Education sectors, affecting the largest % of victims at 13.25% among all targeted organizations.
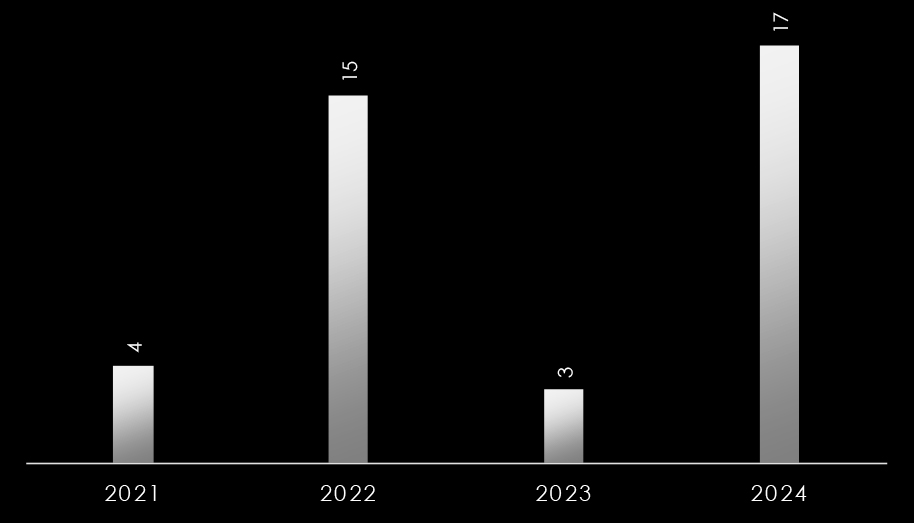
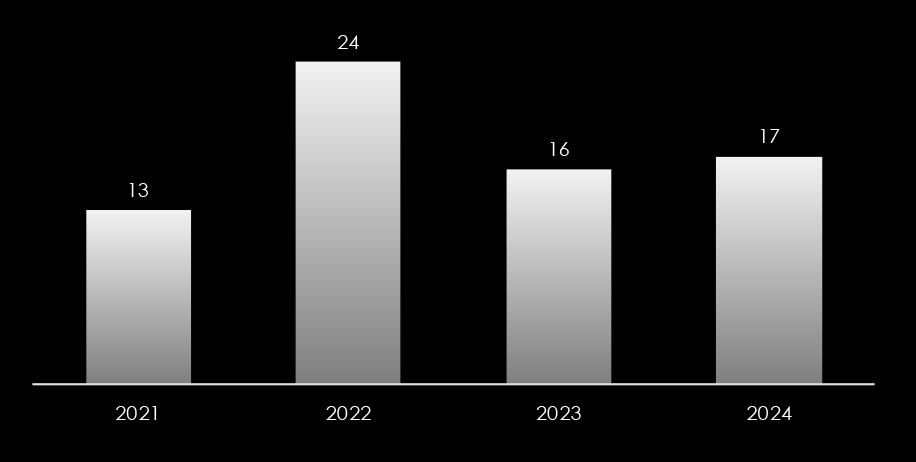
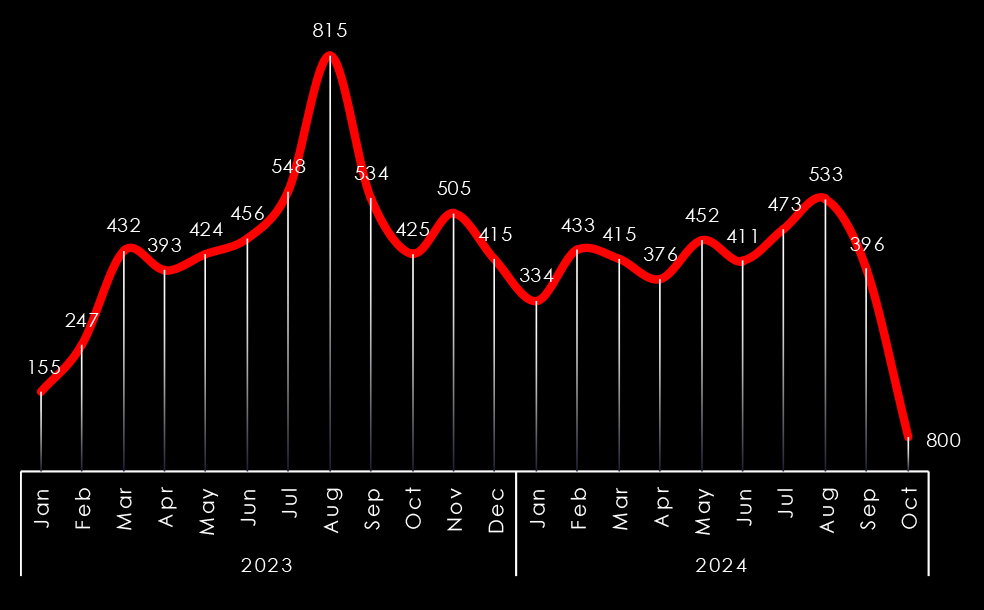
Ransomware attacks in New Zealand have fluctuated dramatically between 2021 and 2024. In 2021, the country experienced a minimal number of such incidents. However, 2022 saw a steep rise in ransomware attacks. This surge was followed by a notable decline in 2023, only to see a sharp increase once again in 2024, highlighting the volatile nature of cyber threats during this period.
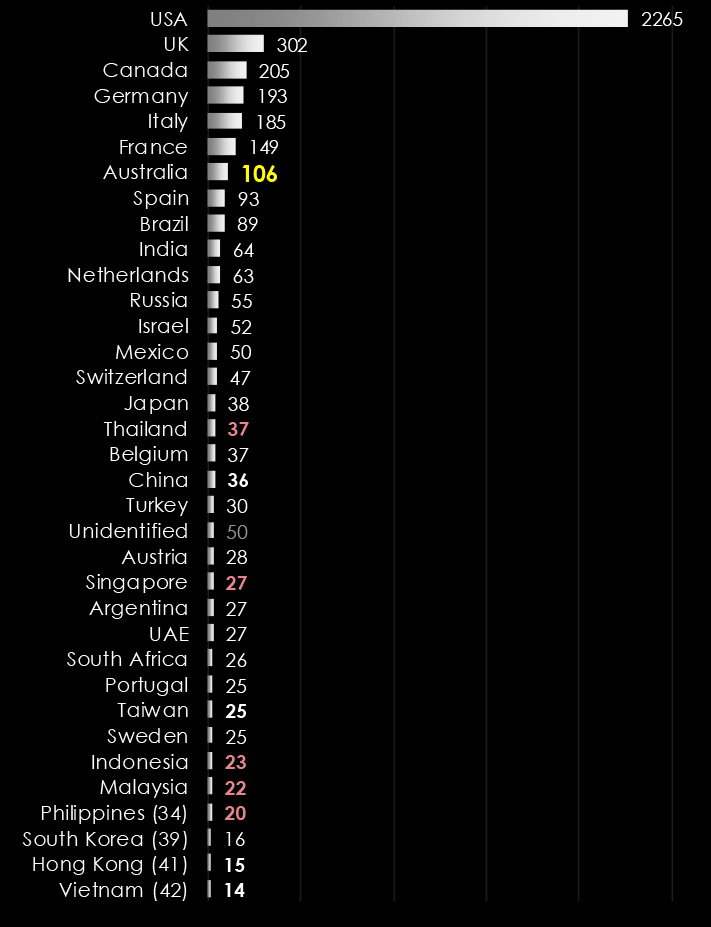
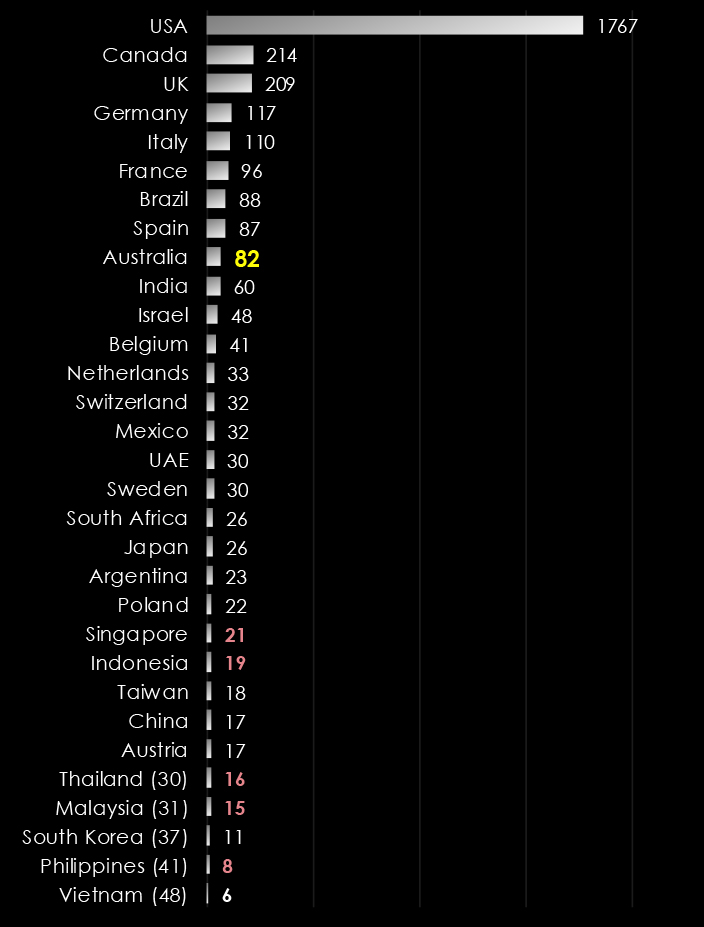
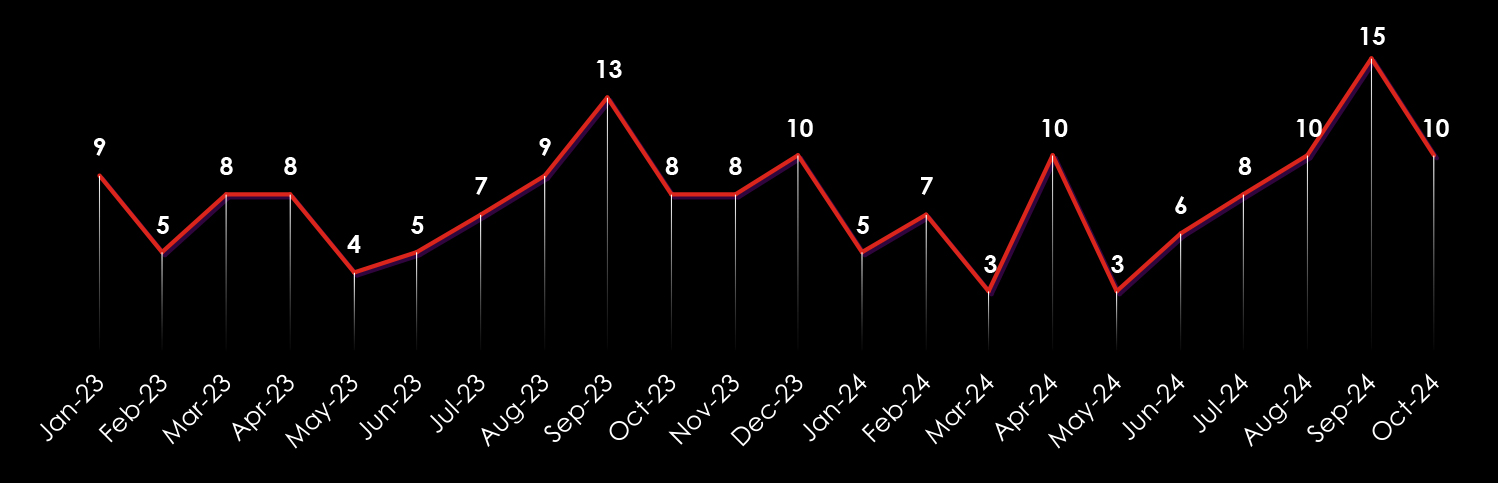
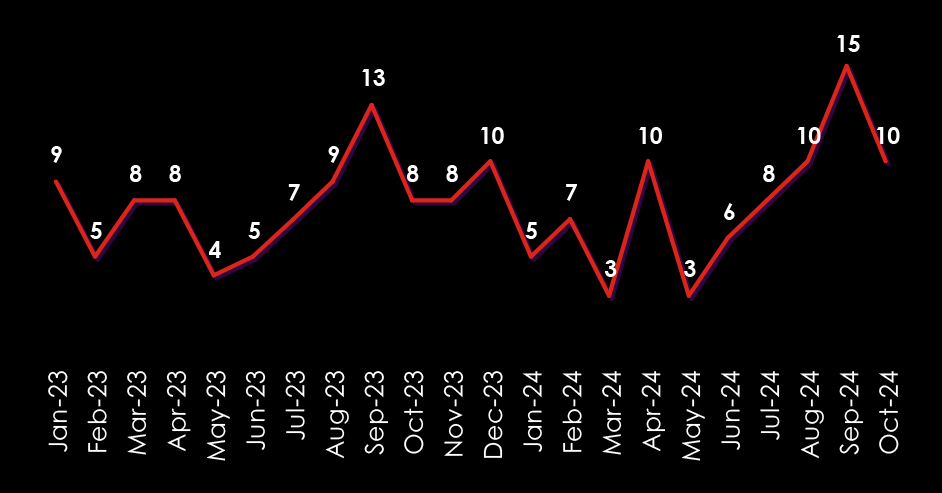
Observing the trends in victim numbers in Australia from 2023 until now shows somewhat significant growth during 2023, with a ramp-up in later months. The first three quarters of 2024 did not record many victims, most likely due to LockBit takedown.
This is in line with ransomware gangs expanding their focus from just the US and EU to the rest of the world, particularly Asia. Thanks to the affiliate Ransomware-as-a-Service programs, multi-lingual, global threat actors can deploy and execute some of the most dangerous ransomware like LockBit3.
The days of nearly exclusive Russian-speaking gangs solely targeting the US and EU are gone, and increasingly warming ties between Russia, China, and North Korea are showing in cybercrime and ransomware.
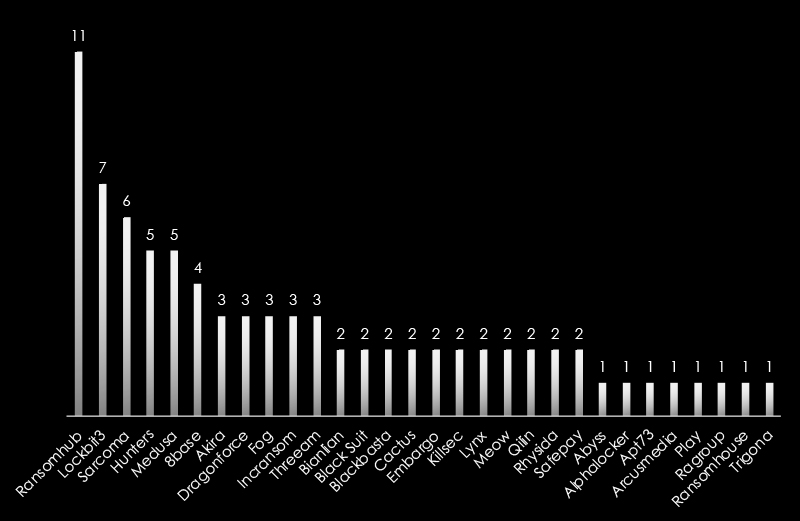
Since January 2024, ransomware incidents in Australia and New Zealand have highlighted a notable trend. Emerging groups like RansomHub, Sarcoma, SafePay, and others are increasingly targeting Australian entities, surpassing the activity of well-established groups such as Akira, Play, and others. These new actors demonstrate heightened aggression, likely aiming to exploit vulnerabilities with innovative tactics. Their dominance signals a shift in the ransomware landscape, emphasizing the need for proactive measures against evolving threats in the region.
Looking at the industries of identifiable ransomware victims in Australia and New Zealand, we can observe a diverse range of affected industries ranging from education to manufacturing.
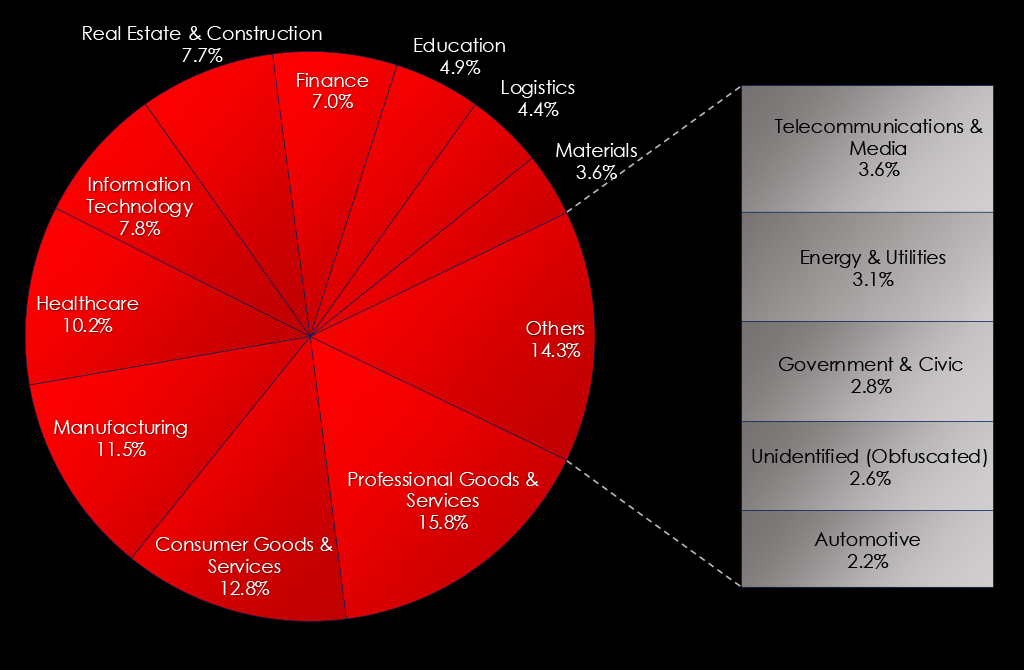
Since the start of 2023, Professional & Consumer Goods & Services have been the most frequent victims of ransomware. This is due to a high number of small and medium-sized businesses, including small law or accounting firms.
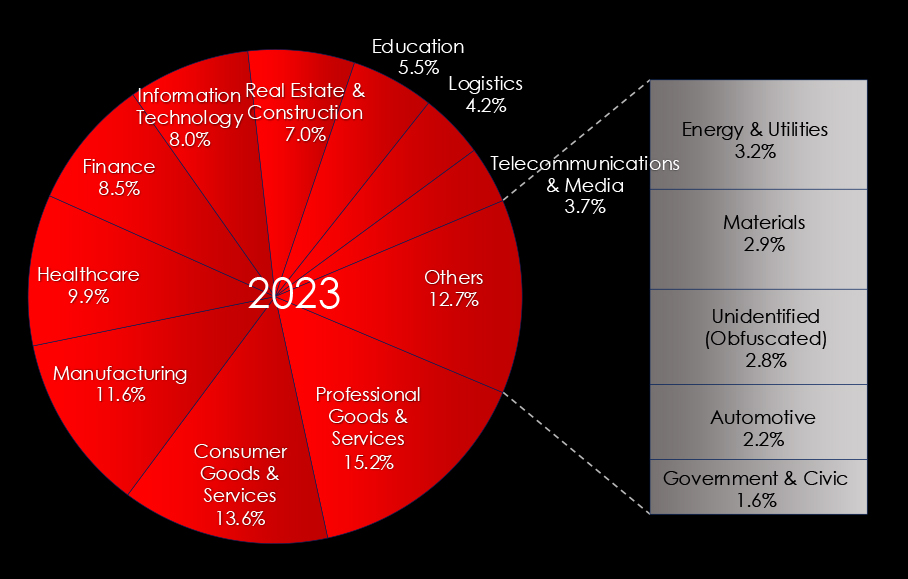
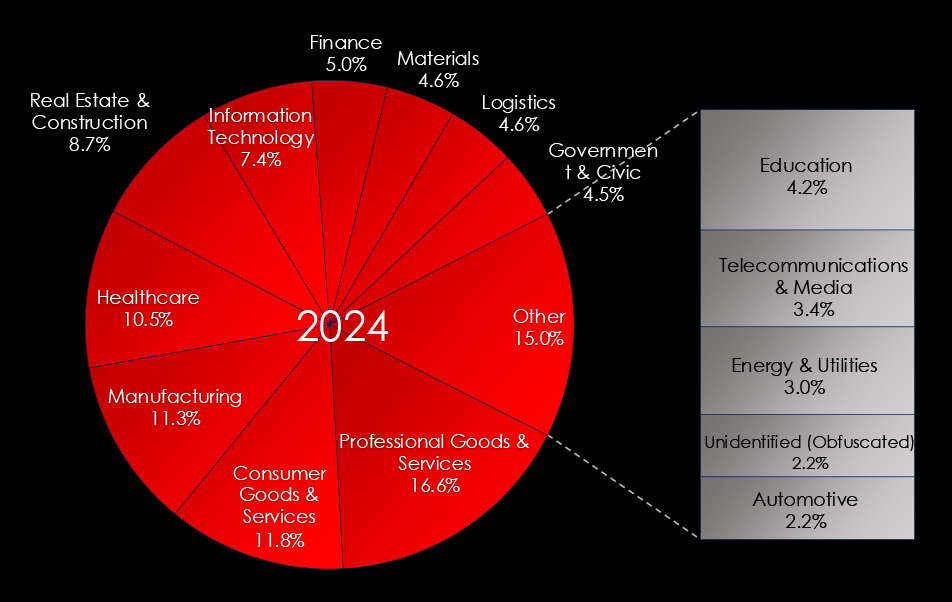
Separating 2023 and 2024 we can see some movements. For example, the Finance industry fell from 8.5% to just a 5.0% share of all victims, and Real Estate & Construction jumped up to 8.7% from 7.0%.
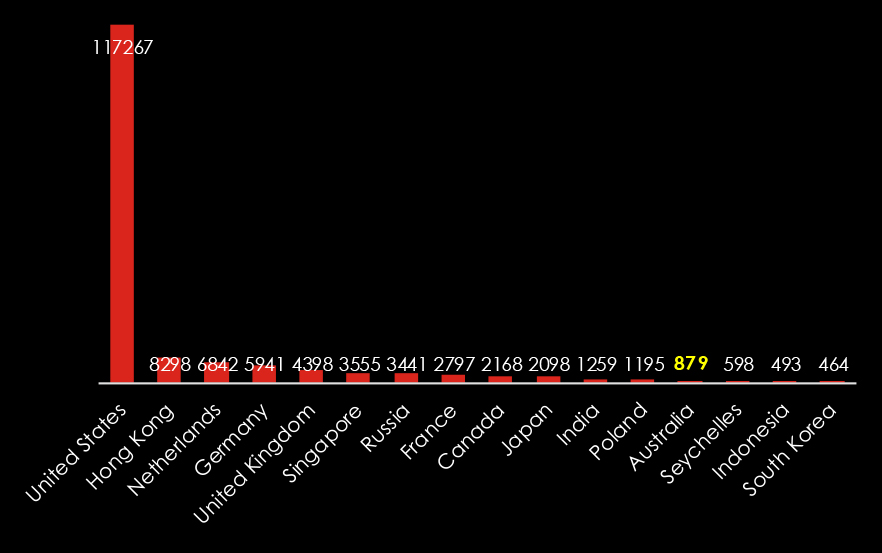
During the last 3 months period CYFIRMA’s advanced telemetry systems observed a total of 1,95,140 phishing campaigns.
This data represents the ASN-based origin of the phishing emails captured.
While the US remains the largest source by far, Southeast Asian countries are steadily growing as a source of Phishing attacks.
Australia ranked 13th overall.
Note: The US is the most targeted country by cybercrime and as a result, it also contains the most compromised devices used in botnets as proxies to deploy malware and send phishing around the world.
Narrowing down the selection of countries to the Asia-Pacific region we can have a more detailed view of the regional threat landscape.
Hong Kong stands out largely due to the fact it is commonly used by Chinese cyber criminals as a proxy to send phishing outside China. Similarly, Singapore is known for business-friendly hosting practices which also allow for malicious hosting as proxies. Furthermore, the good international reputation of Singapore allows attackers to bypass region-based IP blocking.
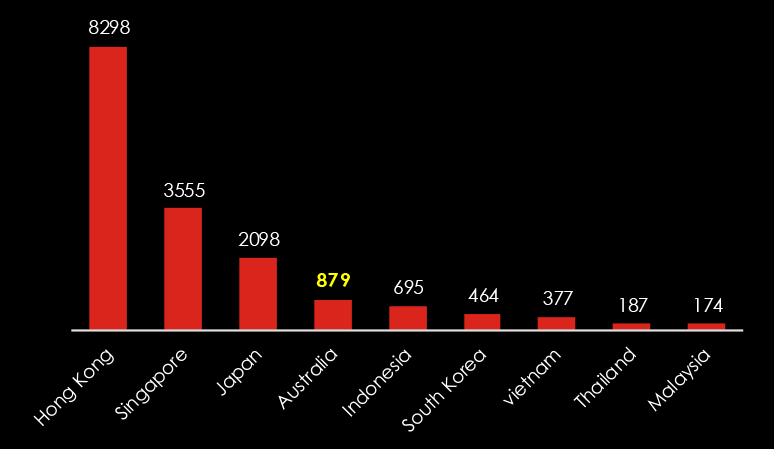
Looking at observed themes originating from Australia and New Zealand, the most prominent are Financial and Cloud Services, suggesting that local cybercrime is focused on local account takeovers. These accounts can be sold for a small price to be used for other malicious activities, such as spam or scams by more advanced threat actors.
These are generally considered low-hanging fruits using available info stealers malware sent by phishing as opposed to high-skill hacking. The high focus on financial themes implies that the main share of cybercriminals is financially motivated.
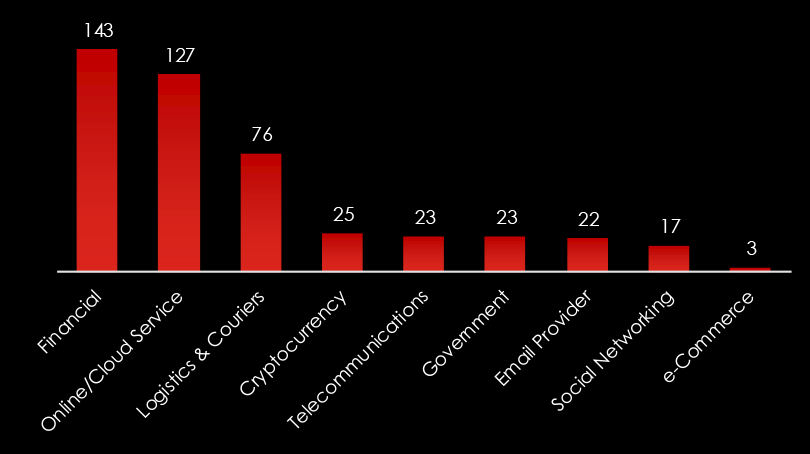
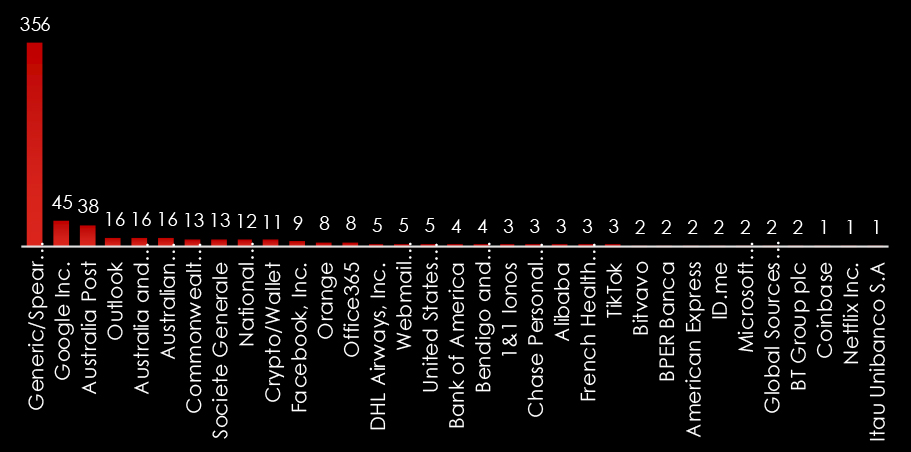
Drilling down into what specific brands are impersonated and in turn targeted by Australian-based campaigns, we see that Generic/Spear Phishing and Australia Post platforms are by far the most common.
We do observe a significant amount of Generic/Spear Phishing.
We can also see a lot of foreign brands, correlating with activities of advanced threat actors aiming abroad.
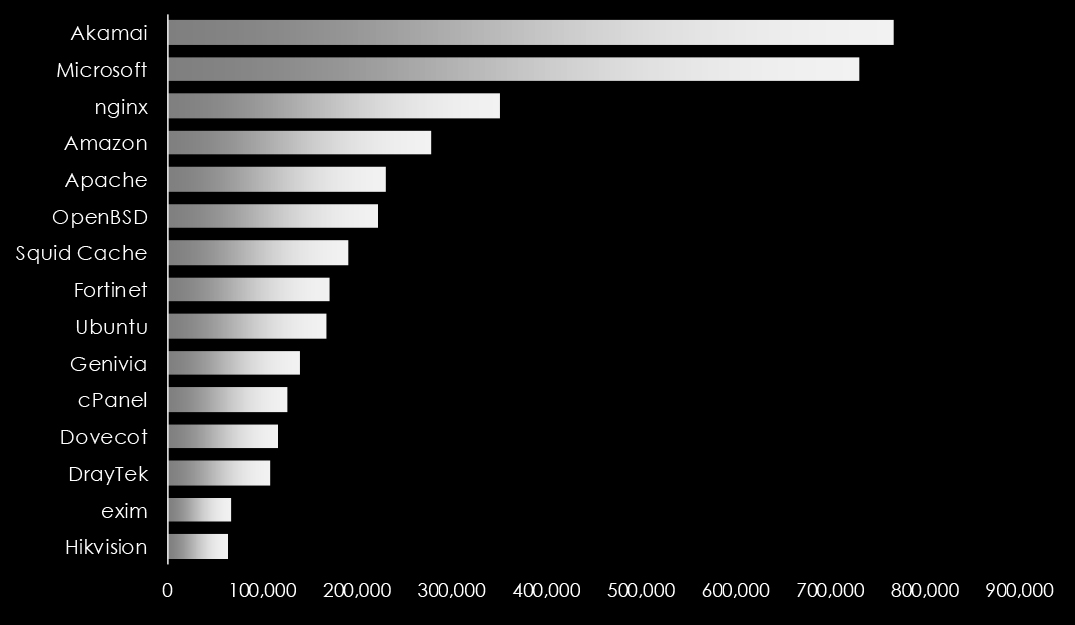
Exposed IoT devices play a significant role in cyber attacks due to their often inadequate security features and widespread adoption across various sectors. These devices can serve as entry points or targets in larger network breaches, primarily because they frequently lack robust encryption, undergo infrequent updates, and have default or weak credentials that are easily exploited. Once compromised, IoT devices can be used to form botnets, enabling attackers to conduct DDoS (Distributed Denial of Service) attacks, data breaches, or surveillance. Their connectivity and access to larger networks also make them a valuable asset for attackers looking to move laterally within infrastructure, escalate privileges, or disrupt critical services. This vulnerability is exacerbated by the rapid expansion of IoT devices in homes, industries, and cities without corresponding advancements in their security frameworks.
| Exploited Vulnerabilities | Vendor | Product |
| CVE-2021-26855 | Microsoft | Exchange Server (ProxyLogon) |
| CVE-2024-1709 | ConnectWise | ScreenConnect |
| CVE-2024-28995 | SolarWinds | SolarWinds Serv-U |
| CVE-2022-26134 | Atlassian | Confluence Server |
| CVE-2024-21887 | Ivanti | Ivanti Secure Connect and Policy Secure |
| CVE-2024-36401 | Geoserver | Geoserver |
| CVE-2023-20198 | Cisco | Cisco IOS XE |
| CVE-2023-4966 | Citrix | Citrix ADC and Citrix Gateway |
| CVE-2023-28771 | Zyxel | ZyXEL P660HN-T1A v1, ZyXEL P660HN-T1A v2, Billion 5200W-T |
| CVE-2024-43047 | Qualcomm | Multiple Chipsets |
| CVE-2023-6548 | Citrix | NetScaler ADC and Gateway |
| CVE-2023-20887 | VMware | Aria Operations |
| CVE-2024-40711 | Veeam | Backup and Recovery |