



This Asia Pacific (APAC) Threat Landscape Report provides a comprehensive overview of the evolving cybersecurity landscape in the region. In recent years, Asia Pacific has witnessed a significant increase in cyber threats, driven by factors such as rapid digitalization, increased internet penetration, and geopolitical tensions. This report aims to provide key insights into the current state of cyber threats, and emerging trends.
THE GEOGRAPHICAL SCOPE OF THIS REPORT
Japan, Bangladesh, Indonesia, Philippines, Vietnam
YET TO BE UPDATED
Australia, India, Malaysia, New Zealand, Singapore, South Korea, Taiwan, Thailand
UPDATED METHODOLOGY
This is a running report. Our research team will update this report on an ongoing basis to keep the reader updated on the evolving cyber threat landscape of the region.
Trend: Ransomware attacks on critical infrastructure
Motives: Disruption/Geopolitical/Extortion
Trend: Spyware, malware and plug-ins to collect data.
Motive: Reputation impact, disruption, extortion
Trend: Brute force attacks, credential reuse and data exfiltration via malware.
Motive: Operational disruption, espionage, IP exfiltration
Trend: social engineering/phishing. jump server Exploits, remote access tool compromise
Motive: Operational disruption, espionage, IP exfiltration
Trend: Device scanning, firmware, phishing/malware download
Motives: Disruption, data harvesting, remote attacks (DDOS)
Trend: Multi-behavioral malware (IT/OT, different operating system
Target: CII trade secrets documents containing proprietary processes
INCREASED SOPHISTICATION OF CYBER ATTACKS
The region has witnessed a rise in the sophistication of cyber attacks, with threat actors employing advanced techniques to compromise systems and networks.
TARGETED THREATS AGAINST CRITICAL INFRASTRUCTURE
The region has witnessed a rise in the sophistication of cyber attacks, with threat actors employing advanced techniques to compromise systems and networks.
RISE IN RANSOMWARE INCIDENTS
Ransomware attacks have surged in frequency and severity, posing significant challenges to businesses and government entities. The attackers often demand cryptocurrency payments for the release of compromised data.
NATION-STATE THREATS AND CYBER ESPIONAGE
Evidence suggests an increase in nation-state-sponsored cyber activities, including cyber espionage and information warfare. This poses significant geopolitical and security concerns for the region.
SUPPLY CHAIN VULNERABILITIES
The report identifies vulnerabilities in the regional supply chain, with cybercriminals exploiting weaknesses in third-party relationships to gain unauthorized access to targeted organizations.

TEXTILE INDUSTRY
When considering the Bangladesh threat landscape, the country’s prominent textile industry becomes a notable focal point for threat actors. Bangladesh stands as the world’s second-largest clothing exporter, second only to China. The textile manufacturing market in Bangladesh is on a growth trajectory, expected to expand from USD 17.99 billion in 2023 to USD 23.86 billion by 2028, with over 4,500 active factories. The clothing and textile sector accounts for a substantial 75% of the nation’s manufacturing employment and contributes significantly to Bangladesh’s GDP, exceeding 13%. Furthermore, textiles and related products constitute over 84% of export earnings. This industry’s lucrative nature, extensive supply chain interconnections, and economic impact make it an appealing target for threat actors interested in disrupting production, compromising trade secrets, and exploiting vulnerabilities, thereby influencing both the country’s economic stability and global trade dynamics.

SHIPBUILDING
The nation’s shipbuilding industry emerges as a significant point of interest for threat actors. Bangladesh, as a maritime nation with aspirations to become a developed economy by 2041 through the prospects of the Blue Economy, places a strategic emphasis on its shipbuilding sector. Presently, with over 200 shipbuilding companies, this industry wields substantial influence with its ability to generate considerable foreign currency through ship exports, drive employment opportunities, establish vital support for backward linkage industries, and significantly contribute to the national GDP. These attributes that make the shipbuilding industry a cornerstone of economic development, rendering it an appealing target for threat actors keen on disrupting economic stability, disrupting international trade, or compromising sensitive shipbuilding technologies, thus undermining Bangladesh’s path toward economic advancement and its maritime ambitions.

TOURISM
Bangladesh boasts breathtaking natural attractions like the Sundarbans, one of the largest mangrove forests globally, and Cox’s Bazar Sea Beach, the longest in the world, among others. These natural wonders position the country as a potential hotspot for local and international tourists. Presently, the tourism industry contributes 3.02% to the nation’s GDP and accounts for 8.07% of its total employment. Notably, the Bangladesh Tourism Board (BTB) has outlined an ambitious 25-year tourism master plan to attract 10 million tourists by 2040 and generate an annual revenue of $8 billion. While this vision holds the promise of increased inbound and domestic tourism and a boost in sector investment, it also garners the attention of threat actors who may seek to disrupt the sector’s growth, compromise the safety of travellers, or exploit vulnerabilities within the industry for economic or political gain, potentially hampering Bangladesh’s path to realizing its tourism aspirations.

INFORMATION TECHNOLOGY
Bangladesh is swiftly establishing itself as a prominent player in the global IT arena, successfully securing a significant share of the IT market in South Asia. This industry is acknowledged as one of the nation’s most promising sectors and is projected to reach a substantial valuation of USD 5 billion by 2025. Notably, the Information and Communication Technology (ICT) sector has already contributed 1.28% to Bangladesh’s GDP, while simultaneously creating over 300,000 jobs. The rapid growth and economic potential of the IT sector make it a prime target for threat actors who may seek to exploit vulnerabilities, engage in cyber espionage, or compromise sensitive information. This heightened interest from threat actors is driven by the industry’s potential for economic disruption, intellectual property theft, and its pivotal role in shaping Bangladesh’s technological future.

LEATHER INDUSTRY
Bangladesh’s leather sector is a well-established industry, ranking second in terms of export earnings. Thanks to its remarkable value, substantial growth prospects, and extensive employment opportunities, the leather industry has been accorded top priority status. Notably, Bangladesh captures a 3% share in the global leather and leather products market, with nearly 60% of its annual output being destined for export. Significantly, the government has formulated a forward-looking ten-year perspective plan that sets a target of elevating the leather sector’s export earnings to a range of $10-$12 billion by 2030. The appeal of this industry to threat actors is underpinned by the potential for economic disruption, exploitation of supply chain vulnerabilities, and the theft of proprietary designs and technologies, all of which could impede the sector’s growth and its vital role in shaping Bangladesh’s economic future.
Bangladesh, positioned as the world’s eighth most populous country with over 170 million people, is becoming a key player in the wider Indo-Pacific region. Despite its historical status as one of the world’s most destitute nations, sustained economic growth and social transformation have propelled Bangladesh into a new era of development. However, the geopolitical landscape in and around Bangladesh remains susceptible to instability and conflict, fueled by historical relations, demographic shifts, and the potential ramifications of climate change.
The region is currently navigating significant geostrategic challenges, primarily driven by the ascent of India and China as superpowers, with prominent issues such as the South China Sea disputes and Taiwan garnering attention. Meanwhile, Bangladesh’s economic rise has quietly reshaped the geopolitical dynamics, shifting South Asia’s economic center eastward and fostering the reintegration of an eastern subcontinent once divided by animosities and formidable borders.
The geographic proximity of Bangladesh to neighboring countries, including Nepal, Bhutan, China, and Burma, positions it as an attractive partner with growing diplomatic, political, and economic ties. India, in particular, has strengthened its relationship with Bangladesh, transforming a historically complex connection into a productive partnership with tangible outcomes in various sectors.
Amidst this geopolitical landscape, Dhaka’s orientation towards the Indo-Pacific, starting from the Bay of Bengal, holds strategic significance. However, the complexity of regional relationships is evident, with China expressing concerns over Bangladesh joining the Quad, a grouping aimed at countering Beijing’s influence. In addition, Bangladesh’s strategic location is of great value to China, prompting initiatives to build alternative routes and secure port facilities in the Indian Ocean and Bay of Bengal region.
The intricate network of international relationships in the region, shaped by history, geography, economy, and strategic interests, carries the potential for conflict escalation, particularly in cyberspace. Factors such as the Chinese economic slowdown, Western pressure on technology manufacturing relocation, and Russia’s increasing dependence on China add layers of complexity to the regional dynamics, with potential manifestations in trade policies, territorial disputes, military buildup, and cyber conflicts.
The looming prospect of a conflict over Taiwan adds a significant flashpoint to the regional security horizon, with cyber warfare anticipated to play a major role, presenting unprecedented challenges. While overt military confrontation remains distant, cyber-attacks targeting governmental and private entities are projected to rise as a means of enforcing boundaries.
In this evolving landscape, the overarching priority for businesses in the region is to strengthen common network security standards and cybersecurity practices across sectors, acknowledging the potential cyber threats arising from the intricate geopolitical dynamics shaping the Bangladesh threat landscape.
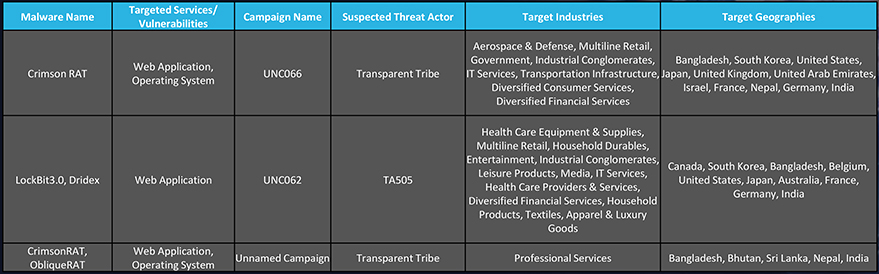
We observed 4 campaigns targeting various industries in Bangladesh during 2023. Russian, and Pakistan state-sponsored threat actors are behind most of these campaigns. Here are some details about observed sample campaigns.
A noticeable shift has been noted in the behavior of Russian threat actors. They are expanding the scope of their attacks to encompass additional geographic regions, extending beyond their traditional targets in North America and Western Europe to include the Asia-Pacific and EMEA. Furthermore, there are concerns that these threat actors may be considering retaliatory actions, either directly or indirectly, against the United States and its allied nations.
The motivations driving threat actors from Pakistan to target Bangladesh can be multifaceted and include a range of factors such as historical geopolitical tensions, economic interests, political and ideological motives, cyber espionage, and regional dynamics. These cyberattacks may serve purposes as diverse as exerting influence, economic gains, intelligence gathering, and proxy actions.
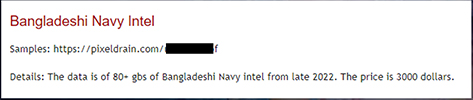
The CYFIRMA Research team observed the sale of 80 GB of Bangladeshi Navy intel from late 2022 for USD 3000.
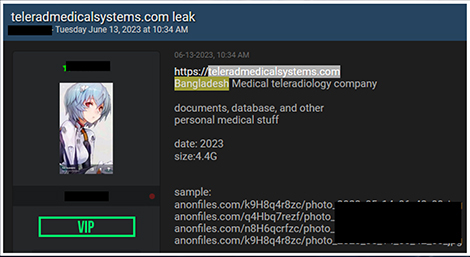
We observed a data leak related to Telerad Medical Systems Ltd (TMS). TMS is a Medical Equipment Importer, distributor, sales, supply, and service company in Bangladesh. Leaked data contains 4.4 GB of documents, databases, and other personal medical stuff.
Recently observed data leak of Bangladesh Police Database and files. Threat actor claims that these files were obtained in 2020 from the email account of a high-ranking Bangladeshi Police official.
Link3 Technologies Ltd data leaked in an underground forum. Link3 Technologies Ltd is a full-service IT Solution Provider that has been operating in the Bangladesh market for more than ten `years with a very high level of success, achieved through uncompromised service quality and customer satisfaction. Leaked data includes App installation and registered user data.


Ransomware groups target Bangladesh for various reasons, including the country’s increasing economic significance, growth in critical sectors like textiles and IT, and the potential for financial gains through ransom payments. Bangladesh’s expanding digital infrastructure and financial systems provide attractive targets for cybercriminals seeking to exploit vulnerabilities and encrypt critical data, thereby demanding ransoms. Additionally, its geopolitical location in South Asia and regional conflicts could make it a potential battleground for cyberattacks aimed at exerting influence and promoting political agendas. As a result, ransomware groups view Bangladesh as a lucrative target, leveraging these factors to advance their cybercriminal activities.

Recently, the ALPHV ransomware group infiltrated Bangladesh Krishi Bank’s network, extracting over 170 GB of crucial information. Their presence went undetected for 12 days, allowing them ample time to study internal documentation and steal valuable data. The compromised information includes highly sensitive financial records such as account details, statements, and tax information. The hackers also acquired employee data, including emails, passport copies, labour papers, and employment contracts, potentially exposing the personal information of the bank’s staff.


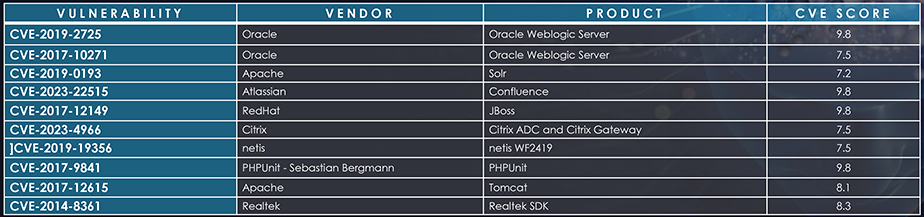
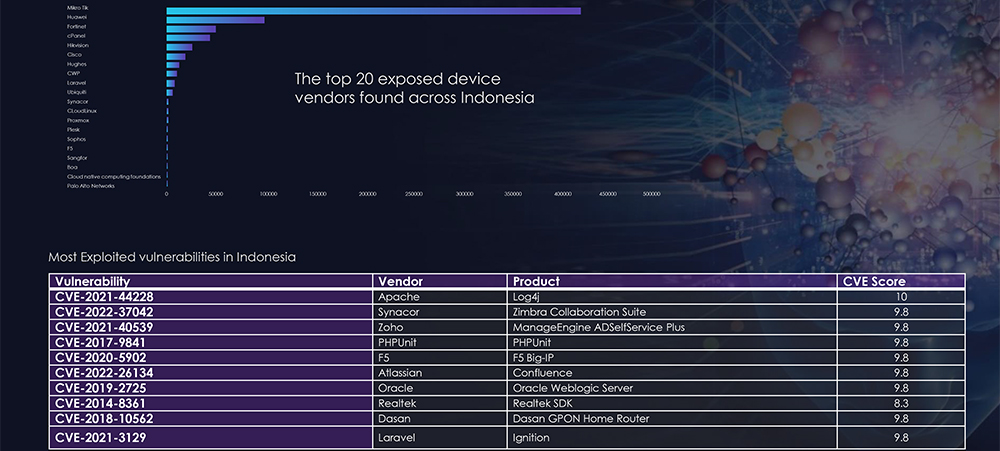
Most Exploited vulnerabilities in Bangladesh
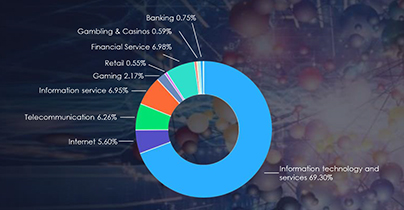
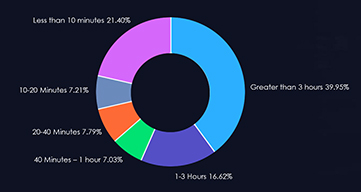
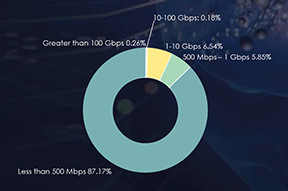
In the last six months, Bangladesh’s threat landscape has undergone a notable impact from distributed denial-of-service (DDoS) attacks, with the Information Technology and Services sector being particularly affected, representing a significant 69.30% of the attacks. Moreover, a substantial 39.95% of these attacks endured for periods exceeding three hours, indicating a prolonged and impactful threat scenario. Additionally, attacks within the one to three-hour duration range accounted for 16.62%, underscoring a notable proportion of sustained assaults. Examining bitrates, attacks with speeds ranging from 500 Mbps to 1 Gbps constituted 5.85%, while those with less than 500 Mbps made up the majority share at 87.17%. This diverse distribution highlights the necessity for a comprehensive and adaptive cybersecurity strategy to effectively mitigate the varying intensities of DDoS threats in Bangladesh.

Manufacturing Mastery: Manufacturing contributes significantly to Japan’s GDP, accounting for approximately 20%. This includes automobiles and industrial robots, to semiconductors and machine tools. Tokyo-based startups have ventured into supplying robots and satellites to the burgeoning global space industry, poised to generate over US$1 trillion in revenue by 2040.
Driving Forces in Automotive: Japan’s automotive industry ranks among the world’s largest, consistently securing a spot in the top three car manufacturing countries since the 1960s, even surpassing Germany. An array of companies produce a wide range of vehicles and engines, with prominent manufacturers like Toyota, Honda, and Nissan. This industry, including its global subsidiaries, remains under constant surveillance by financially motivated and APT threat actors keen on monetary gain and intellectual property theft.
Aerospace Excellence: Renowned for its global leadership in aerospace research and development (R&D), Japan’s space program encompasses various government ministries, offices, and agencies. The wealth of data within this industry serves as a prime target for APT actors, holding immense value.
Steel’s Global Dominance: Japan’s steel industry boasts advanced technology, particularly in the production of high-grade steel, giving it a competitive edge over its foreign counterparts. Ranking third globally in crude steel production, Japan produced 83.19 million tons in 2020. Operating on a global scale, the industry exports its domestically produced steel, particularly to rapidly developing Asian markets, while playing a pivotal role in supporting essential global infrastructure.
Thriving Fastener Industry: Japan’s fastener industry (i.e nuts, bolts, and screw manufacturing) is a formidable economic force, comprising of approximately 3,000 manufacturers, generating, yielding roughly one trillion yen worth of fasteners annually, along with about 400 distributors and trading companies yielding around 450 billion yen in annual revenue.
Japan’s diverse industrial sectors and cutting-edge technology products make it an appealing target for nation-state attackers and financially motivated threat actors. Furthermore, hacktivists have also been observed targeting Japanese industries alongside APT and other threat actors, reflecting the multifaceted cybersecurity challenges these sectors face.
From a geopolitical standpoint, Japan confronts substantial challenges stemming from China, Russia, and North Korea. These challenges relate to regional dominance, its strategic alliances with QUAD and NATO, as well as ongoing territorial disputes.
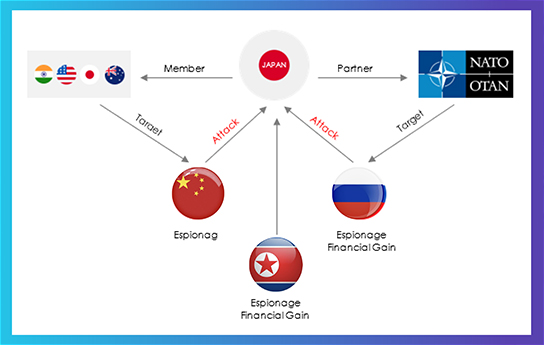

CHINA
Japan’s geopolitical risk factors in relation to China have shifted significantly in recent years. After World War II, Japan adopted a strong pacifist stance, prioritizing economic growth over military expenditure. However, the rise of China’s expansionist policies in the Indo-Pacific, particularly the looming threat of a Chinese invasion of Taiwan, has prompted Japan to reevaluate its security posture. Japanese Prime Minister Fumio Kishida’s announcement to double defense spending from one to two percent of GDP signifies a substantial departure from the country’s historical defense policy. This change, which builds upon the efforts of the previous Prime Minister Shinzo Abe, reflects Japan’s increasing focus on countering China and deepening military integration with the United States. As Japan strategically shifts military capabilities to its southwest islands, Taiwan emerges as a key flashpoint in its security considerations.
In essence, Japan’s evolving geopolitical risk factors with respect to China are characterized by a departure from decades of pacifism, a substantial increase in defense spending, a growing emphasis on countering Chinese influence, and a heightened awareness of Taiwan’s significance as a potential security flashpoint. These developments represent a significant transformation in Japanese security policy as it adapts to changing regional dynamics and challenges posed by China’s assertive posture in the Indo-Pacific.

NORTH KOREA
During the Cold War, Japan primarily focused on the threat posed by the Soviet Union, positioning its limited military capabilities in the northern regions. However, with the end of the Cold War, Japan shifted its attention towards the threat emanating from North Korea in the east.
In recent years, North Korea has been escalating tensions through a series of missile tests and nuclear posturing on the Korean Peninsula. The year 2022 witnessed unprecedented missile tests, including intercontinental ballistic missiles fired over Japanese territory. Furthermore, North Korea has strengthened its alignment with Russia and China, pledging closer strategic and tactical cooperation which enables North Korea to conduct more aggressive testing with relative impunity.
In addition to this, North Korea’s export of weapons to Russia for it’s war in Ukraine, possibly in exchange for cyber know-how and intelligence, raises concerns about the potential for North Korean cyber activities. Japan, along with South Korea and Australia, is among the most exposed geographies to North Korean cyber activities, however, North Korean threat actors are known for their opportunistic approach, engaging in criminal activities such as ransomware-based operations to generate financial profit wherever opportunities arise.

RUSSIA
Japan’s relationship with Russia has been strained due to a longstanding territorial dispute over the Kuril Islands, known as the Northern Territories in Japan. Recent developments indicate a significant change in Japan’s rhetoric concerning these disputed islands: Japanese Foreign Minister Yoshimasa Hayashi has accused Russia of occupying the Northern Territories without legal grounds, while Prime Minister Fumio Kishida asserted Japan’s sovereignty over them.
This shift in Japan’s stance follows Russia’s aggression in Ukraine and contrasts with the previous administration’s efforts to resolve the territorial dispute peacefully using softer language. While Russia’s current military capacity may not permit overt provocation, concerns have arisen about the use of cyberattacks to caution Japan not to overstep boundaries regarding the disputed islands.
Japan’s changing security posture is not occurring in isolation. It is part of a broader transformation in the U.S.-Japan alliance, involving South Korea, Australia, and the Philippines in defense alliances. This shift is in response to China’s assertive behavior in the region; a more capable North Korea, and Russia’s growing discontent, potentially leading to unpredictable actions against states with which it has territorial disputes.
These geopolitical factors require Japan to maintain a vigilant and adaptive approach to its national security and defense strategies.
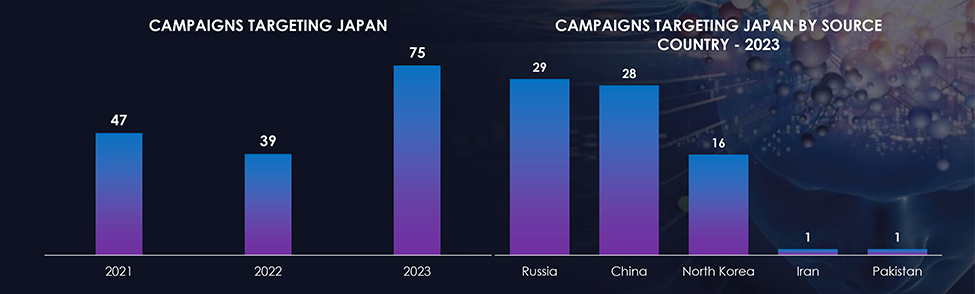
We observed 75 campaigns targeting various industries in Japan during 2023. Chinese, Russian, and North Korean state-sponsored threat actors are behind most of these campaigns.
The number of observed campaigns significantly increased compared to the last two years indicating threat actors’ interest in the economic and intellectual superpower; Japan.
In 2023, both Russian and Chinese threat actors actively targeted Japan. Meanwhile, North Korean threat actors doubled their campaign, compared to 2022 (8).
Recent incidents of data breaches have come to light in Japan. Here are some notable cases:

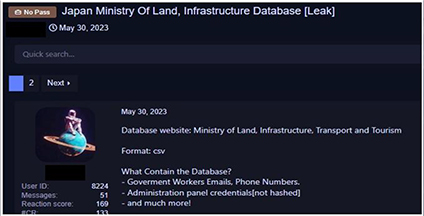
The research team observed a data leak associated with the Japanese Ministry of Land, and Infrastructure which contains employees’ email, phone numbers, and administration panel credentials.
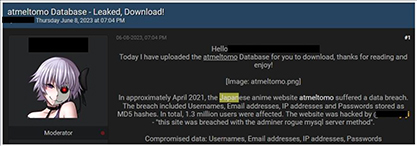
Japan’s foremost email friend search platform; Atmeltomo, experienced a data breach that subsequently became available for sale on a well-known hacking forum. This security incident led to the exposure of 1.3 million records, encompassing 580,000 distinct email addresses, as well as usernames, IP addresses, and MD5 password hashes.
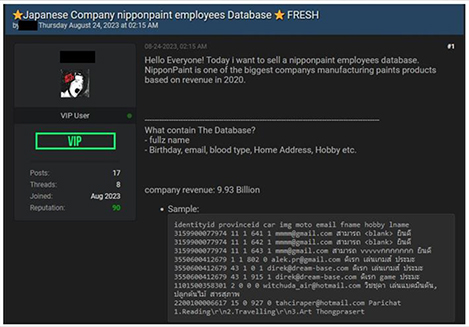
NipponPaint, one of Japan’s largest manufacturers of paint products, fell victim to a data breach that was later made available for purchase on a widely recognized hacking forum. This cybersecurity incident resulted in the compromise of the company’s employee database, which included personal details such as names, birth dates, email addresses, blood types, addresses, hobbies, and more.
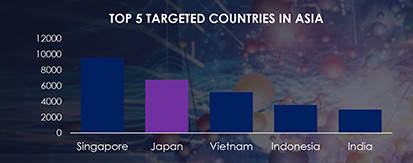
During the period spanning from January 1st to December 1st, CYFIRMA’s advanced telemetry systems meticulously detected a staggering total of 720,038 phishing campaigns. Within this extensive dataset, it’s noteworthy that Japan emerged as the second-most targeted geographic region in Asia.
The observed campaign in Japan reveals several prominent themes exploited in phishing attacks. Among these, the sectors most frequently targeted include Government, Financial, Social Networking, Online/Cloud Services, and Transportation. These findings shed light on the diverse range of sectors that malicious actors are leveraging to carry out phishing attacks within Japan. Understanding these prevalent themes is crucial for enhancing cybersecurity measures and safeguarding against the evolving tactics employed by cybercriminals.


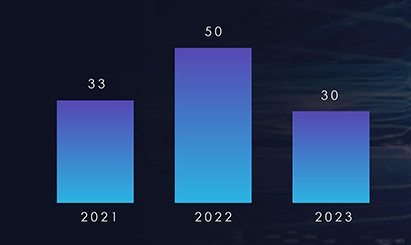
Japan stands out as one of the most prominent targets of ransomware attacks in the Asia Pacific region. Among the sectors within Japan, the automotive, manufacturing, IT, and entertainment industries have experienced the most pronounced impact from these ransomware incidents. Notably, this threat landscape is influenced by formidable ransomware groups, including LockBit, BlackCat (Alphvm), and Cl0p, who feature prominently on the list of perpetrators targeting Japanese companies.
During our Open-Source Intelligence (OSINT) investigation, we discovered a substantial volume of internet-connected devices and systems linked to Japan. Specifically, our search revealed a staggering count of approximately 300,000 systems that exhibit vulnerabilities within the multiple versions of the Apache HTTP Server. These vulnerabilities span a spectrum from critical to medium severity, underscoring the potential risks associated with this widespread exposure.
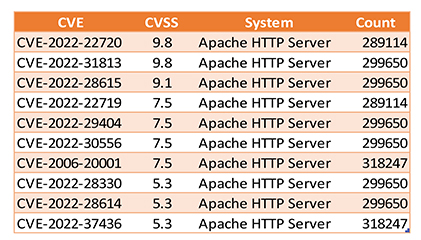

JVN trend depicts increased exploitation of vulnerability spread across various IT products.
Note: JVN, which stands for Japan Vulnerability Notes, is a portal site on IT product vulnerability information handled in the Japanese framework called “The Information Security Early Warning Partnership”. It provides detailed information on each vulnerability including a summarized description, affected products, possible impacts, solutions, vendor statements, and reference documents.
The exploitation of vulnerabilities, particularly zero-day vulnerabilities, serves as a favored entry point for threat actors seeking to bypass detection mechanisms. Notably, both Chinese and Russian threat actors have gained notoriety for their adeptness in leveraging zero-day exploits as part of their espionage efforts. Moreover, these threat actors actively seek opportunities to launch supply chain attacks, aiming to compromise a wider attack surface. This multifaceted approach underscores the continually evolving tactics employed by these adversaries. Given Japan’s expansive industrial sectors and the significant shift towards industrial automation, it becomes paramount to emphasize the critical importance of effective vulnerability management. This approach is essential to secure various aspects of the technology landscape, including Operational Technology (OT), Industrial Control Systems (ICS), IoT devices, and all interconnected systems, ensuring the continued integrity and security of Japan’s critical infrastructure.

The Quantum of DDoS attacks increased globally after the start of the Russia-Ukraine war when pro-Russian and pro-Ukraine hacktivists started targeting each other with DDoS campaigns and also started targeting alliance nations to show support to their respective country. Japan is the most targeted country in Asia by pro-Russian hacktivists. Recently we observed a Russian hacktivist group launching DDoS attacks on Japanese Organizations in response to Japanese government general secretary Hirokazu Matsuno’s announcement of “tough anti-Russian measures”.
Overall, we observed 31 campaigns targeting Japan. Government Institutions, Transportation, and Manufacturing are the most targeted industries by pro-Russian hacktivists.
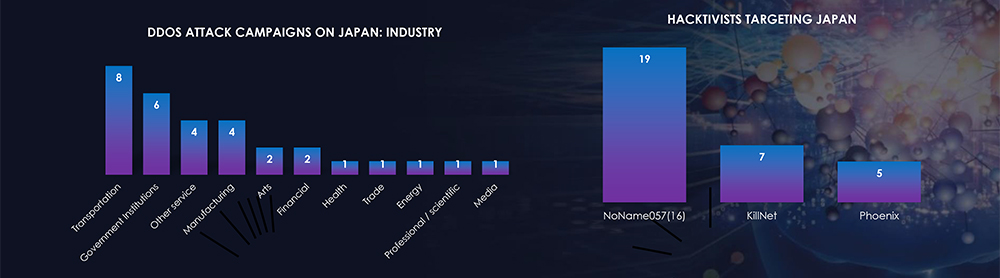
Along with the pro-Russian hacktivists threat, Anonymous Italy recently re-launched cyberattacks against nuclear power-linked groups in Japan as part of an operation called #OpFukushima which was initiated earlier in April 2021. The campaign was launched to protest against the Government’s plan to release the treated radioactive water from the Fukushima nuclear plant into the sea. In the campaign, hacktivists started targeting the Japan Atomic Energy Agency, Japan Atomic Power Co., the Atomic Energy Society of Japan, and associated companies.
The cyber threat landscape extends beyond Japan’s geographical borders, with overseas subsidiaries and affiliated companies emerging as appealing targets for threat actors seeking access to global Japanese brands. In recent large-scale attacks on Japanese enterprises, adversaries have strategically chosen to compromise these overseas entities as a gateway into the networks of their Japanese counterparts. Several key factors contribute to this approach:
Varied Security Oversight: overseas affiliates often exhibit varying levels of security oversight compared to their Japanese counterparts. This discrepancy can make them more vulnerable entry points for attackers.
Security Vulnerabilities via Acquisitions: the acquisition of overseas firms can introduce pre-existing security vulnerabilities into the parent company’s network. Additionally, it may lead to the development of separate security hierarchies that do not align with the security culture of the parent company, creating potential weak links in the overall defense.
Language Barriers: language barriers can also play a role in this strategy. Attackers may exploit communication challenges to infiltrate Japanese companies through overseas partners, taking advantage of gaps in understanding and coordination.

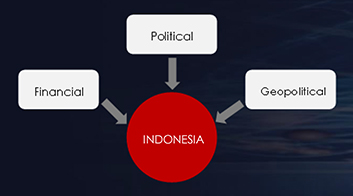
Financial Motivation: Indonesia is the largest economy in Southeast Asia and possesses abundant natural resources. This makes it an attractive target for cybercriminals seeking financial gains through activities such as hacking into financial institutions, conducting ransomware attacks, or stealing sensitive financial data.
Political Motivation: Indonesia is the world’s fourth most populous country and has a diverse political landscape. Political motivations for targeting Indonesia could include influencing elections, destabilizing the government, or compromising political figures or organizations.
Geopolitical Motivation: Indonesia’s strategic location in Southeast Asia, along with its large population and economic potential, makes it an important player in regional and global geopolitics. Threat actors with geopolitical motivations target Indonesia to gain a competitive advantage, disrupt regional stability, or gather intelligence.
TRENDS IN THE INDONESIA THREAT LANDSCAPE
Growth in economic activities in Indonesia especially in various industrial sectors like manufacturing, eCommerce, Travel and Tourism, Infrastructure, Construction, Mining, and Aviation attracts financially motivated threat actors, state-sponsored threat actors, and other threat actors who are interested in data leaks.
The surge of eCommerce has been a notable trend, intensifying even more in the post-pandemic era.
Russian, Chinese, and North Korean threat actors actively target Indonesian organizations.
Cyber-attacks on Indonesian organizations not only do financial and reputational damage but also have a negative impact on attracting investments from potential global investors.
Despite government efforts, Indonesia’s digital literacy remains moderate.
The South China Sea disputes, involving territorial claims and maritime rights, have become a focal point of geopolitical contention. China’s assertion of sovereignty over a significant portion of the South China Sea has led to territorial tensions with neighboring countries, including Indonesia which will continue to create in chaos in the region.
MANUFACTURING
With Indonesia ambitiously aiming to secure a position among
the world’s largest economies by 2030, the manufacturing sector has become an appealing target for cyber threats. Threat actors may seek to exploit vulnerabilities within the manufacturing infrastructure for various reasons, including potential economic disruption, theft of intellectual property or industrial espionage.
INFRASTRUCTURE AND CONSTRUCTION
The Indonesian government’s substantial investment commitment of $430 billion from 2020 to 2024 amplifies the sector’s significance, making it a focal point for both economic development and potential cyber threats. As outlined in a report by PwC. The critical areas of roads, tolls parts, airports railways, water and power plants in Indonesia present significant opportunities for investment but also pose cybersecurity challenges. Threat actors may be drawn to this sector due to the potential for financial gains, the large-scale impact of disruptions to critical infrastructure, and the myriad of interconnected system susceptible to cyber-attacks
TRAVEL AND TOURISM
The diversity of Indonesia comprising a huge number of islands each offering a unique atmosphere makes it particularly appealing to international travellers. The surge in foreign tourist arrivals further highlights the industry’s resilience, following the easing of pandemic restrictions. Threat actors are likely interested in this sector due to its economic importance, the sheer volume of transactions and the potential for exploiting vulnerabilities in the complex travel ecosystem, including booking systems, personal data records and payment processes.
MINING
Indonesia stand as a significant player in the global mining industry, renowned for its substantial production of coal, gold, tin, copper, and nickel. Indonesia’s mining sector is poised to emerge as one of the top potential leading industries within the country. This prominence, however, also attracts the attention of threat actors within the cybersecurity realm. The strategic importance of the mining industry in Indonesia, contributing significantly to the country’s economy, makes it a lucrative target for cyber threats. Threats actors may be interested in exploting vulnerabilities within the mining sector for various reasoms, including potential financial gains, stealing sensitive geological data, disrupting operations or engaging in industrial espionage.
AVIATION
With Indonesian airports experiencing a surge in air traffic and the expansion of infrastructure to cater to tourist destinations, the need for robust cybersecurity measures is crucial to safeguard against potential cyber threats and ensure the resilience of the aviation industry’s operations. The areas of growth highlighted by the international trade administration, including enhancements to ground infrastructure, runways and air traffic systems present specific points of interest for threat actors seeking to exploit potential vulnerabilities within the aviation sector.
eCOMMERCE
In the Indonesian threat landscape the surge of eCommerce has been a notable trend, intensifying even more in the post-pandemic era. Dominated by platforms such as Tokopedia and Shopee, online shopping has gained significant traction, with a Deloitte survey indicating that 31% of Indonesians opt for online shopping due to its convenience and practicability. This dynamic eCommerce landscape not only presents opportunities but also presents ample opportunities for cybercriminals to exploit vulnerabilities, engage in data theft for monetization on the dark web, and conduct fraudulent transactions.
The Asia-Pacific region, with its significant population and pivotal role in global trade, is a focal point for geopolitical competition, primarily exemplified by the rivalry between the United States and China. Indonesia, as Southeast Asia’s largest economy, holds a vital position in this landscape, thanks to its economic growth and control of critical sea lanes. This competition is compounded by multifaceted geopolitical threats stemming from complex regional relations, demographic shifts, and climate change.
Notably, China’s ascent as a superpower shapes the key geopolitical concerns in the region, with the South China Sea disputes and the Taiwan issue at the forefront. China’s territorial claims extend to the South China Sea, including Indonesia’s exclusive economic zone in the Natuna Sea. This has led to territorial tensions, with near-armed conflict in 2019 and 2020.
Indonesia’s foreign policy historically emphasizes nonalignment, aiming to balance relations with the United States and China. Recent efforts have seen the mending of relations with China, with growing economic ties and political interactions. Simultaneously, Jakarta maintains strong security ties with the United States.
However, these developments strain relations with China, and as regional countries assert their sovereignty and economic interests, tensions could rise. Cyber espionage activities primarily target government entities but are expected to expand to non-governmental organizations and commercial entities. The Asia-Pacific region houses some of the world’s most active state-sponsored cyber actors, led by China, followed by Russia and North Korea, while India emerges as an aspiring cyber power.
The potential flashpoint in the regional security landscape centers around the Taiwan issue, with cyber campaigns likely preceding any conflict. While overt military confrontations remain unlikely, cyberattacks targeting various entities are projected to increase. Strengthening network security standards and cybersecurity practices is the top priority for businesses, as regional stability and economic prosperity depend on cybersecurity resilience in this volatile geopolitical environment.
We observed 5 campaigns targeting various industries in Indonesia during 2023. Chinese, Russian, and North Korean state-sponsored threat actors are behind most of these campaigns. Here are some details about observed sample campaigns.
Chinese state-sponsored threat actors targeting Indonesia could be motivated by various factors, including economic interests, geopolitical considerations, and regional dynamics. Economic espionage may drive attempts to acquire trade secrets and intellectual property, providing China with economic advantages. Geopolitical tensions or strategic interests in the Asia-Pacific region could lead to cyber activities aimed at gathering intelligence, exerting influence, or addressing security concerns. Additionally, the pursuit of military intelligence, political influence, or access to valuable resources in Indonesia may contribute to the motivation behind these state-sponsored cyber operations.
A discernible change is observed in the conduct of Russian threat actors. They are broadening their range of attacks to include additional geographical regions, such as the Asia-Pacific and EMEA, in addition to their typical targets in North America and Western Europe. Moreover, there is speculation that these actors might be planning retaliatory attacks, either directly or indirectly, against the United States and its allied nations.
In May 2023 LockBit Ransomware group successfully compromised Bank Syariah Indonesia (BSI), a subsidiary of the state-owned enterprise Bank Mandiri. The cyberattack resulted in the acquisition of 1.5 terabytes of data, including nine databases containing information about the bank’s employees and more than 15 million customers. The stolen databases contained sensitive data such as customers’ full names, phone numbers, addresses, proprietary documentation, account numbers, card numbers, NonDisclosure Agreements (NDAs), transaction histories, contracts, and passwords. Following the breach, LockBit demanded a ransom of US$20 million. However, negotiations between BSI and the ransomware group broke down, leading LockBit to publish the stolen data on various underground leak forums. This exposure heightened the risk of cyberattacks and scams targeting BSI clients and employees. In addition to the immediate consequences, the data breach poses long-term risks. Efforts to attract global investors may be adversely affected, and the bank faces potential legal consequences, including lawsuits and penalties.

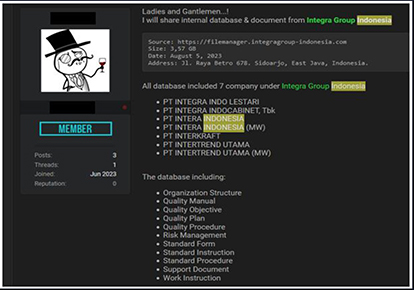
Integra Group (www[.]integragroup-indonesia[.]com); Indonesia’s largest wood manufacturer group, was compromised. An unknown threat actor advertised 3.57 GB data of 7 companies under Integra Group.
Badan Tenaga Nuklir Nasional (BATAN) is an Indonesian Non-Ministerial Government Institution tasked with carrying out government duties in the field of research, development, and utilization of nuclear energy data that got compromised and leaked in an underground forum. Leaked data contains the employee’s name, email address, and password.

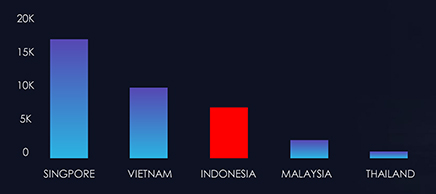
During the period spanning from January 1st to October 12th, CYFIRMA’s advanced telemetry systems meticulously detected a staggering total of 568,521 phishing campaigns. Within this extensive dataset, it’s noteworthy that Indonesia emerged as the Third-most targeted geographic region in Southeast Asia.

The observed campaign in Indonesia reveals several prominent themes exploited in phishing attacks. Among these, the sectors most frequently targeted include Social Networking, Logistics and Couriers, Financial, Online/Cloud Services, and Email Providers. These findings shed light on the diverse range of sectors that malicious actors are leveraging to carry out phishing attacks within Indonesia. Understanding these prevalent themes is crucial for enhancing cybersecurity measures and safeguarding against the evolving tactics employed by cybercriminals.
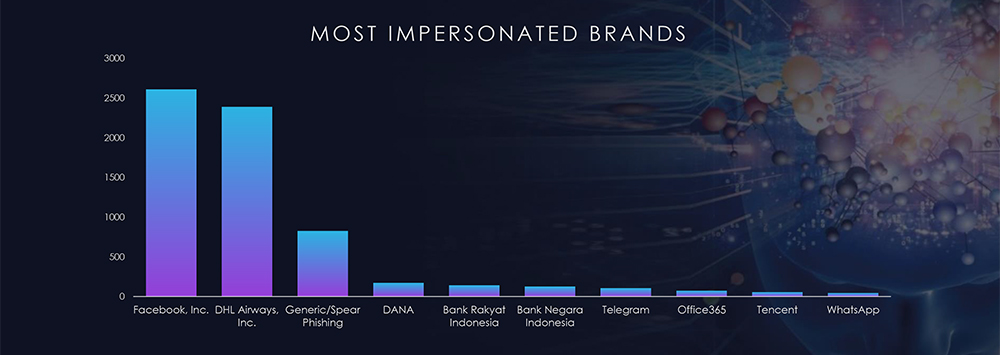

Ransomware groups target Indonesia due to its significant and growing economy, increasing digital transformation, potential vulnerabilities in cybersecurity practices among certain organizations, geopolitical and economic motivations, the widespread use of cryptocurrencies, relative lack of cybersecurity awareness, regional and global connectivity, and, in some cases, political instability. The country’s expanding digital infrastructure and the perceived financial capacity of high-profile targets make it an attractive environment for cybercriminals seeking substantial ransom payouts. Notably, this threat landscape is influenced by formidable ransomware groups, including LockBit, BlackCat (Alphvm), and 8Base, which feature prominently on the list of perpetrators targeting Indonesian companies.
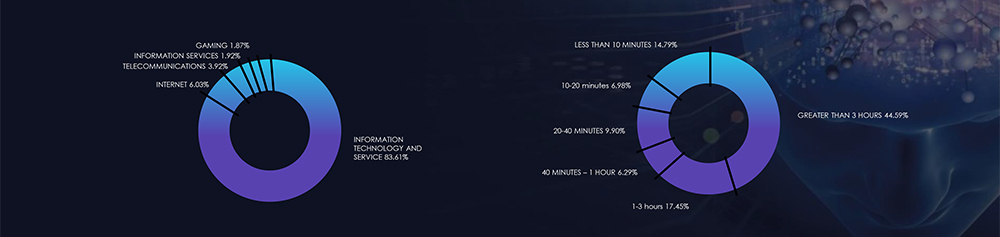
Over the past six months in Indonesia, the threat landscape has been significantly impacted by distributed denial-of-service (DDoS) attacks, with the Information Technology and Services sector bearing the brunt, accounting for a substantial 83.61% of the attacks. Internet-related services also faced notable disruptions at 6.03%, followed by the Telecommunications sector at 3.92%. Information Services, Gaming, and Retail were subject to lower but still impactful percentages, with 1.92%, 1.87%, and 0.59%, respectively. Sectors such as Financial Services, Website Design & Management, Computer Software, Gambling & Casinos, and Banking each experienced less than 1% of the attacks, ranging from 0.48% to 0.32%. The remaining category, labelled as “Others,” accounted for a minimal 0.12%. This comprehensive breakdown underscores the varied impact of DDoS attacks across different industries in Indonesia, emphasizing the diverse targets and the need for robust cybersecurity measures.

FINANCIAL SECTOR
The financial sector is the most targeted industry by ransomware in the Philippines. This is because financial institutions store a large amount of sensitive financial data, which is valuable to cybercriminals.

GOVERNMENT SECTOR
The government sector is also a prime target for ransomware attacks. Government agencies control critical infrastructure and store a large amount of sensitive data, such as personal information and national security secrets.

HEALTHCARE SECTOR
The healthcare sector is vulnerable to ransomware attacks because it stores a large amount of sensitive patient data, such as medical records and financial information.

EDUCATION SECTOR
The education sector is also a target for ransomware attacks. Educational institutions store a large amount of student data and intellectual property, which is valuable to cybercriminals.

RETAIL SECTOR
The retail sector is vulnerable to ransomware attacks because it processes a large volume of credit card transactions. Cybercriminals can use ransomware to encrypt credit card data and then demand a ransom payment in exchange for the decryption key.
In the past 90 days, the Philippines has experienced ransomware attacks from various groups, including Cl0p, Medusa, LockBit3, AlphV, and Everest. These incidents highlight the ongoing and diverse cyber threats faced by organizations in the region, emphasizing the critical need for robust cybersecurity measures and vigilance to protect against ransomware attacks.
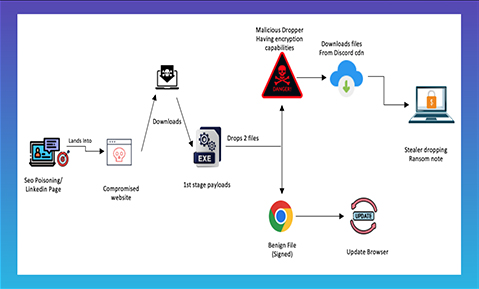
Recently, PhilHealth experienced a Medusa ransomware attack, accompanied by a $300,000 ransom demand. This led to the temporary suspension of the online systems of the state health insurer. After the ransom payment deadline passed, the responsible group uploaded more than 600 gigabytes of files to a leak site and a Telegram channel. The leaked information encompassed photos, bank cards, transaction receipts, and other sensitive data belonging to the victims.

REDENERGY STEALER-AS-A-RANSOMWARE
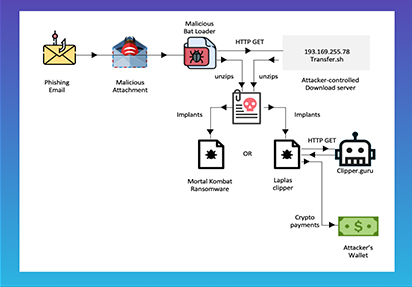
MORTALKOMBAT RANSOMWARE
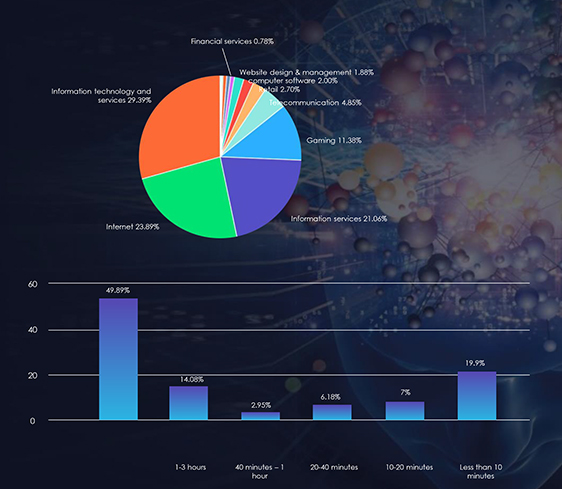
Over the last six months, the Philippines has confronted a dynamic landscape of distributed denial-of-service (DDoS) attacks, revealing a nuanced distribution of threats across industries. The Information Technology and Services sector emerged as the primary target, facing a substantial 29.39% of attacks, signifying a heightened and specific risk. Close behind were Internet-based services and Information Services, each with significant percentages, underlining a noteworthy impact on entities involved in data management and online platforms. Noteworthy percentages in the gaming, telecommunications, and Internet sectors emphasize the breadth of the threat, necessitating heightened cybersecurity measures. Although facing comparatively lower percentages, sectors like banking and financial services underscore the critical need for robust cybersecurity practices to protect sensitive data. This multifaceted distribution highlights the diverse industries grappling with DDoS challenges in the Philippines, demanding tailored and vigilant cybersecurity strategies.
A massive data hack in April 2023, which exposed 817.54 gigabytes of both applicant and employee records under multiple state agencies, including the Philippine National Police (PNP), National Bureau of Investigation (NBI), Bureau of Internal Revenue (BIR), and Special Action Force (SAF), has put the personal information of millions of Filipinos at risk.


Cyber espionage is a growing threat to all organizations, including businesses, governments, and critical infrastructure. It is the use of computers and networks to steal sensitive information, such as trade secrets, government secrets, and personal information.
One specific area where cyber espionage is increasing is in the Philippines. Cyfirma has identified two advanced persistent threat (APT) groups that have targeted the Philippines, namely, Earth Estries and FamousSparrow.
Earth Estries, a well-known hacking group, has become a major player in a cyber espionage campaign that targets government and technology sectors in multiple countries. The campaign was discovered in August, and its primary focus is on two regions: Asia (Philippines, Taiwan, and Malaysia) and Germany and the United States. Earth Estries has been linked to a highly sophisticated operation with extensive experience in cyber espionage and illicit activities. The campaign has been active since at least 2020 and has global implications.
Interestingly, there are overlaps in tactics, techniques, and procedures (TTPs) between Earth Estries and FamousSparrow.
Earth Estries demonstrates a high level of sophistication, using advanced skills and experience in cyberespionage and illicit activities. Their arsenal includes various backdoors and hacking tools, with a focus on evading detection. They use PowerShell downgrade attacks to bypass security measures and exploit public services such as GitHub, Gmail, AnonFiles, and File.io for communication and data transfer.
FamousSparrow is a cyber-espionage entity with connections to APT groups like SparklingGoblin and Metasploit, which have been associated with activities originating from China and has been targeting government and technology sectors in the Philippines, as well as other countries in Asia, South Africa, Germany, and the United States.

CYFIRMA observed and tracked 12 active campaigns targeting various industries in Vietnam during 2023. Chinese, Russian, and North Korean state-sponsored threat actors are behind most of these campaigns.
Threat actors are actively exploiting Atlassian-Confluence vulnerabilities (CVE-2023-22515, CVE-2022-26134, CVE-2022-26138, CVE-2019-3396) in Vietnam.
Organizations in Information Technology, Manufacturing, Tourism, Logistics, and Construction Industries are actively exploited by state-sponsored and financially motivated threat actors.

INFORMATION TECHNOLOGY
With a strategic emphasis on Information and Communication Technology (ICT), the Vietnamese government has undertaken initiatives to propel its development, recognizing its significance as a priority industry. The ambitious goal is to elevate Vietnam’s digital economy to an impressive US$50 billion by 2025, offering substantial growth prospects for the ICT market. This trajectory is underscored by World Bank data, indicating an annual growth rate of 10% in Vietnam’s digital economy, with the potential to exceed a formidable US$200 billion by 2045. Within this burgeoning digital landscape, the Vietnam Information Technology (IT) industry becomes a focal point of interest for threat actors. The convergence of economic ambitions and technological advancements renders the IT sector susceptible to cyber threats, with threat actors aiming to exploit vulnerabilities for economic gains, intellectual property theft, or to gain a competitive advantage.

MANUFACTURING INDUSTRY
The manufacturing sector stands as a pivotal force in Vietnam’s economic landscape, constituting a substantial 24.76% of the country’s GDP and contributing significantly to its merchandise exports, accounting for 85% in 2022. Notably, this industry’s prowess extends beyond traditional production, with recent years witnessing an uptick in the manufacturing of sophisticated products like automotive parts, consumer electronics, and telecom equipment, showcasing Vietnam’s commitment to technological advancement. Leveraging advanced technologies, the Vietnamese manufacturing industry has earned a competitive edge, producing high-quality goods at a cost-effective scale. In the context of the threat landscape, the strategic importance and economic impact of Vietnam’s manufacturing industry make it an attractive target for threat actors. Cyber adversaries may seek to exploit vulnerabilities in the industry’s digital infrastructure for various motives, including economic espionage, intellectual property theft, or disrupting supply chains. Recognizing the nexus between technological innovation and economic growth, safeguarding the manufacturing sector becomes imperative, necessitating robust cybersecurity measures to protect against evolving threats and preserve Vietnam’s economic resilience.

TOURISM
Amidst the first half of 2023, Vietnam’s tourism sector showcased notable growth, welcoming nearly 5.6 million international visitors, achieving 70% of the annual target. Projections from Future Market Insights anticipate a robust tourism revenue of US$27,500 million by the year’s end, with a long-term forecast envisioning an impressive US$135,000 million by 2033. Within this thriving landscape, the Vietnam tourism industry becomes an intriguing target for threat actors. The sector’s economic significance, driven by increasing international footfall and substantial revenue projections, makes it an attractive focal point for cyber adversaries. Threat actors may aim to exploit vulnerabilities in the industry’s digital infrastructure for diverse reasons, such as financial fraud, data theft, or disrupting the country’s image as a tourist destination. Recognizing the symbiotic relationship between a secure digital landscape and the sustained growth of Vietnam’s tourism sector, it becomes imperative to fortify cybersecurity measures to safeguard against potential threats and preserve the industry’s positive trajectory.

LOGISTICS
The logistics sector in Vietnam stands out as a rapidly expanding industry, constituting approximately 4.5% of the country’s GDP. Positioned as the 10th among emerging logistics markets globally, Vietnam’s logistics market is valued at US$40 billion, with projections estimating a market size of US$45.19 billion by end of 2023 and an anticipated growth to US$65.34 billion by 2029. Notably, over 30 companies, including industry giants like DHL, FedEx, and Maersk, contribute to the provision of international logistics services in Vietnam. Within this dynamic context, the Vietnam logistics industry emerges as a focal point for threat actors. The sector’s substantial economic contribution and strategic position in global logistics networks make it an appealing target for cyber adversaries. Threat actors may seek to exploit digital vulnerabilities in the logistics infrastructure for motives such as supply chain disruption, data theft, or financial fraud. Recognizing the critical role of secure logistics in supporting economic activities, fortifying cybersecurity measures becomes imperative to mitigate risks and ensure the resilience of Vietnam’s logistics industry against evolving cyber threats.

CONSTRUCTION INDUSTRY
With a current valuation of USD 23.1 billion, the Vietnam construction market is poised for substantial growth, projected to register a robust CAGR of over 8.5% in the forecast period. Emerging as the latest East Asian growth engine, Vietnam has captivated the interest of international investors, underscoring its strategic importance in the global construction landscape. However, this burgeoning sector also attracts the attention of threat actors in the Vietnam threat landscape. The construction industry’s pivotal role in the country’s economic development, coupled with its increasing international prominence, makes it an attractive target for cyber adversaries. Threat actors may aim to exploit digital vulnerabilities within the construction infrastructure for motives such as intellectual property theft, economic espionage, or disrupting critical projects. Recognizing the interconnectedness of digital infrastructure and the construction industry’s growth, bolstering cybersecurity measures becomes imperative to safeguard against potential threats and ensure the sustained development of Vietnam’s construction sector.
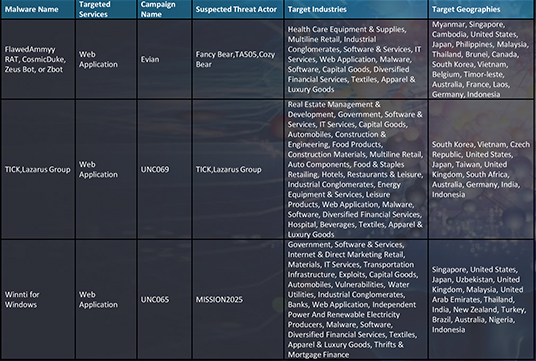
APT41/MISSION 2025
LAZARUS GROUP
TA505
APT28/Fancy Bear
Highlighting 3 active campaigns – as a sample.
Observed 12 active campaigns targeting various industries in Vietnam during 2023. Chinese and North Korean state-sponsored threat actors are behind most of these campaigns.
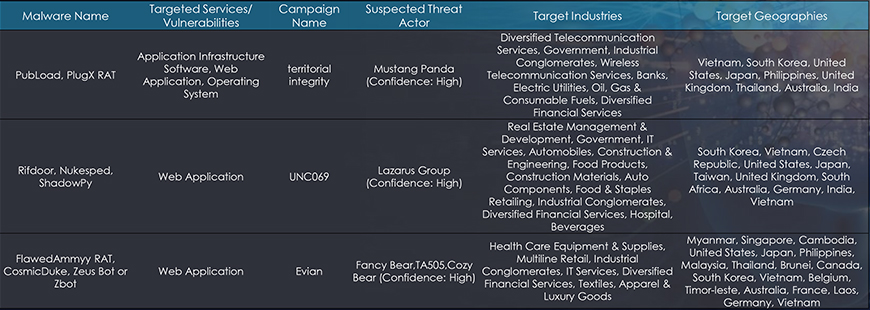
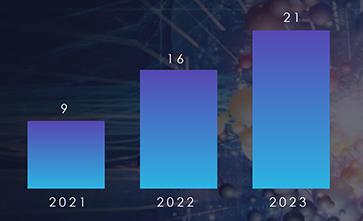
Between Jan to October 2023, as part of the external threat landscape monitoring and analysis, we observed 12 campaigns targeting various conglomerates. The following trends have been observed of the different State-Sponsored groups and Cybercriminals, who have potentially carried out the observed cyberattack campaigns:
No. of campaigns carried out by North Korean Groups: 4 out of 12 (33.33%)
State-Sponsored: All 4 (100%)
Insights: North-Korean Hackers are observed of possible collaboration with Chinese Groups, Russian Groups and offering their services/expertise as part of the Hacker-as-a-Service (HaaS model) to steal sensitive information in return for financial gains.
No. of campaigns carried out by Chinese Groups: 3 out of 12 (25%)
State-Sponsored: All 3 (100%)
Insights: Chinese threat groups are targeting organizations predominantly for espionage activities to assist their local companies and support their government’s agenda as part of Made in China 2025 objectives.
No. of campaigns carried out by Russian Groups: 5 out of 12 (41.67%)
Cybercriminals: 3 out of 5 (60%)
State-Sponsored: 2 out of 5 (40%)
Insights: Russian threat actors are being observed of expanding their attack surface to other geographical regions such as Asia-Pacific, EMEA, in addition to their traditional geographies – North America, Western Europe to target organizations.
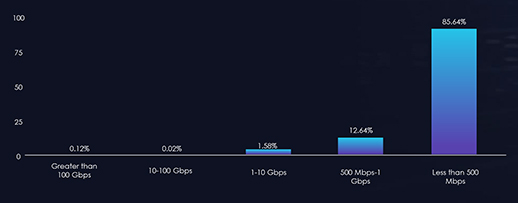
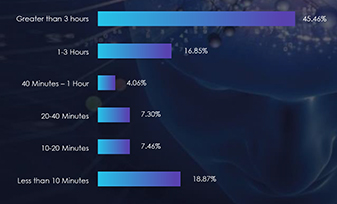
In the last six months, Vietnam’s threat landscape has undergone a notable impact from distributed denial-of-service (DDoS) attacks, with the Information Technology and Services sector being particularly affected, representing a significant 92.06% of the attacks. Moreover, a substantial 45.46% of these attacks endured for periods exceeding three hours, indicating a prolonged and impactful threat scenario. Additionally, attacks within the one to three-hour duration range accounted for 16.85%, underscoring a notable proportion of sustained assaults. Examining bitrates, attacks with speeds ranging from 500 Mbps to 1 Gbps constituted 12.64%, while those with less than 500 Mbps made up the majority share at 85.64%. This diverse distribution highlights the necessity for a comprehensive and adaptive cybersecurity strategy to effectively mitigate the varying intensities of DDoS threats in Vietnam.
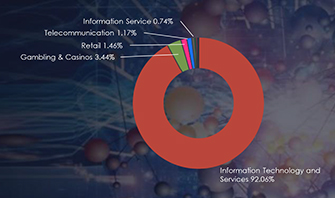
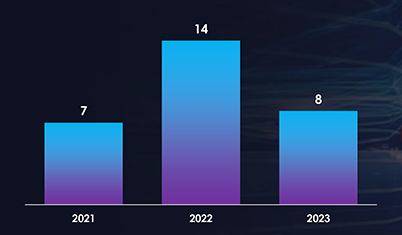
LockBit ransomware has primarily targeted Manufacturing, Healthcare, Transportation & Logistics, Telecommunications, and Food & Beverages sectors in Vietnam, affecting the largest proportion of victims at 37% among all targeted organizations.
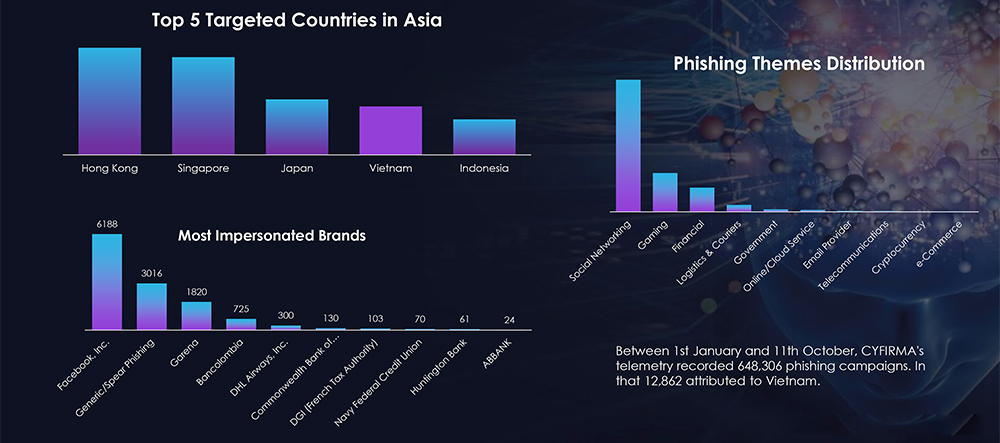
Between 1st January and 11th October, CYFIRMA’s telemetry recorded 648,306 phishing campaigns. In that 12,862 attributed to Vietnam.
Most Exploited vulnerabilities in Vietnam
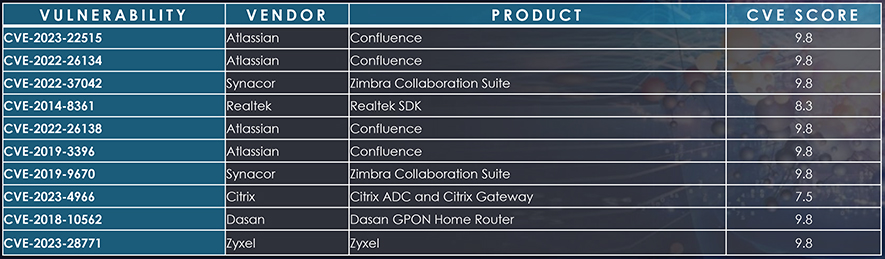
We observed Atlassian Confluence has been actively exploited by threat actors in Vietnam