



The Asia Pacific (APAC) Threat Landscape Report provides a comprehensive overview of the evolving cybersecurity landscape in the region. In recent years, Asia Pacific has witnessed a significant increase in cyber threats, driven by factors such as rapid digitalization, increased internet penetration, and geopolitical tensions. This report aims to provide key insights into the current state of cyber threats, and emerging trends.
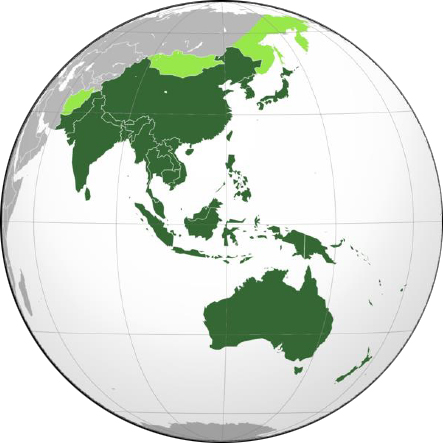
THE GEOGRAPHICAL SCOPE OF THIS REPORT
Taiwan, Thailand
APAC Volume – 1
Australia, Bangladesh, India, Indonesia
APAC Volume – 2
Japan, Philippines, Vietnam, Malaysia
APAC Volume – 3
Taiwan, Thailand
YET TO BE UPDATED
New Zealand, Singapore, South Korea
UPDATED METHODOLOGY
This is a running report. Our research team will update this report on an ongoing basis to keep the readers updated on the evolving cyber threat landscape of the region.
Trend: Ransomware attacks on critical infrastructure
Motives: Disruption/Geopolitical/Extortion
Trend: Spyware, malware, and plug-ins to collect data.
Motive: Reputation impact, disruption, extortion
Trend: Brute force attacks, credential reuse, and data exfiltration via malware
Motive: Operational disruption, espionage, IP exfiltration
Trend: social engineering/phishing. jump server Exploits, remote access tool compromise
Motive: Operational disruption, espionage, IP exfiltration
Trend: Device scanning, firmware, phishing/malware download
Motives: Disruption, data harvesting, remote attacks (DDOS)
Trend: Multi-behavioral malware (IT/OT, different operating systems
Target: CII trade secrets documents containing proprietary processes
INCREASED SOPHISTICATION OF CYBER ATTACKS
The region has witnessed a rise in the sophistication of cyber attacks, with threat actors employing advanced techniques to compromise systems and networks.
TARGETED THREATS AGAINST CRITICAL INFRASTRUCTURE
Critical infrastructure sectors face heightened risks, with threat actors showing a growing interest in targeting key industries, such as energy, finance, and telecommunications.
RISE IN RANSOMWARE INCIDENTS
Ransomware attacks have surged in frequency and severity, posing significant challenges to businesses and government entities. The attackers often demand cryptocurrency payments for the release of compromised data.
NATION-STATE THREATS AND CYBER ESPIONAGE
Evidence suggests an increase in nation-state-sponsored cyber activities, including cyber espionage and information warfare. This poses significant geopolitical and security concerns for the region.
SUPPLY CHAIN VULNERABILITIES
The report identifies vulnerabilities in the regional supply chain, with cybercriminals exploiting weaknesses in third-party relationships to gain unauthorized access to targeted organizations.
Economic Circumstances and Technological Advancements:
Cybercrime Landscape:
Incentives for Cybercrime:
Taiwan:

APT41 (also known as Barium, Winnti, or Wicked Panda)
Origin: China
Activities: APT41 remains a significant threat to Taiwan, focusing on cyber espionage across various sectors, including technology and defense. The group is notorious for leveraging software supply chain attacks and exploiting zero-day vulnerabilities, often targeting government institutions and tech companies for data exfiltration.
Storm-1376 (also known as Spamouflage or Dragonbridge)
Origin: China
Activities: This group has been increasingly active in Taiwan, particularly in the realm of information operations (IO). Using AI-generated content, Storm-1376 has sought to influence Taiwanese public opinion, especially during election periods. Their tactics include deepfake videos, fake social media accounts, and AI-generated news, all aimed at sowing discord and advancing China’s geopolitical interests.
APT10 (also known as Stone Panda, MenuPass, or Red Apollo)
Origin: China
Activities: APT10 continues to pose a threat to Taiwan, particularly targeting Managed Service Providers (MSPs) to gain indirect access to sensitive data across multiple industries, including healthcare, aerospace, and IT. Their operations are characterized by long-term espionage campaigns aimed at strategic sectors.
TICK (also known as Bronze Butler)
Origin: China
Activities: TICK is an advanced persistent threat (APT) group primarily focused on cyber espionage, targeting sectors with high concentrations of intellectual property and sensitive information. While their activities are most well-known in South Korea and Japan, TICK has also expanded its operations to target high-tech and defense sectors in Taiwan. They use a range of malware, including custom tools like Daserf and Invader, and are known for leveraging zero-day vulnerabilities to infiltrate networks and exfiltrate data.
Team Tonto (also known as BRONZE HUNTLEY or Karma Panda)
Origin: China
Activities: Team Tonto has a history of targeting government, military, and technology sectors in Taiwan, among other regions. They employ sophisticated tactics such as spear-phishing, credential dumping, and the use of advanced malware like ShadowPad. Recent activities suggest that they continue to focus on long-term espionage campaigns, aiming to gather intelligence and disrupt Taiwanese governmental and institutional operations.
GALLIUM
Origin: China
Activities: Specializing in long-term espionage campaigns, GALLIUM targets telecommunications and IT service providers in Taiwan. The group is known for maintaining persistent access to compromised networks, often using sophisticated tools and techniques to evade detection.
Lazarus Group
Origin: North Korea
Activities: Known for its financially motivated cyber-attacks, Lazarus Group has also targeted Taiwan’s financial institutions and cryptocurrency exchanges. Their tactics include spear-phishing, custom malware, and large-scale cyber heists, which help fund North Korea’s weapons programs.
OceanLotus (also known as APT32 or SeaLotus)
Origin: Vietnam
Activities: OceanLotus has increasingly focused on Taiwan as part of its broader Southeast Asian espionage operations. The group targets government entities, businesses, and research institutions, often using advanced malware and spear-phishing to achieve their objectives.
As for Russian threat actors, their focus remains primarily on regions closer to home, particularly in relation to ongoing conflicts. While some cybercriminals may still opportunistically target Taiwanese organizations for profit, they are currently overshadowed by the more prominent threat actors mentioned above.
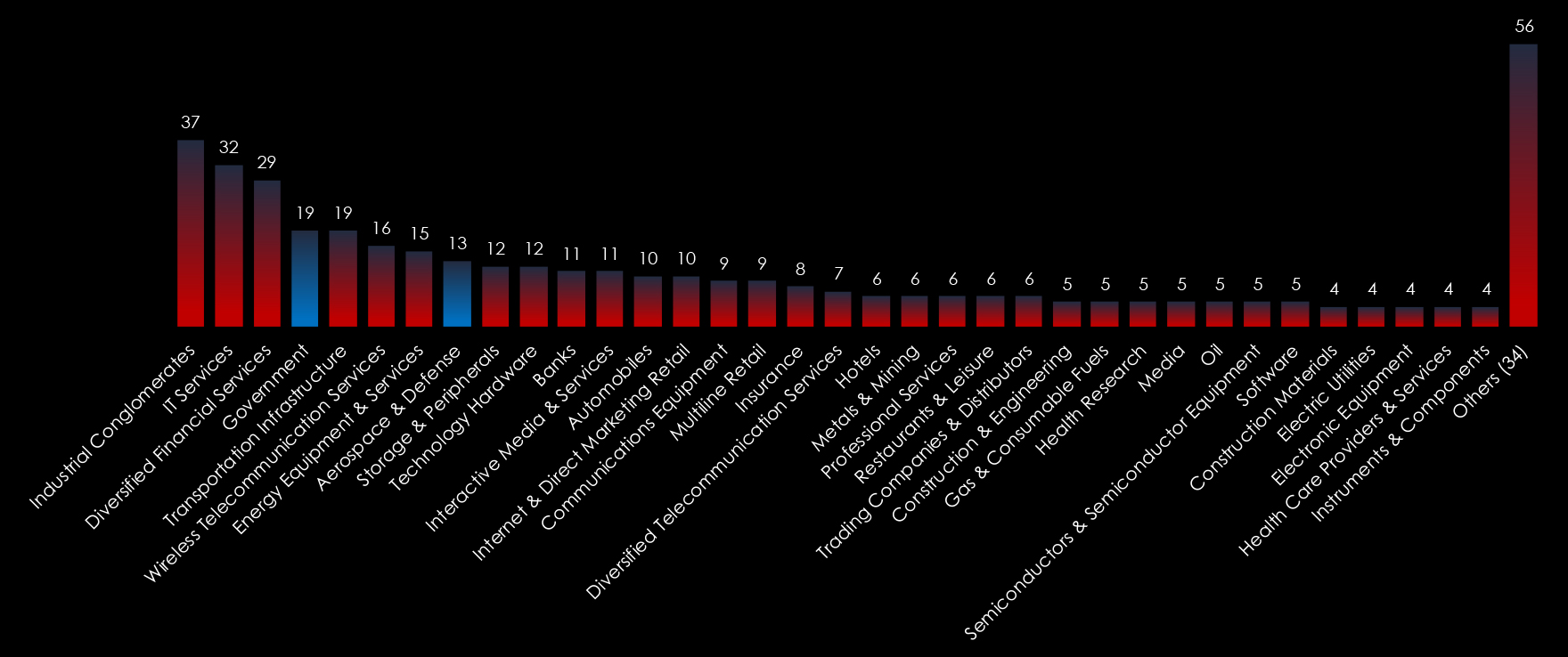
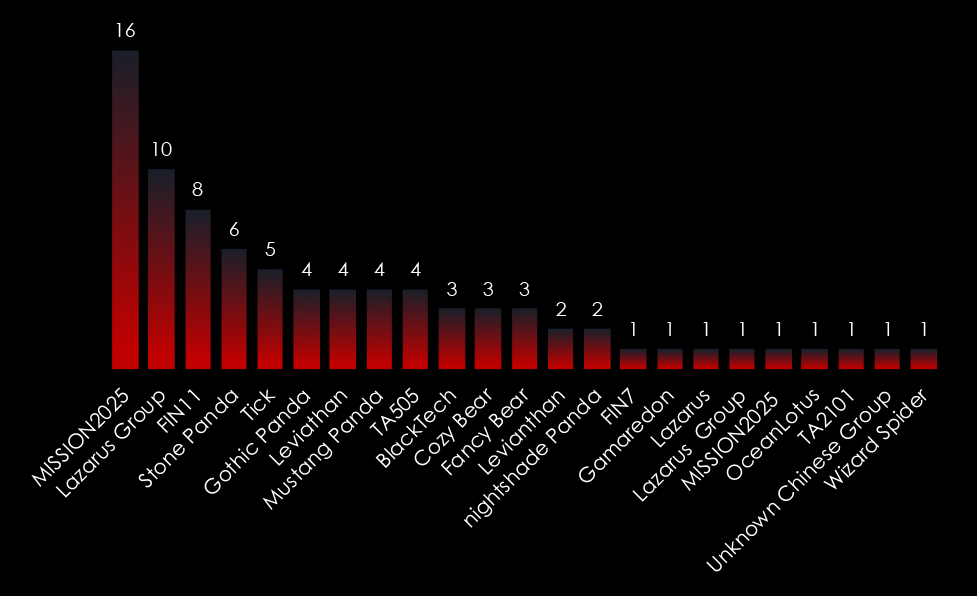
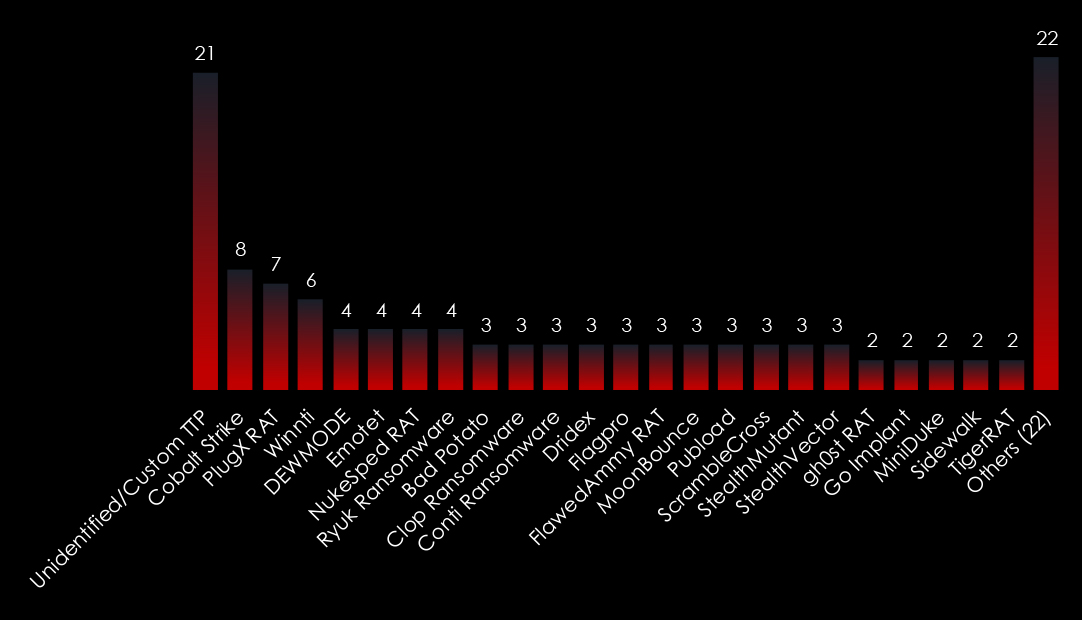
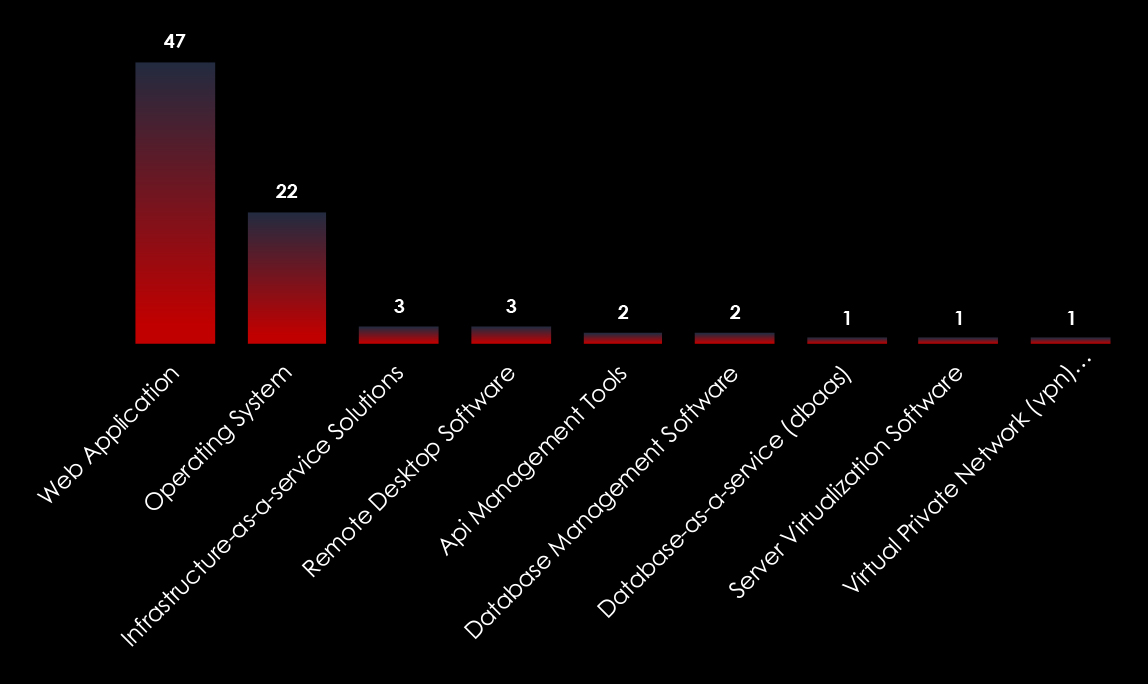
Analyzing global and regional activities in detail provides indirect insight into the local cybercrime scene; what local cybercriminals are targeting and how they fit into the global external threat landscape.
We will examine Taiwanese phishing in comparison to Hong Kong’s: while they appear to be in similar positions, many phishing campaigns originating out of Hong Kong are also directed to Taiwan.
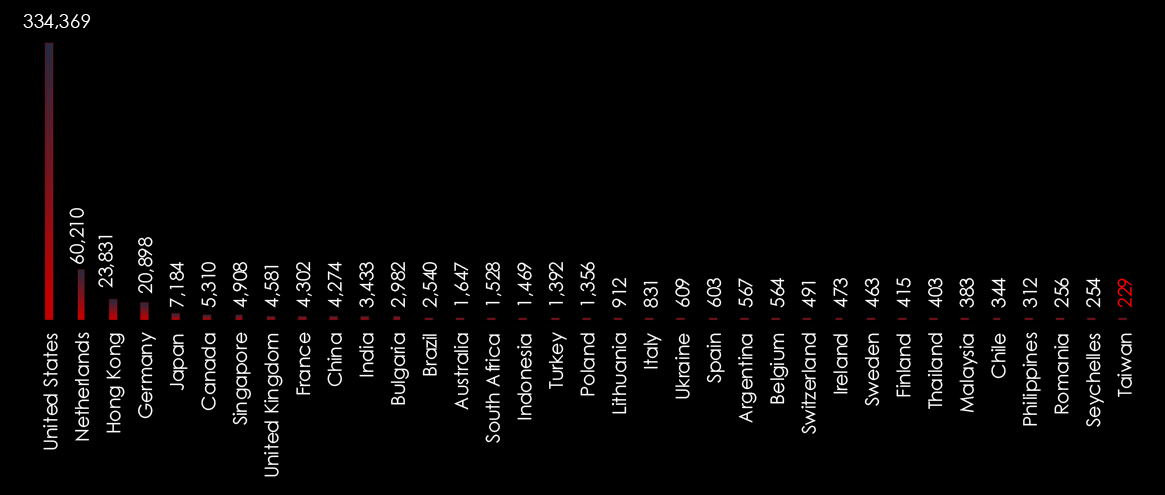
During the last 6 months period CYFIRMA’s advanced telemetry systems observed a total of 504,663 phishing campaigns.
Data represent the ASN-based origin of the phishing emails captured.
While the US remains the largest source by far, Asian countries are steadily growing as a source of Phishing attacks.
Taiwan ranked 35th
Note: The US is the most targeted country by cybercrime and as a result, it also contains the most compromised devices used in botnets as proxies to deploy malware and send phishing around the world.
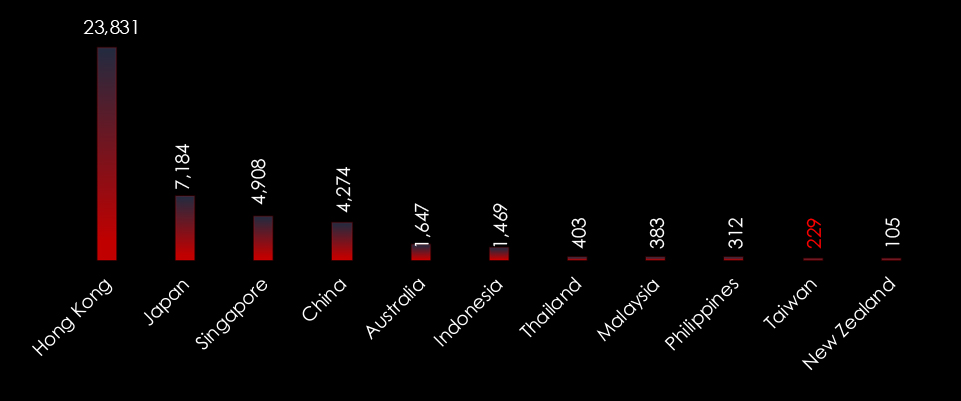
Narrowing down the selection of countries to the Asia-Pacific region we can have a more detailed view of the regional threat landscape.
Hong Kong stands out largely due to the fact it is commonly used by Chinese cyber criminals as a proxy to send phishing emails outside of mainland China.
Similarly, Singapore is known for business-friendly hosting practices which also allow for malicious hosting as proxies. Furthermore, the good international reputation of Singapore allows attackers to bypass region-based IP blocking.
Both Hong Kong and Singapore are frequently used to send Phishing emails to Taiwan.
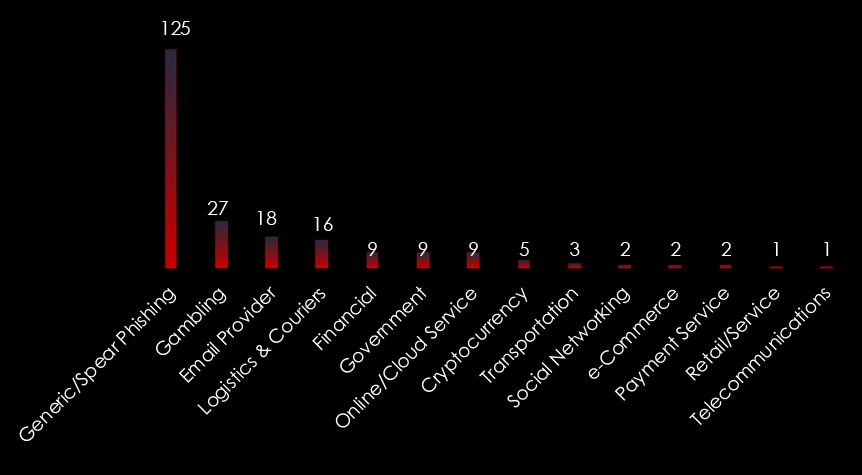
Phishing campaigns originating from Taiwan predominantly target the Gambling sector, Email service providers, and Logistics & Courier themes. This combination is interesting, as phishing attacks on gambling and logistics & courier services are generally aimed at consumers or end-users, facilitating direct monetization through scams—typical of conventional cybercriminal activity.
However, phishing attacks that exploit email service providers often result in account takeovers, leading to potential identity theft, access to other user accounts, and even espionage. This suggests that sophisticated phishing campaigns are more common in Taiwan, relatively when compared to other thematic attacks.
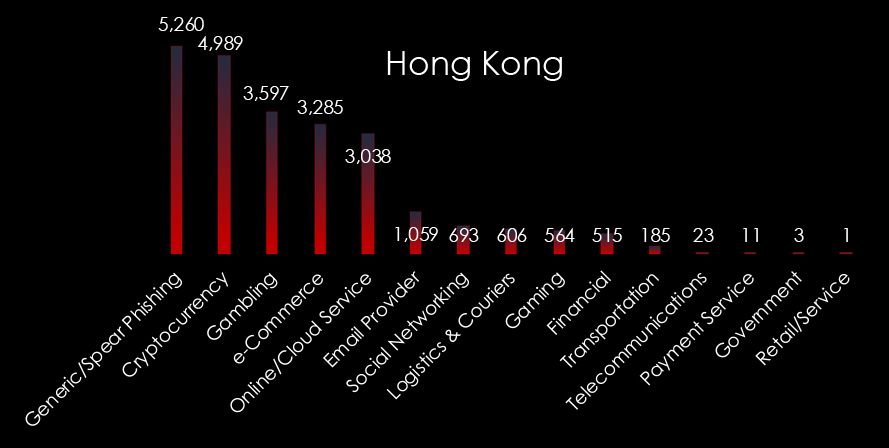
Looking at observed themes originating from Hong Kong the two most prominently targeted are Cyrptocurrency, Gambling, and e-Commerce. Suggesting that local cybercrime is focused on financial scams.
Online/Cloud services are mostly comprised of Office365 and similar to deliver fake links or documents, which are delivery methods for a wide variety of phishing themes.
This typically means local cybercrime has reached a certain maturity where organized cybercrime is systematically exploiting end-users for financial gains.
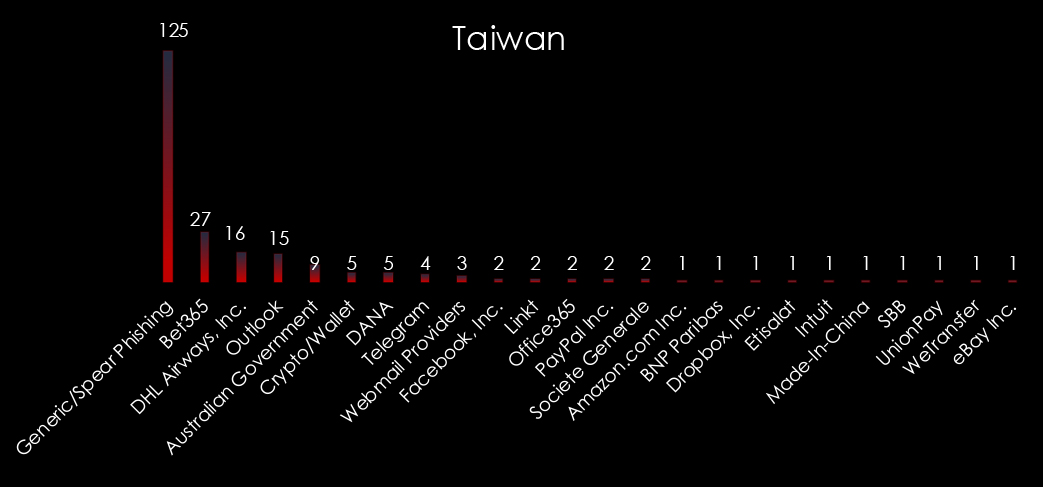
Breaking down observed phishing into identified brands we can have a look at what specific phishing themes are deployed in Taiwan-origin phishing.
Brands pretty much correlated with the observed themes in the previous slide. Interesting is the presence of the Australian Government as a theme, illustrating that the country of origin is not always the country the phishing is aimed at.

Drilling down into what specific brands are impersonated and in turn targeted by Hong Kong-origin campaigns, we do observe a significant amount of e-commerce and financial organizations.
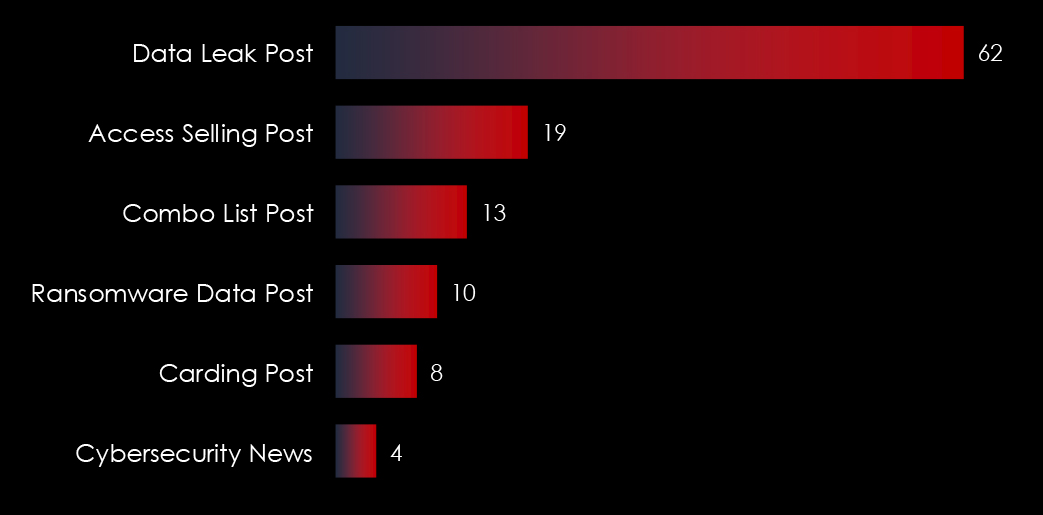
According to our telemetry in the last 6 months, there were 123 data leak posts mentioning Taiwan.
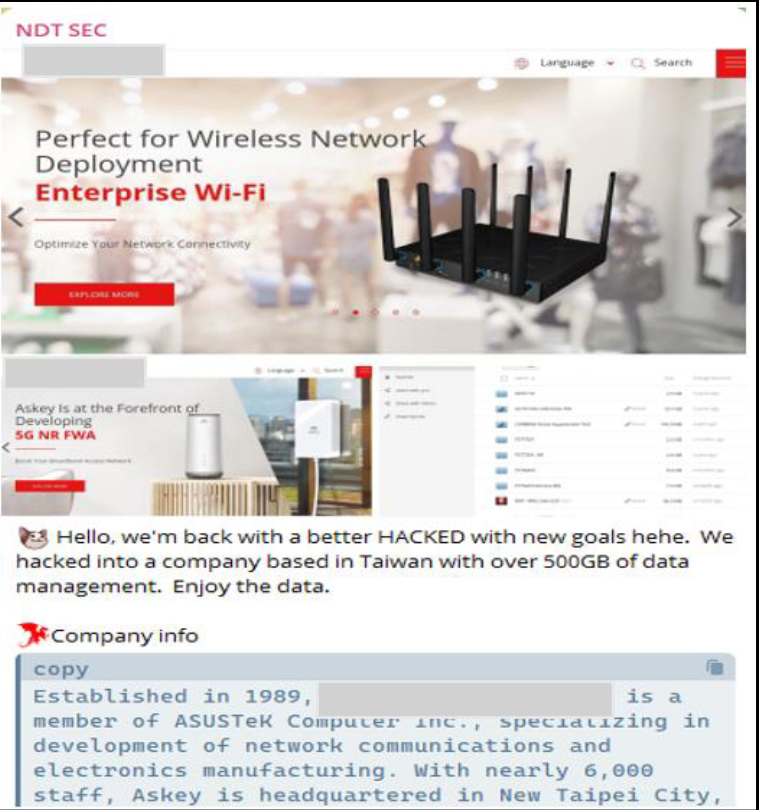
Recently, the CYFIRMA Research team observed that a hacker group has reportedly breached the network of Askey Computer Corp., a Taiwan-based subsidiary of ASUSTeK Computer Inc., gaining unauthorized access to over 500GB of sensitive data. The attackers have publicly claimed responsibility for the breach, showcasing their access to internal files. Askey specializes in the development of network communications and electronics manufacturing, making this breach particularly significant given the potential exposure of critical infrastructure and customer data.
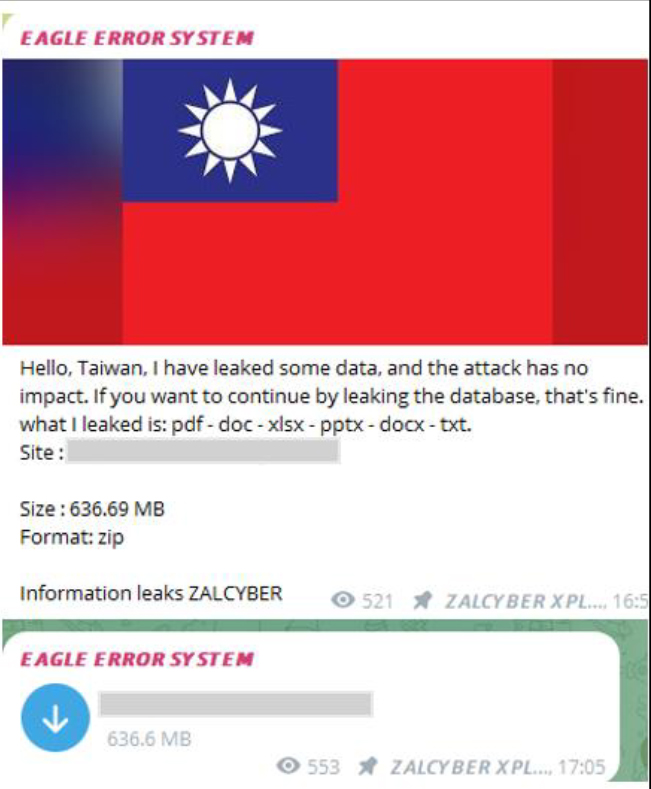
A recent post from an entity identified as “Eagle Error System” in Telegram announced the leak of data from a Taiwanese government website (https[:]//www[.]taiwan[.]gov[.]tw/). The leaked data, amounting to 636.69 MB in a ZIP file, includes various document types such as PDFs, DOCs, XLSX, PPTX, and TXT files. This incident poses significant concerns over the security and integrity of government data and highlights the ongoing risks of cyberattacks against public institutions.
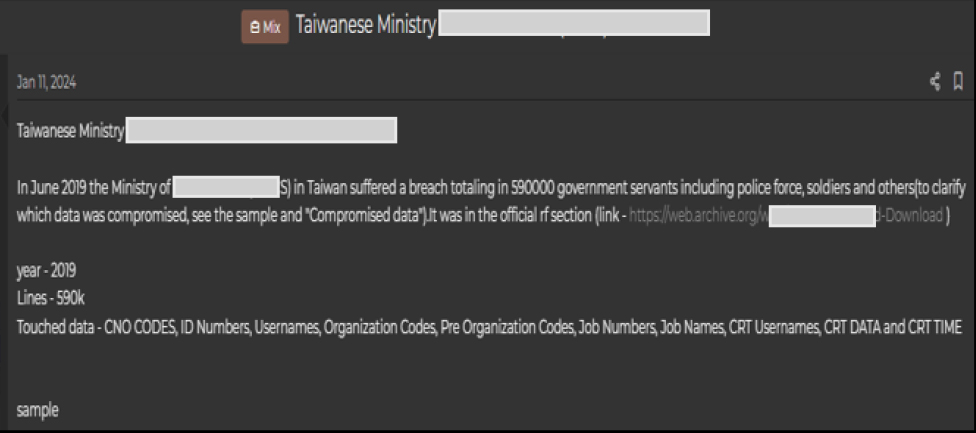
In June 2019, the Ministry of Civil Services (MOCS) in Taiwan experienced a significant data breach affecting 590,000 government employees, including members of the police force, soldiers, and other civil servants. The data is getting recirculated very frequently in the underground forums and reportedly includes CNO codes, ID numbers, usernames, organization codes, job numbers, job names, and other sensitive information related to government personnel. This breach, which has been discussed in various online forums, highlights the potential exposure of critical personal and organizational information, raising concerns over the security of government data systems in Taiwan.
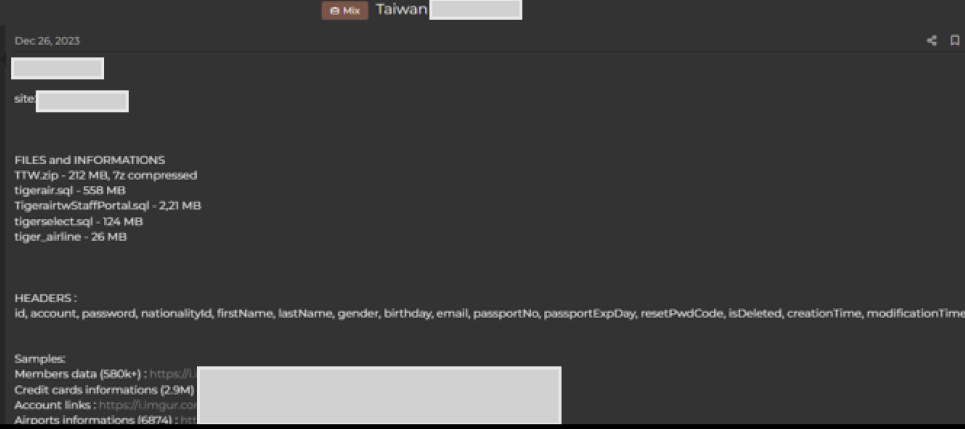
In December 2023, a significant data breach was reported involving Taiwan tigerairtw[.]com, a low-cost airline. The breach exposed various files and databases totalling several gigabytes, including critical personal information. The compromised data includes customer and staff records, such as IDs, account details, passwords, national ID numbers, names, gender, birthdates, emails, passport numbers, and other sensitive details. Additionally, data from Tigerair’s staff portal and other internal databases was leaked, with a substantial amount of personally identifiable information (PII), now publicly accessible. This breach presents serious security and privacy risks for the affected individuals and highlights vulnerabilities in the airline’s cybersecurity infrastructure.
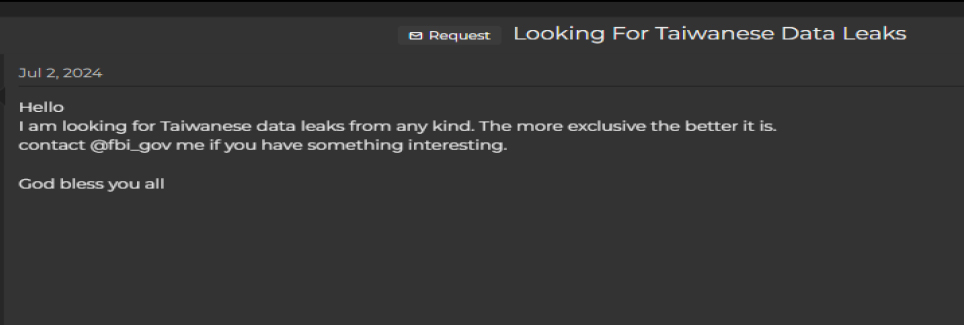
In July 2024, a request was posted by a user on a forum seeking exclusive data leaks related to Taiwan. The post specifically invites others to share Taiwanese data breaches of any kind, emphasizing a preference for more exclusive and significant leaks. This request underlines an active interest in acquiring sensitive information related to Taiwan, potentially for purposes that could include espionage, financial exploitation, or other malicious activities, raising concerns about targeted threats against Taiwanese entities.
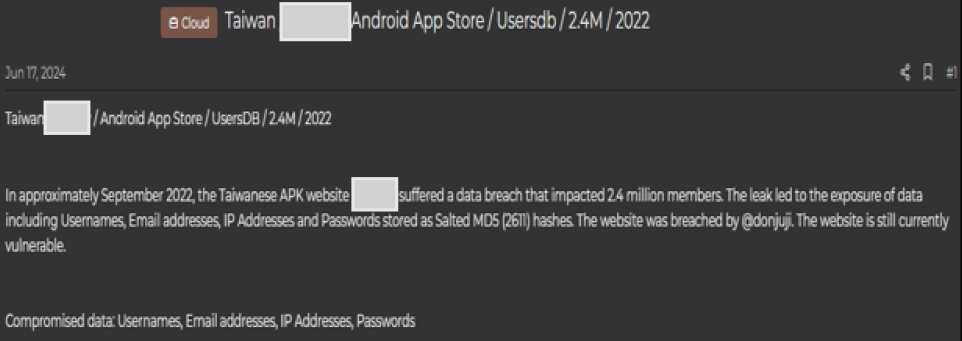
In June 2024, it was reported that the Taiwanese APK website, APK[.]TW, suffered a significant data breach around September 2022, affecting 2.4 million users. The breach exposed sensitive information, including usernames, email addresses, IP addresses, and passwords, which were stored using salted MD5 hashes. The breach was carried out by an individual or group known as @donjuji, and it was noted that the website remains vulnerable. This incident highlights ongoing cybersecurity risks for platforms that manage large user databases, particularly those with inadequate encryption and security measures.
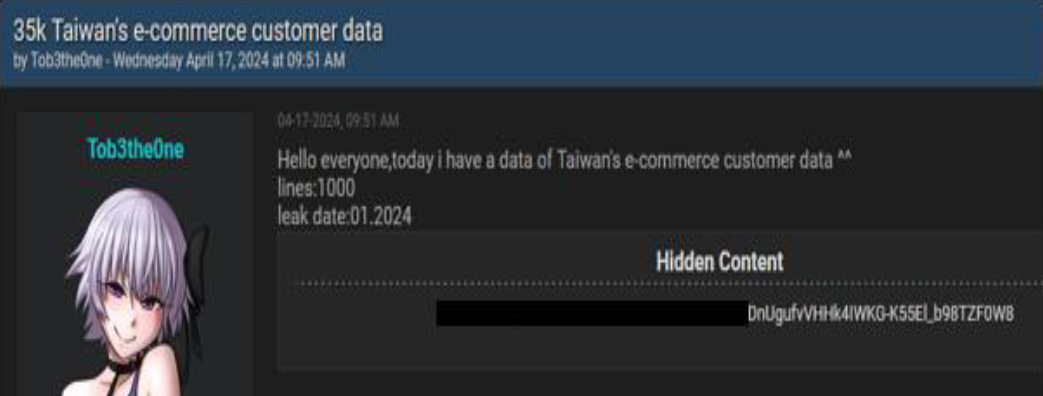
On April 17, 2024, a user named “Tob3the0ne” posted in an underground forum about a leak involving customer data from a Taiwanese e-commerce platform. The post mentions that the data leak contains 35,000 customer records with 1,000 lines of data, which were leaked in January 2024. The post also provides a link to download the leaked data, suggesting that sensitive information may now be accessible to unauthorized parties. This incident raises serious concerns about the security of customer information on Taiwanese e-commerce platforms and highlights the potential risks of data breaches in the retail sector.
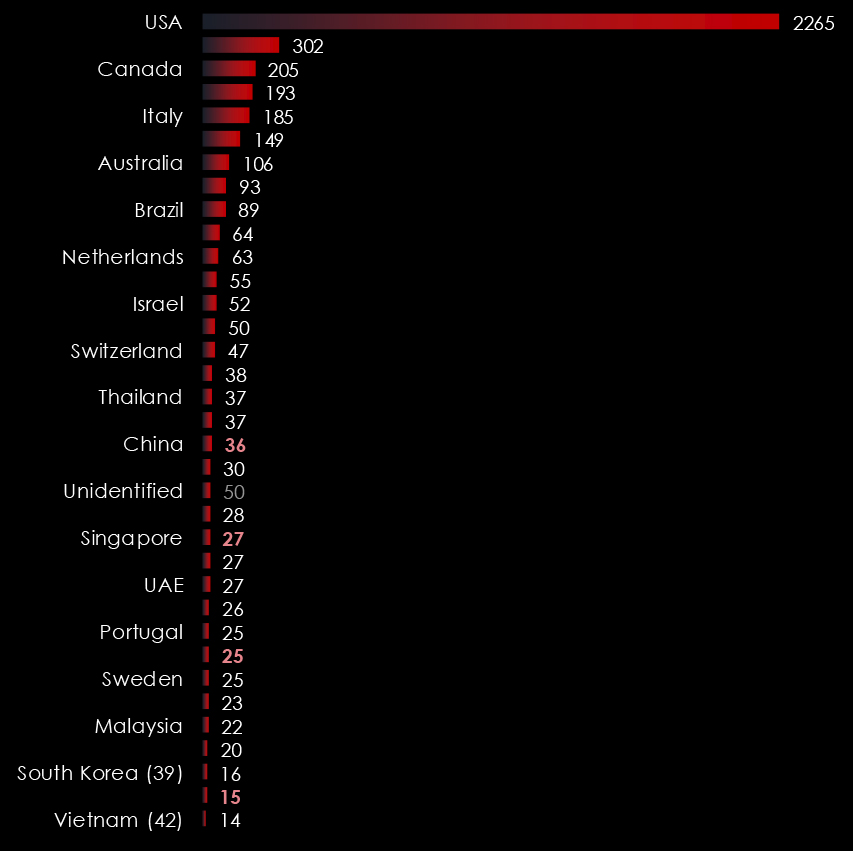
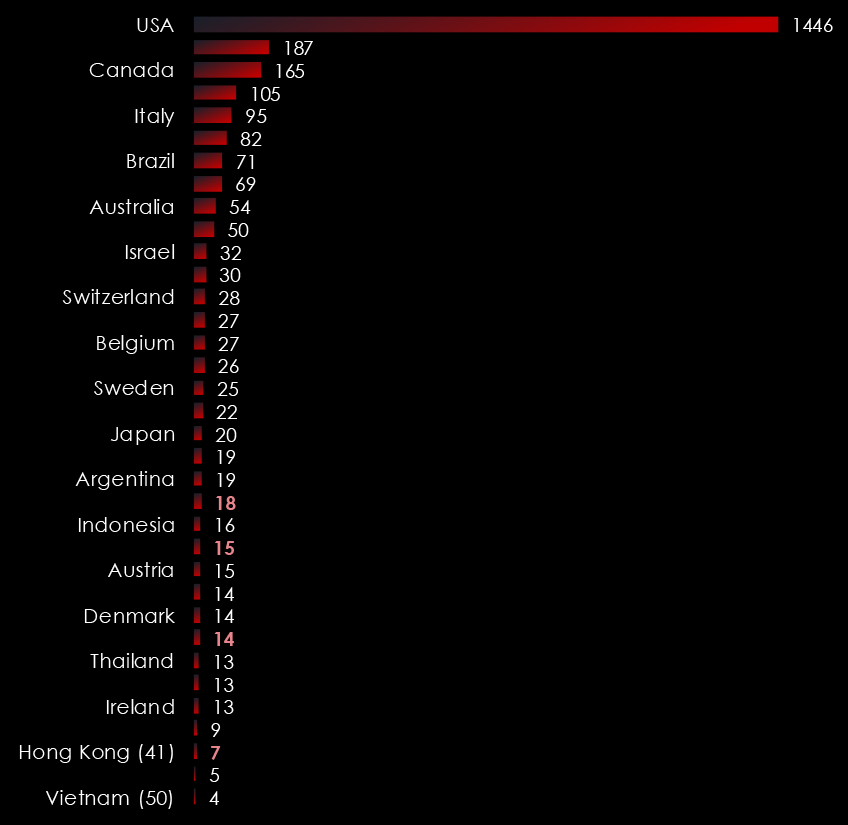
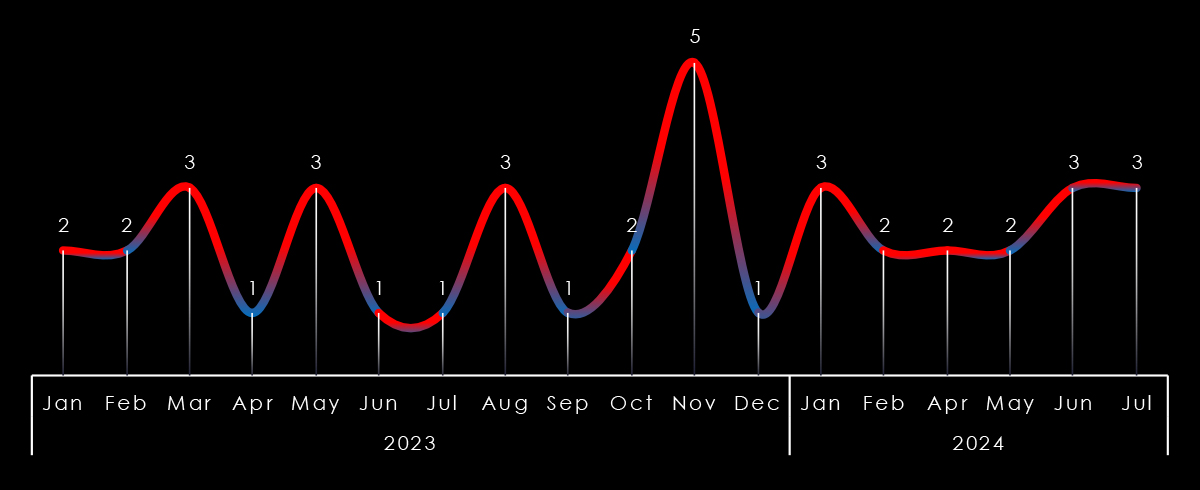
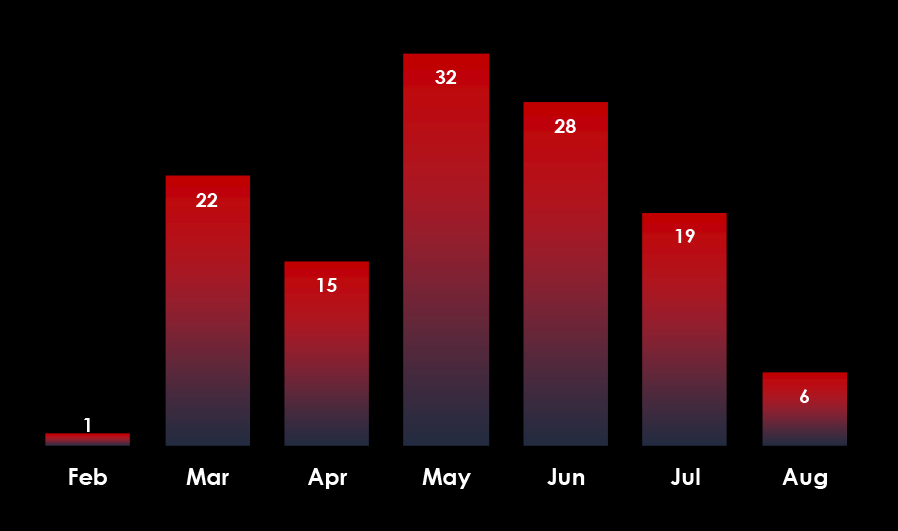
Trendline counting victims in Taiwan from 2023 until now shows remarkably consistent and sustained interest, especially in 2024 when the trendline has stabilized.
This is in line with ransomware gangs expanding their focus from the US and EU to the rest of the World, particularly Asia. Thanks to the affiliate Ransomware-as-a-Service programs, global, multi-lingual threat actors can deploy and execute some of the most dangerous ransomware like LockBit3 (or most recently, RansomHub).
The time of nearly exclusive Russian-speaking gangs looking only at the US and EU is gone, with increasingly warming ties between Russia, China, and North Korea showing in the development of cybercrime and ransomware.
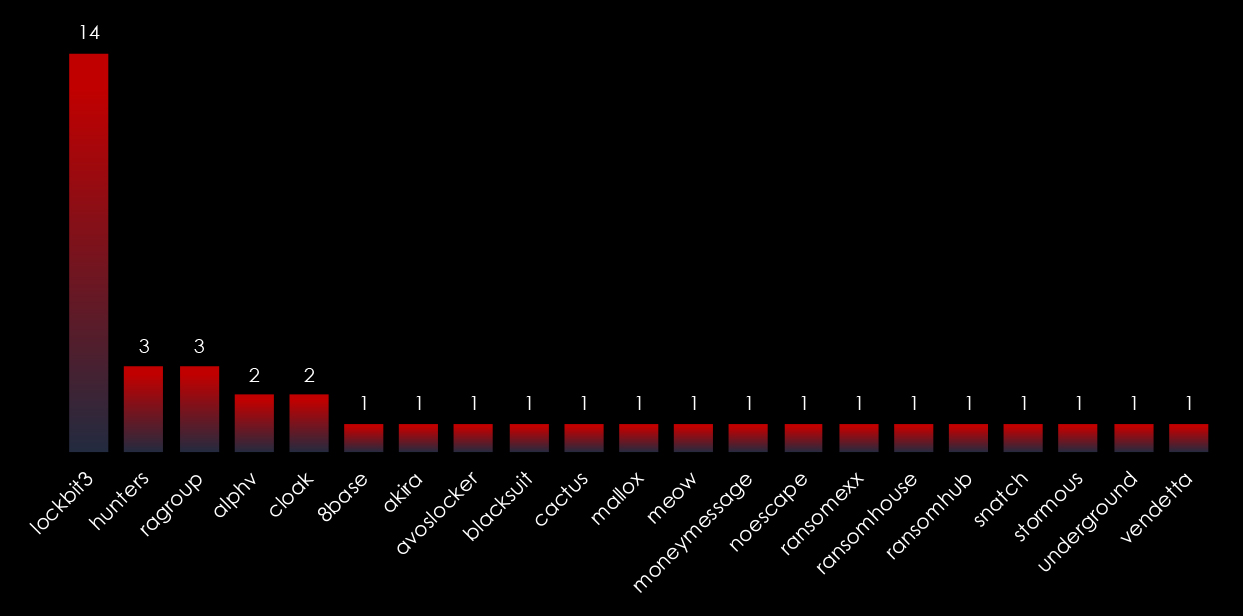
LockBit3 is by far the most frequent ransomware used in Taiwan. However, 20 different gangs recorded victims in Taiwan, collectively presenting the same level of threat.
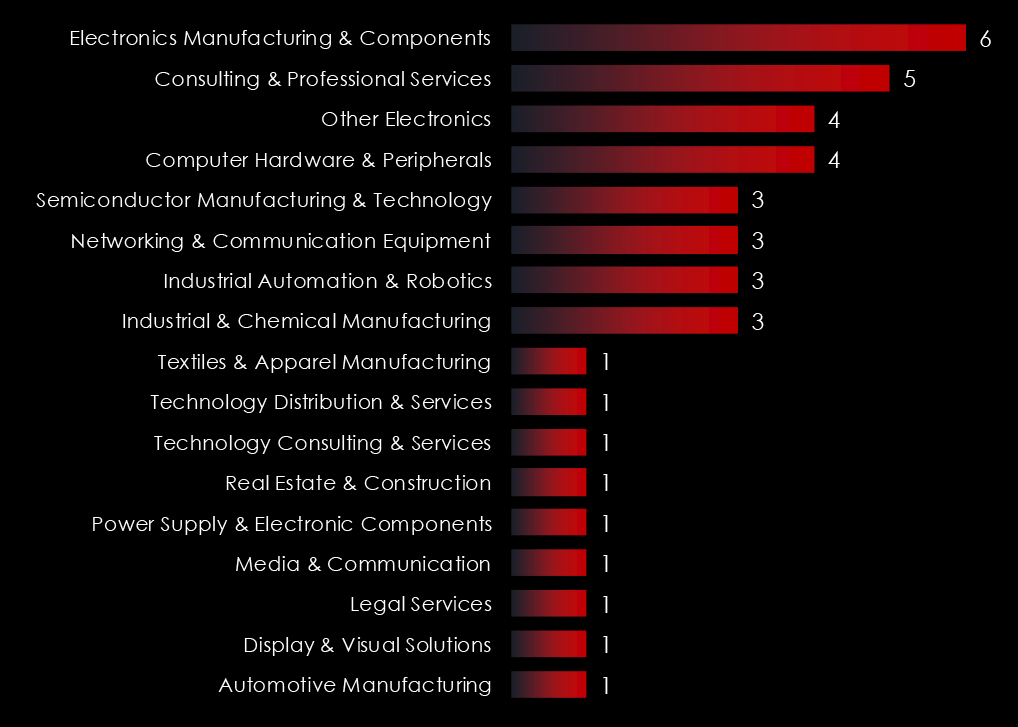
Analyzing the industries of Taiwan ransomware victims, we can see a wide variety of sectors, underlining the opportunistic nature of cybercrime.
The Electronics and Semiconductor Manufacturing sectors are the most prominent.
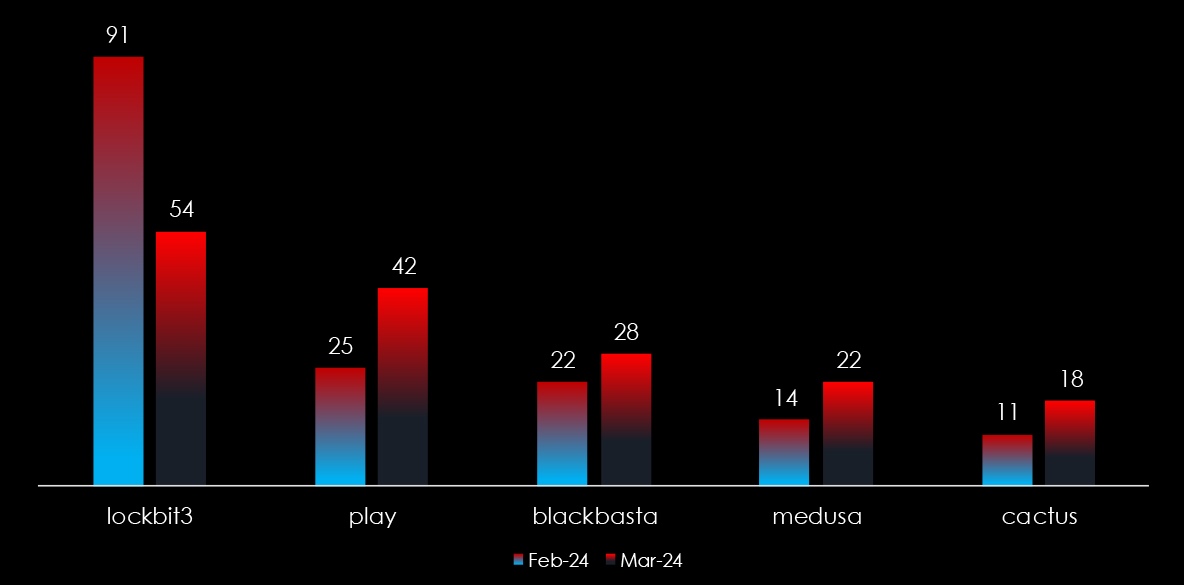
To paint a picture of the current ransomware affiliate-based structure, here is a chart of the Lockibit3 takedown effect. It shows how affiliates diverted to other RaaS and the total number of attacks did not go down significantly.
Overall, we can see how the highest threat changes over time. In 2023 it was by far Cl0p, at the start of 2024 it was LockBit3, and more recently RansomHub has dominated the threat landscape.
In other words, it could be said that flavors of ransomware are changing, but the numerous affiliates carrying out the attacks remain and gain momentum internationally.
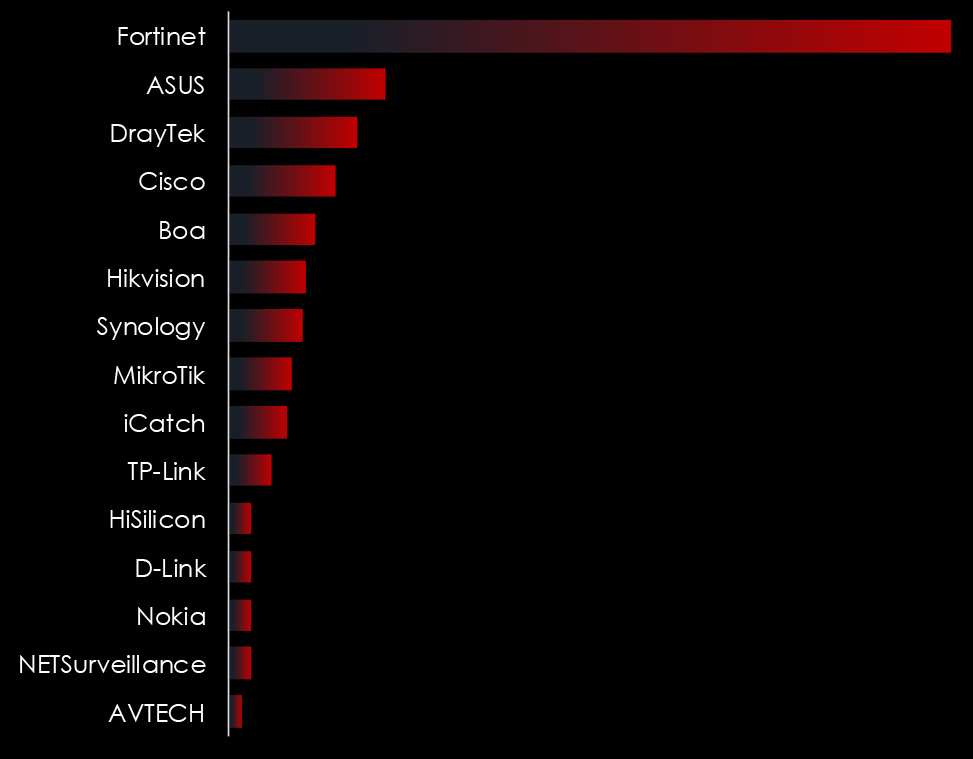
Exposed IoT devices play a significant role in cyber attacks due to often inadequate security features and widespread adoption across various sectors. These devices can serve as entry points or targets in larger network breaches, primarily because they frequently lack robust encryption, undergo infrequent updates, and have default or weak credentials that are easily exploited. Once compromised, IoT devices can be used to form botnets, enabling attackers to conduct DDoS (Distributed Denial of Service) attacks, data breaches, or surveillance. Their connectivity and access to larger networks also make them a valuable asset for attackers looking to move laterally within the infrastructure, escalate privileges, or disrupt critical services. This vulnerability is exacerbated by the rapid expansion of IoT devices in homes, industries, and cities without corresponding advancements in their security frameworks.
| Vulnerability | Vendor | Product |
| CVE-2023-20198 | Cisco | Cisco IOS XE |
| CVE-2021-42013 | Apache | Apache HTTP Server |
| CVE-2018-10562 | Dasan | Dasan GPON Home Router |
| CVE-2014-8361 | Realtek | Realtek SDK |
| CVE-2017-9841 | PHPUnit | PHPUnit |
| CVE-2017-18368 | Zyxel/Billion | ZyXEL P660HN-T1A v1, ZyXEL P660HN-T1A v2, Billion 5200W-T |
| CVE-2015-2051 | D-Link | D-Link DIR-645, DAP-1522 revB, DAP-1650 revB, DIR-880L, DIR-865L, DIR-860L revA, DIR-860L revB DIR-815 revB, DIR-300 revB, DIR-600 revB, DIR-645, TEW-751DR, TEW-733GR |
| CVE-2024-27198 | JetBrains | TeamCity |
| CVE-2018-7600 | Drupal | Drupal |
| CVE-2023-1389 | TP-Link | TP-Link Archer AX21 |
| CVE-2023-42793 | JetBrains | TeamCity |
| CVE-2020-16846 | SaltStack | Salt |
| CVE-2023-22518 | Atlassian | Confluence |
| CVE-2022-37042 | Synacor | Zimbra Collaboration Suite |
| CVE-2023-22527 | Atlassian | Confluence |
Geopolitical Leverage
Thailand’s strategic location in Southeast Asia, bridging the region between China and Western-aligned nations, gives it importance in regional geopolitics. By infiltrating Thailand’s cyber infrastructure, state actors can gain leverage in diplomatic and military negotiations, influencing regional alliances, and shifting power dynamics.
Espionage and Intelligence on Foreign Relations
Thailand’s diplomatic involvement in ASEAN and its role as a mediator in regional conflicts make it a valuable target for espionage. By compromising governmental and diplomatic systems, state actors can extract sensitive information about Thailand’s foreign relations, defense policies, and regional partnerships.
Exploitation of Thailand’s Digital Economy
Thailand’s rapid digitalization, particularly in the finance, fintech, and e-commerce sectors, makes it an attractive target for cybercriminals and state actors. These sectors handle vast amounts of financial data, and access to these systems can allow for cyber theft, ransomware, or financial manipulation, with far-reaching economic consequences.
Disruption of Critical Infrastructure
Thailand’s critical infrastructure, especially its energy, transportation, and communications networks, provides valuable targets for state actors seeking to disrupt or control key services. By attacking these sectors, cyber threat actors can weaken Thailand’s economic and logistical stability, potentially affecting regional trade and energy security.
Economic Espionage and Intellectual Property Theft
Thailand’s manufacturing and industrial sectors, especially, electronics and automotive industries, are key targets for economic espionage. State-sponsored actors may steal trade secrets, industrial designs, or proprietary technologies to give their own industries a competitive edge in the global market.
Influence and Control Over Political Dynamics
Cyber campaigns aimed at Thailand’s political landscape allow state actors to manipulate public opinion, undermine democratic processes, or discredit opposition parties. Disinformation campaigns, election interference, or attacks on political entities could shape Thailand’s political trajectory to align with the interests of foreign powers.
Testing Ground for New Cyber Tactics
Thailand’s expanding but still relatively vulnerable cybersecurity infrastructure makes it an attractive testing ground for new cyber tactics and tools. State actors may conduct lower-risk operations to test the effectiveness of advanced malware, ransomware, or cyber espionage tools before deploying them in more strategically critical or adversarial nations.
Access to Regional Trade and Supply Chains
Thailand plays a key role in Southeast Asia’s supply chains and logistics networks, particularly manufacturing and agriculture. Targeting Thailand allows state-sponsored actors to disrupt global supply chains, gaining intelligence on international trade agreements and exploiting supply chain vulnerabilities for economic or geopolitical gains.
Military and Defense Surveillance
Thailand’s military ties with both Western and Eastern powers, as well as its internal defense operations, make it a valuable target for military intelligence gathering. State actors may conduct surveillance to monitor military activities, procurements, and alliances to bolster their strategic military positioning in the region.
Cybercriminal Collaborations and Money Laundering
Thailand’s growing digital infrastructure, combined with weaker cybersecurity enforcement in some areas, creates a haven for cybercriminals. It allows for activities, such as ransomware operations, financial fraud, and digital money laundering. State-sponsored cybercriminals can exploit these weaknesses to funnel funds through Thailand or launch cyber campaigns with little fear of legal retaliation.
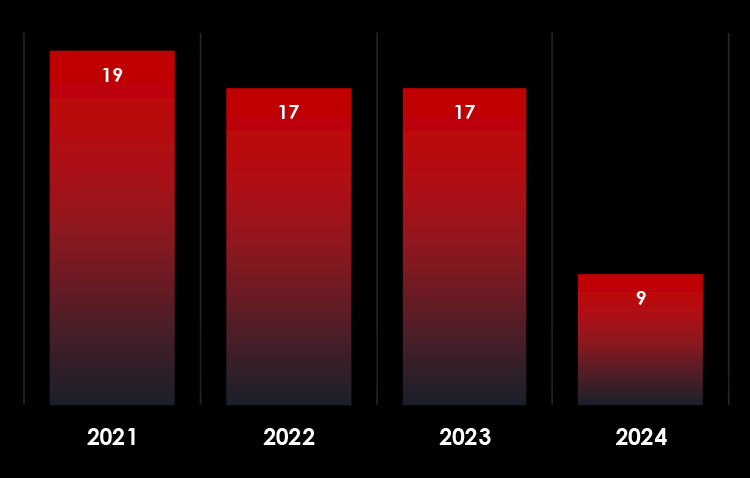
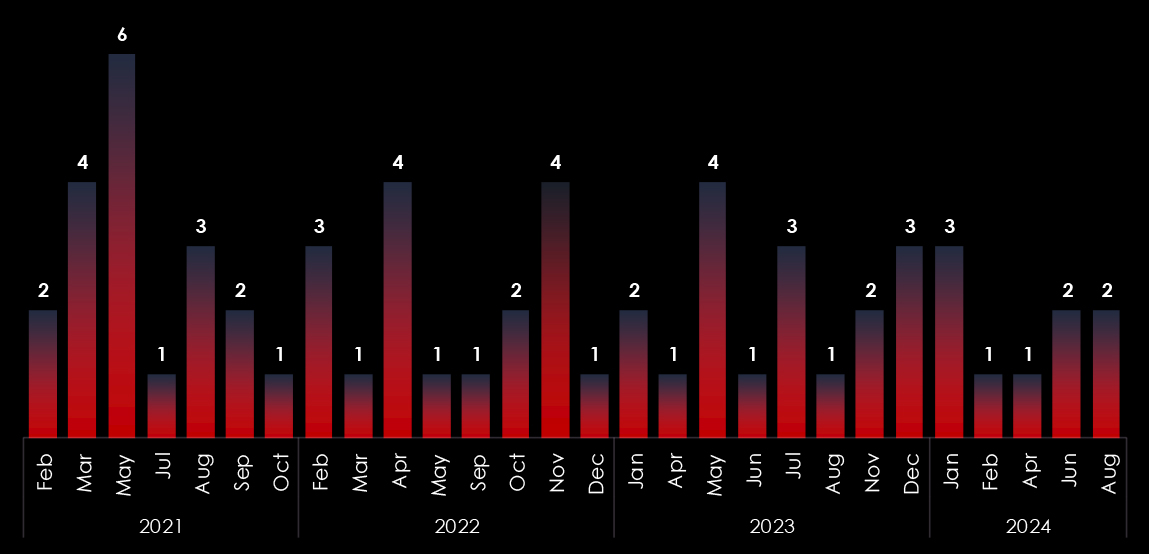
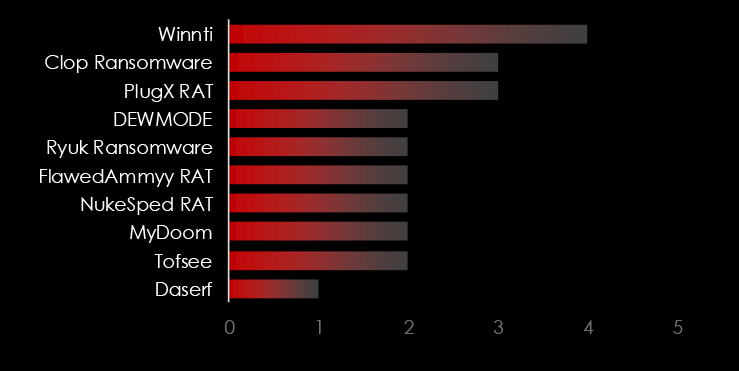
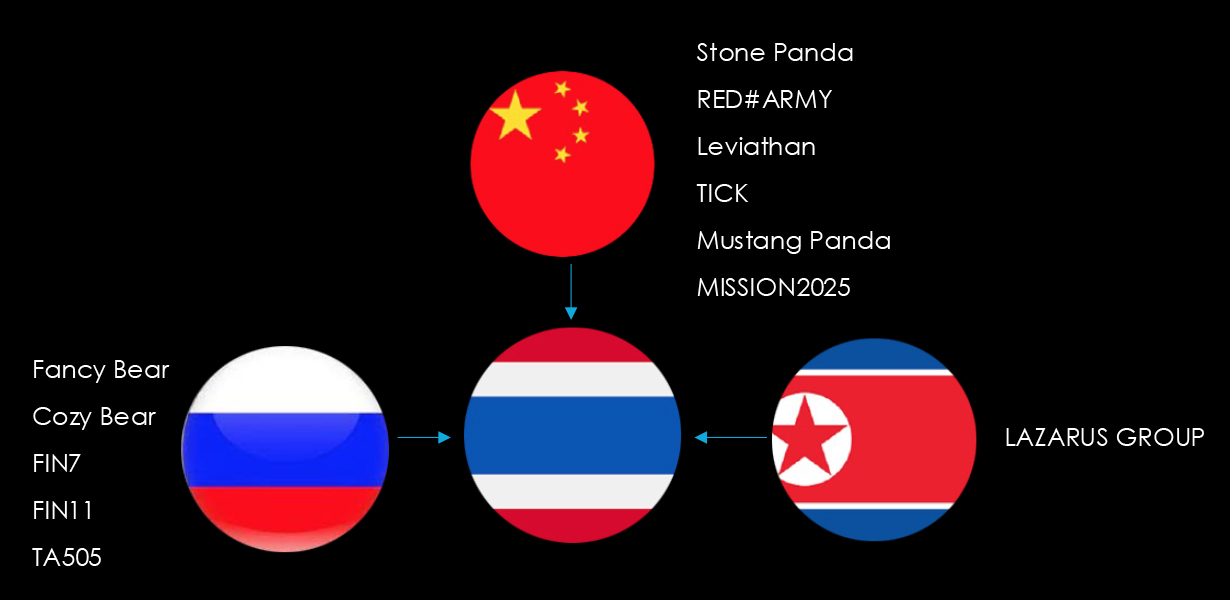
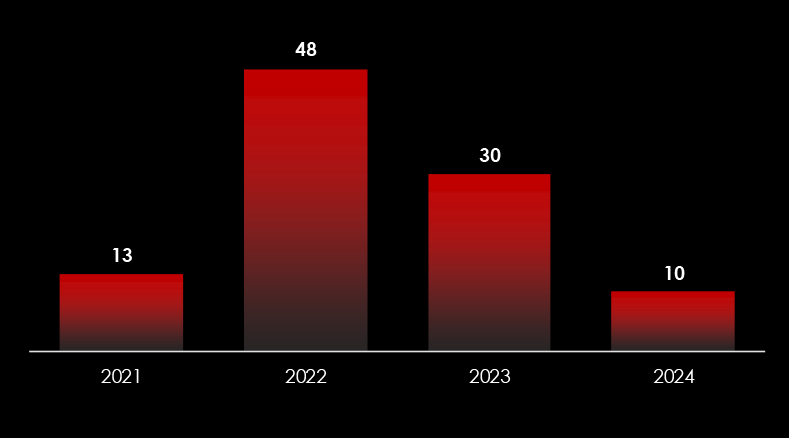
We observed 5 campaigns targeting various industries in Thailand during 2024. Chinese, Russian, and North Korean state-sponsored threat actors are behind most of these campaigns.
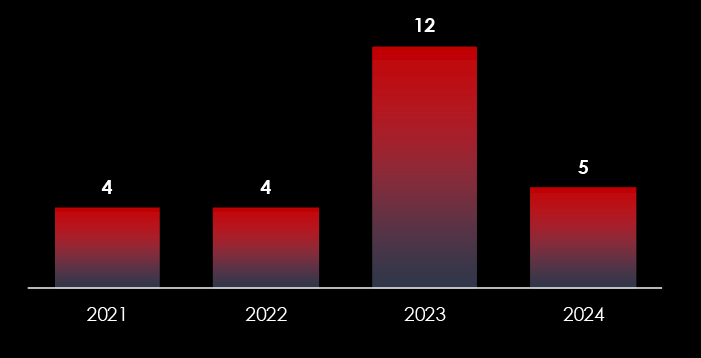
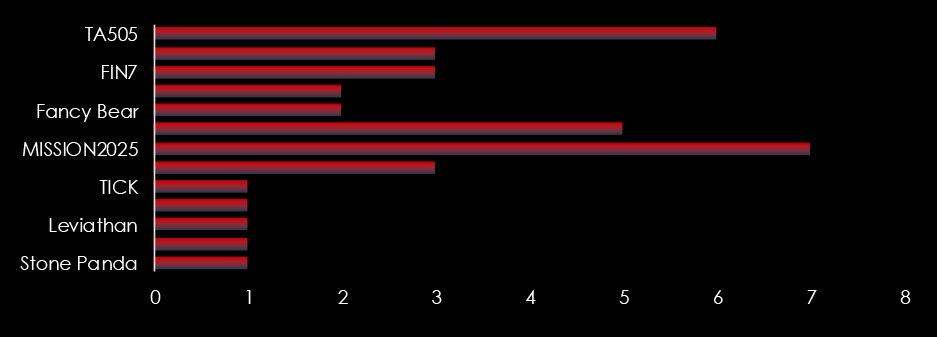
In 2023, there was a substantial rise in the number of observed campaigns, a marked increase when compared to the preceding two years. This uptick highlights the heightened interest of threat actors in the economic and geopolitical dynamics of Thailand.
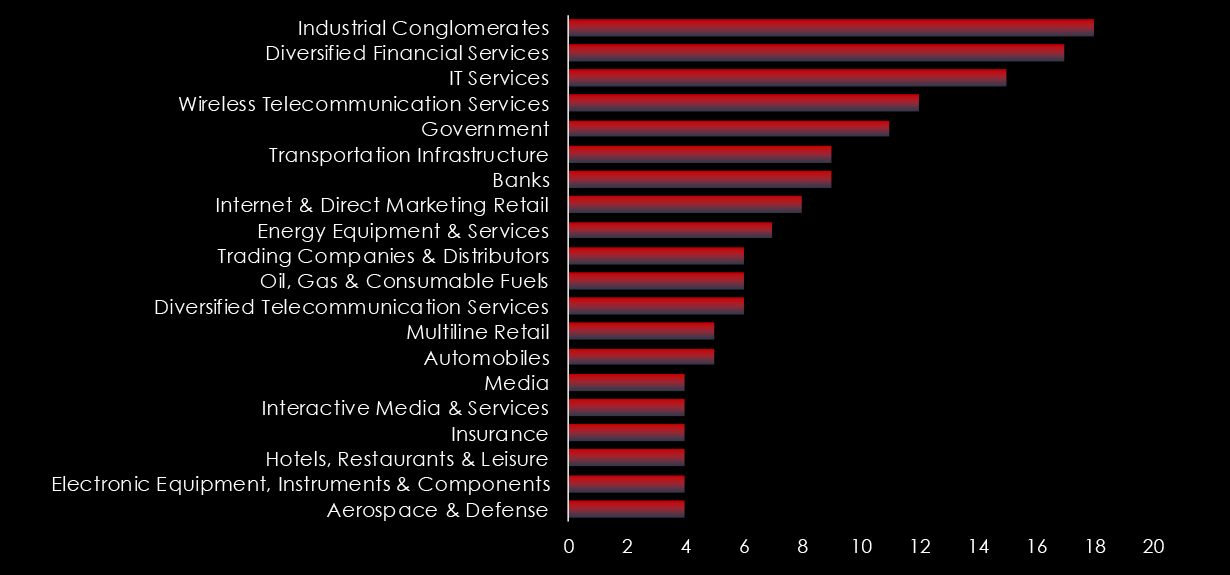
In the observed cyber campaigns, threat actors have methodically targeted a multitude of industries within the critical infrastructure. This deliberate focus is generating substantial economic and social repercussions within the threat landscape, amplifying its overall impact.
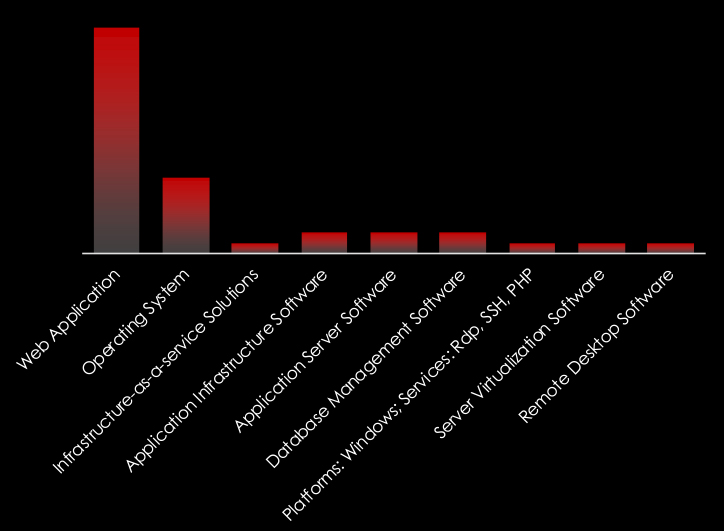
In the observed campaigns threat actors focused on attacking web applications, operating systems, and various other applications.
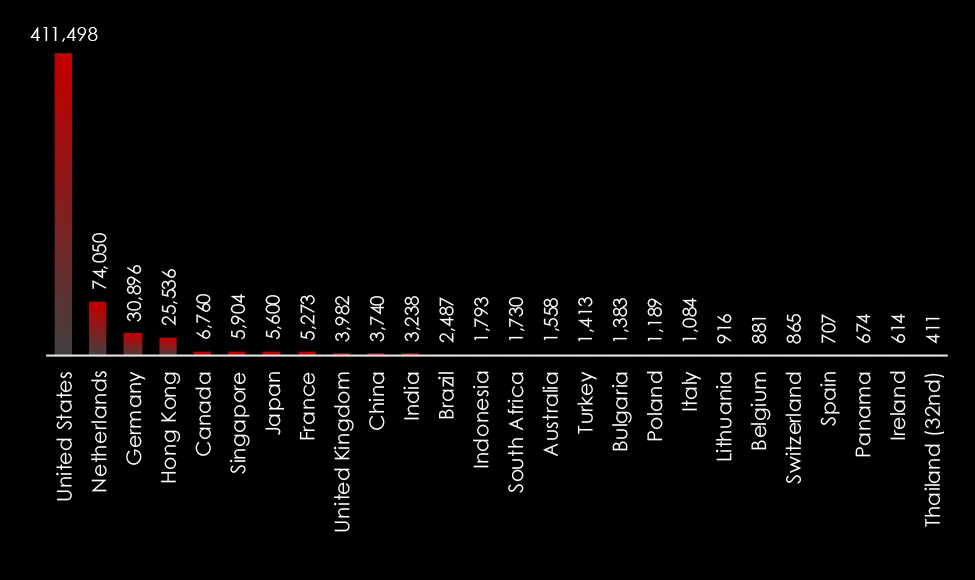
During the last 6 months, CYFIRMA’s advanced telemetry systems detected a total of 607,318 phishing campaigns. This sample size gives us enough insight into the overall threat landscape. Geography is based on the ASN origin of the email. Thailand ranked as the 32nd largest source of phishing globally.
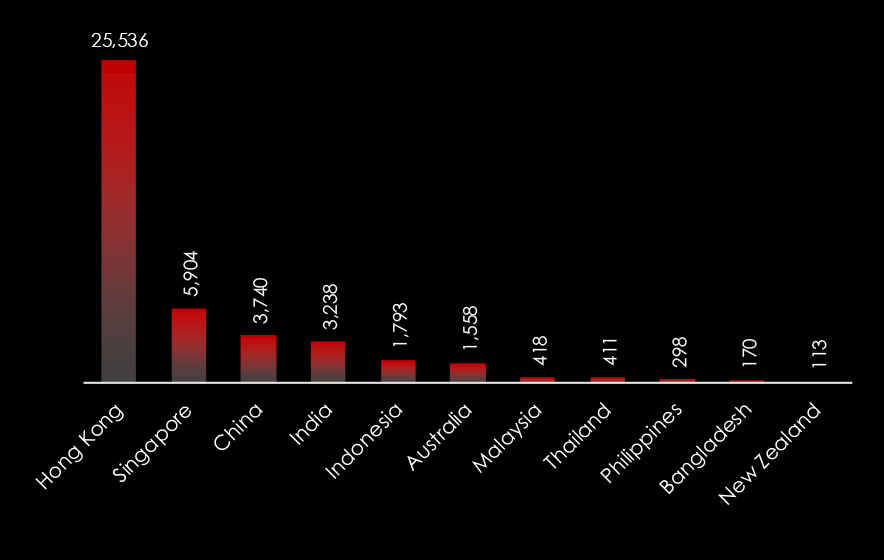
Comparing the most frequent phishing themes globally and in Thailand, we can see that Online/Cloud Services, e-commerce, and Logistics & Couriers with Finance are the most prominent themes in Thailand.
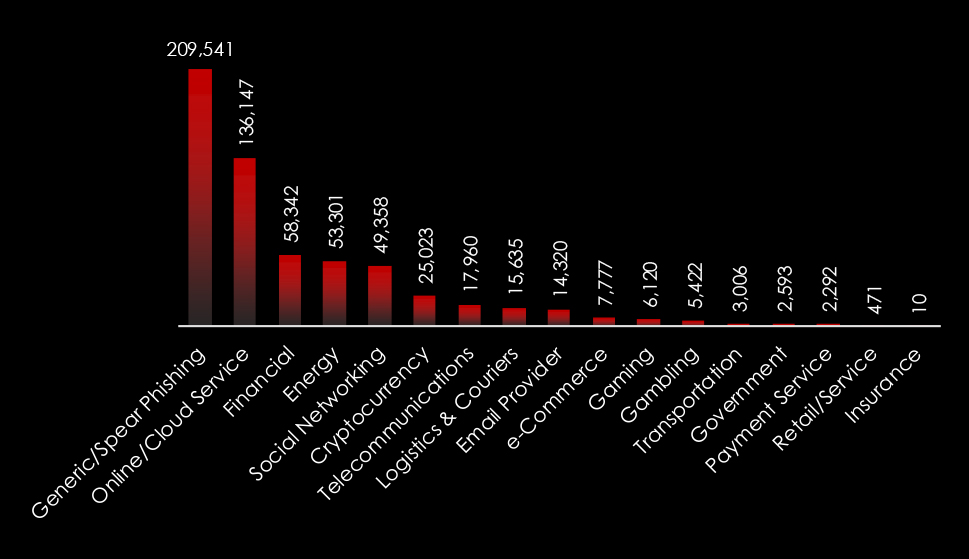
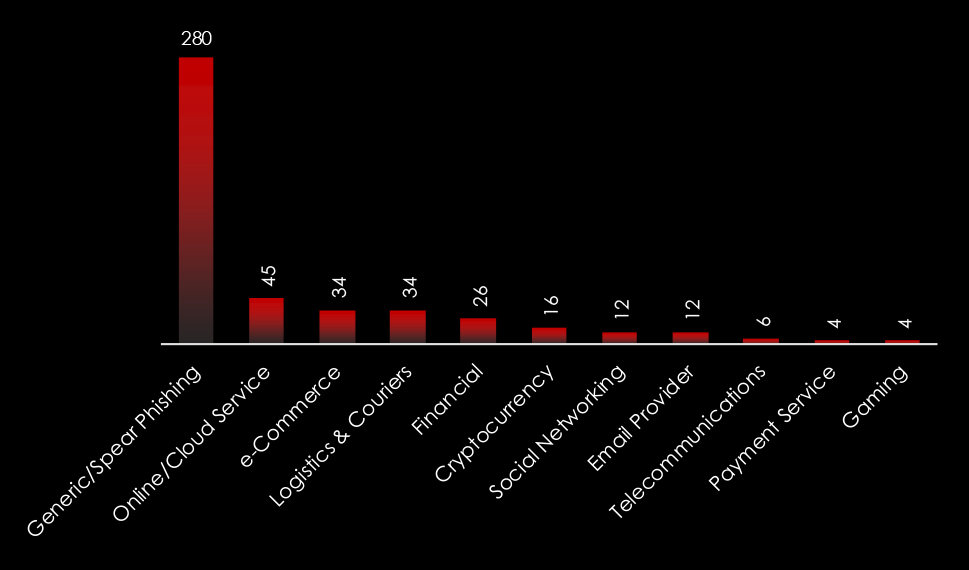
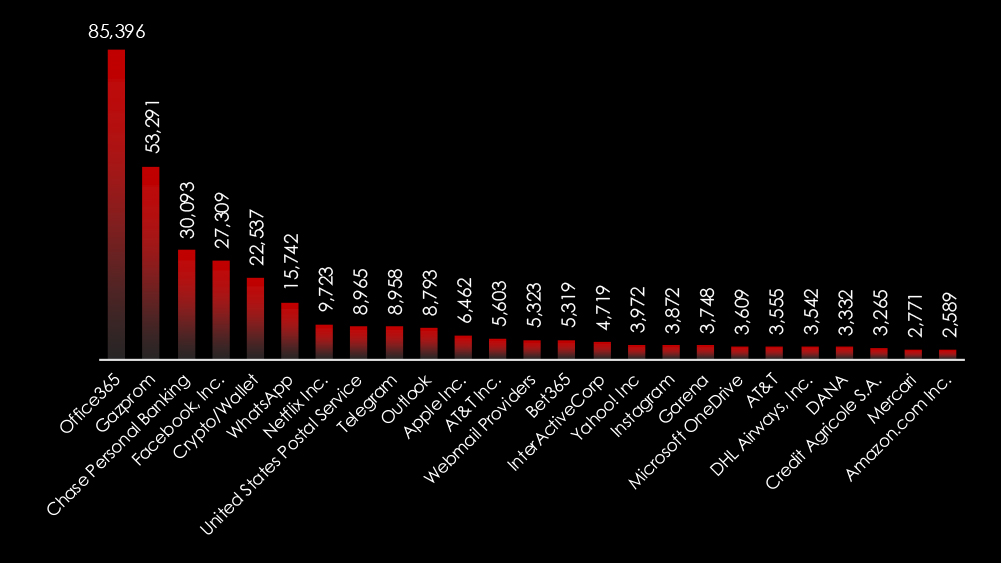
Comparing the most frequently impersonated brands globally and in Thailand, we can see specific Online/Cloud Services, e-Commerce, Logistics & Couriers, Finance brands, and organizations.
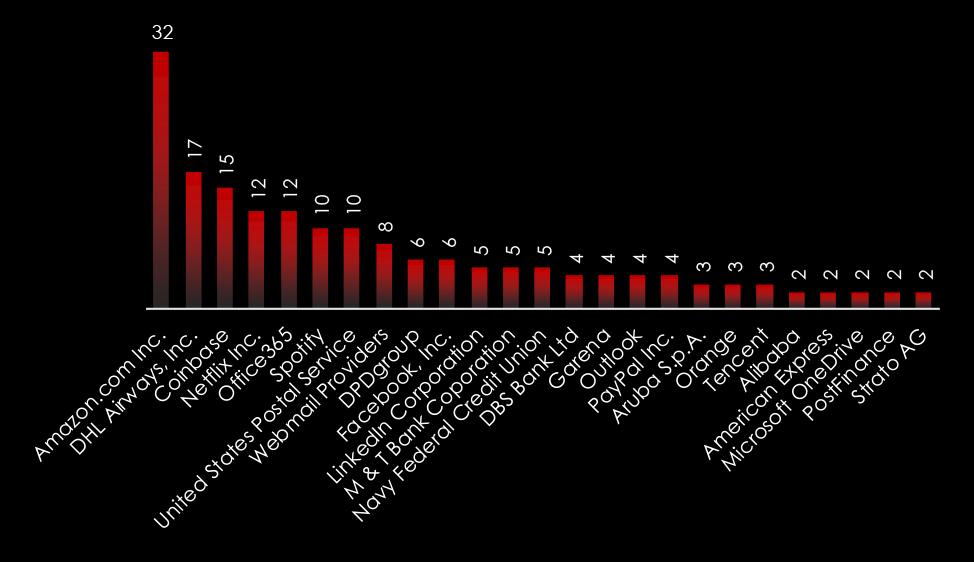
Ransomware groups target Thailand due to its rapidly growing digital economy, increased internet penetration, and expanding digital transformation across various sectors, including finance, healthcare, and e-commerce. The country’s significant reliance on digital infrastructure makes it an attractive target for cybercriminals seeking financial gains. Additionally, the perceived lower levels of cybersecurity awareness and preparedness in some organizations provide opportunities for successful attacks. Ransomware groups exploit these vulnerabilities to encrypt critical data and demand substantial ransoms, knowing that affected entities may be more willing to pay to restore their operations swiftly.
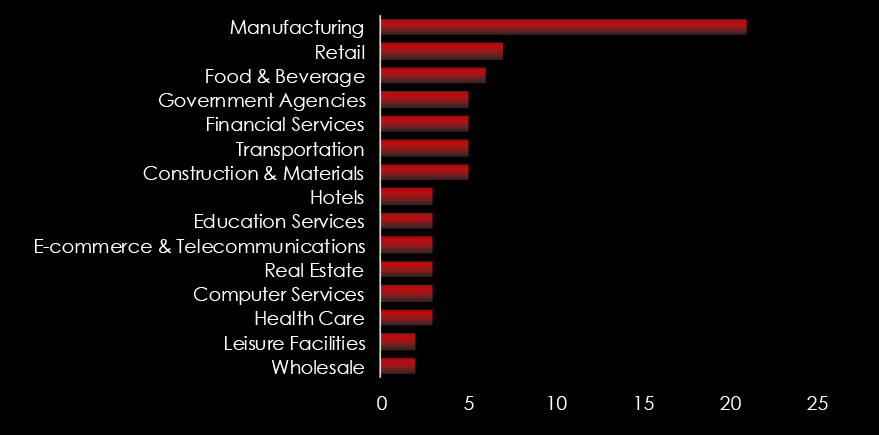
Manufacturing, Retail, Food & Beverage, Government Agencies, and Financial services are the top targets of ransomware actors in Thailand.
Data leaks play a crucial role in the cyber threat landscape, acting as a significant vulnerability that can lead to a wide range of security issues and potential damages. When sensitive or confidential information is accidentally exposed or intentionally stolen and released, it can lead to identity theft, financial fraud, and a severe loss of trust and reputation for the affected organization. Such leaks often provide cybercriminals with the necessary data to conduct more targeted and effective attacks, such as phishing schemes, ransomware attacks, or further unauthorized access into secure systems. Additionally, data leaks can result in hefty regulatory fines and legal challenges, especially if the leaked information includes personally identifiable information (PII) protected under data privacy laws.
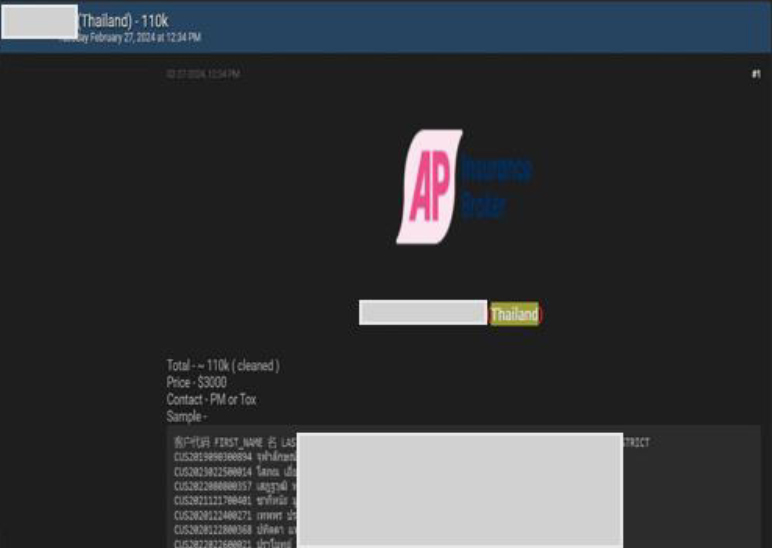
AP Insurance data advertised on a Leak Site
Summary: The CYFIRMA Research team observed a potential data sale related to AP Insurance, {www[.]apinsurance[.]co[.]th } in an underground forum. AP Insurance Broker Co., Ltd. (AP Insurance) is a Thai insurance broker company offering a wide range of insurance products from over 30 leading insurance companies. Their services include various types of insurance, such as motor, health, travel, and life insurance, aiming to cater to the diverse needs of their customers. The company is committed to providing professional advice and optimal insurance solutions to both, individuals and businesses. The data for sale includes sensitive and confidential information, such as first name, last name, ID card, mobile number, address, and other personal details. The price for the data being sold is USD 3000. The threat actor; Infamous, claims responsibility for the data breach.
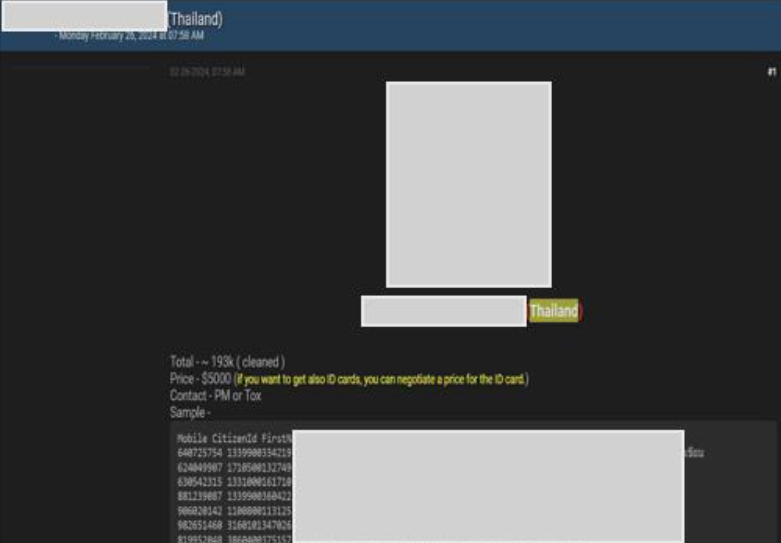
Thai Paiboon Insurance PLC data advertised on a Leak Site
Summary: The CYFIRMA Research team observed a potential data sale related to Thai Paiboon Insurance PLC, {www[.]thaipaiboon[.]com} in an underground forum. Thai Paiboon Insurance PLC is a company that operates in the Insurance industry. The data available for sale includes Mobile Numbers, Citizen IDs, First Names, Last Names, Birthdates, Genders, Addresses, and other confidential information. The price for the data being sold is USD 5000. The threat actor; Infamous, claims responsibility for the data breach.
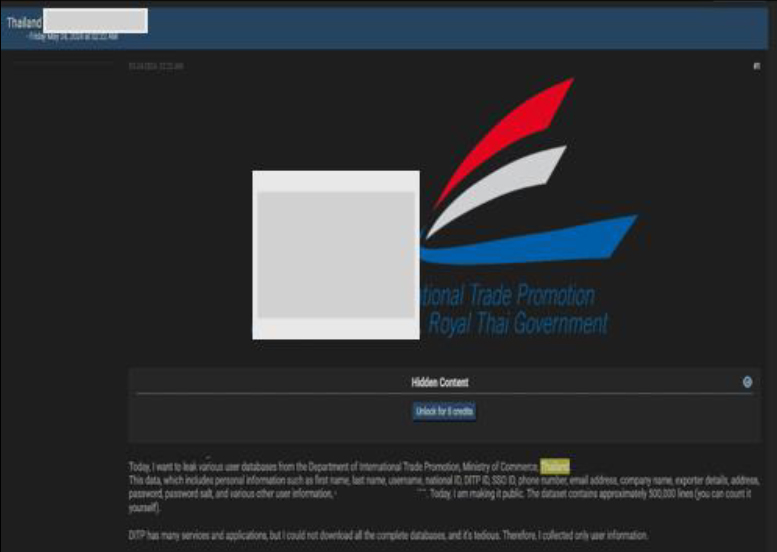
Department of International Trade Promotion, Ministry of Commerce, Thailand data advertised on a Leak Site
Summary: The CYFIRMA Research team observed a potential data leak related to the Department of International Trade Promotion, Ministry of Commerce, Thailand, {www[.]ditp[.]go[.]th} in an underground forum. The Department of International Trade Promotion (DITP) is an important agency within the Ministry of Commerce in Thailand. Its primary mission is to promote and facilitate international trade and enhance the global competitiveness of Thai products and services. The leaked data includes personal information, such as first name, last name, username, national ID, DITP ID, SSO ID, phone number, email address, company name, exporter details, address, password, password salt, and various other user information.
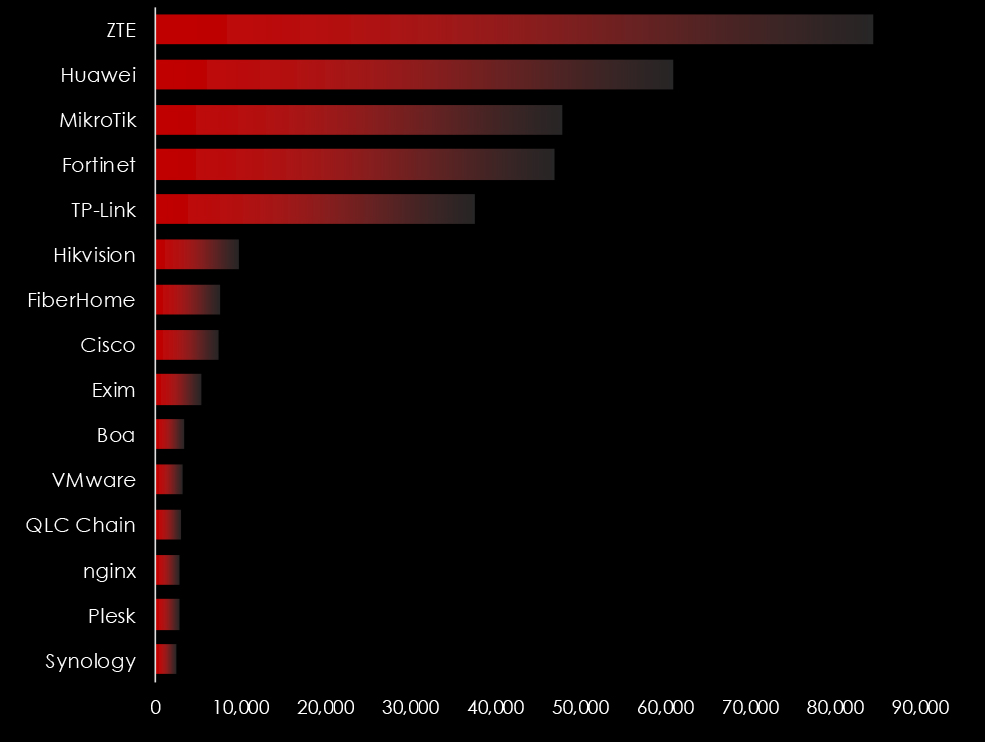
Exposed IoT devices play a significant role in cyber attacks due to their often inadequate security features and widespread adoption across various sectors. These devices can serve as entry points or targets in larger network breaches, primarily because they frequently lack robust encryption, undergo infrequent updates, and have default or weak credentials that are easily exploited. Once compromised, IoT devices can be used to form botnets, enabling attackers to conduct DDoS (Distributed Denial of Service) attacks, data breaches, or surveillance. Their connectivity and access to larger networks also make them a valuable asset for attackers looking to move laterally within infrastructure, escalate privileges, or disrupt critical services. This vulnerability is exacerbated by the rapid expansion of IoT devices in homes, industries, and cities without corresponding advancements in their security frameworks.
| Vulnerability | Vendor | Product |
| CVE-2023-20198 | Cisco | Cisco IOS XE |
| CVE-2018-10562 | Dasan | Dasan GPON Home Router |
| CVE-2014-8361 | Realtek | Realtek SDK |
| CVE-2015-2051 | D-Link | D-Link DIR-645, DAP-1522 revB, DAP-1650 revB, DIR-880L, DIR-865L, DIR-860L revA, DIR-860L revB DIR-815 revB, DIR-300 revB, DIR-600 revB, DIR-645, TEW-751DR, TEW-733GR |
| CVE-2024-27198 | JetBrains | TeamCity |
| CVE-2017-9841 | PHPUnit | PHPUnit |
| CVE-2024-21887 | Ivanti | Ivanti Secure Connect and Policy Secure |
| CVE-2019-7192 | QNAP | QNAP NAS devices running Photo Station |
| CVE-2019-9670 | Synacor | Zimbra Collaboration Suite |
| CVE-2020-16846 | SaltStack | Salt |
| CVE-2017-18368 | Zyxel/Billion | ZyXEL P660HN-T1A v1, ZyXEL P660HN-T1A v2, Billion 5200W-T |
| CVE-2021-3129 | Laravel | Ignition |
| CVE-2021-44228 | Apache | Log4j |
| CVE-2022-37042 | Synacor | Zimbra Collaboration Suite |
| CVE-2023-22527 | Atlassian | Confluence |