



The Asia Pacific (APAC) Threat Landscape Report provides a comprehensive overview of the evolving cybersecurity landscape in the region. In recent years, Asia Pacific has witnessed a significant increase in cyber threats, driven by factors such as rapid digitalization, increased internet penetration, and geopolitical tensions. This report aims to provide key insights into the current state of cyber threats, and emerging trends.
THE GEOGRAPHICAL SCOPE OF THIS REPORT
Japan, Philippines, Vietnam, Malaysia
APAC Volume – 1
Australia, Bangladesh, India, Indonesia
APAC Volume – 2
Japan, Philippines, Vietnam, Malaysia
YET TO BE UPDATED
New Zealand, Singapore, South Korea, Taiwan, Thailand
UPDATED METHODOLOGY
This is a running report. Our research team will update this report on an ongoing basis to keep the reader updated on the evolving cyber threat landscape of the region.
01 MOVEMENT FROM DIGITAL TO KINETIC TARGETS
Trend: Ransomware attacks on critical infrastructure
Motives: Disruption/Geopolitical/Extortion
02 DATA EXFILTRATION FROM IOT DEVICES
Trend: Spyware, malware and plug-ins to collect data.
Motive: Reputation impact, disruption, extortion
03 EXPLOITATION OF LEGACY SYSTEM
Trend: Brute force attacks, credential reuse and data exfiltration via malware
Motive: Operational disruption, espionage, IP exfiltration
04 CROSS-ENVIRONMENT ATTACK
Trend: social engineering/phishing. jump server Exploits, remote access tool compromise
Motive: Operational disruption, espionage, IP exfiltration
05 USE OF BOTNETS, AI, DEEP FAKE
Trend: Device scanning, firmware, phishing/malware download
Motives: Disruption, data harvesting, remote attacks (DDOS)
06 SUPPLY CHAIN OF INFRASTRUCTURE, UTILITY COMPANIES REMAIN AT RISK
Trend: Multi-behavioral malware (IT/OT), different operating system
Target: CII trade secrets documents containing proprietary processes
INCREASED SOPHISTICATION OF CYBER ATTACKS
The region has witnessed a rise in the sophistication of cyber attacks, with threat actors employing advanced techniques to compromise systems and networks.
TARGETED THREATS AGAINST CRITICAL INFRASTRUCTURE
Critical infrastructure sectors face heightened risks, with threat actors showing a growing interest in targeting key industries such as energy, finance, and telecommunications.
RISE IN RANSOMWARE INCIDENTS
Ransomware attacks have surged in frequency and severity, posing significant challenges to businesses and government entities. The attackers often demand cryptocurrency payments for the release of compromised data.
NATION-STATE THREATS AND CYBER ESPIONAGE
Evidence suggests an increase in nation-state-sponsored cyber activities, including cyber espionage and information warfare. This poses significant geopolitical and security concerns for the region.
SUPPLY CHAIN VULNERABILITIES
The report identifies vulnerabilities in the regional supply chain, with cybercriminals exploiting weaknesses in third-party relationships to gain unauthorized access to targeted organizations.
Japan’s diverse industrial sectors and cutting-edge technology products make it an appealing target for nation-state attackers and financially motivated threat actors. Furthermore, hacktivists have also been observed targeting Japanese industries alongside APT and other threat actors, reflecting the multifaceted cybersecurity challenges these sectors face.
From a geopolitical standpoint, Japan confronts substantial challenges stemming from China, Russia, and North Korea. These challenges relate to regional dominance, its strategic alliances with QUAD and NATO, as well as ongoing territorial disputes.
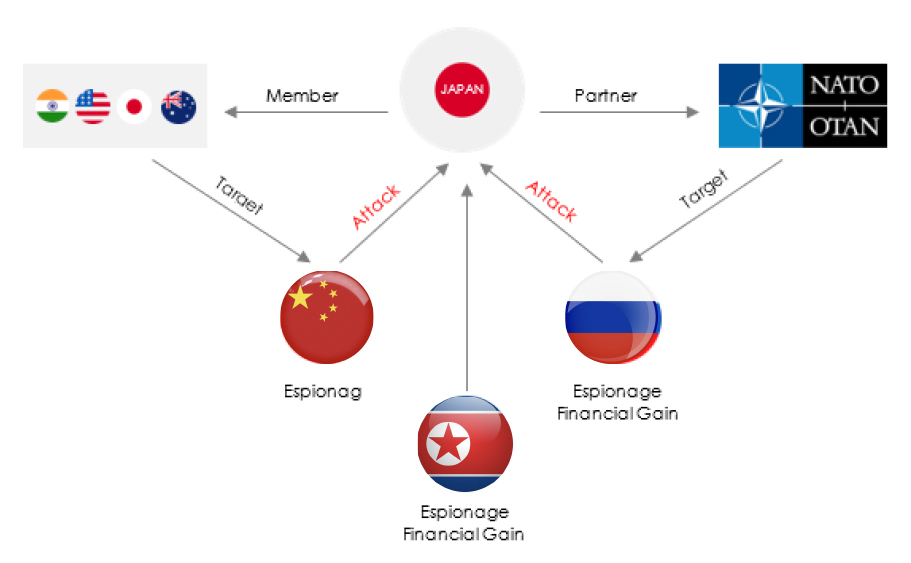
CHINA
Japan’s geopolitical risk factors in relation to China have shifted significantly in recent years. After World War II, Japan adopted a strong pacifist stance, prioritizing economic growth over military expenditure. However, the rise of China’s expansionist policies in the Indo-Pacific, particularly the looming threat of a Chinese invasion of Taiwan, has prompted Japan to reevaluate its security posture. Japanese Prime Minister Fumio Kishida’s announcement to double defense spending from one to two percent of GDP signifies a substantial departure from the country’s historical defense policy. This change, which builds upon the efforts of the previous Prime Minister Shinzo Abe, reflects Japan’s increasing focus on countering China and deepening military integration with the United States. As Japan strategically shifts military capabilities to its southwest islands, Taiwan emerges as a key flashpoint in its security considerations.
In essence, Japan’s evolving geopolitical risk factors with respect to China are characterized by a departure from decades of pacifism, a substantial increase in defense spending, a growing emphasis on countering Chinese influence, and a heightened awareness of Taiwan’s significance as a potential security flashpoint. These developments represent a significant transformation in Japanese security policy as it adapts to changing regional dynamics and challenges posed by China’s assertive posture in the Indo-Pacific.
NORTH KOREA
During the Cold War, Japan primarily focused on the threat posed by the Soviet Union, positioning its limited military capabilities in the northern regions. However, with the end of the Cold War, Japan shifted its attention towards the threat emanating from North Korea in the east.
In recent years, North Korea has been escalating tensions through a series of missile tests and nuclear posturing on the Korean Peninsula. The year 2022 witnessed unprecedented missile tests, including intercontinental ballistic missiles fired over Japanese territory. Furthermore, North Korea has strengthened its alignment with Russia and China, pledging closer strategic and tactical cooperation which enables North Korea to conduct more aggressive testing with relative impunity.
In addition to this, North Korea’s export of weapons to Russia for its war in Ukraine, possibly in exchange for cyber know-how and intelligence, raises concerns about the potential for North Korean cyber activities. Japan – along with South Korea and Australia – is among the most exposed geographies to North Korean cyber activities, however, North Korean threat actors are known for their opportunistic approach, engaging in criminal activities such as ransomware-based operations to generate financial profit wherever opportunities arise.
RUSSIA
Japan’s relationship with Russia has been strained due to a longstanding territorial dispute over the Kuril Islands, known as the Northern Territories in Japan. Recent developments indicate a significant change in Japan’s rhetoric concerning these disputed islands: Japanese Foreign Minister Yoshimasa Hayashi has accused Russia of occupying the Northern Territories without legal grounds, while Prime Minister Fumio Kishida asserted Japan’s sovereignty over them.
This shift in Japan’s stance follows Russia’s aggression in Ukraine and contrasts with the previous administration’s efforts to resolve the territorial dispute peacefully using softer language. While Russia’s current military capacity may not permit overt provocation, concerns have arisen about the use of cyberattacks to caution Japan not to overstep boundaries.
Japan’s changing security posture is not occurring in isolation. It is part of a broader transformation in the U.S.-Japan alliance, involving South Korea, Australia, and the Philippines in defense alliances. This shift is in response to China’s assertive behavior in the region; a more capable North Korea, and Russia’s growing discontent, potentially leading to unpredictable actions.
These geopolitical factors require Japan to maintain a vigilant and adaptive approach to its national security and defense strategies.
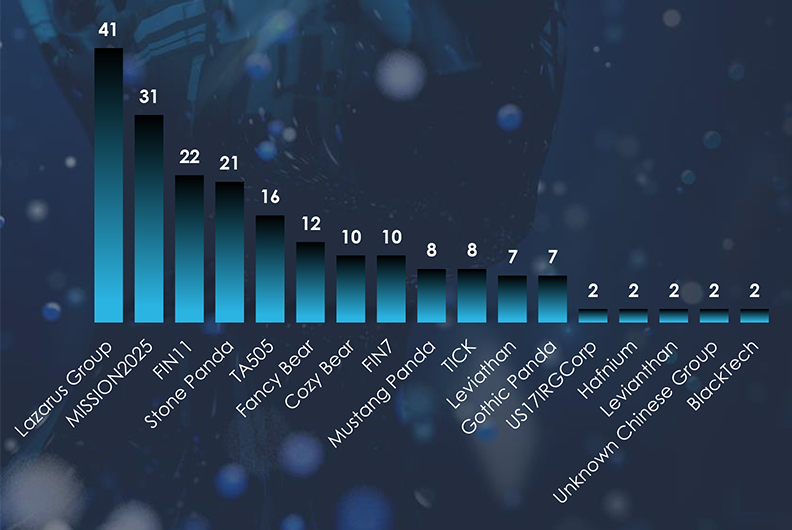
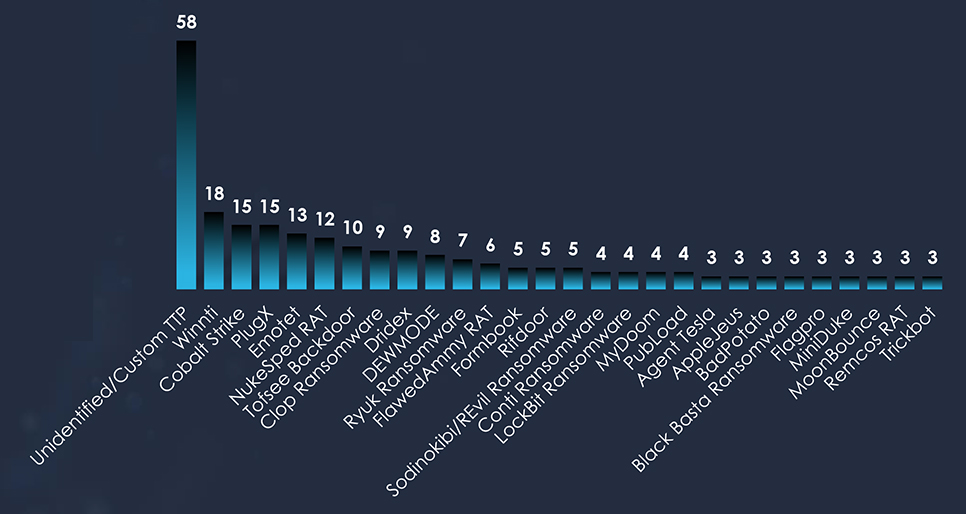
Top observed malware highly correlates with the suspected actors. Winnti & PlugX for MISSION2025, NukeSped RAT & Tofsee for Lazarus Group, and Emotet with various ransomware by Russian cybercrime syndicates. Cobalt Strike is used by everyone as it is highly effective and offers plausible deniability.

| Malware Name | Targeted Services/ Vulnerabilities | Campaign Name | Suspected Threat Actor | Target Industries | Target Geographies |
| Korplug, Sogu, NukeSped RAT | Web Application | amnok | Mustang Panda,Lazarus Group | Multiline Retail, Electronic Equipment, Instruments & Components, Industrial Conglomerates, Energy Equipment & Services, Oil, Gas & Consumable Fuels, Diversified Financial Services | Singapore, Norway, the United States, Japan, the United Kingdom, Australia, Switzerland, Germany |
| NukeSped RAT, DLRAT | Web Application | Gather speed | Lazarus Group | Banks, Diversified Financial Services, Professional Services | Canada, South Korea, the United States, Japan, the United Kingdom, Australia, India |
| Winnti | Web Application | ivanti | MISSION2025, Stone Panda | Diversified Telecommunication Services, Industrial Conglomerates, Wireless Telecommunication Services, IT Services | Netherlands, Singapore, the United States, Japan, the United Kingdom, Germany |

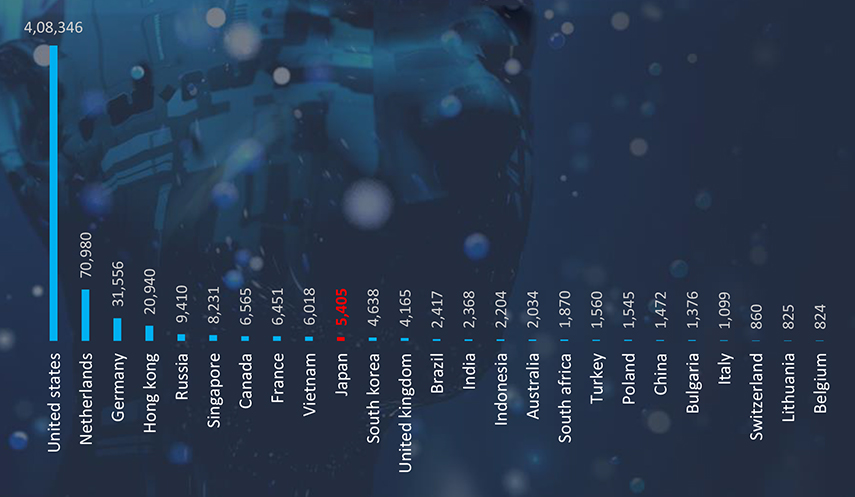
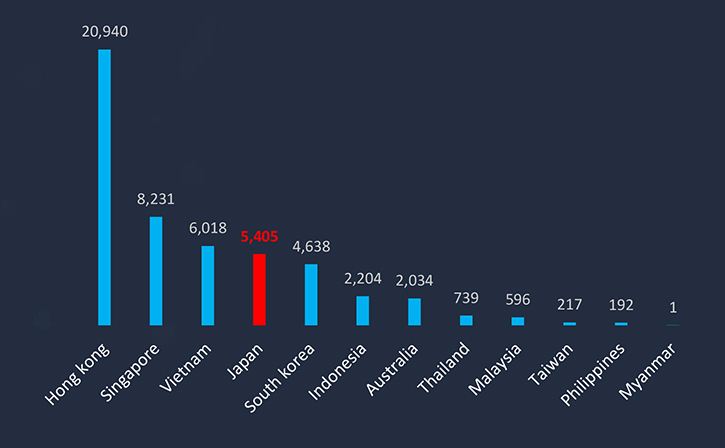
During the last 6 months, CYFIRMA’s advanced telemetry systems detected a total of 608,999 phishing campaigns. This sample size gives us enough insight into the overall threat landscape. Geography is based on ASN origin of the email. Japan ranked as the 10th largest source of phishing globally.
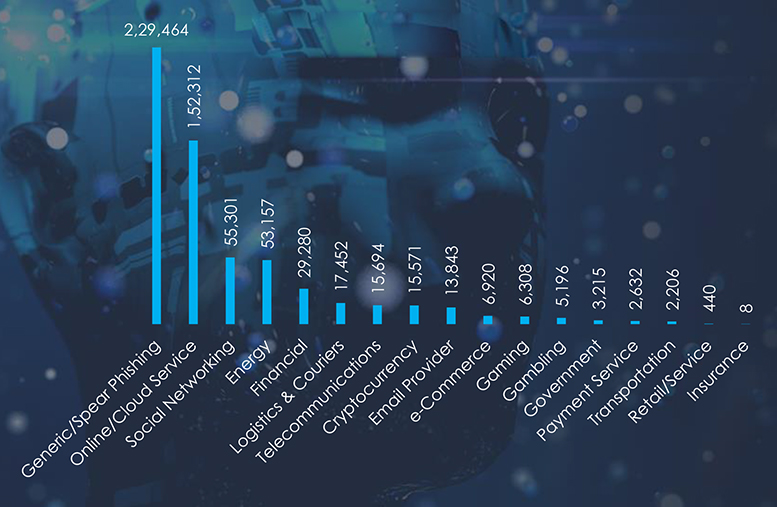
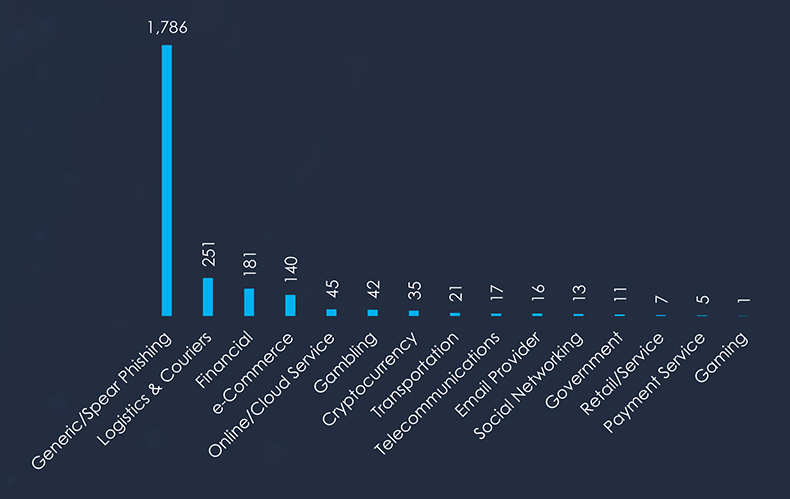
Comparing the most frequent phishing themes globally and in Japan, we can see that Logistics & Couriers, Finance and e-Commerce are the most prominent themes in Japan.
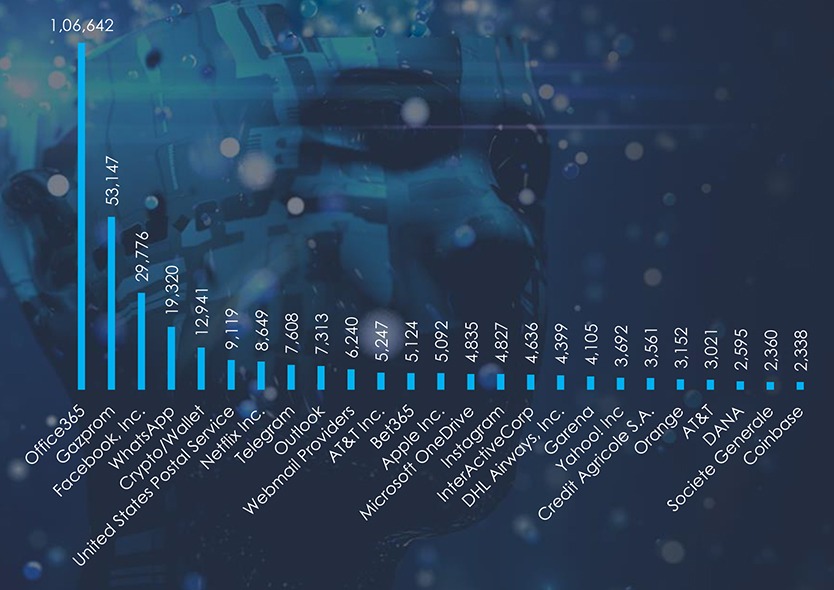
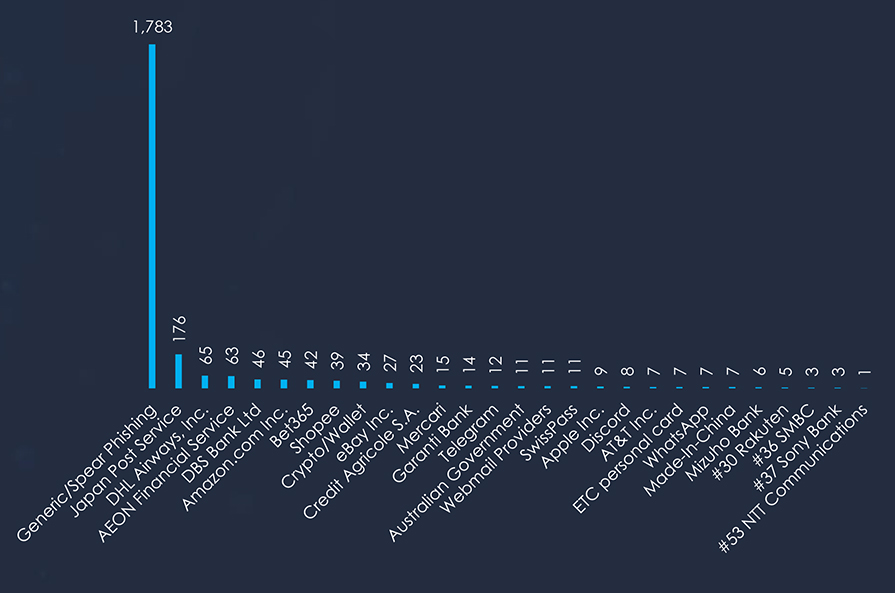
Comparing the most frequently impersonated brands globally and in Japan, we can see the specific Logistics & Couriers, Finance. and E-commerce brands and organizations.
Analysing domains of phishing links in the “Generic/Spear Phishing” category for Japan statistics showed a significant presence of AEON, Amazon, and SMBC-Card.
Data leaks play a crucial role in the landscape of cyber threats, acting as a significant vulnerability that can lead to a wide range of security issues and potential damages. When sensitive or confidential information is accidentally exposed or intentionally stolen and released, it can lead to identity theft, financial fraud, and a severe loss of trust and reputation for the affected organization. Such leaks often provide cybercriminals with the necessary data to conduct more targeted and effective attacks, such as phishing schemes, ransomware attacks, or further unauthorized access into secure systems. Additionally, data leaks can result in hefty regulatory fines and legal challenges, especially if the leaked information includes personally identifiable information (PII) protected under data privacy laws.
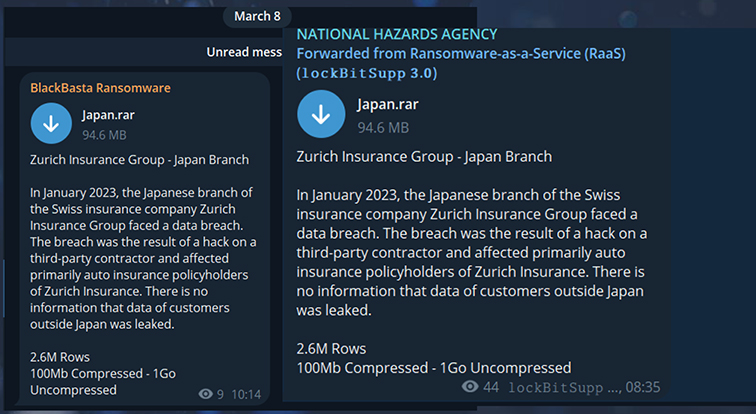
The Zurich Insurance (Japan) breach from 2023 is back in the spotlight as the leaked data is re-circulating on Telegram. Additionally, the BlackBasta ransomware group has also re-shared the old data in their Telegram group highlighting its demand and significance.
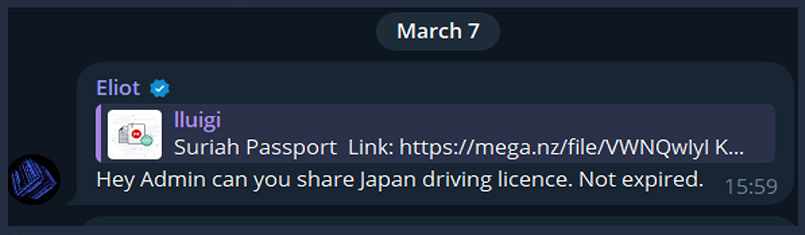
A user on Telegram requesting fresh Japanese driving license leaks, hinting that they might plan to use it for forging documents for other harmful purposes.
Daiho Industrial, a leading plastics processing industry in Japan, has recently experienced a data leak. The leaked data, approximately 187 GB in size, is now circulating on a Telegram data leak channel and has been reshared across multiple groups, making it freely available for download.

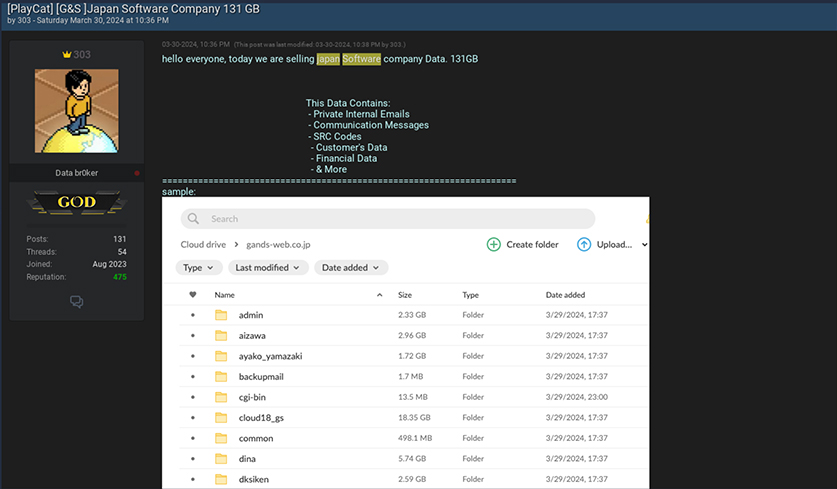
CYFIRMA identified a threat actor known as DATA Br0ker offering a 131GB database from a Japanese software company (G&S) for sale on underground forums. This database comprises private internal emails, communication messages, source codes, customer data, financial records, and additional sensitive information. It’s worth noting that this company’s data appears to be available on other underground platforms as well.
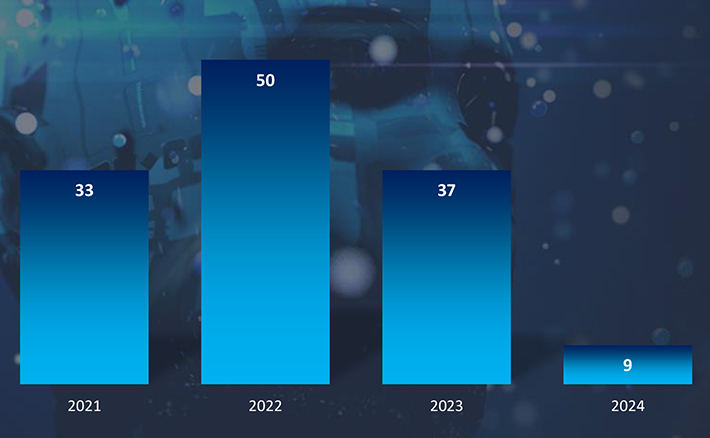
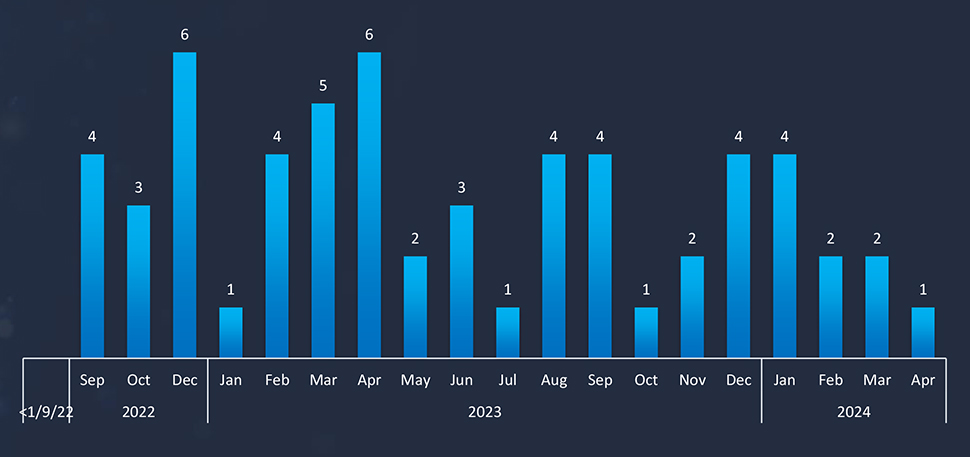
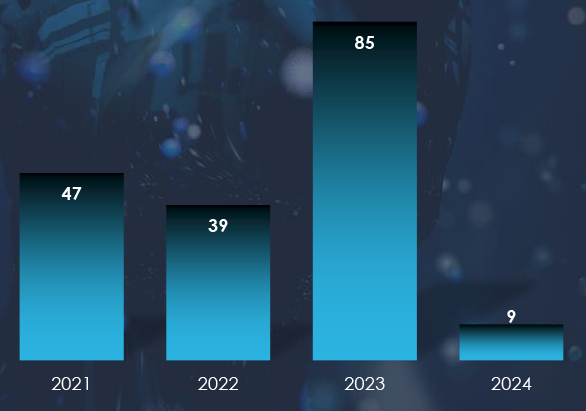
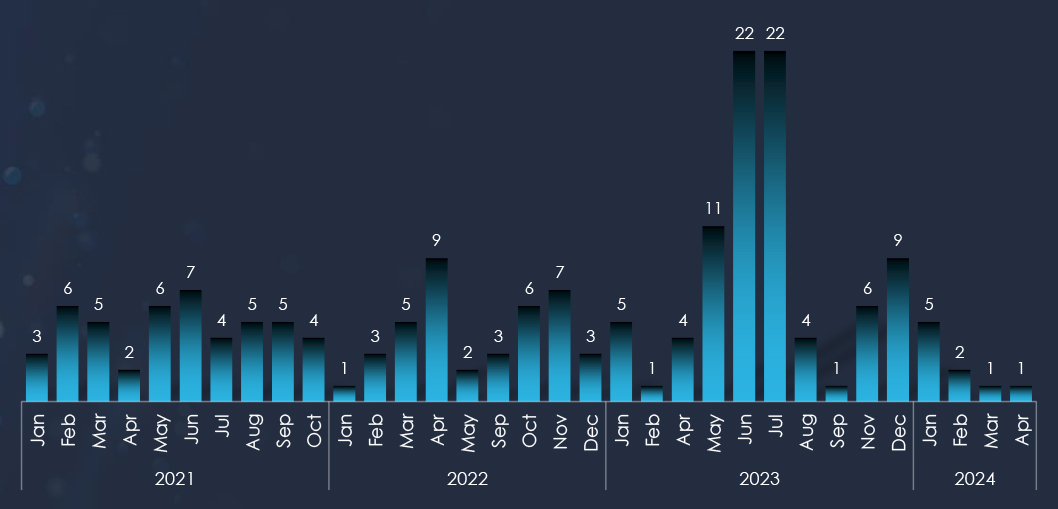
Japan stands as one of the most targeted countries in the world, and the most targeted country in the Asia Pacific Region. English-speaking countries – led by the USA – remain the most targeted, with the US alone recording half of all ransomware victims.
As per statistics by year since 2021 and by month since September 2022, we can see a slightly downward trend in observed victims, This is great news because the overall number of victims globally was growing.
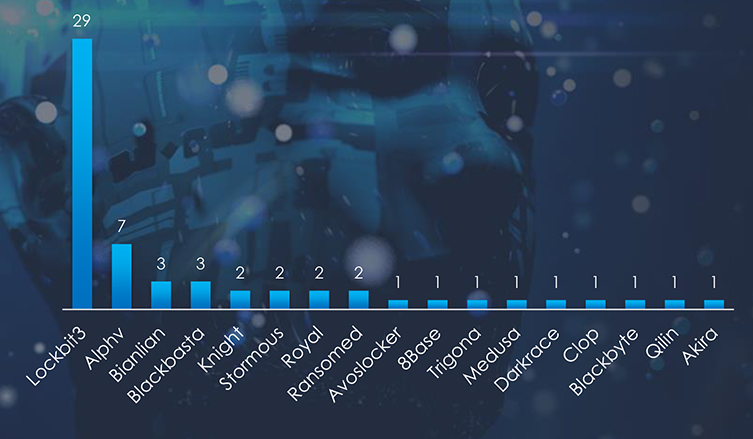
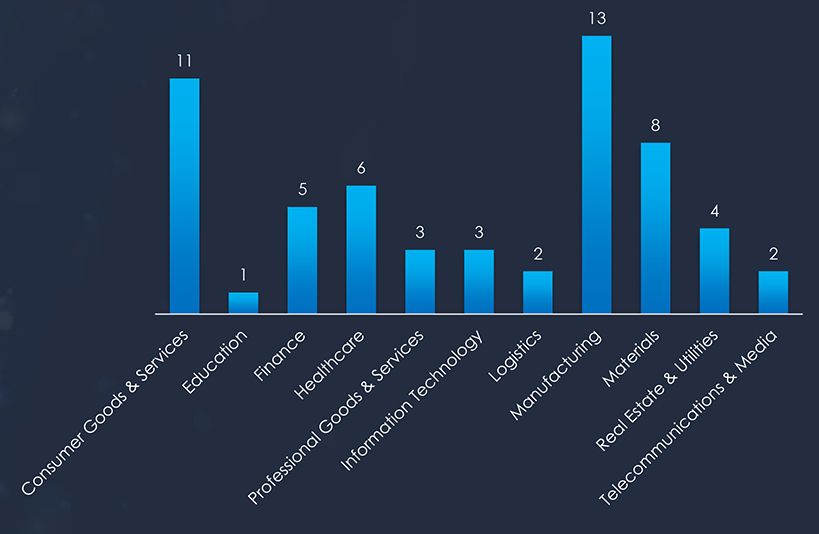
Since 2022, LockBit3 has been the most prominent ransomware in Japan. Among the sectors within Japan, Manufacturing is the most targeted industry. Followed by Consumer Goods & Services, Materials and Healthcare.
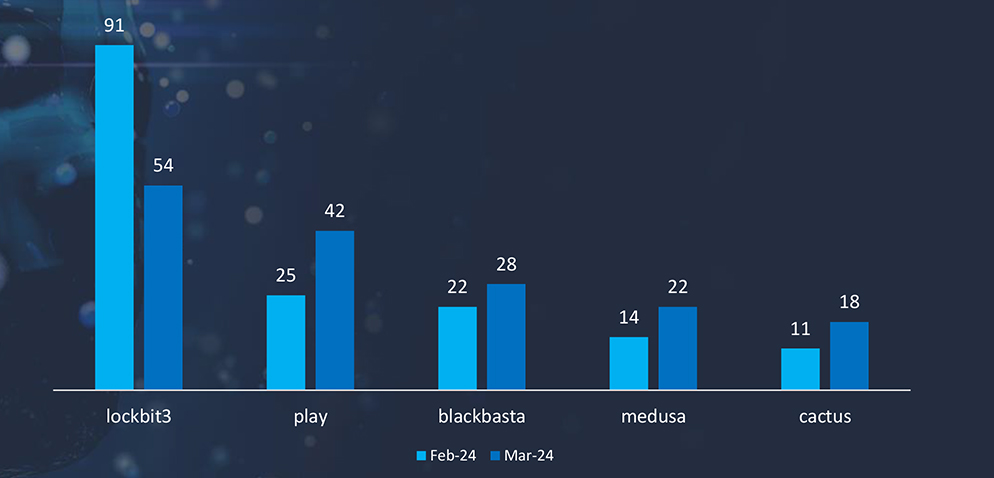
Law enforcement actions in February against LockBit3 have significantly affected the LockBit3 affiliate program. Unfortunately, it did not affect the number of ransomware attacks as the affiliates simply moved to other Ransomare-as-a-Service.
| Exploited Vulnerabilities | Vendor | Product |
| CVE-2023-22527 | Atlassian | Confluence |
| CVE-2023-20198 | Cisco | Cisco IOS XE |
| CVE-2023-22518 | Atlassian | Confluence |
| CVE-2017-9841 | PHPUnit – Sebastian Bergmann | PHPUnit |
| CVE-2018-10562 | Dasan | Dasan GPON Home Router |
| CVE-2021-3129 | Laravel | Ignition |
| CVE-2017-18368 | Zyxel/Billion | ZyXEL P660HN-T1A v1, ZyXEL P660HN-T1A v2, Billion 5200W-T |
| CVE-2015-2051 | D-Link | D-Link DIR-645, DAP-1522 revB, DAP-1650 revB, DIR-880L, DIR-865L, DIR-860L revA, DIR-860L revB DIR-815 revB, DIR-300 revB, DIR-600 revB, DIR-645, TEW-751DR, TEW-733GR |
| CVE-2018-14558 | Tenda | Tenda AC7/AC9/AC10 |
| CVE-2023-42793 | JetBrains | TeamCity |
| CVE-2016-1555 | NETGEAR | WN604, WN802Tv2, WNAP210v2, WNAP320, WNDAP350, WNDAP360, and WNDAP660 |
| CVE-2016-3088 | Apache | ActiveMQ |
| CVE-2017-1000486 | PrimeFaces | PrimeTek |
| CVE-2017-15944 | Palo Alto Networks | PAN-OS |
| CVE-2020-15505 | MobileIron | MobileIron Mobile Device Management (MDM) |
All the observed exploited vulnerabilities in the above list are also part of the CISA Known Exploited Vulnerability list.
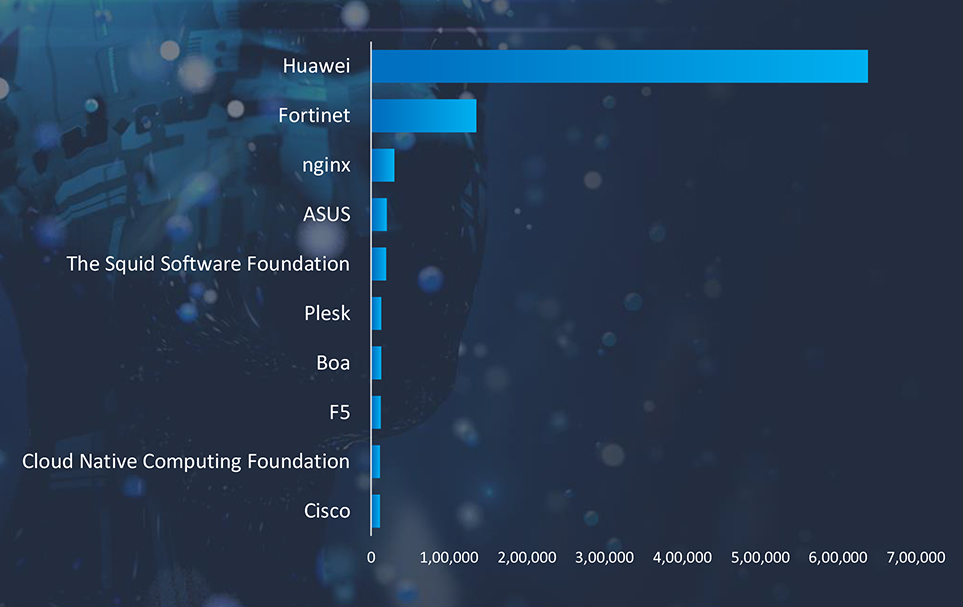
Exposed IoT devices play a significant role in cyber attacks due to their often inadequate security features and widespread adoption across various sectors. These devices can serve as entry points or targets in larger network breaches, primarily because they frequently lack robust encryption, undergo infrequent updates, and have default or weak credentials that are easily exploited. Once compromised, IoT devices can be used to form botnets, enabling attackers to conduct DDoS (Distributed Denial of Service) attacks, data breaches, or surveillance. Their connectivity and access to larger networks also make them a valuable asset for attackers looking to move laterally within infrastructure, escalate privileges, or disrupt critical services. This vulnerability is exacerbated by the rapid expansion of IoT devices in homes, industries, and cities without corresponding advancements in their security frameworks.
Industrial Control Systems (ICS) are integral to the functioning of various critical infrastructures such as power plants, water treatment facilities, transportation systems, and manufacturing units. These systems are strategically important, making them potential targets for various threat actors.
In our OSINT research, we found around 3,269 Industrial Control Systems exposed to the Internet owned by organizations in Japan, potentially allowing an attacker to access them.
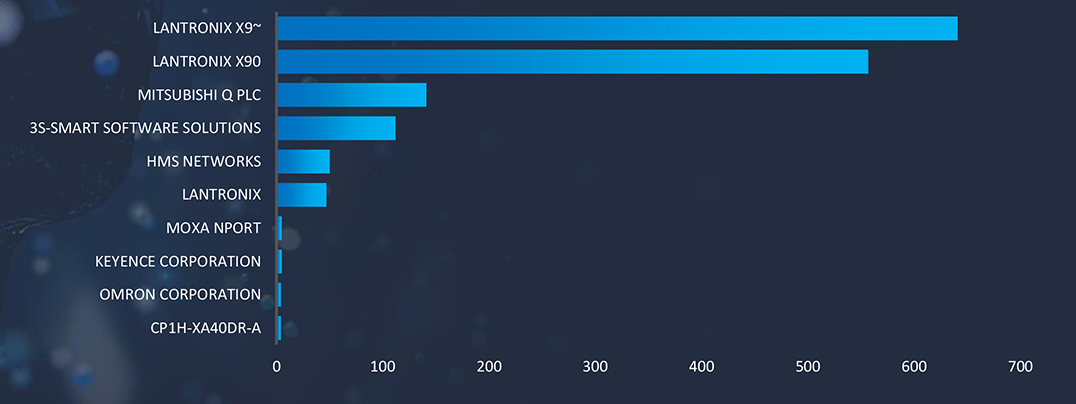
JVN trend depicts increased exploitation of vulnerabilities spread across various IT products.
Note: JVN, which stands for Japan Vulnerability Notes, is a portal site on IT product vulnerability information handled in the Japanese framework called “The Information Security Early Warning Partnership.“ It provides detailed information on each vulnerability including a summarized description, affected products, possible impacts, solutions, vendor statements, and reference documents.
The exploitation of vulnerabilities, particularly zero-day vulnerabilities, serves as a favored entry point for threat actors seeking to bypass detection mechanisms. Notably, both Chinese and Russian threat actors have gained notoriety for their adeptness in leveraging zero-day exploits as part of their espionage efforts. Moreover, these threat actors actively seek opportunities to launch supply chain attacks, aiming to compromise a wider attack surface. This multifaceted approach underscores the continually evolving tactics employed by these adversaries. Given Japan’s expansive industrial sectors and the significant shift toward industrial automation, it becomes paramount to emphasize the critical importance of effective vulnerability management. This approach is essential to secure various aspects of the technology landscape, including Operational Technology (OT), Industrial Control Systems (ICS), IoT devices, and all interconnected systems, ensuring the continued integrity and security of Japan’s critical infrastructure.
The Quantum of DDoS attacks increased globally after the start of the Russia-Ukraine war when pro-Russian and pro-Ukraine hacktivists started targeting each other with DDoS campaigns and also started targeting alliance nations to show support to their respective country. Japan is the most targeted country in Asia by pro-Russian hacktivists.
Meanwhile, Japan is also receiving heat from pro-Palestine hacker groups, , facing attacks on multiple websites within its digital realm due to its stance on the Israel-Palestine conflict.
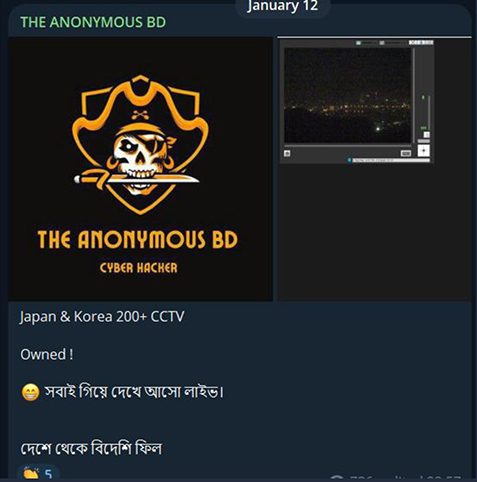
The hacktivist group from Bangladesh, known as “Anonymous BD,” has leaked the IP addresses and credentials of 200 CCTV cameras from Japan and Korea.
The Russian group known as Noname057(16) has been conducting DDoS attacks against several websites, particularly targeting Japan due to its stance against the Russian-Ukraine war.
List of hacktivist groups actively targeting Japan
These channels may represent potential threats to Japan cybersecurity and should be closely monitored and addressed by relevant authorities to prevent any malicious activities.
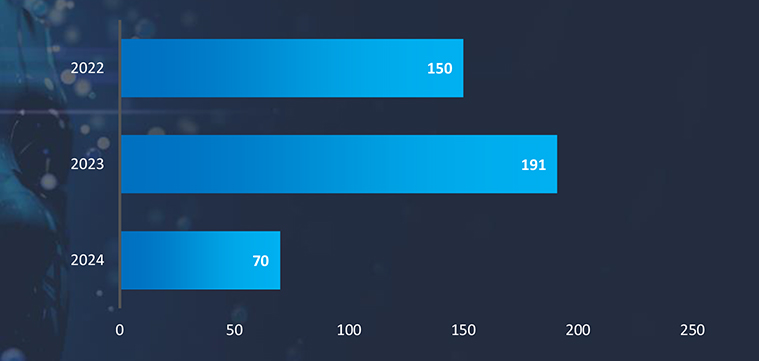
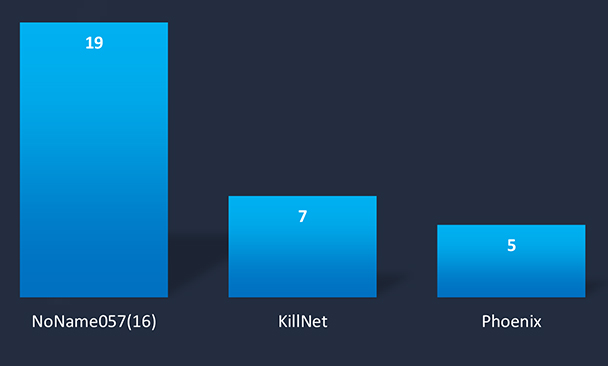
Overall, we observed 31 campaigns targeting Japan. Government Institutions, Transportation, and Manufacturing are the most targeted industries by pro-Russian hacktivists.

The cyber threat landscape extends beyond Japan’s geographical borders, with overseas subsidiaries and affiliated companies emerging as appealing targets for threat actors seeking access to global Japanese brands. In recent large-scale attacks on Japanese enterprises, adversaries have strategically chosen to compromise these overseas entities as a gateway into the networks of their Japanese counterparts. Several key factors contribute to this approach:
Varied Security Oversight: overseas affiliates often exhibit varying levels of security oversight compared to their Japanese counterparts. This discrepancy can make them more vulnerable entry points for attackers.
Security Vulnerabilities via Acquisitions: the acquisition of overseas firms can introduce pre-existing security vulnerabilities into the parent company’s network. Additionally, it may lead to the development of separate security hierarchies that do not align with the security culture of the parent company, creating potential weak links in the overall defense.
Language Barriers: language barriers can also play a role in this strategy. Attackers may exploit communication challenges to infiltrate Japanese companies through overseas partners, taking advantage of gaps in understanding and coordination.
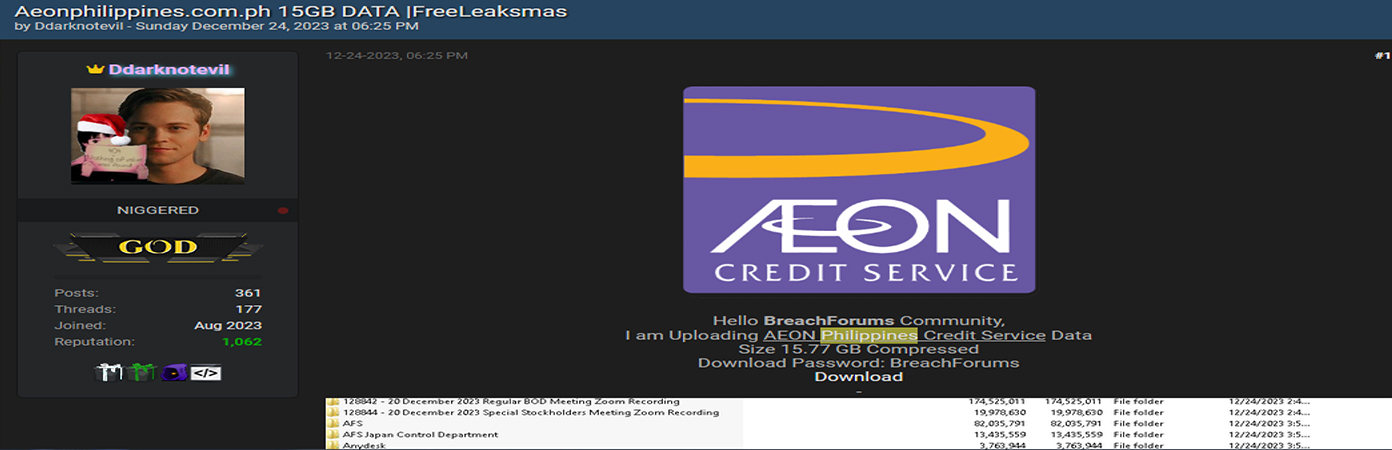
AEON Credit Service (Philippines) Inc., a nascent entity in the financing sector and part of the global AEON Credit Service Co., Ltd., itself a subsidiary of the AEON Group—a Fortune 500 conglomerate and one of Japan’s largest retail group, has experienced a significant data breach which involved approximately 15.77 GB of data, underlining the severity of the situation and the potential exposure of sensitive information.
We observed an increasing trend of campaigns targeting various industries in Philippines. Chinese, North Korean, and Russian state-sponsored threat actors are behind these campaigns.
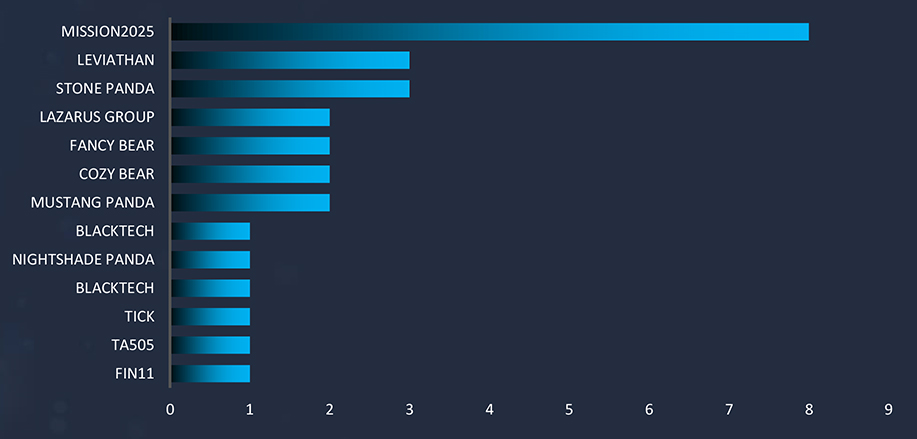
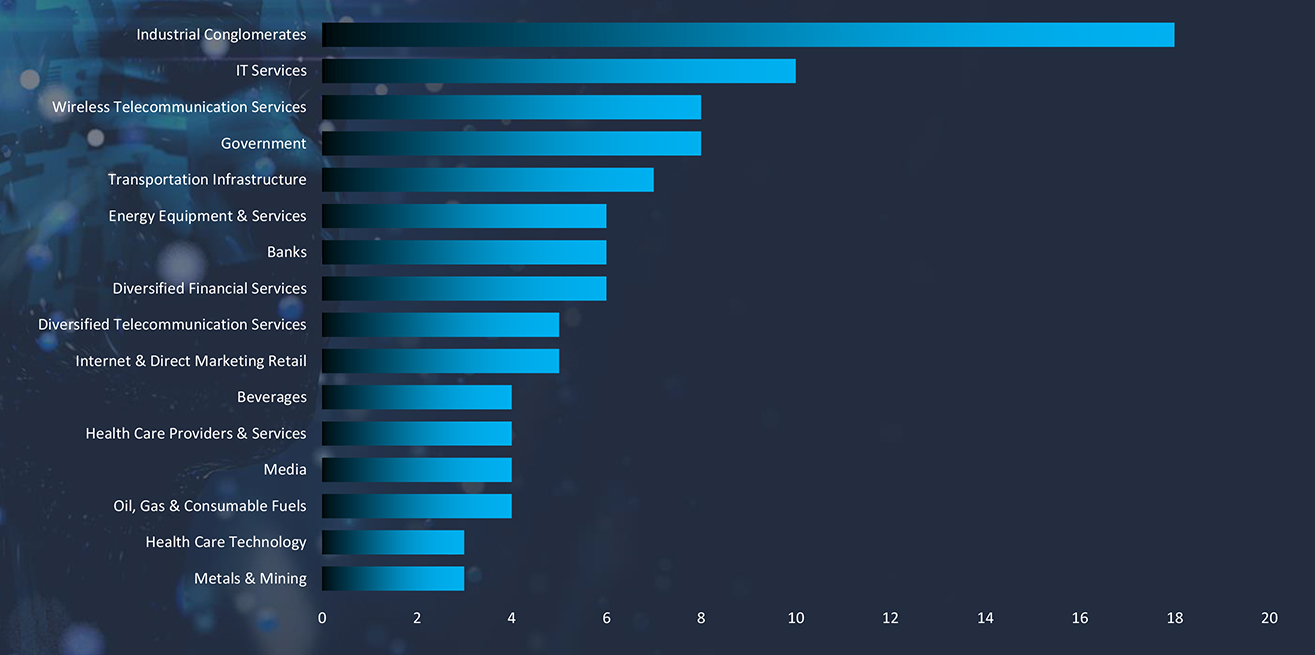
| Malware Name | Targeted Services/ Vulnerabilities | Campaign Name | Suspected Threat Actor | Target Industries | Target Geographies |
| Pubload, PlugX | Web Application, Operating System, Infrastructure-as-a-service Solutions | 2tomas shoal | Mustang Panda | Government, Internet & Direct Marketing Retail, Wireless Telecommunication Services, Media, IT Services, Transportation Infrastructure, Communications Equipment, Hotels, Restaurants & Leisure, Airlines, Air Freight & Logistics, Industrial Conglomerates, Energy Equipment & Services, Insurance, Software, Diversified Financial Services | Brunei, Vietnam, Philippines, Japan, Taiwan, Malaysia, Thailand, India |
| Winnti, LODEINFO | Web Application, Application Security Software | KDX-M7 | MISSION2025,Stone Panda | Aerospace & Defense, Health Care Equipment & Supplies, Health Care Technology, Real Estate Management & Development, Government, Food Products, Food & Staples Retailing, Airlines, Diversified Telecommunication Services, Industrial Conglomerates, Energy Equipment & Services, Metals & Mining, Banks, Health Care Providers & Services, Diversified Financial Services, Beverages, Health Research | Canada, South Korea, the Czech Republic, Singapore, the United States, Japan, Philippines, Taiwan, the United Kingdom, Australia, Germany, India |
| MiniDuke, Winnti | Web Application | All Wealth | Cozy Bear,MISSION2025 | Aerospace & Defense, Diversified Telecommunication Services, Industrial Conglomerates, Energy Equipment & Services, Metals & Mining, Wireless Telecommunication Services, Banks, IT Services, Transportation Infrastructure, Diversified Financial Services | South Korea, Vietnam, United States, Japan, Philippines, Taiwan, the United Kingdom, Australia, Thailand, India |

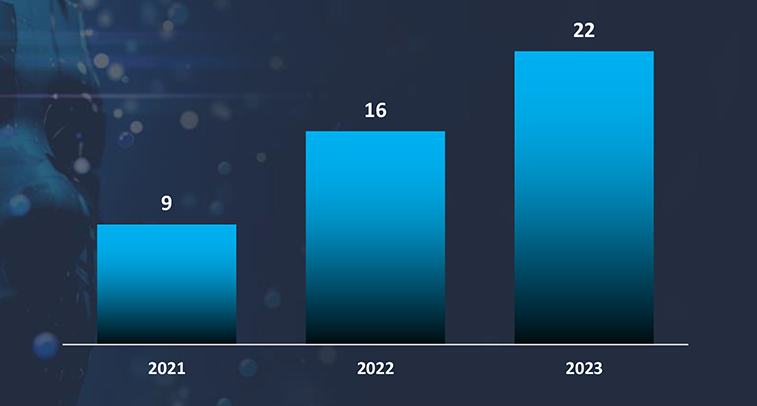
Ransomware groups target the Philippines for several reasons, including its growing digital infrastructure coupled with cybersecurity vulnerabilities. As the Philippines continues to expand its internet penetration and digital services, many organizations and individuals may not yet have robust cybersecurity measures in place, making them more susceptible to cyberattacks. Additionally, the country’s significant English-speaking population makes communication easier for ransom demands, and its diverse and complex regulatory environment can hinder rapid response to cyber threats. These factors, combined with the potential for high financial returns from businesses and government agencies, make the Philippines an attractive target for ransomware groups. Notably, this threat landscape is influenced by formidable ransomware groups, including LockBit, Clop, and Alphvm, which feature prominently on the list of perpetrators targeting Philippines companies.
FINANCIAL SECTOR
The financial sector is the most targeted industry by ransomware in the Philippines. This is because financial institutions store a large amount of sensitive financial data, which is valuable to cybercriminals.
GOVERNMENT SECTOR
The government sector is also a prime target for ransomware attacks. Government agencies control critical infrastructure and store a large amount of sensitive data, such as personal information and national security secrets.
HEALTHCARE SECTOR
The healthcare sector is vulnerable to ransomware attacks because it stores a large amount of sensitive patient data, such as medical records and financial information.
EDUCATION SECTOR
The education sector is also a target for ransomware attacks. Educational institutions store a large amount of student data and intellectual property, which is valuable to cybercriminals.
RETAIL SECTOR
The retail sector is vulnerable to ransomware attacks because it processes a large volume of credit card transactions. Cybercriminals can use ransomware to encrypt credit card data and then demand a ransom payment in exchange for the decryption key.
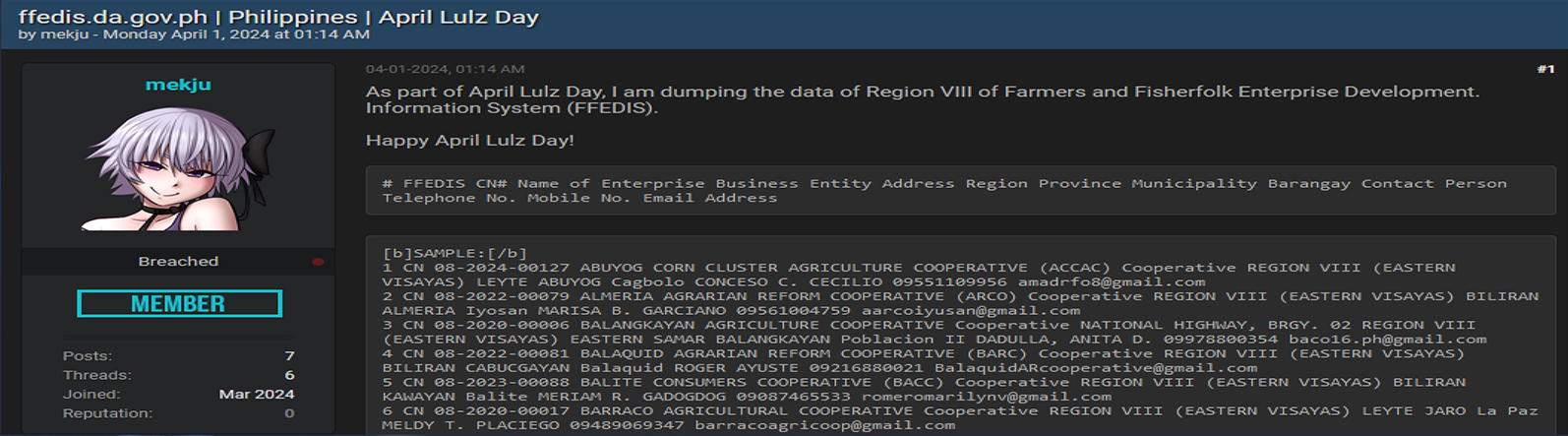
The FFEDIS, a digital platform hosted by ffedis.da.gov.ph in the Philippines, serves as a pivotal tool for government agencies in devising strategies and initiatives aimed at fostering enterprise growth. It bridges the gap between producer groups, the private sector, local government units (LGUs), and prospective donors, aligning their efforts with the demands of both local and global markets while facilitating resource mobilization for continued enterprise advancement. However, a recent security breach resulted in the unauthorized disclosure of sensitive information. This compromised data encompasses details such as the names of enterprises, their business addresses, regional and local administrative identifiers (including region, province, municipality, and barangay), along with the contact information of representatives—names, phone and mobile numbers, and email addresses.
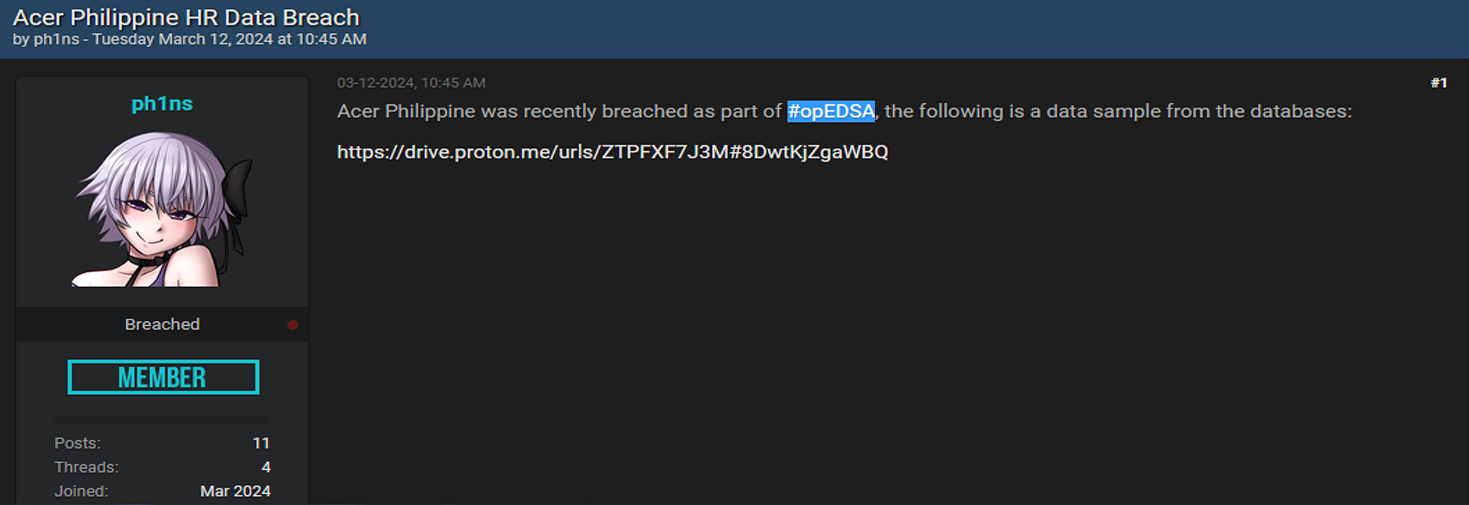
A cybersecurity incident has impacted the Philippine branch of Acer, a Taiwanese technology company, with its data being compromised and subsequently advertised on an underground forum. The breach involved a database from Acer Philippines, which contained sensitive information related to employee attendance. This database included comprehensive details such as employees’ names, usernames, passwords, job roles, departmental affiliations, employer names, birthdates, mobile numbers, and email addresses. This cyberattack was conducted under the guise of “#OpEDSA,” a movement advocating for political reform within the Philippines, which has previously targeted various companies operating in the country.
AEON Credit Service (Philippines) Inc., a nascent entity in the financing sector and part of the global AEON Credit Service Co., Ltd., itself a subsidiary of the AEON Group—a Fortune 500 conglomerate and one of Japan’s largest retail group has experienced a significant data breach. The breach involved approximately 15.77 GB of data, underlining the severity of the situation and the potential exposure of sensitive information.

| Exploited Vulnerabilities | Vendor | Product |
| CVE-2017-9841 | PHPUnit – Sebastian Bergmann | PHPUnit |
| CVE-2022-26134 | Atlassian | Confluence |
| CVE-2024-1709 | ConnectWise | ScreenConnect |
| CVE-2023-46805 | Ivanti | Ivanti Secure Connect and Policy Secure |
| CVE-2016-3088 | Apache | ActiveMQ |
| CVE-2018-13379 | Fortinet | FortiOS |
| CVE-2018-7600 | Drupal | Drupal |
| CVE-2019-11510 | Pulse Secure | Pulse Secure VPN |
| CVE-2019-15107 | Webmin | Webmin |
| CVE-2019-19781 | Citrix | Application Delivery Controller |
| CVE-2019-2725 | Oracle | Oracle Weblogic Server |
| CVE-2019-3396 | Atlassian | Confluence |
| CVE-2019-7192 | QNAP | QNAP NAS devices running Photo Station |
| CVE-2019-7238 | Sonatype | Nexus Repository Manager |
| CVE-2019-9670 | Synacor | Zimbra Collaboration Suite |
INFORMATION TECHNOLOGY
With a strategic emphasis on Information and Communication Technology (ICT), the Vietnamese government has undertaken initiatives to propel its development, recognizing its significance as a priority industry. The ambitious goal is to elevate Vietnam’s digital economy to an impressive US$50 billion by 2025, offering substantial growth prospects for the ICT market. This trajectory is underscored by World Bank data, indicating an annual growth rate of 10% in Vietnam’s digital economy, with the potential to exceed a formidable US$200 billion by 2045. Within this burgeoning digital landscape, the Vietnam Information Technology (IT) industry becomes a focal point of interest for threat actors. The convergence of economic ambitions and technological advancements renders the IT sector susceptible to cyber threats, with threat actors aiming to exploit vulnerabilities for economic gains, intellectual property theft, or to gain a competitive advantage.
MANUFACTURING INDUSTRY
The manufacturing sector stands as a pivotal force in Vietnam’s economic landscape, constituting a substantial 24.76% of the country’s GDP and contributing significantly to its merchandise exports, accounting for 85% in 2022. Notably, this industry’s prowess extends beyond traditional production, with recent years witnessing an uptick in the manufacturing of sophisticated products like automotive parts, consumer electronics, and telecom equipment, showcasing Vietnam’s commitment to technological advancement. Leveraging advanced technologies, the Vietnamese manufacturing industry has earned a competitive edge, producing high-quality goods at a cost-effective scale. In the context of the threat landscape, the strategic importance and economic impact of Vietnam’s manufacturing industry make it an attractive target for threat actors. Cyber adversaries may seek to exploit vulnerabilities in the industry’s digital infrastructure for various motives, including economic espionage, intellectual property theft, or disrupting supply chains. Recognizing the nexus between technological innovation and economic growth, safeguarding the manufacturing sector becomes imperative, necessitating robust cybersecurity measures to protect against evolving threats and preserve Vietnam’s economic resilience.
TOURISM
Amidst the first half of 2023, Vietnam’s tourism sector showcased notable growth, welcoming nearly 5.6 million international visitors, achieving 70% of the annual target. Projections from Future Market Insights anticipate a robust tourism revenue of US$27,500 million by the year’s end, with a long-term forecast envisioning an impressive US$135,000 million by 2033. Within this thriving landscape, the Vietnam tourism industry becomes an intriguing target for threat actors. The sector’s economic significance, driven by increasing international footfall and substantial revenue projections, makes it an attractive focal point for cyber adversaries. Threat actors may aim to exploit vulnerabilities in the industry’s digital infrastructure for diverse reasons, such as financial fraud, data theft, or disrupting the country’s image as a tourist destination. Recognizing the symbiotic relationship between a secure digital landscape and the sustained growth of Vietnam’s tourism sector, it becomes imperative to fortify cybersecurity measures to safeguard against potential threats and preserve the industry’s positive trajectory.
LOGISTICS
The logistics sector in Vietnam stands out as a rapidly expanding industry, constituting approximately 4.5% of the country’s GDP. Positioned as the 10th among emerging logistics markets globally, Vietnam’s logistics market is valued at US$40 billion and anticipated growth to US$65.34 billion by 2029. Notably, over 30 companies, including industry giants like DHL, FedEx, and Maersk, contribute to the provision of international logistics services in Vietnam. Within this dynamic context, the Vietnam logistics industry emerges as a focal point for threat actors. The sector’s substantial economic contribution and strategic position in global logistics networks make it an appealing target for cyber adversaries. Threat actors may seek to exploit digital vulnerabilities in the logistics infrastructure for motives such as supply chain disruption, data theft, or financial fraud. Recognizing the critical role of secure logistics in supporting economic activities, fortifying cybersecurity measures becomes imperative to mitigate risks and ensure the resilience of Vietnam’s logistics industry against evolving cyber threats.
CONSTRUCTION INDUSTRY
With a current valuation of USD 23.1 billion, the Vietnam construction market is poised for substantial growth, projected to register a robust CAGR of over 8.5% in the forecast period. Emerging as the latest East Asian growth engine, Vietnam has captivated the interest of international investors, underscoring its strategic importance in the global construction landscape. However, this burgeoning sector also attracts the attention of threat actors in the Vietnam threat landscape. The construction industry’s pivotal role in the country’s economic development, coupled with its increasing international prominence, makes it an attractive target for cyber adversaries. Threat actors may aim to exploit digital vulnerabilities within the construction infrastructure for motives such as intellectual property theft, economic espionage, or disrupting critical projects. Recognizing the interconnectedness of digital infrastructure and the construction industry’s growth, bolstering cybersecurity measures becomes imperative to safeguard against potential threats and ensure the sustained development of Vietnam’s construction sector.
Vietnam’s geopolitical stance and its relationships with global powers profoundly influence its cybersecurity strategies.
South China Sea Disputes: Vietnam’s ongoing territorial disputes with China over the South China Sea not only heighten regional security tensions but also escalate the risk of cyber espionage and attacks aimed at disrupting critical infrastructures. In response, Vietnam has been compelled to bolster its cyber defenses to protect sensitive government and military data, reflecting the direct impact of geopolitical strife on national cybersecurity needs.
Enhanced Ties with the U.S.: The strategic deepening of relations between Vietnam and the United States, aimed at counterbalancing Chinese influence, extends into the cyber realm. This partnership facilitates technology transfer, intelligence sharing, and enhancements in Vietnam’s cyber defense capabilities. Such cooperation is critical for Vietnam to defend against sophisticated cyber threats and ensure the security of its digital infrastructure.
ASEAN Collaboration: As an active participant in ASEAN, Vietnam leverages regional collaboration to address security challenges that span national borders, including cyber threats. Through ASEAN, Vietnam engages in cooperative efforts to combat cybercrime and strengthen regional cyber resilience. This includes adopting shared cybersecurity frameworks and conducting joint exercises, crucial for protecting economic activities and communication networks across Southeast Asia.
Domestic Cyber Controls: Domestically, Vietnam employs stringent internet content controls and surveillance measures to maintain governmental stability and manage public narratives on sensitive issues. These internal cybersecurity measures not only help in monitoring and mitigating domestic cyber threats but also affect Vietnam’s international image concerning human rights and digital freedom.
This integrated approach highlights how Vietnam’s geopolitical maneuvers and concerns are intricately linked to its cybersecurity strategies, emphasizing the critical role of robust cyber defenses in safeguarding national interests and shaping its international engagements.

We observed an increasing trend of campaigns targeting various industries in Vietnam. Chinese, North Korean, and Russian state-sponsored threat actors are behind these campaigns.
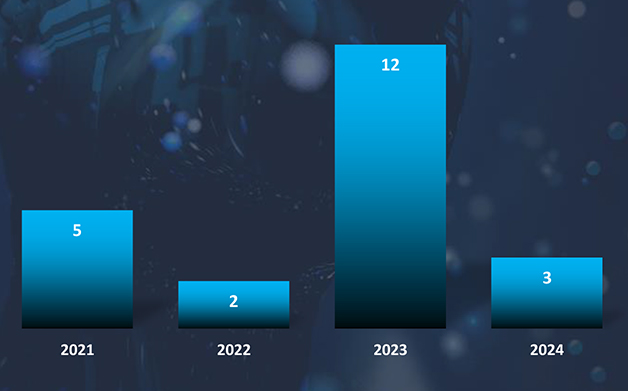
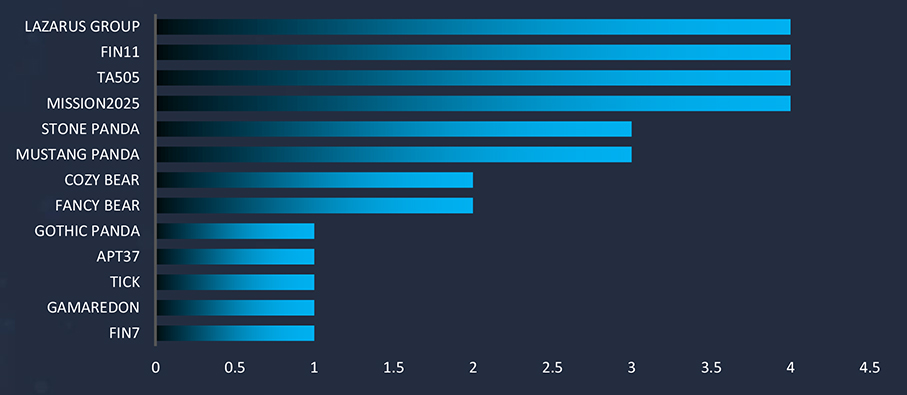
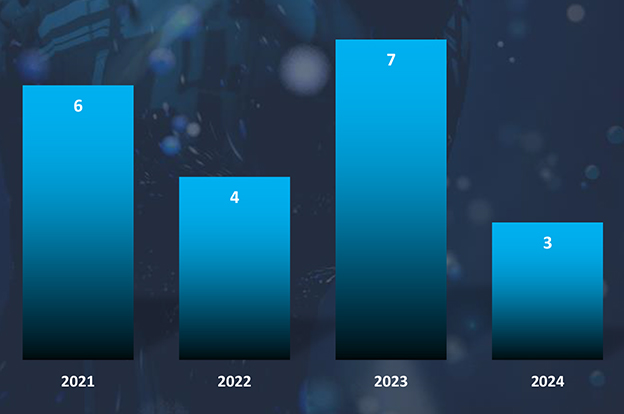
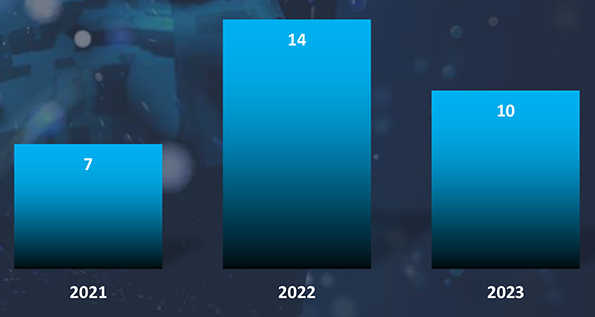
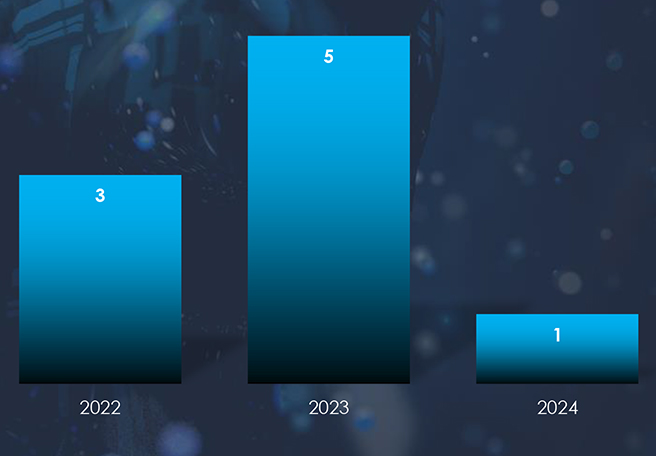
In 2023, there was a substantial rise in the number of observed campaigns, a marked increase when compared to the preceding two years. This uptick highlights the heightened interest of threat actors in the economic and geopolitical dynamics of Vietnam.
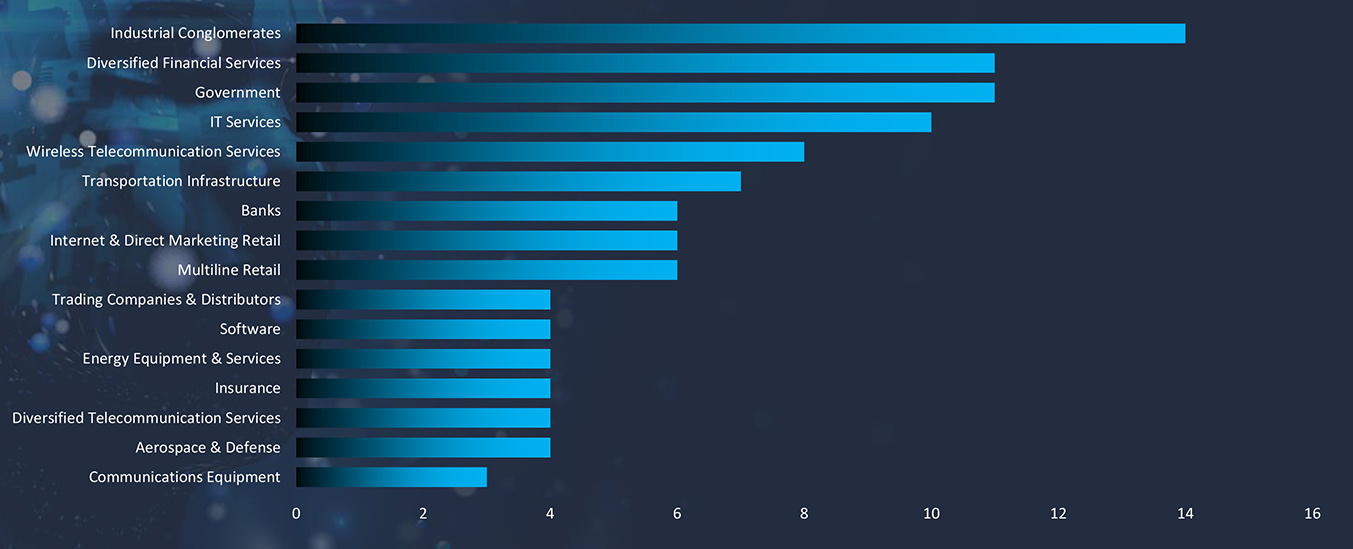
In the observed cyber campaigns, threat actors have methodically targeted a multitude of industries within the critical infrastructure. This deliberate focus is generating substantial economic and social repercussions within the threat landscape, amplifying its overall impact.
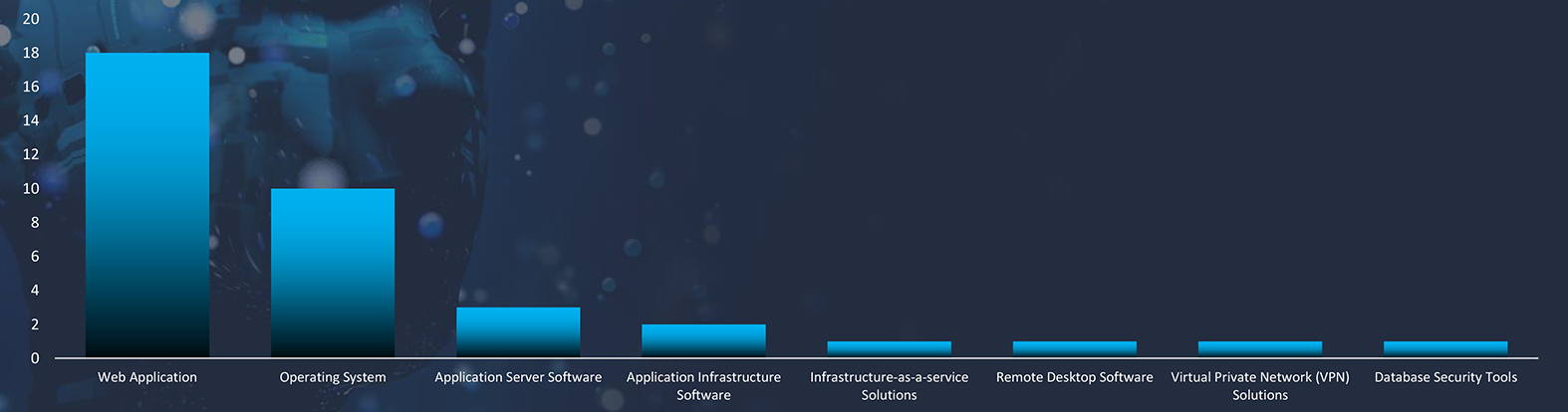
In the observed campaigns threat actors focused on attacking web applications, operating systems, and various other applications.
Here are some details about the observed sample campaigns.
| Malware Name | Targeted Services/ vulnerabilities | Campaign Name | Suspected Threat Actor | Target Industries | Target Geographies |
| Winnti, Commodity Nalware | Web Application | Camaro Delta | Mustang Panda, MISSION2025 | Aerospace & Defense, Multiline Retail, Marine, Government, Industrial Conglomerates, Internet & Direct Marketing Retail, Wireless Telecommunication Services, IT Services, Transportation Infrastructure, Communications Equipment, Diversified Financial Services | Vietnam, South Korea, Singapore, the United States, Philippines, Japan, Taiwan, Australia, Thailand, India, Indonesia |
| Pubload, PlugX | Web Application, Operating System, Infrastructure-as-a-service Solutions | 2tomas shoal | Mustang Panda | Government, Internet & Direct Marketing Retail, Wireless Telecommunication Services, Media, IT Services, Transportation Infrastructure, Communications Equipment, Hotels, Restaurants & Leisure, Airlines, Air Freight & Logistics, Industrial Conglomerates, Energy Equipment & Services, Insurance, Software, Diversified Financial Services | Brunei, Vietnam, Philippines, Japan, Taiwan, Malaysia, Thailand, India |
| MiniDuke, Winnti | Web Application | All Wealth | Cozy Bear,MISSION2025 | Aerospace & Defense, Diversified Telecommunication Services, Industrial Conglomerates, Energy Equipment & Services, Metals & Mining, Wireless Telecommunication Services, Banks, IT Services, Transportation Infrastructure, Diversified Financial Services | South Korea, Vietnam, the United States, Japan, Philippines, Taiwan, the United Kingdom, Australia, Thailand, India |
Data leaks play a crucial role in the landscape of cyber threats, acting as a significant vulnerability that can lead to a wide range of security issues and potential damages. When sensitive or confidential information is accidentally exposed or intentionally stolen and released, it can lead to identity theft, financial fraud, and a severe loss of trust and reputation for the affected organization. Such leaks often provide cybercriminals with the necessary data to conduct more targeted and effective attacks, such as phishing schemes, ransomware attacks, or further unauthorized access into secure systems. Additionally, data leaks can result in hefty regulatory fines and legal challenges, especially if the leaked information includes personally identifiable information (PII) protected under data privacy laws.
A user on an Underground Forum called “Soldier” is selling Vietnam-based admin access to .edu domains. Soldier has a good reputation on the forum and also share breaches from various countries like Italy, UK, Poland, Peru, Brazil, India, Japan, and Russia on their Telegram channel.
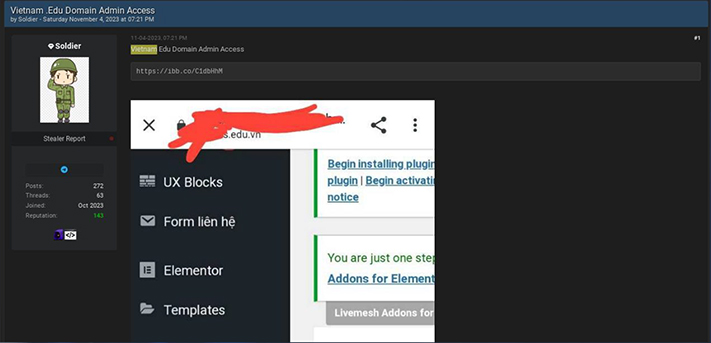
Threat actor “Soldier” also using the Telegram channel to sale database of organizations belongs to Vietnam.
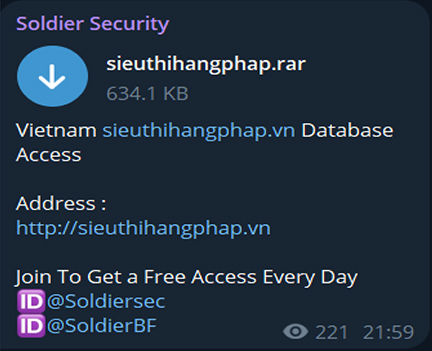
A user with moniker “mamypoko” on the Breachforum is looking for a database related to Vietnam, indicating the user might be planning to use it for scamming or other social engineering attacks. This highlights the demand for Vietnam databases which motivates cybercriminals to target Vietnamese organizations.
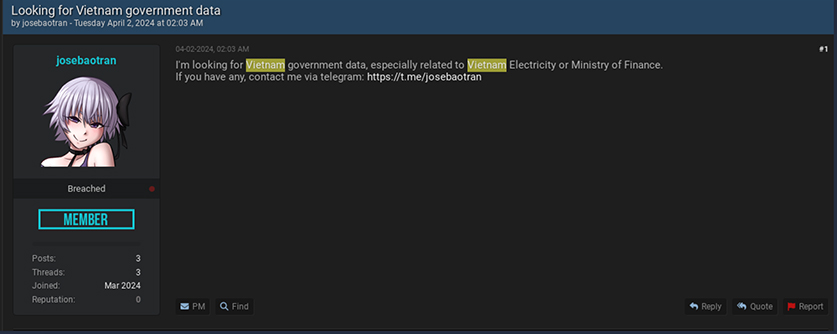
Another user going by the pseudonym “Joesbaotran” is interested in purchasing data related to the Vietnam government, particularly focusing on information related to electricity or the Ministry of Finance. He has shared his Telegram contact information for potential sellers. This highlights the potential cyber threats to Vietnamese critical infrastructure.
CYFIRMA observed a data leak related to Vietnam Post Corporation, a Vietnamese government-owned postal service. This data breach exposed their internal SRCs for their back-end infrastructure. The size of the leaked data is 2.34 GB.

CYFIRMA observed Vietnamese government employee’s database in the underground forum which includes more than 19,000 rows. Leaked data contains date of birth, full name, place of birth, hometowns, job titles and other details.
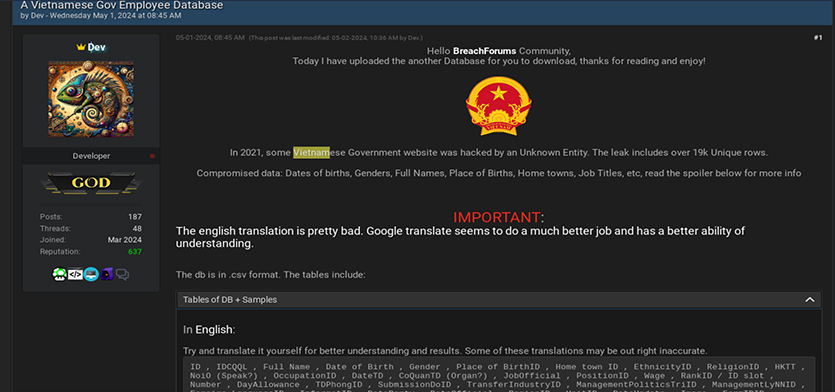
A user named “Ares22” on a breach forum is selling a large dataset containing personal information of individuals from Vietnam. This data includes names, dates of birth, telephone numbers, and email addresses.
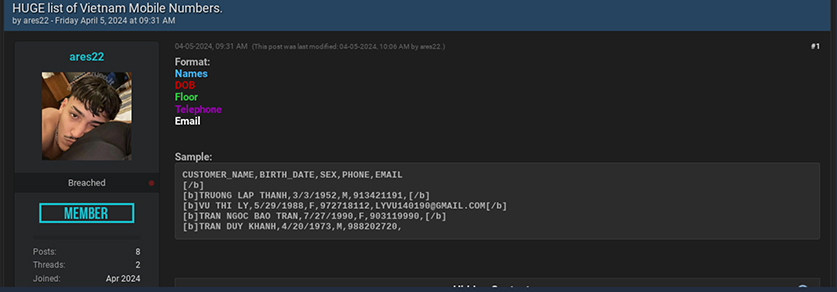
A user named “Mini” shared data from a logistics company in Vietnam, which includes details such as the company name, address, contact person’s personal phone number, and email address.
A user with a good reputation named “PieWithNothing” is selling data related to KFC from Vietnam consist of full name, phone, and delivery addresses, however, there are some duplicates entries to increase the data size.
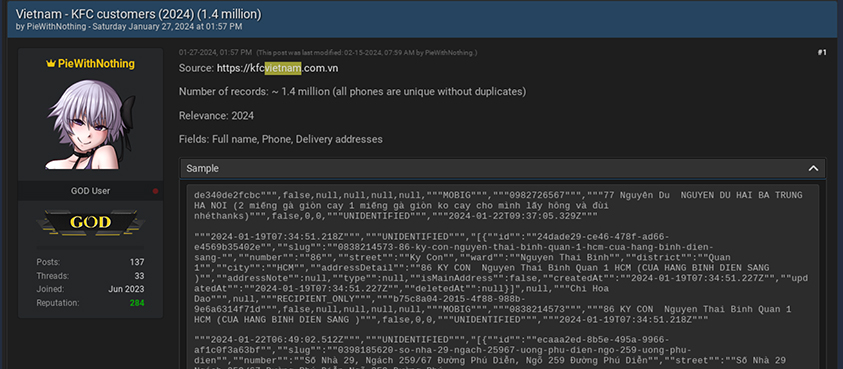
A user with the moniker “6789” is selling end user data related to Mediamart, a Vietnam e-commerce organization, consisting of 2 lakhs+ lines of records.
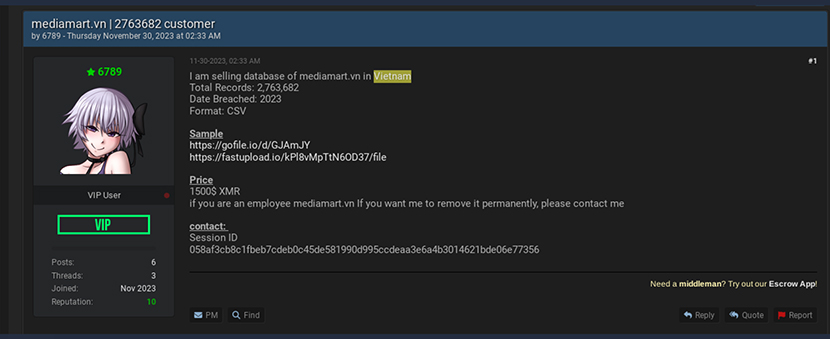
On March 20, 2024, a user named “PreciousMadness” on the Ramp forum and “TheColorYellow” on a similar native forum called XSS, is selling email access to the State Bank of Vietnam.
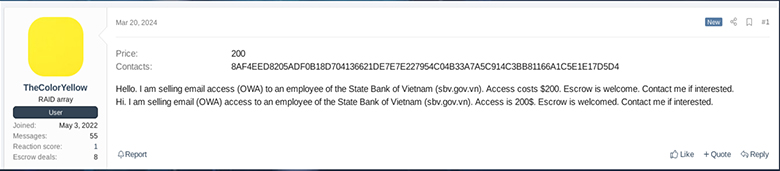
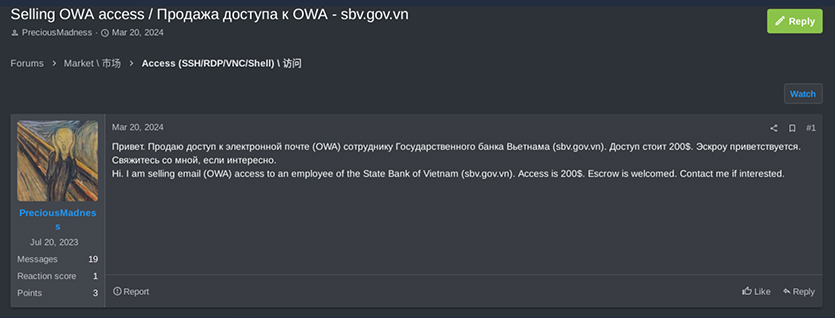
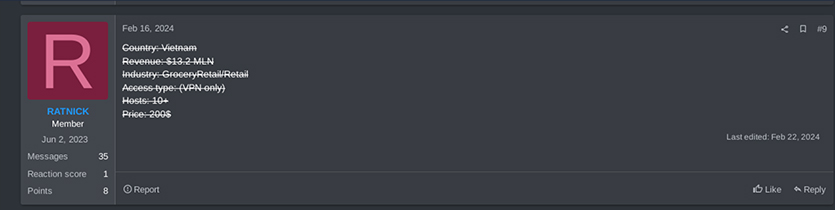
On February 16, 2024, a user named “RATNICK” (an initial access broker) sold VPN access with 10 hosts on the Ramp forum related to Vietnam organizations.
A user on the XSS forum, using the moniker “Piratejack,” is offering access to two organizations based in Vietnam. Both posts are from March 2024 and the post is still up at the time of writing the report.
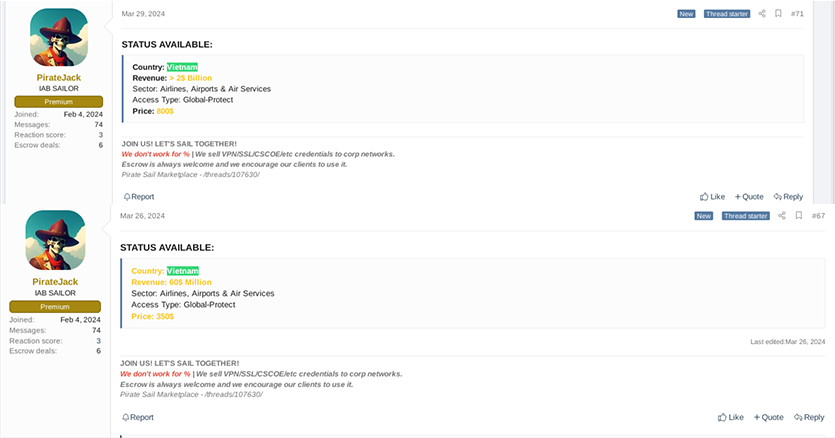
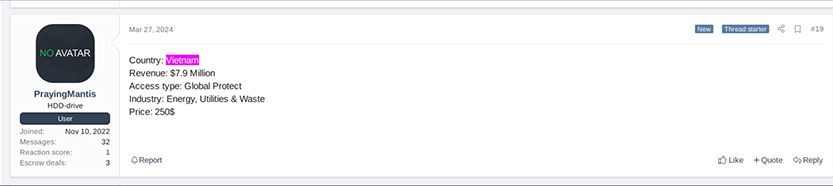
On March 27, 2024, a user named “Prayingmantis” (who has an arguably low reputation) is selling accesses including VPN Global Protect, Citrix, and RDP. Specifically, they’re offering VPN access to a Vietnamese organization, suggesting it’s related to energy, utilities, and waste management.
The Quantum of DDoS attacks increased globally after the start of the Russia-Ukraine war when pro-Russian and pro-Ukraine hacktivists started targeting each other with DDoS campaigns and also started targeting alliance nations to show support to their respective country.
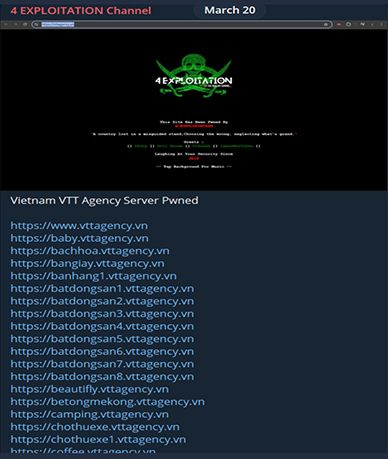
On March 23rd, “4 exploitation group” a Pakistani-based hacktivist group, jointly defaced a Vietnamese organization called Thang Long Shopping.
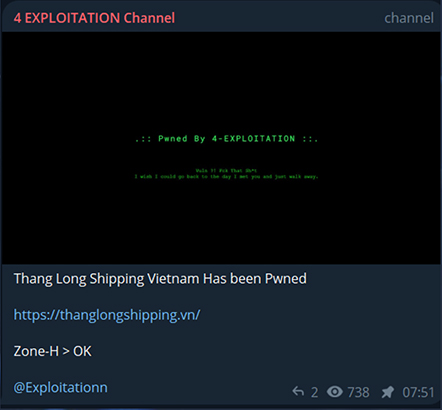
On March 20th, 2024, a same group targeted another organization based in Vietnam, and below is the list of organizations they shared in their Telegram channel that were defaced.
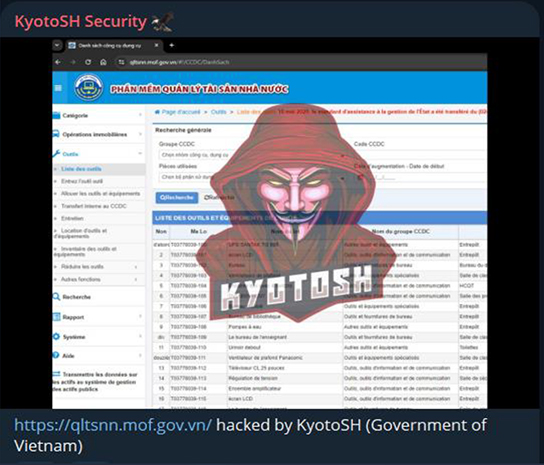
KyotoSH Security, a Russian-based hacktivist group, has claimed responsibility for hacking a Vietnamese government website. However, it’s possible that they obtained credentials from stealer logs or other combo lists, granting them access to the portal, and are now falsely claiming to have hacked the government portal. At CYFIRMA, we’ve observed numerous cases where threat actors purchase stealer logs as initial access, which are then used for various post-attack activities.
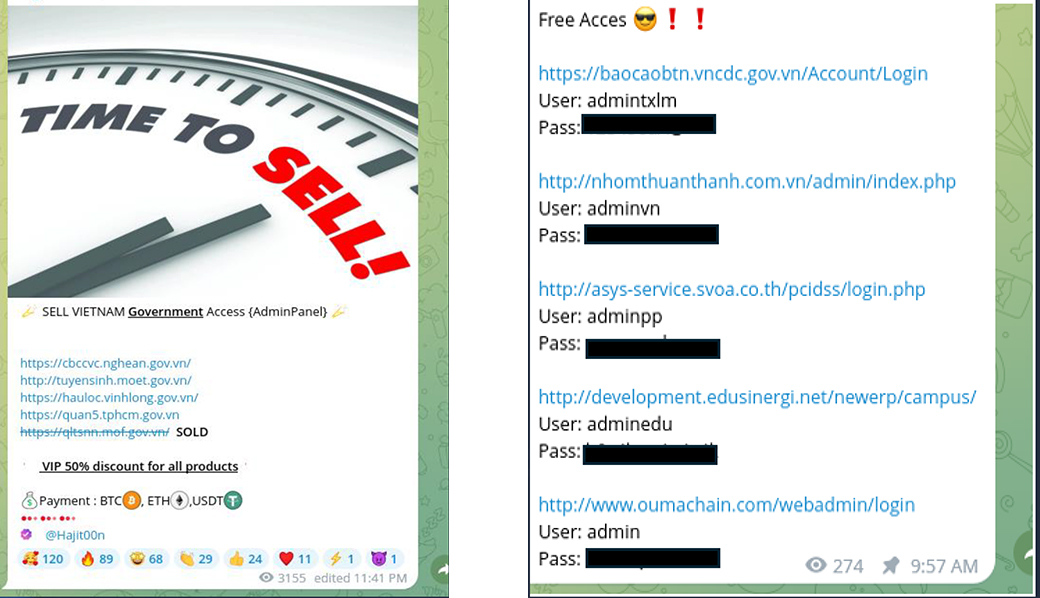
CYFIRMA observed numerous hacktivist collectives actively marketing and distributing unauthorized access credentials to various Vietnamese government entities via Telegram channels. Such activities significantly heighten the risk to national security by potentially facilitating unauthorized data access and systems manipulation.
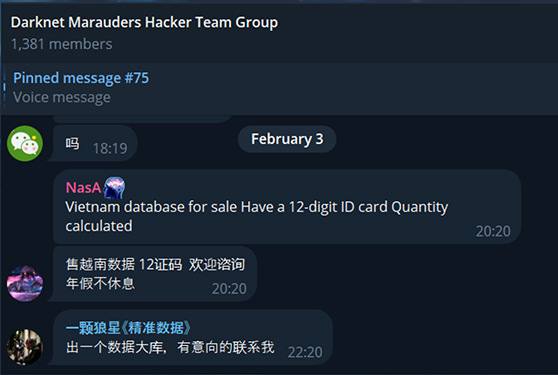
Marauders hacker team is a Chinese-based hacktivist group that shared in their telegram group about selling Vietnam databases.
Another hacktivist group “We are team_r70” – a Yemen based group – defaced education institutions belongs to Vietnam region on February 27th ,2024.
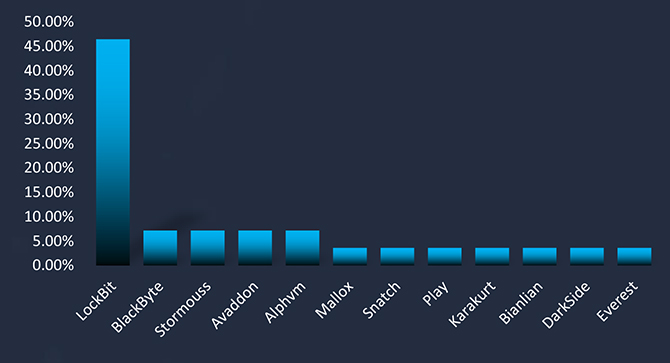
LockBit ransomware is the most active group in Vietnam, affecting the largest % of victims at 46% among all targeted organizations.
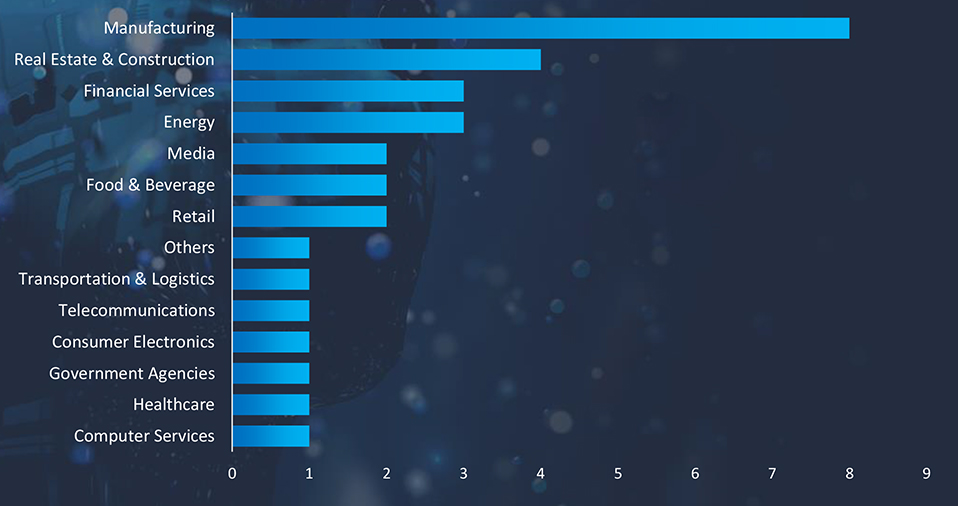
Manufacturing, Real Estate & Construction, Financial Services, Energy, and Media are the top targets of ransomware actors in Vietnam.
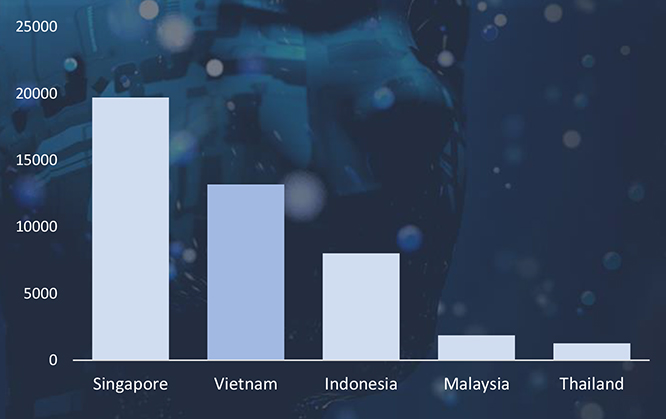
Between May 9th, 2023 and May 9th, 2024 CYFIRMA’s advanced telemetry systems meticulously detected a staggering total of 1,006,950 phishing campaigns. Within this extensive dataset, it’s noteworthy that Vietnam emerged as one of the most targeted geographic regions in Southeast Asia.
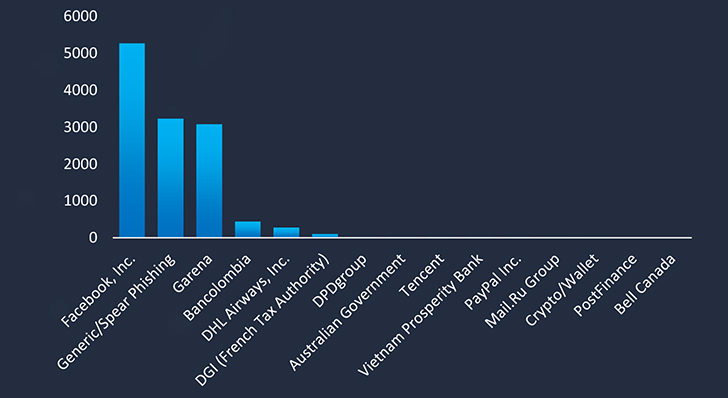
The observed campaign in Vietnam reveals several prominent themes exploited in phishing attacks. Among these, the brands most frequently impersonated include Facebook, Inc. Generic/Spear Phishing, Garena, Bancolombia, DHL Airways, Inc., DGI (French Tax Authority), and DPDgroup. These findings shed light on the diverse range of brands that malicious actors are leveraging to carry out phishing attacks within Vietnam. Understanding these prevalent themes is crucial for enhancing cybersecurity measures and safeguarding against the evolving tactics employed by cybercriminals.
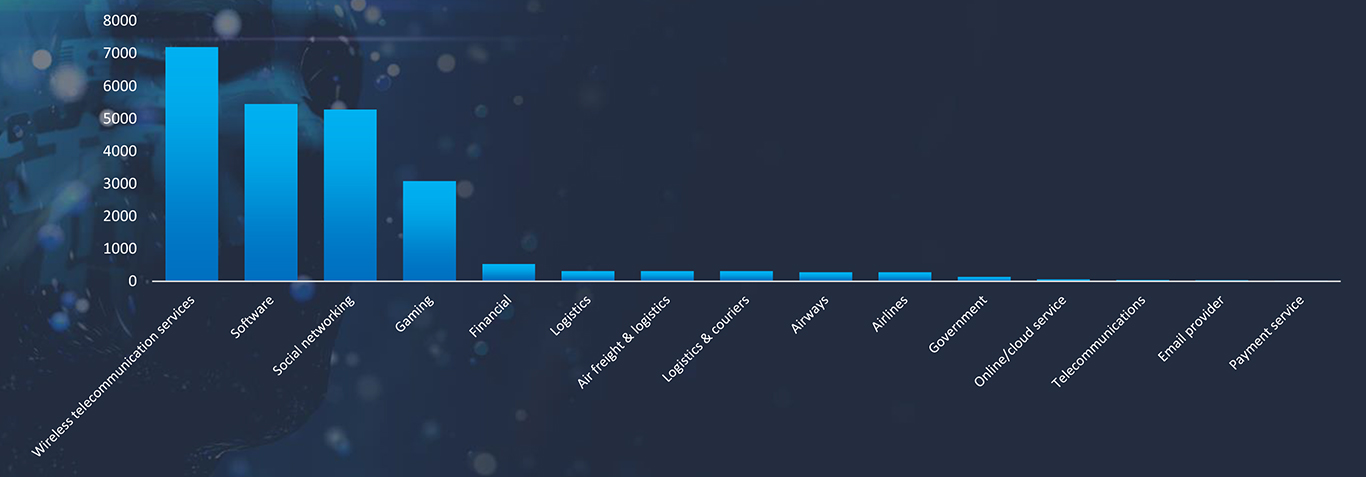
The observed campaign in Vietnam reveals several prominent themes exploited in phishing attacks. Among these, the sectors most frequently targeted include Wireless telecommunication services, Software, Social networking, Gaming, Financial, Logistics, Air freight & logistics, Logistics & couriers, and Airways. These findings shed light on the diverse range of sectors, that malicious actors are leveraging to carry out phishing attacks within Vietnam.
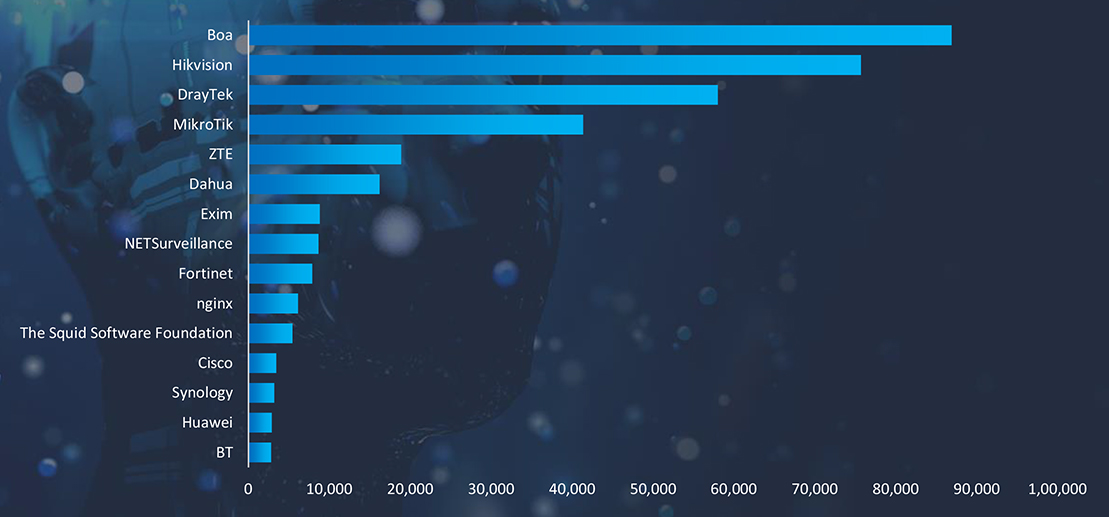
Exposed IoT devices play a significant role in cyber attacks due to their often-inadequate security features and widespread adoption across various sectors. These devices can serve as entry points or targets in larger network breaches, primarily because they frequently lack robust encryption, undergo infrequent updates, and have default or weak credentials that are easily exploited. Once compromised, IoT devices can be used to form botnets, enabling attackers to conduct DDoS (Distributed Denial of Service) attacks, data breaches, or surveillance. Their connectivity and access to larger networks also make them a valuable asset for attackers looking to move laterally within infrastructure, escalate privileges, or disrupt critical services. This vulnerability is exacerbated by the rapid expansion of IoT devices in homes, industries, and cities without corresponding advancements in their security frameworks.
| Exploited Vulnerabilities | Vendor | Product |
| CVE-2017-9841 | PHPUnit | PHPUnit |
| CVE-2018-10562 | Dasan | Dasan GPON Home Router |
| CVE-2023-20198 | Cisco | Cisco IOS XE |
| CVE-2024-3273 | D-Link | D-Link DNS-320L, DNS-325, DNS-327L and DNS-340L |
| CVE-2015-2051 | D-Link | D-Link DIR-645, DAP-1522 revB, DAP-1650 revB, DIR-880L, DIR-865L, DIR-860L revA, DIR-860L revB DIR-815 revB, DIR-300 revB, DIR-600 revB, DIR-645, TEW-751DR, TEW-733GR |
| CVE-2024-21887 | Ivanti | Ivanti Secure Connect and Policy Secure |
| CVE-2021-3129 | Laravel | Ignition |
| CVE-2014-8361 | Realtek | Realtek SDK |
| CVE-2015-1427 | Elastic | Elasticsearch |
| CVE-2016-1555 | NETGEAR | WN604, WN802Tv2, WNAP210v2, WNAP320, WNDAP350, WNDAP360, and WNDAP660 |
| CVE-2016-3088 | Apache | ActiveMQ |
| CVE-2016-6277 | Netgear | NETGEAR R/D Series Routers |
| CVE-2017-1000486 | PrimeFaces | PrimeTek |
| CVE-2017-10271 | Oracle | Oracle Weblogic Server |
| CVE-2017-15944 | Palo Alto Networks | PAN-OS |
State-sponsored threat actors target Malaysia for several strategic reasons.
Malaysia’s diverse industrial sectors and cutting-edge technology products make it an appealing target for nation-state attackers and financially motivated threat actors. Furthermore, hacktivists have also been observed targeting Malaysian industries alongside APT and other threat actors, reflecting the multifaceted cybersecurity challenges these sectors face.
Malaysia Critical National Information Infrastructure (CNII) as per NATIONAL CYBER SECURITY AGENCY (NACSA) – Malaysia
Government, National Defence and Security, Banking and Finance, Information and Communications, Energy, Transportation, Emergency Services, Water, Health Services, Agriculture and Plantation, Trade, Industry and Economy
The Asia-Pacific region, with Malaysia as a critical node, is poised to be a central arena for geopolitical competition in the 21st century. Malaysia’s strategic location, economic significance, and diplomatic maneuvers place it at the nexus of these tensions, requiring adept management of both economic policies and security strategies to navigate the complex geopolitical landscape effectively. As the regional dynamics evolve, the interplay of military build-up, economic dependencies, and cyber warfare will shape the geopolitical risks for Malaysia and its neighbors.
We observed an increasing trend in campaigns targeting various industries in Malaysia. Chinese, Iranian, and North Korean state-sponsored threat actors are behind these campaigns.
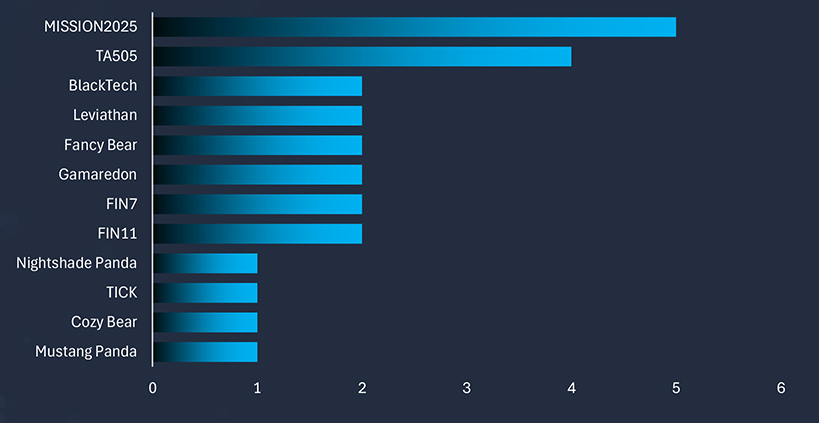
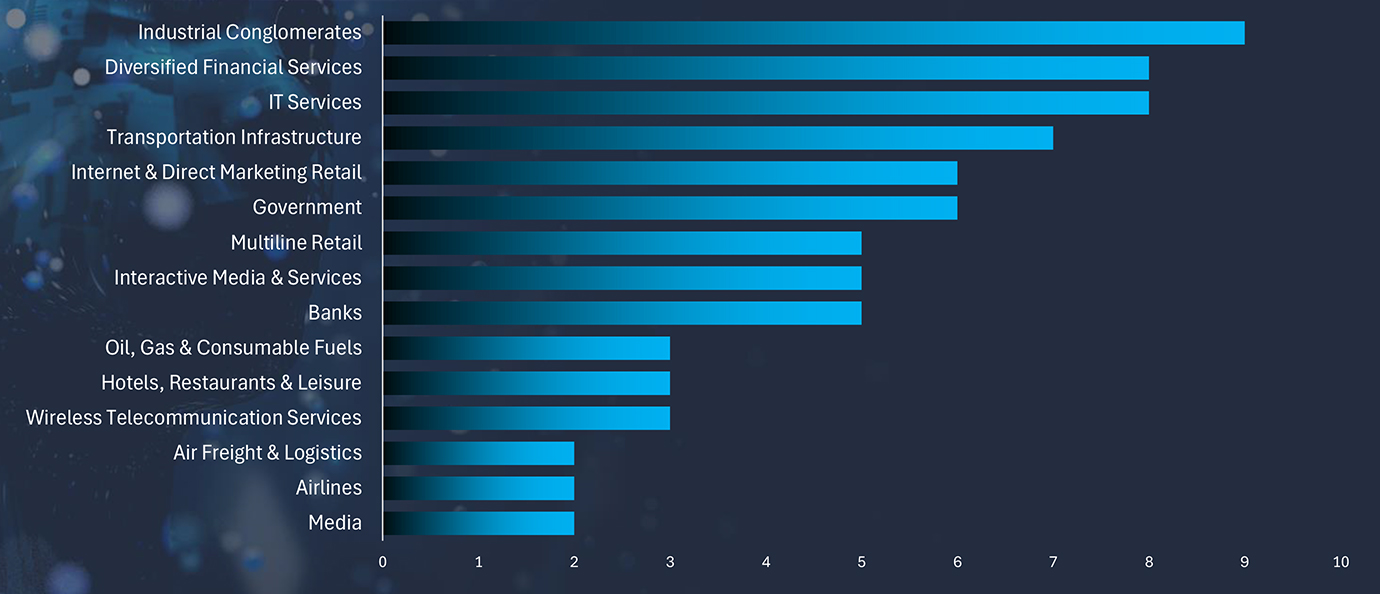

| Malware Name | Targeted Services/ Vulnerabilities | Campaign Name | Suspected Threat Actor | Target Industries | Target Geographies |
| Pubload, PlugX | Web Application, Operating System, Infrastructure-as-a-service Solutions | 2tomas shoal | Mustang Panda | Government, Internet & Direct Marketing Retail, Wireless Telecommunication Services, Media, IT Services, Transportation Infrastructure, Communications Equipment, Hotels, Restaurants & Leisure, Airlines, Air Freight & Logistics, Industrial Conglomerates, Energy Equipment & Services, Insurance, Software, Diversified Financial Services | Brunei, Vietnam, Philippines, Japan, Taiwan, Malaysia, Thailand, India |
| – | Web Application | Void | TA505,FIN11,FIN7,Gamaredon | Auto Components, Real Estate Management & Development, Government, Internet & Direct Marketing Retail, Banks, Interactive Media & Services, Automobiles | South Korea, Vietnam, Singapore, Hungary, the United States, Japan, Ukraine, the United Kingdom, Malaysia, Indonesia |
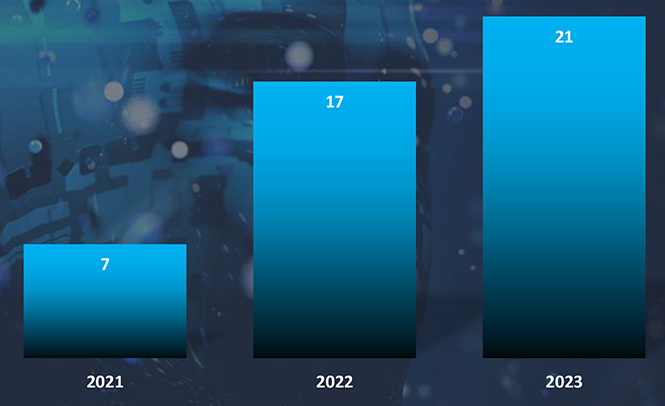
LockBit ransomware is the most active group in Malaysia and has primarily targeted the Manufacturing, Finance, and other critical infrastructure sectors, totaling 48% of victims among all targeted organizations.
Ransomware actors target Malaysia due to several factors, including its growing digital economy and widespread use of technology in business and government operations. This creates numerous vulnerabilities that can be exploited by cybercriminals. Malaysia’s strategic importance in Southeast Asia, coupled with the presence of many multinational companies and a significant SME sector that may not always have robust cybersecurity measures also makes it an attractive target. Additionally, the relative lack of stringent regulatory frameworks and enforcement, compared to some Western countries, provides further incentives for ransomware actors to focus on Malaysian entities, hoping for quicker and less complicated ransom payments.
Between April 10th, 2023 and April 10th, 2024 CYFIRMA’s advanced telemetry systems meticulously detected a staggering total of 981,727 phishing campaigns. Within this extensive dataset, it’s noteworthy that Malaysia emerged as one of the most targeted geographic regions in Southeast Asia.
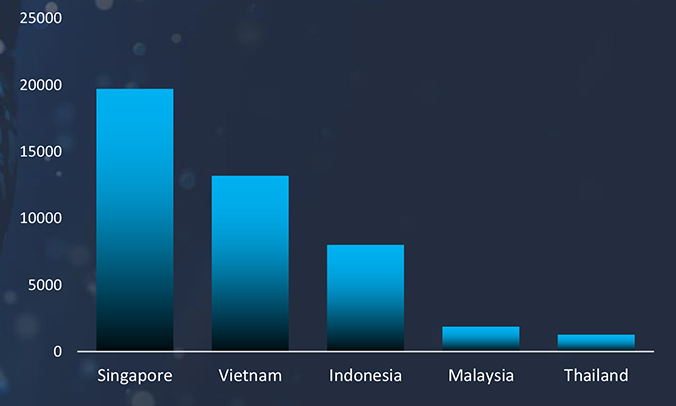
The observed campaigns in Malaysia reveal several prominent themes exploited in phishing attacks. Among these, the sectors most frequently targeted include Software, Airlines, Air Freight & Logistics, Wireless Telecommunication Services, IT Services, and Government. These findings shed light on the diverse range of sectors that malicious actors are leveraging to carry out phishing attacks within Malaysia. Understanding these prevalent themes is crucial for enhancing cybersecurity measures and safeguarding against the evolving tactics employed by cybercriminals.
The Quantum of DDoS attacks increased globally after the start of the Russia-Ukraine war when pro-Russian and pro-Ukraine hacktivists started targeting each other with DDoS campaigns and also started targeting alliance nations to show support to their respective country.
In the case of Malaysia, the hacktivists are targeting Malaysia through methods like DDOS, Defacement, and Data leaks. Here are the channels identified:
These channels may represent potential threats to Malaysia’s cybersecurity and should be closely monitored and addressed by relevant authorities to prevent any malicious activities.
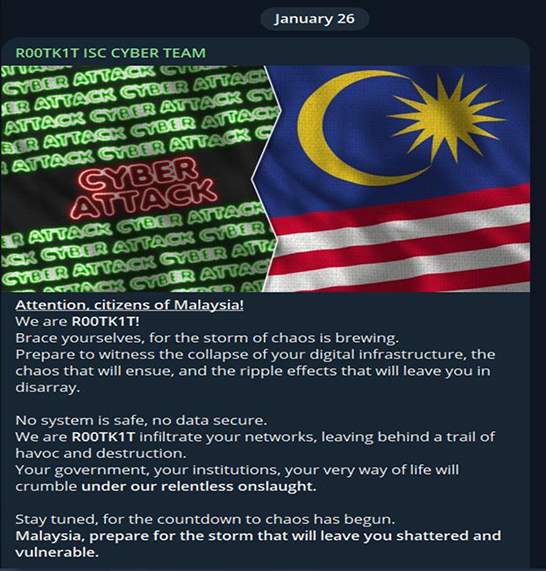
On November 2nd, 2023, the R00tk1t channel was created on Telegram with the motivation to support Israel. They have carried out various attacks including DDoS, defacement, and data leaks. The countries targeted are those against Israel, which includes Malaysia, Iran, Azerbaijan, Lebanon, Palestine, Qatar, and others. The group gained attention when they announced on January 26th, 2024, via their Telegram channel, their intention to hack digital infrastructure belonging to Malaysia. Since then, they have continued launching a series of ongoing attacks.
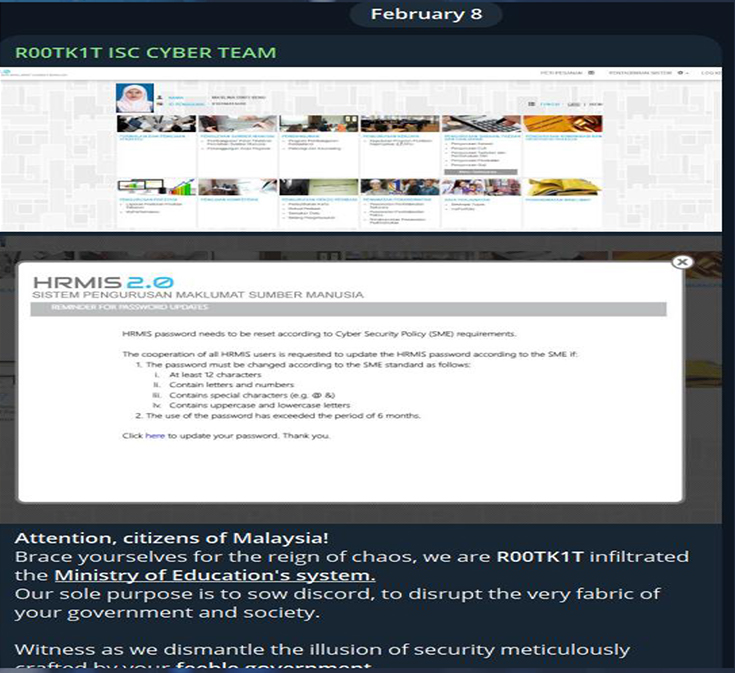
On February 8th, 2024, R00tk1t launched an attack on the Ministry of Education system in Malaysia.
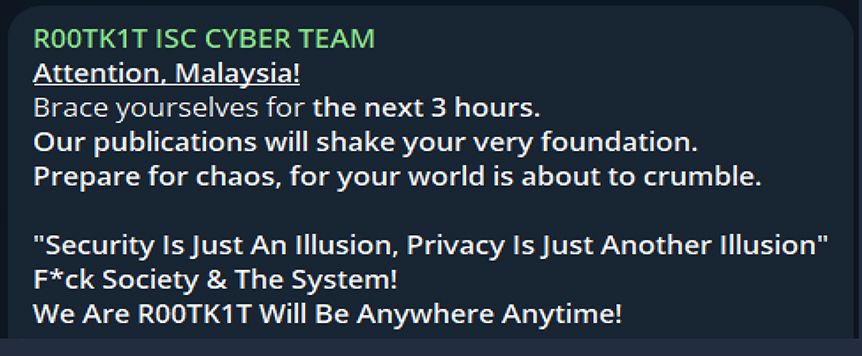
On February 10th, 2024, the R00tk1t group issued a warning, stating their intention to take action against the Malaysian government.
On February 10th, 2024, the group claimed responsibility for attacking the Malaysian court system. The following day they asserted that they had seized control of multiple websites belonging to the Malaysian government.
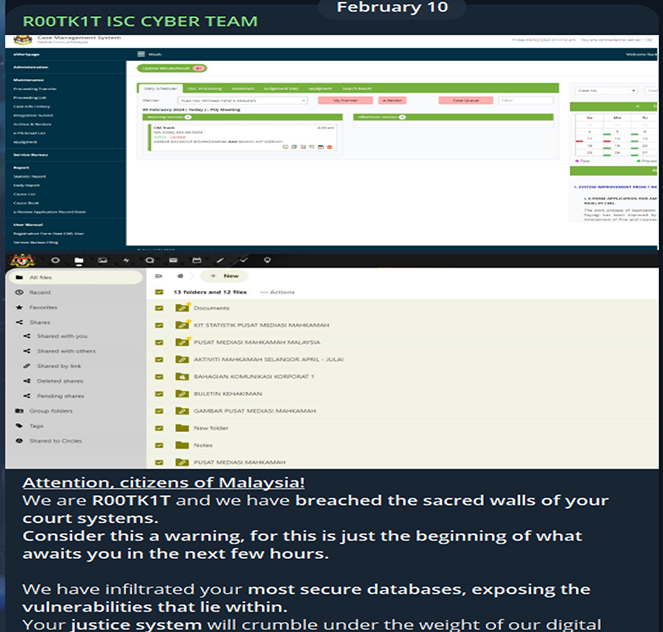

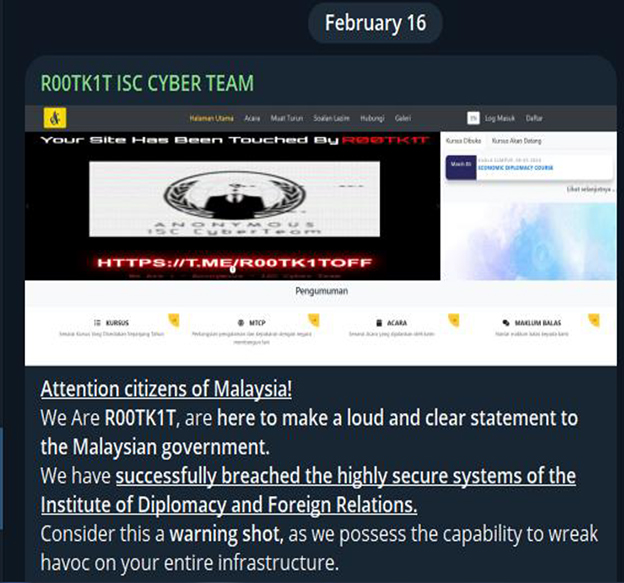
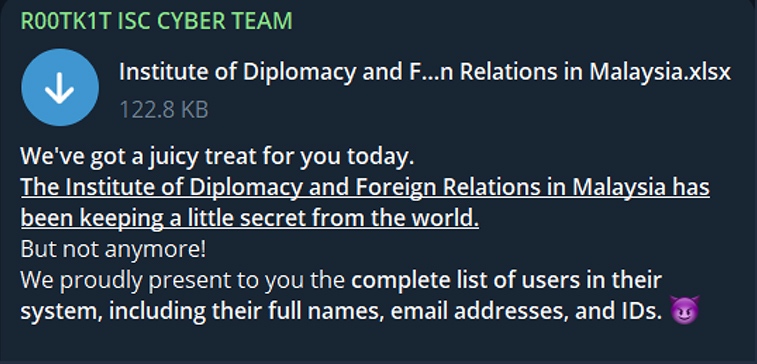
On February 16th, 2024, the R00tk1t group launched an attack on the system of the Institute of Diplomacy and Foreign Relations. They then uploaded the stolen data onto their Telegram channel.
R00tk1t group has attacked numerous Private and Government organizations.
| Date | Target |
| January 30th, 2024 | Aminia |
| February 5th, 2024 | Maxis |
| February 3rd , 2024 | Yoututor Course Website |
| February 7th, 2024 | AMC University College Malaysia |
| February 8th, 2024 | Ministry of Education Malaysia |
| February 8th, 2024 | INS Next-Gen Business Technology Solutions |
| February 9th, 2024 | Raine, Horne & Zaki Property Management Sdn Bhd’s eCommunity. |
| February 10th, 2024 | Federal Court of Malaysia |
| February 11th, 2024 | Aidan Group |
| February 16th, 2024 | Institute of Diplomacy and Foreign Relations. |
| February 16th, 2024 | TNB Malaysia |
| February 19th, 2024 | National Council for Population and Family Development |
| February 19th, 2024 | PADU Malaysia |
| February 19th, 2024 | Putrajaya Government Website |
| February 21st, 2024 | Vaccine Management System Malaysia |
| February 27th, 2024 | Malaysia Airlines Passenger data |
| February 28th, 2024 | UniKL university Malaysia |
| March 14th,2024 | TTL Group Malaysia |
| March 14th,2024 | Reliance Hydraulic Fittings Sdn Bhd |
| March 14th,2024 | Sarawak Government, Malaysia |
| March 16th,2024 | Ministry of Youth and Sports |
| March 16th,2024 | TEKUN National M |
Another hacktivist group, Infinite Insight.ID, from Indonesia, targeted Malaysian ministries. They breached their systems and shared credentials on their Telegram channel.
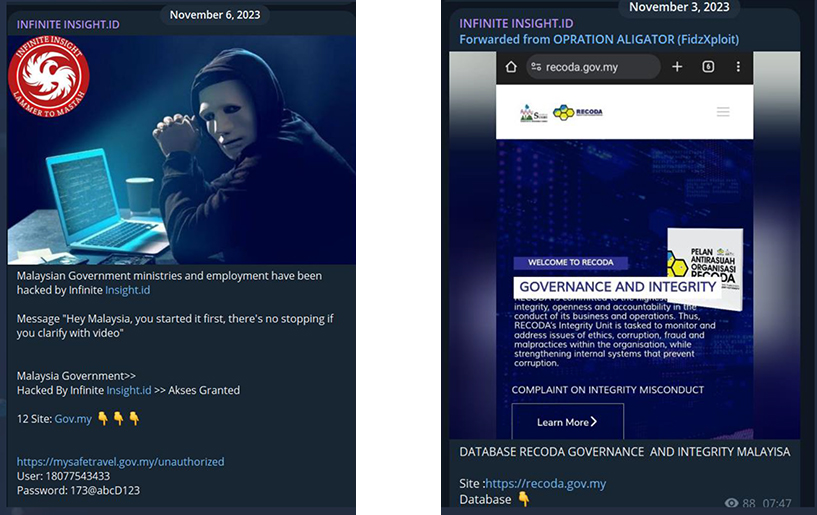
Hacktivist attacks on the Malaysian government and critical infrastructures lead to severe consequences, including the disruption of governmental services and critical operations such as healthcare, finance, and utilities, potentially leading to economic losses. Such attacks could also compromise sensitive data, undermining national security and eroding public trust in government institutions. Additionally, these cyber incidents could escalate geopolitical tensions if foreign entities are implicated, increasing the risk of retaliatory cyber actions and straining international relations. The overall impact can hinder the nation’s technological progress and deter foreign investments, posing long-term challenges to Malaysia’s economic and strategic stability.
Data leaks play a crucial role in the landscape of cyber threats, acting as a significant vulnerability that can lead to a wide range of security issues and potential damages. When sensitive or confidential information is accidentally exposed or intentionally stolen and released, it can lead to identity theft, financial fraud, and a severe loss of trust and reputation for the affected organization. Such leaks often provide cybercriminals with the necessary data to conduct more targeted and effective attacks, such as phishing schemes, ransomware attacks, or further unauthorized access into secure systems. Additionally, data leaks can result in hefty regulatory fines and legal challenges, especially if the leaked information includes personally identifiable information (PII) protected under data privacy laws.
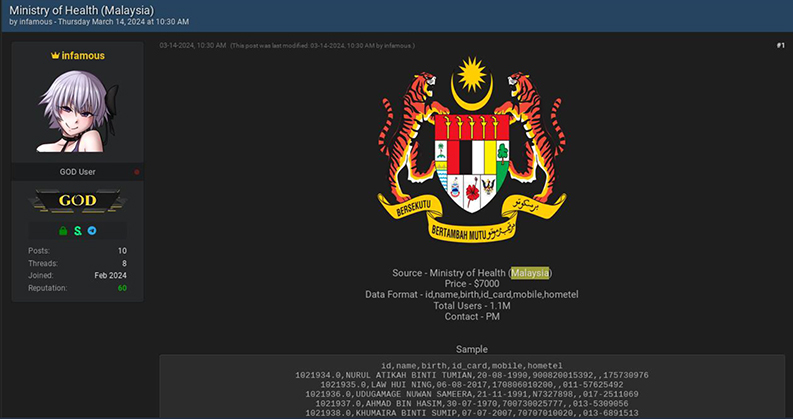
CYFIRMA come across a threat actor operating under the alias “infamous,” who is advertising the sale of a database purportedly from the Ministry of Health in Malaysia. This database contains sensitive information in the format of ID, name, date of birth, ID card number, mobile number, and home telephone number. Allegedly, there are approximately 1.1 million users’ data available for sale. Such a breach poses serious risks to public health data integrity and individuals’ privacy
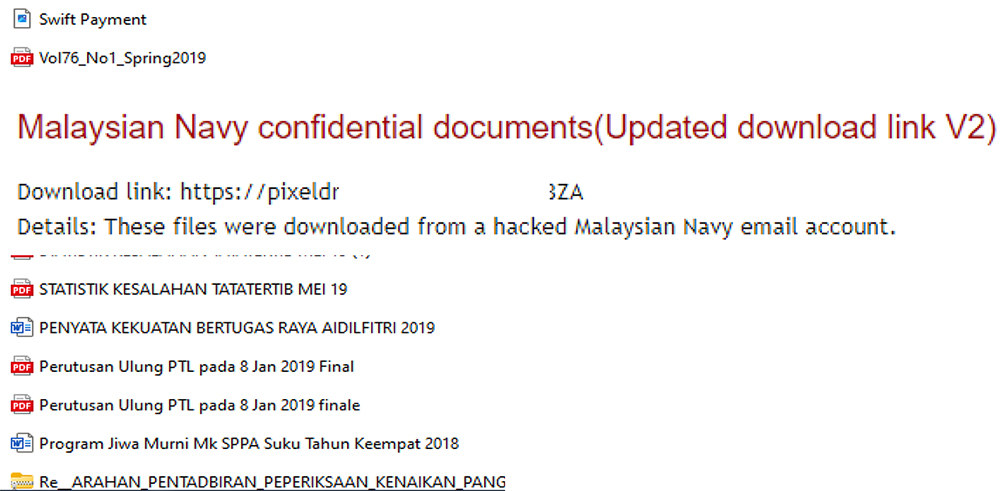
CYFIRMA observed leaked confidential data associated with the Malaysian Navy. Threat actor claims that data was exfiltrated from the official email account.
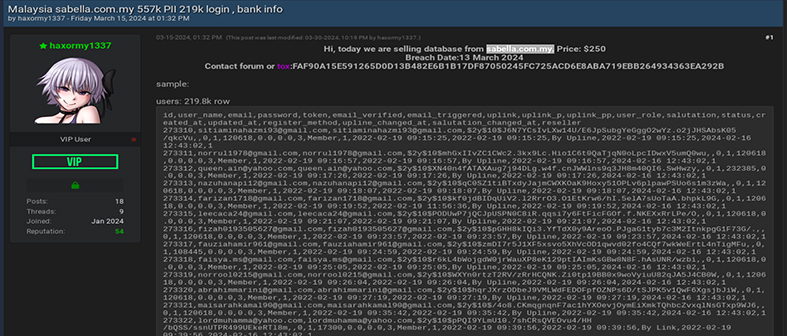
A threat actor operating under the alias “haxormy1337” is selling a database purportedly from Malaysia’s e-commerce platform “sabella.com.my.” This database allegedly contains bank details of all users. Such a breach poses a severe risk to the financial security and privacy of individuals.
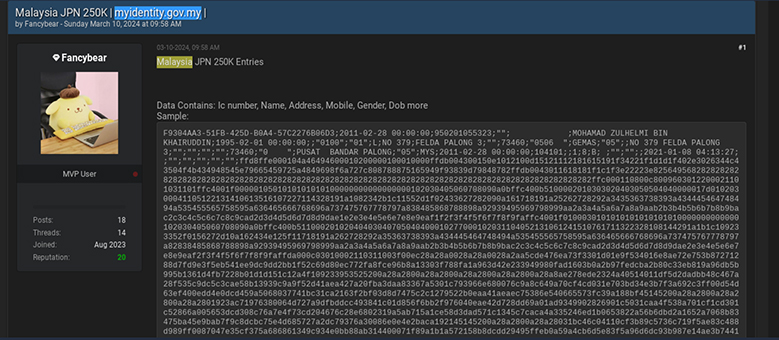
CYFIRMA encountered a threat actor operating under the name “Fanybear,” who is advertising the sale of a database containing information from Malaysian citizens and permanent residents sourced from myidentity.gov.my. This database reportedly includes sensitive details such as IC number, name, address, mobile number, gender, date of birth, and more. Such a breach poses a significant threat to the privacy and security of individuals.
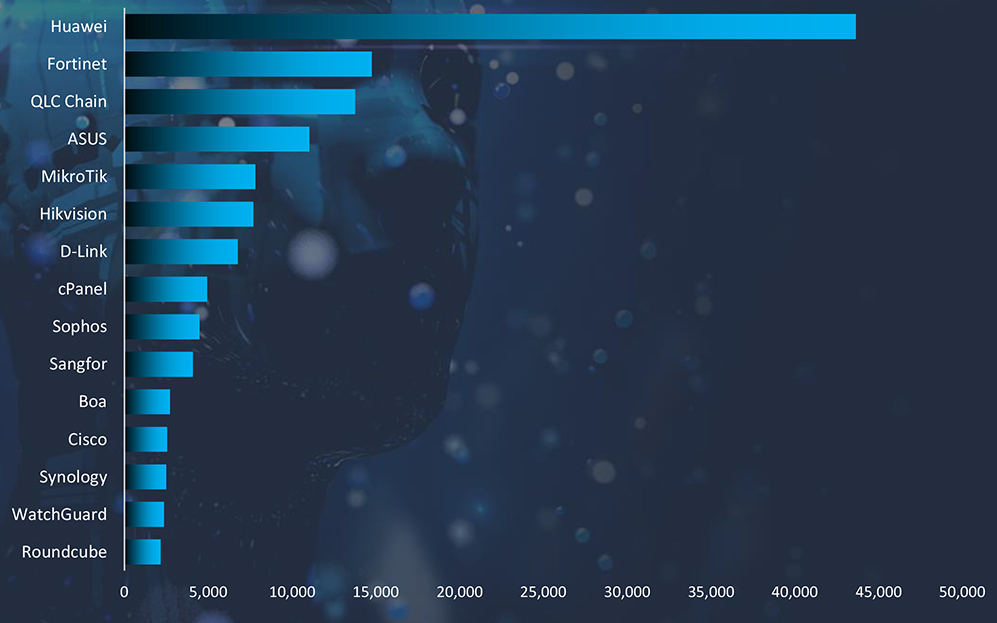
Exposed IoT devices play a significant role in cyber attacks due to their often-inadequate security features and widespread adoption across various sectors. These devices can serve as entry points or targets in larger network breaches, primarily because they frequently lack robust encryption, undergo infrequent updates, and have default or weak credentials that are easily exploited. Once compromised, IoT devices can be used to form botnets, enabling attackers to conduct DDoS (Distributed Denial of Service) attacks, data breaches, or surveillance. Their connectivity and access to larger networks also make them a valuable asset for attackers looking to move laterally within infrastructure, escalate privileges, or disrupt critical services. This vulnerability is exacerbated by the rapid expansion of IoT devices in homes, industries, and cities without corresponding advancements in their security frameworks.
| Vulnerability | CVSS Score | Vendor | Product |
| CVE-2024-21887 | 9.1 | Ivanti | IvantiSecure Connect and Policy Secure |
| CVE-2018-10562 | 9.8 | Dasan | DasanGPON Home Router |
| CVE-2017-9841 | 9.8 | PHPUnit- Sebastian Bergmann | PHPUnit |
| CVE-2024-21893 | 8.2 | Ivanti | IvantiConnect Secure, Policy Secure and Ivanti Neurons for ZTA |
| CVE-2024-27198 | 9.8 | JetBrains | TeamCity |
| CVE-2018-14558 | 9.8 | Tenda | TendaAC7/AC9/AC10 |
| CVE-2023-22527 | 9.8 | Atlassian | Confluence |
| CVE-2024-1709 | 10 | ConnectWise | ScreenConnect |
| CVE-2020-15505 | 9.8 | MobileIron | MobileIronMobile Device Management (MDM) |
| CVE-2016-1555 | 9.8 | NETGEAR | WN604,WN802Tv2, WNAP210v2, WNAP320, WNDAP350, WNDAP360, and WNDAP660 |
| CVE-2016-3088 | 9.8 | Apache | ActiveMQ |
| CVE-2017-1000486 | 9.8 | PrimeFaces | PrimeTek |
| CVE-2017-10271 | 7.5 | Oracle | OracleWeblogicServer |
| CVE-2017-15944 | 9.8 | PaloAlto Networks | PAN-OS |