The Asia Pacific (APAC) Threat Landscape Report provides a comprehensive overview of the evolving cybersecurity landscape in the region. In recent years, Asia Pacific has witnessed a significant increase in cyber threats, driven by factors such as rapid digitalization, increased internet penetration, and geopolitical tensions. This report aims to provide key insights into the current state of cyber threats, and emerging trends.

THE GEOGRAPHICAL SCOPE OF THIS REPORT
India, Indonesia, Australia, Bangladesh
APAC Volume – 1
Australia, Bangladesh, India, Indonesia
APAC Volume – 2
Japan, Malaysia, Philippines, Vietnam
YET TO BE UPDATED
New Zealand, Singapore, South Korea, Taiwan, Thailand
UPDATED METHODOLOGY
This is a running report. Our research team will update this report on an ongoing basis to keep the reader updated on the evolving cyber threat landscape of the region.
01 MOVEMENT FROM DIGITAL TO KINETIC TARGETS
Trend: Ransomware attacks on critical infrastructure
Motives: Disruption/Geopolitical/Extortion
02 DATA EXFILTRATION FROM IOT DEVICES
Trend: Spyware, malware, and plug-ins to collect data. Motive: Reputation impact, disruption, extortion
03 EXPLOITATION OF LEGACY SYSTEM
Trend: Brute force attacks, credential reuse, and data exfiltration via malware
Motive: Operational disruption, espionage, IP exfiltration
04 CROSS-ENVIRONMENT ATTACK
Trend: social engineering/phishing. jump server Exploits, remote access tool compromise
Motive: Operational disruption, espionage, IP exfiltration
05 USE OF BOTNETS, AI, DEEP FAKE
Trend: Device scanning, firmware, phishing/malware download
Motives: Disruption, data harvesting, remote attacks (DDOS)
06 SUPPLY CHAIN OF INFRASTRUCTURE, UTILITY COMPANIES REMAIN AT RISK
Trend: Multi-behavioral malware (IT/OT, different operating systems
Target: CII trade secrets documents containing proprietary processes
INCREASED SOPHISTICATION OF CYBER ATTACKS
The region has witnessed a rise in the sophistication of cyber attacks, with threat actors employing advanced techniques to compromise systems and networks.
TARGETED THREATS AGAINST CRITICAL INFRASTRUCTURE
Critical infrastructure sectors face heightened risks, with threat actors showing a growing interest in targeting key industries such as energy, finance, and telecommunications.
RISE IN RANSOMWARE INCIDENTS
Ransomware attacks have surged in frequency and severity, posing significant challenges to businesses and government entities. The attackers often demand cryptocurrency payments for the release of compromised data.
NATION-STATE THREATS AND CYBER ESPIONAGE
Evidence suggests an increase in nation-state-sponsored cyber activities, including cyber espionage and information warfare. This poses significant geopolitical and security concerns for the region.
SUPPLY CHAIN VULNERABILITIES
The report identifies vulnerabilities in the regional supply chain, with cybercriminals exploiting weaknesses in third-party relationships to gain unauthorized access to targeted organizations.
Digital Payments and Financial Services
India’s digital payments and financial services landscape is experiencing robust growth, fueled by innovations such as the Unified Payments Interface (UPI) and the Bharat Bill Payment System (BBPS). These platforms have significantly simplified transactions and increased their volume. This advancement is supported by the Reserve Bank of India’s regulatory measures that encourage new technologies, including the digital rupee and more sophisticated payment methods. Concurrently, the surge in digital transactions has also led to increased cybersecurity threats, with banking customers facing phishing, vishing, and smishing schemes, and financial institutions being targeted by ransomware and malware attacks.
Work from Home and Remote Operations
In India, remote work and operations have expanded significantly, accommodating a variety of job roles across sectors. This transformation, accelerated by the pandemic, has led to more flexible working conditions and a shift towards hybrid and fully remote jobs. However, this shift to remote operations has also brought with it an increase in cybersecurity threats. Remote work environments often lack the stringent security measures found in traditional office settings, making them more vulnerable to attacks. Cyber threats such as phishing, malware, and ransomware have become more common, targeting both individual remote workers and the IT infrastructures of large organizations.
E-Governance and Digital India Initiatives
India’s e-governance and Digital India initiatives have revolutionized how citizens access government services, enhancing efficiency and creating a digitally empowered society. These programs focus on developing a robust digital infrastructure and ensuring services are accessible on demand while promoting digital literacy. However, this digital shift also increases cybersecurity risks, including advanced persistent threats to government data, disruptive DDoS attacks, data breaches, and unauthorized access.
Healthcare Digitalization
In India, the healthcare sector is increasingly leveraging digital tools for efficient patient data management, telemedicine, and research initiatives. This digital transformation, while beneficial, also introduces significant cybersecurity risks. Prominent among these are data theft incidents, where sensitive personal health information (PHI) is targeted, and ransomware attacks on medical and research institutions.
Growth of E-Commerce
India’s e-commerce sector is experiencing rapid growth, projected to significantly expand from its current market size due to increased internet penetration and evolving consumer behaviors. The market’s expansion is driven by digitalization, facilitating a broader reach into tier-2 and tier-3 cities and introducing new ways to shop and transact online. This boom has not only expanded consumer access but also amplified vulnerabilities within the digital commerce space. One notable risk is supply chain attacks, where the integrity of products and services is compromised through third-party vendors. Additionally, the sector faces serious threats from customer data breaches, involving theft of large databases that contain personal and payment information of users.
Increased Use of IoT Devices
The increasing use of IoT devices in India has greatly enhanced connectivity and utility in various sectors including healthcare, manufacturing, and consumer goods. However, this expansion also presents significant cybersecurity challenges. As the number of connected devices grows, so does the complexity of managing their security. Key threats include IoT botnets, which have seen a sharp increase in activity, and are often used for DDoS attacks that can disrupt network services. Other prevalent risks involve the exploitation of device vulnerabilities, which can lead to unauthorized access and control over devices.
Rising Cyber Espionage
Amid escalating geopolitical tensions, there has been a notable increase in cyber espionage activities within the region, particularly targeting the government, defense, and high-tech sectors. These operations often involve state-sponsored attacks that aim to spy on critical national infrastructure and strategic industries, jeopardizing national security. Additionally, there is a significant threat from the theft of intellectual property, where foreign entities target proprietary technologies and research to gain competitive advantages.
Global Leadership
India’s emerging role as a global leader has inadvertently increased its exposure to cyber threats, making it a more attractive target for cyberattacks. This heightened profile, combined with its significant advancements in technology and digital infrastructure, invites more sophisticated cyber threats from various international actors. These actors are often motivated by geopolitical tensions or the desire to disrupt India’s growing influence and economic progress.
We observed 42 campaigns targeting various industries in India during 2023. Chinese, Russian, Pakistan, and North Korean state-sponsored threat actors are behind most of these campaigns.


In 2023, there was a substantial rise in the number of observed campaigns, a marked increase when compared to the preceding two years. This uptick highlights the heightened interest of threat actors in the economic and geopolitical dynamics of India.

In the observed cyber campaigns, threat actors have methodically targeted a multitude of industries within the critical infrastructure. This deliberate focus is generating substantial economic and social repercussions within the threat landscape, amplifying its overall impact.


In the observed campaigns threat actors focused on attacking web applications, operating systems, and various other applications.
| Malware Name | Targeted Services/ Vulnerabilities | Campaign Name | Suspected Threat Actor | Target Industries | Target Geographies |
| NukeSped RAT, DLRAT | Web Application | Gather speed | Lazarus Group | Banks, Diversified Financial Services, Professional Services | Canada, South Korea, United States, Japan, United Kingdom, Australia, India |
| Winnti, Commodity Malware | Web Application | Camaro Delta | Mustang Panda, MISSION2025 | Aerospace & Defense, Multiline Retail, Marine, Government, Industrial Conglomerates, Internet & Direct Marketing Retail, Wireless Telecommunication Services, IT Services, Transportation Infrastructure, Communications Equipment, Diversified Financial Services | Vietnam, South Korea, Singapore, the United States, the Philippines, Japan, Taiwan, Australia, Thailand, India, Indonesia |



Ransomware groups target India primarily because of its vast and rapidly digitizing economy, which includes a burgeoning IT sector, extensive digital payment systems, and a growing reliance on technology across both public and private sectors. These factors create numerous vulnerabilities that cybercriminals can exploit. India’s diverse cyber infrastructure often lacks uniform security measures, making it easier for ransomware attacks to penetrate less secure systems. Furthermore, the high value and critical nature of data handled by Indian businesses and government agencies make them attractive targets for ransomware attacks aimed at securing large ransoms. The overall combination of high-tech adoption rates and varied cybersecurity readiness presents ample opportunities for ransomware groups to capitalize on.
We observed a significant increase in Ransomware victims from India. Notably, this threat landscape is influenced by formidable ransomware groups, including LockBit, BlackCat (Alphvm), and Clop, which feature prominently on the list of perpetrators targeting Indian companies.

Banking and Finance, Manufacturing, Computer Services, Health Care, and Information Technology are the top targets of ransomware actors in India.
During the last one year, CYFIRMA’s advanced telemetry systems detected a total of 953,182 phishing campaigns. This sample size gives us enough insight into the overall threat landscape. Geography is based on the ASN origin of the email. India is ranked one of the top targeted countries in the APAC region.


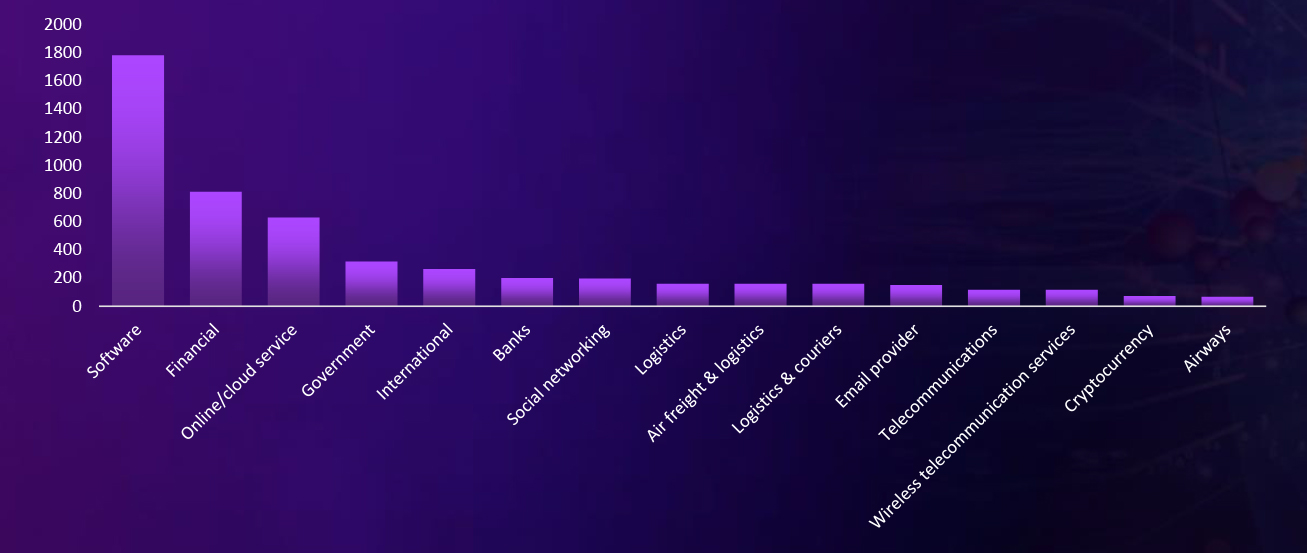
The observed campaign in India reveals several prominent themes exploited in phishing attacks. Among these, the sectors most frequently targeted include Software, financials, Online/cloud service, Government, Logistics, and Telecommunications. These findings shed light on the diverse range of sectors that malicious actors are leveraging to carry out phishing attacks within India. Understanding these prevalent themes is crucial for enhancing cybersecurity measures and safeguarding against the evolving tactics employed by cybercriminals.
In the ongoing conflict between Israel and Palestine, numerous pro-Palestine hacktivist groups from countries such as Indonesia, Brazil, Bangladesh, Turkey, and Pakistan have targeted India’s cyberspace due to India’s stance on Israel. These hacktivist groups have engaged in various activities including defacing, DDoSing, and leaking data from low-security level organizations, schools, universities, and government websites. Additionally, multiple hacktivist groups have been observed resharing old leaked data, falsely claiming it as their own to incite public concern. However, many of these groups are merely obtaining data from underground forums and reposting it on platforms like Telegram, exaggerating their involvement in the leaks.
On April 23, 2024, the Indonesian hacktivist group known as Anon Black Flag defaced the website of Avecgroup, a company involved in real estate business.

On April 20, 2024, a group named irfannotsepuh, an Indonesia-based hacktivist group, conducted a DDoS attack on the website of Neo Foods, a Bangalore-based food processing company, specializing in preserved vegetables and culinary products.

On April 17, 2024, the Indonesian hacktivist group Z-BL4CX-H4T launched an attack on the Public Works Department of Uttar Pradesh, extracting data from their systems. They subsequently shared a sample of the extracted data within their group.

On April 3, 2024, Anonymous Egypt reshared a leaked database of Agri India, an organization likely associated with an AgriTech Hackathon, aimed at addressing challenges within the agricultural sector by proposing tech solutions.

On March 20, 2024, Pro-Palestine Hackers Movement group claimed to have attacked HVL an electrical equipment company.

On March 8, 2024, the Indonesian hacktivist group Z-BL4CX-H4T claimed responsibility for hacking Transforce, a company specializing in air and rail cargo transportation.

On January 31, 2024, Lulzsec Indonesia reposted a DDOS attack originally carried out by another Indonesian hacktivist group, Toxcar Cyber Team, targeting the official website of Indian coal authorities.

There have been instances of Indian hacktivist groups engaging in cyber-attacks against the cyberspace of other countries. In response, hacktivist groups from those targeted countries have initiated counterattacks, leading to a cycle of cyber warfare. This escalation reflects a growing trend of hacktivist activities resembling a virtual conflict between nations.
Indian Hacktivist Groups
Other nation groups attacking Indian Cyber Space
Hacktivist attacks on the Indian government and critical infrastructures lead to severe consequences, including the disruption of governmental services and critical operations, such as healthcare, finance, and utilities, potentially leading to economic losses. Such attacks could also compromise sensitive data, undermining national security and eroding public trust in government institutions. Additionally, these cyber incidents could escalate geopolitical tensions if foreign entities are implicated, increasing the risk of retaliatory cyber actions and straining international relations. The overall impact can hinder the nation’s technological progress and deter foreign investments, posing long-term challenges to India’s economic and strategic stability.
Data leaks play a crucial role in the landscape of cyber threats, acting as a significant vulnerability that can lead to a wide range of security issues and potential damages. When sensitive or confidential information is accidentally exposed or intentionally stolen and released, it can lead to identity theft, financial fraud, and a severe loss of trust and reputation for the affected organization. Such leaks often provide cybercriminals with the necessary data to conduct more targeted and effective attacks, such as phishing schemes, ransomware attacks, or further unauthorized access into secure systems. Additionally, data leaks can result in hefty regulatory fines and legal challenges, especially if the leaked information includes personally identifiable information (PII) protected under data privacy laws.

CYFIRMA encountered a threat actor named Tanaka, who is selling a database related to Mutual Fund Investment in India, specifically ZFUNDS. This database allegedly contains sensitive information including IC number, name, address, mobile number, gender, date of birth, and more. Such a breach poses a significant risk to the privacy and security of individuals’ financial information, underscoring the urgent need for enhanced cybersecurity measures within the investment sector.

CYFIRMA came across a threat actor known as ShakalaBumBum, who claims to be a Pakistani hacker. They boast of hacking into India’s CERT network and obtaining data from Indian Oil, an oil company. Additionally, they’ve purportedly leaked government data from entities, such as the police and BSNL.

CYFIRMA detected a threat actor operating under the alias IntelBroker, who is offering for sale a database purportedly from XpressBrees, a B2C logistics company. This database may contain sensitive information pertaining to logistics operations and customer details.

CYFIRMA came across a threat actor known as SenjorZeroday, who is offering for sale a database allegedly from Indradhanush Gas Grid Limited. This poses a serious security risk, particularly within critical infrastructure sectors.

CYFIRMA identified a threat actor known as KrytonZambie, who is advertising the sale of databases from LeadSquared, a marketing automation and CRM software provider for businesses, and WeRize, a company creating software for financial products. The threat actor claims to still have access to their networks, indicating a serious security breach.

CYFIRMA identified a threat actor known as “888“, who is selling a database purportedly containing information about India’s exports, Indian ports, foreign ports, and more. This compromised data presents significant risks, potentially impacting national security and economic interests. It underscores the urgent need for heightened cybersecurity measures to safeguard critical information about trade and logistics.

CYFIRMA encountered a threat actor known as Tanaka, who is selling a database purportedly from GoldenPay, an Aadhaar-enabled payment system, facilitating online financial transactions at POS/Micro ATM. This database likely contains sensitive financial information and personal details of users.
CYFIRMA identified a threat actor operating under the name PirateJack, who is selling access to Indian companies across various sectors, including IT companies and business services. Additionally, other threat actors are reportedly selling VPN and RDP access. Such activities pose serious cybersecurity threats to Indian businesses, emphasizing the critical need for enhanced security measures to protect against unauthorized access and data breaches.



CYFIRMA detected a threat actor using the alias BLBEV2, who is selling VPN access purportedly from RailTel Corporation of India, a broadband and VPN services provider company, with potential connections to Indian Railways.


In our OSINT research, we found more than 500 Industrial Control Systems exposed to the Internet, owned by organizations in India, potentially allowing an attacker to access them.

Exposed IoT devices play a significant role in cyber attacks due to their often inadequate security features and widespread adoption across various sectors. These devices can serve as entry points or targets in larger network breaches, primarily because they frequently lack robust encryption, undergo infrequent updates, and have default or weak credentials that are easily exploited. Once compromised, IoT devices can be used to form botnets, enabling attackers to conduct DDoS (Distributed Denial of Service) attacks, data breaches, or surveillance. Their connectivity and access to larger networks also make them a valuable asset for attackers looking to move laterally within infrastructure, escalate privileges, or disrupt critical services. This vulnerability is exacerbated by the rapid expansion of IoT devices in homes, industries, and cities without corresponding advancements in their security frameworks.
Most Exploited Vulnerabilities in India – Last 3 months
| Vulnerability | CVSS Score | Vendor | Product |
| CVE-2018-10562 | 9.8 | Dasan | Dasan GPON Home Router |
| CVE-2014-8361 | 8.3 | Realtek | Realtek SDK |
| CVE-2015-2051 | 10 | D-Link | D-Link DIR-645, DAP-1522 revB, DAP-1650 revB, DIR-880L, DIR-865L, DIR-860L revA, DIR-860L revB DIR-815 revB, DIR-300 revB, DIR-600 revB, DIR-645, TEW-751DR, TEW-733GR |
| CVE-2023-20198 | 10 | Cisco | Cisco IOS XE |
| CVE-2016-6277 | 8.8 | Netgear | NETGEAR R/D Series Routers |
| CVE-2017-18368 | 9.8 | Zyxel/Billion | ZyXEL P660HN-T1A v1, ZyXEL P660HN-T1A v2, Billion 5200W-T |
| CVE-2020-16846 | 9.8 | SaltStack | Salt |
| CVE-2017-9841 | 9.8 | PHPUnit | PHPUnit |
| CVE-2021-3129 | 9.8 | Laravel | Ignition |
| CVE-2024-21893 | 8.2 | Ivanti | Ivanti Connect Secure, Policy Secure and Ivanti Neurons for ZTA |
| CVE-2024-21887 | 9.1 | Ivanti | Ivanti Secure Connect and Policy Secure |
| CVE-2024-27198 | 9.8 | JetBrains | TeamCity |
| CVE-2021-44228 | 10 | Apache | Log4j |
| CVE-2023-47246 | 9.8 | SysAid | SysAid On-Premise |
| CVE-2019-9978 | 6.1 | WordPress | WordPress Social Warfare plugin |
The Maldives #Indiaout campaign
The #IndiaOut was initially not a campaign but was a thought that originated in 2013 in Maldives, under Abdulla Yameen’s pro-China administration, marked by terminating agreements with India and fostering anti-India sentiment. Despite Ibrahim Solih reinstating pro-India policies in 2018, the campaign persisted, fueled by figures like Yameen and outlets like Dhiyares News. Social media, street protests, and attacks on Indian diplomats characterized the campaign, which was seen in the wild by 2021.
Agenda
The #IndiaOut campaign in the Maldives aimed to diminish India’s influence. Its widespread social media efforts spurred political shifts, leading to the downfall of the Solih government, a hidden agenda of the campaign. Mohamed Muizzu’s rise to power underscored the campaign’s pro-China stance, reshaping regional governance and expanding China’s footprint in the Maldives.
Bangladesh A New Addition to #Indiaout campaign
In January 2024, an “India Out” campaign emerged, backed by opposition parties and certain civilians in Bangladesh. They allege Indian government interference in Bangladesh’s recent election, won by Prime Minister Sheikh Hasina’s Awami League for a fourth term. With the opposition boycotting the polls, the hashtag #IndiaOut is trending. Hackers from Bangladesh and allied groups are reportedly gearing up to launch retaliatory attacks against India.
Agenda of #Indiaout Campaign
After securing more than 220 seats, Sheikh Hasina earned her fourth consecutive term with the Awami League’s victory. Following this, despite the Bangladesh Nationalist Party’s (BNP) election boycott and minimal political influence, it Spearheaded the #IndiaOut campaign. By harnessing anti-India sentiments, the BNP aims to destabilize Hasina’s government, enhancing its domestic position and aspiring to become a major player in regional politics, possibly influencing ongoing Indian elections.
Twitter accounts that engaged in the campaign aggressively
Tweets by PinakiTweetsBD
Tweets by revolt_71
Tweets by RussellAnamul
Tweets by IndiaOutCamp_BD
Tweets by rupom
Telegram Channels recently Participating in Campaign Against India
https://t.me/systemadminbd
https://t.me/IndiaOutbd
Hashtags used in India out Campaign :
#Indiaout #BoycottIndia #OpIndia #BoycottIndianProducts #SaveBangladeshFromIndia
Possible Impact on India
China’s Geopolitical Interest:
China aims to bolster its influence in Asia, countering India, as is evident in the pro-China administration in the Maldives under Mohamed Muizzu. China’s substantial investments in the Maldives, spanning military aid to infrastructure projects, signal its strategic intent. India’s military withdrawal underscores China’s growing sway. In Bangladesh, while direct interference is uncertain, China may indirectly support hacktivists targeting Indian entities, potentially complicating India’s security.
Overall, the #IndiaOut campaigns in the Maldives and Bangladesh, fueled by anti-India sentiments, pose cybersecurity threats to India. With hacktivist groups targeting Indian entities and China’s geopolitical maneuvers, India faces challenges to its security and regional influence. The situation underscores the complexities of regional dynamics and India’s strategic positioning.

Financial Motivation: Indonesia is the largest economy in Southeast Asia and possesses abundant natural resources. This makes it an attractive target for cybercriminals seeking financial gains through activities, such as hacking into financial institutions, conducting ransomware attacks, or stealing sensitive financial data.
Political Motivation: Indonesia is the world’s fourth most populous country and has a diverse political landscape. Political motivations for targeting Indonesia could include influencing elections, destabilizing the government, or compromising political figures or organizations.
Geopolitical Motivation: Indonesia’s strategic location in Southeast Asia, along with its large population and economic potential, makes it an important player in regional and global geopolitics. Threat actors with geopolitical motivations target Indonesia to gain a competitive advantage, disrupt regional stability, or gather intelligence.

The Asia-Pacific region, with its significant population and pivotal role in global trade, is a focal point for geopolitical competition, primarily exemplified by the rivalry between the United States and China. Indonesia, as Southeast Asia’s largest economy, holds a vital position in this landscape, thanks to its economic growth and control of critical sea lanes. This competition is compounded by multifaceted geopolitical threats stemming from complex regional relations, demographic shifts, and climate change.
Notably, China’s ascent as a superpower shapes the key geopolitical concerns in the region, with the South China Sea disputes and the Taiwan issue at the forefront. China’s territorial claims extend to the South China Sea, including Indonesia’s exclusive economic zone in the Natuna Sea. This has led to territorial tensions, with near-armed conflict in 2019 and 2020.
Indonesia’s foreign policy historically emphasizes nonalignment, aiming to balance relations with the United States and China. Recent efforts have seen the mending of relations with China, with growing economic ties and political interactions. Simultaneously, Jakarta maintains strong security ties with the United States.
However, these developments strain relations with China, and as regional countries assert their sovereignty and economic interests, tensions could rise. Cyber espionage activities primarily target government entities but are expected to expand to non-governmental organizations and commercial entities. The Asia-Pacific region houses some of the world’s most active state-sponsored cyber actors, led by China, followed by Russia and North Korea, while India emerges as an aspiring cyber power.
The potential flashpoint in the regional security landscape centers around the Taiwan issue, with cyber campaigns likely preceding any conflict. While overt military confrontations remain unlikely, cyberattacks targeting various entities are projected to increase. Strengthening network security standards and cybersecurity practices is the top priority for businesses, as regional stability and economic prosperity depend on cybersecurity resilience in this volatile geopolitical environment.
We observed a year-on-year increase in campaigns targeting various industries in Indonesia. Chinese, North Korean, and Russian state-sponsored threat actors are behind these campaigns.

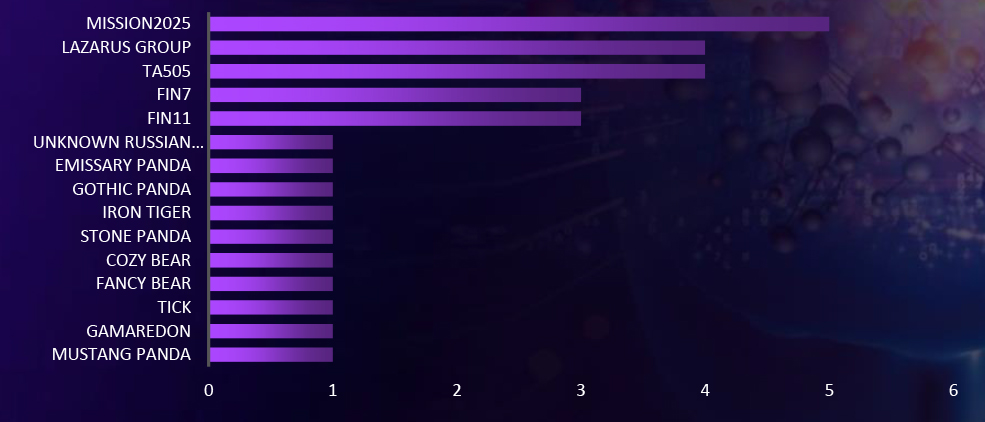

| Malware Name | Targeted Services/ Vulnerabilities | Campaign Name | Suspected Threat Actor | Target Industries | Target Geographies |
| Winnti, Commodity Malware | Web Application | Camaro Delta | Mustang Panda, MISSION2025 | Aerospace & Defense, Multiline Retail, Marine, Government, Industrial Conglomerates, Internet & Direct Marketing Retail, Wireless Telecommunication Services, IT Services, Transportation Infrastructure, Communications Equipment, Diversified Financial Services | Vietnam, South Korea, Singapore, the United States, the Philippines, Japan, Taiwan, Australia, Thailand, India, Indonesia |
| – | Web Application | Void | TA505,FIN11, FIN7, Gamaredon | Auto Components, Real Estate Management & Development, Government, Internet & Direct Marketing Retail, Banks, Interactive Media & Services, Automobiles | South Korea, Vietnam, Singapore, Hungary, the United States, Japan, Ukraine, United Kingdom, Malaysia, Indonesia |
| Rifdoor, Nukesped, ShadowPy | Web Application | UNC069 | TICK, Lazarus Group | Real Estate Management & Development, Government, IT Services, Automobiles, Construction & Engineering, Food Products, Construction Materials, Multiline Retail, Auto Components, Food & Staples Retailing, Hotels, Restaurants & Leisure, Industrial Conglomerates, Energy Equipment & Services, Leisure Products, Diversified Financial Services, Hospital, Beverages, Textiles, Apparel & Luxury Goods | South Korea, Vietnam, the Czech Republic, the United States, Japan, Taiwan, the United Kingdom, South Africa, Australia, Germany, India, Indonesia |


The threat actor “abyss0” purportedly leaked data from Indosat Ooredoo, claiming it occurred in December 2023 but was only posted on April 4, 2024. The leaked data includes employee login information and detailed floor plans, indicating a serious breach. With Indosat Ooredoo estimated to have 102 million subscribers as of 2022, the breach raises significant concerns about privacy and security implications, despite questions surrounding the timing and authenticity of the leak’s claim versus its actual posting date.

Indonesian citizens’ KYC data was leaked in an underground forum. The information provided in the leaked data, which includes various types of personal identification, such as the Kartu Tanda Penduduk (Resident Identity Card), Surat Izin Mengemudi (Driver’s License), KIS Healthy Indonesia card (Health Card), Directorate General of Taxation records, Participant Card, and Family Card, poses a significant threat to individuals’ privacy and security. The leakage of such sensitive data, posted by the threat actor “Blastoise” on January 25, 2024, could potentially lead to identity theft, financial fraud, and other forms of malicious exploitation.

The involvement of the threat actor “Blastoise” in another data leak, this time pertaining to Denpasar, the capital city and economic center of Bali, Indonesia, raises significant concerns about cybersecurity in the region. As a prominent city in the Nusa Tenggara Islands and the second largest in Eastern Indonesia after Makassar City, Denpasar’s exposure to such data breaches could have far-reaching consequences for individuals and businesses in the area.

CYFIRMA discovered a data leak posted by the threat actor “Blastoise” on April 5, 2024, containing admin login and user database information from Petrokimia Gresik, a fertilizer company based in Gresik, East Java, Indonesia.

The discovery of a data leak involving ANGKASA PURA AIRPORTS INDONESIA, posted by the threat actor “TNG2R” on February 7, 2024, is deeply concerning. The leaked data, totaling 72 GB and comprising 68,237,264 records containing sensitive personal information such as names, emails, NIK (Indonesian ID numbers), NPWP (tax identification numbers), phone numbers, addresses, dates of birth, genders, incomes, and more, poses significant privacy and security risks for the affected individuals.

We discovered a data leak involving Jember State Polytechnic, a higher education institution focusing on vocational education in Indonesia, posted by the threat actor “Blasties” on January 7, 2024, which raises serious concerns regarding cybersecurity within the institution. The leaked data, which includes admin login and user database information, underscores the urgency of assessing the breach’s extent, mitigating potential risks, and fortifying the institution’s cybersecurity measures.

A data leak discovered by CYFIRMA, involving MyPertamina, a digital financial service platform integrated with the LinkAja app for non-cash fuel payments at Pertamina’s public fueling stations, posted by the threat actor “Bjorka” on January 24, 2024, is highly concerning. The leaked data, comprising approximately 44,237,264 records in CSV file format, contains sensitive personal information including names, emails, NIK (Indonesian ID numbers), NPWP (tax identification numbers), phone numbers, addresses, dates of birth, and genders. This presents significant privacy and security risks for the individuals affected.

A data leak discovered by CYFIRMA, involving Indonesian banks’ access, posted by the threat actor “Cyber Niggers AKA Aegis” on November 28, 2023, is deeply troubling. The sale of such access poses a significant threat to the security and integrity of the banking system in Indonesia.


A data leak discovered by CYFIRMA, attributed to the threat actor “Ddarknotevil,” posted on December 21, 2023, and February 13, 2024, is deeply concerning. The first leak, concerning the Dareliman Database, is reported to be approximately 13 GB in size and in SQL file format. The second leak purportedly contains private financial data and documents from the Ministry for Economic Affairs, totaling around 136 GB.
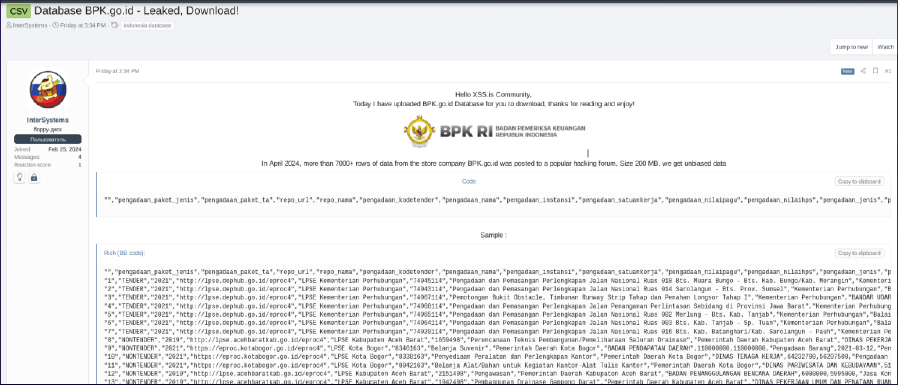
A data leak discovered by CYFIRMA, posted by the threat actor “InterSystems” on April 5, 2024, involving the Badan Pemeriksa Keuangan Republik Indonesia (Indonesian Supreme Audit Agency), is a significant security concern. The leaked data reportedly includes admin login credentials and user database information, comprising over 7000+ rows of data from the agency’s database. This breach raises serious issues regarding the integrity and security of sensitive government information.

The sale of Indonesia airport access by the threat actor “TheColorYellow” on March 1, 2024, discovered by CYFIRMA is deeply concerning. Access to airport systems pose significant security risks, not only for the airports themselves but also for the safety and privacy of passengers and personnel.

The sale of Indonesian bank access by the threat actor “comradbinski” on December 1, 2023, discovered by CYFIRMA is extremely alarming. Access to banking systems pose a significant threat to the security of financial institutions and their customers.
The Quantum of DDoS attacks increased globally after the start of the Russia-Ukraine war when pro-Russian and pro-Ukraine hacktivists started targeting each other with DDoS campaigns and also started targeting alliance nations to show support to their respective country.
In the case of Indonesia, the presence of hacktivist channels potentially linked to Indian-origin attacks targeting Indonesia through methods like DDOS, Defacement, and Data leaks were observed. Here are the channels identified:
These channels may represent potential threats to Indonesian cybersecurity and should be closely monitored and addressed by relevant authorities to prevent any malicious activities.
Indonesian Hacktivist Groups in action

Meanwhile, it appears there are several Indonesian hacktivist channels believed to support Palestine and engage in attacks against India and Israel using methods like DDOS, Defacement, and Data leaks. Here’s the list of these channels:
Indonesian Hacktivist Groups in action

Cyber hacktivist groups from India and Indonesia have engaged in campaigns targeting organizations in each other’s countries through DDoS attacks, defacement, and data breaches. These activities not only disrupt government entities but also have broader implications for businesses in both countries.
Impact on Organizations
Strategic Consequences

During the period spanning from April 10th, 2023 to April 10th, 2024 CYFIRMA’s advanced telemetry systems meticulously detected a staggering total of 981,727 phishing campaigns. Within this extensive dataset, it’s noteworthy that Indonesia emerged as one of the most targeted geographic regions in Southeast Asia.

The observed campaigns in Indonesia reveal several prominent themes exploited in phishing attacks. Among these, the sectors most frequently targeted include Software, Airlines, Air Freight & Logistics, Government, Wireless Telecommunication, Media, and Banks. These findings shed light on the diverse range of sectors that malicious actors are leveraging to carry out phishing attacks within Indonesia. Understanding these prevalent themes is crucial for enhancing cybersecurity measures and safeguarding against the evolving tactics employed by cybercriminals.
We observed a year-on-year increase in ransomware attacks on Indonesia targeting various industries.

Ransomware groups target Indonesia due to its significant and growing economy, increasing digital transformation, potential vulnerabilities in cybersecurity practices among certain organizations, geopolitical and economic motivations, the widespread use of cryptocurrencies, relative lack of cybersecurity awareness, regional and global connectivity, and, in some cases, political instability. The country’s expanding digital infrastructure and the perceived financial capacity of high-profile targets make it an attractive environment for cybercriminals seeking substantial ransom payouts. Notably, this threat landscape is influenced by formidable ransomware groups, including LockBit, BlackCat (Alphvm), and Bianlian, which feature prominently on the list of perpetrators targeting Indonesian companies.
| Exploited Vulnerabilities | Vendor | Product |
| CVE-2023-20198 | Cisco | Cisco IOS XE |
| CVE-2017-9841 | PHPUnit | PHPUnit |
| CVE-2015-2051 | D-Link | D-Link DIR-645, DAP-1522 revB, DAP-1650 revB, DIR-880L, DIR-865L, DIR-860L revA, DIR-860L revB DIR-815 revB, DIR-300 revB, DIR-600 revB, DIR-645, TEW-751DR, TEW-733GR |
| CVE-2014-8361 | Realtek | Realtek SDK |
| CVE-2016-6277 | Netgear | NETGEAR R/D Series Routers |
| CVE-2019-11510 | Pulse Secure | Pulse Secure VPN |
| CVE-2024-24919 | Check Point | Check Point Security Gateway |
| CVE-2024-27198 | JetBrains | TeamCity |
| CVE-2018-10562 | Dasan | Dasan GPON Home Router |
| CVE-2024-1709 | ConnectWise | ScreenConnect |
| CVE-2019-9670 | Synacor | Zimbra Collaboration Suite |
| CVE-2020-25213 | WordPress | WordPress |
| CVE-2023-42793 | JetBrains | TeamCity |
| CVE-2019-3396 | Atlassian | Confluence |
| CVE-2022-26134 | Atlassian | Confluence |
All the observed exploited vulnerabilities in the given list are also part of the CISA’s Known Exploited Vulnerability list.
As per CISA, the following vulnerabilities are exploited by Ransomware Groups as well: CVE-2019-11510, CVE-2024-27198, CVE-2018-10562, CVE-2024-1709, CVE-2023-42793, CVE-2019-3396, CVE-2022-26134
MINING
Australia’s mining sector stands as a cornerstone of the nation’s economy, ranking as the world’s fourth-largest mining nation, following China, the United States, and Russia. It boasts prominent positions as a top producer of commodities such as gold, iron ore, lead, zinc, and nickel. Furthermore, Australia holds the world’s largest uranium reserves and ranks fourth in black coal resources. Recent data from the Australian Bureau of Statistics (ABS) reveals that the mining industry contributed a staggering A$455 billion ($298.64 billion) in export revenue during the 2022–23 fiscal year, accounting for approximately two-thirds of the nation’s total export revenue. This marks a notable 10.5% increase from the previous record set in 2021–22.
Given its economic significance and the wealth of valuable data it generates, the mining industry has become a prime target for cyber espionage campaigns. Threat actors, ranging from nation-states to organized criminal groups, are increasingly drawn to the sector’s vast data reservoirs, aiming to steal proprietary information, gain competitive advantages, or influence sales and mergers. The mining sector’s strategic importance in global supply chains further amplifies its susceptibility to cyber threats. Sophisticated and highly targeted cyber-attacks, orchestrated by diverse attacker groups including hacktivists, hostile governments, and organized criminals, seek to exploit the industry’s vulnerabilities. These threats capitalize on the mining sector’s heavy reliance on integrated and automated systems, which, if compromised, could have cascading impacts on regional and global supply chains and national economies.
MANUFACTURING
Australia’s manufacturing landscape is characterized by its diversity, encompassing major sub-industries such as food, beverages, and tobacco; machinery and equipment; petroleum, coal, and chemicals; and metal products. Anticipating the future, the next two decades will witness a transformative shift in Australia’s manufacturing sector towards a more integrated, collaborative, and export-oriented ecosystem. This evolution is set to emphasize high-value customized solutions within global value chains, with a keen focus on value addition in both pre-production (design and R&D) and post-production (after-sales services). Additionally, sustainable manufacturing practices and a move towards low-volume, high-margin customized production are expected to shape the industry’s trajectory.
According to the 2023 CommBank Manufacturing Insights Report, a significant 72% of Australian manufacturers have optimistic production growth projections for the upcoming year. Concurrently, an equal proportion are gearing up to boost capital expenditure, earmarking investments in innovative technologies to refine processes, enhance efficiency, bolster productivity, elevate quality, and expand capacity.
While technological advancements have been instrumental in propelling the manufacturing sector forward, fostering innovation, and driving operational enhancements, they also introduce a burgeoning array of cyber threats. The integration of advanced technologies, interconnected systems, and digital transformation initiatives has expanded the industry’s cyber-attack surface, making it an attractive target for threat actors. Threat actors are increasingly drawn to the manufacturing industry due to its pivotal role in the economy, critical infrastructure connections, intellectual property repositories, and the potential for disrupting global supply chains. The sector’s reliance on interconnected systems, data-driven operations, and integrated technologies presents vulnerabilities that cybercriminals aim to exploit, ranging from intellectual property theft and industrial espionage to operational disruptions and financial extortion.
AGRICULTURE
Australia’s agriculture sector stands as a linchpin of the nation’s economy, playing a pivotal role in both domestic production and international exports. The sector’s diverse array of primary products, including wheat, milk, fruits, nuts, vegetables, and meat, significantly contributes to the country’s GDP. Notably, key export commodities such as beef, wheat, wine, wool, and lamb underscore Australia’s global prominence in agricultural trade. The beef industry, in particular, shines as Australia’s largest agricultural enterprise, positioning the nation as the world’s second-largest beef exporter, trailing only behind Brazil. Impressively, approximately 72% of Australia’s agricultural production finds its way to international markets.
Despite its economic significance and global reach, the Australian agricultural industry finds itself increasingly in the crosshairs of cyber threats. Disturbingly, recent data positions the sector as the sixth most susceptible to data breaches. Threat vectors plaguing the industry encompass a spectrum of cyberattacks, ranging from data breaches and ransomware incidents to phishing campaigns, scam emails, and malware infiltrations.
The multifaceted nature of Australia’s agricultural sector, encompassing a spectrum from small-scale enterprises to expansive global operations, presents a complex cybersecurity landscape. This diversity translates into varying degrees of IT proficiency and cybersecurity awareness across the industry. While the sector witnesses a burgeoning influx of technological investments, there remains a discernible gap in prioritizing cybersecurity measures.
The integration of digital platforms, payment gateways, and advanced agricultural machinery, exemplified by precision agriculture technologies, inadvertently provides cyber adversaries with avenues to exploit vulnerabilities. These vulnerabilities extend beyond financial transactions, encompassing a broad spectrum of risks, including unauthorized access to personal and business data, compromise of production systems, and theft of intellectual property.
IT INDUSTRY
Australia’s IT sector is experiencing robust growth, boasting a compound annual growth rate of 13.47% projected between 2022 and 2027. By 2027, the industry is forecasted to achieve a commendable value of US$146.98 billion. Demonstrating its momentum, Australia’s broader tech ecosystem currently stands at a valuation of $167 billion, marking an impressive 80% growth over the past five years. This surge is underpinned by Australia’s proficiency in diverse technological domains, encompassing Software as a Service (SaaS), fintech, cybersecurity, and digital gaming.
However, as the IT industry expands and evolves, it becomes an increasingly attractive target for cyber threats within the Australian landscape. The sector’s rapid growth, expansive value, and multifaceted expertise present a lucrative opportunity for threat actors.
Threat actors are drawn to the IT industry due to its pivotal role in the digital transformation era. With its vast repositories of valuable data, intellectual property, and financial transactions, the sector offers a treasure trove for cybercriminals seeking unauthorized access, data theft, or financial gain. Additionally, the interconnected nature of the IT ecosystem, encompassing cloud services, online platforms, and digital infrastructures, amplifies the sector’s susceptibility to cyber threats.
FINANCE
Australia’s financial services industry stands as a cornerstone of the nation’s economy, contributing a substantial $140 billion to the GDP. Notably, the sector’s growth trajectory has outpaced the overall economy in recent decades, evidenced by financial institutions’ assets surging to nearly 500% of GDP by 2020, a significant leap from the 200% recorded in the 1990s.
However, alongside its economic prominence, the finance industry’s digital transformation has attracted heightened cyber threats within the Australian landscape. In 2022 alone, targeted attacks on Financial Service Institutions (FSIs) escalated by approximately 200%. Threat actors are particularly drawn to the finance sector due to its wealth of valuable assets and data. The sector’s vast repositories, including credit card details, account information, personally identifiable information (PII), and critical network access, present lucrative opportunities for cybercriminals. These threat actors, motivated by financial gains or other malicious intentions, frequently target FSIs through sophisticated cybercrime campaigns, leveraging tactics such as ransomware attacks to extort funds or disrupt operations.
TOURISM
Beyond its economic contributions, Australia’s allure as a tourism hotspot is undeniable. The country’s diverse offerings cater to a broad spectrum of travelers, from the captivating depths of the Whitsundays for scuba enthusiasts and the iconic vistas of Uluru to the pristine trails of the Daintree Rainforest and the world-renowned New Year’s Eve fireworks spectacle in Sydney.
However, the tourism industry’s digital evolution and global prominence have inadvertently heightened its vulnerability to cyber threats within the Australian context. Threat actors are increasingly targeting the tourism sector, enticed by its vast customer base, extensive data repositories, and intricate supply chains. Threat actors view the tourism industry as a lucrative target, given its wealth of sensitive data, including traveler information, financial transactions, and reservation details. Additionally, the sector’s interconnected ecosystem, encompassing travel agencies, hospitality services, and online platforms, presents numerous avenues for cybercriminals to exploit vulnerabilities, ranging from data breaches and financial fraud to ransomware attacks.
LOGISTICS
The logistics industry plays an indispensable role in bolstering Australia’s economy, overseeing the intricate processes of production, storage, inventory management, and the efficient delivery and distribution of goods and services. As of 2023, the Australia Freight and Logistics Market commands a significant valuation of approximately 89.86 billion USD, with projections indicating a growth trajectory to reach 113.94 billion USD by 2029. This growth underscores the sector’s vitality, driven by the nation’s robust import and export dynamics.
However, as the logistics industry evolves and expands, it concurrently becomes a focal point for cyber threats within the Australian threat landscape. Threat actors are increasingly targeting the logistics sector, drawn by its pivotal role in the supply chain ecosystem, an extensive network of stakeholders, and vast volumes of valuable data and goods in transit. Threat actors perceive the logistics industry as an attractive target due to its integral position in facilitating commerce and trade. Disruptions or compromises within the logistics chain can have cascading impacts, ranging from supply chain delays and financial losses to broader economic repercussions. Cybercriminals exploit vulnerabilities within the sector’s digital infrastructure, targeting critical systems, transport networks, and inventory management platforms to execute attacks such as ransomware, data breaches, or operational disruptions.
Nestled in the heart of the Asia Pacific, Australia emerges as a lone state-continent, an outpost of the West facing an increasingly delicate and hostile environment. This unique position sets the stage for a geopolitical tightrope walk with ramifications resonating far beyond its shores.
The Asia Pacific, home to over half the global population, commands strategic importance. Two-thirds of global container trade navigates its sea lanes, making it a vital artery for global trade and energy supply. Australia, with its growing economic power, tradition of aligning with the West, and proximity to critical sea lanes, finds itself thrust into the role of a strategic fulcrum in the unfolding U.S.-Chinese great-power competition.
However, this prominence comes at a cost. The Asia Pacific, and Australia in particular, confronts a myriad of geopolitical threats, positioning the region as a hotbed of competition in the 21st century. The historical backdrop of unsettled relations, demographic shifts, and potential climate change fallout adds layers of complexity, fostering an environment prone to instability and conflict.
Central to the geostrategic challenges is the rise of China as a superpower. The South China Sea disputes and the Taiwan issue loom large, with China pressing territorial claims that could leave Australia with no cost-free choices of political alignment. Australia’s decision to join the AUKUS defense pact underscores its commitment to the West, but this choice strains relations with crucial partners and triggers a full-blown trade war with China.
China’s coercive tactics extend into cyberspace, exemplified by recent cyber attacks on major Australian infrastructure. The use of cyber tools against allies is not unprecedented, as evidenced by Chinese APTs engaging in cyber espionage against Cambodia. This dynamic cyber landscape is further exacerbated by the divergence in visions between the West, led by Australia, and China, with the former upholding neutral rules and the latter fostering a hierarchical order.
The strained relations manifest in frequent cyber attacks, with Chinese APTs targeting the Australian government and military offices. These attacks may spill into the civilian sector if diplomatic ties continue to deteriorate. Economic coercion becomes a weapon as Australia, more than any other country, bears the brunt of China’s restrictions on various products due to geopolitical disagreements.
Beyond the China-centric tensions, the region harbors multiple sources of potential conflicts, ranging from the India-Pakistan feud to North Korea’s posturing. The emergence of security partnerships like the QUAD and AUKUS platforms adds further complexity, as does the economic slowdown in China and the relocation of technology manufacturing.
Russia’s increasing dependence on China raises concerns of a forming Eurasian bloc, intensifying competition in trade, territorial disputes, military buildup, and cyber activities. The Asia Pacific emerges as a hotbed for cyber statecraft, with China leading the charge, closely followed by Russia and North Korea, while India aspires to cyber power status.
North Korea, emboldened by Russian backing, intensifies its cyber criminal activities, targeting South Korea, Japan, Australia, and U.S. security partners like the Philippines. The potential conflict over Taiwan looms as the biggest flashpoint, promising unpredictable cyber fallout and a prelude to a massive cyber campaign to intimidate regional countries.
While overt military confrontation remains distant, cyber attacks targeting governmental and private entities are projected to rise, serving as reminders not to overstep boundaries. The overarching imperative for businesses in the region is clear: bolster common network security standards and cybersecurity practices, fortifying resilience against the uncertainties of the evolving geopolitical landscape.
We observed 7 ongoing campaigns targeting various industries in Australia in 2024. Russian, Chinese, and North Korean state-sponsored threat actors are behind most of these campaigns. Here are some details about observed sample campaigns.
| Malware Name | Targeted Services/ Vulnerabilities | Campaign Name | Suspected Threat Actor | Target Industries | Target Geographies |
| PubLoad, PlugX RAT | Application Infrastructure Software, Web Application, Operating System | territorial integrity | Mustang Panda | Diversified Telecommunication Services, Government, Industrial Conglomerates, Wireless Telecommunication Services, Banks, Electric Utilities, Oil, Gas & Consumable Fuels, Diversified Financial Services | Vietnam, South Korea, the United States, Japan, the Philippines, the United Kingdom, Thailand, Australia, France, India |
| Blackenergy, Kapeka | Operating System, Infrastructure-as-a-service Solutions | graffitist | Sandworm | Government, Industrial Conglomerates, Energy Equipment & Services, Electric Utilities, Oil, Gas & Consumable Fuels, Gas Utilities, Water Utilities | The United States, Japan, Ukraine, Finland, the United Kingdom, Australia, France, Germany |


The number of observed campaigns significantly increased compared to the last two years in 2023 indicating threat actors’ interest in Australia’s economic and geopolitical dominance.

CYFIRMA Research team observed a data leak related to Australia-based Keech (keech[.]com[.]au) manufacturing company. Keech produces a complete range of ground-engaging tools for mining, earthmoving, and construction equipment, as well as high-integrity steel castings for use in agriculture, rail, and defense industries. Indonesia-based threat actor StarsX Cyber Team claimed responsibility for the leak of 125.76MB of data as part of the #opaustralian campaign.

CYFIRMA Research team observed a data leak related to GranvueHomes (www[.]granvuehomes[.]com[.]au). Granvue Homes is Melbourne’s leading new house builder. Leaked data contains name, e-mail, phone, postcode, and other information.

The Australian solar energy company AG Energy suffered a data breach. The leak led to the exposure of data including Full names, Email addresses, home phone numbers, Mobile phone numbers, and Physical addresses. In total, 138k customers were affected.

CYFIRMA Research team observed a data leak related to IAB Australia. IAB Australia is the peak trade association for online advertising in Australia.


Australia, like many developed nations, is susceptible to ransomware attacks due to its strong economy, advanced digital infrastructure, and global connectivity. The attractiveness of potential high ransom payments, coupled with the interconnectivity of critical systems, makes it a target for cybercriminals. Additionally, if cybersecurity measures are not consistently robust, vulnerabilities may be exploited, leading to an increased risk of successful attacks on both public and private sectors. While specific motives can vary, the combination of economic factors and digital prominence contributes to the likelihood of Australia being targeted by ransomware attacks. Notably, this threat landscape is influenced by formidable ransomware groups, including LockBit, BlackCat (Alphvm), Cl0p, and 8Base, which feature prominently on the list of perpetrators targeting Australian companies.

| Vulnerability | Vendor | Product |
| CVE-2020-16846 | SaltStack | Salt |
| CVE-2019-11510 | Pulse Secure | Pulse Secure VPN |
| CVE-2022-26134 | Atlassian | Confluence |
| CVE-2021-44228 | Apache | Log4j |
| CVE-2019-3929 | Barco/AWIND | Barco/AWIND OEM |
| CVE-2014-8361 | Realtek | Realtek SDK |
| CVE-2021-26855 | Microsoft | Exchange |
| CVE-2023-29357 | Microsoft | SharePoint |
| CVE-2021-38647 | Microsoft | Open Management Infrastructure (OMI) |
| CVE-2023-20198 | Cisco | Cisco IOS XE |
| CVE-2020-3452 | Cisco | Cisco ASA and Cisco Firepower Threat Defense |
| CVE-2021-21315 | Node.js | Node.js |
| CVE-2023-22527 | Atlassian | Confluence |
| CVE-2017-9841 | PHPUnit | PHPUnit |
| CVE-2018-10562 | Dasan | Dasan GPON Home Router |
In the last six months, the Australian threat landscape has undergone a notable impact from distributed denial-of-service (DDoS) attacks, with the Information Technology and Services sector being particularly affected, representing a significant 80.90% of the attacks. Moreover, a substantial 56.81% of these attacks endured for periods exceeding three hours, indicating a prolonged and impactful threat scenario. Additionally, attacks within the one to three-hour duration range accounted for 13.05%, underscoring a notable proportion of sustained assaults. Examining bitrates, attacks with speeds ranging from 500 Mbps to 1 Gbps constituted 6.58%, while those with less than 500 Mbps made up the majority share at 90.98%. This diverse distribution highlights the necessity for a comprehensive and adaptive cybersecurity strategy to effectively mitigate the varying intensities of DDoS threats in Australia.



TEXTILE INDUSTRY
When considering the Bangladesh threat landscape, the country’s prominent textile industry becomes a notable focal point for threat actors. Bangladesh stands as the world’s second-largest clothing exporter, second only to China. The textile manufacturing market in Bangladesh is on a growth trajectory, expected to expand from USD 17.99 billion in 2023 to USD 23.86 billion by 2028, with over 4,500 active factories. The clothing and textile sector accounts for a substantial 75% of the nation’s manufacturing employment and contributes significantly to Bangladesh’s GDP, exceeding 13%. Furthermore, textiles and related products constitute over 84% of export earnings. This industry’s lucrative nature, extensive supply chain interconnections, and economic impact make it an appealing target for threat actors interested in disrupting production, compromising trade secrets, and exploiting vulnerabilities, thereby influencing both the country’s economic stability and global trade dynamics.
SHIPBUILDING
The nation’s shipbuilding industry emerges as a significant point of interest for threat actors. Bangladesh, as a maritime nation with aspirations to become a developed economy by 2041 through the prospects of the Blue Economy, places a strategic emphasis on its shipbuilding sector. Presently, with over 200 shipbuilding companies, this industry wields substantial influence with its ability to generate considerable foreign currency through ship exports, drives employment opportunities, establishes vital support for backward linkage industries, and significantly contributes to the national GDP. These attributes that make the shipbuilding industry a cornerstone of economic development render it an appealing target for threat actors keen on disrupting economic stability, disrupting international trade, or compromising sensitive shipbuilding technologies, thus undermining Bangladesh’s path toward economic advancement and its maritime ambitions.
TOURISM
Bangladesh boasts breathtaking natural attractions like the Sundarbans, one of the largest mangrove forests globally, and Cox’s Bazar Sea Beach, the longest in the world, among others. These natural wonders position the country as a potential hotspot for local and international tourists. Presently, the tourism industry contributes 3.02% to the nation’s GDP and accounts for 8.07% of its total employment. Notably, the Bangladesh Tourism Board (BTB) has outlined an ambitious 25-year tourism master plan to attract 10 million tourists by 2040 and generate an annual revenue of $8 billion. While this vision holds the promise of increased inbound and domestic tourism and a boost in sector investment, it also garners the attention of threat actors who may seek to disrupt the sector’s growth, compromise the safety of travellers, or exploit vulnerabilities within the industry for economic or political gain, potentially hampering Bangladesh’s path to realizing its tourism aspirations.
INFORMATION TECHNOLOGY
Bangladesh is swiftly establishing itself as a prominent player in the global IT arena, successfully securing a significant share of the IT market in South Asia. This industry is acknowledged as one of the nation’s most promising sectors and is projected to reach a substantial valuation of USD 5 billion by 2025. Notably, the Information and Communication Technology (ICT) sector has already contributed 1.28% to Bangladesh’s GDP, while simultaneously creating over 300,000 jobs. The rapid growth and economic potential of the IT sector make it a prime target for threat actors who may seek to exploit vulnerabilities, engage in cyber espionage, or compromise sensitive information. This heightened interest from threat actors is driven by the industry’s potential for economic disruption, intellectual property theft, and its pivotal role in shaping Bangladesh’s technological future.
LEATHER INDUSTRY
Bangladesh’s leather sector is a well-established industry, ranking second in terms of export earnings. Thanks to its remarkable value, substantial growth prospects, and extensive employment opportunities, the leather industry has been accorded top priority status. Notably, Bangladesh captures a 3% share in the global leather and leather products market, with nearly 60% of its annual output being destined for export. Significantly, the government has formulated a forward-looking ten-year perspective plan that sets a target of elevating the leather sector’s export earnings to a range of $10-$12 billion by 2030. The appeal of this industry to threat actors is underpinned by the potential for economic disruption, exploitation of supply chain vulnerabilities, and the theft of proprietary designs and technologies, all of which could impede the sector’s growth and its vital role in shaping Bangladesh’s economic future.
Bangladesh, positioned as the world’s eighth most populous country with over 170 million people, is becoming a key player in the wider Indo-Pacific region. Despite its historical status as one of the world’s most destitute nations, sustained economic growth and social transformation have propelled Bangladesh into a new era of development. However, the geopolitical landscape in and around Bangladesh remains susceptible to instability and conflict, fuelled by historical relations, demographic shifts, and the potential ramifications of climate change.
The region is currently navigating significant geostrategic challenges, primarily driven by the ascent of India and China as superpowers, with prominent issues such as the South China Sea disputes and Taiwan garnering attention. Meanwhile, Bangladesh’s economic rise has quietly reshaped the geopolitical dynamics, shifting South Asia’s economic center eastward and fostering the reintegration of an eastern subcontinent once divided by animosities and formidable borders.
The geographic proximity of Bangladesh to neighboring countries, including Nepal, Bhutan, China, and Burma, positions it as an attractive partner with growing diplomatic, political, and economic ties. India, in particular, has strengthened its relationship with Bangladesh, transforming a historically complex connection into a productive partnership with tangible outcomes in various sectors.
Amidst this geopolitical landscape, Dhaka’s orientation towards the Indo-Pacific, starting from the Bay of Bengal, holds strategic significance. However, the complexity of regional relationships is evident, with China expressing concerns over Bangladesh joining the Quad, a grouping aimed at countering Beijing’s influence. In addition, Bangladesh’s strategic location is of great value to China, prompting initiatives to build alternative routes and secure port facilities in the Indian Ocean and Bay of Bengal region.
The intricate network of international relationships in the region, shaped by history, geography, economy, and strategic interests, carries the potential for conflict escalation, particularly in cyberspace. Factors such as the Chinese economic slowdown, Western pressure on technology manufacturing relocation, and Russia’s increasing dependence on China add layers of complexity to the regional dynamics, with potential manifestations in trade policies, territorial disputes, military buildup, and cyber conflicts.
The looming prospect of a conflict over Taiwan adds a significant flashpoint to the regional security horizon, with cyber warfare anticipated to play a major role, presenting unprecedented challenges. While overt military confrontation remains distant, cyber-attacks targeting governmental and private entities are projected to rise as a means of enforcing boundaries.
In this evolving landscape, the overarching priority for businesses in the region is to strengthen common network security standards and cybersecurity practices across sectors, acknowledging the potential cyber threats arising from the intricate geopolitical dynamics shaping the Bangladesh threat landscape.
| Malware Name | Targeted Services/ Vulnerabilities | Campaign Name | Suspected Threat Actor | Target Industries | Target Geographies |
| Crimson RAT | Web Application, Operating System | UNC066 | Transparent Tribe | Aerospace & Defense, Multiline Retail, Government, Industrial Conglomerates, IT Services, Transportation Infrastructure, Diversified Consumer Services, Diversified Financial Services | Bangladesh, South Korea, the United States, Japan, the United Kingdom, United Arab Emirates, Israel, France, Nepal, Germany, India |
| LockBit3.0, Dridex | Web Application | UNC062 | TA505 | Health Care Equipment & Supplies, Multiline Retail, Household Durables, Entertainment, Industrial Conglomerates, Leisure Products, Media, IT Services, Health Care Providers & Services, Diversified Financial Services, Household Products, Textiles, Apparel & Luxury Goods | Canada, South Korea, Bangladesh, Belgium, the United States, Japan, Australia, France, Germany, India |
| CrimsonRAT, ObliqueRAT | Web Application, Operating System | Unnamed Campaign | Transparent Tribe | Professional Services | Bangladesh, Bhutan, Sri Lanka, Nepal, India |

The CYFIRMA Research team observed the sale of 80 GB of Bangladeshi Navy intel from late 2022 for USD 3000.

We observed a data leak related to Telerad Medical Systems Ltd (TMS). TMS is a Medical Equipment Importer, distributor, sales, supply, and service company in Bangladesh. Leaked data contains 4.4 GB of documents, databases, and other personal medical stuff.

Recently observed data leak of Bangladesh Police Database and files. Threat actor claim that these files were obtained in 2020 from the email account of a high-ranking Bangladeshi Police official.

Link3 Technologies Ltd data leaked in an underground forum. Link3 Technologies Ltd is a full-service IT Solutions Provider that has been operating in the Bangladesh market for more than ten years with a very high level of success, achieved through uncompromised service quality and customer satisfaction. Leaked data includes App installation and registered user data.

Ransomware groups target Bangladesh for various reasons, including the country’s increasing economic significance, growth in critical sectors like textiles and IT, and the potential for financial gains through ransom payments. Bangladesh’s expanding digital infrastructure and financial systems provide attractive targets for cybercriminals seeking to exploit vulnerabilities and encrypt critical data, thereby demanding ransoms. Additionally, its geopolitical location in South Asia and regional conflicts could make it a potential battleground for cyberattacks aimed at exerting influence and promoting political agendas. As a result, ransomware groups view Bangladesh as a lucrative target, leveraging these factors to advance their cybercriminal activities.

Recently, Agrani Bank PLC, a state-owned commercial bank of Bangladesh was compromised by a ransomware group.


| VULNERABILITY | VENDOR | PRODUCT |
| CVE-2017-10271 | Oracle | Oracle Weblogic Server |
| CVE-2017-9841 | PHPUnit | PHPUnit |
| CVE-2018-10562 | Dasan | Dasan GPON Home Router |
| CVE-2019-2725 | Oracle | Oracle Weblogic Server |
| CVE-2024-24919 | Check Point | Check Point Security Gateway |
| CVE-2024-27198 | JetBrains | TeamCity |
| CVE-2021-44228 | Apache | Log4j |
| CVE-2014-8361 | Realtek | Realtek SDK |
| CVE-2019-0193 | Apache | Solr |
| CVE-2019-16920 | D-Link | D-Link DIR-615, DIR-655C, DIR-825, DIR-835, DIR-855L, DIR-866L, DIR-652, DIR-862L, DHP-1565, DAP-1533 |
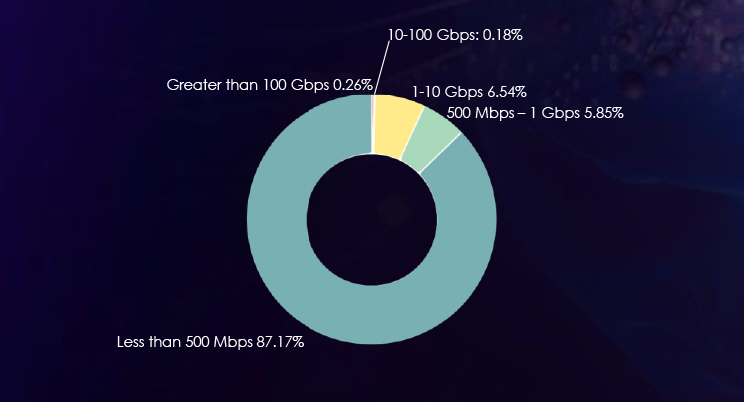
In the last six months, Bangladesh’s threat landscape has undergone a notable impact from distributed denial-of-service (DDoS) attacks, with the Information Technology and Services sector being particularly affected, representing a significant 69.30% of the attacks. Moreover, a substantial 39.95% of these attacks endured for periods exceeding three hours, indicating a prolonged and impactful threat scenario. Additionally, attacks within the one to three-hour duration range accounted for 16.62%, underscoring a notable proportion of sustained assaults. Examining bitrates, attacks with speeds ranging from 500 Mbps to 1 Gbps constituted 5.85%, while those with less than 500 Mbps made up the majority share at 87.17%. This diverse distribution highlights the necessity for a comprehensive and adaptive cybersecurity strategy to effectively mitigate the varying intensities of DDoS threats in Bangladesh.