



Brief Introduction: Makop ransomware is the latest malware and is trending currently. It instructs the users/victims to contact the malware authors via Tox, a P2P instant messaging protocol. The malware encrypts all the files in each folder and added extension .makop to each file. The format of the encrypted file is “Original_name_of_the_file.Original_extension_of_file.[Unique/random Id associated with the File].[.].makop”. It also drops a ransom note with the name “readme-warning.txt” into each compromised folder and desktop also. It skipped some of the folders like Windows and Winnt in their names or path and also skipped some of the files having specific extensions like .exe, .dll or extensions like lockbit, origami etc related to other ransomware infections. The ransomware uses AES256 Key to decrypt strings at runtime in memory and it also creates mutex to avoid running more than one instance of the malware. The ransomware access and modify registry values and also use it to gain persistence.
Risk Score: 8.
Confidence Level: High.
Suspected Malware: Makop Ransomware.
Function: Encryption and Demand Ransom
Threat actor Associations: Unknown
Other Malwares related to Makop: Phobos
First Seen: 2020
Latest Seen: Dec 2021
Target Industry: Multiple
Target Countries: Multiple
File Details: As shown in Figure1, the following are the details related to the ransomware “Makop”.File Type: Windows PE-32 Executable
MD5: 01f8dfe2d719194088a5fafcbe2832ff
SHA256: bff786ac2f9f89305650d5776dbf1ada6ab229ab87be2c335aedaaf7c438185e
Subsystem: GUI
Compilation Time: July 2021
Figure 1
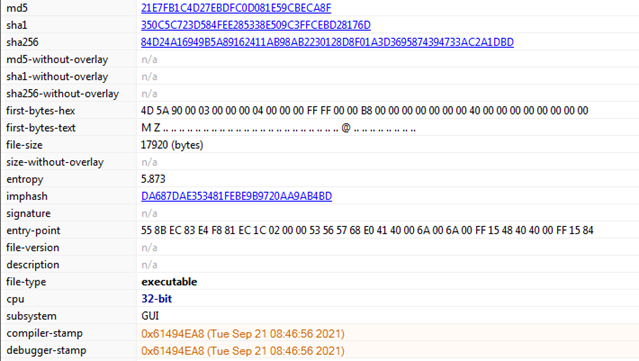
Figure1 above shows that our malware sample is Windows PE-32 executable having GUI subsystem and compile time is 18 July 2021. It also shows various hashes corresponding to the sample file which may also act as IOCs.
Figure2 below shows that the malware sample file is Visual C/C++ based and Figure3 shows that the file is not packed.
Figure2
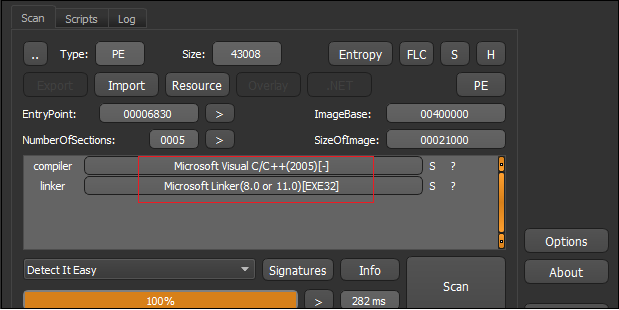
Figure3
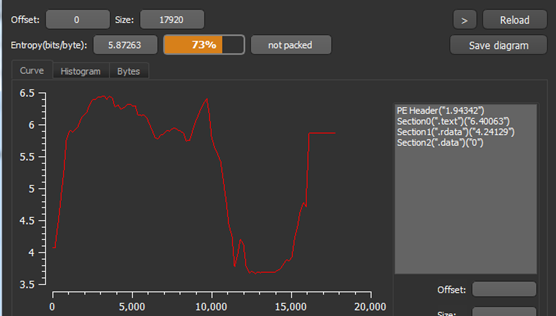
Figure 4
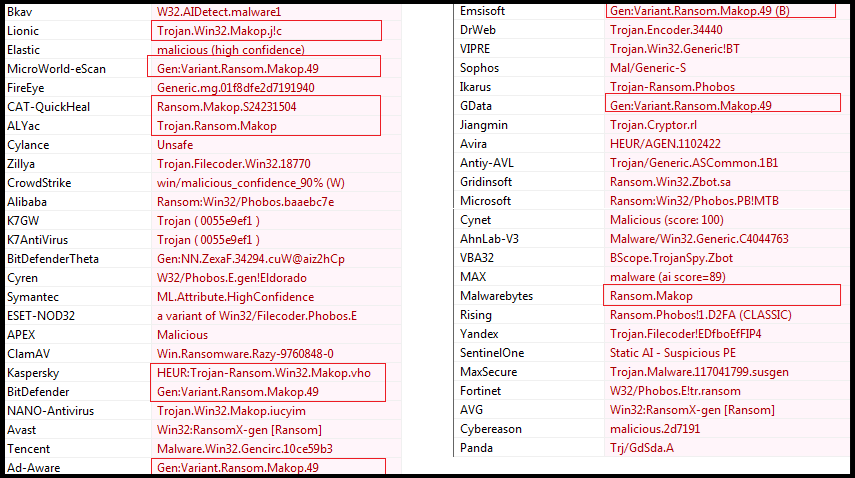
Our research team has analyzed the malicious sample file through various anti-virus engines and most of them were detected as malicious and some specifically (see Figure4 above, highlighted part) detect it as Makop Ransomware.
Figure5 below shows sections present in the malware file and it also has a virtualized section .data means can only be available in memory and indicate towards the presence of some code/data that can only be unpacked in memory by the malware.
Figure5
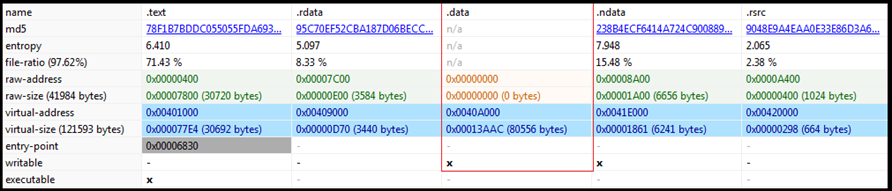
Figure6
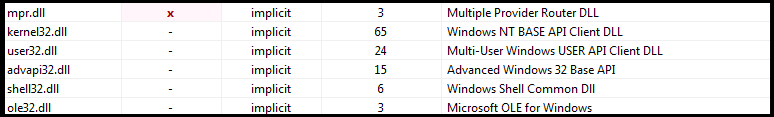
Figure6 above shows various libraries imported by the ransomware. The libraries indicate the malware functionality. It can have low-level functionality which includes memory/hardware access and manipulation. It has the capability to access and manipulate registry entries. It can access user-interface components and ability to control user actions. Mpr.dll contains functions used to handle communication between OS and network providers. It has the ability to open web pages and files.
Figure7
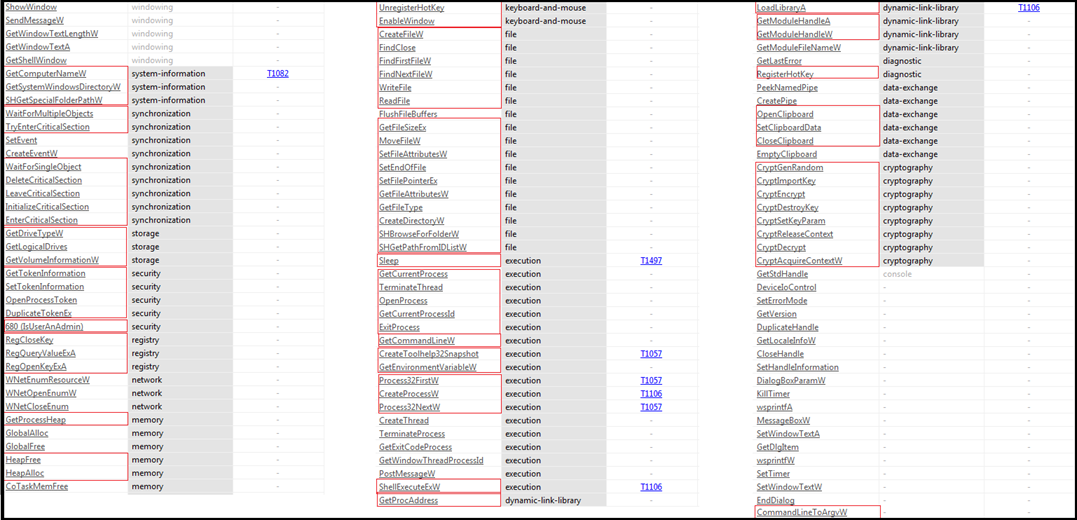
Figure7 above shows APIs imported by the malware and indicate towards following capability and functionality available in the malware:
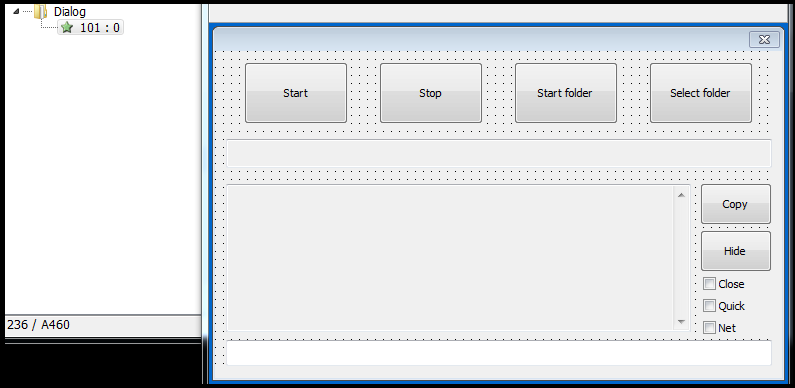
When our research team runs the ransomware, a GUI interface pops up on the screen as shown below in Figure8. The ransomware runs in administrative mode and it is strange that when we click on start then only it starts executing and encrypting the file. The possible reason behind this is that the ransomware has the capability to hide/control GUI components, so when in actual ransomware may execute this interface will be hidden from the user and is used to control the working of the ransomware.
Figure8
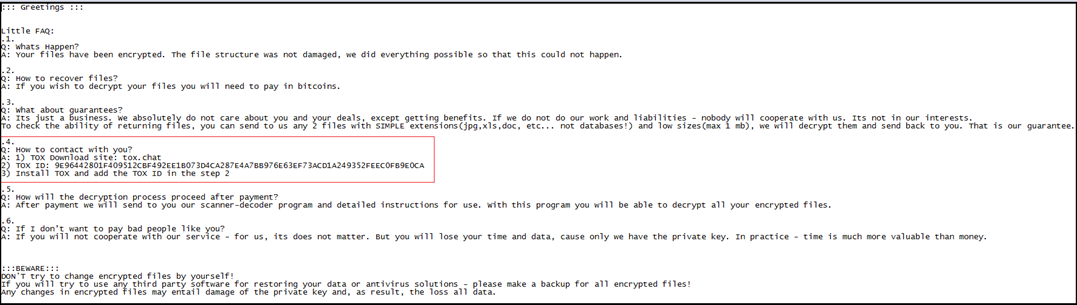
After encrypting file, the “Makop Ransomware” drops the ransom note with the name “readme-warning.txt” shown in Figure9 to each folder and Desktop. The ransom note mentioned a few FAQs and answers like what has happened with the victim machine, how a victim can retrieve their files, how a victim may contact the malware authors for decryption keys, and so on. The ransom note instructs the victim to contact the attacker through Tox (a P2P instant-messing protocol) as shown in Figure9 (highlighted part).
Figure9
Further as shown in Figure10 given below, the “Makop ransomware” encrypt the files in each folder on the victim machine and add extension .makop at the end. The encrypted file name changed to the format mentioned below:
Original_name_of_the_file.Original_extension_of_file.[Unique/random Id associated with the File].[.].makop
Example: Sample1.docx.[3B74C342].makop (as shown in Figure9).
Figure10
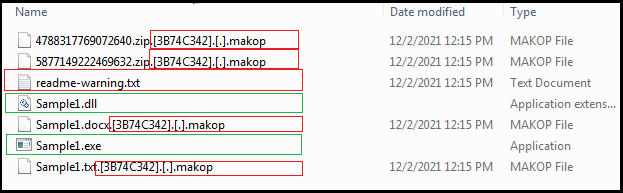
Figure11
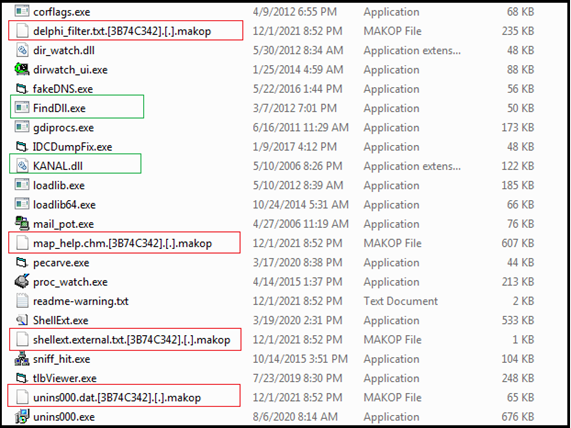
The makop ransomware does not encrypt contents of folders/directories that contain “Windows” or “Winnt” in their path/names like “C:\Windows”, “C:\ProgramData\microsoft\windows\” etc. Further “Makop Ransomware also does not encrypt files having specific extensions like .exe, .dll, .makop, boot.ini as shown in Figure11 above. Some of the extensions like lockbit, origami, raga, shootlock etc are also skipped which are the result of other ransomware infections.
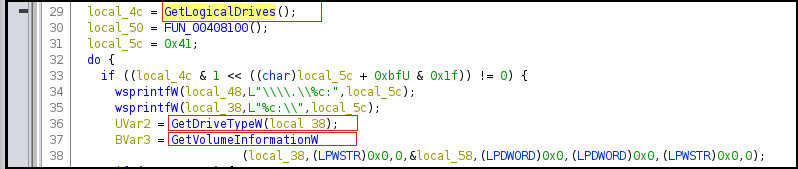
Some of the code snippets (Figure 12) are given below to provide more insights into the functionality possessed by the “Makop Ransomware”
The API GETLogicalDrives is used to find information about logical drives in the system and GetVolumeInformationW retrieves information about the file system and associated volumes while the GetDriveTypeW API checks if a disk drive is a network, RAM, CD-ROM, removable or fixed drive. “Makop Ransomware does not target RAM and CD-ROM Drives.
Figure12
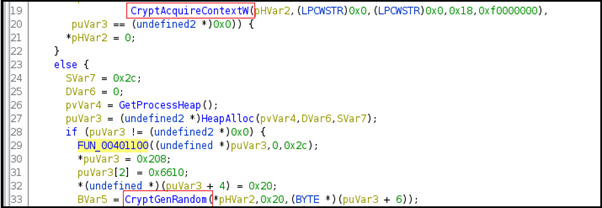
The CryptAcquireContextW API here is used to acquire a handle to a key container within a cryptographic service provider and CryptGenRandom API is used to generate random bytes.
Figure13
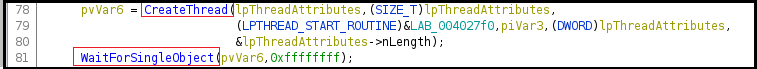
In Figure14 below, the malware is creating a thread and implementing mutex and waiting for a single object to access at a particular time.
Figure14
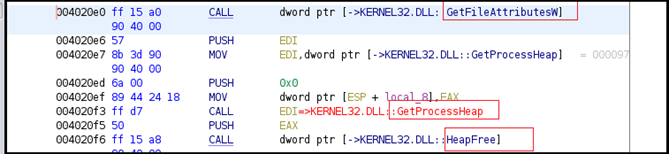
In Figure15 below, the API GetFileAttributeW is used to access file system attributes corresponding to a specified file or directory. Further dynamic memory allocation is implemented using GetProcessHeap to retrieve the handle to the default heap of the calling process.
Figure15
The files are enumerated using the FindFirstFileW and FindNextFileW APIs as shown in Figure16 given below.
Figure16

The cryptographic key is imported by calling the CryptImportKey, as shown in Figure17 below. Using the key, the malware encrypts data by calling the CryptEecrypt function and destroys the cryptographic keys afterward.
Figure17
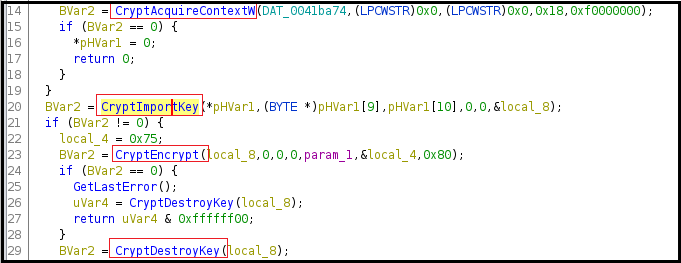
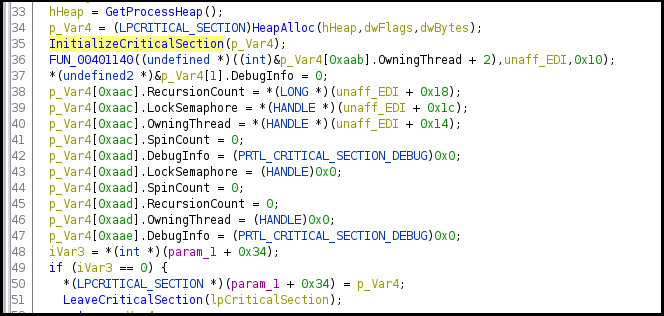
Figure18 shows the malware is initializing the critical section and implementing synchronization/semaphore for the shared resource access.
Figure18
As shown in Figure19 below, the malicious binary accessing and writing into a file.
Figure19
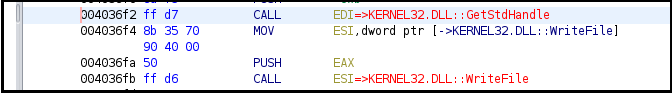
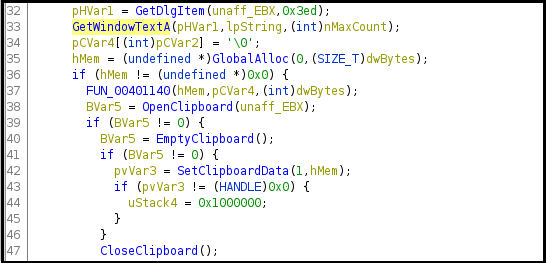
Figure20
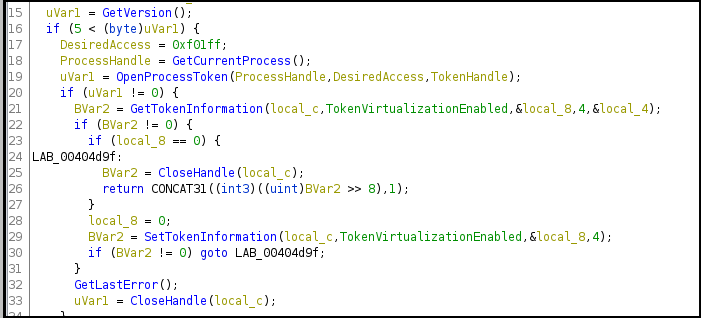
The ransomware uses the GetVersion function to get information about the major and minor version numbers of the OS along with other information The GetTokenInformation API is used to determine the elevation level of the token and the malware opens the access token associated with the current process.
Figure 21
The APIs mentioned in Figure22 given below that is WNetOpenEnumW and WNetEnumResourceW are used to enumerate the network resources.
Figure22
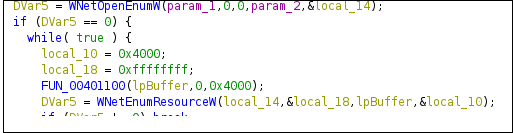
Figure23
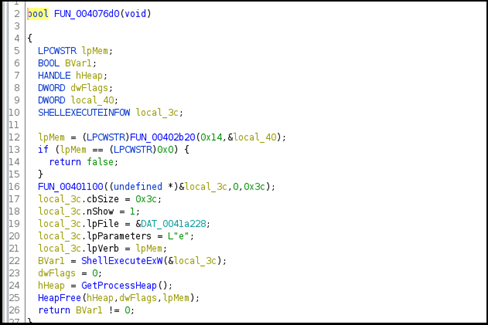
The ransomware retrieves the command-line string/arguments of the current process as shown in Figure24 given below.
Figure24
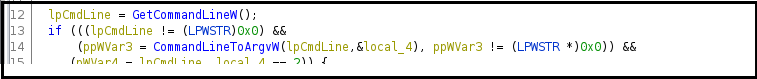
Figure25
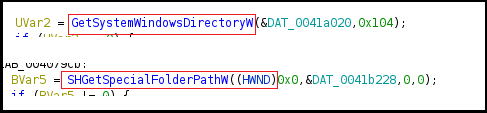
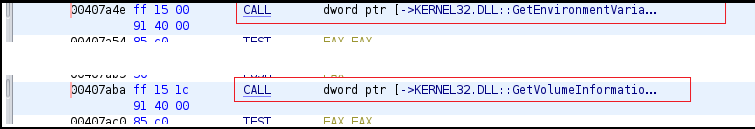
GetSystemWindowsDirectoryW function retrieves shared windows directory on a multiuser system and the SHGetSpecialFolderPathW retrieves the path of folder identified by its CSIDL as shown in Figure25 above. The malware accesses the serial number of the drive by using GetVolumeInformation and also the value of the “SystemDrive” environment variable is retrieved using the GetEnvironmentVariableW API as shown in Figure26 given below.
Figure26
In Figure27, the malware is taking snapshots of the process which includes heap, modules, and thread information. The processes are enumerated using the Process32FirstW and Process32NextW APIs.
Figure27
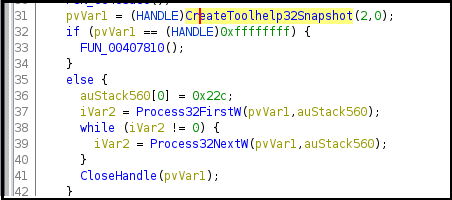
Figure28
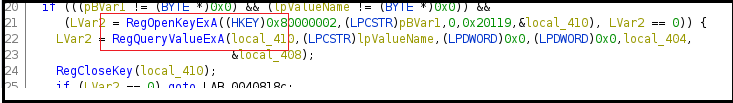
In Figure28 above, the malware is accessing and querying registry entries.
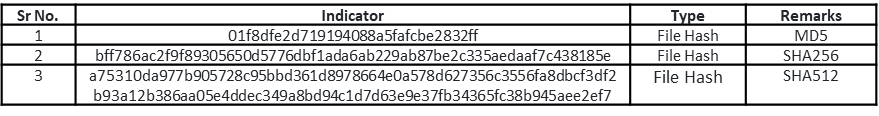
| Sr No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566 Phishing |
| 2 | Execution (TA0002) | T1204.002 Malicious File |
| 3 | Persistence (TA0003) | T1547.001 Registry Keys |
| 4 | Defense Evasion (TA0005) | T1112 Modify Registry |
| 5 | Discovery (TA0007) | T1082 System Information Discovery |
| 6 | Impact (TA0040) | T1486 Data Encrypted |