



Suspected Malware: ShadowPad Malware
Function: Backdoor
Risk Score: 8
Confidence Level: High
Threat actor Associations: China-Based Threat Actors (like Tick, APT41)
Used in Campaigns: CCleaner, NetSarang, ShadowHammer
First Seen: 2015
ShadowPad is a modular backdoor considered to be the successor of PlugX. ShadowPad constitutes various plugins having specific functionality and the malware has the capability to “plug” or “unplug” these plugins at run-time in shellcode format. It can also load additional plugins dynamically from the C2 server when required. ShadowPad is accessed by a limited set of attackers which includes APT41 and Tick group. Since shadowPad is a sophisticated backdoor with a complete set of capabilities, the attackers used it for long-term espionage in the target environment. Further, many threat actors stopped developing their own backdoor after shadowPad and adopted it as their tool of operation due to significant cost reduction in development & maintenance.
Encrypted shadowPad main file has payloads embedded in it and load malicious DLL using DLL sideloading on a legitimate executable.
Sample Details:
File Type: Windows PE Executable
Architecture: 64 Bit
MD5: 5f3093473ae4167fd51d4282fce73741
SHA256: f7ef194f2dcc341ba03f76872cb7c0dfbae8f79118f99cf73dfccfb146c4e966
Subsystem: GUI
Language: MS Visual C++
Compilation Time: 22 March 2021
Embedded Files:
The malicious file contains three embedded files. One is executable, the second is dll and the third is the .dat file (see Figure1). Our research team extracted all and further analyse them.
Embedded .dat File:
MD5: 3db6f7535816e28dd55607d0a60ee9f2
SHA256: d05f80d5ccb1b6d4aea847ad38ef7e8ab619ff33601aa54cc836704e4fb53520
Embedded .dll File:
MD5: ad82d23accb10b4c0fc7f8c9782ae6ad
SHA256: 1e06fd5b9aa0e5260369e52ec2d9f87060941de835234afd198b1d4c0b161678
Embedded .exe File:
MD5: 8fdf8e4ecff114c1e6c9827c53742a1c
SHA256: 2e642afdd36c129e6b50ae919ca608ac0006ce337f2a5a7a6fb1eef6a4ad99e7
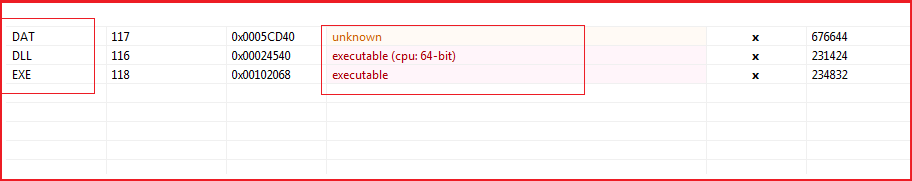
Figure1
Execution/Dropped Files:
Upon execution, the malware creates a new instance of itself, dropped the embedded executable file with the name “OLEVIEW.exe” in the temp folder, and spawns a child with the same name. It also copies the “OLEVIEW.exe” to the System32 folder with the name wsuhost.exe and drops the DLL into system32 with the name “IVIEWERS.dll”. To avoid detection and gain persistence, wsuhost.exe runs as a service and spawns a child with the name “svchost.exe” and terminates itself.
Note: The embedded DLL is the same (in functioning and other parameters like hashes corresponding to different sections, resources, etc.) as dropped DLL (IVIEWERS.dll) but has a different file hash means some modification is done by the malware while dropping the embedded DLL and the hash of dropped “IVIEWERS.dll” for different run instances is different.
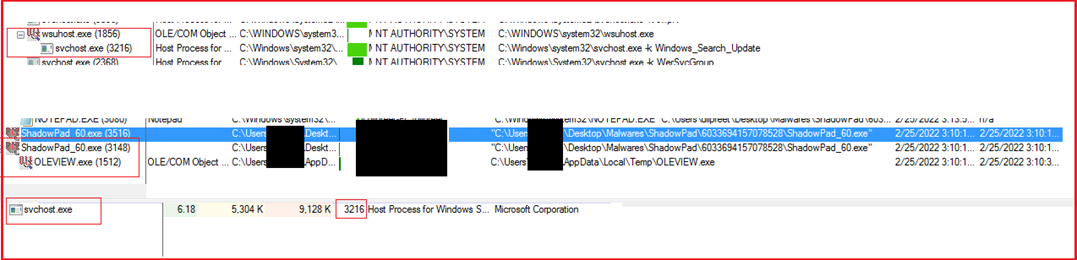
Figure2
C2 Communication:
The svchost process communicates with “http[:]//fljhcqwe[.]com:80” at regular intervals.
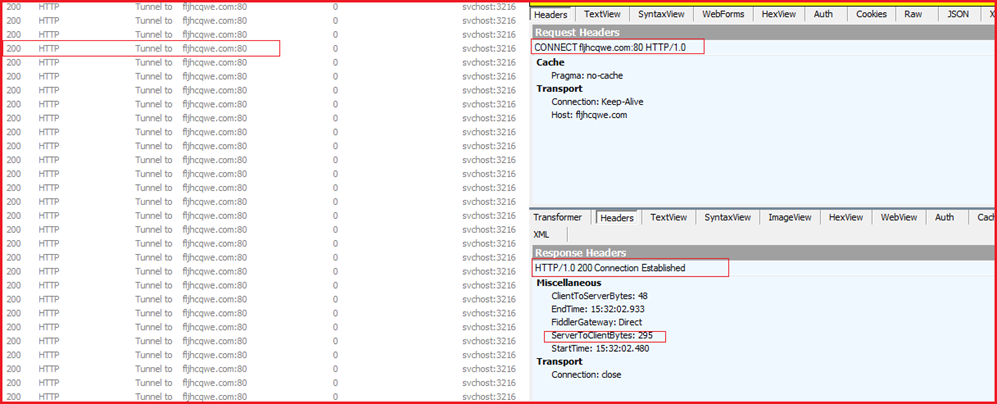
Figure3
Meta Data:
The malware requires administrative privileges to run.
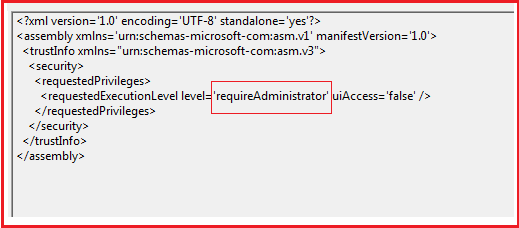
Figure4
The Icon is used for wsuhost.exe process as shown in Figure5 and executes as a service (see Figure6).

Figure5
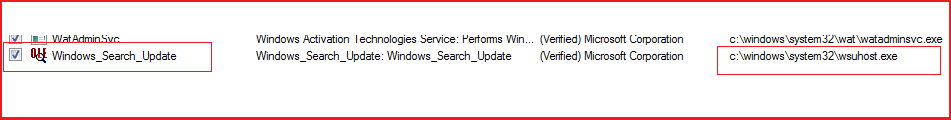
Figure6
Code Snippets:
Sandbox evasion techniques implemented in “IVIEWERS.dll”
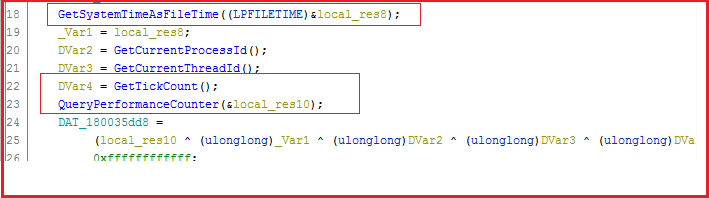
Figure7
The main malware file (f7ef194f2dcc341ba03f76872cb7c0dfbae8f79118f99cf73dfccfb146c4e966) drops two files “OLEVIEW.exe” and “IVIEWERS.dll” from its resource section to disk in folder returned by GetTempPathA and executes “OLEVIEW.exe” and it will further load the malicious “IEVIEWERS.dll”. Logic related to drop other files helper.exe, flsh.exe, IEViewers.dll.dat are also embedded in the same way (see Figure 8).
Encrypted payloads are embedded in the main malware file and DLL sideloading is used to load malicious DLL (IEViewers.dll) by sideloading legitimate executable (OLEVIEW.exe) vulnerable to DLL search order hijacking which is further used to load and decrypt another file (IVIEWERS.dll.dat).
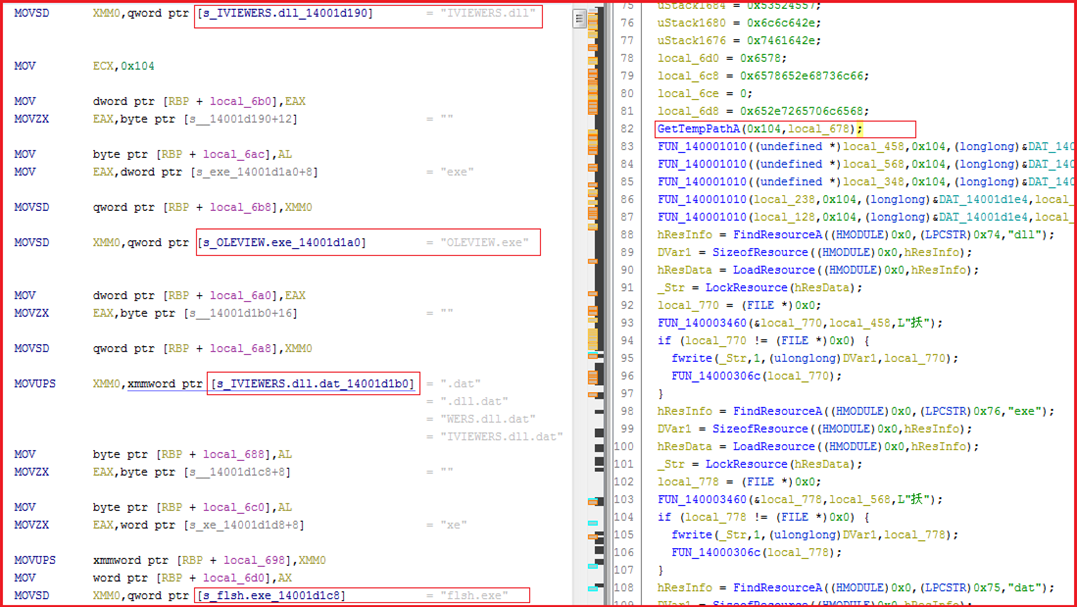
Figure8
The libraries and APIs imported by the malware further provide insights towards the following capabilities possessed by the malware:
ShadowPad is a sophisticated, well-developed backdoor and sold privately to a selected set of customers with a complete or partial set of plugins as per the requirement and it reduces the cost of development and maintenance for threat actors willing to use this fully functional backdoor. It is under continuous development and enhances its capabilities with time. The adoption of any sold or cracked version of this malware raises the difficulty for researchers to surely attribute it to the right threat actors and require long-term monitoring and cautious validation. Malware sample has the functionality to communicate with C2 server, dropped malicious payloads, execute them, modify registries, and add or remove plugins at run time through a controller framework at a remote location.
|
Sr No. |
Indicator | Type | Remarks |
|
1 |
5f3093473ae4167fd51d4282fce73741 |
MD5 Hash |
Main File |
| 2 | 8fdf8e4ecff114c1e6c9827c53742a1 | MD5 Hash | OLEVIEW.exe/wsuhost.exe |
| 3 | ad82d23accb10b4c0fc7f8c9782ae6ad | MD5 Hash | Embedded IVIEWERS.dll |
| 4 | 84d9d5cae48242e3a2ae838dc31e96a4 | MD5 Hash | Dropped IVIEWERS.dll |
| 5 | f7ef194f2dcc341ba03f76872cb7c0dfbae8f79118f99cf73dfccfb146c4e966 | SHA256 Hash | Main File |
| 6 | 2e642afdd36c129e6b50ae919ca608ac0006ce337f2a5a7a6fb1eef6a4ad99e7 | SHA256 Hash | OLEVIEW.exe/wsuhost.exe |
| 7 | 1e06fd5b9aa0e5260369e52ec2d9f87060941de835234afd198b1d4c0b161678 | SHA256 Hash | Embedded IVIEWERS.dll |
| 8 |
9494a3d8296002a0d2f9473fbace9edb5639c60168bf2e12077d8513ba9ba20f |
SHA256 Hash | Dropped IVIEWERS.dll |
| 9 | C:\Users\%UserName%\AppData\Local\Temp | Path | Dropped File OLEVIEW.exe |
| 10 | C:\Windows\System32\wsuhost.exe | Path | File wsuhost.exe |
| 11 | C:\Windows\System32\IVIEWERS.dll | Path | IVIEWERS.dll |
| 12 | http[:]//fljhcqwe[.]com:80 | URL | C2 Communication |
| 13 | c:\users\administrator\source\repos\consoleapplication6\x64\release\consoleapplication6.pdb | Path |
PDB Path |
| Sr No. | Tactic | Technique |
| 1 | Privilege Escalation (TA0004) | T1055 Process Injection |
| T1055.001 DLL Injection | ||
| 2 | Defense Evasion (TA0005) | T1027 Obfuscation Files or Information |
| T1112 Modify Registry | ||
| T1055 Process Injection | ||
| T1055.001 DLL Injection | ||
| 3 | Discovery (TA0007) | T1057 Process Discovery |
| T1082 System Information Discovery | ||
| T1124 System Time Discovery | ||
| 4 | Command & Control (TA0011) | T1071.001 Web Protocols |
| 5 | Exfiltration (TA0010) | T1029 Scheduled Transfer |