



At CYFIRMA, we provide timely insights into prevalent threats and malicious tactics affecting organizations and individuals. Our research team recently identified a binary in the wild, identified as an information stealer; “SamsStealer”. It is a 32-bit Windows executable designed to stealthily extract sensitive information from victims’ systems. Written in .NET, this malware targets a wide range of browsers and applications, including Discord, Chrome, and Microsoft Edge, to steal passwords, cookies, and cryptocurrency wallet data. After gathering the desired data, it compresses it into a ZIP archive, uploads it to an online file-sharing service, and sends the download link via Telegram to the attacker. With its stealthy operation and comprehensive data exfiltration capabilities, the stealer poses a significant threat to users’ privacy and security.
“SamsStealer,” represents a new wave of information stealers targeting Windows systems. This malicious executable, written in .NET, has been observed propagating in a Telegram channel named “SamsExploit”. The information stealer exhibits behaviour designed to covertly extract sensitive information from victims’ computers. In this report, we provide an in-depth analysis of the malware, examining its characteristics, execution flow, targeted browsers and applications, stolen information, cleanup and exfiltration methods, and communication channels. By understanding the modus operandi of this malware, we aim to equip users and security professionals with the knowledge needed to detect, mitigate, and protect against this evolving cyber threat.
The CYFIRMA research team is dedicated to continuously investigating evolving threats, malware, and the Tactics, Techniques, and Procedures (TTPs) employed by malicious actors. We actively monitor current threats, track ongoing campaigns, assess their progression, and stay vigilant for new developments in this dynamic landscape. Building on these efforts, we have recently identified a new information stealer circulating freely in the threat landscape, with its latest version, V2, being distributed via a Telegram channel with the name “SamsExploit”.
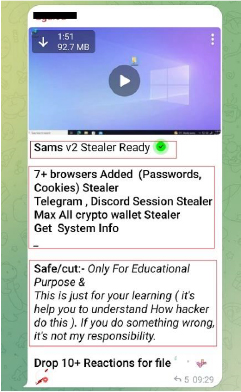
Enhanced Capabilities and Regional Origins of SamsStealer:
The latest version, V2, claims to enhance its capabilities by targeting an additional 7 browsers to steal passwords and cookies, as well as Telegram, Discord, and cryptocurrency wallets. Additionally, like many freely available tools, the author asserts that this stealer is intended for educational purposes—a common disclaimer seen on platforms like Telegram and GitHub when distributing such malware, but often customized and exploited for malicious purposes by seasoned cybercriminals and threat actors. The group’s users predominantly speak Hindi, suggesting their origin is likely from South Asia, particularly India.
It is a common practice within the cybercrime community to reuse and rebrand info stealers. Criminals often acquire existing info stealers, customize them for their own purpose and add specific features to target specific victims or suit their particular modus operandi. This approach saves time and resources while leveraging the expertise of other cybercriminals. Info stealers are not only favored by seasoned cybercriminals but are also popular among less sophisticated attackers. These tools provide an accessible entry point for beginners to learn about malware deployment and data exfiltration techniques. The ease of use and availability of pre-configured options make them an attractive choice for those new to cybercrime, allowing even novice hackers to execute effective attacks and such freely available malware always pose a threat to individuals and organizations.
OSINT Investigation Reveals Multiple SamsStealer Samples:
As per OSINT investigation, we have identified many samples of SamsStealer submitted online since April 24.
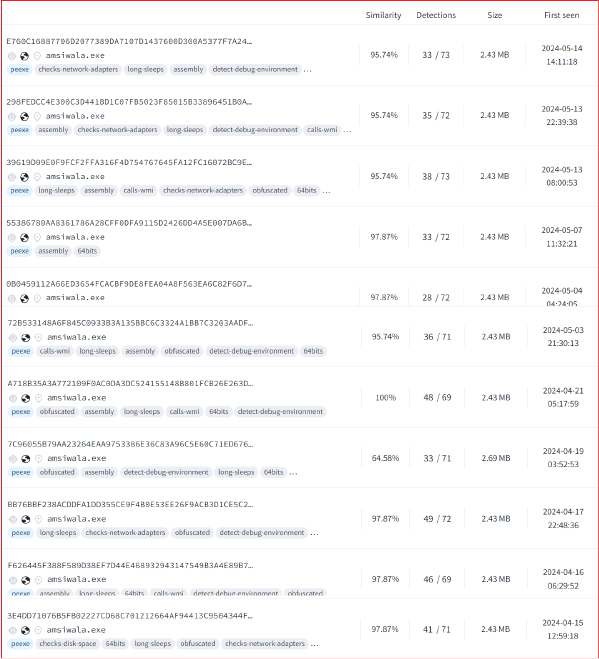
The Proliferation of Info Stealers in Cybercrime:
In the space of cybercrime, info stealers have become increasingly prevalent. These malicious tools are designed to covertly steal sensitive data from unsuspecting individuals and organizations. They are readily available for purchase on underground online forums and Telegram channels, making them a popular choice among cybercriminals due to their affordability and effectiveness in breaching computer systems.
Given the growing demand for info stealers, it is crucial for organizations to implement robust cybersecurity measures to safeguard their systems and data. Regular updates, strong passwords, multi-factor authentication, and comprehensive endpoint security solutions are essential tools in combating these cyber threats.
Basic Details:
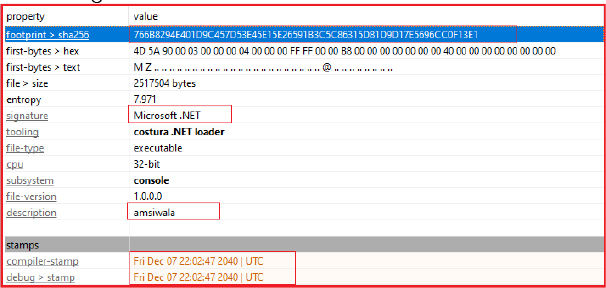
MD5: 83f94302ae92909bc3b2834a5342d4a5
SHA256: 766b8294e401d9c457d53e45e15e26591b3c5c86315d81d9d17e5696cc0f13e1
File Type: Win32 EXE
Basic Info:
The information stealer binary is a 32-bit Windows executable, written in .NET, and the name in the description given as “amsiwala”. However, the malware is propagated as “SamsStealer” in a Telegram channel.
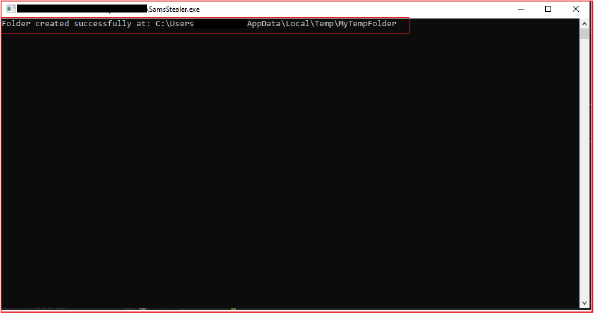
Upon execution, the stealer creates a temporary folder “MyTempFolder” in the system’s temporary directory “C:\Users\Username\AppData\Local\Temp\”.
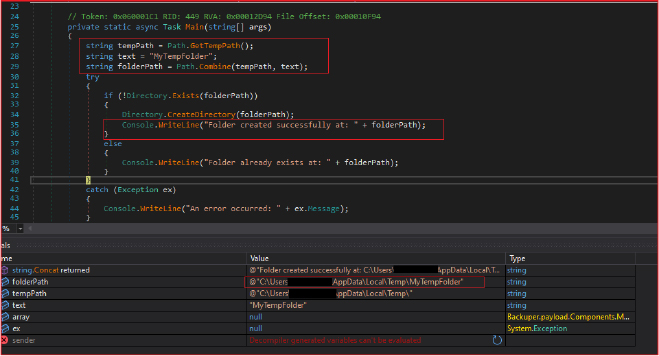
If the folder is created successfully, it notifies the console. It later hides the console window before executing the rest of the code.
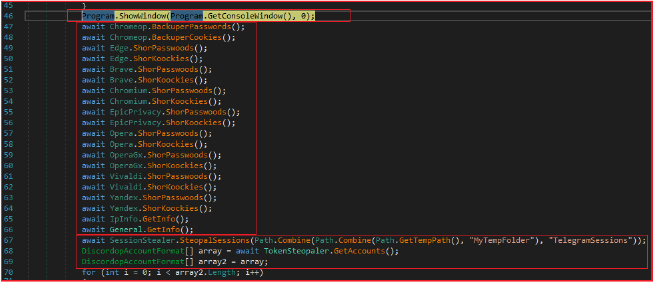
Information Gathering:
The malware makes asynchronous calls to methods to steal passwords and cookies from these respective browsers. It gathers IP and general system information, steals session information from messaging applications like Telegram, it retrieves Discord account information, steals wallet information, and saves it in the temporary folder created earlier and later exfiltrates the data.
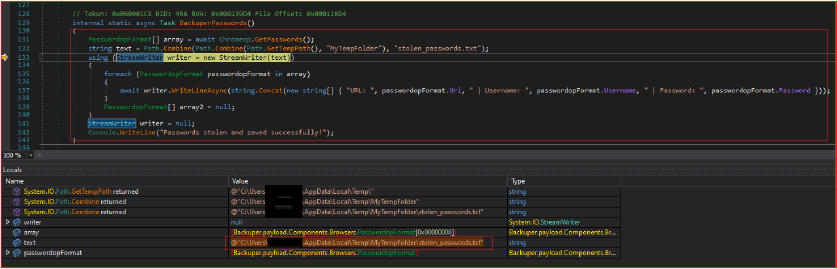
The malware steals passwords from Chrome, formatting it, and storing it in a text file within the previously created temporary folder. It retrieves an array of Passwords along with their associated URLs and usernames. Further, it prints a success message to the hidden console indicating that passwords have been stolen and saved successfully.
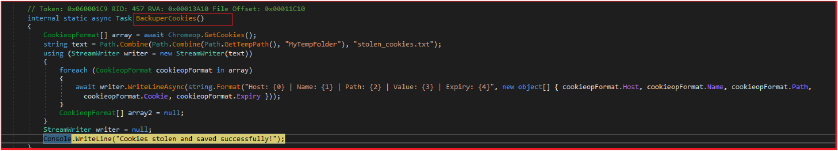
The stealer further operates similarly to the password-stealing operation but focuses on stealing and saving cookies from the Chrome browser. These cookies may contain sensitive session information, potentially allowing unauthorized access to various online accounts.
Similar to the above operations, the stealer targets the Microsoft Edge browser for password and cookie theft. The stolen passwords and cookies are saved to a text file within the temporary folder. Further, the stealer retrieves passwords and cookies from other browsers including Brave, Chromium, EpicPrivacy, Opera, gaming browser OperaGx, Vivaldi, and Yandex.
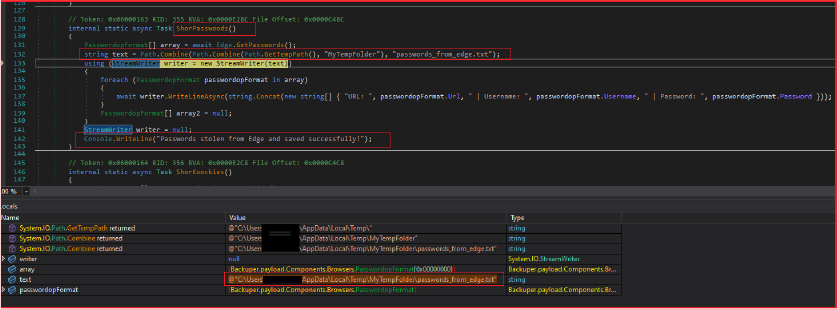
Geolocation and IP Identification:
It makes an HTTP GET request to the URL “http[:]//ip-api[.]com/json/?fields=225545” to fetch information about the current IP address
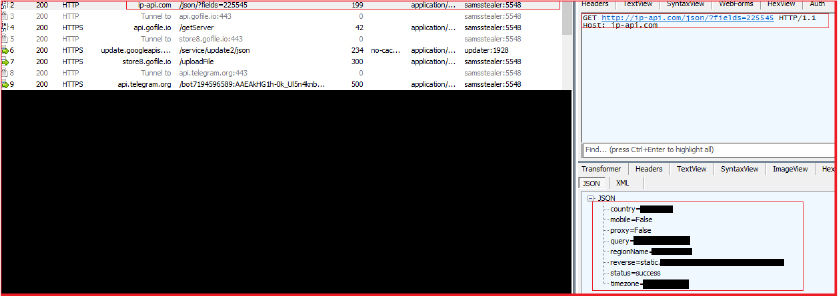
The response is deserialized into an object. The stealer then extracts various pieces of information from the deserialized object, such as country, region name, timezone, reverse DNS, mobile status, proxy status, and the queried IP address. It does this by accessing specific fields in the deserialized object. This functionality is used for purposes such as geolocation and IP identification.
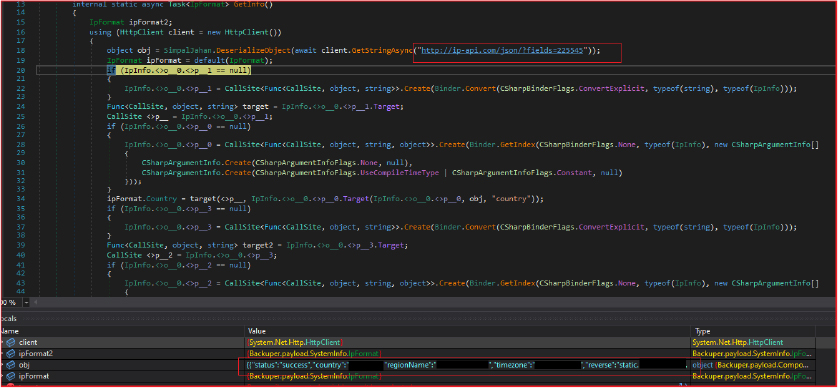
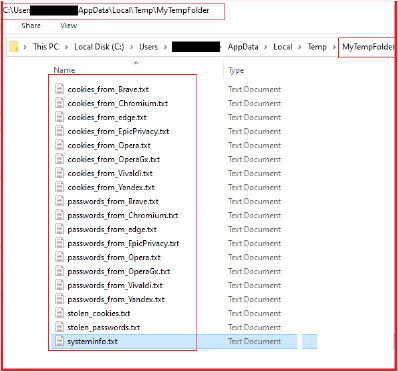
Storing Files in the “MyTempFolder” Directory:
The following are the files with different names stored in the earlier created folder in the Temp directory with the name “MyTempFolder”. It contains extracted information from various browsers, cookies, passwords wallets, and system information.
Targeting Telegram:
The stealer is designed to steal session data from the Telegram Desktop application. To steal session data from the Telegram Desktop application running on the victim’s system, it first identifies relevant files and directories associated with Telegram sessions, copies them to a temporary folder created earlier, and compresses them into a zip file. The operation aims to gain unauthorized access to Telegram accounts and extract sensitive information, such as messages and contact lists, for malicious purposes.
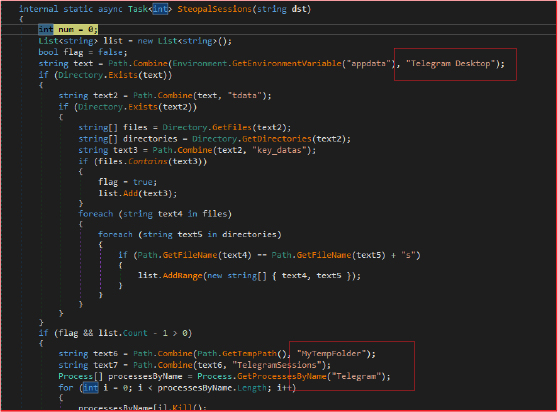
Targeting Discord and Browser Tokens:
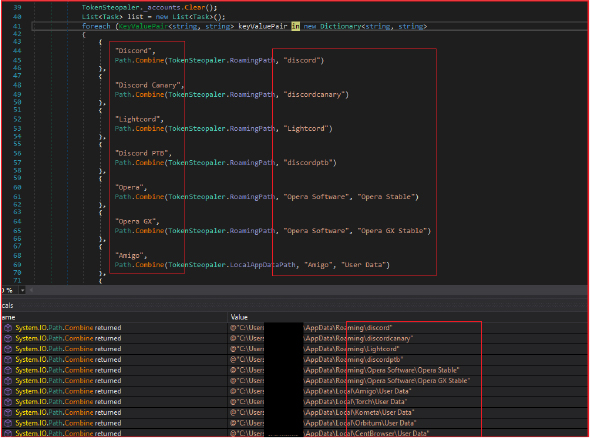
The stealer facilitates the stealthy extraction of account tokens from multiple applications and browsers installed on the victim’s system. By targeting a diverse range of software, including messaging platforms like Discord, and browsers like Chrome, Firefox, and Opera, among others, the malware aims to gather sensitive information that could be exploited for unauthorized access or further malicious activities. It leverages concurrency to enhance efficiency.
Applications and browsers targeted are Discord, Discord Canary, Lightcord, Discord PTB, Opera, Opera GX, Amigo, Torch, Kometa, Orbitum, CentBrowse, 7Sta, Sputnik, Vivaldi, Chrome SxS (Canary), Chrome, FireFox, Epic Privacy Browser, Microsoft Edge, Uran, Yandex, Brave, and Iridium.
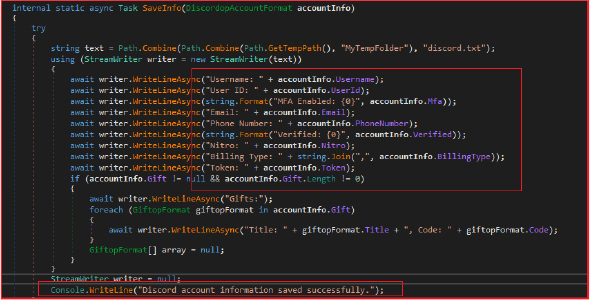
The stealer collects and saves Discord account information to the text file. This includes various details such as username, user ID, authentication status, contact information, subscription status, billing details, and account token.
Stealing Crypto Wallet Data:
The stealer also aims at stealing cryptocurrency wallet data. By systematically locating and copying wallet contents from predefined paths, it enables the malware to acquire valuable information necessary for unauthorized access to cryptocurrency holdings.
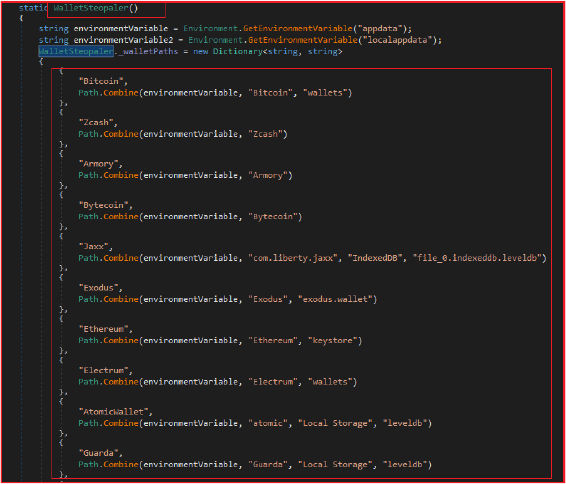
It identifies various types of cryptocurrency wallets such as Bitcoin, Ethereum, Zcash, etc., by their known default paths. By copying the contents of these wallets to the designated location, the malware gains access to private keys, wallet addresses, and other sensitive information crucial for accessing and controlling cryptocurrency assets.
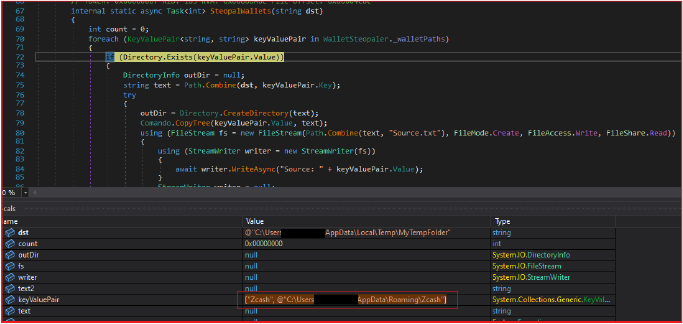
Finally, it returns the count of successfully copied wallets. Following cryptocurrency wallets are targeted by the stealer.
Cleanup Operation:
After stealing and retrieving all information from the victim machine, the stealer stores the data in a text file in the “MyTempFolder” and later performs cleanup operations by removing empty text files (0KB size). This functionality is useful not only for preventing clutter caused by empty or unnecessary files but also to optimize the data exfiltration efforts by reducing the volume of unnecessary files.
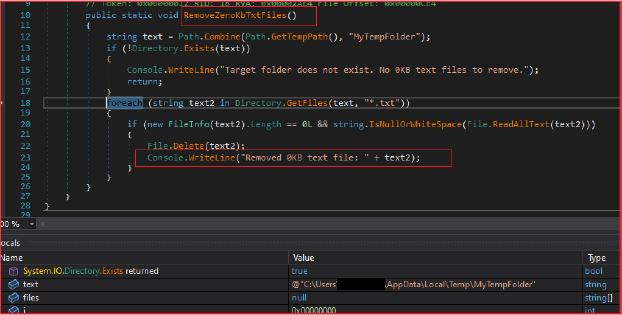
Data Compression and Exfiltration Process:
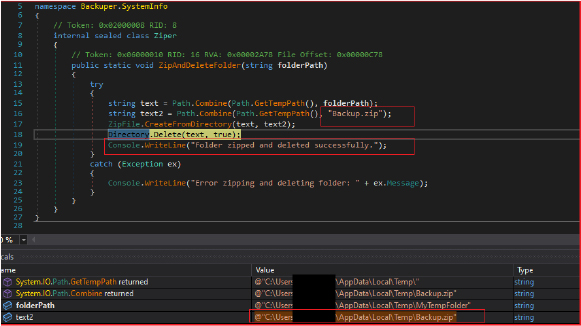
The stealer then compresses the “MyTempFolder” folder which contains all the extracted data from the victim’s machine into a ZIP archive, saves the zip file with the name “Backup.zip” at path “C:\Users\Username\AppData\Local\Temp\” and then deletes the original folder “MyTempFolder”. Finally, it logs a message confirming the successful zipping and deletion of the folder.
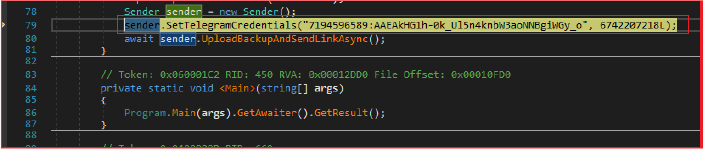
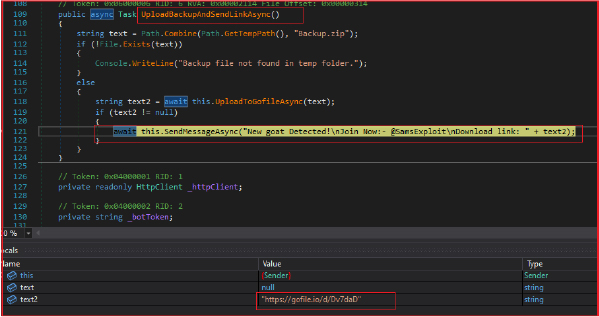
The stealer then uploads the “Backup.zip” file to the free online file-sharing service “gofile.io” and sends the download link via the messaging service “Telegram” to the attacker. It initializes an instance of HttpClient for HTTP requests and sets the bot token and chat ID required for sending messages via Telegram.
It checks if the backup ZIP file exists in the temporary folder. If the file exists, it uploads it to “gofile.io” and obtains the download link (highlighted in the below screenshot).
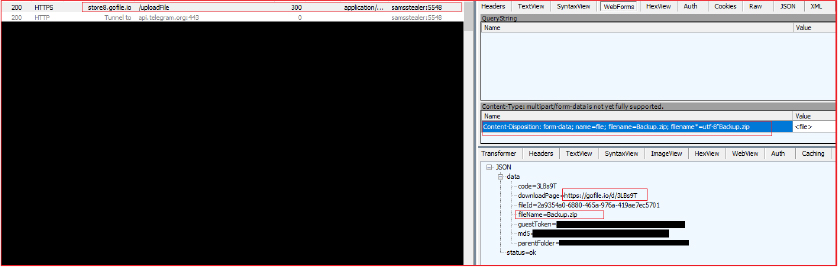
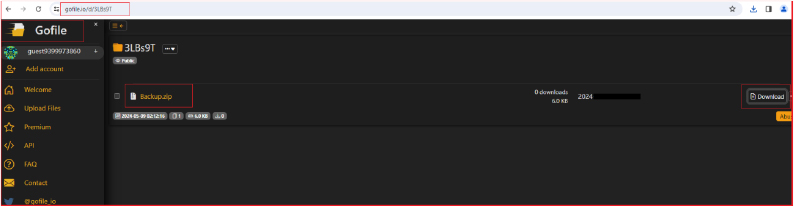
As shown below, the zip file “Backup.zip” is uploaded to the free online file-sharing service gofile.
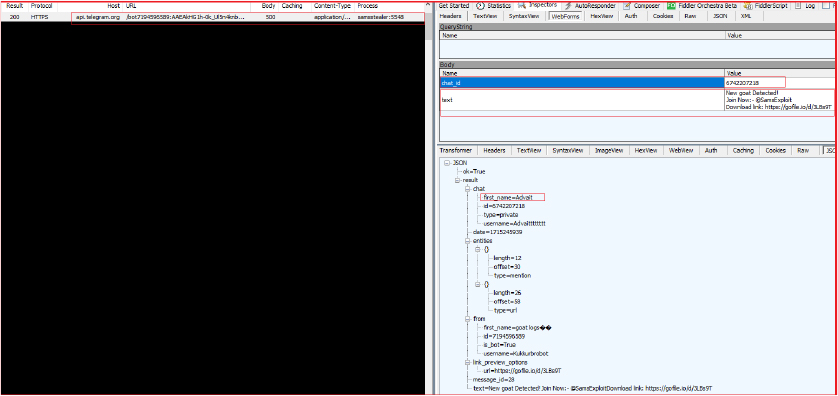
Upon successful upload, it sends the message:
New goat Detected
Join Now: @SamsExploit
Download Link: https[:]//gofile[.]io/xxxxx
to the specified Telegram chat ID with the zip file download link of the gofile service.
At Cyfirma, our commitment is to provide timely insights into prevalent threats and malicious tactics. Our recent identification of this new information stealer “SamsStealer” presents a significant threat to user privacy and security by stealthily extracting sensitive data from victim systems. Through its comprehensive approach, it targets a wide range of browsers, applications, and cryptocurrency wallets to gather passwords, cookies, session data, and cryptocurrency wallet information. Leveraging a combination of asynchronous operations, concurrency, and cleanup mechanisms, the malware efficiently collects and exfiltrates stolen data. By utilizing online file-sharing services like gofile.io and messaging platforms like Telegram for data transmission, the malware ensures seamless communication with its operators. As cyber threats continue to evolve, understanding the tactics and techniques employed by malware like SamsStealer is crucial for effective threat detection, mitigation, and prevention strategies.
As organizations and individuals navigate the increasingly complex threat landscape, it is imperative to remain vigilant and adopt proactive defense strategies informed by technical insights and analysis. Our ongoing research aims to provide timely intelligence and technical expertise to empower defenders in their efforts to safeguard against evolving cyber threats.
| Sr No. | Indicator | Type | Remarks |
| 83f94302ae92909bc3b2834a5342d4a5 | MD5 File Hash | SamsStealer | |
| 824e149b9c2bdd5dbe37f472533230af | MD5 File Hash | Other Sample | |
| 1f913f8d71f0f4d65858b5ba0ea94a9c | MD5 File Hash | Other Sample | |
| 56acc1496d8e5bbc0e412c683971b809 | MD5 File Hash | Other Sample | |
| 631eacb4519fd49048491c9b5ec6bda5 | MD5 File Hash | Other Sample | |
| 64410e06f80e75b6503e5525c323243b | MD5 File Hash | Other Sample | |
| 7d63047a48fa8984f11544149c2f0e70 | MD5 File Hash | Other Sample | |
| da493648ca3b8fd9dbad7bbca659b796 | MD5 File Hash | Other Sample | |
| 02fe599ed41cc4bd54a1d6a3cc2d830a | MD5 File Hash | Other Sample | |
| cb95c77750732c0a4dd29c1d4feb6f69 | MD5 File Hash | Other Sample | |
| 11751f8d847764936b7bf014302da87f | MD5 File Hash | Other Sample | |
| 31c73ad35b23e4d98ed974e604b85e00 | MD5 File Hash | Other Sample |
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing |
| T1566.001: Spear phishing Attachment | ||
| 2 | Execution (TA0002) | T1204: User Execution |
| T1204.002: Malicious File | ||
| 3 | Discovery (TA0007) | T1082: System Information Discovery |
| 4 | Collection (TA0009) | T1005: Data from Local System |
| 5 | Exfiltration (TA0010) | T1041: Exfiltration Over Command-and-Control Channel |
| T1567.003: Exfiltration to Text Storage Sites |
rule SamsStealer
{
meta:
description = “SamsStealer”
author = “CRT”
date = “18-05-2024”
strings:
$amsiwala = “amsiwala”
$guid = “f835a9e7-2542-45c2-9d85-ec0c9fdffb16”
$tempFolder = “MyTempFolder”
$backupPasswords = “BackuperPasswords”
$backupCookies = “BackuperCookies”
$shortPasswords = “ShorPasswoods”
$shortCookies = “ShorKoockies”
$stealSessions = “SteopalSessions”
$tokenStealer = “TokenSteopaler”
$walletStealer = “WalletSteopaler”
$stealWallets = “SteopalWallets”
$removeZeroKbTxtFiles = “RemoveZeroKbTxtFiles”
$telegramBotToken = “7194596589:AAEAkHG1h-0k_Ul5n4knbW3aoNNBgiWGy_o”
$stolenPasswords = “stolen_passwords.txt”
$stolenCookies = “stolen_cookies.txt”
$passwordsFromEdge = “passwords_from_edge.txt”
$cookiesFromEdge = “cookies_from_edge.txt”
$passwordsFromBrave = “passwords_from_Brave.txt”
$cookiesFromBrave = “cookies_from_Brave.txt”
$passwordsFromChromium = “passwords_from_Chromium.txt”
$cookiesFromChromium = “cookies_from_Chromium.txt”
$passwordsFromEpicPrivacy = “passwords_from_EpicPrivacy.txt”
$cookiesFromEpicPrivacy = “cookies_from_EpicPrivacy.txt”
$passwordsFromOpera = “passwords_from_Opera.txt”
$cookiesFromOpera = “cookies_from_Opera.txt”
$passwordsFromOperaGx = “passwords_from_OperaGx.txt”
$cookiesFromOperaGx = “cookies_from_OperaGx.txt”
$passwordsFromVivaldi = “passwords_from_Vivaldi.txt”
$cookiesFromVivaldi = “cookies_from_Vivaldi.txt”
$passwordsFromYandex = “passwords_from_Yandex.txt”
$cookiesFromYandex = “cookies_from_Yandex.txt”
$sourceTxt = “Source.txt”
$removedZeroKbTxtFile = “Removed 0KB text file”
$ipApiUrl = “http://ip-api.com/json/?fields=225545”
$backupZip = “Backup.zip”
$newGoatDetected = “New goat Detected!”
$samsExploitChannel = “@SamsExploit”
condition:
any of them
}