


As the festive shopping season approaches, Black Friday and Cyber Monday bring a significant surge in online sales and, with it, a sharp increase in cybercrime. Fraudsters exploit consumers’ urgency and retailers’ heightened online activity through phishing campaigns, fake websites, data breaches, and malicious advertisements. This report examines the evolving threat landscape surrounding these high-traffic retail events, the techniques used by cybercriminals, and how both consumers and businesses can protect themselves during this peak shopping period.
Black Friday and Cyber Monday have become global shopping phenomena, generating billions of dollars in online and in-store sales. While consumers eagerly search for discounts, cybercriminals capitalize on the opportunity to target unsuspecting victims.
The continued digital transformation of retail has introduced new shopping channels and new vulnerabilities, and threat actors now deploy increasingly sophisticated scams, including fake e-commerce platforms, deceptive social media promotions, and phishing emails impersonating trusted retailers. With the rising adoption of mobile commerce, digital wallets, and third-party payment solutions, attackers have more potential entry points than ever before.
The threat landscape surrounding Black Friday and Cyber Monday has evolved rapidly, with attackers now relying on more targeted and advanced tactics.
1. Proliferation of Fake Retail Websites and Mobile Apps
Cybercriminals develop counterfeit e-commerce websites and mobile applications that closely resemble legitimate brands, often advertising unrealistic discounts to entice users into sharing payment information or login credentials. Victims frequently receive counterfeit goods—or nothing at all.
2. Phishing and Smishing Campaigns
Attackers send convincing emails or SMS messages impersonating well-known retailers and delivery services. These messages urge recipients to confirm orders, resolve account issues, or claim rewards, ultimately leading them to malicious websites designed to steal credentials or financial information.
3. Malvertising and Fake Social Media Promotions
Malicious advertisements placed on search engines and social media platforms redirect users to malware-laden or credential-harvesting pages. These ads often mimic legitimate discount offers.
4. Supply Chain and Vendor Exploitation
Retailers often rely on various third-party vendors for logistics, payment solutions, and marketing. Threat actors increasingly target these external partners to infiltrate larger networks, exfiltrate customer data, or deploy ransomware campaigns.
5. Mobile and Payment System Exploitation
As consumers shift to mobile commerce, attackers exploit vulnerabilities in QR codes, digital wallets, and payment applications. Fake shopping apps—especially those distributed through unofficial app stores—continue to rise.
6. Gift Card Scams
Gift cards remain highly attractive to scammers due to their anonymity and rapid cash-out potential. Attackers impersonate employers, retailers, or acquaintances to pressure victims into purchasing gift cards and sharing the codes.
Holiday seasons significantly increase consumer activity, giving cybercriminals an expanded window to deploy malicious campaigns.
Although Cyber Monday and Black Friday are yet to begin, CYFIRMA researchers have already identified multiple malicious websites designed to impersonate legitimate sales promotions. These domains exploit the excitement surrounding festive season discounts to lure victims into phishing traps.
Below are a few examples of phishing websites that have been created for the black Friday sale.
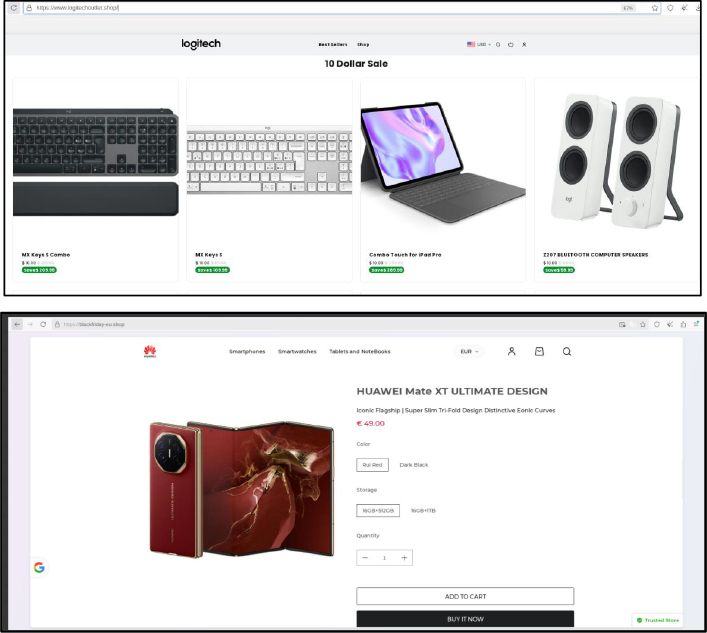
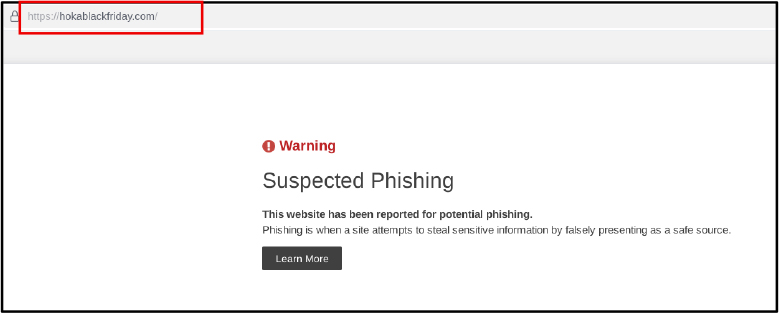
In addition to fraudulent websites, researchers observed attackers distributing ZIP files that automatically download when users visit certain malicious pages. Upon investigation, the ZIP file contained a document referencing kitchen items and a suspicious cgi-bin directory.
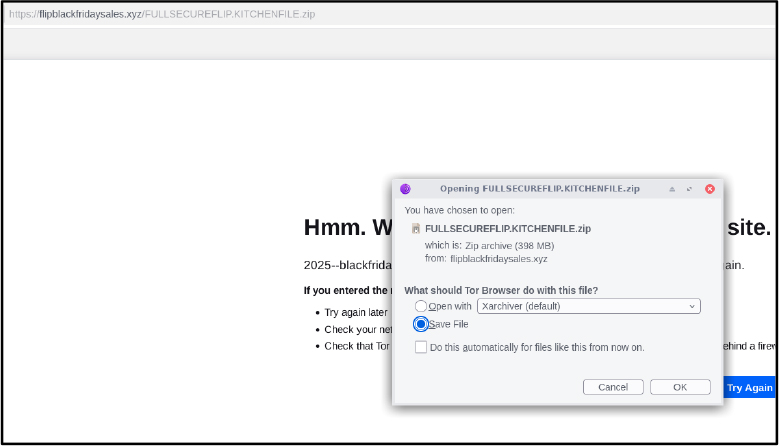
This behavior indicates the following:
1. Suspicious or Compromised Server
2. Possible Drive-by or Social Engineering Attack
3. Potential Indicators of a Web Shell
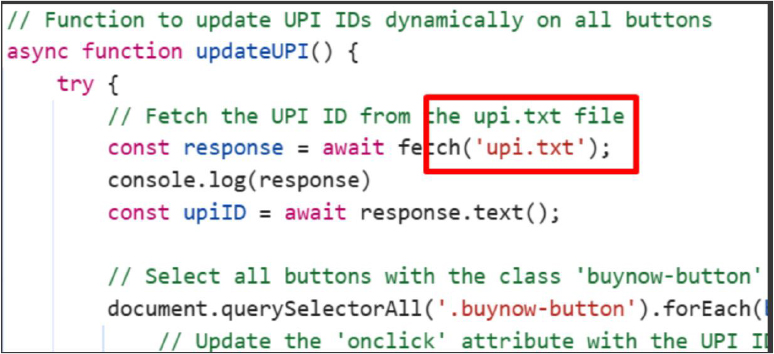
Further analysis revealed a large collection of fake phishing websites created within the folder structure. When users attempted to purchase items, they were redirected to a UPI-based payment page.

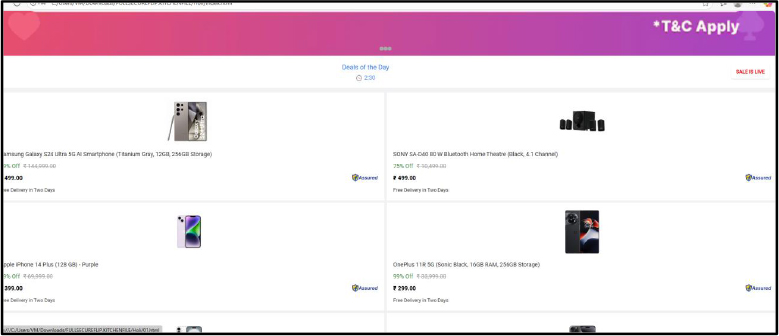
The code used on these scam sites retrieves a fraudster’s UPI ID from a separate upi.txt file. This allows the attacker to change the UPI ID dynamically without updating the entire website, making detection and takedown more challenging.
Below is the observed scammers’ UPI ID,

The “netc.” prefix in a UPI handle is typically associated with FASTag and toll-payment systems, not regular person-to-person transactions. Although such IDs can appear during system testing or internal automated operations, scammers may also exploit similar autogenerated handles to mask their real identity. By using these system-style or dynamically generated UPI IDs, scammers can effectively evade identification, making victims believe they are interacting with a legitimate source.
Furthermore, although this particular UPI ID is currently inactive, such IDs can still be used to trick victims during the active scam window. Scammers often activate these autogenerated handles temporarily, use them to collect funds, and then deactivate or abandon them to avoid tracing.
As scammers increasingly develop sophisticated phishing panels, fake payment pages, and automated redirection mechanisms (such as those observed in the malicious UPI-based payment flows), much of this infrastructure is now being sourced, customized, or supported through underground cybercriminal marketplaces. Dark web forums and Telegram groups have become central hubs where threat actors can easily access phishing kits, web templates, UPI fraud modules, credential-stealing scripts, and pre-configured admin panels.
The rise of Phishing-as-a-Service (PhaaS) has significantly lowered the technical entry barrier, enabling even low-skilled attackers to rapidly deploy professional-looking phishing websites. These services provide ready-made templates, hosting support, automated management dashboards, and continuous updates, allowing cybercriminals to scale their campaigns with minimal effort. As a result, the phishing infrastructure observed in this year’s festive shopping scams reflects a broader trend: attackers no longer need to build tools from scratch—most of the components they use are purchased or rented through these underground ecosystems.

The festive shopping season presents a lucrative opportunity for cybercriminals, who exploit increased consumer spending and high online traffic to launch targeted attacks. As the sophistication and accessibility of cybercrime tools continue to grow, both consumers and organizations must remain vigilant.
Proactive cybersecurity measures, awareness training, and robust monitoring are essential to mitigating the risks associated with seasonal cyber threats.
| S.No | Indicator | Remarks |
| 1 | hokablackfriday[.]com | Malicious |
| 2 | 2025blackfriday[.]com | Malicious |
| 3 | blackfriday-eu[.]shop | Malicious |
| 4 | logitechoutlet[.]shop | Malicious |
| 5 | hXXps://flipblackfridaysales[.]xyz/FULLSECUREFLIP.KITCHENFILE.zip | Malicious |
| 6 | 2025zhclblackfriday[.]shop | Malicious |
1. Verify Legitimacy of Websites and Apps
Both consumers and retailers should ensure shopping sites, payment pages, and mobile apps are legitimate. Consumers must avoid suspicious URLs, while retailers should monitor and remove spoofed domains or fake apps impersonating their brand.
2. Strengthen Payment Security and Avoid Unverified Methods
Consumers should use secure, recognized payment gateways instead of UPI links or QR codes on unknown sites. Retailers must protect their payment workflows from manipulation, ensuring no external scripts or TXT-based payment IDs can be injected.
3. Avoid Downloading Unknown Files or Attachments
Attackers often distribute malicious ZIP files disguised as order updates or catalogues. Consumers should avoid downloading unknown files, and retailers should filter or block suspicious attachments using email/web security tools.
4. Enhance Identity and Account Protection
Both groups should enable multi-factor authentication (MFA) across email, banking, and retail platforms to prevent unauthorized access caused by phishing or credential theft.
5. Monitor for Fraudulent Activity
Consumers should regularly check bank and payment alerts, while retailers must monitor their networks, customer transactions, and threat intelligence feeds to detect unusual activity and fraudulent payments.
6. Raise Awareness About Seasonal Phishing Scams
Consumers should stay informed about festive scam trends, and retailers should proactively educate their customers and employees about fake sale sites, phishing emails, and UPI-based fraud campaigns.
7. Secure Third-Party and Supply Chain Integrations
Retailers should assess the security of payment processors, logistics partners, and marketing vendors—common attack paths during festive seasons—while consumers should avoid interacting with unknown or redirected payment platforms.
8. Monitor Underground Marketplaces for Threat Indicators
Organizations should track dark web and Telegram channels for phishing kits or cloned brand templates, and consumers should stay cautious of deals circulating on unofficial platforms known to be exploited by scammers.