

In this report, our researchers analyzed recent cyber activity targeting Bahrain, including politically motivated hacktivism, credential leaks, government email breaches, and ransomware incidents. Key events ranged from Anonymous Vietnam’s disruption of critical national websites in December 2023 to data sales by BIGBROTHER and ShinyHunters in mid-2025, alongside ransomware attacks on private firms, such as Bin Faqeeh Real Estate. Rising domestic unrest and Bahrain’s alignment with Israel have amplified hacktivist narratives, while credential dumps and initial-access sales highlight risks of account takeover and rapid escalation into ransomware or state-linked operations.
The authenticity of the breaches below remains unverified at the time of reporting, as the claim originates solely from threat actors.
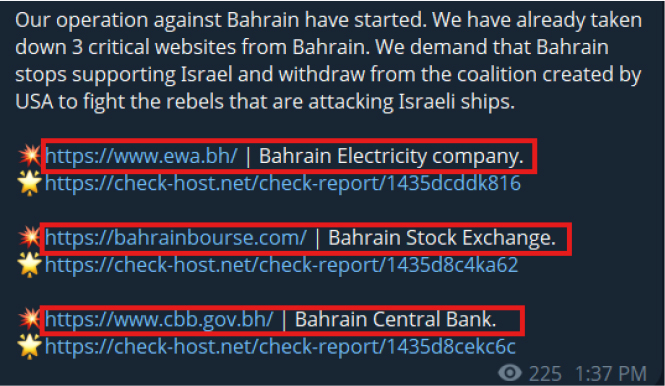
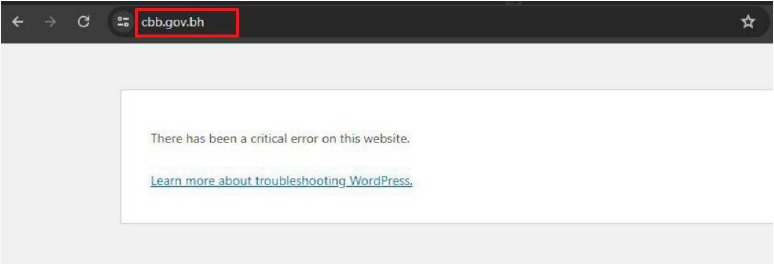
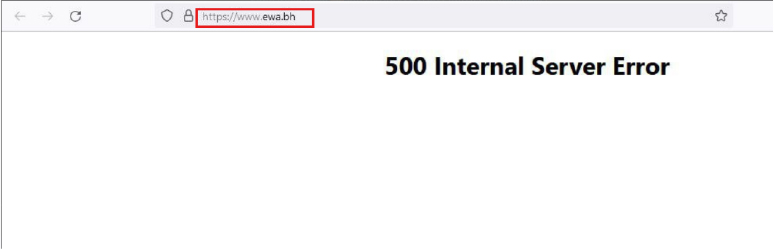
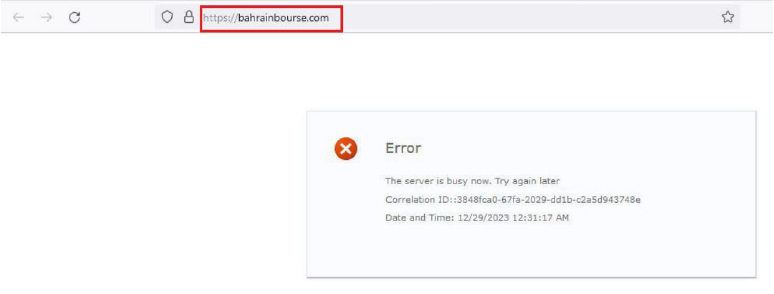
On 29-Dec-2023, threat actor Anonymous Vietnam conducted an attack against Bahrain, claiming responsibility for disrupting three critical national websites: Bahrain Electricity Company (ewa.bh), Bahrain Stock Exchange (bahrainbourse.com), and the Central Bank of Bahrain (cbb.gov.bh), citing Bahrain’s support for Israel and its participation in a U.S.-led coalition as the motive. This activity was later reposted on the Telegram channel Raidforums | Discussion on 28-Oct-2024 and again on 19-Jan-2025, indicating continued amplification of politically motivated hacktivist narratives targeting Bahrain.
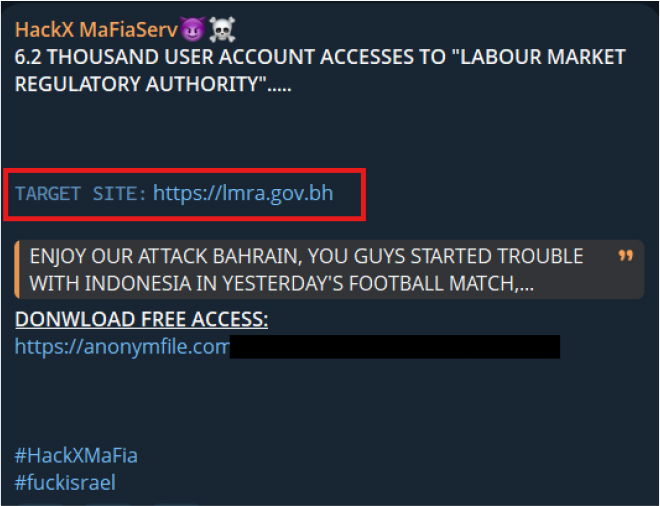
On 28-Oct-2024, threat actor HackX MaFiaServ posted on Telegram, claiming access to 6.2k user accounts from Bahrain’s Labour Market Regulatory Authority (lmra.gov.bh), along with a credential dump link, allegedly motivated by political tensions and a football-related dispute. The attack suggests credential harvesting and data exfiltration, posing risks of account takeover and information leakage. At the time of validation, the shared file was inaccessible.
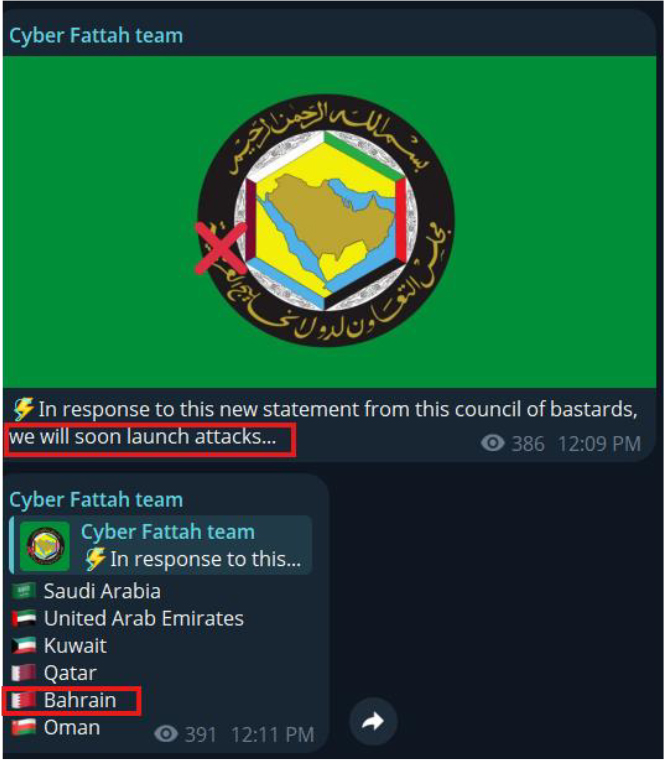
On 02-Sep-2025, the threat actor Cyber Fattah team posted on Telegram announcing plans to launch cyberattacks in response to political developments, explicitly listing Bahrain among their intended Gulf targets. The messaging indicates forthcoming hacktivist activity aimed at the disruption of critical infrastructure and government services, with a likely focus on DDoS, defacement, or data exposure operations.
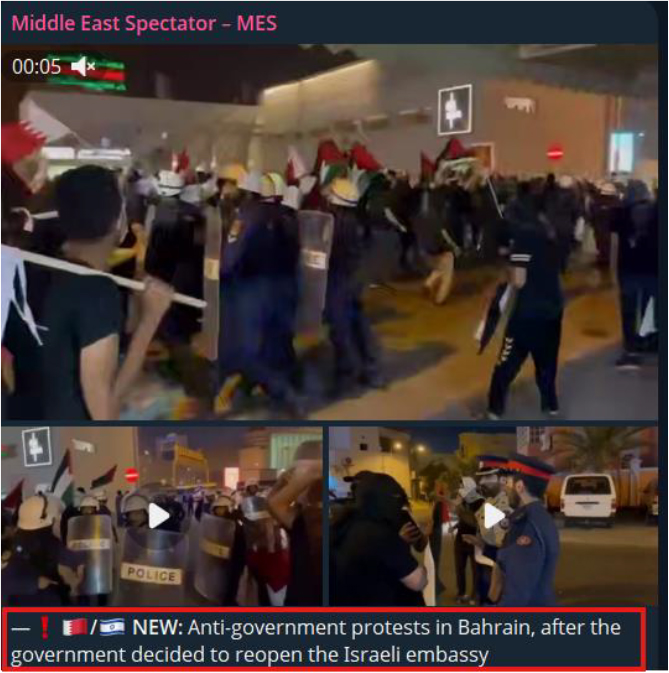
On 02-Sep-2025, the Telegram channel Middle_East_Spectator reported anti-government protests in Bahrain following the government’s decision to reopen the Israeli embassy. The development highlights growing domestic unrest linked to Bahrain’s geopolitical alignment with Israel, which could fuel hacktivist narratives and cyber operations targeting national institutions. This intersection of political tensions and cyber activism raises the likelihood of increased attacks against government, financial, and critical infrastructure assets in Bahrain.
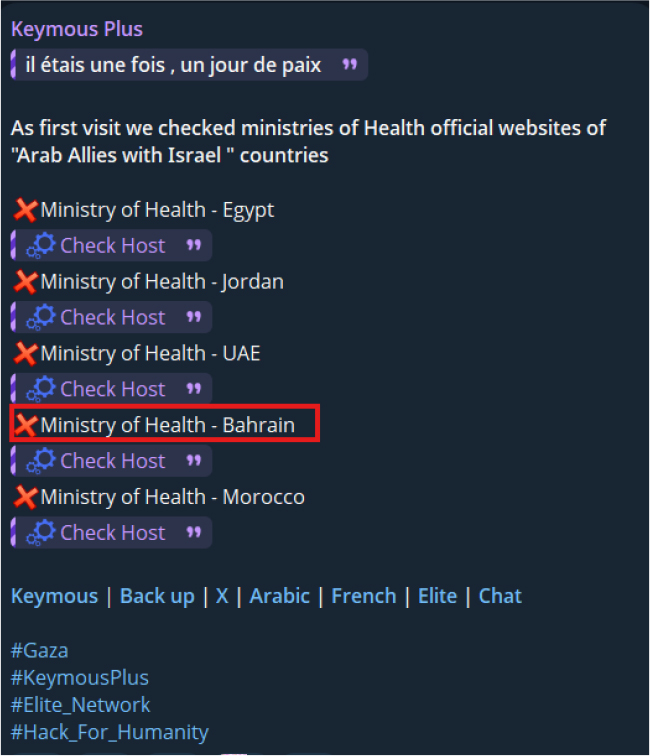
On 26-Aug-2025, the threat group Keymous Plus posted (and ANONSEC 16 reposted) claims of probing the Ministry of Health of Bahrain, as part of broader reconnaissance targeting Arab countries allied with Israel. The activity indicates preliminary scanning and availability testing, suggesting potential for DDoS, defacement, or credential-harvesting operations, although no active exploitation was confirmed at the time. Multiple Telegram/X channels were shared to distribute updates and coordinate within the threat actor network.
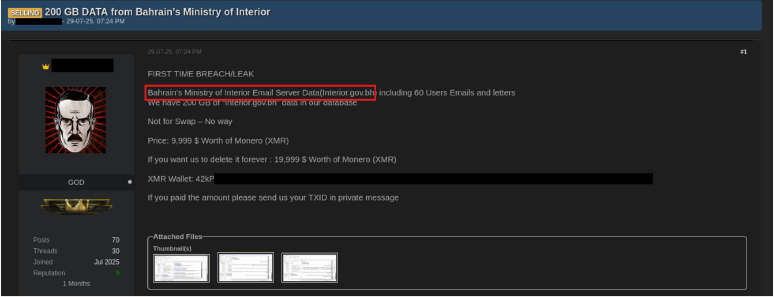
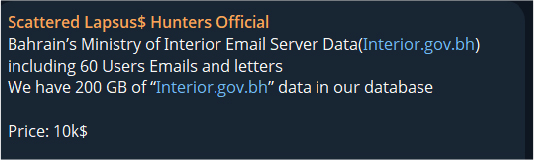
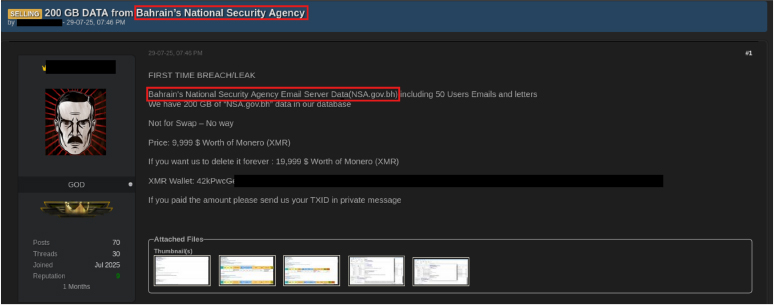
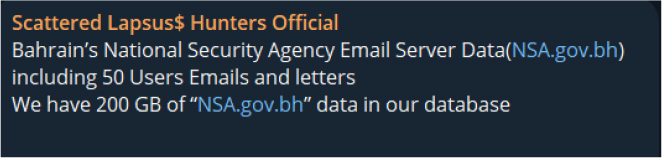
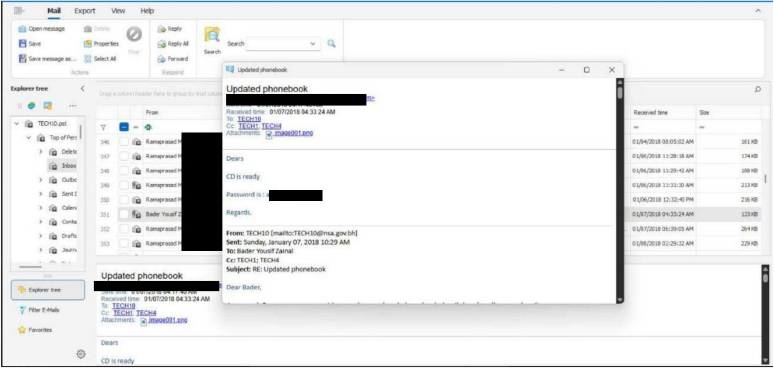
On 29 July 2025, a threat actor using the alias BIGBROTHER claimed the first breach/leak of Bahrain’s Ministry of Interior email server (Interior.gov.bh). The actor alleged possession of 200 GB of data, including emails and letters from 60 users, offering it for USD 9,999 worth of Monero (XMR). An additional option was proposed for USD 19,999 in XMR to “delete the data forever,” underscoring a double-extortion approach. The post, marked as “not for swap,” included a Monero wallet address with instructions for buyers to provide their transaction ID (TXID) via private message. On 20 September 2025, the threat group ShinyHunters also claimed to have exfiltrated sensitive data from the Ministry of Interior (Interior.gov.bh), again referencing a 200 GB dataset affecting 60 users and pricing it at USD 10,000. This listing was initially circulated on the Scattered Lapsus$ Hunters Official Telegram channel and later amplified across underground forums and channels associated with ShinyHunters, BlackCat, Babuk, and Lapsus$. On the same date, ShinyHunters further claimed to have compromised the National Security Agency (NSA.gov.bh), exposing 200 GB of data from 50 users, which was also offered for USD 10,000. Collectively, these disclosures highlight a wave of coordinated, financially motivated campaigns targeting Bahrain’s critical government infrastructure, with significant implications for both internal communications and national security.
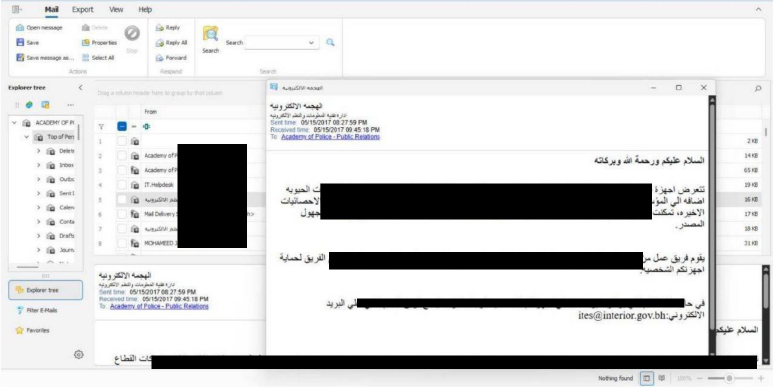
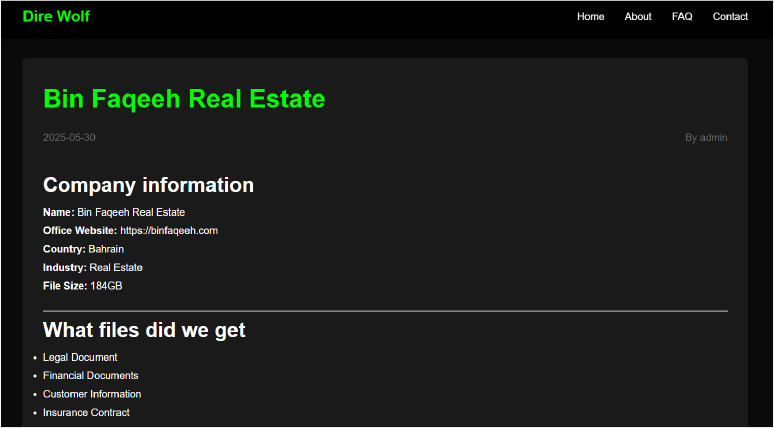
On 30th May 2025, the ransomware group Direwolf claimed responsibility for a major data breach targeting Bin Faqeeh Real Estate, a prominent property development company in Bahrain. The group reported exfiltrating approximately 184 GB of data, which included legal and financial documents, customer information, insurance contracts, claims history, business contracts, bank reconciliations, transactions and statements, accounting records, employment contracts, confidentiality agreements, and audit files. As part of their extortion process, Direwolf announced the release of sample files and a file list on 30th May 2025, followed by a plan to publish all documents on 18 June 2025 if their demands were not met. On 18 June 2025, the group followed through on its threat, publishing the full dataset on its leak site, thereby confirming the breach and exposing Bin Faqeeh’s sensitive corporate and customer information.
The cyber threat landscape around Bahrain is escalating, driven by a combination of politically motivated hacktivism, large-scale government email breaches, and ransomware campaigns. The amplification of anti-government narratives, coupled with Bahrain’s geopolitical alignment with Israel, increases the likelihood of disruptive attacks on national institutions and critical infrastructure. These trends show that Bahraini organizations face mounting risks from both financially motivated actors and ideologically driven hacktivists, with the added potential for state-linked operations to exploit regional instability.