



This report is Part 2 of a comprehensive analysis of ransomware activity in 2023. Part 1 covered major ransomware attacks, the top five prolific ransomware families since January 2023, and the geographical distribution of ransomware, whereas, this publication will delve into targeted industries, industrial trends analysis for H1-2022 and H1-2023, the ongoing evolution of ransomware attacks, notable new ransomware groups, the vulnerabilities exploited in 2023, and trends comparison between H1 2022 and H1 2023. By examining these themes, organizations can gain valuable insights into the evolving threat landscape and enhance their cybersecurity strategies to mitigate ransomware risks effectively.
Ransomware attacks continue to pose significant threats to organizations worldwide, causing severe financial and reputational damage. In the first half of 2023, a surge in ransomware activity has been observed, highlighting the need for heightened vigilance and proactive defense measures. This report aims to shed light on the key aspects of ransomware activity during this period, including the vulnerabilities exploited, industries targeted, geographic focus, and the emergence of new ransomware variants.
Understanding ransomware attack tactics, techniques, and trends is crucial for organizations to effectively mitigate risks, protect critical data, and ensure business continuity. By analyzing the ransomware landscape in the first half of 2023, this report aims to provide valuable insights that can empower organizations to strengthen their cybersecurity posture and stay ahead of evolving threats.
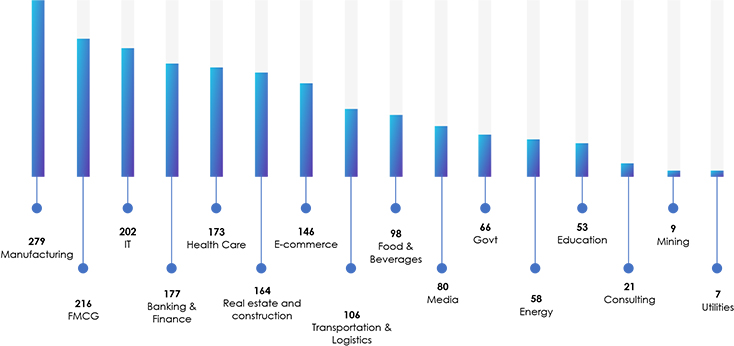
The report presents an overview of ransomware attacks from January 2023 to June 2023. The Manufacturing sector witnessed the highest number of incidents, reporting 279 attacks, followed by the Fast-Moving Consumer Goods (FMCG) sector with 216 attacks, with the IT industry reporting 202 incidents. The Health Care industry accounted for 173 victims, while the Banking and Finance sector faced 177 reported attacks.
Several factors contribute to the targeting of specific industries. Manufacturing may be targeted due to its reliance on operational continuity and potential vulnerabilities in industrial control systems, whereas, Healthcare is attractive due to the criticality of patient data, and the potential to disrupt essential services. The FMCG sector is targeted for its widespread consumer impact and potential supply chain disruptions, the IT industry is attractive due to its access to valuable data and networks, and Banking and Finance are targeted for their financial assets and sensitive customer information. The motives can include financial gains, disruption, theft of intellectual property, or leveraging data for future attacks.
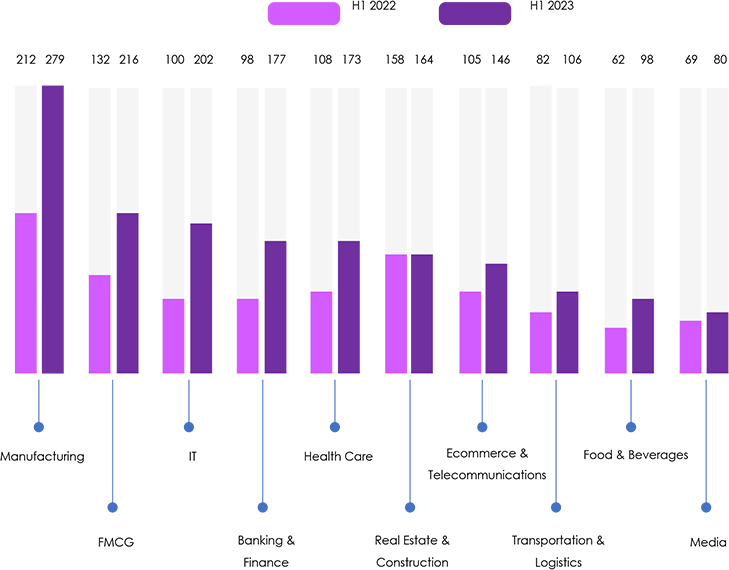
Compared to H1 2022, H1 2023 reveals an overall increase in ransomware attack victims, with FMCG experiencing a substantial 63.6% surge, and IT encountering a notable 102% increase. Banking and Finance faced a significant 80.6% rise, while Health Care saw a 60.2% upswing.
| Sr No | Ransomware | Updates |
| 1 | ALPHV/BlackCat |
|
| 2 | Play Ransomware | Two new custom software tools named Grixba and VSS Copying Tool developed |
| 3 | Vice Society | Automation of Data Theft. |
| 4 | Royal | Started Encrypting Linux OS. |
| 5 | LockBit |
|
In February 2023, the BlackCat group introduced a new version called Sphynx, aimed at enhancing their evasion capabilities. This iteration includes various enhancements to strengthen their tactics against detection. One notable change is the replacement of a specific parameter with a more complex set of arguments, posing a greater challenge for detection, as defenders can no longer rely on standardized commands, making it harder to identify and combat the ransomware effectively.
In May, researchers made a significant discovery concerning the ALPHV Ransomware Group. The group employed signed malicious Windows kernel drivers to bypass security software detection. The malware, named ‘POORTRY,’ had been previously detected in ransomware attacks by Microsoft, Mandiant, Sophos, and SentinelOne. To evade detection, the hackers created an improved version of the POORTRY driver, signing it with a stolen or leaked cross-signing certificate, after the original Microsoft-signed driver’s code-signing keys were revoked due to extensive publicity. With this updated driver, the hackers could elevate their privileges on compromised machines and disable security agents, enabling them to execute their malicious activities without raising suspicion.
In April, Researchers observed the Play ransomware group creating two custom software tools using .NET framework, called ‘Grixba’ and ‘VSS Copying Tool’, which they utilize to enhance the efficiency of their cyberattacks.
Grixba is a network-scanning tool used for identifying users and computers within a domain. It leverages the Costura framework, a popular .NET development tool that allows developers to package application dependencies into a single executable file. The “costura.commandline.dll” DLL file, embedded by Costura, enables Grixba to parse command lines effectively.
The threat actors employ this .NET info stealer to enumerate software and services using various methods like WMI, WinRM, Remote Registry, and Remote Services. Once enumerated, the malware checks for the presence of security and backup software, remote administration tools, and other programs, collecting this valuable information. The collected data is then stored in CSV files, compressed into a ZIP archive, and finally sent to the attackers’ C2 server. This provides them with crucial insights to plan their next steps in the attack.
The VSS Copying Tool, developed using the Costura tool, embeds the AlphaVSS library, a .NET framework that facilitates interaction with the Volume Shadow Copy Service (VSS). This library simplifies VSS tasks for .NET programs by providing controlled APIs to generate, manage, and delete shadow copies, as well as access information about existing shadow copies. With AlphaVSS, the tool effectively copies files from VSS snapshots to a target directory, allowing attackers to access and copy files from VSS volumes on compromised machines, even when the operating system has them locked, before initiating encryption. This capability empowers the Play ransomware to steal files from existing shadow volume copies, even when those files are actively used by applications.
In early 2023, the Vice Society ransomware gang implemented an advanced PowerShell script to automate data theft from compromised networks. This new data exfiltrator operates seamlessly by utilizing “living off the land” binaries and scripts, ensuring that security software remains unaware of their activities. Before the final step of encrypting data, the script efficiently carries out data exfiltration through a series of functions such as Work(), Show(), CreateJobLocal(), and fill(). By employing these functions, the script scans for suitable directories, processes groups of directories, and ultimately exfiltrates the data via HTTP POST requests to the servers controlled by Vice Society.
Throughout its history, the LockBit operation has undergone various iterations of its encryptor. It started with a custom encryptor and later transitioned to LockBit 3.0 (also known as LockBit Black), which was derived from the source code of the BlackMatter gang.
In February 2023, a new encryptor named ‘LockBit Green’ emerged, revealing that it was based on the leaked source code of the disbanded Conti gang.
A noticeable change in LockBit Green is the utilization of a random extension instead of the typical .lockbit extension for encrypted files.
By April 2023, a significant milestone was marked as LockBit expanded its focus to target macOS systems, making it the first major ransomware operation to do so. This development represents a notable expansion in their target range and poses a heightened security threat to Mac users.
The MalasLocker is a ransomware group that started its operation at the end of March 2023, which encrypts files and appends a “This file is encrypted, look for README.txt for decryption instructions” message at the end of every encrypted file.
This ransomware operation has been targeting Zimbra servers, infiltrating them to steal emails and encrypt files. Surprisingly, instead of the typical ransom payment demands, the threat actors have taken a unique approach, claiming that in order to receive an encryptor and prevent data leakage, a donation to a specified charity is required. This unconventional demand introduces an element of humanitarianism, albeit, within the context of a criminal act.
At the time of this report’s publication, the ransomware had added 169 victims to its list.
Akira’s ransomware operation is targeting corporate networks globally. The ransomware’s peak function is not immediately after its launch in March 2023. Instead, it occurs at the end of April and in May 2023. The Group will add the file extension “.akira” to the encrypted files’ name during the encryption process. Upon encrypting the files on a computer, the ransomware generates a ransom note named “akira_readme.txt” in every folder, explaining the situation to the victim and providing links to the Akira data leak and negotiation sites. At the time of this report’s publication, the ransomware had added 76 victims to its list.
RA Group, a ransomware group, is rapidly spreading their C++-based ransomware by leveraging leaked Babuk ransomware source code. They employ double extortion tactics, threatening to expose stolen data unless victims pay the ransom or contact them within a specified timeframe. Upon activation, the ransomware places a personalized ransom note named “How To Restore Your Files.txt” on the victim’s computer and even includes the victim’s name in the executable itself, a unique approach. Encryption is done using curve25519 and hc-128 algorithms, targeting specific portions of files rather than the entire content. The ransomware appends the “.GAGUP” extension to encrypted files. It deletes Recycle Bin contents and utilizes vssadmin.exe to remove volume shadow copies. It scans logical drives and exploits APIs to encrypt files on network shares. As of now, ten victims have been identified.
Rhysida is a recently emerged ransomware family, written in C++. The team presents itself as a “cybersecurity team” aiming to assist their targets by identifying vulnerabilities in their systems and emphasizing the potential consequences of these security issues. Ransomware is employed through various means, with the primary methods being deployment via Cobalt Strike or a similar framework, as well as through the utilization of phishing campaigns.
The group adopts a similar approach to modern-day multi-extortion groups by coercively warning victims of potential public distribution of the exfiltrated data, aiming to pressure them into compliance. When executed, the ransomware initiates a cmd.exe window, scanning through all files on local drives. Once the files are encrypted, the ransomware appends the “.rhysida” extension to them. The ransom notes generated by the ransomware are created as PDF documents with the name “CriticalBreachDetected.pdf” and are saved within the affected folders on the targeted drives. At the time of this report’s publication, the ransomware had added 23 victims to its list.
NoEscape is an emerging ransomware group that has recently gained momentum. Written in C++, NoEscape operates as a prominent Ransomware-as-a-Service (RaaS) platform, catering to affiliates and customers in the criminal ecosystem. The ransomware builder interface provides extensive customization options, enabling affiliates to create personalized ransomware executables. The ransomware encrypts the files, appends a unique string of characters to filenames, and generates a ransom note file called “HOW_TO_RECOVER_FILES.txt.” NoEscape executes commands to delete shadow copies and system backups to hinder recovery efforts, eliminating potential restoration options.
| Sr No | CVE ID | CVSS Score | NAME | Affected Product | Associated Ransomware |
| 1 | CVE-2023-27350 | CVSS 9.8 | PaperCut MF/NG Improper Access Control Vulnerability | PaperCutMF: before 22.0.9; PaperCut NG: before 22.0.9 |
Bl00dy Ransomware, Cl0p Ransomware, LockBit Ransomware. |
| 2 | CVE-2022-47986 | CVSS 9.8 | IBM Aspera Faspex Code Execution Vulnerability | IBM Aspera Faspex for Windows: 4.4.1 – 4.4.2 PL1 & IBM Aspera Faspex for Linux: 4.4.1 – 4.4.2 PL1 |
Buhti Ransomware |
| 3 | CVE-2023-27351 | CVSS 8.2 | PaperCutMF/NG Improper Authentication Vulnerability | PaperCut NG: before 22.0.9 PaperCutMF: before 22.0.9 |
Bl00dy Ransomware, Cl0p Ransomware, LockBit Ransomware. |
| 4 | CVE-2022-41352 | CVSS 9.8 | Zimbra Collaboration (ZCS) Arbitrary File Upload Vulnerability | Zimbra Collaboration (ZCS) 8.8.15 and 9.0 | Rorschach/BabLock Ransomware. |
| 5 | CVE-2021-27876 | CVSS 8.1 | Veritas Backup Exec Agent File Access Vulnerability | Veritas Backup Exec before 21.2. | BlackCat Ransomware. |
| 6 | CVE-2021-27877 | CVSS 9.8 | Veritas Backup Exec Agent Improper Authentication Vulnerability | Veritas Backup Exec before 21.2. | BlackCat Ransomware. |
| 7 | CVE-2021-27878 | CVSS 8.8 | Veritas Backup Exec Agent Command Execution Vulnerability | Veritas Backup Exec before 21.2 | BlackCat Ransomware. |
| 8 | CVE-2023-28252 | CVSS 7.8 | Microsoft Windows Common Log File System (CLFS) Driver Privilege Escalation Vulnerability | Windows: 10 – 11 22H2 & Windows Server: 2008 – 2022 20H2 |
Nokoyawa Ransomware. |
| 9 | CVE-2023-0669 | CVSS 7.2 | Fortra GoAnywhere MFT Remote Code Execution Vulnerability | Up to (excluding) 7.1.2 |
Clop Ransomware. |
| 10 | CVE-2023-24880 | CVSS 4.4 | Microsoft Windows SmartScreen Security Feature Bypass Vulnerability | Windows SmartScreen Security Feature Bypass Vulnerability Up to (excluding) 10.0.14393.5786 |
Magniber ransomware. |
| 11 | CVE-2023-27532 | CVSS 7.5 | Vulnerability in Veeam Backup & Replication | Backup & Replication: before 12.0.0.1420 P20230223 | BlackBasta. |
| 12 | CVE-2023-34362 | CVSS 9.8 | Vulnerability in MOVEit Transfer file transfer software | MOVEit Transfer before 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1), | Cl0p Ransomware. |
| 13 | CVE-2016-0099 | CVSS 7.8 | Microsoft Windows Secondary Logon Service Privilege Escalation Vulnerability | The Secondary Logon Service in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, and Windows 10 Gold and 1511 | Trigona Ransomware. |
| 14 | CVE-2021-21974 | CVSS 8.8 | ESXi OpenSLP heap-overflow vulnerability | Vmware ESXi Vmware vCenter Server (vCenter Server) Vmware Cloud Foundation (Cloud Foundation) |
ESXiArgs Ransomware |
| 15 | CVE-2022-24682 | CVSS 6.1 | Zimbra Webmail Cross-Site Scripting Vulnerability | Zimbra Collaboration Suite 8.8.x before 8.8.15 patch | MalasLocker |
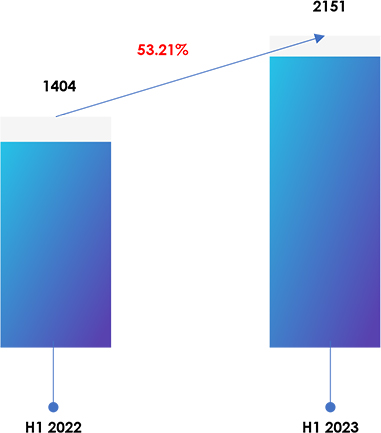
A significant surge in ransomware attacks is evident, with a rise of approximately 53%. This increase may be attributed to evolving attack techniques, intensified use of ransomware-as-a-service (RaaS) models, and more sophisticated targeting of industries with valuable data. Additionally, remote work practices and the proliferation of connected devices have expanded the attack surface, making organizations more vulnerable to ransomware threats.
Ransomware presents a highly critical threat to both organizations and individuals within the external threat landscape, causing significant harm by encrypting data and demanding extortion payments. The potential consequences are far-reaching, including severe financial losses, data recovery expenses, and business disruptions, leading to downtime and decreased productivity. Moreover, ransomware attacks can result in data breaches, exposing sensitive information and customer data, leading to potential regulatory compliance challenges and legal consequences. Reputational damage can also be substantial, with organizations facing public scrutiny, loss of customer trust, and reduced market confidence.
Ransomware operators are strategically attracted to companies that house high-value sensitive data, such as personally identifiable information (PII), financial records, and valuable intellectual property. Industries like manufacturing, healthcare, finance, and technology are prime targets due to the substantial worth of the data they possess. These cybercriminals specifically seek out sectors with critical information that can fetch significant profits on the dark web or through extortion.
Moreover, ransomware attackers are known to target countries with robust economies and thriving digital infrastructures. These nations become alluring targets due to their financial prosperity, making them more likely to possess lucrative assets that warrant sizable ransom demands. The potential for immense financial gain drives cybercriminals to exploit vulnerabilities in both organizations and countries, encrypting critical data, and demanding hefty ransoms for its safe release.
This report highlights the ever evolving and persistent threat posed by ransomware attacks. The emergence of new ransomware variants and the adaptability of established ransomware groups demonstrate the need for continuous vigilance and proactive cybersecurity measures, such as comprehensive defence strategies, continuous monitoring, employee education, and rapid incident response to effectively combat the rising ransomware menace and safeguard organizations against potentially devastating consequences.
The Manufacturing industry remains a primary target, emphasizing the necessity for robust security practices in critical sectors. Additionally, the top 5 ransomware families’ widespread impact underscores the global nature of these cyber threats.