



This report provides a comprehensive analysis of ransomware activity in 2023, divided into two parts. Part 1 covers major ransomware attacks, the top five prolific ransomware families, since January 2023, and the geographical distribution of ransomware.
Part 2 delves into targeted industries, industrial trends analysis for H1-2022 and H1-2023, the ongoing evolution of ransomware attacks, notable new ransomware groups, the notable vulnerabilities exploited in 2023, and trends comparison between H1 2022 and H1 2023.
By examining these trends, organizations can gain valuable insights into the evolving threat landscape and enhance their cybersecurity strategies to mitigate ransomware risks effectively.
Ransomware attacks continue to pose significant threats to organizations worldwide, causing severe financial and reputational damage. In the first half of 2023, a surge in ransomware activity has been observed, highlighting the need for heightened vigilance and proactive defense measures. Understanding ransomware attack tactics, techniques, and trends, is crucial for organizations to effectively mitigate risks, protect critical data, and ensure business continuity.
This report aims to shed light on the key aspects of ransomware activity during this period, including the vulnerabilities exploited, industries targeted, geographic focus, and the emergence of new ransomware variants, providing valuable insights that can empower organizations to strengthen their cybersecurity posture and stay ahead of evolving threats.
Yum Brands
Yum! Brands: KFC, Pizza Hut, and Taco Bell reported a ransomware attack in January 2023. Yum! Brands and their subsidiaries operate or franchise more than 55,000 restaurants across 155 countries and were compelled to suspend operations as a direct consequence of the ransomware attack. The hospitality giant confirmed that names, driver’s license, and ID card information were stolen.
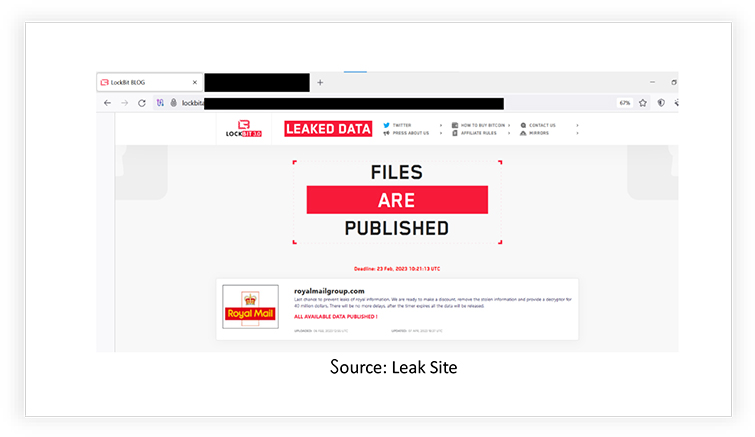
LockBit Ransomware Group Attacks Royal Mail
LockBit Ransomware Group claimed responsibility for the Royal Mail cyberattack that took place in early January, halting international shipping services by demanding £65 million ransom. Royal Mail took a firm stance and rejected this demand, forcing the threat actors to lower their demand to £40 million. Royal Mail remained resolute, however, subsequently data relating to current employees (and more) was leaked on the threat actor’s site. Interestingly, the threat actor also chose to release the negotiations dialogue.
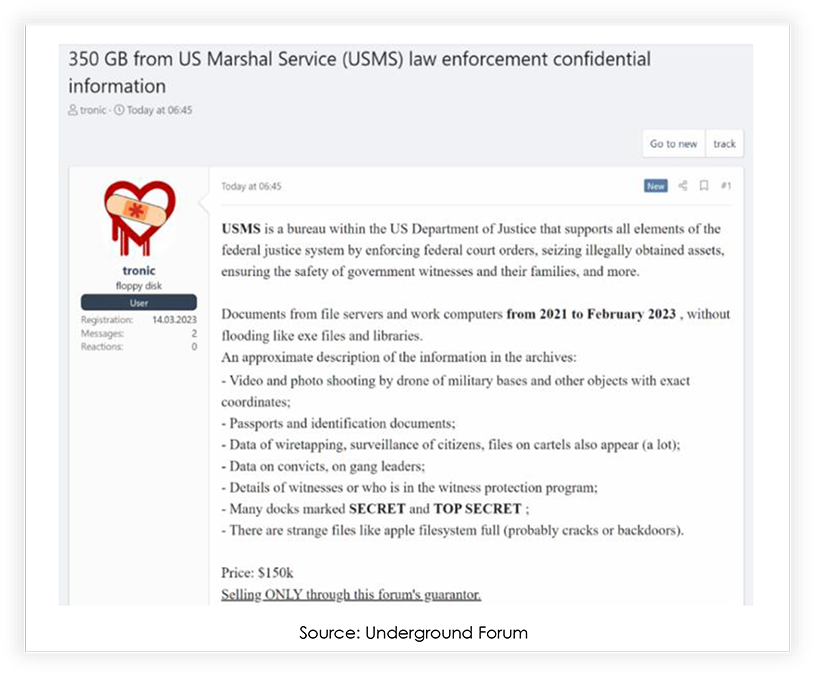
US Marshals Service Targeted
In February, the US Marshals Service suffered a ransomware attack, where a significant amount of sensitive data was compromised, including aerial footage, photos of secure locations, passports, wiretapping information, and data on individuals in witness protection, labelled as SECRET or TOP SECRET. The stolen database size is 350GB, which is reportedly being sold for $150,000.
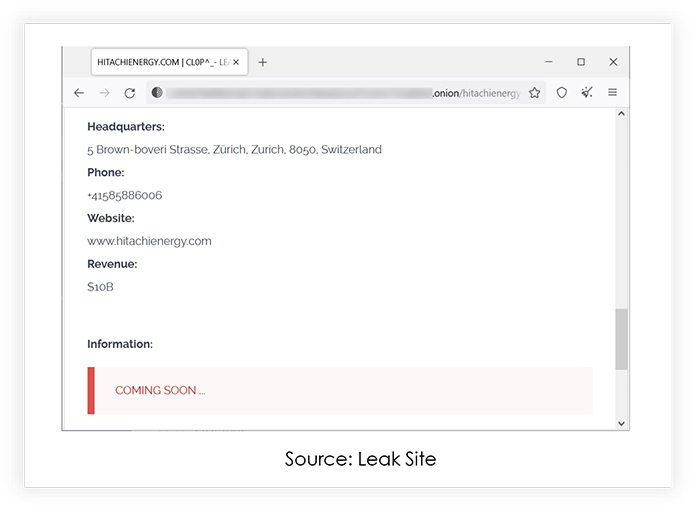
Cl0p Shatters Hitachi Energy and Hatch Bank’s Data Fortress
Hitachi Energy and ‘Hatch Bank’, a prominent fintech banking platform, both fell victim to significant data breaches, involving the Fortra GoAnywhere MFT (Managed File Transfer) software. These breaches exploited a zero-day vulnerability, CVE-2023-0669, disclosed on February 3, 2023. Hitachi Energy disconnected the compromised system and initiated an internal investigation, while Hatch Bank reported the theft of personal information of around 140,000 customers. The threat actors responsible for the ransomware attack have now published Hatch Bank’s entire dataset and a portion of Hitachi’s data on their leak site. Additionally, Cl0p ransomware claims to have breached 130 organizations using the same GoAnywhere vulnerability.
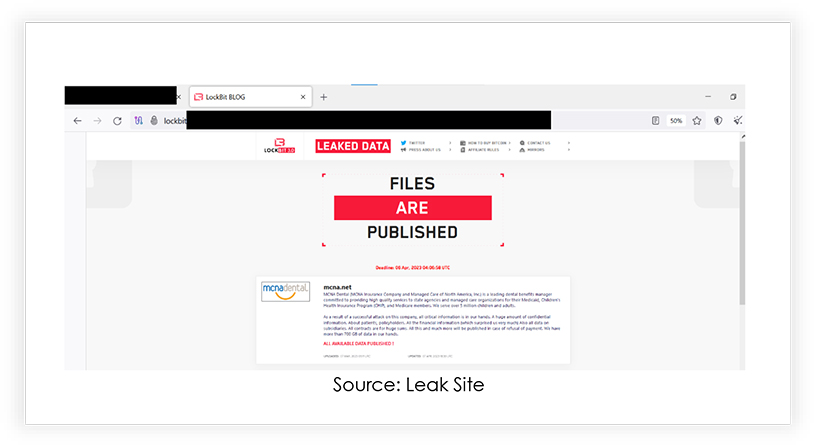
MCNA Dental Data Breach Ransomware Assault
Managed Care of North America (MCNA) Dental is a leading provider of government-sponsored dental care and oral health insurance in the U.S. The organization suffered a LockBit ransomware attack in March, involving the theft of detailed personal information of 8.9 million users for a ransom of ten million dollars. LockBit subsequently released 700GB of confidential data, when MCNA refused to pay the ransom. The entire data cache is now available on its website for public download.
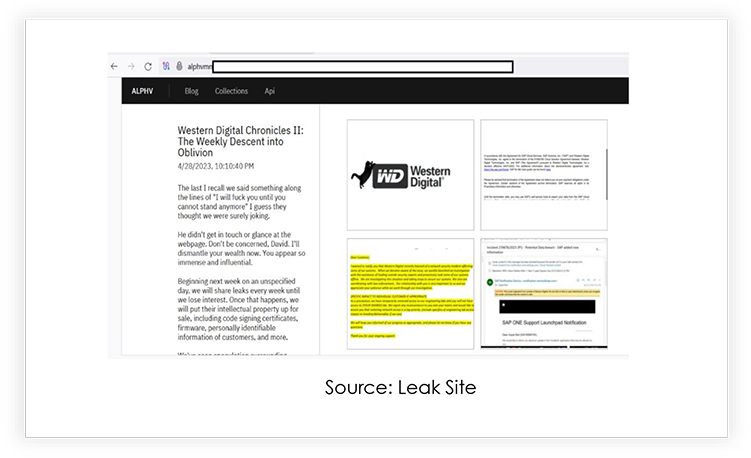
Western Digital Cyberattack
In March 2023, Western Digital; a data infrastructure company, suffered a cyberattack when an unauthorized party accessed a database containing personal information of online store customers (including stored hashed and salted passwords, along with partial credit card numbers in an encrypted format). In response to the attack, the company shut down its cloud services, mobile, desktop, and web apps for two weeks, while the hackers attempted to extort Western Digital, using their data leak site, claiming to have stolen a SAP Backoffice database with customer information.
Ten terabytes of data was compromised in total, and internal emails and video conferences, stolen from Western Digital were leaked by the threat actors.
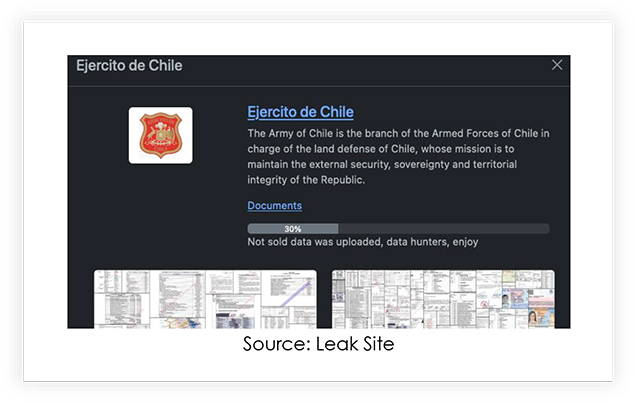
The Rhysida targets the Chilean Army
In May 2023, the Chilean army fell victim to a ransomware attack, attributed to Rhysida Ransomware, and soon after, local media sources were reporting that an Army corporal had been charged in connection with the incident. Recently, the ransomware group publicly disclosed around 360,000 documents from the Chilean Army, stating that this release constitutes only 30% of the overall compromised data.
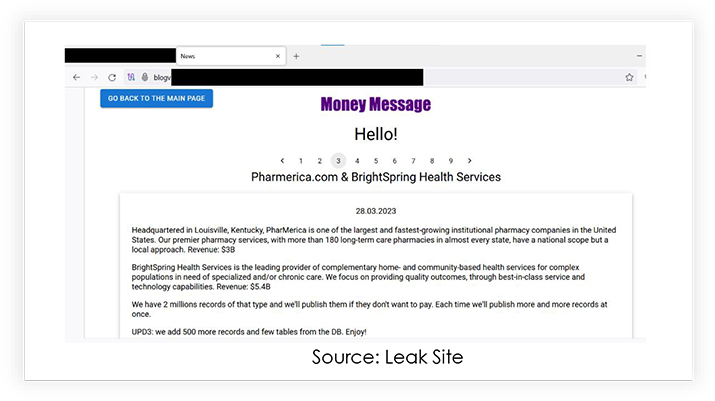
PharMerica Data Breach Exposes 5.8 million Patients to Ransomware Attack
PharMerica; a pharmacy services provider, operating across all 50 U.S. states, suffered an attack claimed by the Money Message ransomware gang. The exfiltrated data, totaling a substantial 4.7 TB in size, contained over 1.6 million unique records of personal information, including sensitive details like full names, addresses, date of birth, social security numbers (SSNs), medications, and health insurance information. PharMerica chose not to pay the ransom, and the threat actors published the stolen data.
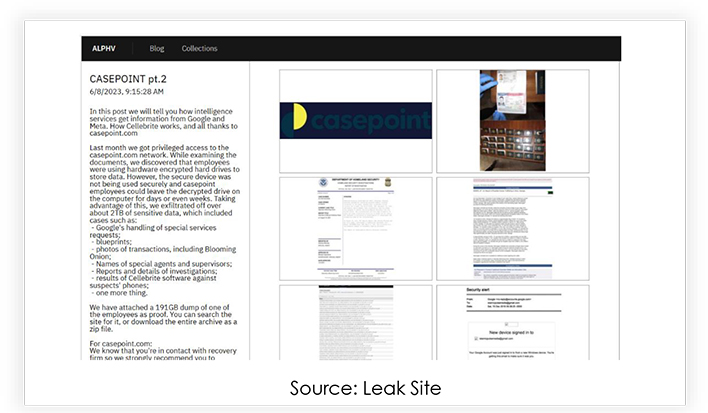
Casepoint targeted by BlackCat/ALPHV Ransomware Group
Casepoint is a platform for posting legal documents, related to litigation, investigations, and compliance, and is used by several arms of the U.S. government. In May, the company was listed on the victim list of the ALPHV Ransomware group, claiming possession of 2 terabytes of data from Casepoint. The information includes:
Threat actors provided a wide variety of samples, the size of the dump is 191GB.
MOVEit fell victim to Cl0p:
MOVEit (a widely used file transfer tool) disclosed a hack that also impacted other organizations such as Zellis (a payroll provider), British Airways, the BBC, as well as the Canadian province of Nova Scotia. The responsibility for the attack has been claimed by the Russian ransomware group known as Cl0p.
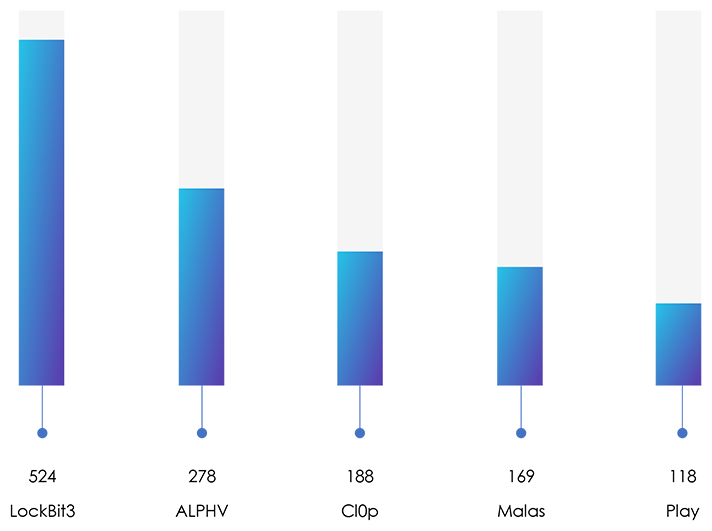
The cybersecurity landscape is plagued by numerous ransomware groups, but LockBit, ALPHV, Malas, Cl0p, and Royal Ransomware are the leading five in terms of victim count.
Their success is due to several crucial factors, for instance secure payment infrastructure, advanced encryption and evasion techniques, effective social engineering, exploitation of vulnerabilities, and the implementation of sophisticated attack methods. This combination of elements has facilitated their capability to target and compromise a substantial number of victims, setting them apart from other ransomware groups.
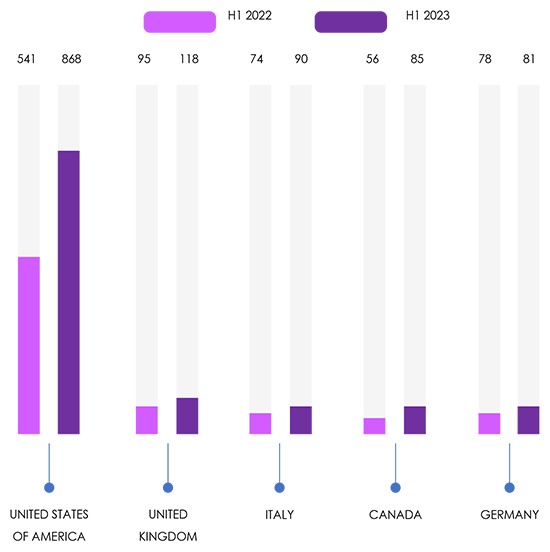
In the first half of 2022, the United States had 541 ransomware victims, increasing 60% over the following 12 months. The United Kingdom witnessed a 24% increase, with Italy and Canada experiencing a 22% and 52% rise (Germany, however, only increased by 4%).
Several factors contribute to these countries being in the top five: their strong economies make them attractive targets for cybercriminals, and their digital infrastructures are lucrative targets for ransomware attacks. Additionally, the widespread use of internet- connected devices and the high adoption rates of technology increase the attack surface and vulnerability of these countries to cyber threats.
The year 2023 has seen a surge in ransomware attacks, affecting numerous organizations worldwide. Major incidents include Yum Brands, Royal Mail, US Marshals Service, Hitachi Energy, Hatch Bank, MCNA Dental, Western Digital, Chilean Army, and PharMerica, impacting millions of people and exposing sensitive data. The top five most prolific ransomware families since January 2023 are Lockbit, ALPHV, Cl0p, Malas, and Play Ransomware, with Lockbit leading the pack with a staggering 524 victims. The geographical distribution of ransomware shows a significant increase in attacks in the United States, United Kingdom, Italy, and Canada, while Germany experienced a smaller rise. The attractiveness of these countries to cybercriminals is attributed to their strong economies, lucrative digital infrastructures, high adoption of technology, and widespread use of internet-connected devices. As ransomware attacks continue to target high-profile entities, organizations worldwide must remain vigilant and take robust cybersecurity measures to safeguard against these persistent threats.
Part 2 of this report contains an External Threat Landscape Management (ETLM) overview and provides a comprehensive impact assessment for H1-2023, along with strategic and tactical recommendations.