


Quishing, the phishing scheme exploiting QR codes, is on the rise, with a 433% increase in reported incidents from 2023 to 2024. Cybercriminals embed malicious links within QR codes, tricking users into revealing sensitive information. Nearly 90% of these attacks target user credentials, highlighting the sophistication of Quishing tactics. Industries that use QR codes, particularly retail and e-commerce, face significant risks, with over 1,200 QR code scams reported this year. To combat these threats, users must verify QR codes and utilize trusted payment apps, while businesses should implement robust security measures and educate customers.
The CYFIRMA Research team has conducted a thorough examination of Quishing, a modern cyber fraud tactic that combines QR codes and phishing schemes. This evolving threat exploits the growing use of QR codes in various transactions, promotions, and information sharing. As QR codes become increasingly prevalent, they also present new opportunities for cybercriminals. Alarmingly, there has been a marked rise in QR code phishing incidents from 2023 to 2024, highlighting the critical need for public awareness and effective security measures. Given their ability to provide easy access to information, it is vital for users to exercise caution when scanning QR codes to protect themselves from potential exploitation.
Quishing typically involves embedding harmful links within QR codes that redirect users to fraudulent websites. Cybercriminals utilize social engineering tactics, such as urgency and familiarity, to trick users into scanning these codes. For instance, a large percentage of QR code attacks are linked to credential phishing, where attackers create look-alike login pages designed to steal personal information. The sophistication of these attacks makes them particularly dangerous; users may not realize they have been compromised until it’s too late. Attacks that present fake multi-factor authentication (MFA) notifications account for a significant portion of Quishing attempts, using fear of losing access to essential services to manipulate victims.
Unlike traditional phishing techniques that rely on obvious deceptive emails, Quishing utilizes QR codes to conceal the underlying malicious links. This lack of transparency means users are less likely to recognize the risks involved, as QR codes do not typically display a URL that can be scrutinized. As a result, Quishing attacks can often bypass conventional security filters and trigger less suspicion among users.
The rise of digital payments has heightened the stakes for Quishing attacks. As users increasingly turn to mobile wallets and payment applications, the potential for encountering fraudulent QR codes rises correspondingly. A significant increase in QR code usage for payments is anticipated, leading to greater exposure for users. Attackers can easily create counterfeit QR codes that, when scanned, direct users to phishing sites designed to harvest sensitive payment information.
For businesses operating in retail, food services, and e-commerce, the implications of Quishing are profound. Reports of QR code scams reflect a worrying trend, as attackers exploit the convenience of QR codes to undermine customer trust and brand integrity. A breach not only threatens financial security but also tarnishes reputations, potentially leading to long-lasting damage to customer relationships.
One notable example involves fraudulent QR codes placed in public areas, such as restaurants or parking lots, directing users to phishing sites that appear legitimate. Users scanning these codes may be asked to enter sensitive information, including credit card details, which the attackers then exploit. The ease of deploying fake QR codes makes this method particularly appealing to cybercriminals, as they can quickly spread their attacks across multiple locations.
Quishing attacks can be categorized into different types:
Particularly vulnerable industries include those that have integrated QR codes into their operations. E-commerce, hospitality, and food services rely heavily on these codes for streamlined transactions, making them prime targets for Quishing. The convenience that QR codes offer also contributes to their widespread adoption, inadvertently creating opportunities for cybercriminals.
Social engineering is pivotal in the success of Quishing attacks. Cybercriminals design their messages to provoke emotional responses, fear, urgency, or trust, which can lead users to make hasty decisions without adequately assessing risks. For example, an email might claim that urgent action is needed to secure an account, prompting users to scan a QR code that appears legitimate. Such tactics can significantly lower defenses, allowing attackers to capitalize on human psychology to achieve their goals.
The prevalence of smartphones and the growing reliance on QR codes for contactless payments contribute to the rise of Quishing. As more users become accustomed to scanning codes without questioning their origins, the likelihood of falling victim to these attacks increases. Additionally, the shift to mobile devices for transactions limits traditional security measures, creating vulnerabilities that attackers can exploit.
The ramifications of Quishing extend beyond financial loss. The average cost of a phishing attack on businesses is substantial, accounting for lost revenue, remediation costs, and damage to reputation. Victims may also experience emotional distress and a loss of trust in digital payment systems. Furthermore, businesses face potential legal repercussions if customer data is compromised, leading to regulatory fines and a loss of consumer confidence.
Cybercriminals employ various methods and tools to conduct Quishing attacks, including:
Several recent scams highlight the evolving tactics used in Quishing:
These examples highlight the need for vigilance and awareness among consumers to avoid becoming victims of Quishing attacks.
Various phishing attempts have targeted users through text messages, including fake account alerts and fraudulent links. See below:
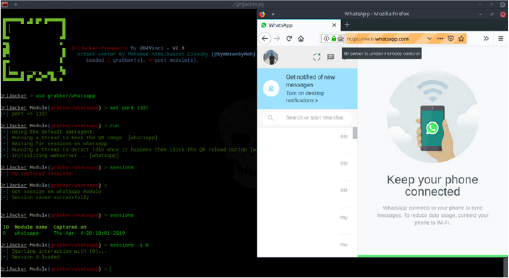
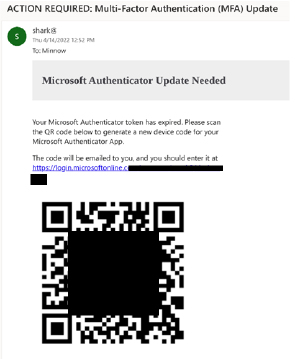
The victim will scan the QR code found in the email body with their mobile device. The QR code will direct the victim to the attacker-controlled server (running the server module of SquarePhish), with a URL parameter set to their email address.
To protect against Quishing, users, and businesses can adopt several preventive measures:
For businesses, securing payment QR codes and providing customer education on potential risks is essential to mitigate Quishing threats.
As digital payment adoption continues to rise, Quishing threats are likely to evolve. Organizations must remain vigilant, adapting their security protocols to address new tactics employed by cybercriminals. Continuous education for both consumers and businesses will be vital in combating this modern cyber threat. The emphasis on secure practices and technological adaptations will play a crucial role in the ongoing battle against Quishing.
In conclusion, Quishing poses a significant and evolving threat to individuals and organizations leveraging QR codes for digital interactions and payments. The research from CYFIRMA highlights the alarming increase in QR code phishing attempts and emphasizes the necessity for comprehensive security measures. Organizations must prioritize user education, implement stringent verification processes for QR codes, and stay informed about emerging threats. By adopting a proactive approach guided by insights from cybersecurity experts, businesses can effectively mitigate the risks associated with Quishing and protect their critical assets. Remaining vigilant and adaptable in the face of this modern cyber threat is essential for maintaining trust and security in digital transactions.