


CYFIRMA examines a sophisticated phishing campaign that leverages QR-code-based delivery, commonly referred to as “quishing,” to target employees with messages related to payroll and compensation. By combining personalized social engineering with obfuscated scripts and dynamically generated infrastructure, attackers increase the likelihood of engagement while evading traditional security controls. The campaign demonstrates a high level of operational sophistication, emphasizing the shift toward targeted, industry-specific threats. Findings underscore the need for enhanced user awareness, proactive monitoring, and intelligence-driven defenses to protect organizational credentials and sensitive data.
Phishing continues to evolve as a primary method for credential compromise, with threat actors increasingly adopting techniques designed to bypass traditional enterprise security controls. One such evolution is QR-code phishing, or quishing, which leverages QR codes embedded in seemingly legitimate business communications to redirect users to malicious content. By prompting users to scan QR codes rather than click links, attackers effectively shift the attack surface away from monitored corporate environments and onto employees’ personal mobile devices, where security visibility and controls are often limited or absent.
The campaign analyzed in this report reflects a broader trend toward targeted, context-aware attacks that exploit trusted business processes, such as payroll or compensation updates. Once initiated on a personal device, the attack proceeds outside the organization’s email gateways, endpoint protection platforms, and web filtering controls, significantly reducing the likelihood of detection. This approach not only increases the success rate of credential harvesting but also complicates incident response and forensic investigation.
As these techniques mature, similar campaigns are expected to further blend social engineering with adaptive infrastructure and evasive delivery mechanisms. Understanding how quishing campaigns transition users from protected corporate systems to unmanaged personal devices is critical for anticipating future threats and developing effective detection, prevention, and user awareness strategies. This report examines these dynamics to support informed risk management and defensive planning.
The attack originates from a phishing email claiming to be a payroll update / payroll document notification. The message is designed to create urgency and legitimacy by referencing employee compensation–related information. The email instructs the recipient to scan a QR code to review or acknowledge payroll changes. This delivery method avoids traditional URL inspection by email security gateways.
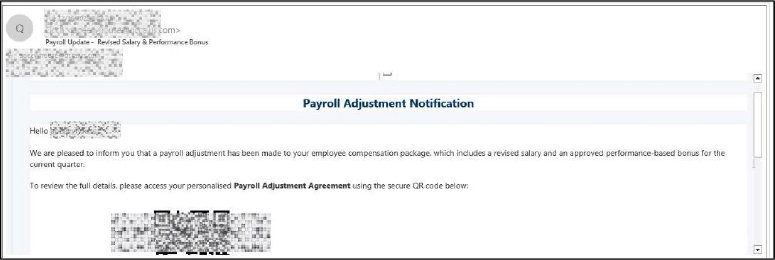
After scanning the QR code, the victim is redirected to an external website hosted on an untrusted domain that is unrelated to any legitimate payroll or corporate system. The QR code URL follows a structured but deceptive pattern in which a malicious or compromised domain is combined with randomly generated directory names and an embedded target specific email identifier. https://<malicious-domain>/<randomized-directory>/<unique-token>/$<target-email-address>
The redirected page presents a fake CAPTCHA or human verification prompt, asking the user to interact with the page to proceed. This CAPTCHA is not a real bot protection mechanism. Instead, it serves to:
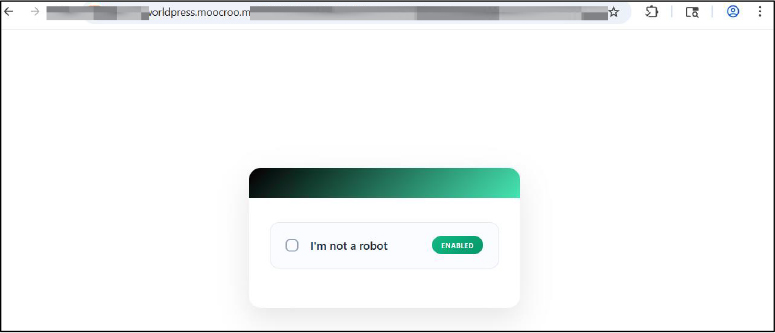
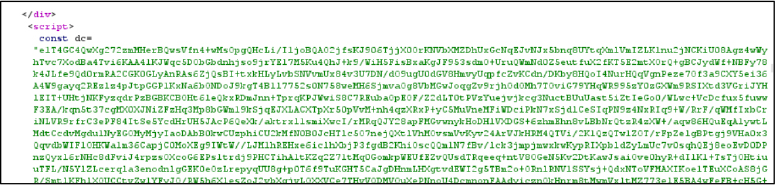
During the CAPTCHA interaction, the page loads and executes highly obfuscated JavaScript code. The script reconstructs hidden instructions at runtime using encoding and encryption techniques, which is characteristic of phishing kits designed to evade detection. This code communicates with attacker controlled infrastructure and prepares the next stage of the attack, where the email id is auto-filled and goes to the next password.
The email auto-fill is performed by heavily obfuscated JavaScript delivered in the server’s response. The code contains an encrypted data payload (const dc=”e1T4GC4QwXg272zm…). When executed in the victim’s browser, this script decrypts the payload using XOR operations and custom algorithms, extracts the victim’s email address that was embedded in the URL path, and automatically populates it into the login form field without any manual input from the user.
Following the automatic email population, the phishing page presents a password entry field. The victim, believing the pre-filled email indicates a legitimate service, is then prompted to enter their account password. This final step is designed to harvest the complete credentials, email, and password from the targeted user.
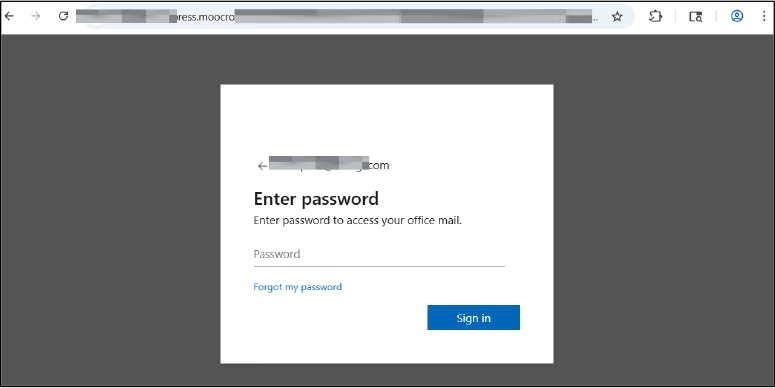
The stolen password is not submitted to the phishing domain. It is encrypted and sent via cross-site POST to a completely different, randomly generated subdomain using the pattern <random-subdomain>.<Malicious domain>. Each victim likely receives a unique endpoint with a long, alphanumeric path. Using separate, rotating domains for data collection helps attackers evade domain-based detection and complicates forensic tracking.
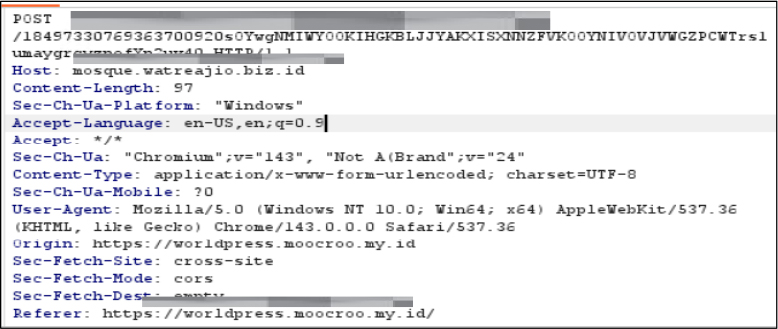
CYFIRMA observed a phishing campaign that demonstrates a highly targeted and sophisticated approach to credential harvesting. Recipients across multiple organizations receive emails crafted to appear as legitimate payroll notifications, leveraging urgency and familiarity with employee compensation systems to entice interaction. Unlike conventional phishing attempts, these messages utilize QR codes rather than embedded hyperlinks, circumventing standard email security filters and reducing the likelihood of automated detection.
Upon scanning the QR code, victims are redirected to externally hosted phishing sites on untrusted domains. In many cases, QR codes are scanned using personal mobile devices, intentionally shifting the attack away from corporate-managed endpoints and security monitoring tools. This transition reduces visibility for enterprise security teams, as personal devices often lack enterprise-grade protections, such as secure web gateways, endpoint detection, or DNS filtering. Each phishing site is uniquely structured with randomized directories and embedded identifiers specific to the targeted individual, enabling attackers to track engagement and dynamically populate the victim’s email address within the fraudulent login form. This level of customization suggests that threat actors are selectively profiling targets based on industry, organizational role, or access level.
The phishing infrastructure is purpose-built to evade traditional defensive mechanisms. Obfuscated JavaScript executed during fake CAPTCHA interactions delays automated analysis while reconstructing encrypted instructions at runtime. This technique not only hinders sandbox-based inspection but also allows the attack flow to adapt dynamically based on user interaction. The script extracts the victim’s email address and auto-fills it into the password entry form, reinforcing the illusion of legitimacy and increasing the likelihood of credential submission. Once credentials are entered, they are encrypted and transmitted to a separate, dynamically generated collection endpoint. The use of rotating subdomains and unique URL paths per victim suggests a deliberate strategy to limit exposure, disrupt pattern-based detection, and complicate forensic attribution.
From a forward-looking perspective, campaigns of this nature are likely to continue evolving toward greater use of unmanaged devices, short-lived infrastructure, and multi-channel delivery methods. Future iterations may incorporate additional verification steps, adaptive content delivery, or messaging platform integration to further evade detection and extend the attack lifecycle. Overall, this campaign reflects a broader shift toward highly customized, multi-stage phishing operations that blend technical sophistication with psychological manipulation, underscoring the growing challenge such threats pose to organizations across industries.
| Tactic | Technique ID | Technique Name |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1059.007 | Command and Scripting Interpreter: JavaScript |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1497.003 | Virtualization/Sandbox Evasion: Time Based Evasion |
| Credential Access | T1556 | Modify Authentication Process |
| Credential Access | T1056.003 | Input Capture: Web Portal Capture |
| Collection | T1114 | Email Collection |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1104 | Multi-Stage Channels |
| Command and Control | T1090.003 | Proxy: Multi-hop Proxy |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
title: QR Code Payroll Phishing Email
description: Detects payroll-themed phishing emails using QR codes
author: CYFIRMA
logsource:
product: email
service: exchange
detection:
keywords:
– “payroll update”
– “payroll document”
– “compensation”
qr_indicators:
– “QR”
– “scan code”
condition: keywords and qr_indicators
level: high
CYFIRMA analyzed a phishing campaign that demonstrates a highly targeted, multi-stage attack leveraging social engineering, technical obfuscation, and per-victim infrastructure to compromise credentials. By combining QR-code delivery, dynamically generated URLs, encrypted JavaScript, and rotating exfiltration endpoints, threat actors maximize the likelihood of user interaction while evading traditional security controls and complicating forensic analysis. The campaign reflects a clear trend toward personalized, industry-focused attacks that exploit trust in familiar business processes. Effective detection and mitigation require a combination of email and web monitoring, behavioral analysis, and endpoint inspection, emphasizing the need for proactive, intelligence-driven defenses.
Enhance User Awareness and Training
Strengthen Email and Communication Policies
Adopt Behavior-Based Monitoring
Segment and Protect Critical Processes
Secure Personal Device Interaction
Implement Threat Intelligence and Proactive Monitoring
Incident Response Preparedness
Periodic Testing and Simulation