


Hacktivist Proxy Operations describe a class of deniable cyber pressure activities in which ideologically aligned, non-state cyber groups conduct disruptive operations that align with state geopolitical interests without requiring formal sponsorship, command-and-control, or direct tasking. Unlike traditional state-sponsored cyber operations, these activities rely on public claims, volunteer participation, and low-complexity techniques to impose psychological, political, and operational costs on adversaries while preserving plausible deniability for the benefiting state. This research advances existing discussions on hacktivism by framing such activity as a repeatable, model-driven form of deniable cyber pressure rather than isolated ideological activism or criminal disruption.

This report documents Hacktivist Proxy Operations as a repeatable operational model rather than a collection of isolated incidents. The model follows a consistent activation sequence: geopolitical trigger events such as sanctions, military assistance announcements, or diplomatic escalations are followed by rapid narrative mobilization in hacktivist communication channels, volunteer coordination, targeted disruptive activity (primarily DDoS attacks, defacement, and symbolic intrusions), and public amplification of claimed impact. Activity typically de-escalates once signalling objectives are achieved, distinguishing these operations from sustained cybercrime or espionage campaigns.
Importantly, this research does not assert direct state control over hacktivist groups. Instead, it demonstrates how such groups provide strategic utility by operating in the grey zone between criminal activity and state cyber operations. Their public posture, reliance on common tooling, and absence of exclusive infrastructure complicate attribution, delay coordinated response, reduce escalation risk, and create ambiguity that is central to their effectiveness.
The findings are supported by structured analysis of open-source intelligence, including underground cybercrime ecosystems and ideologically aligned hacktivist communication channels. Quantitative keyword frequency analysis and temporal correlation show that hacktivist and DDoS activity remains low in absolute volume compared to financially motivated cybercrime, but exhibits sharp, episodic surges aligned with geopolitical developments. This volatility contrasts with the steady behaviour of ransomware and data-theft ecosystems, indicating a distinct motivation and activation mechanism.
While individual hacktivist proxy attacks are often technically unsophisticated, their cumulative impact includes service disruption, reputational damage, defensive resource exhaustion, and manipulation of public perception. For critical infrastructure operators, government institutions, and strategically significant private enterprises, repeated low-intensity disruption can generate disproportionate strategic pressure despite limited technical impact.
The report concludes that existing cyber defence and threat-classification frameworks insufficiently account for proxy-based cyber pressure operations. Treating hacktivist activity solely as a nuisance or criminal behaviour underestimates its strategic role in contemporary state competition. Effective mitigation does not require attribution certainty, but rather improved resilience, geopolitical context awareness, and operational preparedness for episodic, narrative-driven disruption.
Cyber operations have become an integral component of contemporary geopolitical competition. States increasingly pursue strategic objectives in cyberspace through deliberately ambiguous and deniable methods that remain below established thresholds for retaliation. This shift reflects both the maturation of cyber capabilities and the political risks associated with overt escalation in an interconnected global environment.
Within this context, hacktivist activity has undergone a substantive transformation. Traditionally understood as digital protest or ideologically motivated disruption conducted by loosely organized individuals, hacktivism is now frequently observed operating in close temporal and strategic alignment with state interests. These activities neither resemble classic state-sponsored cyber operations nor fully align with financially motivated cybercrime. Instead, they occupy an intermediate space in which non-state actors generate strategic effects without formal sponsorship, command-and-control structures, or proprietary tooling.
This report examines that intermediate space. Rather than analysing hacktivism as activism or nuisance activity, the research focuses on Hacktivist Proxy Operations, a model in which ideologically aligned cyber groups function as deniable instruments of pressure within broader state competition. In this model, hacktivist groups apply disruptive force, shape narratives, and signal resolve in response to geopolitical events, while states benefit indirectly without assuming explicit responsibility.
Hacktivist Proxy Operations do not require coordination orders, financial sponsorship, or direct technical assistance to be effective. Strategic alignment can emerge through shared narratives, permissive domestic environments, selective law-enforcement tolerance, and amplified ideological messaging. The absence of formal control is not a weakness, but a defining feature that enables plausible deniability, complicates attribution, and constrains escalation options.
The increasing prevalence of this model challenges existing cyber threat frameworks. Many organizations continue to classify hacktivist activity as low-sophistication or low-impact, prioritizing defences against ransomware, espionage, or advanced persistent threats. This approach overlooks the cumulative strategic impact of sustained, low-intensity disruption when synchronized with geopolitical pressure, leading to proxy campaigns being analysed in isolation rather than as coordinated pressure strategies.
This report addresses that gap by documenting Hacktivist Proxy Operations as a repeatable operational pattern rather than an abstract concept. Using structured analysis of open-source intelligence, underground cyber ecosystems, and hacktivist communication channels, the study identifies consistent activation triggers, behavioural sequences, and de-escalation characteristics that distinguish proxy-based disruption from independent activism or criminal activity.
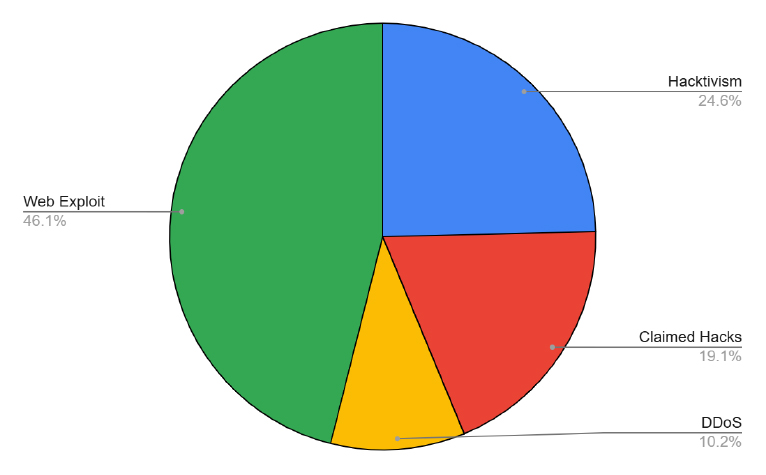
Figure 1: Data of the last 6 months
By framing hacktivist proxy activity as an operational model, this report provides a foundation for more accurate threat assessment, improved defensive planning, and more proportionate policy responses. Recognizing the model does not require proving state control; it requires acknowledging strategic utility and adapting to a cyber threat landscape increasingly defined by ambiguity, deniability, and indirect coercion.
Hacktivism historically emerged as a form of digital protest, driven by ideological, political, or social motivations rather than financial gain. Early hacktivist campaigns focused on website defacements, distributed denial-of-service (DDoS) attacks, and symbolic disruptions intended to draw attention to perceived injustices. These activities were often sporadic, poorly coordinated, and short-lived, reflecting the decentralized nature of the groups involved.

However, the geopolitical landscape of the 2020s has significantly altered this dynamic. States facing economic sanctions, diplomatic isolation, or conventional military constraints have increasingly turned to asymmetric tools to project influence and impose costs on adversaries. Cyber operations offer an attractive option due to their low cost, scalability, and ambiguity. Within this context, hacktivist groups have become particularly valuable as deniable intermediaries.
Plausible deniability refers to the ability of a state to deny responsibility for actions conducted on its behalf due to a lack of direct, attributable evidence. In cyberspace, this concept is particularly powerful because technical attribution is inherently complex, time-consuming, and probabilistic rather than definitive.
Hacktivist proxies enhance plausible deniability by introducing multiple layers of separation between the state and the operation. These groups often claim ideological motivations that align broadly with state interests but stop short of explicit coordination. Infrastructure used in attacks may be shared with criminal actors or hosted in third countries, further complicating attribution. Communication channels are informal, transient, and encrypted, making intelligence collection difficult.
The strategic value of this model lies not only in denial but also in narrative control. When confronted with accusations, states can frame hacktivist activity as the actions of independent citizens, patriotic volunteers, or even foreign provocateurs. This ambiguity slows diplomatic responses, weakens consensus-building among allies, and reduces the likelihood of direct retaliation.
Attribution challenges are central to the effectiveness of hacktivist proxies. Technical indicators such as IP addresses, malware signatures, or infrastructure reuse are often inconclusive or deliberately misleading. Hacktivist groups frequently use publicly available tools, shared botnets, and rented infrastructure, reducing the uniqueness of technical fingerprints.
Behavioural attribution, which examines targeting patterns, timing, and strategic alignment, provides stronger indicators but lacks the certainty required for diplomatic or legal action. States exploiting this gap understand that ambiguity itself is a strategic asset. By operating below the threshold of armed conflict and avoiding overt signatures, they can impose costs without triggering collective defense mechanisms or sanctions escalation.
Hacktivist Proxy Operations function through a repeatable activation model rather than bespoke, one-off campaigns. While individual groups differ in ideology, branding, and tooling, the underlying operational sequence remains consistent across regions and geopolitical contexts. This section documents that sequence as an activation chain, defining the core primitive that enables deniable cyber pressure.
Crucially, this model does not depend on formal state sponsorship, advanced tooling, or persistent access. Its effectiveness derives from timing, narrative alignment, volunteer mobilization, and public amplification. The absence of centralized control is not a limitation; it is a structural feature that enhances deniability and constrains escalation.
The Hacktivist Proxy Primitive
At its core, Hacktivist Proxy Operations rely on a simple but powerful primitive:
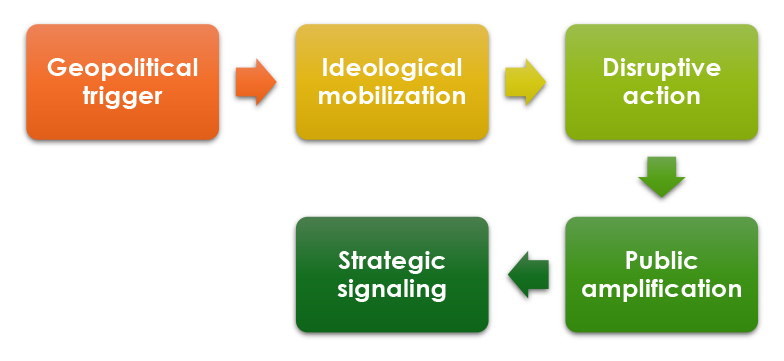
This primitive is low-cost, repeatable, and resilient. It requires no zero-day vulnerabilities, no covert malware infrastructure, and no sustained access to target environments. Instead, it leverages open communication platforms, widely available attack tools, and public narratives to generate strategic effect.
Unlike traditional cyber operations, which seek technical dominance or long-term access, hacktivist proxy activity seeks visibility, disruption, and signalling. The objective is not necessarily to cause lasting damage, but to demonstrate capability, impose friction, and influence perception at critical moments.
Phase 1: Geopolitical Trigger
Hacktivist proxy campaigns are consistently preceded by identifiable external events. These triggers are typically geopolitical in nature and include, but are not limited to:
These events provide both justification and narrative framing for subsequent activity. Importantly, the trigger does not need to be explicitly referenced by a state actor. Hacktivist groups often frame their actions as spontaneous retaliation or resistance, allowing the activation to appear organic rather than coordinated.
From an analytical perspective, the presence of a clear external trigger distinguishes proxy-based hacktivism from background cyber noise. In the absence of such triggers, hacktivist activity tends to remain low or fragmented.
Phase 2: Narrative Mobilization and Signalling
Following the trigger event, ideologically aligned hacktivist channels rapidly shift tone. Messaging analysis consistently reveals a transition from routine posting to overt mobilization language, including:
This phase is critical because it establishes legitimacy and intent within the hacktivist ecosystem. The narrative does not require factual precision; its function is motivational rather than informational. In many cases, exaggerated or symbolic language is used to lower participation thresholds and accelerate volunteer engagement.
Notably, this mobilization occurs in public or semi-public spaces. Unlike covert state operations, visibility is a feature rather than a risk. Public signalling reinforces the perception of grassroots action and complicates attribution.
Phase 3: Volunteer Coordination and Target Selection
Once mobilization is underway, hacktivist groups move rapidly to identify targets. Target selection is rarely random. Analysis shows a preference for entities that maximize symbolic, political, or economic visibility, including:
Coordination mechanisms vary in sophistication, ranging from shared target lists and timing windows to loosely synchronized calls for action. The technical barrier to participation is intentionally low. Widely available DDoS tools, web exploitation scripts, or defacement techniques are favoured over custom tooling.
This design serves two purposes. First, it enables rapid scaling through volunteer participation. Second, it ensures that activity remains technically indistinct from common cybercrime or nuisance attacks, further obscuring attribution.
Phase 4: Disruptive Execution
The execution phase is typically characterized by short bursts of disruptive activity rather than sustained intrusion. Common techniques include:
While these actions are often technically unsophisticated, their impact is amplified by timing and narrative framing. Even limited or temporary disruptions can generate disproportionate attention when they coincide with sensitive political moments.
Importantly, execution is frequently accompanied by real-time public reporting by the hacktivist groups themselves. Claims of success are broadcast immediately, often with inflated impact assessments. This public posture differentiates hacktivist proxy activity from covert cyber operations and reinforces its signalling function.
Phase 5: Amplification and Psychological Impact
Public amplification is not an afterthought; it is a core component of the operational model. Hacktivist groups actively disseminate screenshots, logs, and claims through social media and messaging platforms. These materials are designed to:
The psychological impact of this phase often exceeds the technical impact of the underlying attacks. Even when claims are exaggerated or inaccurate, the perception of ongoing disruption can strain defensive resources, damage reputations, and create political pressure.
Phase 6: De-escalation and Dormancy
A defining feature of Hacktivist Proxy Operations is controlled de-escalation. After an initial surge of activity, campaigns often taper off rapidly. Groups shift focus, reduce posting frequency, or declare symbolic victory.
This de-escalation serves multiple functions. It limits exposure and burnout within volunteer communities, reduces the likelihood of sustained countermeasures, and preserves the ability to reactivate in response to future triggers. The episodic nature of activity further distinguishes proxy operations from profit-driven cybercrime, which tends to exhibit continuity rather than bursts.
Hacktivist Proxy Operations derive their effectiveness not from technical sophistication, but from their ability to impose disproportionate strategic and psychological impact relative to the resources expended. While individual incidents are often short-lived and limited in scope, their cumulative effect, particularly when synchronized with geopolitical events, creates sustained pressure across political, operational, and reputational dimensions.
This section assesses impact across four domains: operational disruption, psychological and reputational effects, defensive cost asymmetry, and strategic signalling.
Operational Impact
At a purely technical level, most hacktivist proxy activities fall into categories traditionally considered manageable: DDoS attacks, website defacements, and short-term service interruptions. These actions rarely result in permanent damage, data destruction, or long-term system compromise.
However, operational impact should not be evaluated solely on technical severity. Timing and target selection amplify consequences. Disruption of public-facing government services, transportation portals, financial platforms, or media outlets, particularly during periods of political sensitivity, can generate outsized operational strain. Even brief outages may require emergency response procedures, executive escalation, and inter-agency coordination.
Additionally, repeated low-intensity disruptions force organizations into a reactive posture. Incident response teams must remain on heightened alert, diverting attention from other security priorities. Over time, this resource diversion becomes a material operational cost, even in the absence of severe technical damage.
Psychological and Reputational Impact
The psychological dimension is central to the effectiveness of hacktivist proxy operations. Public claims, screenshots, and narrative framing often exaggerate impact, but perception rather than accuracy drives consequence.
For government institutions, visible disruption undermines public confidence and creates the appearance of vulnerability. For private organizations, particularly those in regulated or critical sectors, repeated association with cyber incidents can damage trust among customers, partners, and investors.
Media amplification further compounds these effects. Hacktivist groups actively exploit the speed and reach of digital platforms to shape narratives before accurate technical assessments are available. Even when claims are later disproven or contextualized, the initial perception often persists.
This reputational pressure is difficult to quantify but should not be underestimated. In several observed cases, the reputational fallout from hacktivist claims exceeded the actual operational impact of the underlying activity.
Defensive Cost Asymmetry
Hacktivist proxy operations exploit a fundamental asymmetry in cyber defense economics. The cost of launching a disruptive attack, particularly DDoS-based activity, is low, relying on volunteer participation and widely available tooling. The cost of defense, by contrast, includes infrastructure scaling, monitoring, incident response, communications management, and post-incident review.

This asymmetry favors the attacker, especially during repeated activation cycles. Organizations may successfully mitigate each individual incident, yet still incur cumulative costs in the workforce, operational disruption, and opportunity loss.
For smaller organizations or public institutions with limited cyber budgets, this asymmetry is particularly pronounced. Even when defenses hold, the effort required to maintain resilience during repeated campaigns can strain resources and degrade overall security posture.
Strategic Signalling and State-Level Effects
At the strategic level, Hacktivist Proxy Operations function as a signalling mechanism. They allow aligned states to demonstrate reach, relevance, and resolve without engaging in overt, attributable cyber operations.
The signalling effect operates on multiple audiences simultaneously:
Because these operations remain below traditional thresholds for retaliation, they constrain response options. Targeted states must weigh the risks of escalation against the costs of inaction, often resulting in restrained or fragmented responses.
Over time, this dynamic normalizes persistent, low-level cyber pressure as a feature of international competition. The risk is not escalation through severity, but erosion through normalization.
Implications for Governments
For governments, the primary risk lies in misclassification. Treating hacktivist proxy activity solely as a criminal nuisance underestimates its strategic role and may lead to inadequate preparation. Conversely, over-attributing such activity risks escalation based on uncertain evidence.
Effective response requires recognizing hacktivist proxy operations as a grey-zone challenge: persistent, deniable, and politically contextual. This recognition should inform national cyber strategies, public communication approaches, and inter-agency coordination mechanisms.
Implications for the Private Sector
Private sector organizations, particularly those in critical infrastructure, finance, transportation, energy, and media, are increasingly exposed to hacktivist proxy activity due to their symbolic and economic significance.
Unlike cybercrime, targeting is often unrelated to an organization’s own actions or security posture. Instead, targeting reflects geopolitical alignment, national affiliation, or sector visibility. This unpredictability complicates traditional risk modelling and threat prioritization.
Organizations must therefore plan not only for technical resilience, but for reputational management and sustained disruption scenarios driven by external political events.
Summary of Impact Assessment
Hacktivist Proxy Operations achieve impact through aggregation rather than escalation. Individually limited actions combine to produce operational strain, reputational damage, and strategic signalling effects that exceed their technical complexity.
The key risk is not catastrophic failure, but persistent pressure, pressure that exploits ambiguity, timing, and perception to influence behaviour without triggering a decisive response. Understanding this impact profile is essential for developing proportionate and effective defensive strategies.

Evolution in Modern Conflicts
The transformation of hacktivism into a proxy warfare tool has been most visible during periods of heightened geopolitical tension. Since 2022, conflicts involving Eastern Europe, the Middle East, and East Asia have coincided with surges in ideologically framed cyber campaigns targeting governments, critical infrastructure, and private sector entities. Multiple ideologically aligned hacktivist collectives have demonstrated this pattern, combining nationalist or political branding with sustained disruptive activity temporally aligned to geopolitical events.

Operational Characteristics
Modern hacktivist proxy operations exhibit characteristics that distinguish them from traditional grassroots activism. These campaigns are often sustained over discrete periods of heightened activity, involve target prioritization consistent with strategic objectives, and demonstrate an understanding of geopolitical leverage points.
Target selection frequently focuses on symbolic and economic pressure points rather than purely technical vulnerabilities. Government websites, public transportation systems, financial services, and media organizations are favoured because disruptions generate public attention and political pressure. Attacks are often timed to coincide with high-visibility events, amplifying their psychological impact.
Another notable feature is the integration of information operations, where cyber disruption is paired with narrative amplification to shape perception alongside technical impact. This blending of disruption and messaging aligns closely with state-level hybrid warfare doctrines.
Convergence with Cybercrime
One of the most concerning developments is the increasing overlap between hacktivist groups and cybercriminal ecosystems. Many hacktivist campaigns now incorporate tactics traditionally associated with financially motivated actors, including data theft, extortion, and ransomware deployment.
This convergence serves multiple strategic purposes. Financially, it allows groups to sustain operations without direct state funding. Operationally, it introduces additional ambiguity, as attacks can be dismissed as criminal rather than political. Strategically, it enables states to benefit from both disruption and economic harm inflicted on adversaries. In practice, operational overlap between hacktivist and cybercriminal ecosystems has been observed, including shared tooling and infrastructure, further increasing attribution ambiguity.
A recurring pattern observed between 2023 and 2025 involves coordinated hacktivist campaigns targeting countries following the imposition of economic sanctions or military support decisions. In several instances, waves of DDoS attacks, data leaks, and website defacements began within days of official announcements, targeting both government entities and private companies associated with critical industries.
These campaigns often followed a predictable lifecycle. Initial attacks focused on visibility, disrupting public-facing services, and generating media attention. Subsequent phases involved claims of data breaches, some genuine and others exaggerated or fabricated. Finally, sustained low-level disruptions continued for weeks or months, maintaining pressure while avoiding escalation.
The consistency of this pattern across multiple geopolitical contexts suggests an operational playbook rather than spontaneous activism. While definitive attribution remains elusive, the strategic alignment and timing strongly indicate the use of hacktivist proxies as a tool of statecraft.

A key weakness exploited by hacktivist proxy operations is the persistent tendency of organizations to deprioritize ideologically motivated disruption as low-sophistication or low-impact activity. Security operations functions often concentrate detection and response resources on advanced malware, ransomware, and insider threats, while treating repeated DDoS attacks or defacement attempts as isolated nuisance events. This approach overlooks the strategic context in which such activity occurs. Without integrating geopolitical awareness, narrative analysis, and temporal correlation into cyber threat intelligence workflows, organizations may fail to recognize coordinated pressure campaigns, misinterpret episodic disruption as random noise, and miss early indicators of future targeting driven by external political developments.
Mitigating hacktivist proxy operations requires treating them as a grey-zone cyber pressure model, rather than as purely technical or criminal incidents. Because these operations exploit timing, visibility, and narrative amplification rather than advanced exploitation, effective response depends on strategic awareness, operational preparedness, and tactical resilience.
The strategic use of hacktivist proxies is likely to expand as geopolitical competition intensifies and norms around cyber conflict remain underdeveloped. Advances in automation, artificial intelligence, and social media manipulation will further enhance the effectiveness of these groups, enabling more targeted, scalable, and psychologically impactful campaigns.
As long as plausible deniability remains viable, states will continue to exploit hacktivist proxies as a low-risk, high-reward tool. Addressing this challenge will require not only technical defences, but also policy innovation, international cooperation, and a more nuanced understanding of how cyber operations intersect with global politics.
Hacktivist Proxy Operations represent a structurally distinct and increasingly normalized feature of contemporary cyber conflict. Rather than relying on covert access, advanced tooling, or formal command structures, these operations exploit timing, narrative alignment, and deniability to impose strategic pressure at moments of geopolitical sensitivity. Their effectiveness lies not in technical sophistication, but in their ability to generate visibility, disruption, and psychological impact while remaining below established thresholds for escalation.
This report demonstrates that hacktivist proxy activity is best understood not as isolated incidents or a variant of traditional hacktivism, but as a repeatable operational model. Through structured analysis of open-source intelligence and underground cyber ecosystems, the research identified consistent activation patterns linked to external geopolitical triggers, rapid mobilization through public communication channels, targeted disruption of symbolically significant sectors, and controlled de-escalation once signalling objectives are achieved. These characteristics distinguish hacktivist proxy operations from both financially motivated cybercrime and formally sponsored state cyber campaigns.
Importantly, the findings do not rely on claims of direct state control. The strategic value of hacktivist proxies arises precisely from their non-state status. By operating through ideologically aligned actors, states benefit from deniable pressure while avoiding attribution certainty and limiting escalation risk. This ambiguity complicates defensive response and challenges existing cyber threat classification frameworks, which tend to prioritize persistent espionage and high-impact technical compromise over episodic, narrative-driven disruption.
For governments and organizations, the primary risk is not catastrophic technical failure, but persistent low-intensity pressure that accumulates operational cost, erodes public confidence, and diverts defensive resources. Mischaracterizing such activity as a mere nuisance or activism risks underestimating its strategic role, while over-attribution or disproportionate response risks amplifying the narratives that proxy operations are designed to exploit.
Effective mitigation, therefore, requires a shift in perspective. Rather than focusing exclusively on attribution or technical severity, defenders must prioritize resilience, anticipation, and proportional response. Integrating geopolitical context into cyber threat assessment, preparing for episodic surges in disruptive activity, and managing public communication with discipline are as critical as deploying technical controls. Recognizing hacktivist proxy operations as a distinct category of cyber pressure enables more accurate risk assessment and more effective defensive planning.
As geopolitical competition increasingly unfolds in the grey zone, deniable cyber pressure is likely to remain a preferred instrument. Hacktivist proxies offer a low-cost, adaptable, and politically insulated means of signalling intent and imposing friction. Understanding this model and responding with clarity and restraint is essential for navigating an increasingly ambiguous and contested cyber domain.